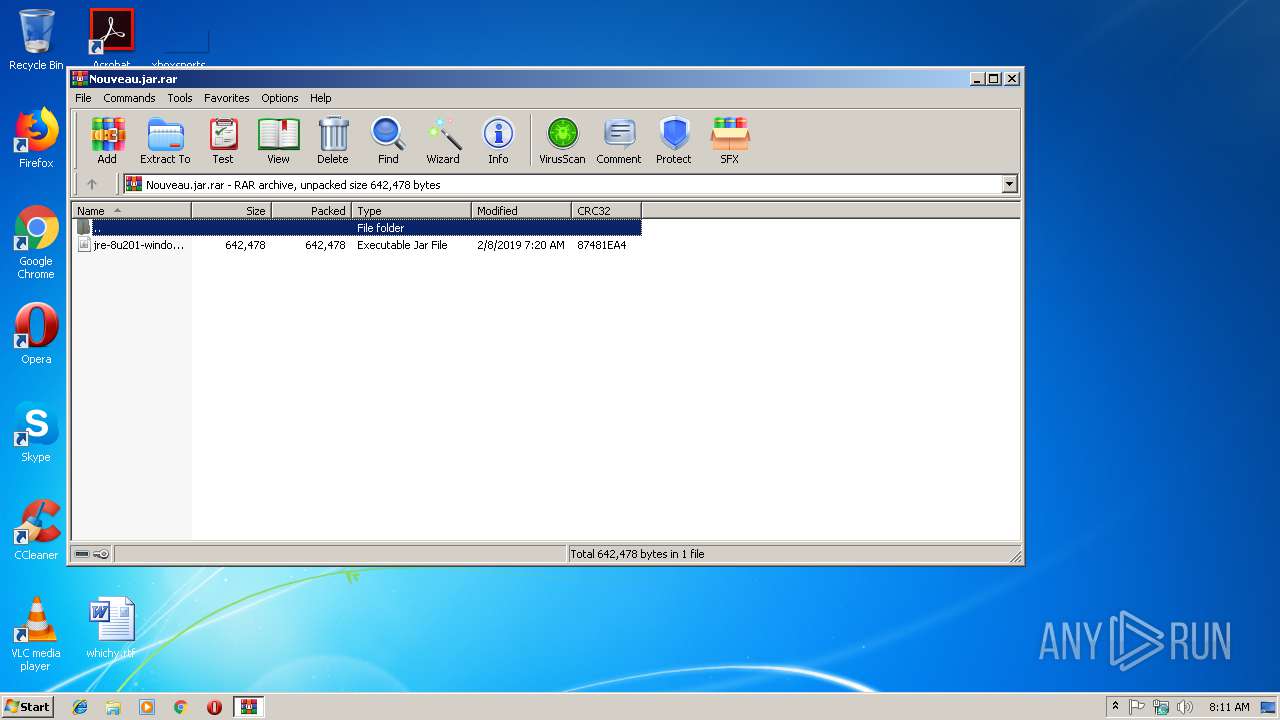
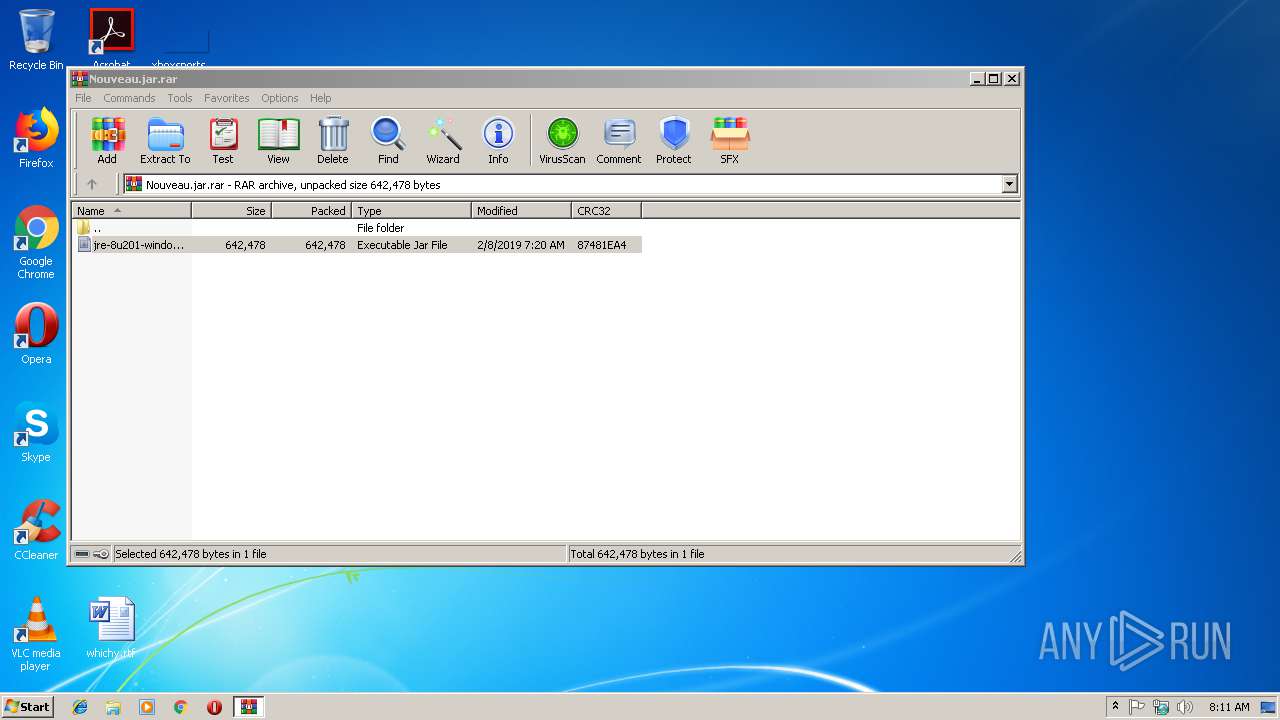
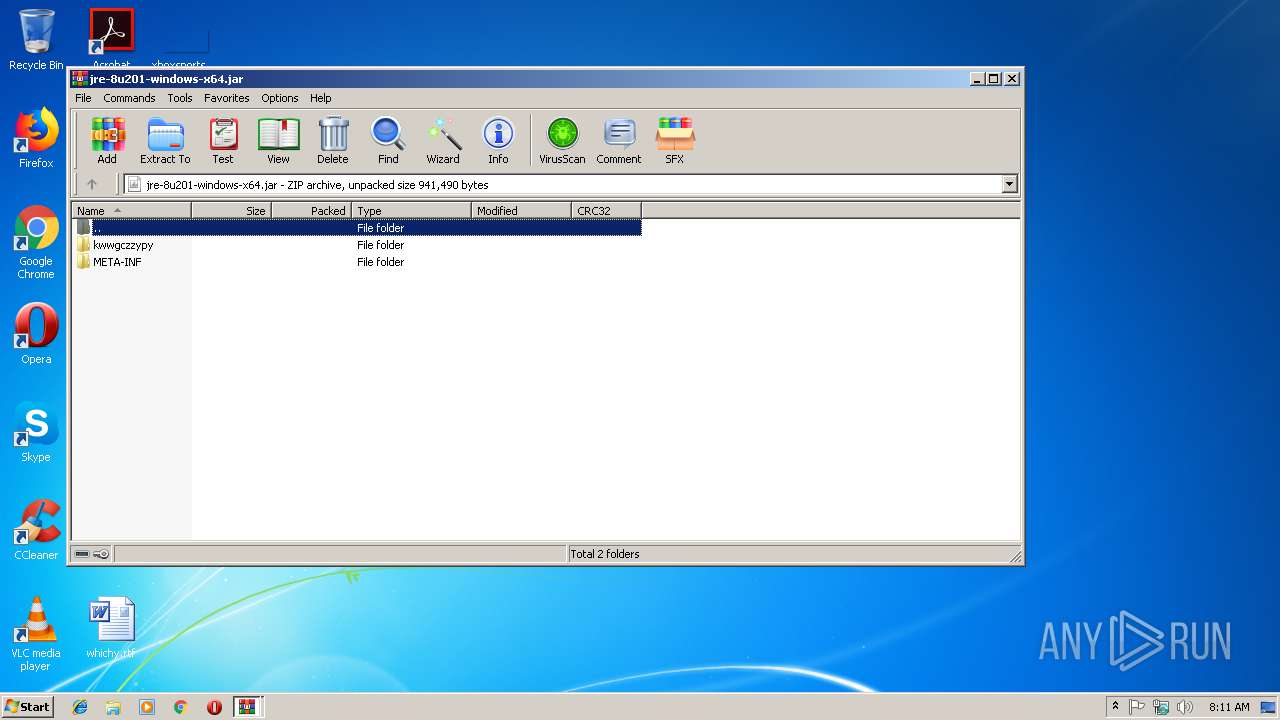
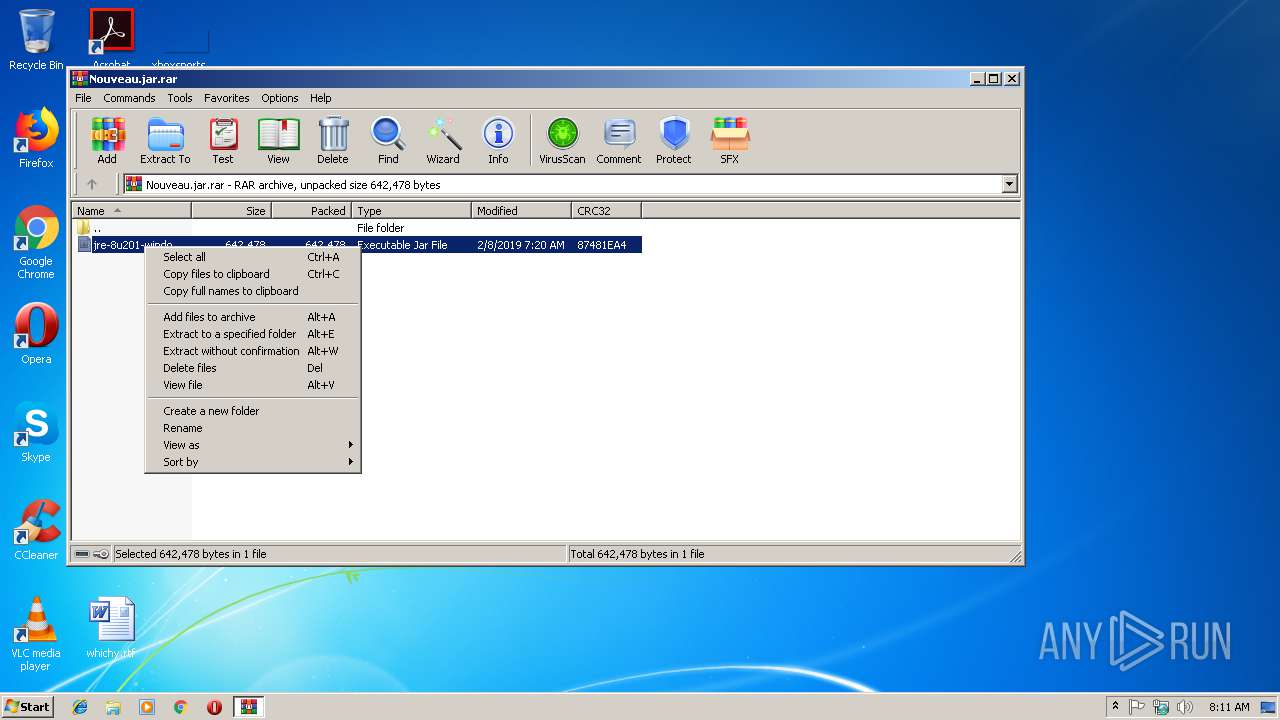
| File name: | Nouveau.jar |
| Full analysis: | https://app.any.run/tasks/fb08a685-8243-4ce1-a823-469ea2f514a2 |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | February 11, 2019, 08:10:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C23912EABB94BC8E237231012F4A5B80 |
| SHA1: | 22C22F9B587C57387A5848F4BCD3F7F1A147142F |
| SHA256: | 94A65D3616639DC1B52FD7942276A475C45D6C280799B958497155A6B46AEF8C |
| SSDEEP: | 12288:sR03cqHwusgi42wUaXqHRKC4Sr7uDGpY+Fqm/+DozJ9BcE/dfZkpgjCBF/PP5xgN:sOcGvd2w8MPS2iAm/+DozJHh/kpgjWpc |
MALICIOUS
Writes to a start menu file
- WScript.exe (PID: 2740)
Changes the autorun value in the registry
- wscript.exe (PID: 3228)
- WScript.exe (PID: 2740)
- reg.exe (PID: 2584)
Connects to CnC server
- WScript.exe (PID: 2740)
DUNIHI was detected
- WScript.exe (PID: 2740)
AdWind was detected
- java.exe (PID: 2768)
Loads dropped or rewritten executable
- svchost.exe (PID: 816)
- java.exe (PID: 2768)
- javaw.exe (PID: 2840)
- javaw.exe (PID: 2204)
- javaw.exe (PID: 3708)
- wscript.exe (PID: 3228)
- explorer.exe (PID: 116)
- cmd.exe (PID: 3528)
- javaw.exe (PID: 3632)
- java.exe (PID: 2712)
Application was dropped or rewritten from another process
- java.exe (PID: 2768)
- javaw.exe (PID: 2204)
- javaw.exe (PID: 2840)
- javaw.exe (PID: 3632)
- java.exe (PID: 2712)
- javaw.exe (PID: 3708)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3468)
- wscript.exe (PID: 3228)
Executes JAVA applets
- explorer.exe (PID: 116)
- cmd.exe (PID: 3528)
- wscript.exe (PID: 3228)
- javaw.exe (PID: 2840)
Executes scripts
- javaw.exe (PID: 3708)
- wscript.exe (PID: 3228)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 3124)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3228)
- javaw.exe (PID: 2840)
- java.exe (PID: 2768)
Creates files in the user directory
- wscript.exe (PID: 3228)
- WScript.exe (PID: 2740)
- javaw.exe (PID: 2840)
- xcopy.exe (PID: 3300)
Connects to unusual port
- WScript.exe (PID: 2740)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3300)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 2840)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 2840)
Starts itself from another location
- javaw.exe (PID: 2840)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
65
Monitored processes
25
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 816 | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -version | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2476 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive1230924861210978264.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2584 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v ZYhRQlVdovW /t REG_EXPAND_SZ /d "\"C:\Users\admin\AppData\Roaming\Oracle\bin\javaw.exe\" -jar \"C:\Users\admin\MnDUThwnuWt\zFIfZwxPmWf.paBrKK\"" /f | C:\Windows\system32\reg.exe | javaw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive4055006280000470612.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2712 | C:\Users\admin\AppData\Roaming\Oracle\bin\java.exe -jar C:\Users\admin\AppData\Local\Temp\_0.16026920281406227857135345292851464.class | C:\Users\admin\AppData\Roaming\Oracle\bin\java.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2740 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\nOEIXYweyr.vbs" | C:\Windows\System32\WScript.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2768 | "C:\Program Files\Java\jre1.8.0_92\bin\java.exe" -jar C:\Users\admin\AppData\Local\Temp\_0.5095062297411482163979030849212189.class | C:\Program Files\Java\jre1.8.0_92\bin\java.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2840 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\ntfsmgr.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | wscript.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
4 139
Read events
4 056
Write events
83
Delete events
0
Modification events
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Nouveau.jar.rar | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3468) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
87
Suspicious files
2
Text files
30
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2768 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive2451347384801487964.vbs | — | |
MD5:— | SHA256:— | |||
| 3468 | WinRAR.exe | C:\Users\admin\Desktop\jre-8u201-windows-x64.jar | compressed | |
MD5:— | SHA256:— | |||
| 3708 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3228 | wscript.exe | C:\Users\admin\AppData\Roaming\nOEIXYweyr.vbs | text | |
MD5:— | SHA256:— | |||
| 3228 | wscript.exe | C:\Users\admin\AppData\Roaming\ntfsmgr.jar | java | |
MD5:— | SHA256:— | |||
| 2204 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2740 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\nOEIXYweyr.vbs | text | |
MD5:— | SHA256:— | |||
| 3528 | cmd.exe | C:\Users\admin\AppData\Local\Temp\output.txt | text | |
MD5:— | SHA256:— | |||
| 2840 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2768 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
2
DNS requests
0
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2740 | WScript.exe | POST | — | 5.206.225.115:7788 | http://5.206.225.115:7788/is-ready | NL | — | — | malicious |
— | — | POST | 404 | 5.206.225.115:7788 | http://5.206.225.115:7788/is-ready | NL | xml | 345 b | malicious |
2740 | WScript.exe | POST | 404 | 5.206.225.115:7788 | http://5.206.225.115:7788/is-ready | NL | xml | 345 b | malicious |
2740 | WScript.exe | POST | 404 | 5.206.225.115:7788 | http://5.206.225.115:7788/is-ready | NL | xml | 345 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2740 | WScript.exe | 5.206.225.115:7788 | — | Dotsi, Unipessoal Lda. | NL | malicious |
— | — | 5.206.225.115:7788 | — | Dotsi, Unipessoal Lda. | NL | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
2740 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin 1 |
2740 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin UA |
2740 | WScript.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dunihi VBS.Downloader.Trojan |
2740 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin 1 |
2740 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin UA |
2740 | WScript.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dunihi VBS.Downloader.Trojan |
2740 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin 1 |
2740 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin UA |
2740 | WScript.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dunihi VBS.Downloader.Trojan |
— | — | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin 1 |