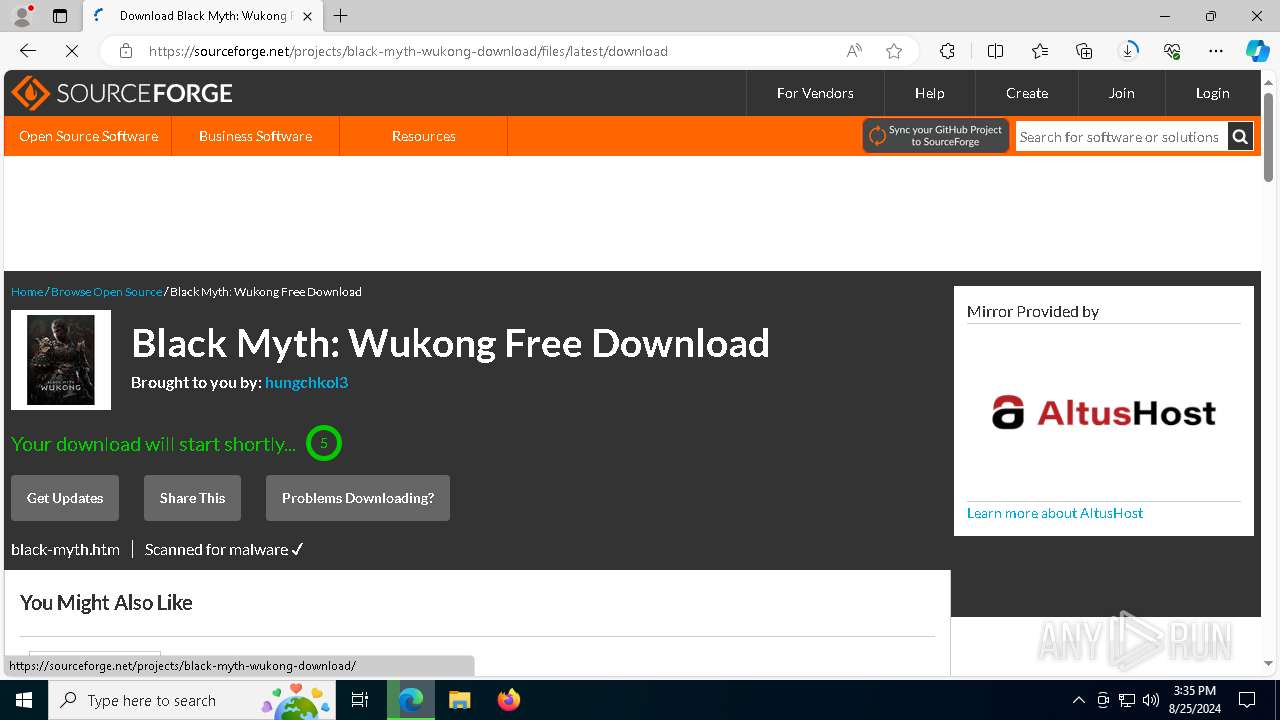
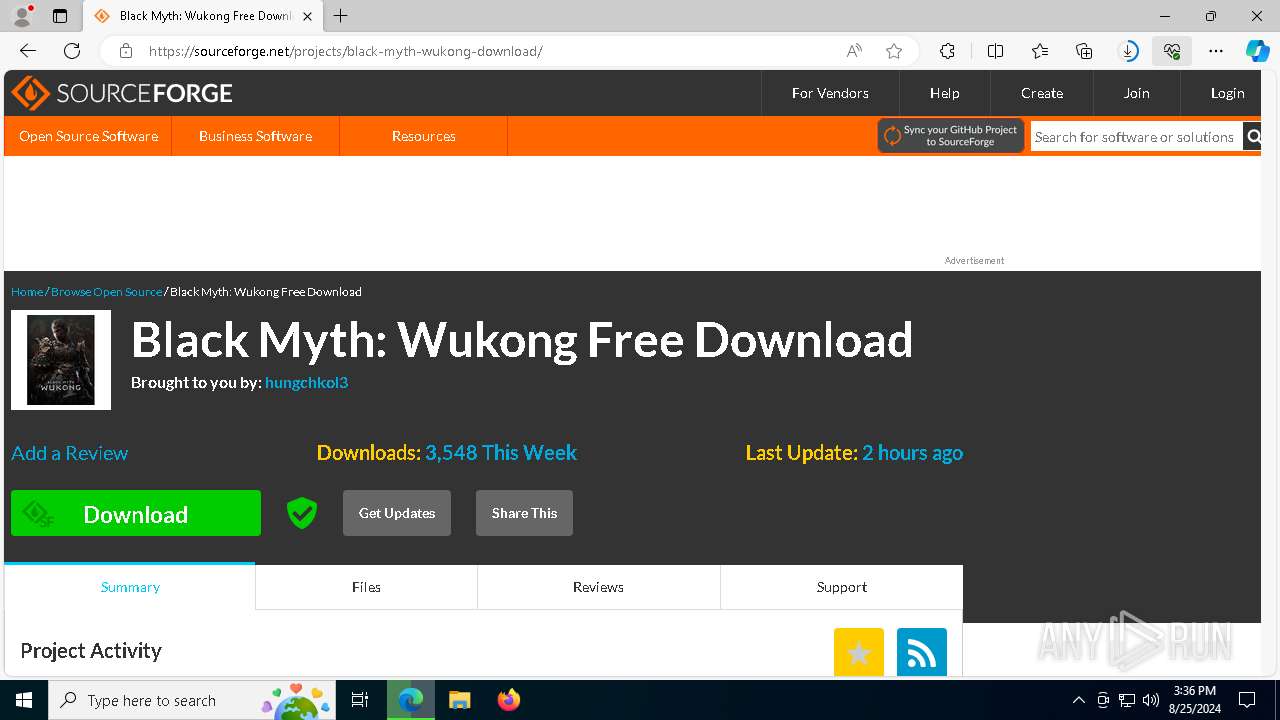
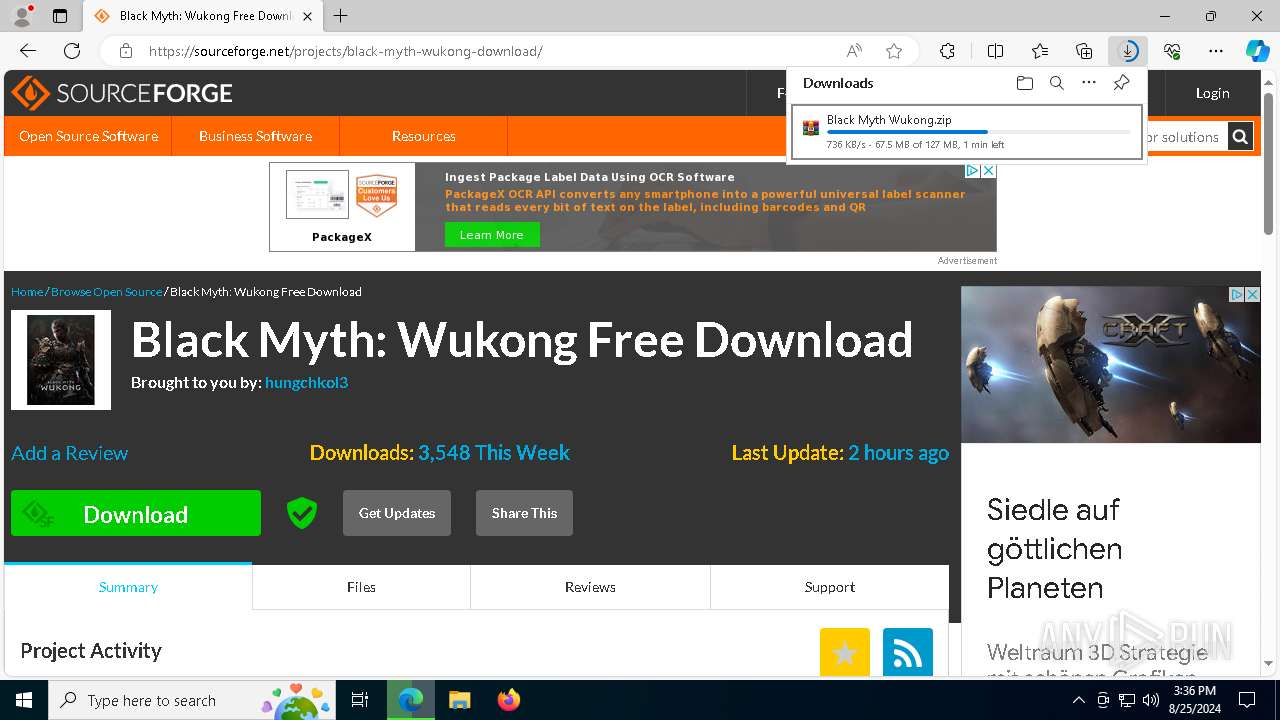
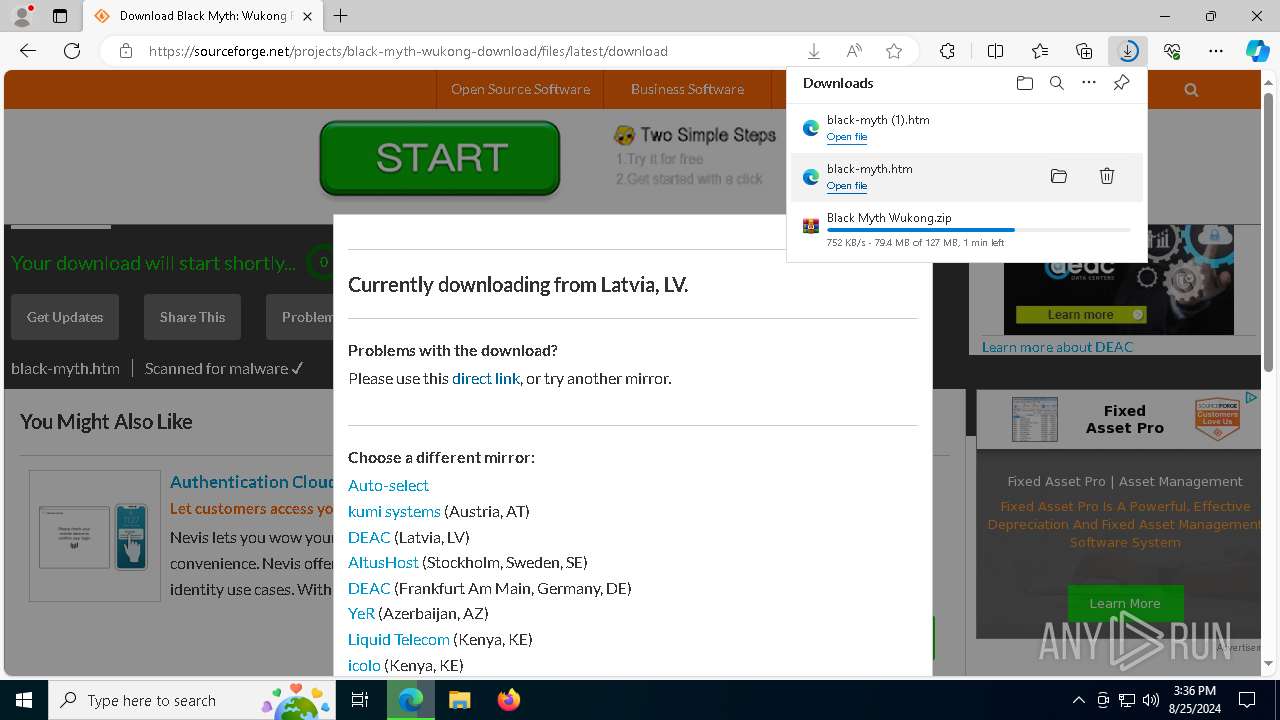
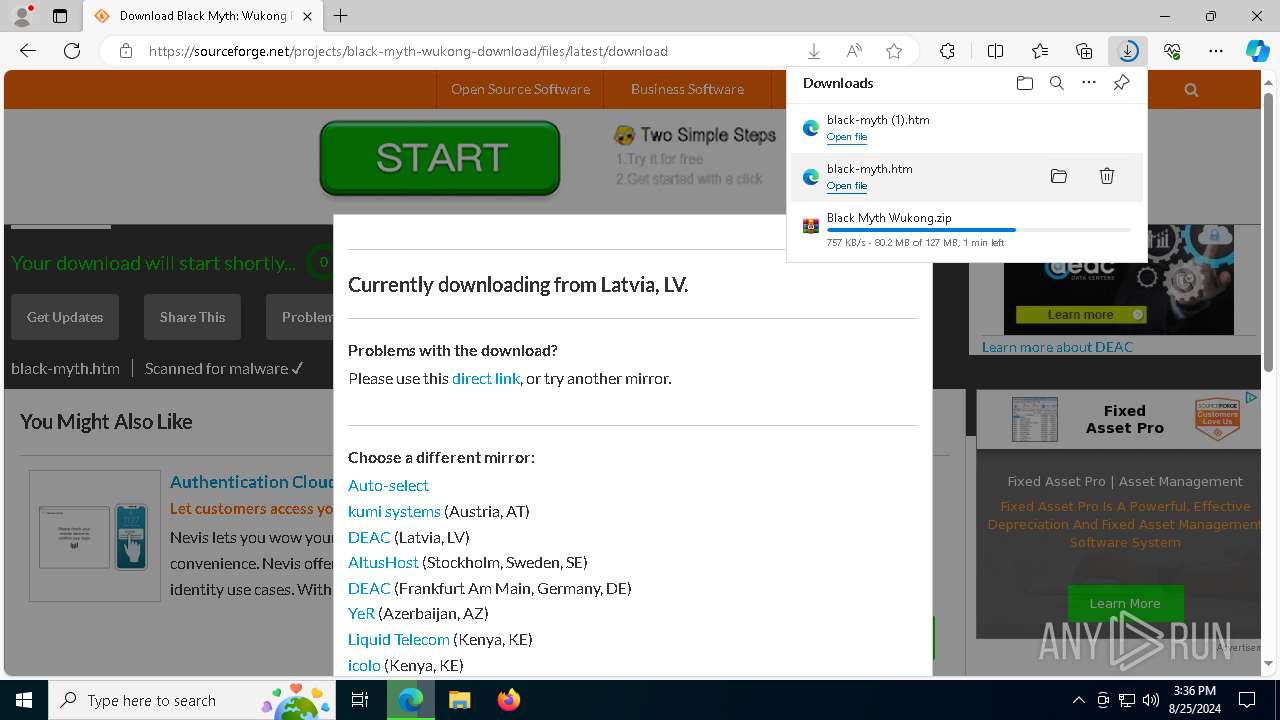
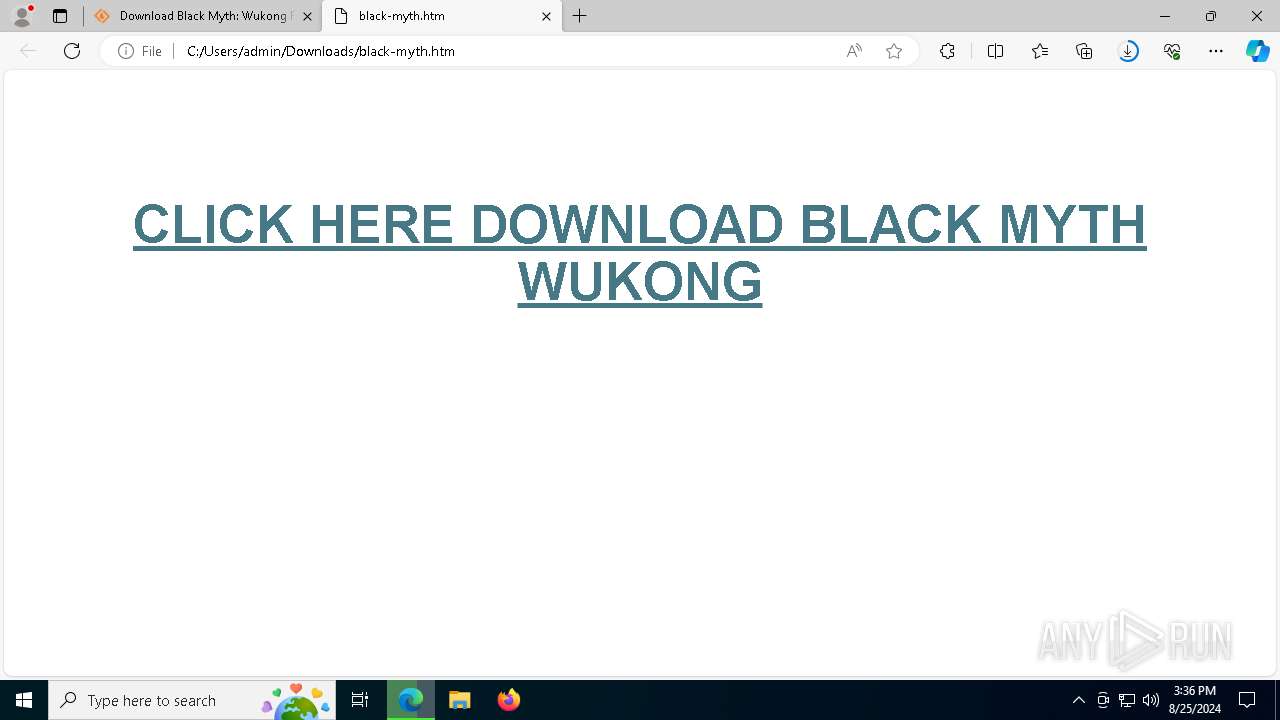
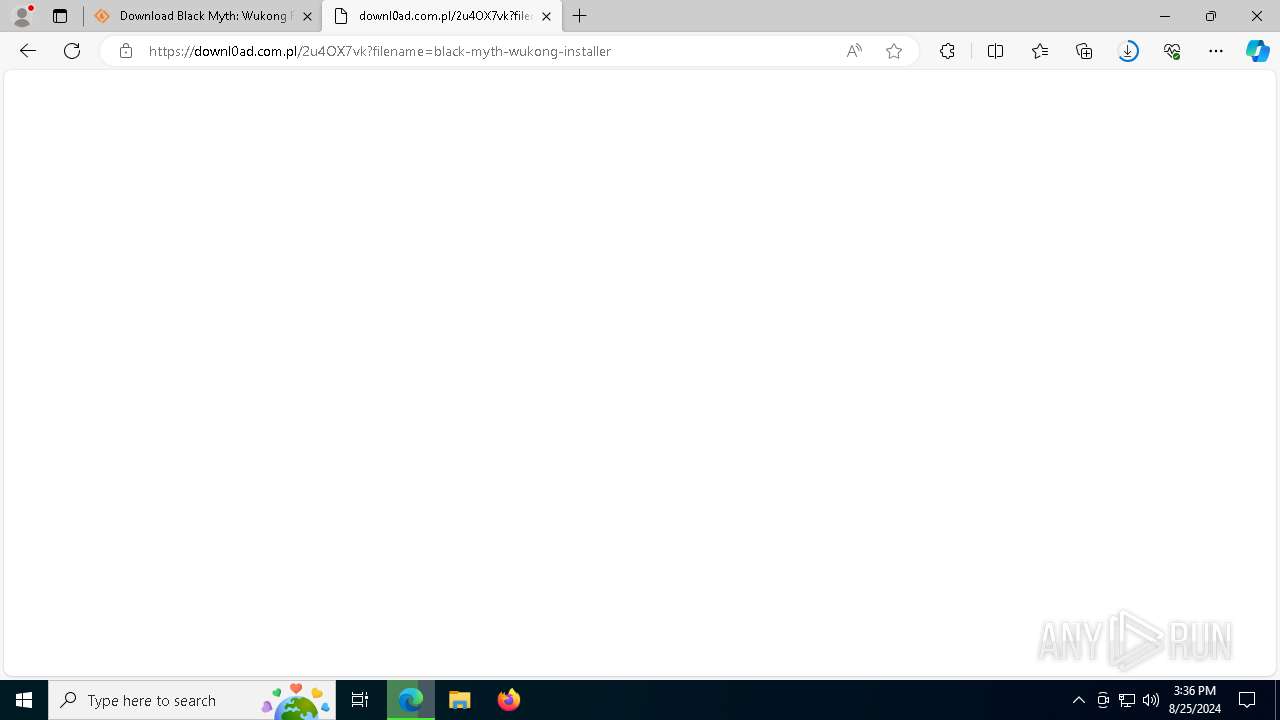
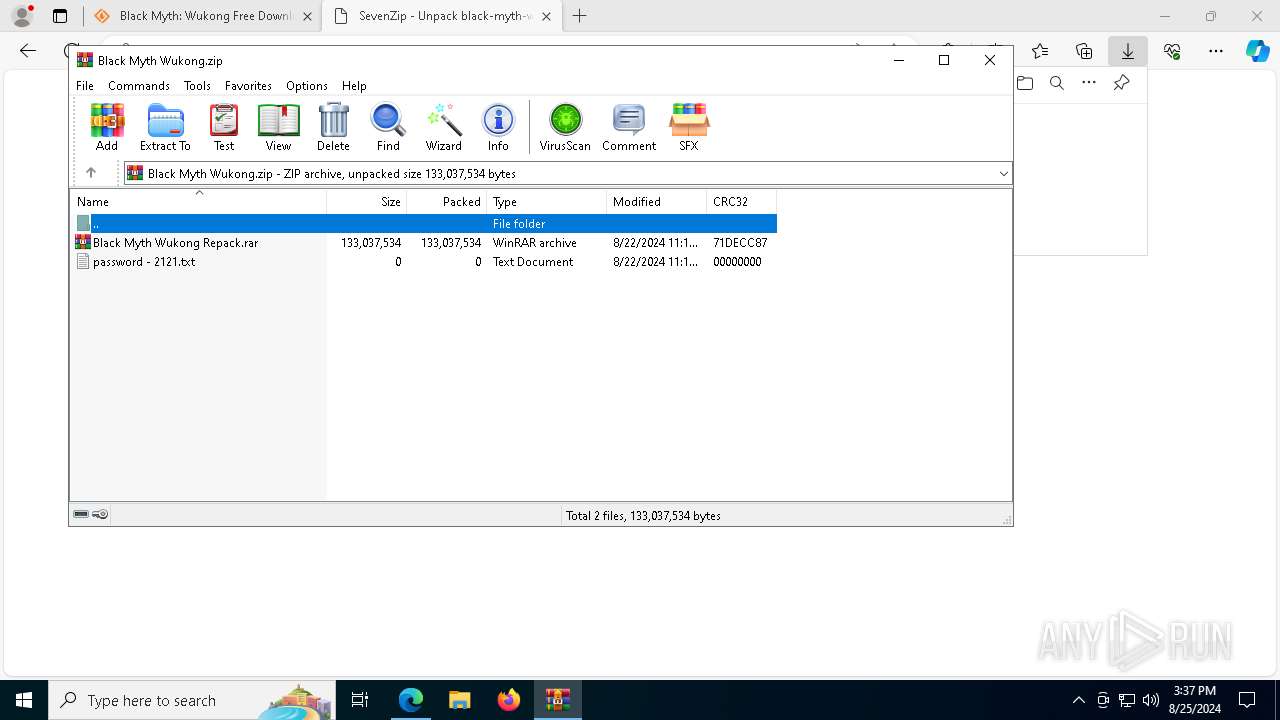
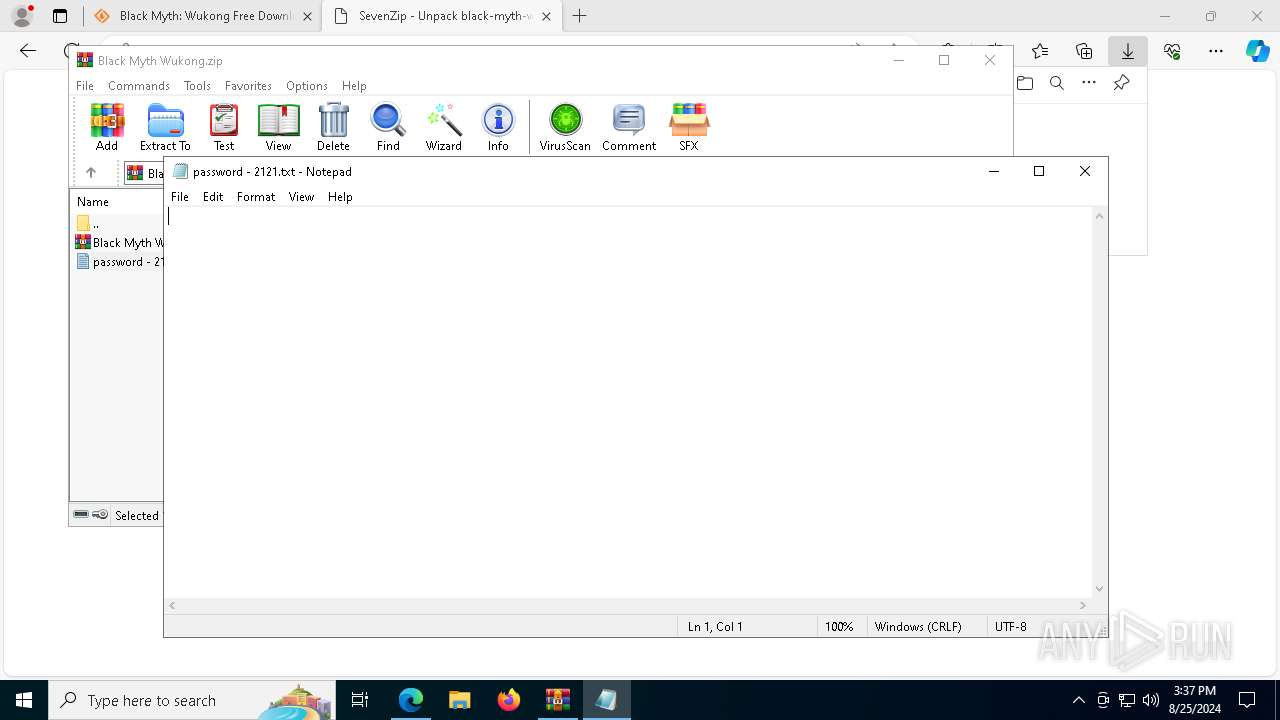
| URL: | https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwja3-TAupCIAxWZWUEAHY0aAlgQFnoECAsQAQ&url=https%3A%2F%2Fsourceforge.net%2Fprojects%2Fblack-myth-wukong%2Ffiles%2F&usg=AOvVaw0jFJH1-PTBWt9FC0r2hmx7&opi=89978449 |
| Full analysis: | https://app.any.run/tasks/003cec86-7015-400f-8173-e50633a41ff9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 25, 2024, 15:34:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C4EC171ACE764C1AB3A491FD8AE9EB5C |
| SHA1: | 534D7F57DE96638C402FF58E52A771BBB5D179AC |
| SHA256: | 927D221F2B0D71A67F355238A042F4B4756B5E2A0B3F1084C85A3FE41D04C097 |
| SSDEEP: | 6:2OLI2sq+wp1w4pN0xs3UYNRR3zC2nIAAy7ESlBxwa:2V2JnN0TY55IsYiX |
MALICIOUS
LUMMA has been detected (SURICATA)
- Installer.exe (PID: 3568)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
Actions looks like stealing of personal data
- Installer.exe (PID: 3568)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
Stealers network behavior
- Installer.exe (PID: 3568)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
LUMMA has been detected (YARA)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7404)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6132)
- WinRAR.exe (PID: 5504)
- ShellExperienceHost.exe (PID: 1064)
Application launched itself
- WinRAR.exe (PID: 6132)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6132)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5504)
- WinRAR.exe (PID: 6880)
Searches for installed software
- Installer.exe (PID: 3568)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
- Installer.exe (PID: 7536)
INFO
Reads the computer name
- identity_helper.exe (PID: 7872)
- Installer.exe (PID: 3568)
- ShellExperienceHost.exe (PID: 1064)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6648)
- WinRAR.exe (PID: 6132)
- OpenWith.exe (PID: 6296)
Reads Environment values
- identity_helper.exe (PID: 7872)
Checks supported languages
- identity_helper.exe (PID: 7872)
- Installer.exe (PID: 3568)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
- ShellExperienceHost.exe (PID: 1064)
- Installer.exe (PID: 6212)
Connects to unusual port
- msedge.exe (PID: 6988)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2092)
Application launched itself
- msedge.exe (PID: 6648)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5504)
- WinRAR.exe (PID: 6880)
Reads the software policy settings
- Installer.exe (PID: 3568)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 2224)
- Installer.exe (PID: 7404)
Manual execution by a user
- WinRAR.exe (PID: 2992)
- WinRAR.exe (PID: 6880)
- Installer.exe (PID: 7404)
- Installer.exe (PID: 2224)
- notepad++.exe (PID: 940)
- Installer.exe (PID: 6212)
- Installer.exe (PID: 7536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(7536) Installer.exe
C2 (9)deicedosmzj.shop
southedhiscuso.shop
cagedwifedsozm.shop
consciousourwi.shop
interactiedovspm.shop
charecteristicdxp.shop
potentioallykeos.shop
reagoofydwqioo.shop
weiggheticulop.shop
(PID) Process(7404) Installer.exe
C2 (9)deicedosmzj.shop
southedhiscuso.shop
cagedwifedsozm.shop
consciousourwi.shop
interactiedovspm.shop
charecteristicdxp.shop
potentioallykeos.shop
reagoofydwqioo.shop
weiggheticulop.shop
Total processes
236
Monitored processes
98
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=44 --mojo-platform-channel-handle=7776 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 788 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=74 --mojo-platform-channel-handle=7608 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
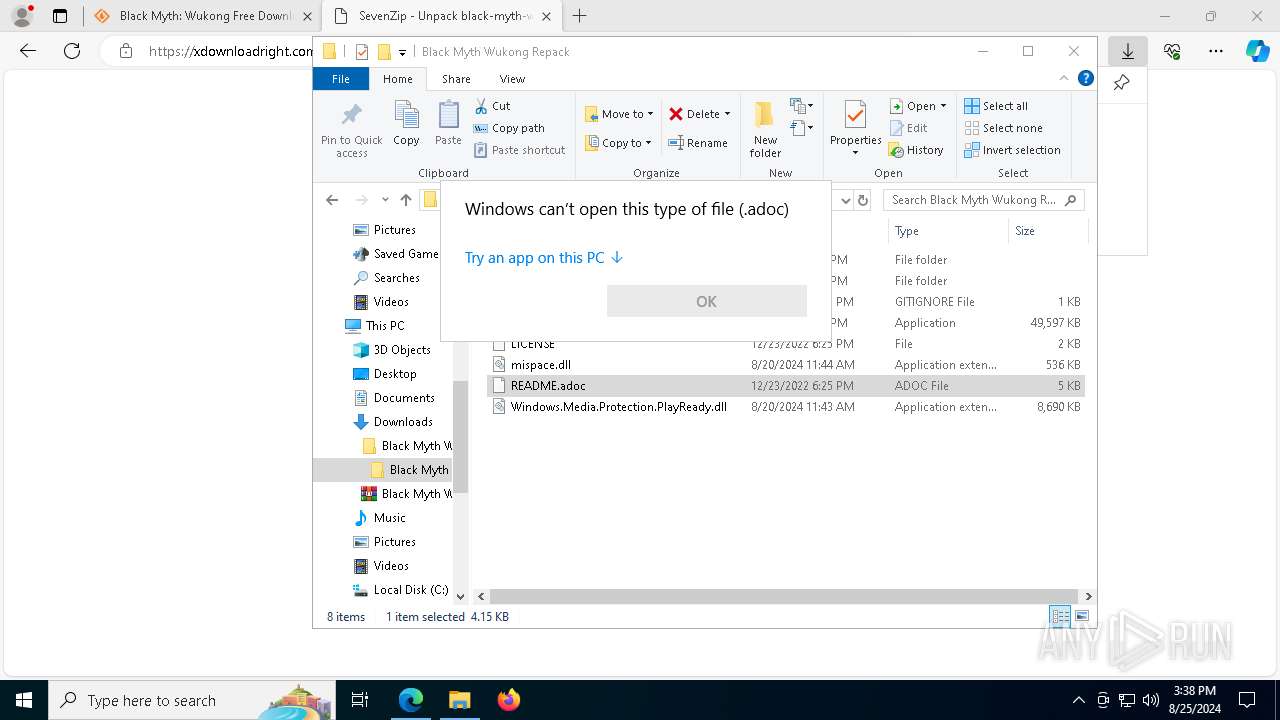
| 940 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\Black Myth Wukong\Black Myth Wukong Repack\README.adoc" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8652 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1064 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=7456 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6164 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5388 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1288 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8276 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3536 --field-trial-handle=2424,i,5264802206198586636,16478762546117241676,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
33 987
Read events
33 650
Write events
316
Delete events
21
Modification events
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6648) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
16
Suspicious files
451
Text files
231
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11da7e.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11da8e.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11da8e.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11da9e.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11da7e.TMP | — | |
MD5:— | SHA256:— | |||
| 6648 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
288
DNS requests
294
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1124 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6488 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724900014&P2=404&P3=2&P4=N5e2fcr3Ip5bC5DzuUsd%2bclx5XLUErymyxmEeF846n91lDMtLW2Wq%2bpWGJh205s7850OIa4khVG%2bm%2btvbeM%2fog%3d%3d | unknown | — | — | whitelisted |
7716 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7716 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6488 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724900014&P2=404&P3=2&P4=N5e2fcr3Ip5bC5DzuUsd%2bclx5XLUErymyxmEeF846n91lDMtLW2Wq%2bpWGJh205s7850OIa4khVG%2bm%2btvbeM%2fog%3d%3d | unknown | — | — | whitelisted |
6488 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724900014&P2=404&P3=2&P4=N5e2fcr3Ip5bC5DzuUsd%2bclx5XLUErymyxmEeF846n91lDMtLW2Wq%2bpWGJh205s7850OIa4khVG%2bm%2btvbeM%2fog%3d%3d | unknown | — | — | whitelisted |
6488 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724900014&P2=404&P3=2&P4=N5e2fcr3Ip5bC5DzuUsd%2bclx5XLUErymyxmEeF846n91lDMtLW2Wq%2bpWGJh205s7850OIa4khVG%2bm%2btvbeM%2fog%3d%3d | unknown | — | — | whitelisted |
6488 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724900014&P2=404&P3=2&P4=N5e2fcr3Ip5bC5DzuUsd%2bclx5XLUErymyxmEeF846n91lDMtLW2Wq%2bpWGJh205s7850OIa4khVG%2bm%2btvbeM%2fog%3d%3d | unknown | — | — | whitelisted |
6488 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/34ab5090-f94b-4ad8-a820-46efdd30b975?P1=1724900014&P2=404&P3=2&P4=b5TCwV1fO2GPBFPe0iGlXA914oO2C6fd269a7nUg%2bnGtNEC4kJp2aivnbw6Xnd1HoDEFTi0GMVcwuOe%2bFo%2bJHA%3d%3d | unknown | — | — | whitelisted |
6488 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/34ab5090-f94b-4ad8-a820-46efdd30b975?P1=1724900014&P2=404&P3=2&P4=b5TCwV1fO2GPBFPe0iGlXA914oO2C6fd269a7nUg%2bnGtNEC4kJp2aivnbw6Xnd1HoDEFTi0GMVcwuOe%2bFo%2bJHA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5144 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3236 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6648 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6988 | msedge.exe | 142.250.184.196:443 | www.google.com | — | — | whitelisted |
6988 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6988 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6988 | msedge.exe | 13.107.253.67:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6988 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
sourceforge.net |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|