| File name: | 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07 |
| Full analysis: | https://app.any.run/tasks/38b989cc-6480-4af8-8188-9a6c97fab89c |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | December 13, 2024, 20:53:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 17 sections |
| MD5: | 6B46F08A41733D2B127B9870F29CC2ED |
| SHA1: | BAC3F1C7D009A67291C79D2BE035D223A38D7B78 |
| SHA256: | 9509E39A154F11B49864204C878A94C184D2AB9B17CA81F8272ABD7DC2E53D07 |
| SSDEEP: | 1536:tXZyXbZYbku4k6Nqr4iPzeDQFjWSWAaKuVBIX0BFNhtypH8rA:tXwm4LaCNh0pH8rA |
MALICIOUS
COBALTSTRIKE has been detected (YARA)
- 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe (PID: 5208)
SUSPICIOUS
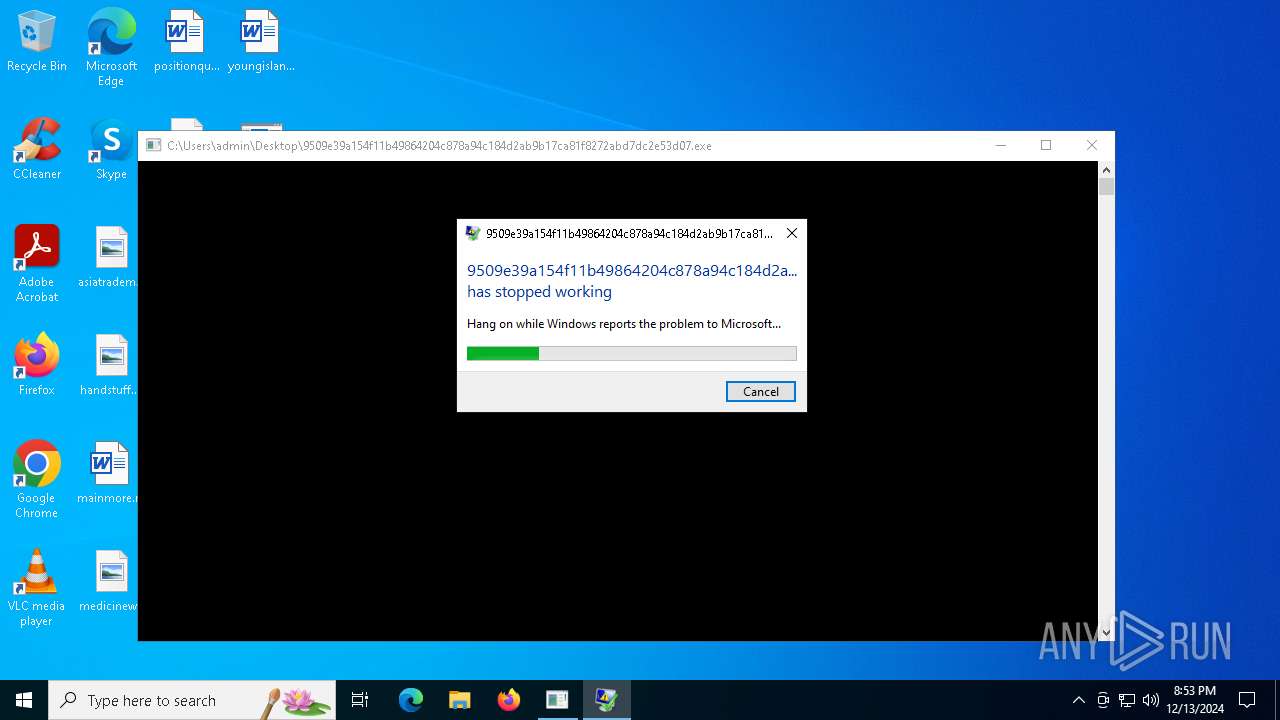
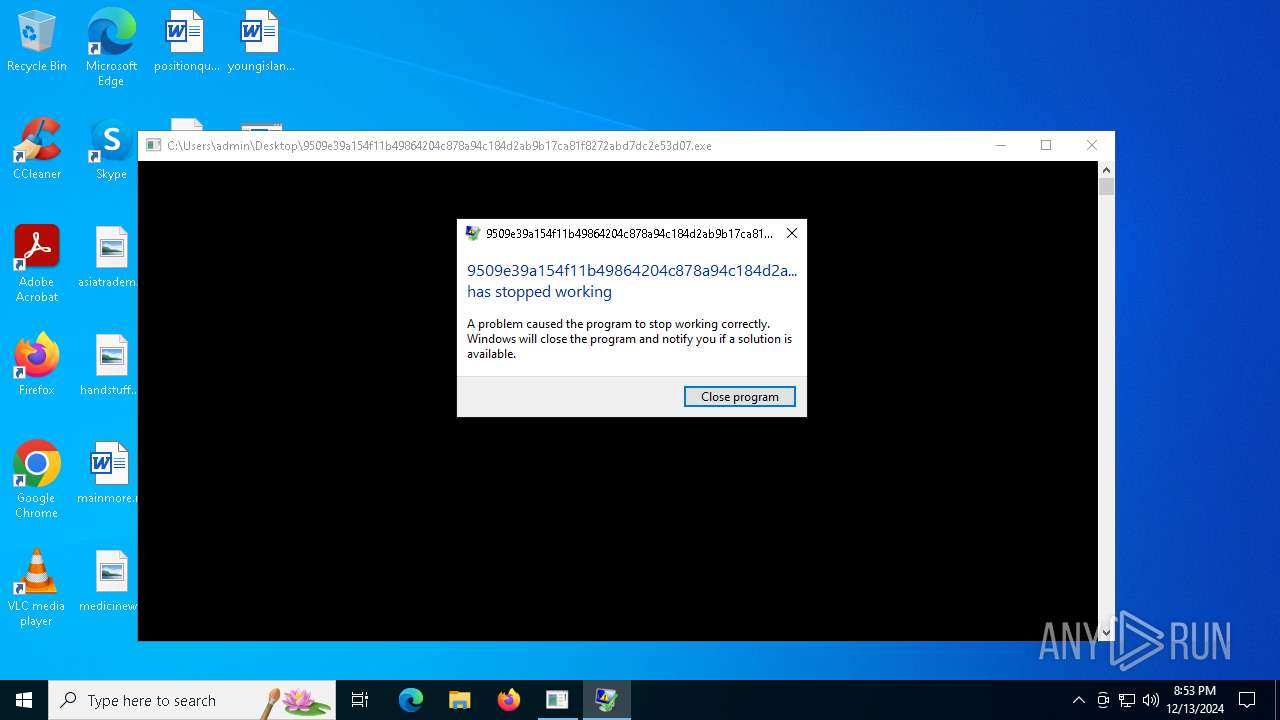
Executes application which crashes
- 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe (PID: 5208)
INFO
Reads the software policy settings
- WerFault.exe (PID: 5548)
Checks supported languages
- 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe (PID: 5208)
Creates files or folders in the user directory
- WerFault.exe (PID: 5548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CobalStrike
(PID) Process(5208) 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe
C2192.168.10.129:8000/LPYh
HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; NP06)
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:11 13:38:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.24 |
| CodeSize: | 7680 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 3072 |
| EntryPoint: | 0x1500 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
121
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5208 | "C:\Users\admin\Desktop\9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe" | C:\Users\admin\Desktop\9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
CobalStrike(PID) Process(5208) 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe C2192.168.10.129:8000/LPYh HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; NP06) | |||||||||||||||
| 5548 | C:\WINDOWS\system32\WerFault.exe -u -p 5208 -s 160 | C:\Windows\System32\WerFault.exe | 9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 741
Read events
6 741
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5548 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_9509e39a154f11b4_79a37240e8c3874fdf6ed4fc3cf7d27e3eeecc_ccc85c88_c291b555-2ac5-4571-a925-21108ecba3fa\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5548 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER718C.tmp.xml | xml | |
MD5:76D2FD9956B416D1ACE2246E4C94751D | SHA256:849ED303C957B76ED8A67135A92E7644DBA174F0C28CAD0BD5B0422608554B8A | |||
| 5548 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\9509e39a154f11b49864204c878a94c184d2ab9b17ca81f8272abd7dc2e53d07.exe.5208.dmp | binary | |
MD5:C6A8095C7E254A640A42D38E83354D6D | SHA256:5B51DCC70555CA583FB3B694BB32812B24BB5C767E5CF11C94E34E0CE250086D | |||
| 5548 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER70DE.tmp.dmp | binary | |
MD5:FF11AF58A83C4E20B8D523478BFE1E49 | SHA256:AC6D6DFB2523FB1B54A2A58E6DB48C2FE09ADFD7DA94DDF1D5F254D73D4A672E | |||
| 5548 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER713C.tmp.WERInternalMetadata.xml | xml | |
MD5:168D3E6E36CBB01074B8F73291971C3E | SHA256:AB8B4EDD685D314C56BE83FC951528146737E1D6F92897FA4B38651928E330DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5448 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5548 | WerFault.exe | 20.189.173.21:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |