| File name: | SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469 |
| Full analysis: | https://app.any.run/tasks/775c2ba4-9251-4cfc-9acb-dee55cb899ed |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 08, 2023, 17:06:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 74F28E28DF4386BEFA5B4167FA511B33 |
| SHA1: | 76900B7A8D1D63F04912C2C7A8D2D284E81C134F |
| SHA256: | 9554E7EF83F9C1AABED52BE7A308D7E25C99E7D71E006146AEE045D29784F92D |
| SSDEEP: | 49152:AzRt3OiddajazTdIabTt8rgzhJ+VJ5wLrSBhEQ1GwSDWVaUimKoWQ8Gk+BvD58fO:AzRkOa2zTdIkWMzhJ8SSowSiEpmvjjxE |
MALICIOUS
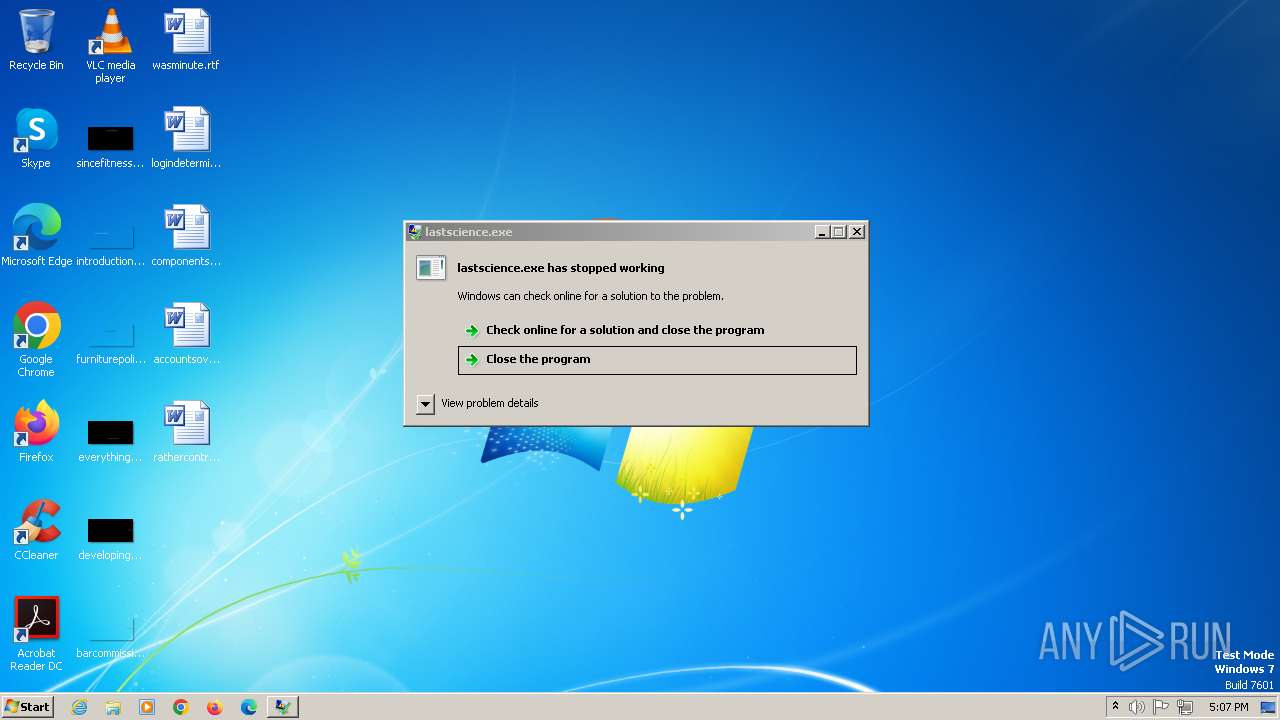
Drops the executable file immediately after the start
- SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe (PID: 2092)
- lastsciiencepro.exe (PID: 2076)
Application was dropped or rewritten from another process
- lastscience.exe (PID: 2952)
- lastsciiencepro.exe (PID: 2076)
- lastscience.exe (PID: 2832)
- lastscience.exe (PID: 1308)
- lastsciience.exe (PID: 2828)
- lastscience.exe (PID: 2764)
Connects to the CnC server
- lastscience.exe (PID: 1308)
LUMMA was detected
- lastscience.exe (PID: 1308)
SUSPICIOUS
Process drops legitimate windows executable
- SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe (PID: 2092)
Reads the Internet Settings
- lastscience.exe (PID: 2952)
- lastscience.exe (PID: 1308)
- lastsciience.exe (PID: 2828)
Connects to the server without a host name
- lastscience.exe (PID: 2952)
- lastsciience.exe (PID: 2828)
Application launched itself
- lastscience.exe (PID: 2952)
INFO
Checks supported languages
- SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe (PID: 2092)
- lastsciiencepro.exe (PID: 2076)
- lastscience.exe (PID: 2952)
- lastscience.exe (PID: 1308)
- lastsciience.exe (PID: 2828)
Create files in a temporary directory
- SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe (PID: 2092)
- lastsciiencepro.exe (PID: 2076)
Reads the computer name
- lastscience.exe (PID: 2952)
- lastsciience.exe (PID: 2828)
- lastscience.exe (PID: 1308)
Reads the machine GUID from the registry
- lastscience.exe (PID: 2952)
- lastscience.exe (PID: 1308)
- lastsciience.exe (PID: 2828)
Reads Environment values
- lastscience.exe (PID: 2952)
- lastsciience.exe (PID: 2828)
Checks proxy server information
- lastscience.exe (PID: 1308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2062:07:25 14:18:00+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.2 |
| CodeSize: | 31744 |
| InitializedDataSize: | 1619456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8200 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.10.5 |
| ProductVersionNumber: | 1.4.10.5 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | SoFi |
| FileDescription: | POPSUGAR powers the optimism and dreams of women around the |
| FileVersion: | 1.4.10.5 |
| InternalName: | SendEffectively |
| ProductName: | Process Prevailing |
| ProductVersion: | 1.4.10.5 |
Total processes
39
Monitored processes
7
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1308 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | lastscience.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2076 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\lastsciiencepro.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\lastsciiencepro.exe | — | SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe | — | explorer.exe | |||||||||||
User: admin Company: SoFi Integrity Level: MEDIUM Description: POPSUGAR powers the optimism and dreams of women around the Exit code: 0 Version: 1.4.10.5 Modules
| |||||||||||||||
| 2764 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | — | lastscience.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2828 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastsciience.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastsciience.exe | lastsciiencepro.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2832 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | — | lastscience.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2952 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | lastsciiencepro.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
901
Read events
889
Write events
12
Delete events
0
Modification events
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000BD000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1308) lastscience.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | lastsciiencepro.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastsciience.exe | executable | |
MD5:EA0A13D98986C220A8273E407D805A46 | SHA256:CFBD7B968B4C2A063A2A7FA144810B46D10632760743FD049074EF2B578AB69E | |||
| 2076 | lastsciiencepro.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\lastscience.exe | executable | |
MD5:5118CBA991F9D9DA1BF691826EE94B91 | SHA256:7262D0BC1D9B48C5CA8CFF8DA3C0060AFFCFC3792651083D18D07936AF30F238 | |||
| 2092 | SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\lastsciiencepro.exe | executable | |
MD5:81D34D81C4B40BA209760C61BAAAD458 | SHA256:257891B32E5B952CF172A11AFFD291E4964EC9C1B24E51E174A4146503F8164A | |||
| 2092 | SecuriteInfo.com.W32.MSIL_Kryptik.FJL.gen.Eldorado.20998.18469.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\watchprevailing.exe | executable | |
MD5:0A258548C05C1F8BADED9CCFBD4B6896 | SHA256:81917C705392768FFC709D098A64C2928E323762D1A67DF441DBE207B9CDDC85 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
9
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2828 | lastsciience.exe | GET | 200 | 172.86.98.101:80 | http://172.86.98.101/xs12pro/Hcubzvylx.pdf | unknown | binary | 1.00 Mb | unknown |
2952 | lastscience.exe | GET | 200 | 172.86.98.101:80 | http://172.86.98.101/xs12pro/Czbzftdagy.mp4 | unknown | binary | 486 Kb | unknown |
1308 | lastscience.exe | POST | 200 | 188.114.96.3:80 | http://blessdeckite.fun/api | unknown | html | 4.62 Kb | unknown |
1308 | lastscience.exe | GET | 200 | 188.114.96.3:80 | http://blessdeckite.fun/ | unknown | html | 4.61 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2952 | lastscience.exe | 172.86.98.101:80 | — | QUICKPACKET | CA | unknown |
1308 | lastscience.exe | 188.114.96.3:80 | blessdeckite.fun | CLOUDFLARENET | NL | unknown |
2828 | lastsciience.exe | 172.86.98.101:80 | — | QUICKPACKET | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
blessdeckite.fun |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1308 | lastscience.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Check-In |
1308 | lastscience.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Check-In |
2828 | lastsciience.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host PDF Request |