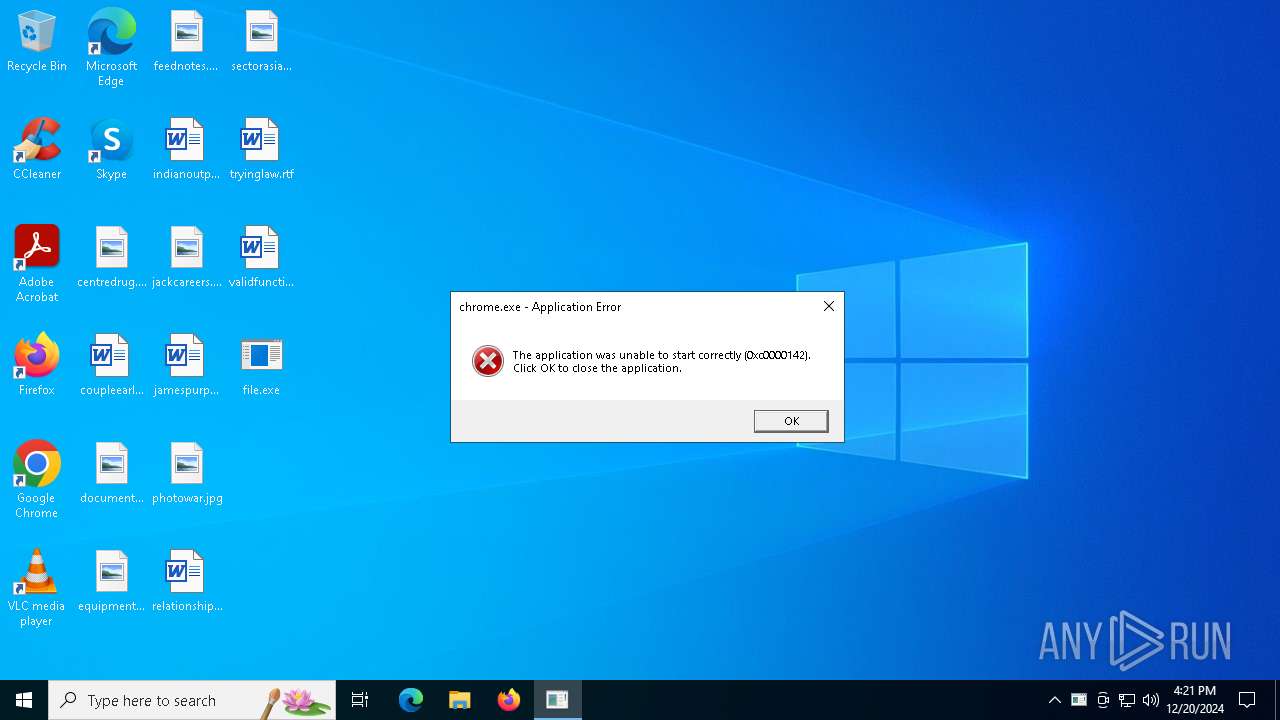
| File name: | file.exe |
| Full analysis: | https://app.any.run/tasks/6d21ccb7-e823-4ae3-b105-969163c1728a |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 20, 2024, 16:20:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 903052DC4EC888F7F5BCEB743304B9A2 |
| SHA1: | 9A915074586344F727528A5FC63B86B6083E291B |
| SHA256: | 94892AE5C3BEE71AD27491E1801B78AF3789A15CACC1817DE0A970854B841587 |
| SSDEEP: | 98304:TFJlXlebgxnkZ8V6ZoMIvet83oZlJS5gOD6t2hm+YGi+N3J7zrFfvPP287uE10Yc:XN3J7zrFfvPP287uE10YbLD4uu4 |
MALICIOUS
AMADEY mutex has been found
- file.exe (PID: 968)
- skotes.exe (PID: 5788)
- NMmicronick.exe (PID: 5992)
- skotes.exe (PID: 2624)
- Gxtuum.exe (PID: 6260)
- Gxtuum.exe (PID: 6436)
- Gxtuum.exe (PID: 3208)
AMADEY has been detected (SURICATA)
- skotes.exe (PID: 5788)
Connects to the CnC server
- skotes.exe (PID: 5788)
- svchost.exe (PID: 2192)
- f224d09151.exe (PID: 6624)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- 01bfc38a74.exe (PID: 5916)
- caecc034cc.exe (PID: 4188)
- 587dfd33b3.exe (PID: 1448)
- a269558120.exe (PID: 6192)
- dffcc75edc044fa6a6b7f27e5907889e.exe (PID: 7908)
- d78c286d75.exe (PID: 7736)
Steals credentials from Web Browsers
- 01bfc38a74.exe (PID: 5916)
- 5420c6736f.exe (PID: 5432)
- 587dfd33b3.exe (PID: 1448)
- dddb8a292b.exe (PID: 8148)
- d78c286d75.exe (PID: 7736)
AMADEY has been detected (YARA)
- skotes.exe (PID: 5788)
Actions looks like stealing of personal data
- 01bfc38a74.exe (PID: 5916)
- caecc034cc.exe (PID: 4188)
- 5420c6736f.exe (PID: 5432)
- 587dfd33b3.exe (PID: 1448)
- 0fc2c42e92.exe (PID: 3688)
- a269558120.exe (PID: 6192)
- dddb8a292b.exe (PID: 8148)
- dffcc75edc044fa6a6b7f27e5907889e.exe (PID: 7908)
- d78c286d75.exe (PID: 7736)
LUMMA mutex has been found
- 01bfc38a74.exe (PID: 5916)
- caecc034cc.exe (PID: 4188)
- 5420c6736f.exe (PID: 5432)
- 587dfd33b3.exe (PID: 1448)
- 0fc2c42e92.exe (PID: 3688)
- a269558120.exe (PID: 6192)
- dddb8a292b.exe (PID: 8148)
- dffcc75edc044fa6a6b7f27e5907889e.exe (PID: 7908)
Executing a file with an untrusted certificate
- caecc034cc.exe (PID: 4188)
- caecc034cc.exe (PID: 3796)
- NMmicronick.exe (PID: 4624)
- NMmicronick.exe (PID: 5992)
- Gxtuum.exe (PID: 4996)
- Gxtuum.exe (PID: 6260)
- Gxtuum.exe (PID: 6288)
- Gxtuum.exe (PID: 6436)
- 27aead1158.exe (PID: 7932)
- Gxtuum.exe (PID: 6440)
- Gxtuum.exe (PID: 3208)
LUMMA has been detected (YARA)
- 01bfc38a74.exe (PID: 5916)
- 5420c6736f.exe (PID: 5432)
- caecc034cc.exe (PID: 4188)
PURECRYPTER has been detected (YARA)
- NMmicronick.exe (PID: 4624)
CRYPTBOT mutex has been found
- aed45e6ed3.exe (PID: 1348)
- 99de4b6e54.exe (PID: 6328)
Adds path to the Windows Defender exclusion list
- 18765d3f82.exe (PID: 5392)
- 154fc53503.exe (PID: 7756)
StealC has been detected
- f224d09151.exe (PID: 6624)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
STEALC has been detected (SURICATA)
- f224d09151.exe (PID: 6624)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
GCLEANER has been detected (SURICATA)
- 10eb54c21a.exe (PID: 6912)
Possible tool for stealing has been detected
- c64e5c6f26.exe (PID: 6408)
- firefox.exe (PID: 3608)
COINMINER has been found (auto)
- skotes.exe (PID: 5788)
Uses Task Scheduler to run other applications
- in.exe (PID: 6220)
- in.exe (PID: 4652)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- skotes.exe (PID: 5788)
- 01bfc38a74.exe (PID: 5916)
- svchost.exe (PID: 2192)
- caecc034cc.exe (PID: 4188)
- 587dfd33b3.exe (PID: 1448)
- a269558120.exe (PID: 6192)
- f224d09151.exe (PID: 6624)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
- dffcc75edc044fa6a6b7f27e5907889e.exe (PID: 7908)
- d78c286d75.exe (PID: 7736)
Reads the BIOS version
- file.exe (PID: 968)
- 01bfc38a74.exe (PID: 5916)
- skotes.exe (PID: 5788)
- 99de4b6e54.exe (PID: 6328)
- 10eb54c21a.exe (PID: 6912)
- dddb8a292b.exe (PID: 8148)
- skotes.exe (PID: 3828)
Reads security settings of Internet Explorer
- file.exe (PID: 968)
- skotes.exe (PID: 5788)
- NMmicronick.exe (PID: 5992)
- 18765d3f82.exe (PID: 2624)
- Gxtuum.exe (PID: 6260)
- 18765d3f82.exe (PID: 5392)
- 27aead1158.exe (PID: 7932)
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
Executable content was dropped or overwritten
- file.exe (PID: 968)
- skotes.exe (PID: 5788)
- NMmicronick.exe (PID: 4624)
- NMmicronick.exe (PID: 5992)
- 18765d3f82.exe (PID: 5392)
- a269558120.exe (PID: 6192)
- 10eb54c21a.exe (PID: 6912)
- iwgpdsdO2.exe (PID: 7504)
- iwgpdsdO2.tmp (PID: 7524)
- flashdecompiler2.exe (PID: 7544)
- riDpuiyI3qNN.exe (PID: 7960)
- riDpuiyI3qNN.tmp (PID: 7976)
- 27aead1158.exe (PID: 7932)
- 7z.exe (PID: 7496)
- cmd.exe (PID: 8064)
- in.exe (PID: 6220)
- 154fc53503.exe (PID: 7756)
Process requests binary or script from the Internet
- skotes.exe (PID: 5788)
- a269558120.exe (PID: 6192)
Potential Corporate Privacy Violation
- skotes.exe (PID: 5788)
- a269558120.exe (PID: 6192)
- 10eb54c21a.exe (PID: 6912)
Application launched itself
- caecc034cc.exe (PID: 3796)
- 587dfd33b3.exe (PID: 3060)
- 18765d3f82.exe (PID: 2624)
- d3bbebbc64.exe (PID: 3796)
- 154fc53503.exe (PID: 3828)
- d78c286d75.exe (PID: 1400)
Starts itself from another location
- file.exe (PID: 968)
- NMmicronick.exe (PID: 5992)
Searches for installed software
- aed45e6ed3.exe (PID: 1348)
Starts POWERSHELL.EXE for commands execution
- 18765d3f82.exe (PID: 5392)
- flashdecompiler2.exe (PID: 7544)
- in.exe (PID: 6220)
- 154fc53503.exe (PID: 7756)
- in.exe (PID: 4652)
- Intel_PTT_EK_Recertification.exe (PID: 5988)
Connects to the server without a host name
- skotes.exe (PID: 5788)
- Gxtuum.exe (PID: 6260)
- f224d09151.exe (PID: 6624)
- 10eb54c21a.exe (PID: 6912)
- a269558120.exe (PID: 6192)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
Script adds exclusion path to Windows Defender
- 18765d3f82.exe (PID: 5392)
- 154fc53503.exe (PID: 7756)
There is functionality for VM detection VirtualBox (YARA)
- aed45e6ed3.exe (PID: 1348)
The process executes via Task Scheduler
- skotes.exe (PID: 2624)
- Gxtuum.exe (PID: 6288)
- skotes.exe (PID: 3828)
- Gxtuum.exe (PID: 6440)
- Intel_PTT_EK_Recertification.exe (PID: 5988)
Process drops legitimate windows executable
- 18765d3f82.exe (PID: 5392)
- iwgpdsdO2.tmp (PID: 7524)
- riDpuiyI3qNN.tmp (PID: 7976)
Checks Windows Trust Settings
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
Connects to unusual port
- rundll32.exe (PID: 7040)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
Windows Defender mutex has been found
- f224d09151.exe (PID: 6624)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
Uses TASKKILL.EXE to kill Browsers
- c64e5c6f26.exe (PID: 6408)
Uses TASKKILL.EXE to kill process
- c64e5c6f26.exe (PID: 6408)
Reads the Windows owner or organization settings
- iwgpdsdO2.tmp (PID: 7524)
The process drops C-runtime libraries
- iwgpdsdO2.tmp (PID: 7524)
Drops 7-zip archiver for unpacking
- 27aead1158.exe (PID: 7932)
Starts CMD.EXE for commands execution
- 27aead1158.exe (PID: 7932)
Executing commands from a ".bat" file
- 27aead1158.exe (PID: 7932)
The executable file from the user directory is run by the CMD process
- 7z.exe (PID: 8160)
- 7z.exe (PID: 4652)
- 7z.exe (PID: 4044)
- 7z.exe (PID: 7368)
- 7z.exe (PID: 7392)
- 7z.exe (PID: 7416)
- 7z.exe (PID: 7440)
- 7z.exe (PID: 7496)
- in.exe (PID: 6220)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 8064)
- in.exe (PID: 6220)
- in.exe (PID: 4652)
Found IP address in command line
- powershell.exe (PID: 6412)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 6980)
Executes application which crashes
- 10eb54c21a.exe (PID: 6912)
INFO
Sends debugging messages
- file.exe (PID: 968)
- 01bfc38a74.exe (PID: 5916)
- skotes.exe (PID: 5788)
- aed45e6ed3.exe (PID: 1348)
- 5420c6736f.exe (PID: 5432)
- skotes.exe (PID: 2624)
- 99de4b6e54.exe (PID: 6328)
- 10eb54c21a.exe (PID: 6912)
- f224d09151.exe (PID: 6624)
- a269558120.exe (PID: 6192)
- 274IVIYMZ6HFH4XT7P.exe (PID: 6816)
- f8b52c0f35.exe (PID: 7344)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
- dddb8a292b.exe (PID: 8148)
- skotes.exe (PID: 3828)
Checks proxy server information
- skotes.exe (PID: 5788)
- Gxtuum.exe (PID: 6260)
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
- ae16662188354edfa7f4cc7015382fe6.exe (PID: 7084)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
Checks supported languages
- file.exe (PID: 968)
- skotes.exe (PID: 5788)
- 01bfc38a74.exe (PID: 5916)
- caecc034cc.exe (PID: 3796)
- 587dfd33b3.exe (PID: 3060)
- NMmicronick.exe (PID: 5992)
- 587dfd33b3.exe (PID: 1448)
- Gxtuum.exe (PID: 4996)
- 18765d3f82.exe (PID: 2624)
- 0fc2c42e92.exe (PID: 3688)
- skotes.exe (PID: 2624)
- Gxtuum.exe (PID: 6288)
- d3bbebbc64.exe (PID: 6384)
- 99de4b6e54.exe (PID: 6328)
- 10eb54c21a.exe (PID: 6912)
- 18765d3f82.exe (PID: 5392)
- Gxtuum.exe (PID: 6260)
- c64e5c6f26.exe (PID: 6408)
- 274IVIYMZ6HFH4XT7P.exe (PID: 6816)
- iwgpdsdO2.tmp (PID: 7524)
- iwgpdsdO2.exe (PID: 7504)
- flashdecompiler2.exe (PID: 7544)
- 1GJ6U9RG9HW4NDUSWY4YC8U18XB2X.exe (PID: 7592)
- mode.com (PID: 8124)
- dddb8a292b.exe (PID: 8148)
- 7z.exe (PID: 7496)
- in.exe (PID: 6220)
- 154fc53503.exe (PID: 3828)
- d78c286d75.exe (PID: 1400)
- skotes.exe (PID: 3828)
- Intel_PTT_EK_Recertification.exe (PID: 5988)
- d78c286d75.exe (PID: 7736)
Reads the computer name
- file.exe (PID: 968)
- 01bfc38a74.exe (PID: 5916)
- skotes.exe (PID: 5788)
- NMmicronick.exe (PID: 4624)
- aed45e6ed3.exe (PID: 1348)
- 0fc2c42e92.exe (PID: 3688)
- a269558120.exe (PID: 6192)
- flashdecompiler2.exe (PID: 7544)
- riDpuiyI3qNN.tmp (PID: 7976)
- 7z.exe (PID: 7496)
- 154fc53503.exe (PID: 3828)
Process checks computer location settings
- file.exe (PID: 968)
- skotes.exe (PID: 5788)
- 18765d3f82.exe (PID: 5392)
- Gxtuum.exe (PID: 6260)
The process uses the downloaded file
- file.exe (PID: 968)
- skotes.exe (PID: 5788)
- NMmicronick.exe (PID: 5992)
- Gxtuum.exe (PID: 6260)
- powershell.exe (PID: 7336)
- 154fc53503.exe (PID: 7756)
Creates files or folders in the user directory
- skotes.exe (PID: 5788)
- 10eb54c21a.exe (PID: 6912)
- iwgpdsdO2.tmp (PID: 7524)
- WerFault.exe (PID: 8176)
Reads the software policy settings
- 01bfc38a74.exe (PID: 5916)
- caecc034cc.exe (PID: 4188)
- 587dfd33b3.exe (PID: 1448)
- 18765d3f82.exe (PID: 5392)
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
- ae16662188354edfa7f4cc7015382fe6.exe (PID: 7084)
- dddb8a292b.exe (PID: 8148)
- 154fc53503.exe (PID: 7756)
- dffcc75edc044fa6a6b7f27e5907889e.exe (PID: 7908)
Reads the machine GUID from the registry
- 01bfc38a74.exe (PID: 5916)
- caecc034cc.exe (PID: 4188)
- NMmicronick.exe (PID: 4624)
- aed45e6ed3.exe (PID: 1348)
- Gxtuum.exe (PID: 4996)
- Gxtuum.exe (PID: 6288)
- d3bbebbc64.exe (PID: 6384)
- 99de4b6e54.exe (PID: 6328)
- 18765d3f82.exe (PID: 5392)
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
- ae16662188354edfa7f4cc7015382fe6.exe (PID: 7084)
- dddb8a292b.exe (PID: 8148)
- dffcc75edc044fa6a6b7f27e5907889e.exe (PID: 7908)
- Gxtuum.exe (PID: 6440)
Create files in a temporary directory
- skotes.exe (PID: 5788)
- NMmicronick.exe (PID: 5992)
- Gxtuum.exe (PID: 6260)
- iwgpdsdO2.exe (PID: 7504)
- a269558120.exe (PID: 6192)
- 7z.exe (PID: 4652)
- 7z.exe (PID: 7496)
- 10eb54c21a.exe (PID: 6912)
Themida protector has been detected
- skotes.exe (PID: 5788)
- 01bfc38a74.exe (PID: 5916)
- 5420c6736f.exe (PID: 5432)
- aed45e6ed3.exe (PID: 1348)
.NET Reactor protector has been detected
- NMmicronick.exe (PID: 4624)
Manual execution by a user
- NMmicronick.exe (PID: 5992)
- Gxtuum.exe (PID: 6260)
- Gxtuum.exe (PID: 6436)
- msedge.exe (PID: 1224)
- WinRAR.exe (PID: 5680)
- WinRAR.exe (PID: 7708)
- OpenWith.exe (PID: 7296)
- WinRAR.exe (PID: 7008)
- in.exe (PID: 4652)
- WinRAR.exe (PID: 4952)
- WinRAR.exe (PID: 7076)
- WinRAR.exe (PID: 7684)
- Gxtuum.exe (PID: 3208)
The sample compiled with english language support
- skotes.exe (PID: 5788)
- iwgpdsdO2.tmp (PID: 7524)
- riDpuiyI3qNN.tmp (PID: 7976)
- 27aead1158.exe (PID: 7932)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 7800)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3928)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 6412)
- powershell.exe (PID: 7800)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 6980)
The sample compiled with czech language support
- skotes.exe (PID: 5788)
Reads Environment values
- ae16662188354edfa7f4cc7015382fe6.exe (PID: 7084)
Attempting to use instant messaging service
- ce7eadc6471c4b11adf709e99a706aeb.exe (PID: 7064)
Application launched itself
- msedge.exe (PID: 6420)
- msedge.exe (PID: 1224)
- firefox.exe (PID: 3608)
- firefox.exe (PID: 6644)
The sample compiled with russian language support
- iwgpdsdO2.tmp (PID: 7524)
Changes the registry key values via Powershell
- flashdecompiler2.exe (PID: 7544)
Starts MODE.COM to configure console settings
- mode.com (PID: 8124)
Executable content was dropped or overwritten
- firefox.exe (PID: 6644)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:22 17:40:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 322048 |
| InitializedDataSize: | 104960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x31a000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
281
Monitored processes
156
Malicious processes
38
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=5476 --field-trial-handle=3100,i,18059060334220081753,15323129114739439352,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2396 --field-trial-handle=2400,i,10971682057398369935,12635828122235481384,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 154fc53503.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\Users\admin\Desktop\file.exe" | C:\Users\admin\Desktop\file.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
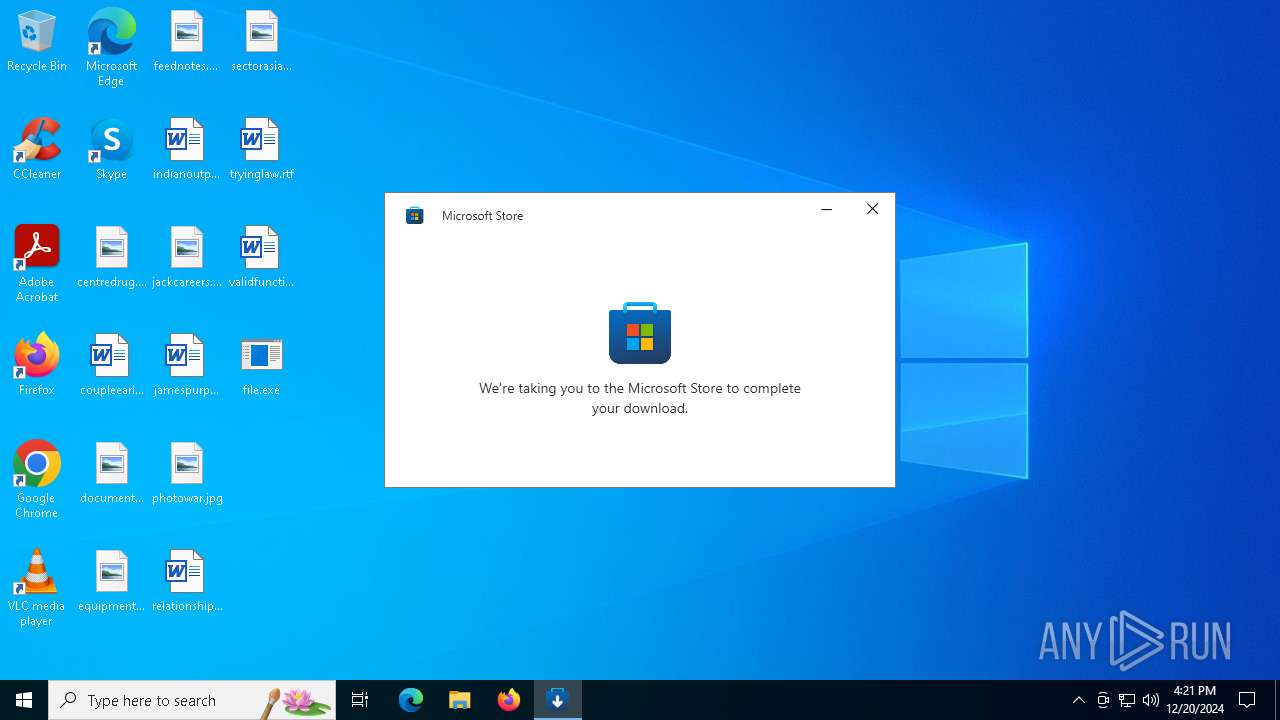
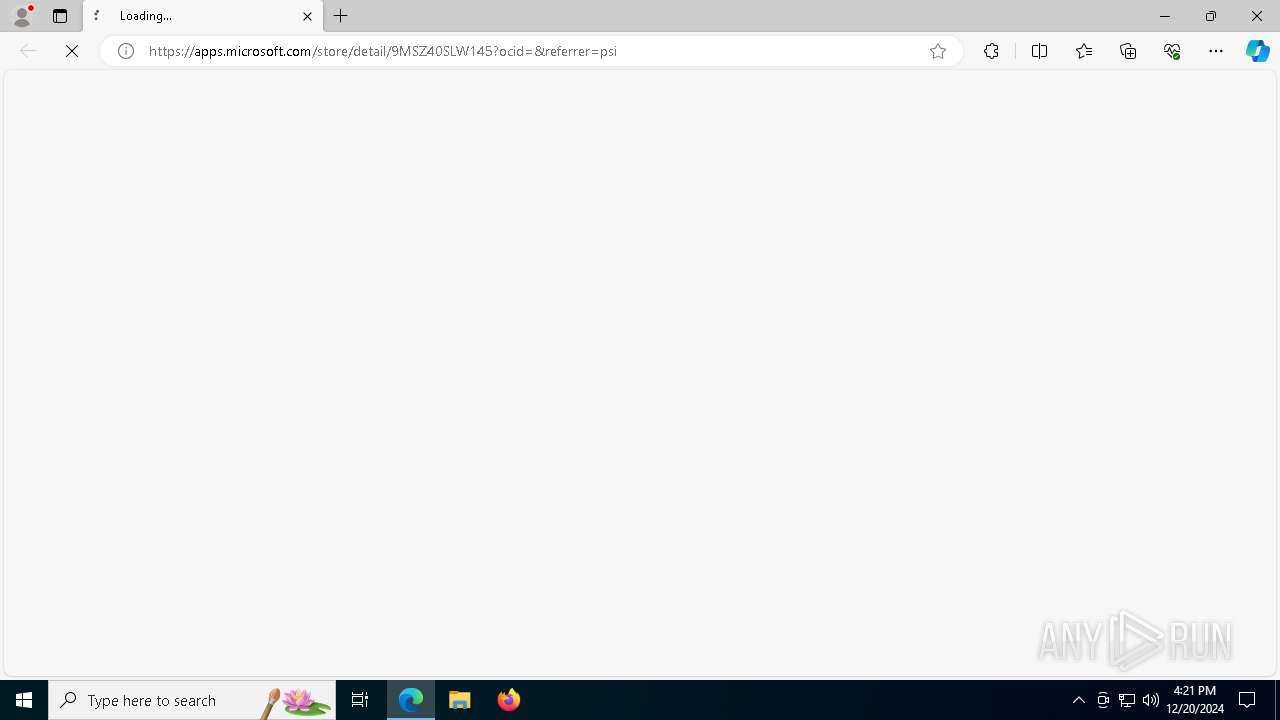
| 1224 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate --single-argument https://apps.microsoft.com/store/detail/9MSZ40SLW145?ocid=&referrer=psi | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1304 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2204 -childID 3 -isForBrowser -prefsHandle 4760 -prefMapHandle 4756 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1344 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1982370b-5034-4eb1-bb0a-49a6f86cf0be} 6644 "\\.\pipe\gecko-crash-server-pipe.6644" 2328ce38bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\AppData\Local\Temp\1018678001\aed45e6ed3.exe" | C:\Users\admin\AppData\Local\Temp\1018678001\aed45e6ed3.exe | skotes.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1400 | "C:\Users\admin\AppData\Local\Temp\1018691001\d78c286d75.exe" | C:\Users\admin\AppData\Local\Temp\1018691001\d78c286d75.exe | — | skotes.exe | |||||||||||
User: admin Company: ⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫⍫ Integrity Level: MEDIUM Description: sourceFinish_setup Exit code: 0 Version: 57.9.4.48 Modules
| |||||||||||||||
| 1448 | "C:\Users\admin\AppData\Local\Temp\1018679001\587dfd33b3.exe" | C:\Users\admin\AppData\Local\Temp\1018679001\587dfd33b3.exe | 587dfd33b3.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
126 803
Read events
126 647
Write events
156
Delete events
0
Modification events
| (PID) Process: | (5788) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5788) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5788) skotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6260) Gxtuum.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6260) Gxtuum.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6260) Gxtuum.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5392) 18765d3f82.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\18765d3f82_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5392) 18765d3f82.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\18765d3f82_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5392) 18765d3f82.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\18765d3f82_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5392) 18765d3f82.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\18765d3f82_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
86
Suspicious files
278
Text files
124
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\NMmicronick[1].exe | executable | |
MD5:09C3F125FB23AC5BF6E7546E314F1CFD | SHA256:2E582150D30010CCA09A21F01BA47CAEA4F9A2F53469C54EE2BF1750D6F3BBCE | |||
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[1].exe | executable | |
MD5:25FB9C54265BBACC7A055174479F0B70 | SHA256:552F8BE2C6B2208A89C728F68488930C661B3A06C35A20D133EF7D3C63A86B9C | |||
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\random[1].exe | executable | |
MD5:27C1F96D7E1B72B6817B6EFEFF037F90 | SHA256:AEC3EC473DE321D123E939985579227EE62B53B3B3EDB7AB96E2A66C17E9696D | |||
| 968 | file.exe | C:\Windows\Tasks\skotes.job | binary | |
MD5:E8D4A9A4D53330E49F5F8D5E0A017AEA | SHA256:DEB9372D7C99110B347EA43DCDED9806F90A9E7A46AD3F62274036B6746C199B | |||
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Temp\1018673001\01bfc38a74.exe | executable | |
MD5:27C1F96D7E1B72B6817B6EFEFF037F90 | SHA256:AEC3EC473DE321D123E939985579227EE62B53B3B3EDB7AB96E2A66C17E9696D | |||
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[2].exe | executable | |
MD5:E8AF4D0D0B47AC68D762B7F288AE8E6E | SHA256:B83449768E7AF68867C8BC42B19FF012722D88EA66AEF69DF48661E63E0EB15E | |||
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\random[1].exe | executable | |
MD5:EF08A45833A7D881C90DED1952F96CB4 | SHA256:33C236DC81AF2A47D595731D6FA47269B2874B281152530FDFFDDA9CBEB3B501 | |||
| 4624 | NMmicronick.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Target.vbs | text | |
MD5:C0C3A36819FF4B33F56A213446479C7B | SHA256:245F85E923146CD4FB848E2D10095EE464EF492961D5A3CDB677BE5A463D9B4B | |||
| 5992 | NMmicronick.exe | C:\Windows\Tasks\Gxtuum.job | binary | |
MD5:E2E13EE110C61FC38EE4051E0819105B | SHA256:04DD4EEE83E076188B9FAE94E2F7AC2F9D668C36D31987F79A3EB95E14E84D01 | |||
| 5788 | skotes.exe | C:\Users\admin\AppData\Local\Temp\1018678001\aed45e6ed3.exe | executable | |
MD5:AB987307E7E74C82D854374F6A3E5444 | SHA256:BB1003E21C2751B7F1BCC5575897D10C30278F1DDA645BD93F954ADE54FE973B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
337
TCP/UDP connections
252
DNS requests
204
Threats
136
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5788 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
5788 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
5788 | skotes.exe | GET | 200 | 31.41.244.11:80 | http://31.41.244.11/files/Krokodyl02/random.exe | unknown | — | — | unknown |
5788 | skotes.exe | GET | 200 | 31.41.244.11:80 | http://31.41.244.11/files/fate/random.exe | unknown | — | — | unknown |
5788 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
5788 | skotes.exe | GET | 200 | 31.41.244.11:80 | http://31.41.244.11/files/london/random.exe | unknown | — | — | unknown |
5788 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
5788 | skotes.exe | GET | 200 | 194.126.174.112:80 | http://194.126.174.112/files/Mnanadra/NMmicronick.exe | unknown | — | — | unknown |
5788 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
5788 | skotes.exe | POST | 200 | 185.215.113.43:80 | http://185.215.113.43/Zu7JuNko/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
440 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.161:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
440 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5788 | skotes.exe | 185.215.113.43:80 | — | 1337team Limited | SC | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
sweepyribs.lat |
| malicious |
grannyejh.lat |
| malicious |
discokeyus.lat |
| malicious |
pancakedipyps.click |
| malicious |
treehoneyi.click |
| malicious |
httpbin.org |
| unknown |
home.fivetk5ht.top |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5788 | skotes.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
5788 | skotes.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
5788 | skotes.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5788 | skotes.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 2 |
5788 | skotes.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5788 | skotes.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5788 | skotes.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (discokeyus .lat) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (grannyejh .lat) |
5916 | 01bfc38a74.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (discokeyus .lat in TLS SNI) |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
file.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
01bfc38a74.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
5420c6736f.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
aed45e6ed3.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
skotes.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
99de4b6e54.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
10eb54c21a.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
a269558120.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
f224d09151.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|