| File name: | 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2 |
| Full analysis: | https://app.any.run/tasks/3ae59f6c-2662-4796-bfce-e9b8136a350b |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 04, 2025, 14:20:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 42E70CD4EEE6335DA9EC3C6A51291BA6 |
| SHA1: | 0ED71BA0F7A2F3C1A7B44E121FCEBF62FC83A852 |
| SHA256: | 923DFBDBC42E0676E790084FBCA633868DE76EF09FBA68C62D713B3F4EE627D2 |
| SSDEEP: | 98304:2tcLES2JA5zDQ3gylo+HfxFKWI6JtRU4rXRijMVyTd43JiExwiuMe6pvht1gkbip:2 |
MALICIOUS
AMADEY mutex has been found
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
- ramez.exe (PID: 3100)
Connects to the CnC server
- ramez.exe (PID: 5452)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 5452)
Executing a file with an untrusted certificate
- 79dcc3a02c.exe (PID: 2660)
AMADEY has been detected (YARA)
- ramez.exe (PID: 5452)
SUSPICIOUS
Reads the BIOS version
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
- ramez.exe (PID: 3100)
Starts itself from another location
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
Reads security settings of Internet Explorer
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
- 79dcc3a02c.exe (PID: 2660)
Executable content was dropped or overwritten
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 5452)
Connects to the server without a host name
- ramez.exe (PID: 5452)
The process executes via Task Scheduler
- ramez.exe (PID: 3100)
Process requests binary or script from the Internet
- ramez.exe (PID: 5452)
Potential Corporate Privacy Violation
- ramez.exe (PID: 5452)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 5452)
INFO
Checks supported languages
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
- ramez.exe (PID: 3100)
- 79dcc3a02c.exe (PID: 2660)
Process checks computer location settings
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
Reads the computer name
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
- 79dcc3a02c.exe (PID: 2660)
Create files in a temporary directory
- 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe (PID: 7428)
- ramez.exe (PID: 5452)
Checks proxy server information
- ramez.exe (PID: 5452)
- 79dcc3a02c.exe (PID: 2660)
Creates files or folders in the user directory
- ramez.exe (PID: 5452)
- 79dcc3a02c.exe (PID: 2660)
Themida protector has been detected
- ramez.exe (PID: 5452)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 8048)
- Taskmgr.exe (PID: 6032)
Manual execution by a user
- Taskmgr.exe (PID: 8048)
- WINWORD.EXE (PID: 5744)
- Taskmgr.exe (PID: 6032)
- Taskmgr.exe (PID: 2652)
- Taskmgr.exe (PID: 2692)
The sample compiled with english language support
- ramez.exe (PID: 5452)
Reads the machine GUID from the registry
- 79dcc3a02c.exe (PID: 2660)
Reads the software policy settings
- 79dcc3a02c.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(5452) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)2025
%-lu
DefaultSettings.XResolution
ComputerName
5.34
?scr=1
0000043f
Programs
-unicode-
------
id:
<c>
"
" && ren
Panda Security
e1
-%lu
un:
" && timeout 1 && del
bi:
+++
Kaspersky Lab
&unit=
ProgramData\
Rem
S-%lu-
00000419
\0000
------
vs:
00000423
POST
/quiet
/te4h2nus/index.php
rundll32.exe
rb
cred.dll|clip.dll|
Bitdefender
random
GetNativeSystemInfo
https://
Norton
Doctor Web
WinDefender
&&
2016
av:
msi
360TotalSecurity
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows NT\CurrentVersion
#
ar:
%USERPROFILE%
Content-Disposition: form-data; name="data"; filename="
--
st=s
DefaultSettings.YResolution
Main
Startup
:::
rundll32
pc:
cred.dll
shutdown -s -t 0
.jpg
=
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
185.156.72.96
Comodo
0123456789
-executionpolicy remotesigned -File "
AVG
og:
dm:
ProductName
wb
ESET
|
d1
<d>
2019
GET
shell32.dll
SYSTEM\ControlSet001\Services\BasicDisplay\Video
clip.dll
abcdefghijklmnopqrstuvwxyz0123456789-_
&& Exit"
"
Content-Type: application/octet-stream
Content-Type: application/x-www-form-urlencoded
2022
Content-Type: multipart/form-data; boundary=----
Sophos
\
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
cmd
CurrentBuild
e3
AVAST Software
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
VideoID
"taskkill /f /im "
kernel32.dll
http://
00000422
zip
dll
/k
\App
Powershell.exe
exe
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
sd:
os:
cmd /C RMDIR /s/q
e2
/Plugins/
ps1
ramez.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
d610cf342e
lv:
r=
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
Avira
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:01 04:57:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 317952 |
| InitializedDataSize: | 107520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x315000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
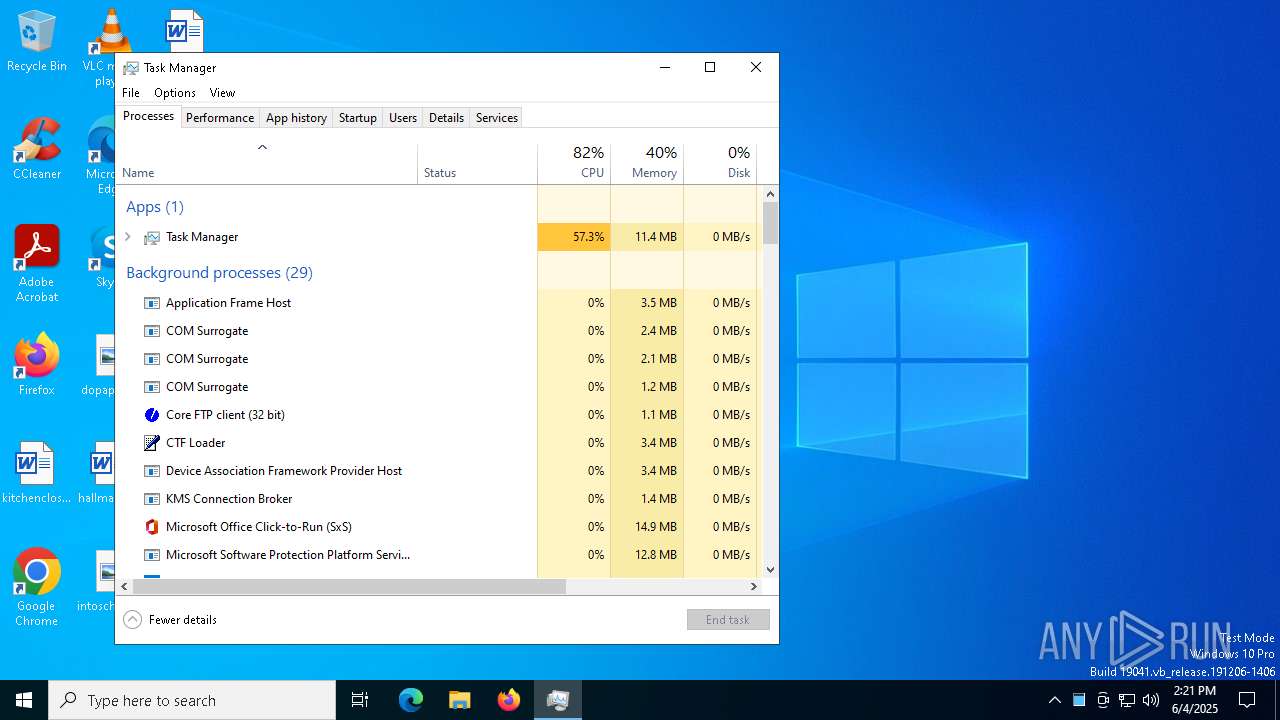
Total processes
145
Monitored processes
13
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "8CFE1FA7-C92B-4D83-A4EF-B8EE0050A0E2" "867C5D4D-EB4D-4B84-BA73-DE8C76879E29" "5744" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2652 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
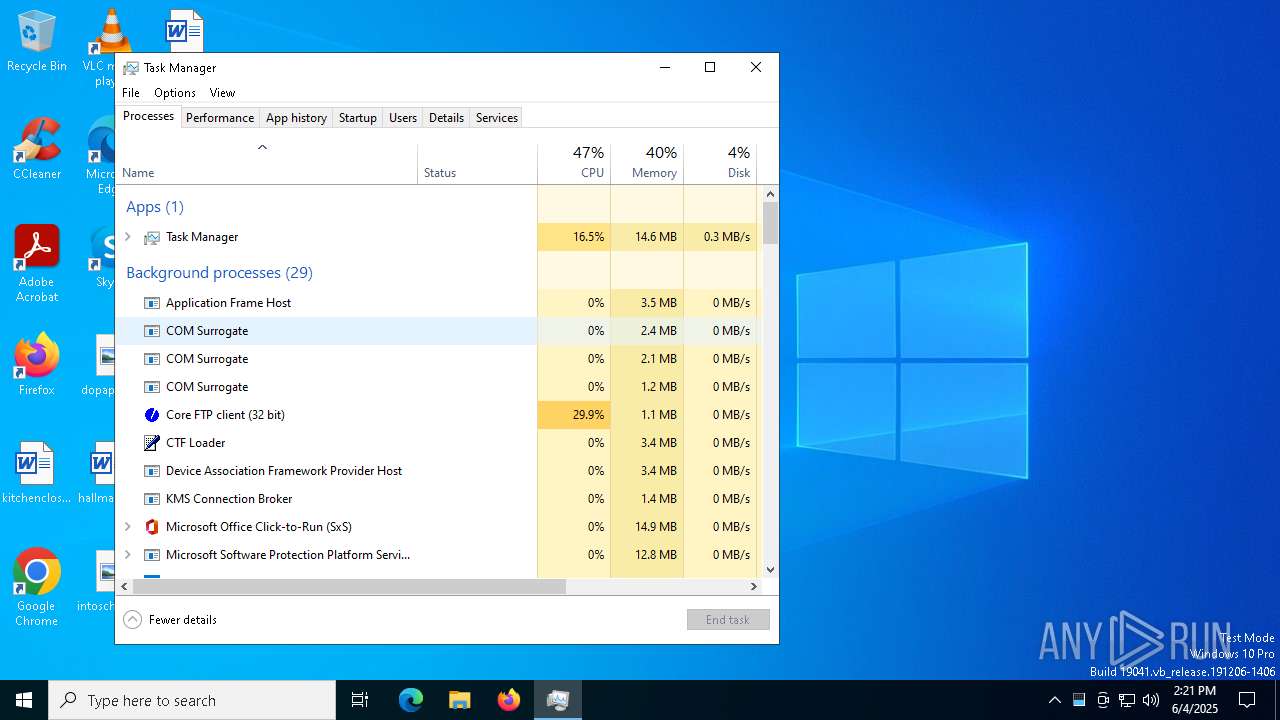
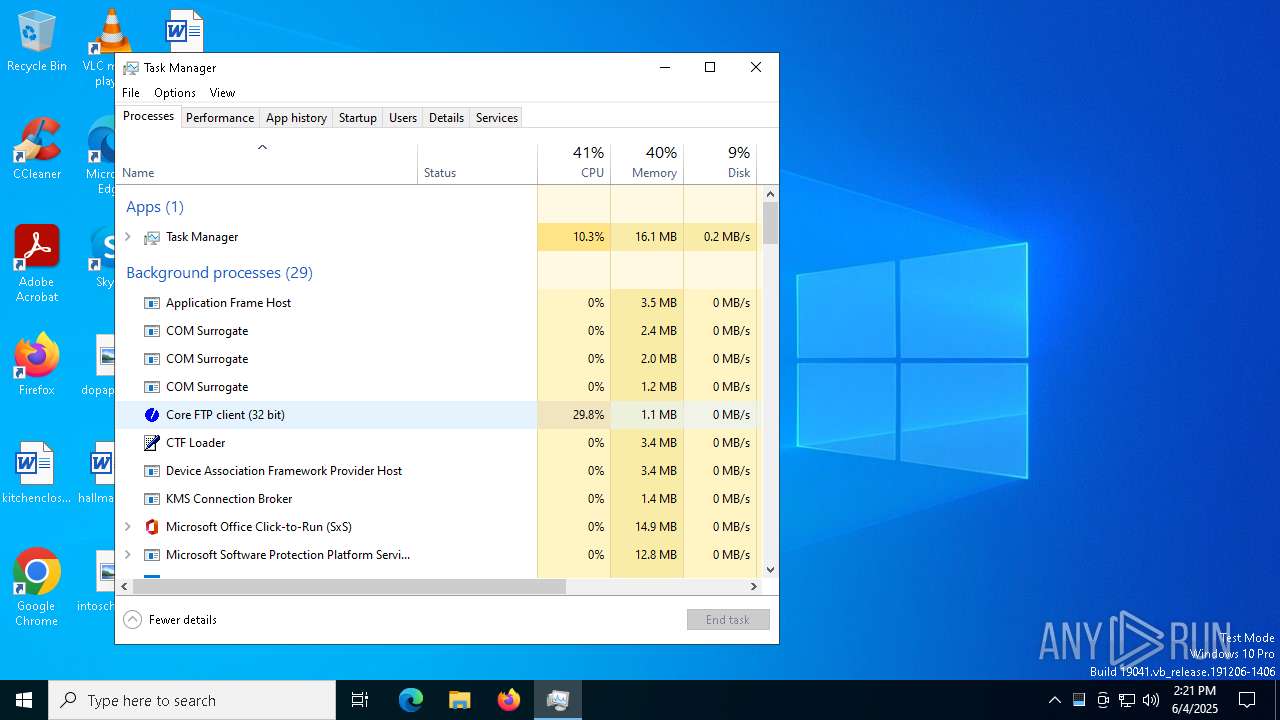
| 2660 | "C:\Users\admin\AppData\Local\Temp\10293200101\79dcc3a02c.exe" | C:\Users\admin\AppData\Local\Temp\10293200101\79dcc3a02c.exe | ramez.exe | ||||||||||||
User: admin Company: Core FTP Integrity Level: MEDIUM Description: Core FTP client Exit code: 1 Version: 2, 2, 1960, 0 Modules
| |||||||||||||||
| 2692 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5452 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
Amadey(PID) Process(5452) ramez.exe C2185.156.72.96 URLhttp://185.156.72.96/te4h2nus/index.php Version5.34 Options Drop directoryd610cf342e Drop nameramez.exe Strings (125)2025 %-lu DefaultSettings.XResolution ComputerName 5.34 ?scr=1 0000043f Programs -unicode- ------ id: <c> " " && ren Panda Security e1 -%lu un: " && timeout 1 && del bi: +++ Kaspersky Lab &unit= ProgramData\ Rem S-%lu- 00000419 \0000 ------ vs: 00000423 POST /quiet /te4h2nus/index.php rundll32.exe rb cred.dll|clip.dll| Bitdefender random GetNativeSystemInfo https:// Norton Doctor Web WinDefender && 2016 av: msi 360TotalSecurity Keyboard Layout\Preload SOFTWARE\Microsoft\Windows NT\CurrentVersion # ar: %USERPROFILE% Content-Disposition: form-data; name="data"; filename=" -- st=s DefaultSettings.YResolution Main Startup ::: rundll32 pc: cred.dll shutdown -s -t 0 .jpg = SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders 185.156.72.96 Comodo 0123456789 -executionpolicy remotesigned -File " AVG og: dm: ProductName wb ESET | d1 <d> 2019 GET shell32.dll SYSTEM\ControlSet001\Services\BasicDisplay\Video clip.dll abcdefghijklmnopqrstuvwxyz0123456789-_ && Exit" "
Content-Type: application/octet-stream Content-Type: application/x-www-form-urlencoded 2022 Content-Type: multipart/form-data; boundary=---- Sophos \ SOFTWARE\Microsoft\Windows\CurrentVersion\Run cmd CurrentBuild e3 AVAST Software SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce VideoID "taskkill /f /im " kernel32.dll http:// 00000422 zip dll /k \App Powershell.exe exe SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName sd: os: cmd /C RMDIR /s/q e2 /Plugins/ ps1 ramez.exe SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders d610cf342e lv: r= SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ Avira | |||||||||||||||
| 5744 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Documents\resolutiontom.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6032 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 083
Read events
12 822
Write events
243
Delete events
18
Modification events
| (PID) Process: | (5452) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5452) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5452) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8048) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (8048) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA043AF67F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AA043AF67F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA043AF67F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA043AF67F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB043AF67F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB043AF67F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB043AF67F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AA043AF67F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB043AF67F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB043AF67F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB043AF67F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB043AF67F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB043AF67F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC043AF67F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA043AF67F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA043AF67F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC043AF67F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC043AF67F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC043AF67F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC043AF67F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC043AF67F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC043AF67F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB043AF67F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA043AF67F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD043AF67F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD043AF67F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD043AF67F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB043AF67F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA043AF67F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB043AF67F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB043AF67F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB043AF67F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB043AF67F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA043AF67F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE043AF67F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE043AF67F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE043AF67F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE043AF67F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (2660) 79dcc3a02c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2660) 79dcc3a02c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2660) 79dcc3a02c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8048) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA043AF67F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015000000000000D0000000000000098AA043AF67F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA043AF67F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA043AF67F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB043AF67F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB043AF67F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB043AF67F00000000000000000000FFFFFFFF49000000490000009090000007000000010000000004250200000000080000000000000080AA043AF67F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB043AF67F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB043AF67F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB043AF67F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB043AF67F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB043AF67F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC043AF67F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA043AF67F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA043AF67F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC043AF67F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC043AF67F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC043AF67F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC043AF67F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC043AF67F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC043AF67F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB043AF67F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA043AF67F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD043AF67F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD043AF67F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD043AF67F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB043AF67F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA043AF67F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB043AF67F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB043AF67F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB043AF67F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB043AF67F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA043AF67F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE043AF67F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE043AF67F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE043AF67F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE043AF67F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (5744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
Executable files
3
Suspicious files
9
Text files
6
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5744 | WINWORD.EXE | C:\Users\admin\Documents\~$solutiontom.rtf | pgc | |
MD5:6858807FF4B67C15F7B3D8EF6550B295 | SHA256:CC7A3F287F6ECA72DA42F83D3A2EA804F4E727B1D9908A3C68333AAA71D85F2A | |||
| 5744 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:1833AA4CD0BEF1558EA48A0256BE53E3 | SHA256:E1D28D46B7EB83B0C369142C23D5B478924C470357361F482C665BEA45194F65 | |||
| 2660 | 79dcc3a02c.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7B5FC60CCA5D8CF767A7572C65728CD6_53DFB8FBFCC33906D37D4A871F5C7952 | binary | |
MD5:465207909EEA9F34D45A574B93B053A1 | SHA256:2DF45BBF7660A9E986BB68CE4DF40CDB6501D0C45894C12CFDC86BBD2E7ADB12 | |||
| 2660 | 79dcc3a02c.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | der | |
MD5:4A90329071AE30B759D279CCA342B0A6 | SHA256:4F544379EDA8E2653F71472AB968AEFD6B5D1F4B3CE28A5EDB14196184ED3B60 | |||
| 2660 | 79dcc3a02c.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\text[1] | text | |
MD5:5E847B1CC501E8A09997640FED7DB52F | SHA256:C06903CB5A25E63794907092B488A8580074C872272A9FC51CEF5E76EEECF7A2 | |||
| 2660 | 79dcc3a02c.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:DF6D3B6132CC71A22A75F2BF5D20D387 | SHA256:A33BC1A92D71B58761274A8EC1DE9E35AD5713B69B5AFB2858199F2334A09229 | |||
| 7428 | 923dfbdbc42e0676e790084fbca633868de76ef09fba68c62d713b3f4ee627d2.exe | C:\Windows\Tasks\ramez.job | binary | |
MD5:D4737CC6C0CC1F6E3EF683C4015C2673 | SHA256:D98B5F9BE86EF168FF61E6D5258032172AA3BCDE7B994CE67D3F1D39411912AA | |||
| 8048 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 5452 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10293200101\79dcc3a02c.exe | executable | |
MD5:341585069E392EE5512C62DFCC0890E4 | SHA256:39078678484F188694E6E3ADA229FE4EBAA622BF89C82C1FA25E958648985B96 | |||
| 2660 | 79dcc3a02c.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
31
DNS requests
23
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5452 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5452 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/unique2/random.exe | unknown | — | — | malicious |
5452 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
5452 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2660 | 79dcc3a02c.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2660 | 79dcc3a02c.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2660 | 79dcc3a02c.exe | GET | 200 | 142.250.186.131:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDtlZ1CqouxeBLS6KxwEWFx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7972 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7552 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5452 | ramez.exe | 185.156.72.96:80 | — | Tov Vaiz Partner | RU | unknown |
5452 | ramez.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5452 | ramez.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
5452 | ramez.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
5452 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5452 | ramez.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5452 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5452 | ramez.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |