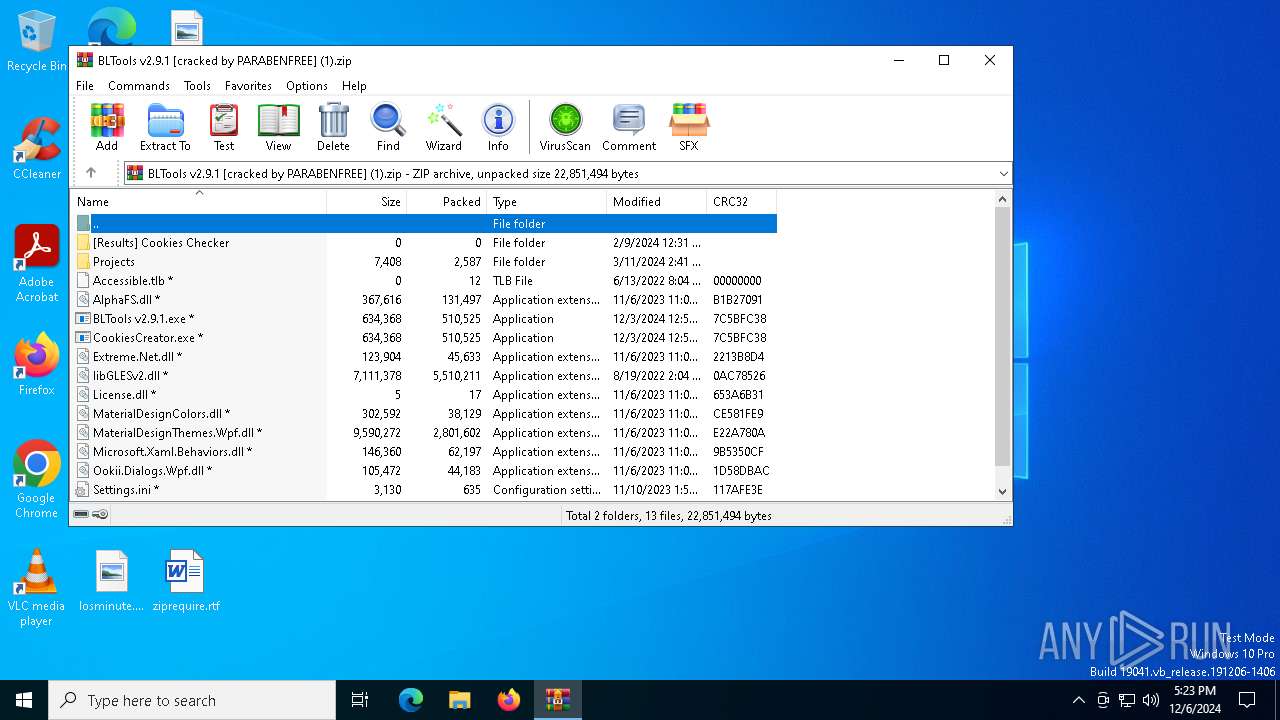
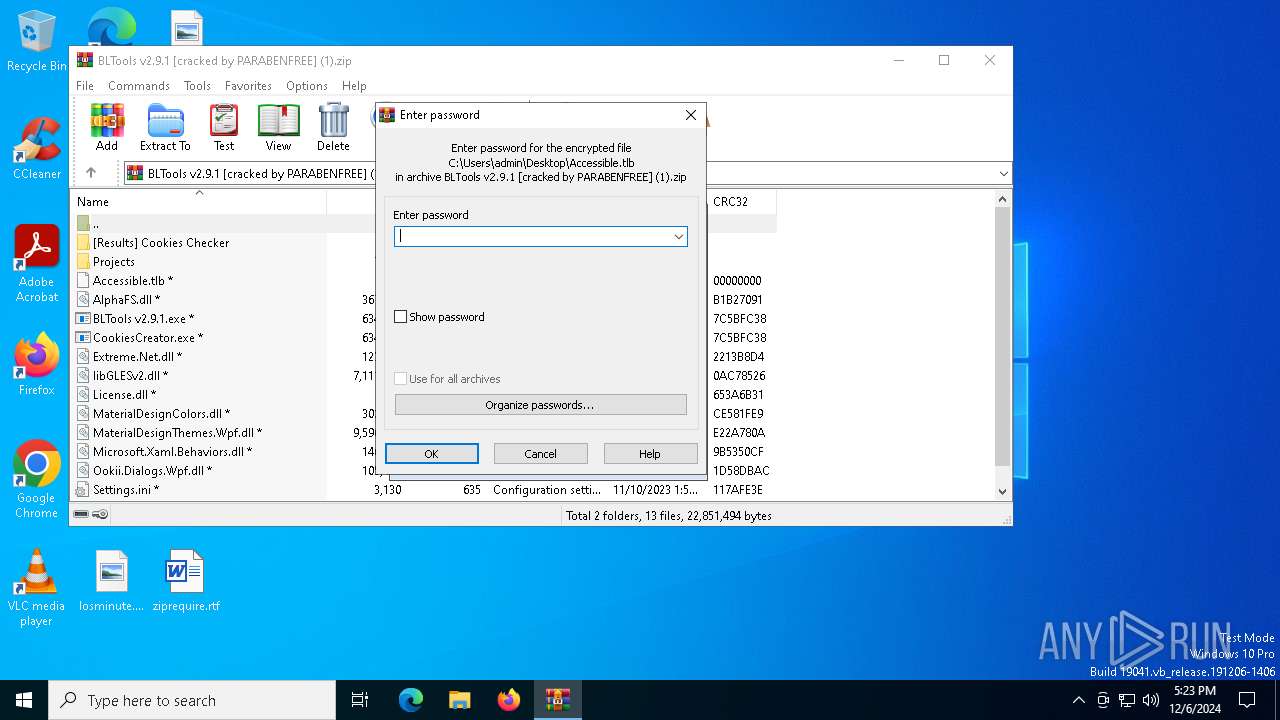
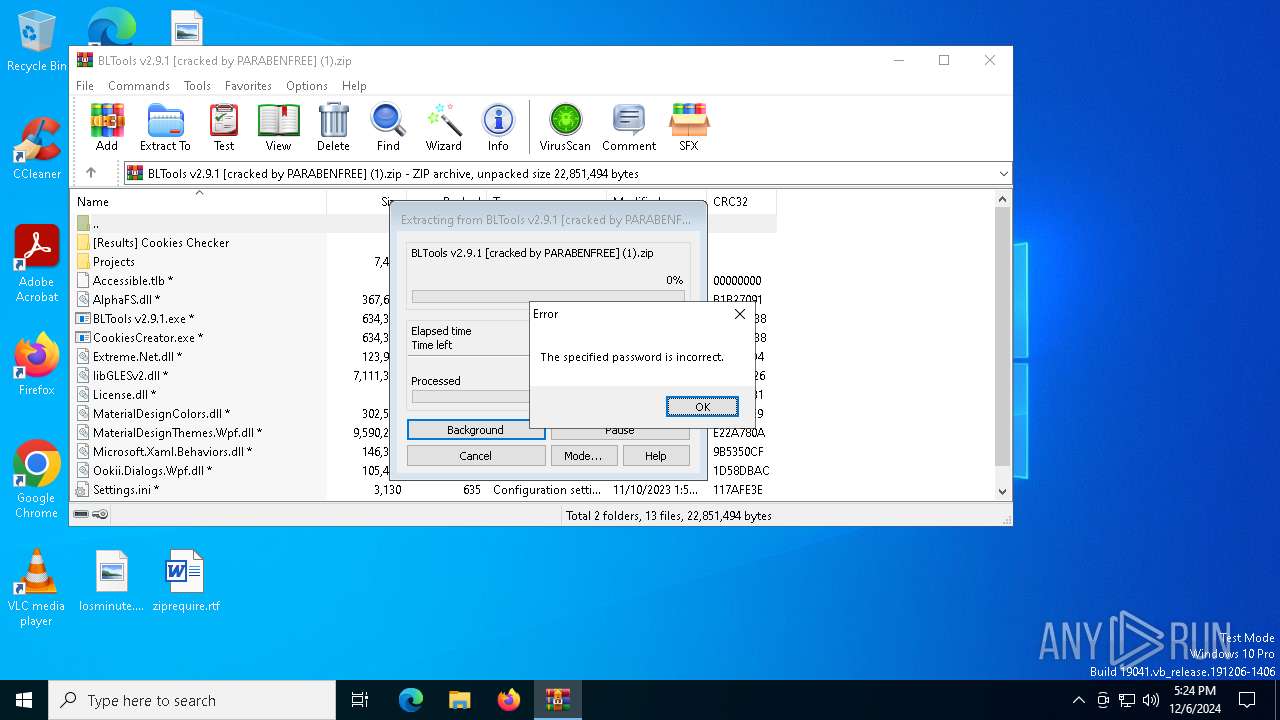
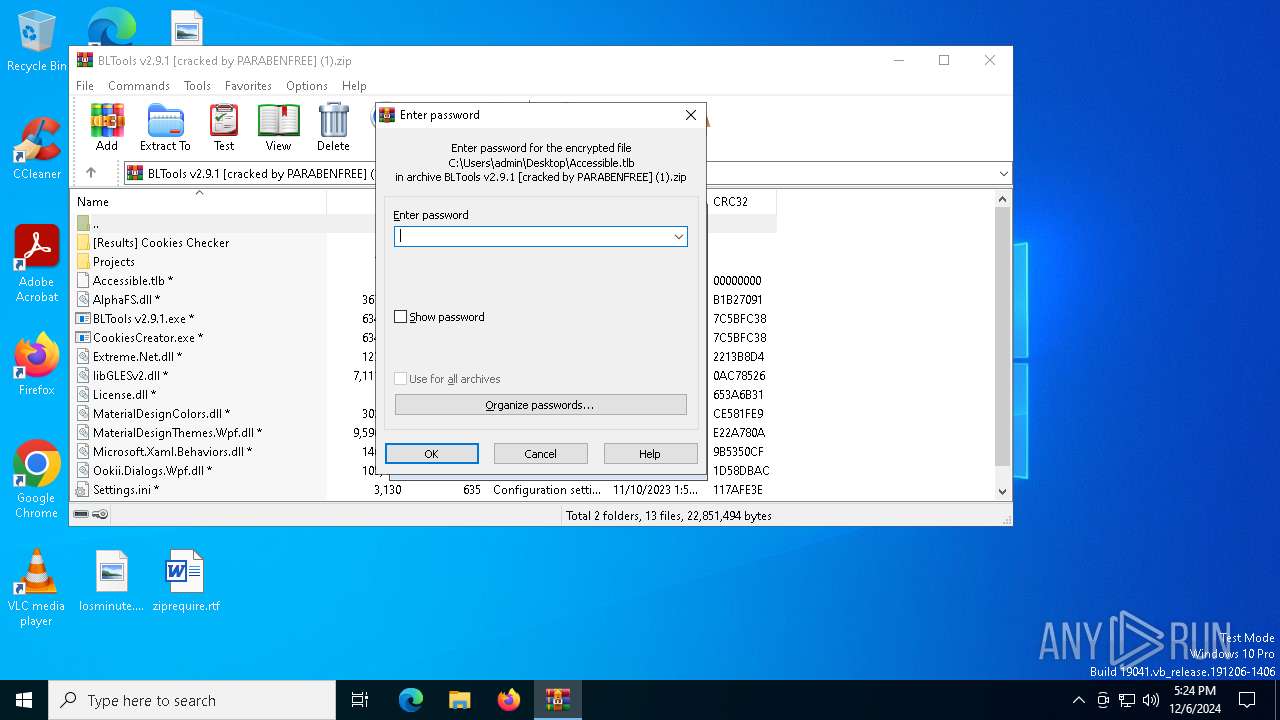
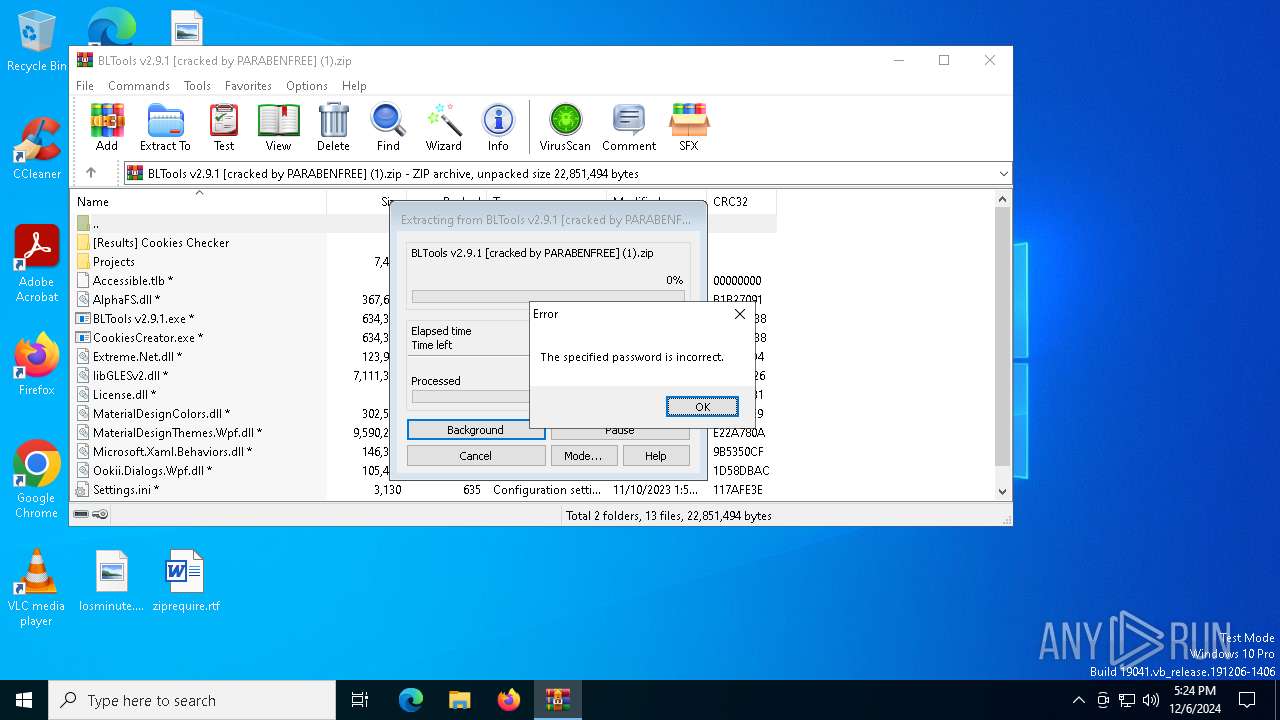
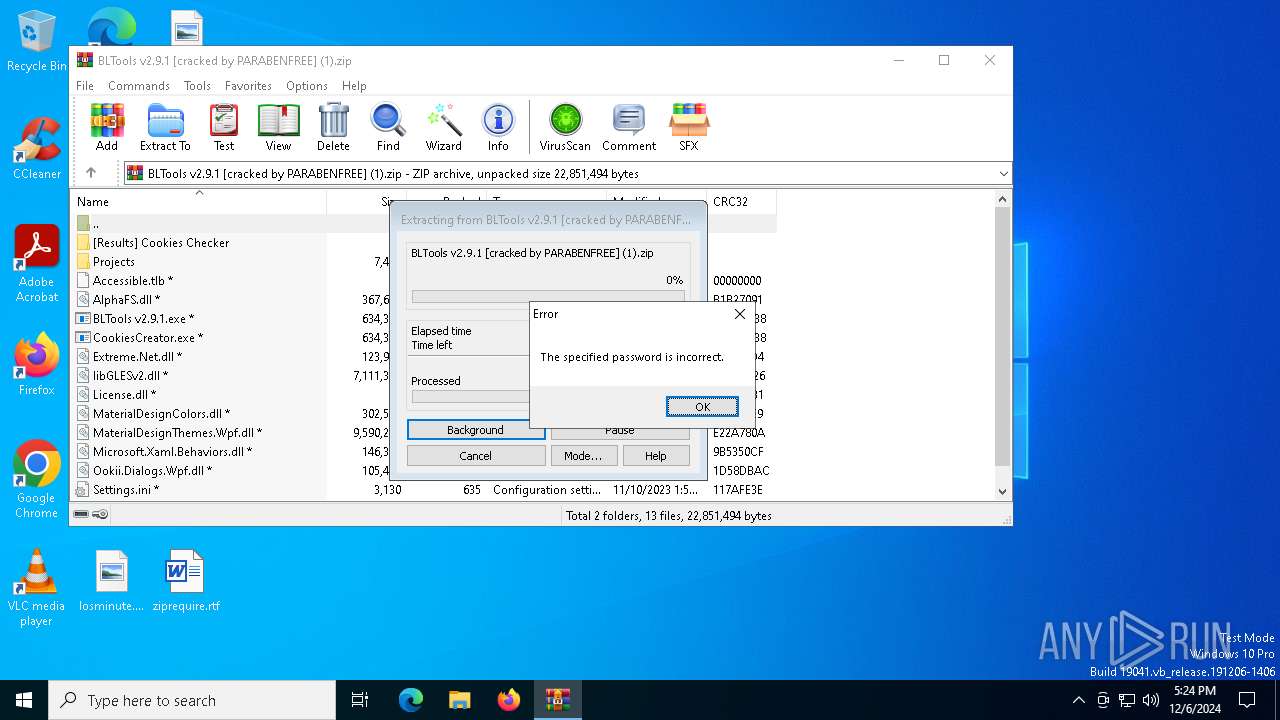
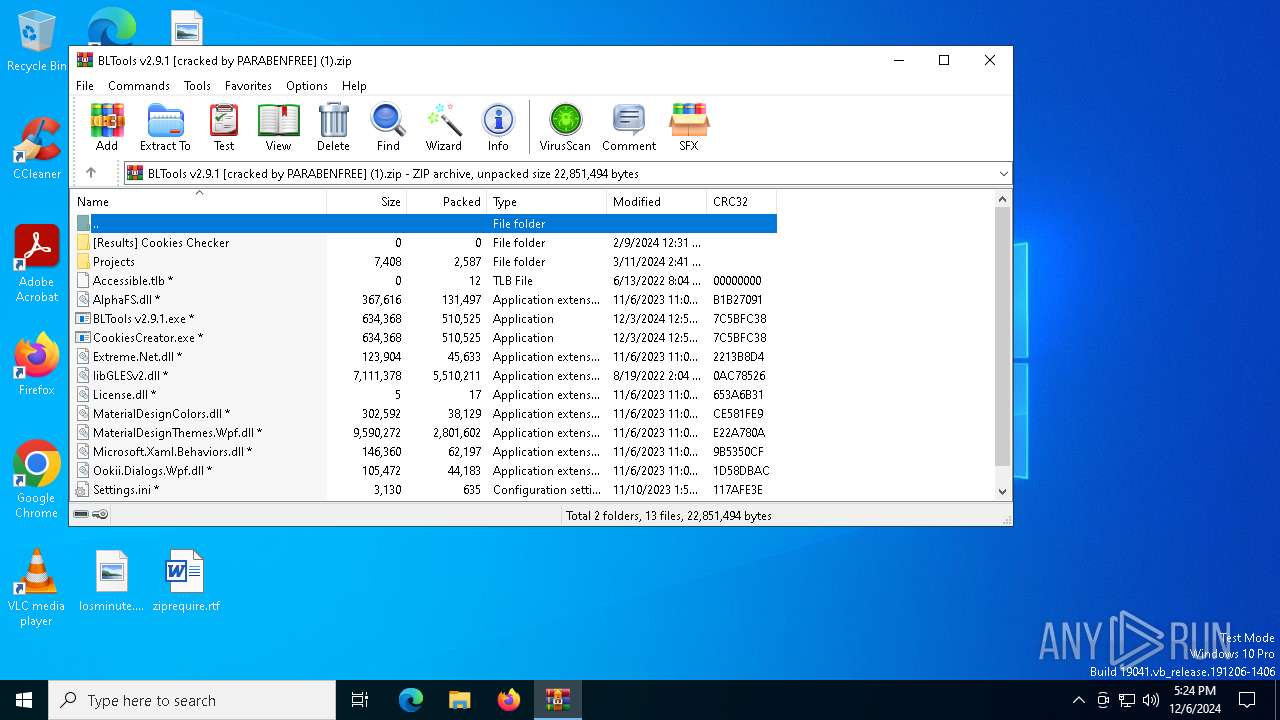
| File name: | BLTools v2.9.1 [cracked by PARABENFREE] (1).zip |
| Full analysis: | https://app.any.run/tasks/b6d570e9-5822-487c-8fbe-80b427b51e88 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 06, 2024, 17:23:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F2E36BE3AB96C5F0FA661C7489AC9CAE |
| SHA1: | 1FC3E7C86A05901ECD3CAE050C61EAC90337186A |
| SHA256: | 956321A423FA04E9A3B2842B099CCCB0F9779AB8B01C5676000366460CA0E693 |
| SSDEEP: | 98304:kRCDFmkfpRC8E7UCIZRLo0q/anDTrbtVSC9m17jd5jgi4B92zPXoUX5f4impRZgs:voKauZB8NV/JYXT+3RQezMn |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- aspnet_regiis.exe (PID: 5200)
Connects to the CnC server
- svchost.exe (PID: 2192)
Actions looks like stealing of personal data
- aspnet_regiis.exe (PID: 5200)
Steals credentials from Web Browsers
- aspnet_regiis.exe (PID: 5200)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6404)
Executable content was dropped or overwritten
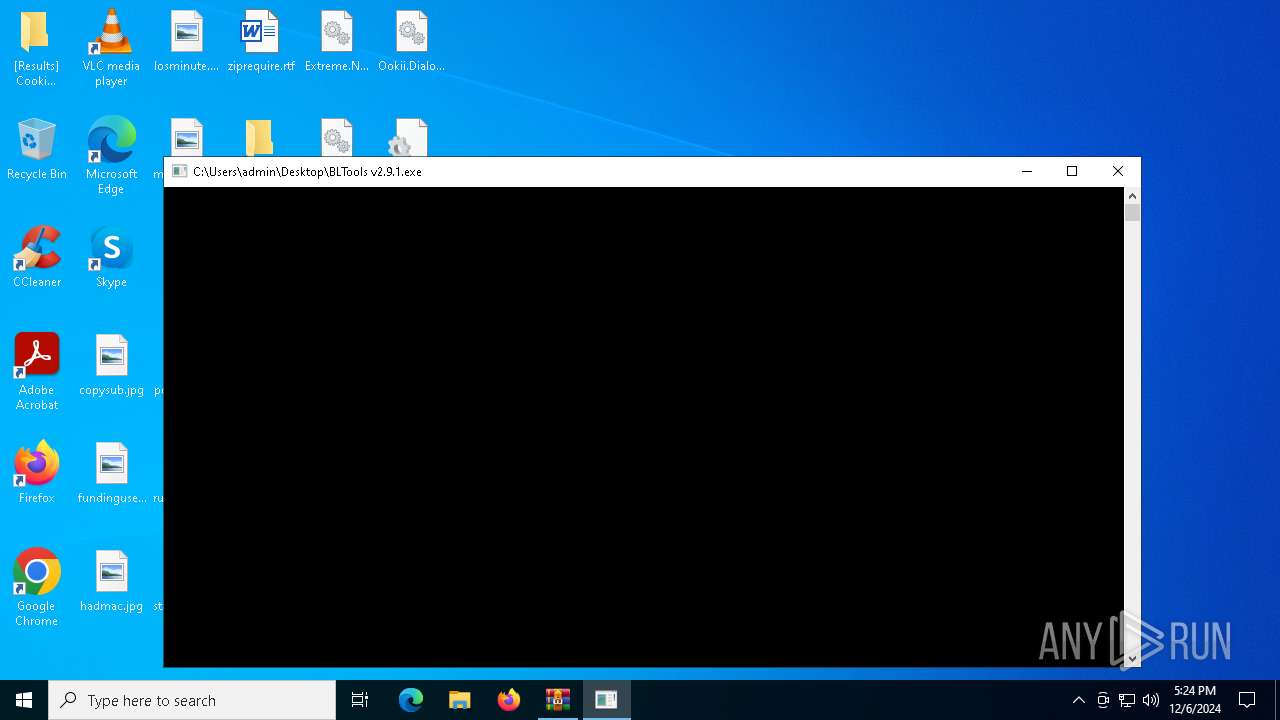
- BLTools v2.9.1.exe (PID: 7160)
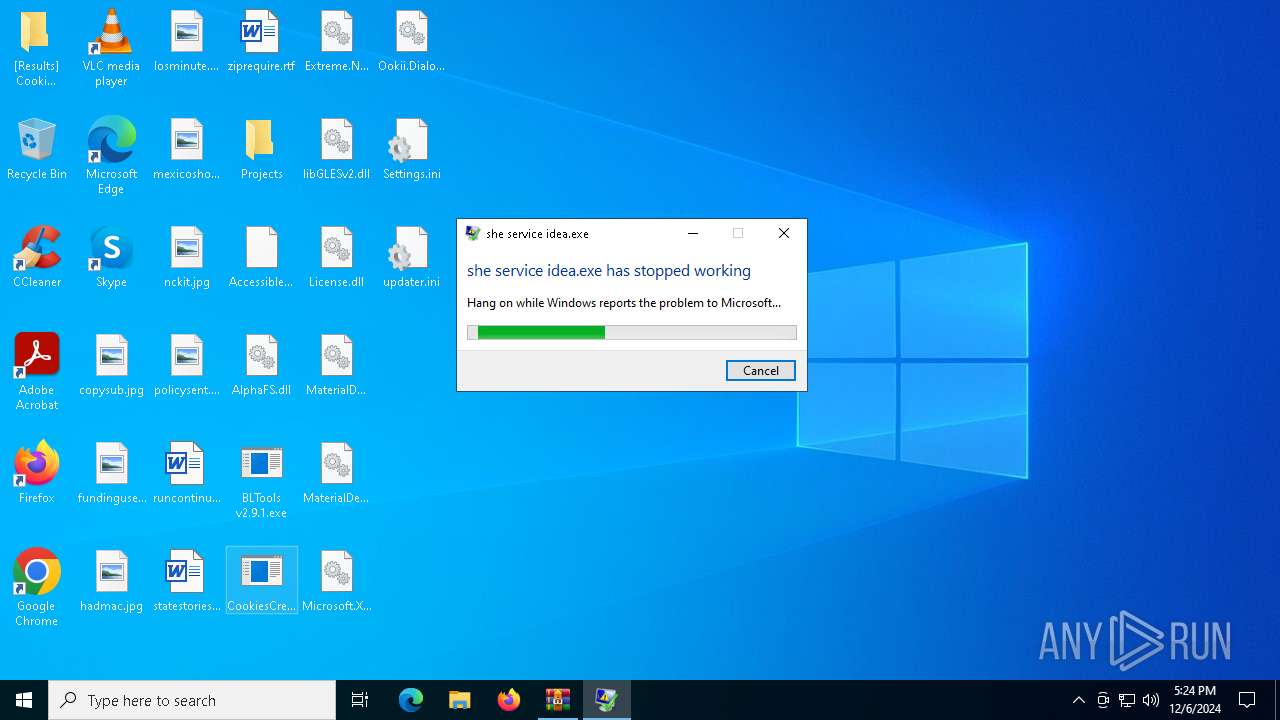
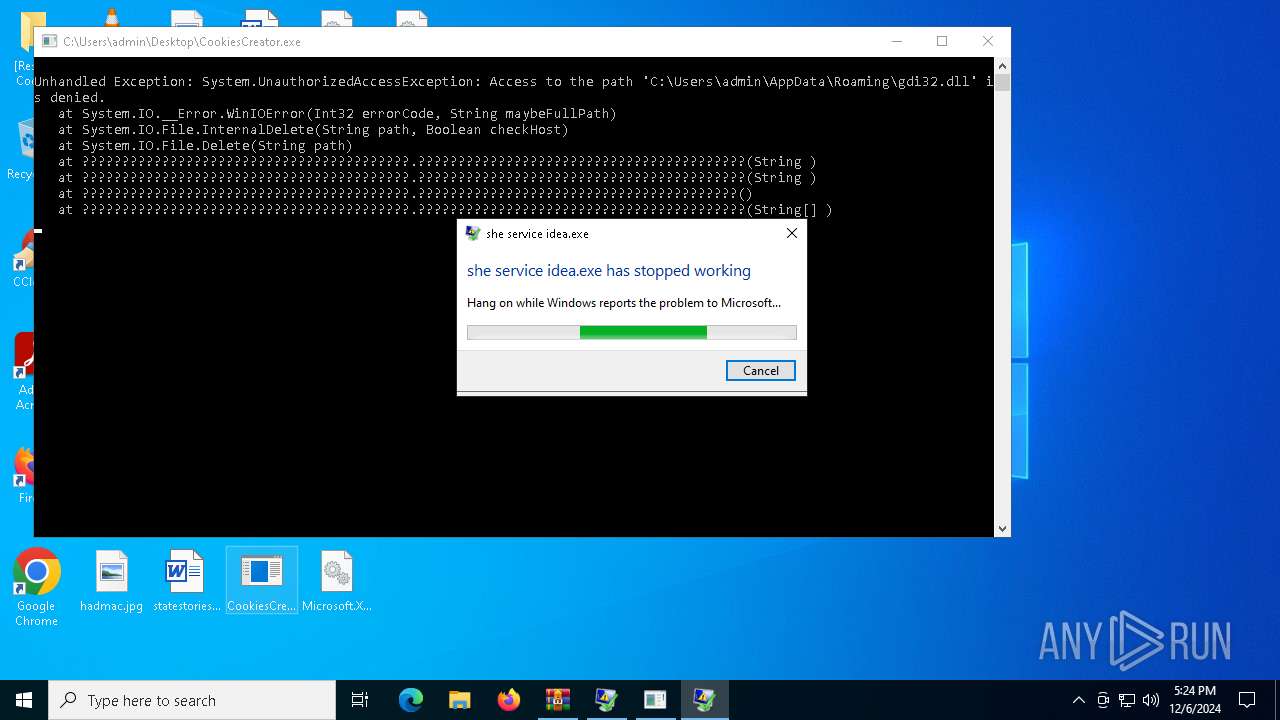
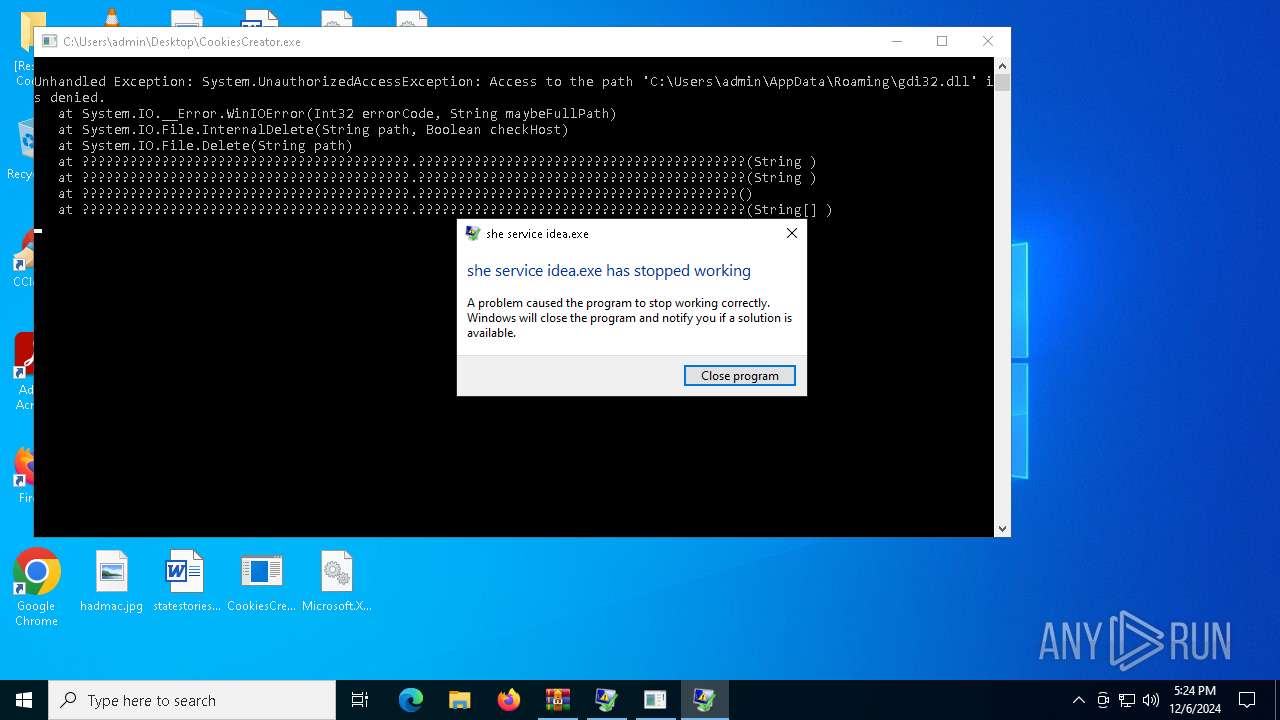
Executes application which crashes
- BLTools v2.9.1.exe (PID: 7160)
- CookiesCreator.exe (PID: 5728)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- aspnet_regiis.exe (PID: 5200)
INFO
Creates files or folders in the user directory
- BLTools v2.9.1.exe (PID: 7160)
Checks supported languages
- BLTools v2.9.1.exe (PID: 7160)
- aspnet_regiis.exe (PID: 5200)
- CookiesCreator.exe (PID: 5728)
Manual execution by a user
- BLTools v2.9.1.exe (PID: 7160)
- CookiesCreator.exe (PID: 5728)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6404)
The process uses the downloaded file
- WinRAR.exe (PID: 6404)
Reads the computer name
- aspnet_regiis.exe (PID: 5200)
- BLTools v2.9.1.exe (PID: 7160)
- CookiesCreator.exe (PID: 5728)
Reads the software policy settings
- aspnet_regiis.exe (PID: 5200)
- WerFault.exe (PID: 6608)
- WerFault.exe (PID: 4640)
Checks proxy server information
- WerFault.exe (PID: 6608)
- WerFault.exe (PID: 4640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | None |
| ZipModifyDate: | 2022:06:13 11:04:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 12 |
| ZipUncompressedSize: | 12 |
| ZipFileName: | Accessible.tlb |
Total processes
135
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4640 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5728 -s 1192 | C:\Windows\SysWOW64\WerFault.exe | CookiesCreator.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe | BLTools v2.9.1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regiis.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | BLTools v2.9.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CookiesCreator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | "C:\Users\admin\Desktop\CookiesCreator.exe" | C:\Users\admin\Desktop\CookiesCreator.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: she service idea.exe Version: 6.6.5.0 Modules
| |||||||||||||||
| 6404 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\BLTools v2.9.1 [cracked by PARABENFREE] (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6608 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7160 -s 1212 | C:\Windows\SysWOW64\WerFault.exe | BLTools v2.9.1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7160 | "C:\Users\admin\Desktop\BLTools v2.9.1.exe" | C:\Users\admin\Desktop\BLTools v2.9.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: she service idea.exe Version: 6.6.5.0 Modules
| |||||||||||||||
Total events
9 747
Read events
9 720
Write events
14
Delete events
13
Modification events
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BLTools v2.9.1 [cracked by PARABENFREE] (1).zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
9
Suspicious files
6
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\libGLESv2.dll | — | |
MD5:— | SHA256:— | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\CookiesCreator.exe | executable | |
MD5:AC122CD459A0577CE7C7DF2CBD80A946 | SHA256:EA9A6FD7A1B29737431269E1561CEEC117388A23FB086772048968F31FB99668 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\License.dll | text | |
MD5:B08A5C34CF0A06615DA2CA89010D8B4F | SHA256:04CC5B3B49A7E9E9B6C66C7BE59A20992BF2653746B5D43829C383FB233F88FA | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\Extreme.Net.dll | executable | |
MD5:F79F0E3A0361CAC000E2D3553753CD68 | SHA256:8A6518AB7419FBEC3AC9875BAA3AFB410AD1398C7AA622A09CD9084EC6CADFCD | |||
| 6608 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_BLTools v2.9.1.e_be657c126eb4f8e3d933e91d67fff3f72f3b38_4579b01a_08b9ec13-57c0-4f73-bcd3-749a2a00fa6a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft.Xaml.Behaviors.dll | executable | |
MD5:95F46F34C099421D917D5FEADBB33EDB | SHA256:8E77A1DD5E2DF4D4AF801376CC3428B082EB49FCB6E647B933967FAE12AD9D5D | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\MaterialDesignColors.dll | executable | |
MD5:5C108C4DA6D03F0FA2C3B4DC7890CB52 | SHA256:B5EC30C93B1D2B4631EE2B178750EC92E302E2E331090EC9783981B9572354F8 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\AlphaFS.dll | executable | |
MD5:F2F6F6798D306D6D7DF4267434B5C5F9 | SHA256:837F2CEAB6BBD9BC4BF076F1CB90B3158191888C3055DD2B78A1E23F1C3AAFDD | |||
| 4640 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_CookiesCreator.e_f92cf0c8426ef23efa2fe3e4680653a6353936b_5a1d59c2_2cd638d3-1832-41de-a18e-78be3834ce8e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\Projects\google photos.proj | text | |
MD5:354C88CAAF500C182A3BE34831415665 | SHA256:86C21411E7A7C4FB5AFE4930E5B328C337FDA9B1F92AC2090BDA4F589928CC50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
39
DNS requests
18
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6608 | WerFault.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6608 | WerFault.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6988 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6988 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.19:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (atten-supporse .biz) |
5200 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (atten-supporse .biz in TLS SNI) |
— | — | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (atten-supporse .biz in TLS SNI) |
5200 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (atten-supporse .biz in TLS SNI) |