| URL: | https://5.252.192.117 |
| Full analysis: | https://app.any.run/tasks/7cf07e16-e567-4f0e-a7d4-072855752acf |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 18, 2019, 08:13:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FDCC64B0B7BB5191D4AEB6F3274CE2BA |
| SHA1: | CC6C961DBF3CF22E450B5C4876D71B5F0AEFEDF5 |
| SHA256: | 955B3BFCC7F8CEE1650CA8EE1B95CB7BDC642D93F9EF78992E990D881F6C4EDB |
| SSDEEP: | 3:N80XQrS:20XQrS |
MALICIOUS
Downloads executable files from the Internet
- iexplore.exe (PID: 3496)
Application was dropped or rewritten from another process
- jss[1].exe (PID: 2136)
- cjihe[1].exe (PID: 2512)
- file[1].exe (PID: 2168)
- j[1].exe (PID: 2344)
- RegAsm.exe (PID: 4052)
- ssl[1].exe (PID: 1828)
- file[1].exe (PID: 4092)
- file[1].exe (PID: 3124)
- u[1].exe (PID: 916)
- file[1].exe (PID: 2640)
- remcos.exe (PID: 2708)
- file[1].exe (PID: 2240)
- file[1].exe (PID: 1448)
- remcos.exe (PID: 4044)
- file[1].exe (PID: 2216)
- file[1].exe (PID: 2696)
- file[1].exe (PID: 2460)
- file[1].exe (PID: 1736)
- file[1].exe (PID: 3824)
- file[1].exe (PID: 3752)
- file[1].exe (PID: 696)
- file[1].exe (PID: 2204)
- file[1].exe (PID: 2884)
- file[1].exe (PID: 1684)
- file[1].exe (PID: 2152)
- file[1].exe (PID: 2484)
- file[1].exe (PID: 3064)
- file[1].exe (PID: 1868)
- file[1].exe (PID: 1420)
- file[1].exe (PID: 2936)
- file[1].exe (PID: 2256)
- file[1].exe (PID: 3032)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3752)
- schtasks.exe (PID: 2980)
Uses Task Scheduler to run other applications
- j[1].exe (PID: 2344)
- u[1].exe (PID: 916)
REMCOS was detected
- vbc.exe (PID: 932)
- file[1].exe (PID: 4092)
- file[1].exe (PID: 2640)
- file[1].exe (PID: 1448)
- remcos.exe (PID: 4044)
Changes the autorun value in the registry
- RegAsm.exe (PID: 4052)
- file[1].exe (PID: 2168)
- file[1].exe (PID: 3124)
- file[1].exe (PID: 2640)
- remcos.exe (PID: 2708)
- remcos.exe (PID: 4044)
- file[1].exe (PID: 2240)
Connects to CnC server
- vbc.exe (PID: 932)
AGENTTESLA was detected
- RegAsm.exe (PID: 4052)
Known privilege escalation attack
- file[1].exe (PID: 4092)
- file[1].exe (PID: 2640)
- remcos.exe (PID: 4044)
- file[1].exe (PID: 1448)
Detected logs from REMCOS RAT
- vbc.exe (PID: 932)
- remcos.exe (PID: 4044)
Actions looks like stealing of personal data
- vbc.exe (PID: 2560)
- RegAsm.exe (PID: 4052)
- vbc.exe (PID: 1160)
- vbc.exe (PID: 3532)
- vbc.exe (PID: 4020)
Uses NirSoft utilities to collect credentials
- vbc.exe (PID: 1160)
- vbc.exe (PID: 2560)
- vbc.exe (PID: 3532)
- vbc.exe (PID: 4020)
Stealing of credential data
- vbc.exe (PID: 2560)
- vbc.exe (PID: 1160)
- vbc.exe (PID: 4020)
- vbc.exe (PID: 3532)
UAC/LUA settings modification
- reg.exe (PID: 3928)
- reg.exe (PID: 3928)
SUSPICIOUS
Reads the BIOS version
- cjihe[1].exe (PID: 2512)
- jss[1].exe (PID: 2136)
- ssl[1].exe (PID: 1828)
- u[1].exe (PID: 916)
Reads Windows Product ID
- RegAsm.exe (PID: 2444)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3712)
- iexplore.exe (PID: 3496)
- RegAsm.exe (PID: 4052)
- file[1].exe (PID: 2168)
- file[1].exe (PID: 2640)
Executes scripts
- ssl[1].exe (PID: 1828)
- j[1].exe (PID: 2344)
- vbc.exe (PID: 4072)
- u[1].exe (PID: 916)
- file[1].exe (PID: 2640)
Creates files in the user directory
- RegAsm.exe (PID: 4052)
- file[1].exe (PID: 2168)
- vbc.exe (PID: 4072)
- vbc.exe (PID: 932)
- file[1].exe (PID: 2640)
Application launched itself
- file[1].exe (PID: 2168)
- vbc.exe (PID: 4072)
- file[1].exe (PID: 3124)
- remcos.exe (PID: 2708)
- file[1].exe (PID: 2240)
Modifies the open verb of a shell class
- file[1].exe (PID: 4092)
- file[1].exe (PID: 2640)
- file[1].exe (PID: 1448)
- remcos.exe (PID: 4044)
Writes files like Keylogger logs
- vbc.exe (PID: 932)
- remcos.exe (PID: 4044)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 3776)
- vbc.exe (PID: 1160)
- vbc.exe (PID: 2848)
- vbc.exe (PID: 4020)
Suspicious files were dropped or overwritten
- file[1].exe (PID: 2168)
Starts CMD.EXE for commands execution
- file[1].exe (PID: 2640)
- WScript.exe (PID: 2068)
- remcos.exe (PID: 4044)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 880)
- cmd.exe (PID: 4036)
Checks for external IP
- RegAsm.exe (PID: 4052)
INFO
Application launched itself
- iexplore.exe (PID: 3712)
Changes internet zones settings
- iexplore.exe (PID: 3712)
Reads internet explorer settings
- iexplore.exe (PID: 3496)
Reads Internet Cache Settings
- iexplore.exe (PID: 3496)
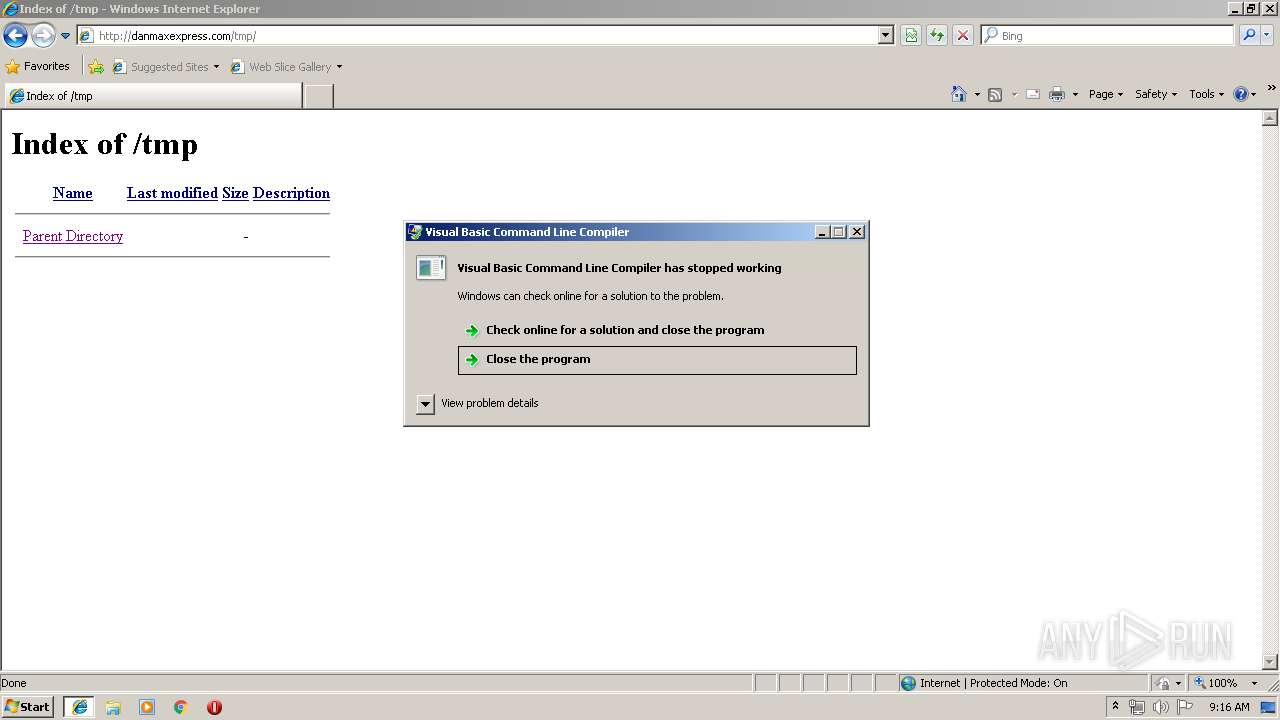
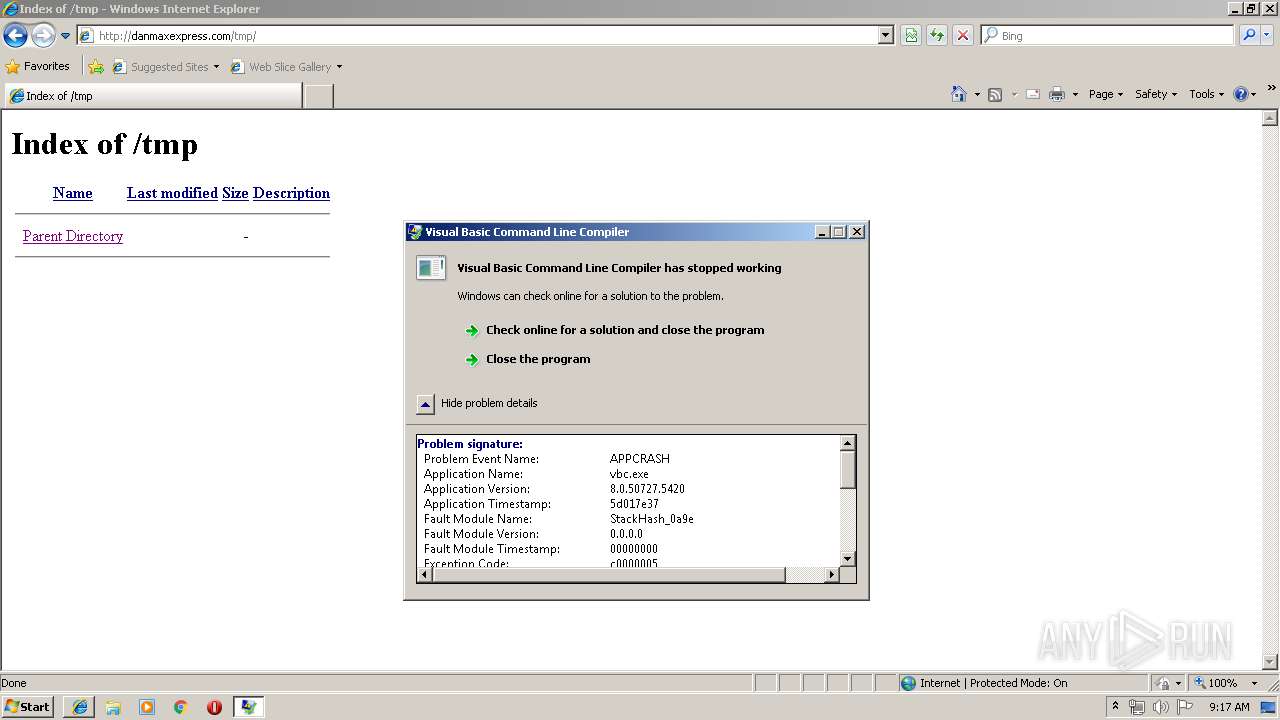
Application was crashed
- vbc.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
109
Monitored processes
58
Malicious processes
24
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe | — | file[1].exe | |||||||||||
User: admin Company: philandro Software GmbH Integrity Level: HIGH Description: AnyDesk Exit code: 1 Version: 702.827.826.899 Modules
| |||||||||||||||
| 880 | /k %windir%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\cmd.exe | — | file[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 916 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\u[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\u[1].exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 932 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | ssl[1].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 984 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | u[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 1 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1160 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\lqptzmhmikyzttpjai" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | vbc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1420 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe | — | file[1].exe | |||||||||||
User: admin Company: philandro Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 1 Version: 702.827.826.899 Modules
| |||||||||||||||
| 1448 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe | file[1].exe | ||||||||||||
User: admin Company: philandro Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 702.827.826.899 Modules
| |||||||||||||||
| 1684 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe | — | file[1].exe | |||||||||||
User: admin Company: philandro Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 1 Version: 702.827.826.899 Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\file[1].exe | — | file[1].exe | |||||||||||
User: admin Company: philandro Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 1 Version: 702.827.826.899 Modules
| |||||||||||||||
Total events
1 570
Read events
1 404
Write events
162
Delete events
4
Modification events
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000078000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {F6CAA457-A933-11E9-95C0-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3712) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30707000400120008000D002F002301 | |||
Executable files
15
Suspicious files
3
Text files
45
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3712 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3712 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:— | SHA256:— | |||
| 3712 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019071820190719\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\RIMVM10U\danmaxexpress_com[1].txt | — | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\RIMVM10U\kk[1].txt | — | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019071820190719\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\RIMVM10U\defaultwebpage[1].htm | html | |
MD5:— | SHA256:— | |||
| 3496 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\THOJPES7\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
96
DNS requests
6
Threats
67
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
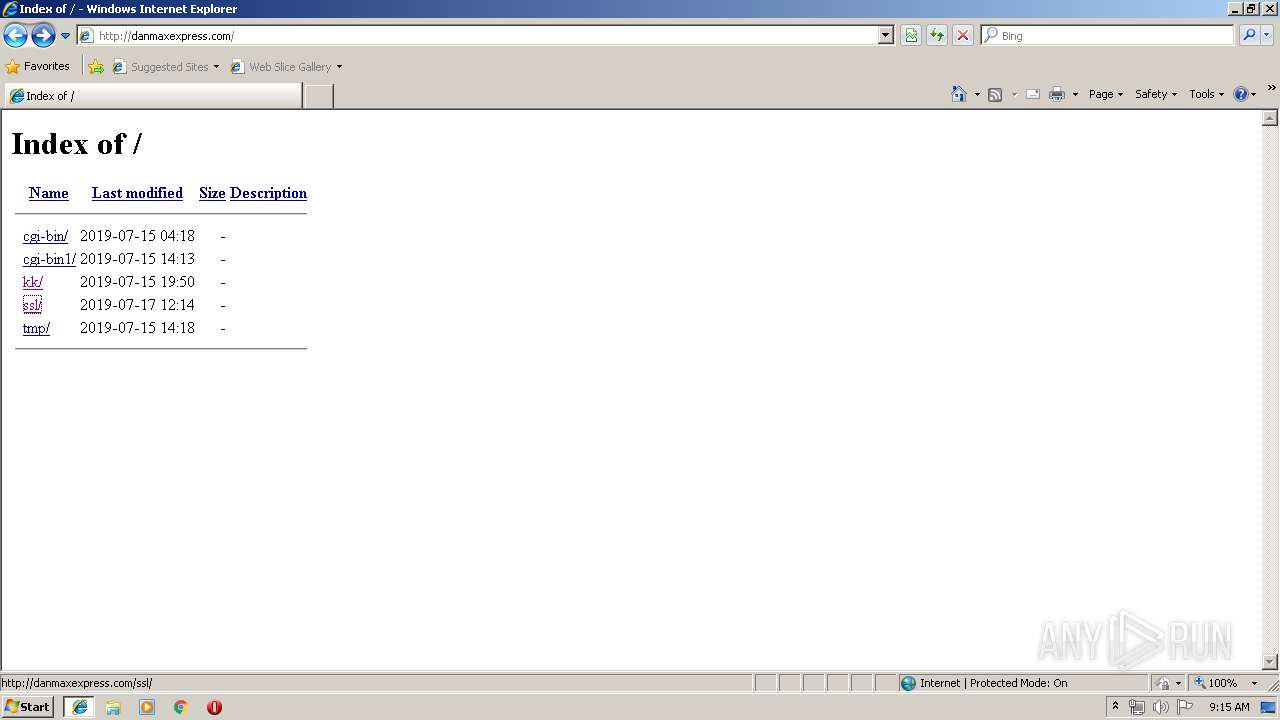
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/ | US | html | 1.28 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/kk/ | US | html | 1.10 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 5.252.192.117:80 | http://5.252.192.117/cgi-sys/defaultwebpage.cgi | unknown | html | 6.75 Kb | suspicious |
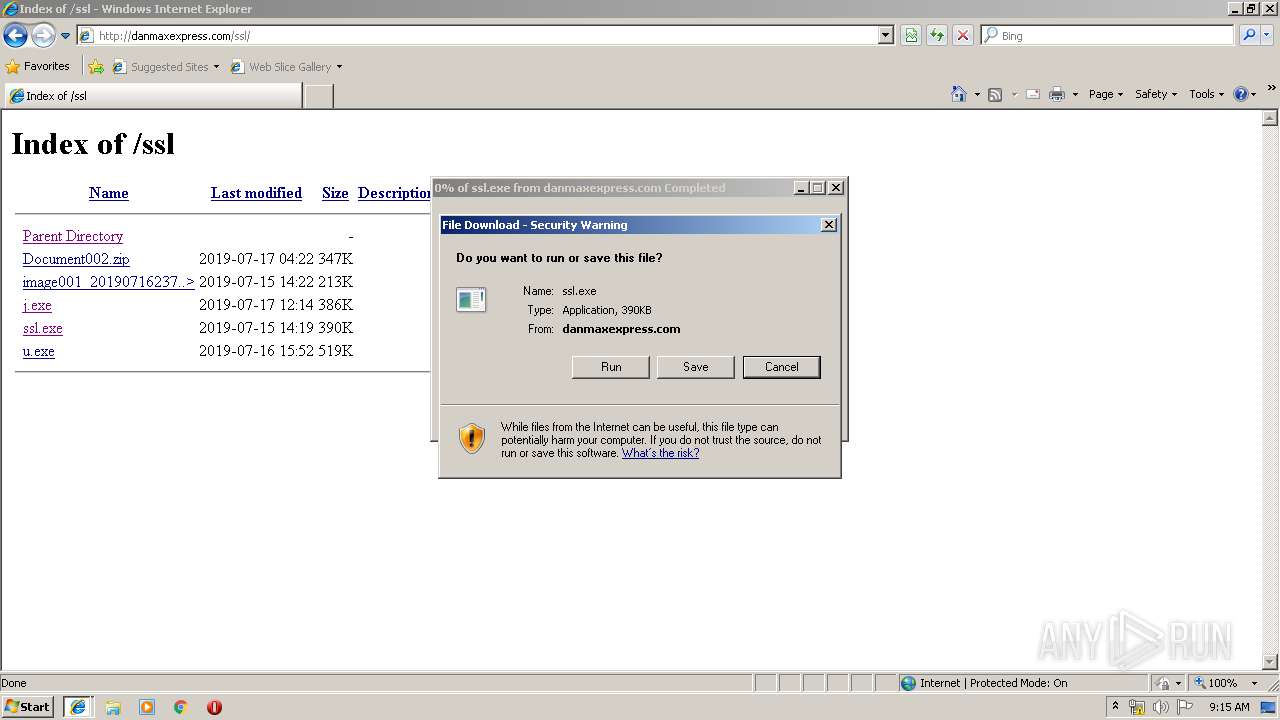
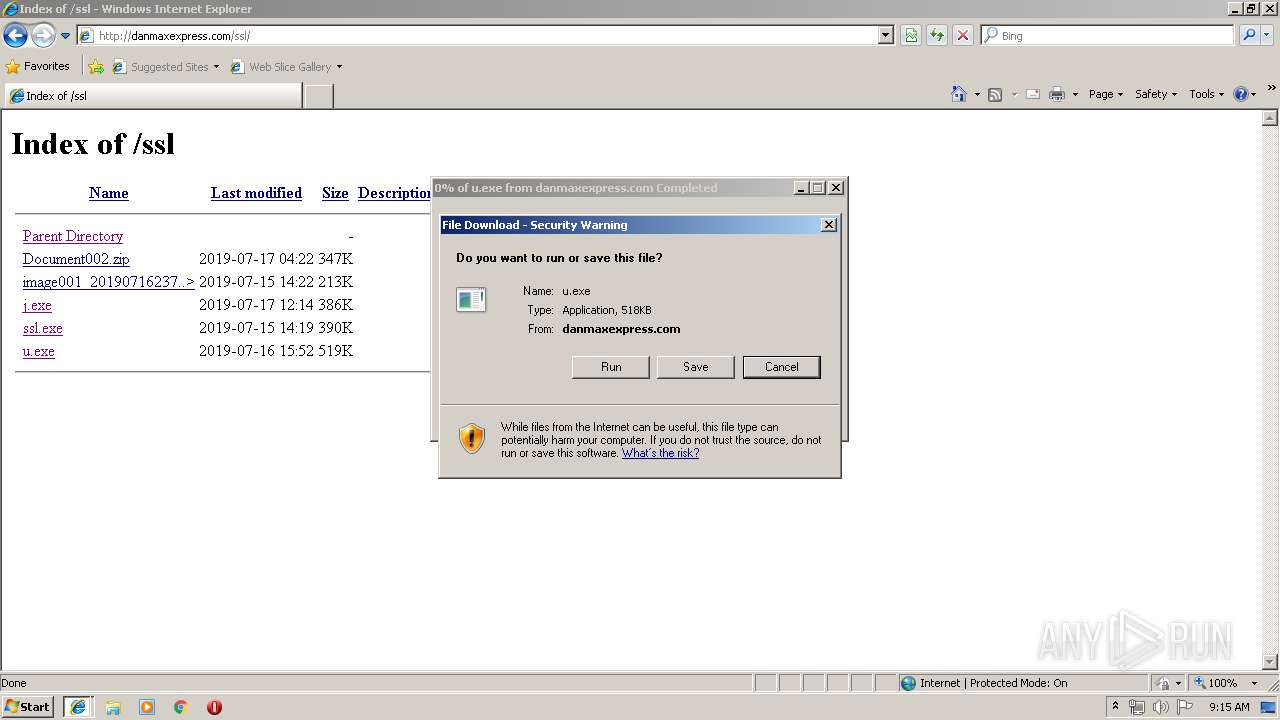
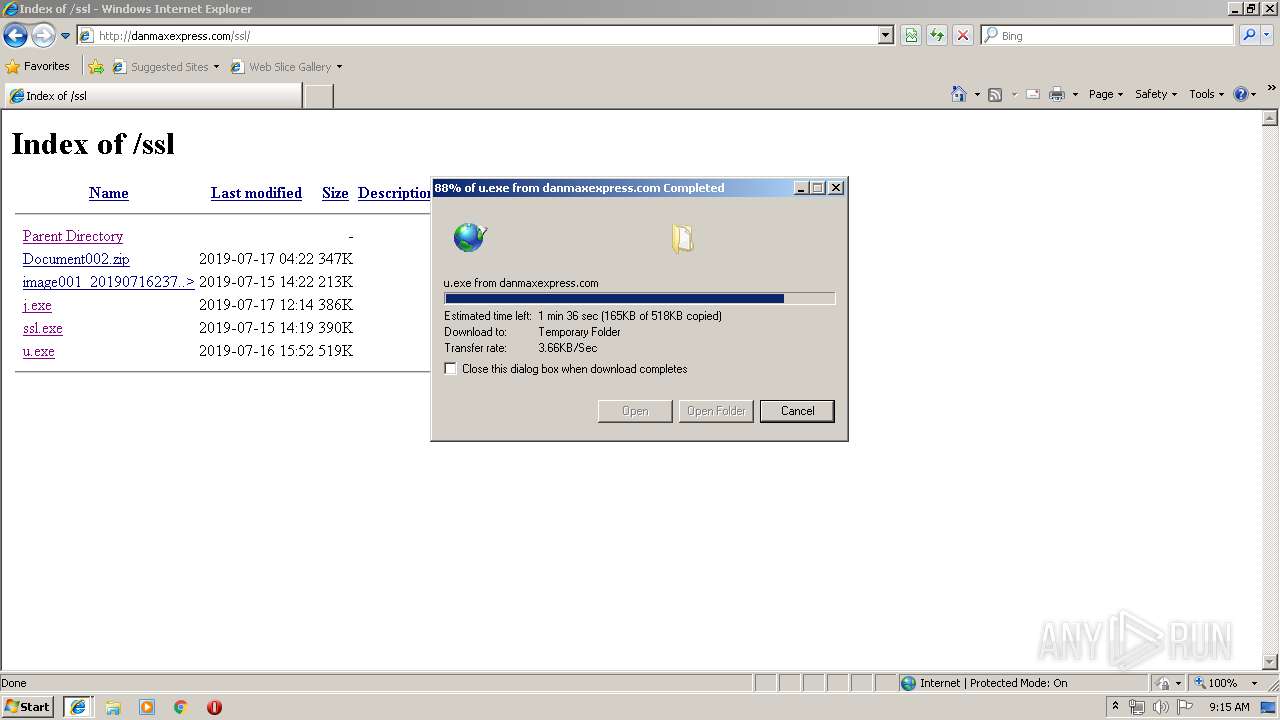
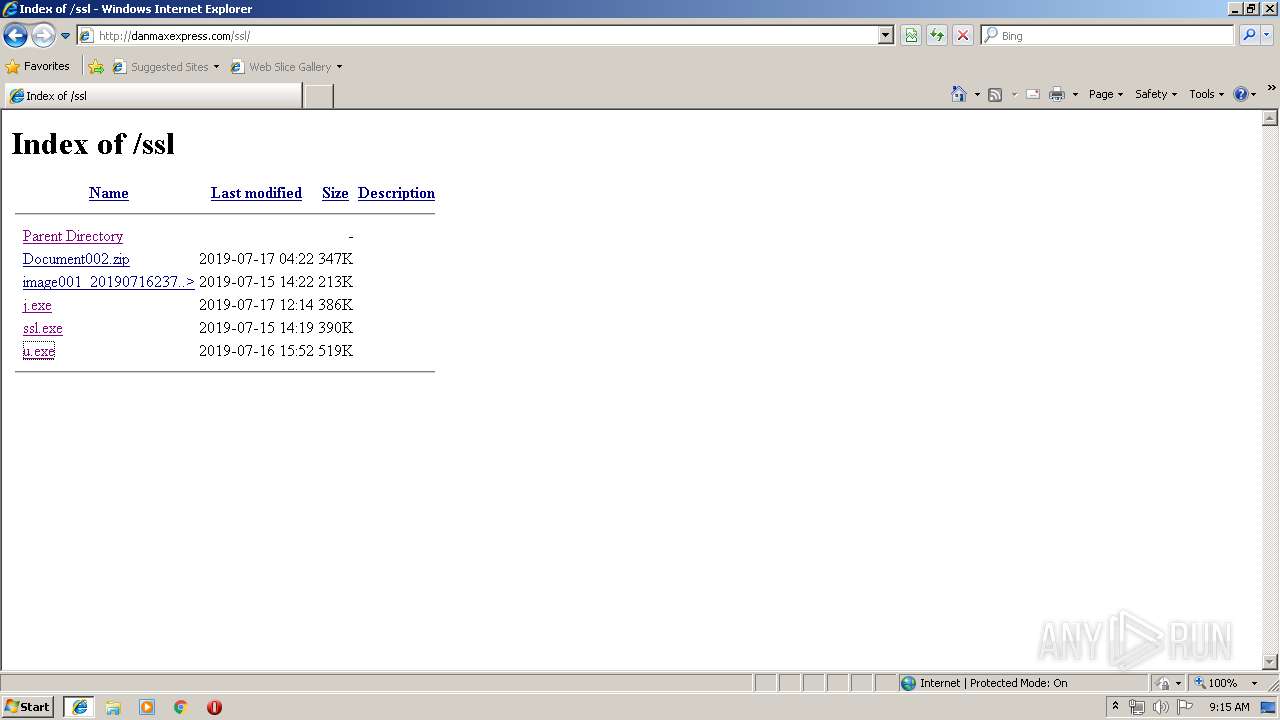
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/kk/cjihe.exe | US | executable | 518 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/kk/jss.exe | US | executable | 543 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/kk/file.exe | US | executable | 1.18 Mb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/ | US | html | 1.28 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/ssl/ | US | html | 1.46 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/ssl/j.exe | US | executable | 386 Kb | malicious |
3496 | iexplore.exe | GET | 200 | 108.170.57.54:80 | http://danmaxexpress.com/ssl/ssl.exe | US | executable | 390 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3712 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3496 | iexplore.exe | 5.252.192.117:443 | — | — | — | suspicious |
3496 | iexplore.exe | 5.252.192.117:80 | — | — | — | suspicious |
3712 | iexplore.exe | 5.252.192.117:80 | — | — | — | suspicious |
3496 | iexplore.exe | 108.170.57.54:80 | danmaxexpress.com | SECURED SERVERS LLC | US | suspicious |
3712 | iexplore.exe | 108.170.57.54:80 | danmaxexpress.com | SECURED SERVERS LLC | US | suspicious |
4072 | vbc.exe | 185.217.1.186:8320 | faxjohn01.dyn.ddnss.de | Icme Limited | SE | malicious |
932 | vbc.exe | 185.247.228.189:7535 | princedaniels.duckdns.org | — | — | malicious |
4052 | RegAsm.exe | 213.180.193.38:587 | smtp.yandex.com | YANDEX LLC | RU | whitelisted |
4044 | remcos.exe | 185.247.228.253:1998 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
danmaxexpress.com |
| malicious |
faxjohn01.dyn.ddnss.de |
| malicious |
princedaniels.duckdns.org |
| malicious |
smtp.yandex.com |
| malicious |
checkip.amazonaws.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3496 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3496 | iexplore.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
932 | vbc.exe | A Network Trojan was detected | ET TROJAN Remcos RAT Checkin 23 |
932 | vbc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Remcos RAT Checkin |
932 | vbc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Remcos RAT |
932 | vbc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Remcos RAT Checkin |
932 | vbc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Remcos RAT |
932 | vbc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Remcos RAT Checkin |
932 | vbc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Remcos RAT |
2 ETPRO signatures available at the full report