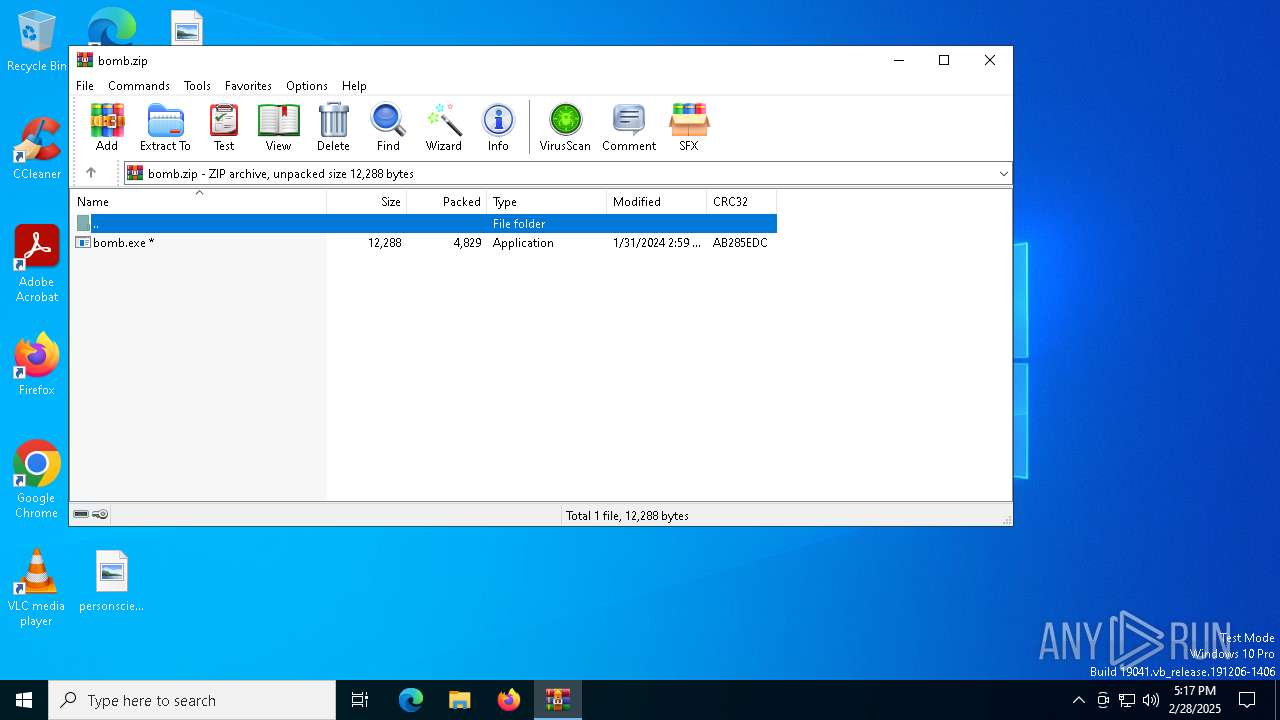
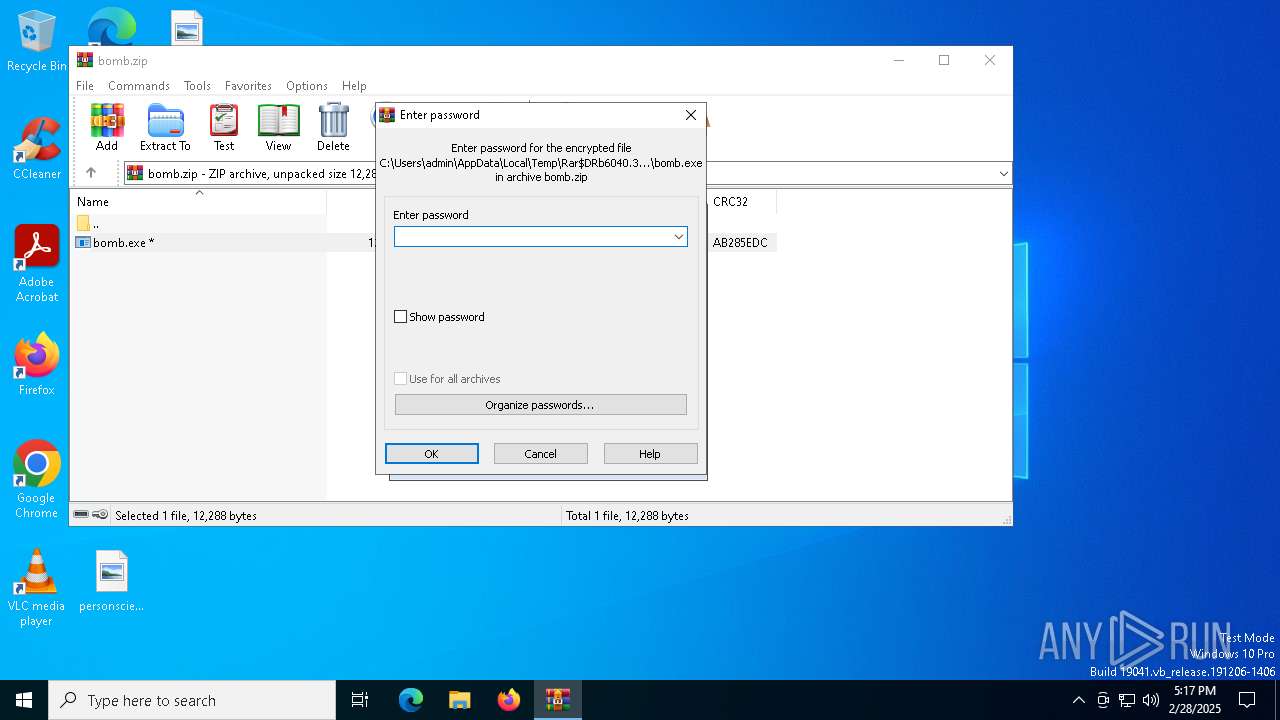
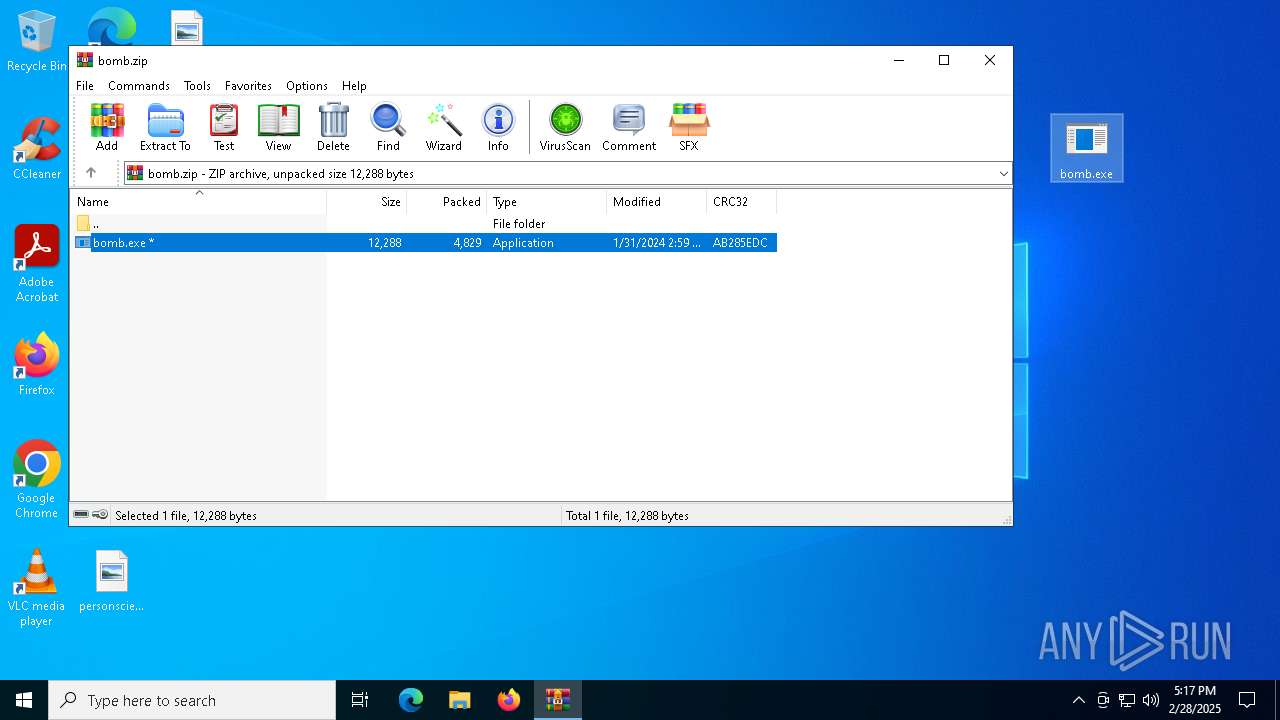
| File name: | bomb.zip |
| Full analysis: | https://app.any.run/tasks/1ee23c62-075c-4171-819d-3bf558cca225 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | February 28, 2025, 17:17:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4D9BD8DAFB8299D0FC3FC98F8B8C27D4 |
| SHA1: | F3B375208D793E65FAABFD237C5391B49F381908 |
| SHA256: | 94936FB4C7BED2E7233FADE7980425B0300451D76A7AC9329C604886E2A9A013 |
| SSDEEP: | 192:aEuBYvQPc0QskFQBTPwR8Ac4Q7SbFL8H/Pj3UhrMj:aEznFcTPwRVASbVYXj/j |
MALICIOUS
AMADEY mutex has been found
- http176.113.115.7minerandom.exe.exe (PID: 7564)
- rapes.exe (PID: 2644)
LUMMA mutex has been found
- http176.113.115.7filesqqdouprandom.exe.exe (PID: 5408)
- httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe (PID: 776)
StealC has been detected
- http176.113.115.7steamrandom.exe.exe (PID: 7908)
VIDAR mutex has been found
- http176.113.115.7files7098980627mAtJWNv.exe.exe (PID: 7976)
RAT has been found (auto)
- bomb.exe (PID: 7864)
TOOL has been found (auto)
- bomb.exe (PID: 7864)
Changes powershell execution policy
- wscript.exe (PID: 8176)
- powershell.exe (PID: 7580)
Run PowerShell with an invisible window
- powershell.exe (PID: 7580)
- powershell.exe (PID: 7456)
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe (PID: 776)
- svchost.exe (PID: 2196)
AMADEY has been detected (SURICATA)
- rapes.exe (PID: 2644)
Starts Visual C# compiler
- http185.7.214.108fg.exe.exe (PID: 6372)
- http92.255.57.221yr.exe.exe (PID: 7172)
- http185.7.214.108js.exe.exe (PID: 7420)
Stego campaign has been detected
- powershell.exe (PID: 7456)
SUSPICIOUS
Potential Corporate Privacy Violation
- bomb.exe (PID: 7864)
Connects to the server without a host name
- bomb.exe (PID: 7864)
- rapes.exe (PID: 2644)
Executes application which crashes
- http172.245.123.17550casse.exe.exe (PID: 8184)
- http176.113.115.7files7098980627mAtJWNv.exe.exe (PID: 1512)
- httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe (PID: 7968)
Process drops legitimate windows executable
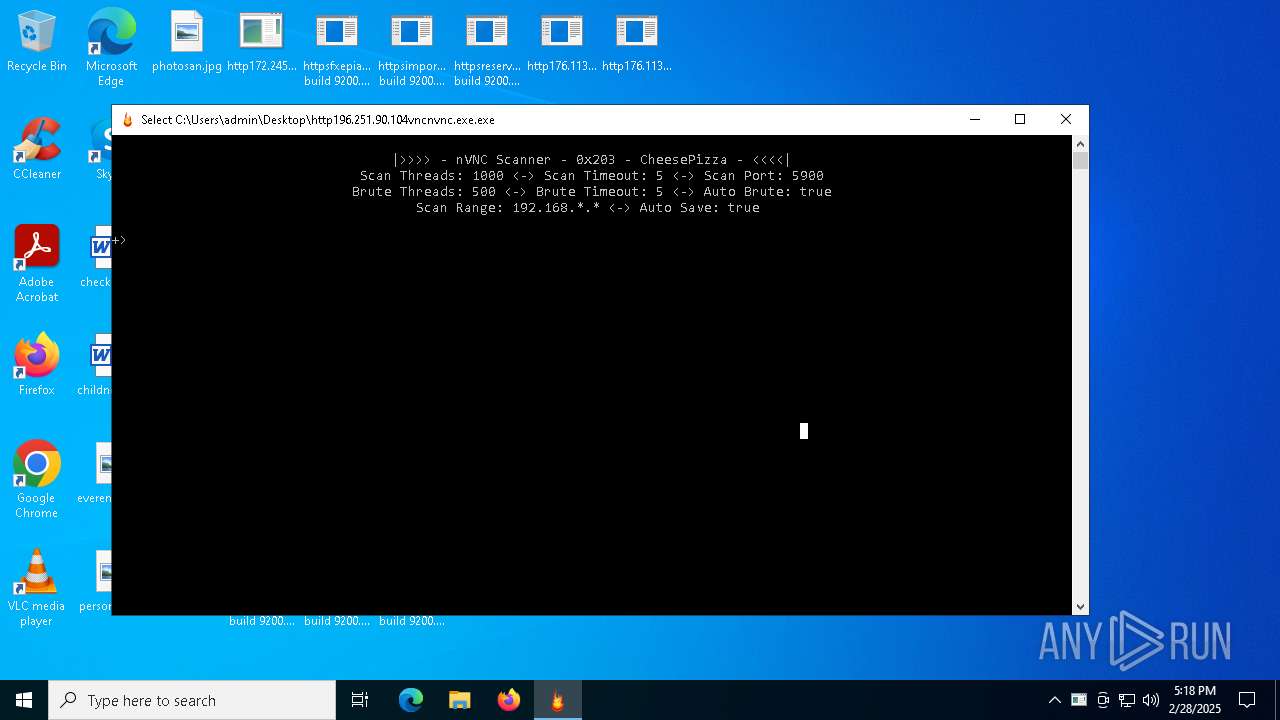
- http196.251.90.104vncnvnc.exe.exe (PID: 4988)
- bomb.exe (PID: 7864)
Process requests binary or script from the Internet
- bomb.exe (PID: 7864)
Executable content was dropped or overwritten
- bomb.exe (PID: 7864)
- http196.251.90.104vncnvnc.exe.exe (PID: 4988)
- http176.113.115.7minerandom.exe.exe (PID: 7564)
- http198.12.81.109230csoss.exe.exe (PID: 5800)
- csc.exe (PID: 8004)
- csc.exe (PID: 4736)
- csc.exe (PID: 7508)
Application launched itself
- http196.251.90.104vncnvnc.exe.exe (PID: 4988)
- http176.113.115.7files7098980627mAtJWNv.exe.exe (PID: 1512)
- httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe (PID: 7968)
- powershell.exe (PID: 7580)
Starts a Microsoft application from unusual location
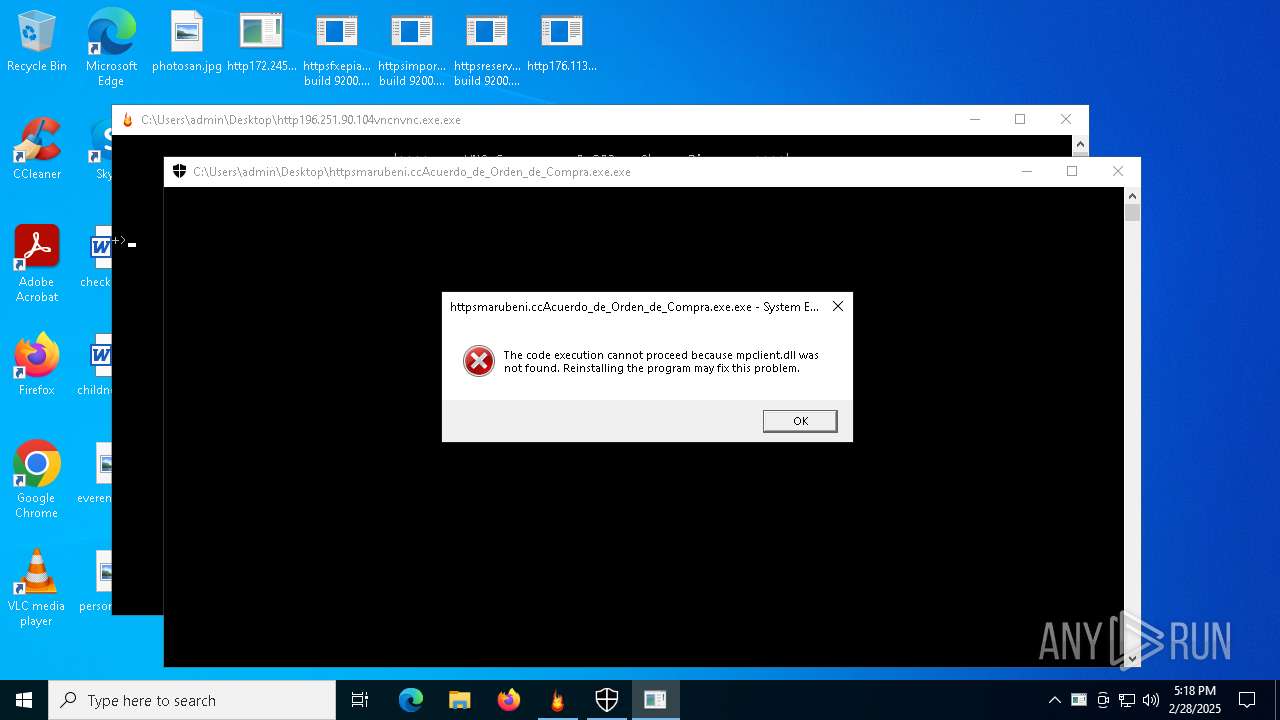
- http45.11.59.49Acuerdo_de_Orden_de_Compra.exe.exe (PID: 7036)
- httpsmarubeni.ccAcuerdo_de_Orden_de_Compra.exe.exe (PID: 4436)
- http176.113.115.7files7481626938MCxU5Fj.exe.exe (PID: 8036)
The process drops C-runtime libraries
- http196.251.90.104vncnvnc.exe.exe (PID: 4988)
Process drops python dynamic module
- http196.251.90.104vncnvnc.exe.exe (PID: 4988)
Starts CMD.EXE for commands execution
- http196.251.90.104vncnvnc.exe.exe (PID: 6184)
- http176.113.115.7files7481626938MCxU5Fj.exe.exe (PID: 8036)
Connects to unusual port
- bomb.exe (PID: 7864)
- httpsraw.githubusercontent.comOscarito20222diciembrerefsheadsmainsena.exe.exe (PID: 7596)
Windows Defender mutex has been found
- http176.113.115.7steamrandom.exe.exe (PID: 7908)
Starts itself from another location
- http176.113.115.7minerandom.exe.exe (PID: 7564)
The process executes VB scripts
- cmd.exe (PID: 7800)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 8176)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 8176)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe (PID: 776)
- rapes.exe (PID: 2644)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 8176)
- powershell.exe (PID: 7580)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8176)
Uses .NET C# to load dll
- http185.7.214.108fg.exe.exe (PID: 6372)
- http92.255.57.221yr.exe.exe (PID: 7172)
- http185.7.214.108js.exe.exe (PID: 7420)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7580)
Found IP address in command line
- powershell.exe (PID: 7456)
Probably download files using WebClient
- powershell.exe (PID: 7580)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6040)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 8112)
Manual execution by a user
- bomb.exe (PID: 7864)
The sample compiled with english language support
- http196.251.90.104vncnvnc.exe.exe (PID: 4988)
- bomb.exe (PID: 7864)
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with german language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with arabic language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with bulgarian language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with czech language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with Indonesian language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with french language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with Italian language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with japanese language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with russian language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with korean language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with polish language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with portuguese language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with turkish language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with slovak language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with swedish language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
The sample compiled with chinese language support
- http198.12.81.109230csoss.exe.exe (PID: 5800)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 7580)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 7580)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:30 21:59:18 |
| ZipCRC: | 0xab285edc |
| ZipCompressedSize: | 4829 |
| ZipUncompressedSize: | 12288 |
| ZipFileName: | bomb.exe |
Total processes
197
Monitored processes
60
Malicious processes
13
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Users\admin\Desktop\httpsgithub.comOscarito20222diciembrerawrefsheadsmainsena.exe.exe" | C:\Users\admin\Desktop\httpsgithub.comOscarito20222diciembrerawrefsheadsmainsena.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 732 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | http92.255.57.221yr.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 776 | "C:\Users\admin\Desktop\httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe" | C:\Users\admin\Desktop\httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe | httpsgithub.com1tthens1PMIrawrefsheadsmainDEVM2.exe.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Chapter Version: 1.0.0.0 Modules
| |||||||||||||||
| 960 | C:\WINDOWS\system32\cmd.exe /c CLS | C:\Windows\SysWOW64\cmd.exe | — | http196.251.90.104vncnvnc.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8184 -s 788 | C:\Windows\SysWOW64\WerFault.exe | — | http172.245.123.17550casse.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\http176.113.115.7files7098980627mAtJWNv.exe.exe" | C:\Users\admin\Desktop\http176.113.115.7files7098980627mAtJWNv.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
| 1628 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | http185.7.214.108js.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\Desktop\http62.60.226.112file8998_3800.exe.exe" | C:\Users\admin\Desktop\http62.60.226.112file8998_3800.exe.exe | — | bomb.exe | |||||||||||
User: admin Company: SAP SE Integrity Level: MEDIUM Description: SAP Enable Now Authoring Tool Version: 10.8.9 (build 5711) Modules
| |||||||||||||||
| 1764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | http196.251.90.104vncnvnc.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 707
Read events
25 643
Write events
62
Delete events
2
Modification events
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\bomb.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7820) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7820) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
99
Suspicious files
57
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8112 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\31dae929-fa3e-477e-bd59-2fc81bc86f81.down_data | — | |
MD5:— | SHA256:— | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6040.38132\bomb.exe | executable | |
MD5:A14E63D27E1AC1DF185FA062103AA9AA | SHA256:DDA39F19837168845DE33959DE34BCFB7EE7F3A29AE55C9FA7F4CB12CB27F453 | |||
| 8112 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\31dae929-fa3e-477e-bd59-2fc81bc86f81.d64442af-7708-456a-96d4-53080d355216.down_meta | binary | |
MD5:B1C027468354002159330F8E4704C474 | SHA256:93ECB807518A9CCB51FBCC4D9216D40015A17D6DD9B2F442743F99A56109D11E | |||
| 8112 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\88dc55a8-8475-4849-a4e0-dbe599cb4af1.d64442af-7708-456a-96d4-53080d355216.down_meta | binary | |
MD5:B1C027468354002159330F8E4704C474 | SHA256:93ECB807518A9CCB51FBCC4D9216D40015A17D6DD9B2F442743F99A56109D11E | |||
| 8112 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\88dc55a8-8475-4849-a4e0-dbe599cb4af1.up_meta_secure | binary | |
MD5:DE010C9679592C1F56FD87AAE7D910DF | SHA256:9A3BA5D5B83260E42B737A80913C84A5651338651401D07F2C3F93DDFBAAA43E | |||
| 8112 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:B307732A566C836EF80CC316F34C35DB | SHA256:FF6F5FFE66D330CDFB37245FCDA06AF699AC7D2ED442FBBD4617B0E54204E792 | |||
| 7864 | bomb.exe | C:\Users\admin\Desktop\httpsprocedeed-verific.comin.phpaction=2id=admin&mn=DESKTOP-JGLLJLD&os=6.2 build 9200.exe | text | |
MD5:3C9AA823B52BFCCF00026C9F75ACC6B4 | SHA256:F1EA7594BF1D50B9104DE12AFA3397B47F3FE49AEE9D0EDF5900D29198D9C9D0 | |||
| 7864 | bomb.exe | C:\Users\admin\Desktop\httpsimportant-confiirm.comin.phpaction=2id=admin&mn=DESKTOP-JGLLJLD&os=6.2 build 9200.exe | text | |
MD5:D214EA754DC144794A02BE32B947AEB0 | SHA256:8E708257368695510EA0629763B9879F68D94CF31EA5533D9B7DC8F05BE2FA45 | |||
| 7864 | bomb.exe | C:\Users\admin\Desktop\httpsfxepiay.comin.phpaction=2id=admin&mn=DESKTOP-JGLLJLD&os=6.2 build 9200.exe | text | |
MD5:EA6EEBA52E199890553F24734857116F | SHA256:ADA61A271D8C0D4B9B90968FF99550A36117596795565A849A183794D45A1F4E | |||
| 8112 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:B8A1492BCE0E97A2F332BA2D47303B7F | SHA256:635A05DE6D6846ADDB8850CFC95E079079B6FB86DE18DDBEFEC03E6789A5C705 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
74
DNS requests
39
Threats
82
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8112 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7880 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7864 | bomb.exe | GET | 200 | 196.251.90.104:80 | http://196.251.90.104/vnc/nvnc.exe | unknown | — | — | unknown |
7880 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7864 | bomb.exe | GET | 200 | 45.11.59.49:80 | http://45.11.59.49/Acuerdo_de_Orden_de_Compra.exe | unknown | — | — | unknown |
7864 | bomb.exe | GET | 200 | 172.245.123.17:80 | http://172.245.123.17/550/casse.exe | unknown | — | — | unknown |
7864 | bomb.exe | GET | — | 62.60.226.112:80 | http://62.60.226.112/file/8998_3800.exe | unknown | — | — | unknown |
7864 | bomb.exe | GET | 200 | 176.113.115.7:80 | http://176.113.115.7/files/qqdoup/random.exe | unknown | — | — | malicious |
7864 | bomb.exe | GET | — | 176.113.115.7:80 | http://176.113.115.7/files/7098980627/mAtJWNv.exe | unknown | — | — | malicious |
7864 | bomb.exe | GET | 200 | 176.113.115.7:80 | http://176.113.115.7/mine/random.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2040 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3008 | backgroundTaskHost.exe | 2.19.96.41:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2040 | backgroundTaskHost.exe | 20.103.156.88:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7864 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7864 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7864 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7864 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7864 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7864 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7864 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7864 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7864 | bomb.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 37 |
7864 | bomb.exe | Misc activity | ET INFO Packed Executable Download |