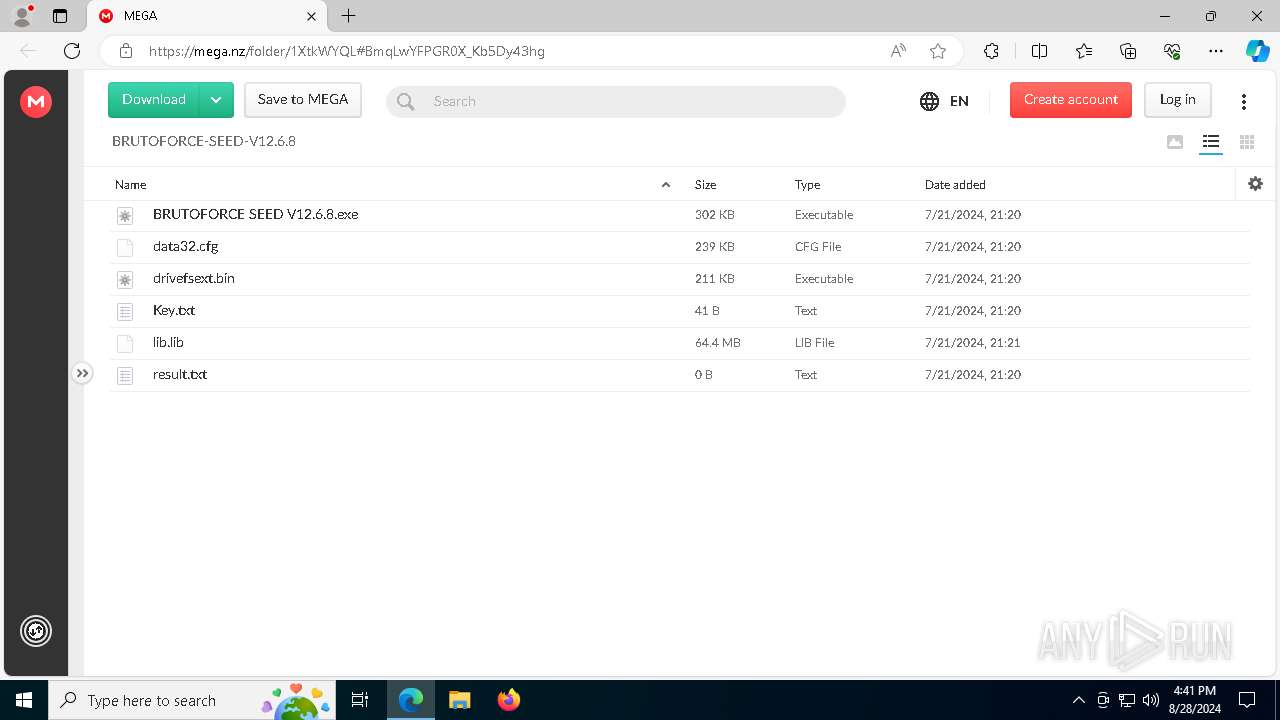
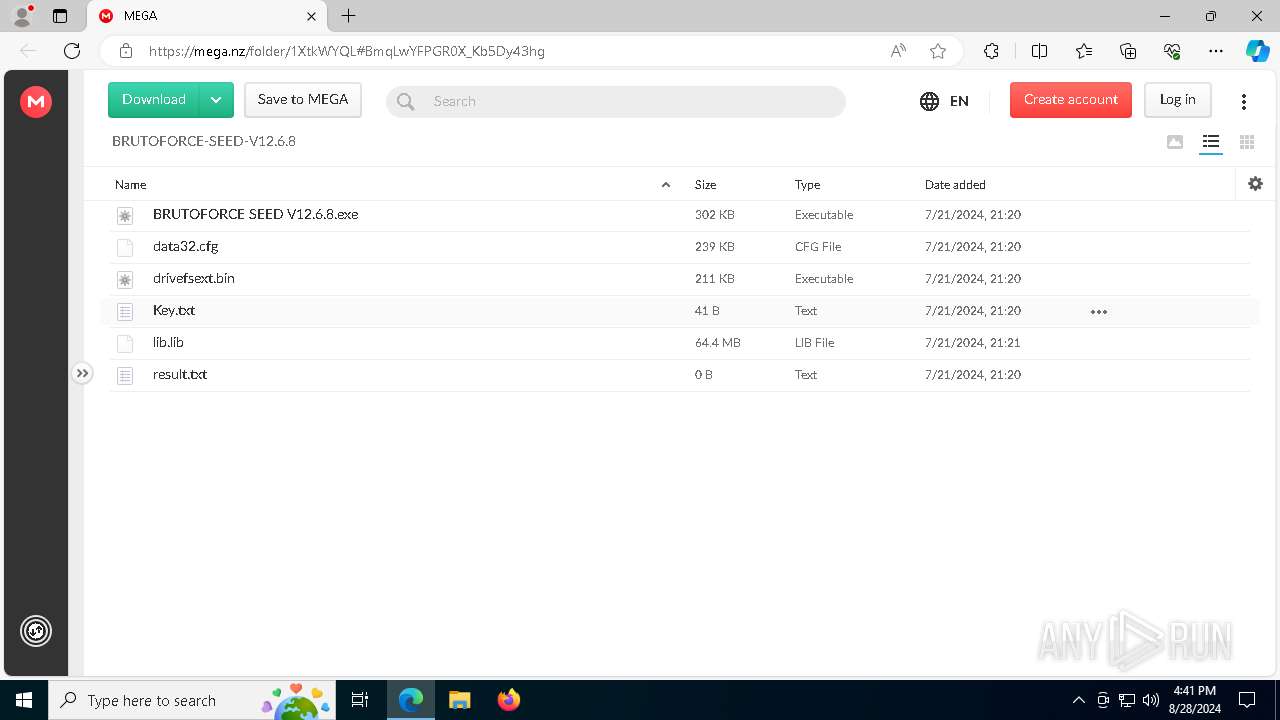
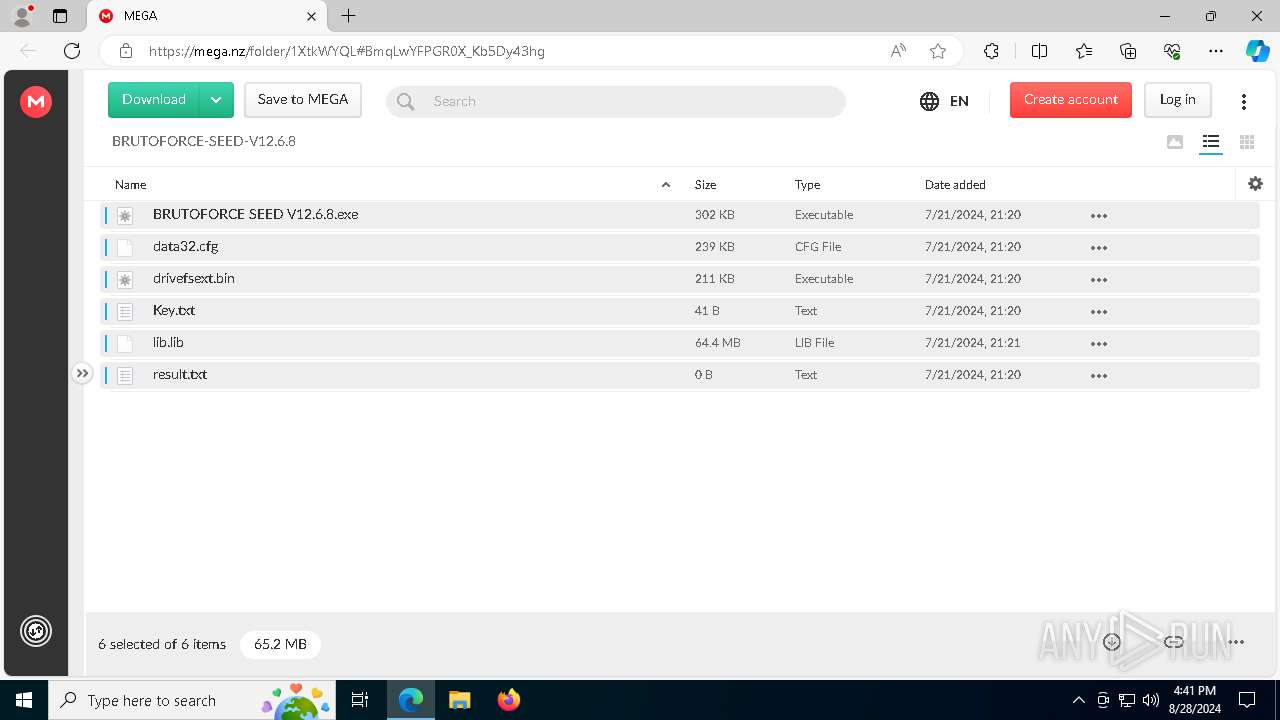
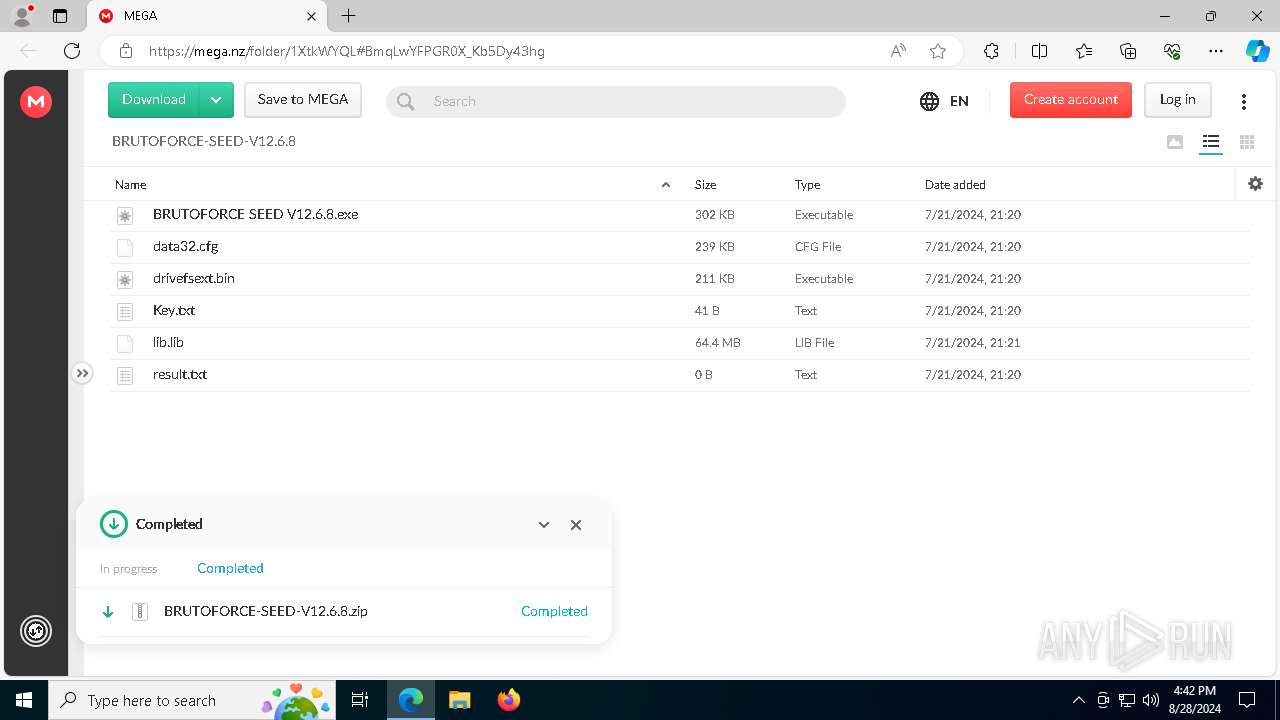
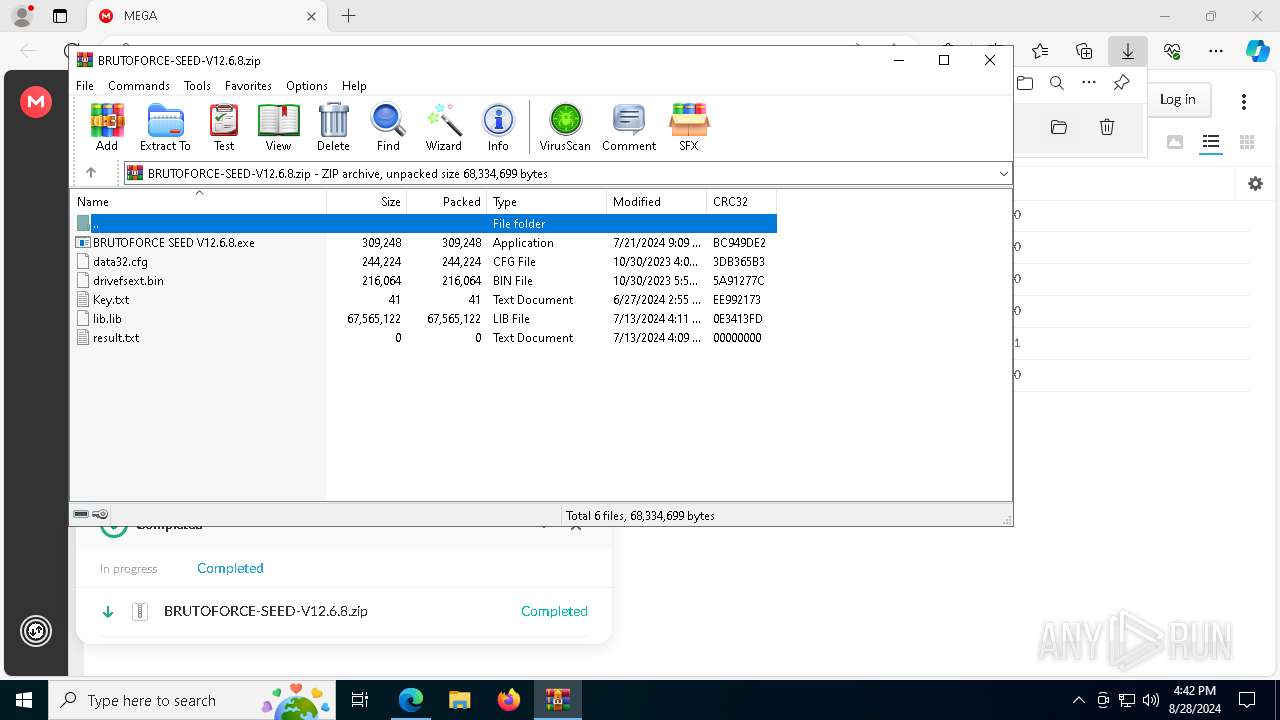
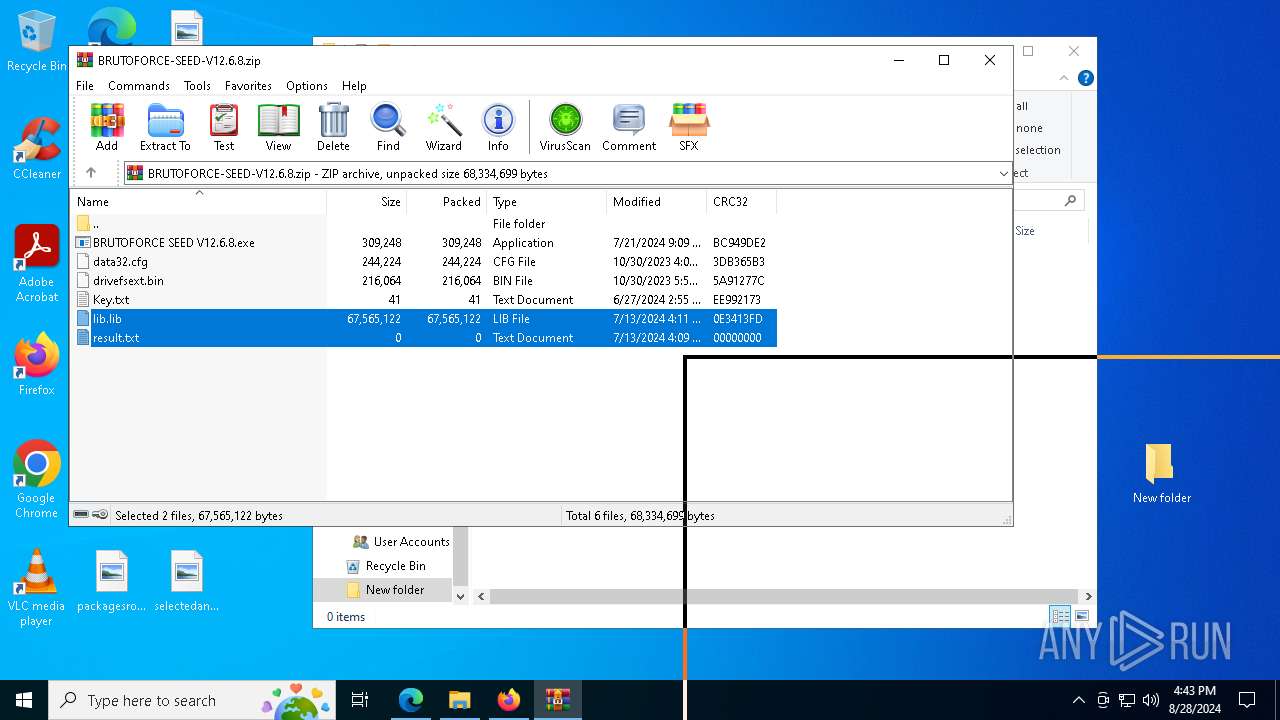
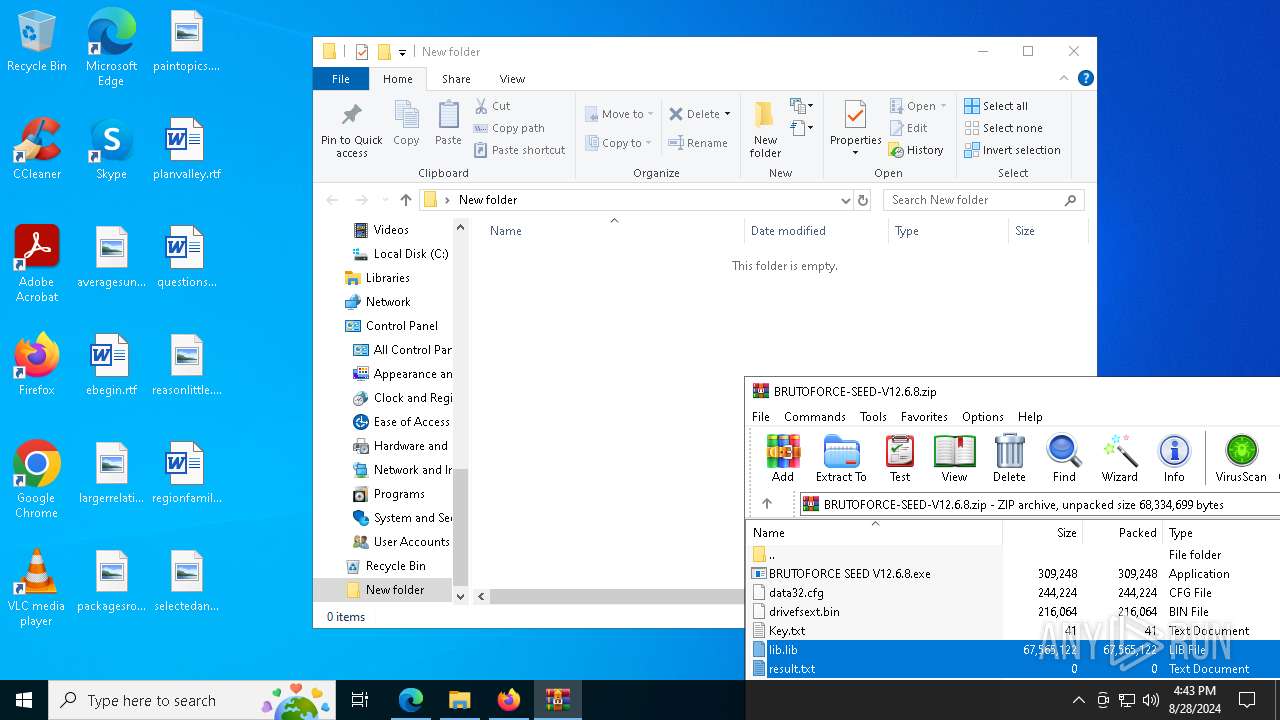
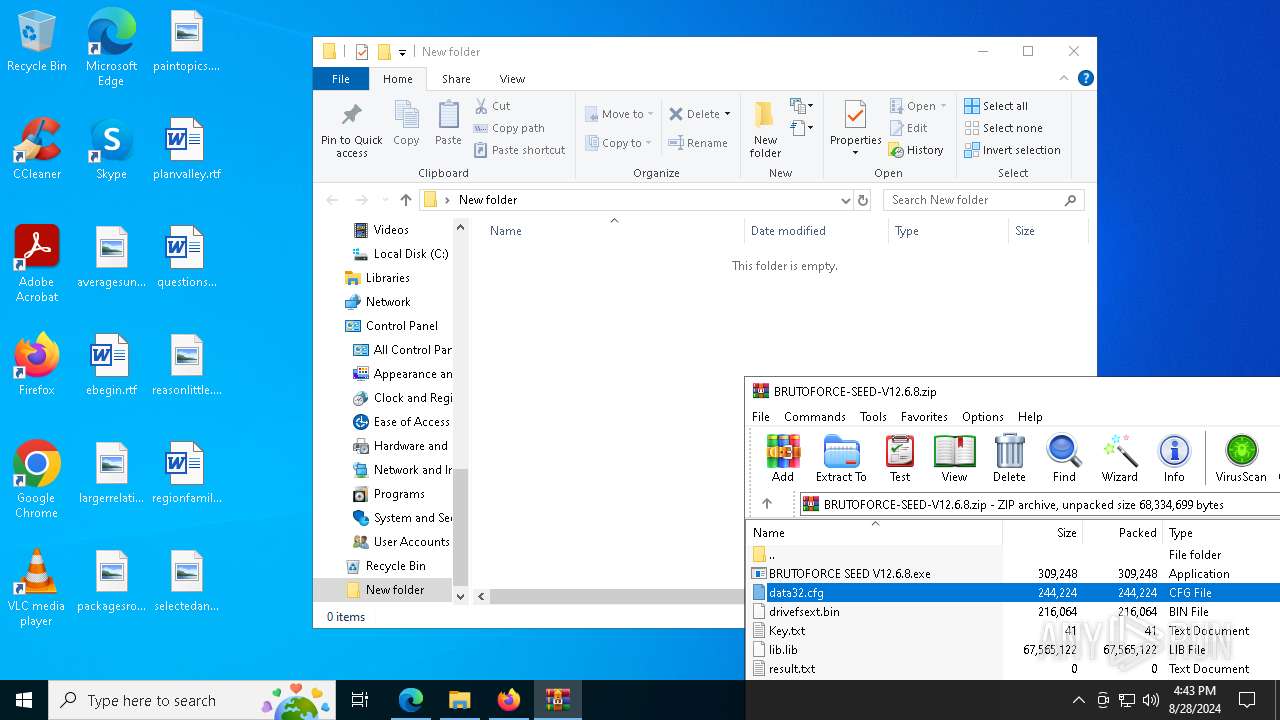
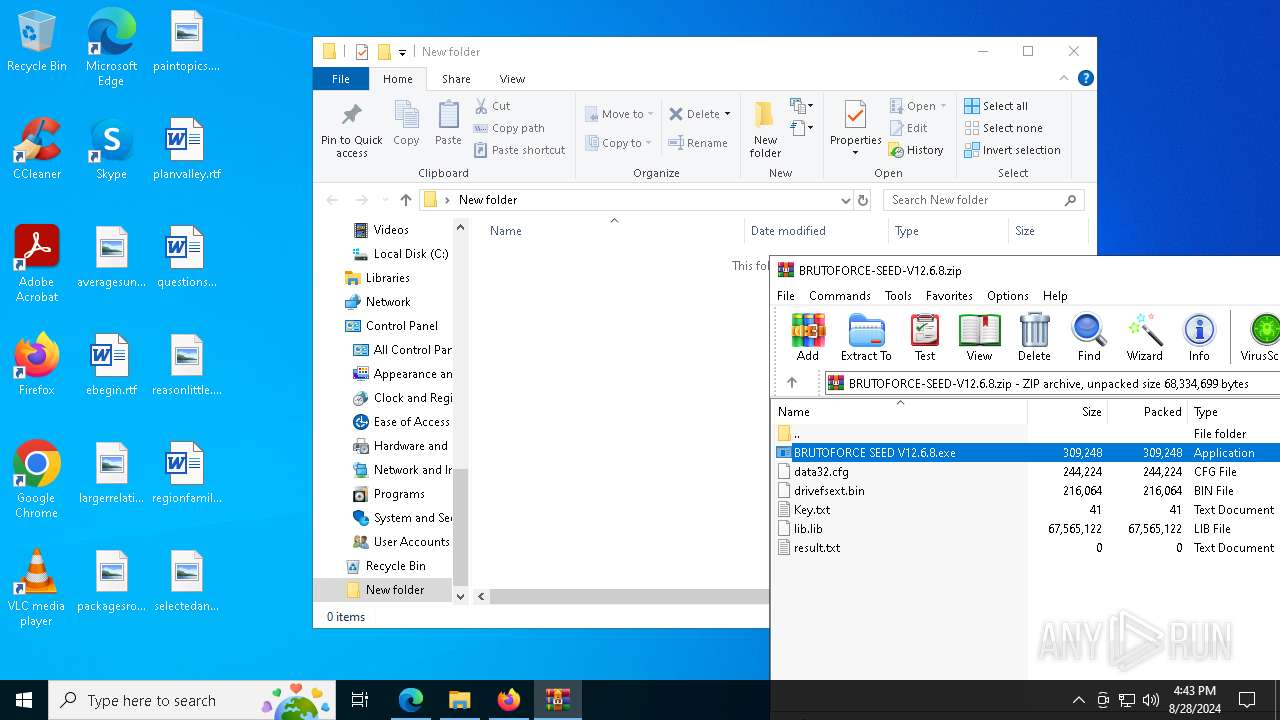
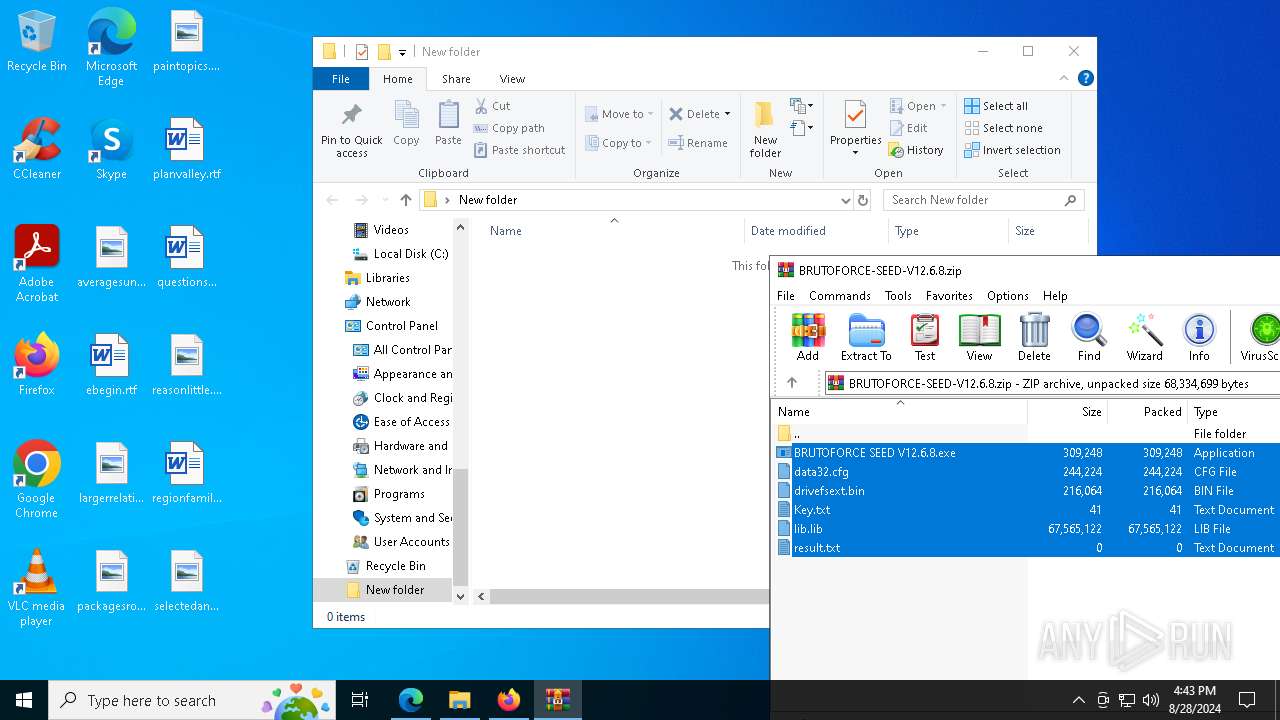
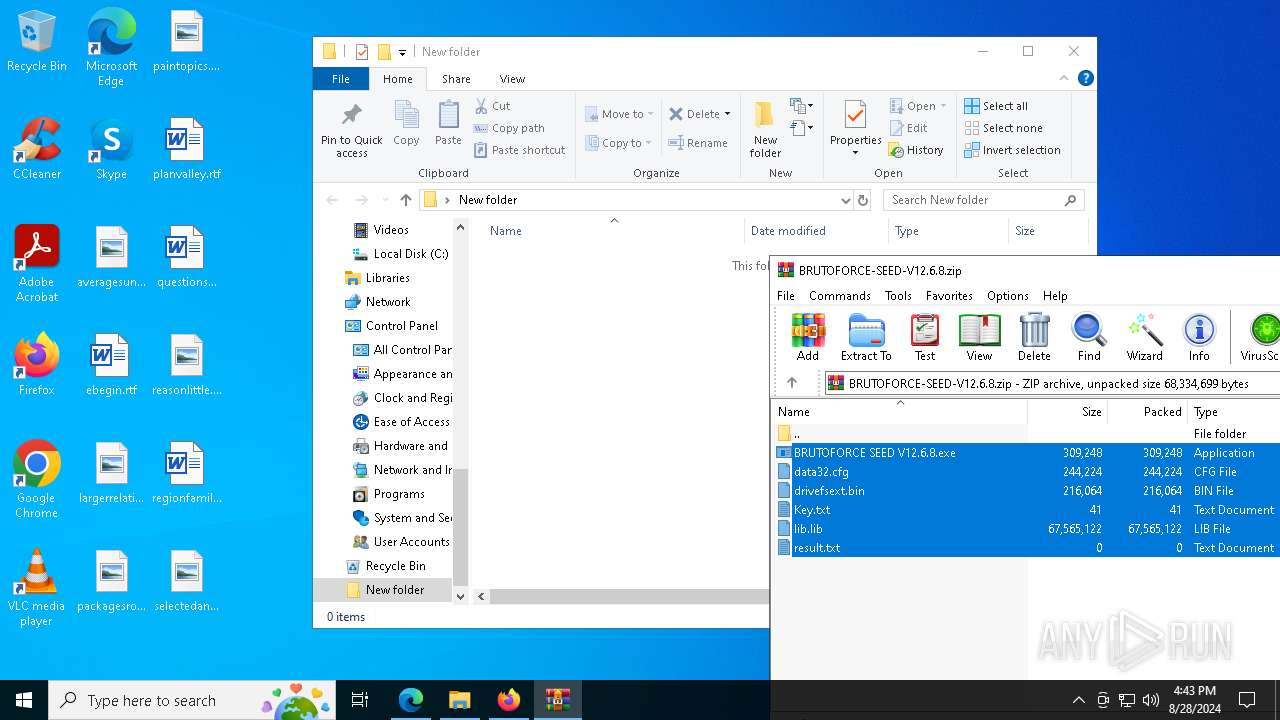
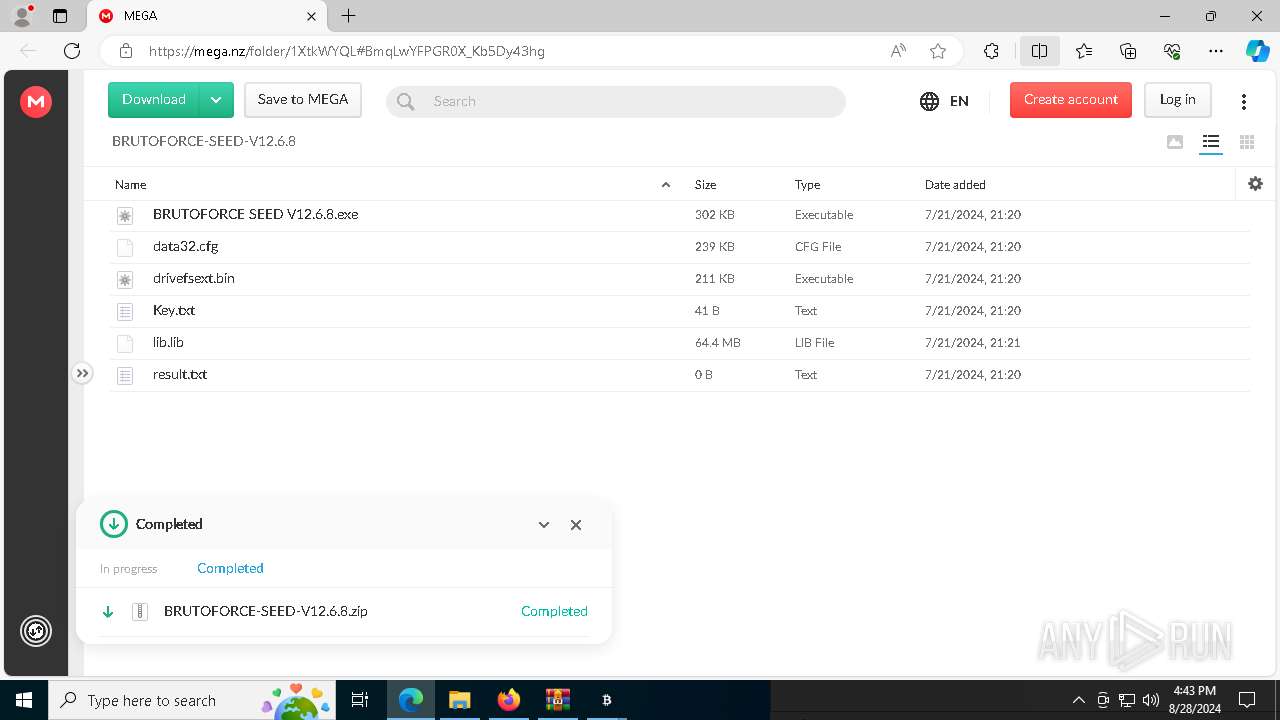
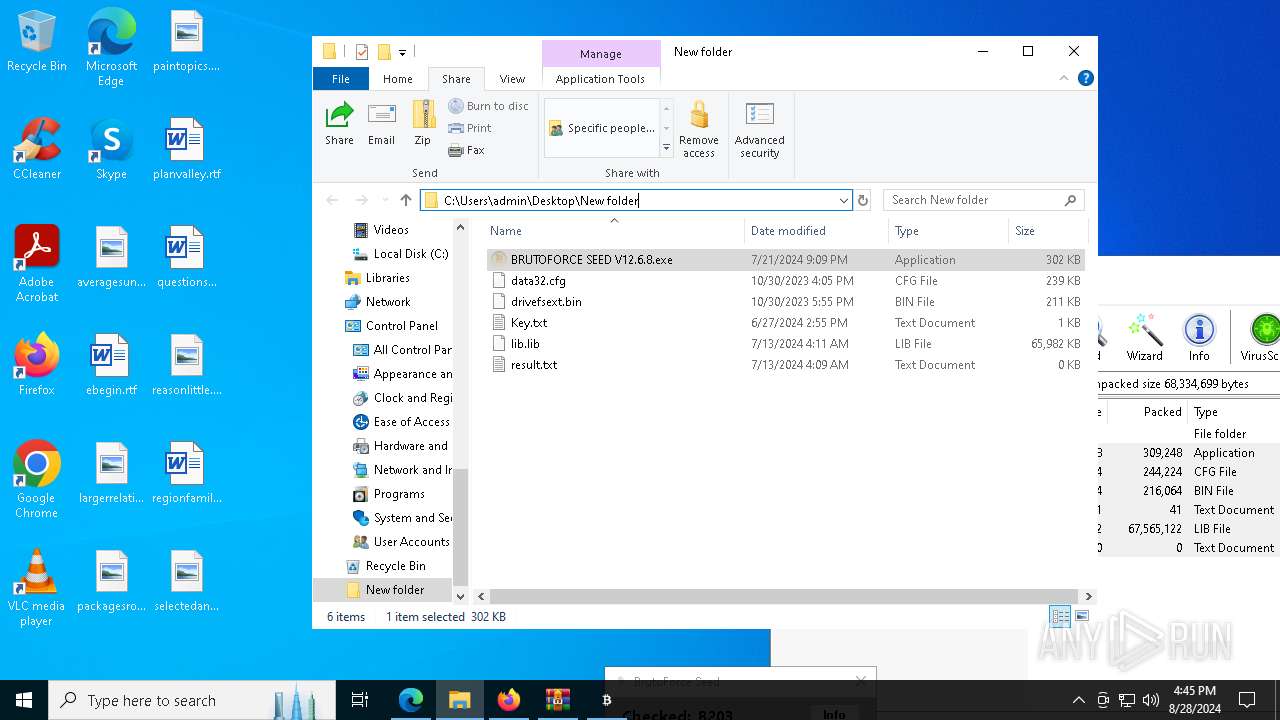
| URL: | https://mega.nz/folder/1XtkWYQL#BmqLwYFPGR0X_Kb5Dy43hg |
| Full analysis: | https://app.any.run/tasks/720ecc2a-fcbf-4993-a0a3-036b4cfb6580 |
| Verdict: | Malicious activity |
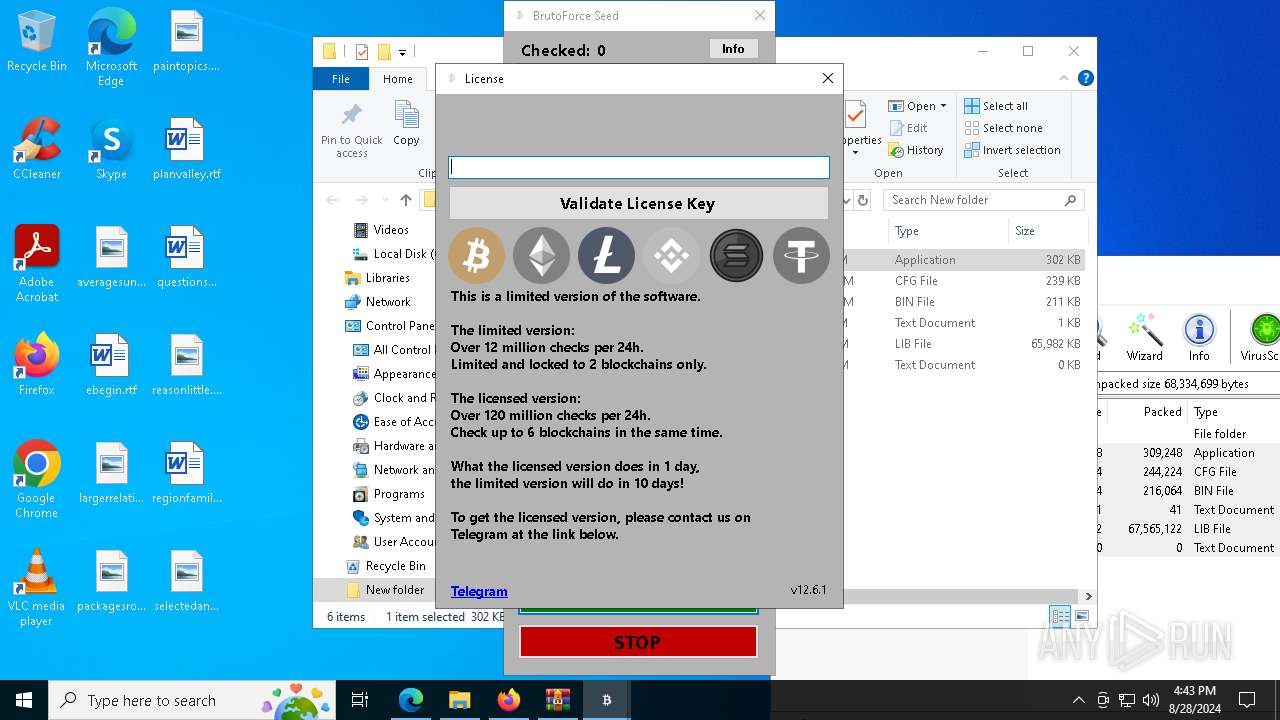
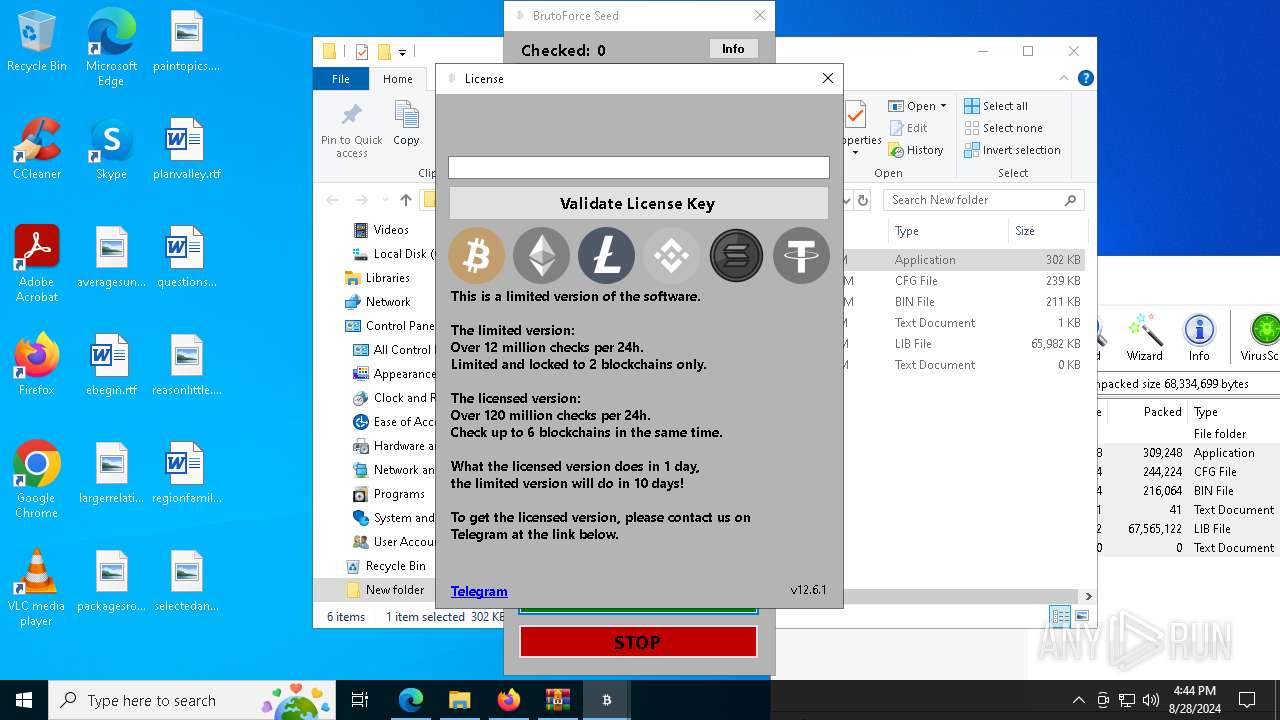
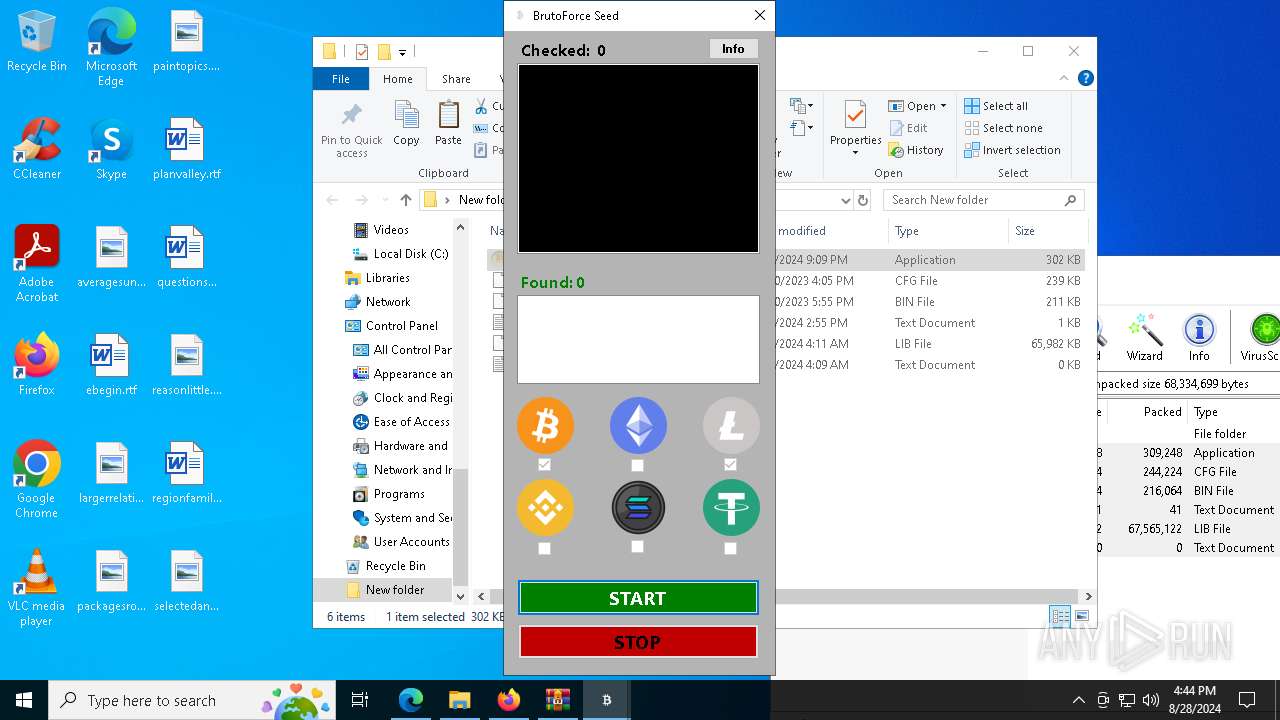
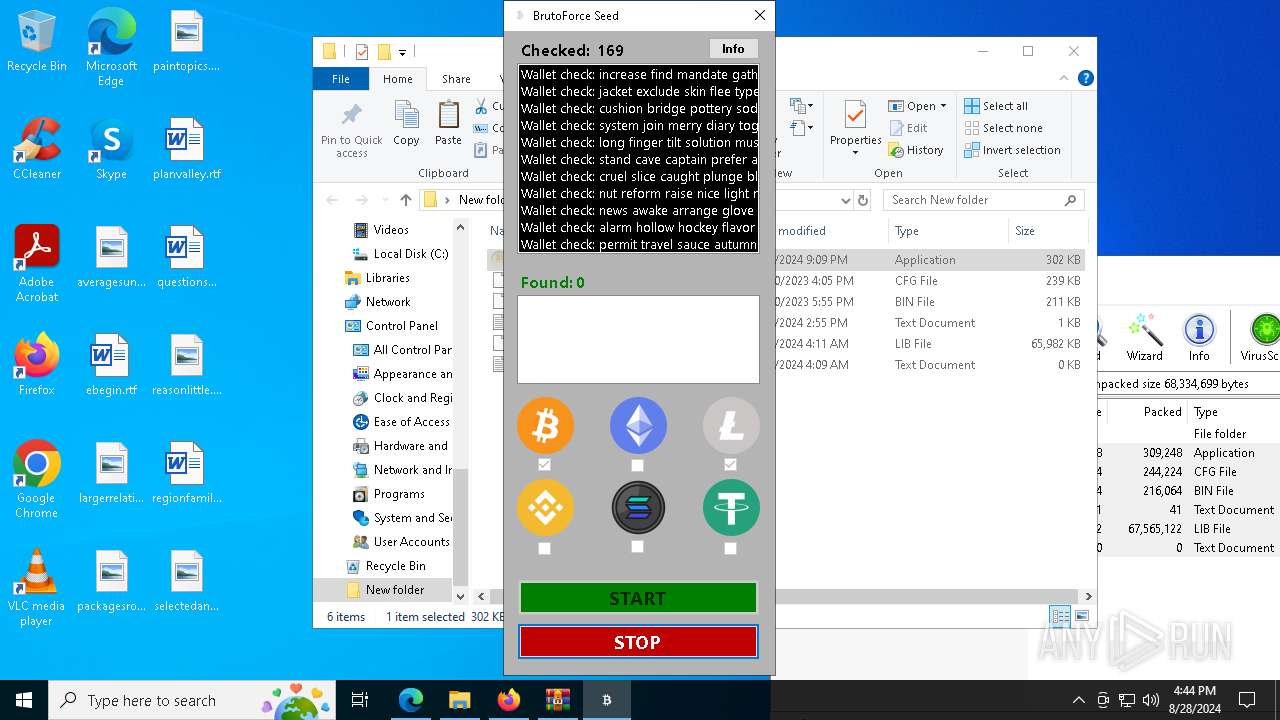
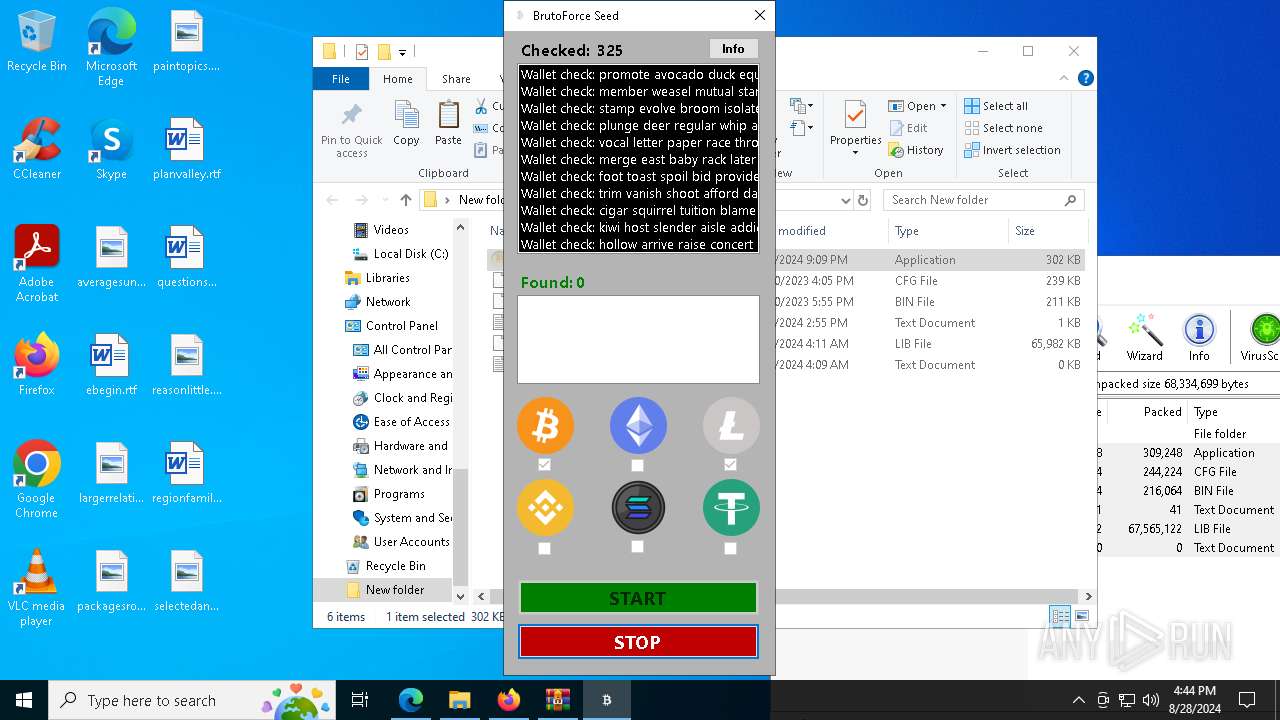
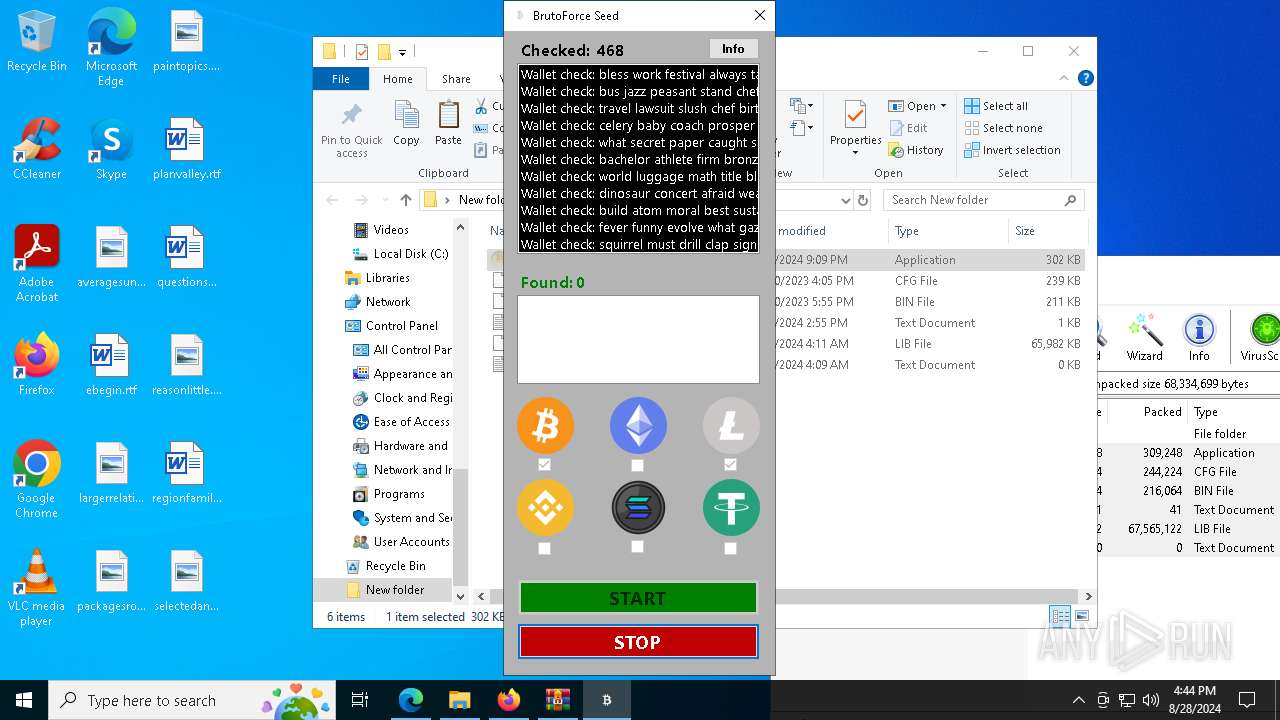
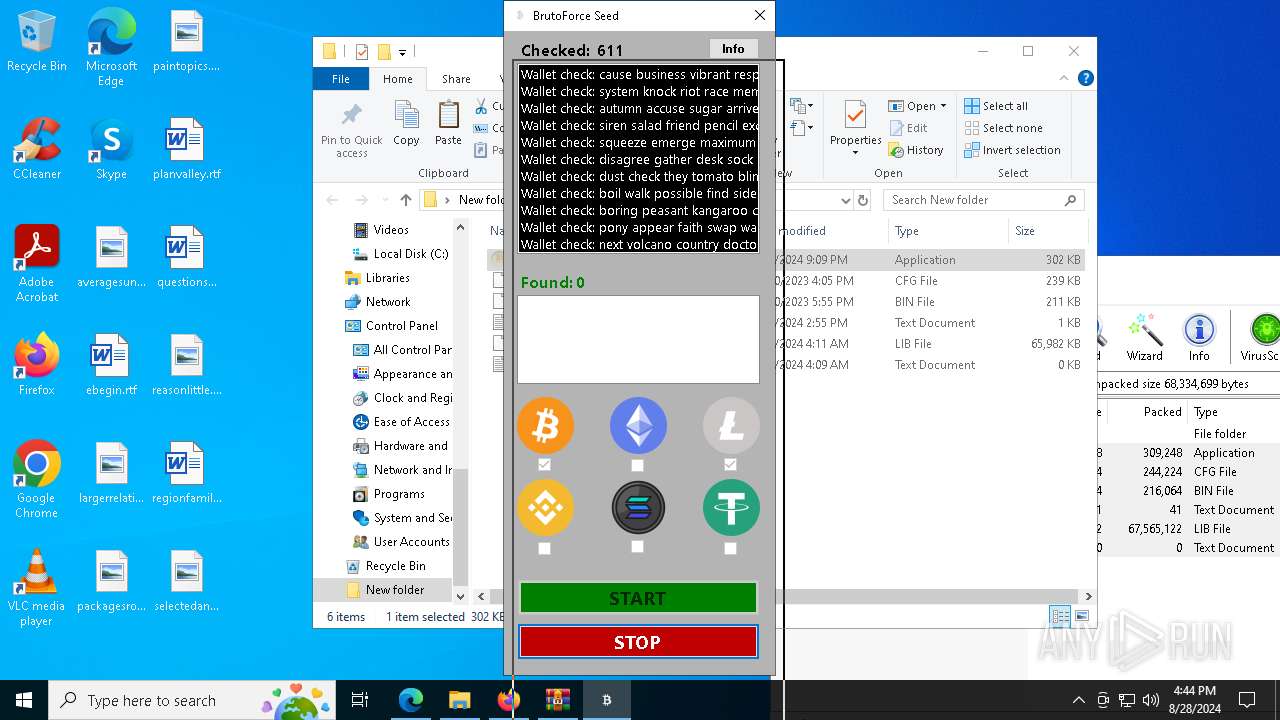
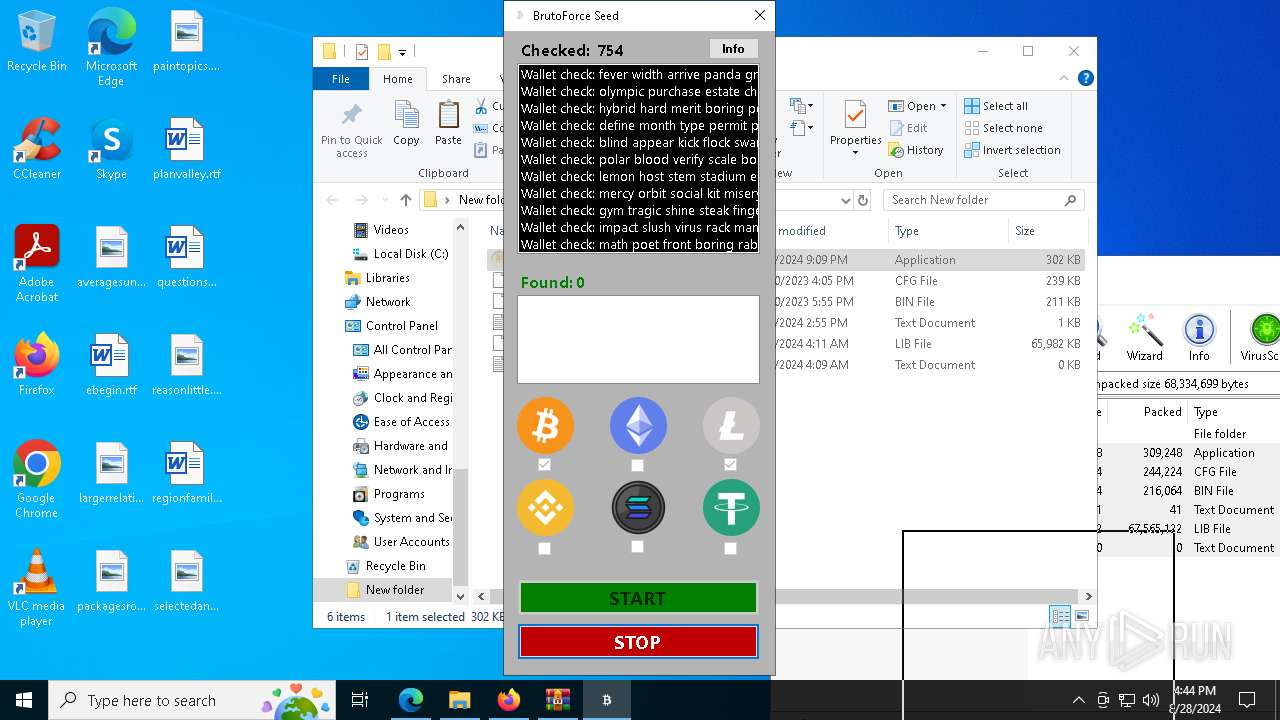
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | August 28, 2024, 16:40:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
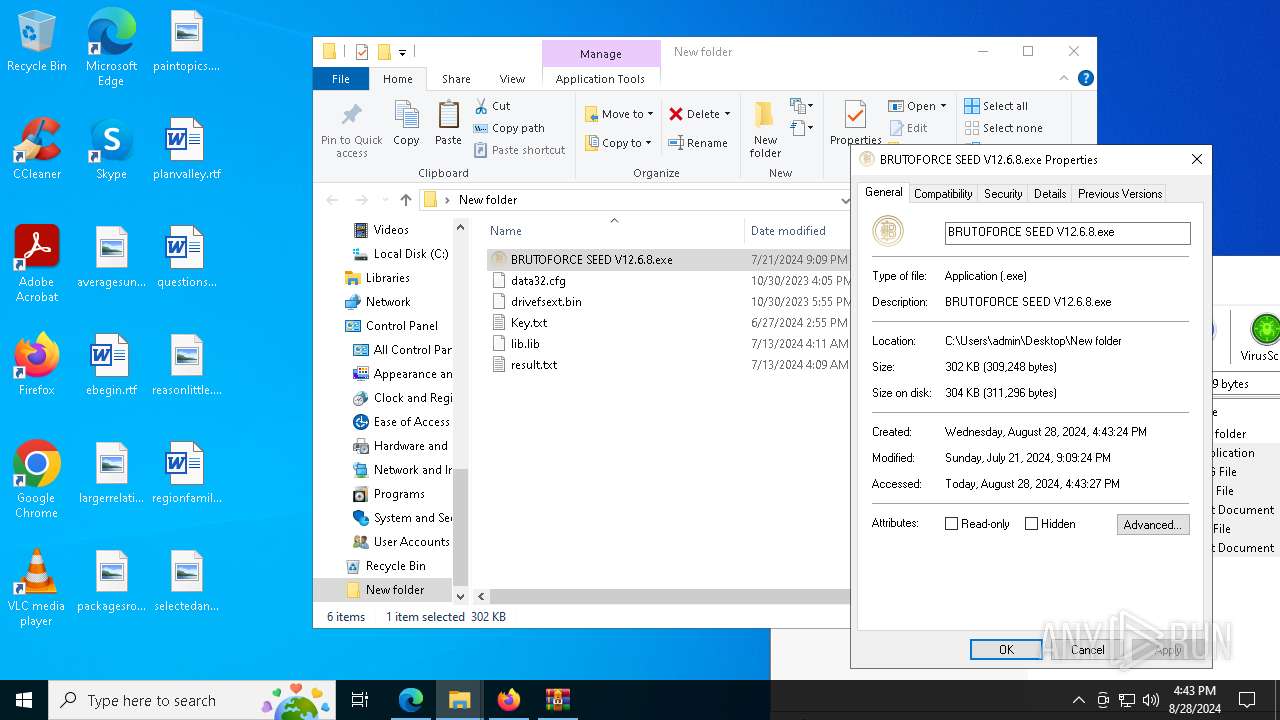
| MD5: | E420D978EEA5033DB5D371270767F74B |
| SHA1: | E96ABC5123E774314EAF7C6A754150D393E1D305 |
| SHA256: | 920ACF057C02BFF6A63BE89A576ADE4B294F819200C113E092DDA22E70ADA4F7 |
| SSDEEP: | 3:N8X/iuyKURlo88juYQP:26PRlr8SY4 |
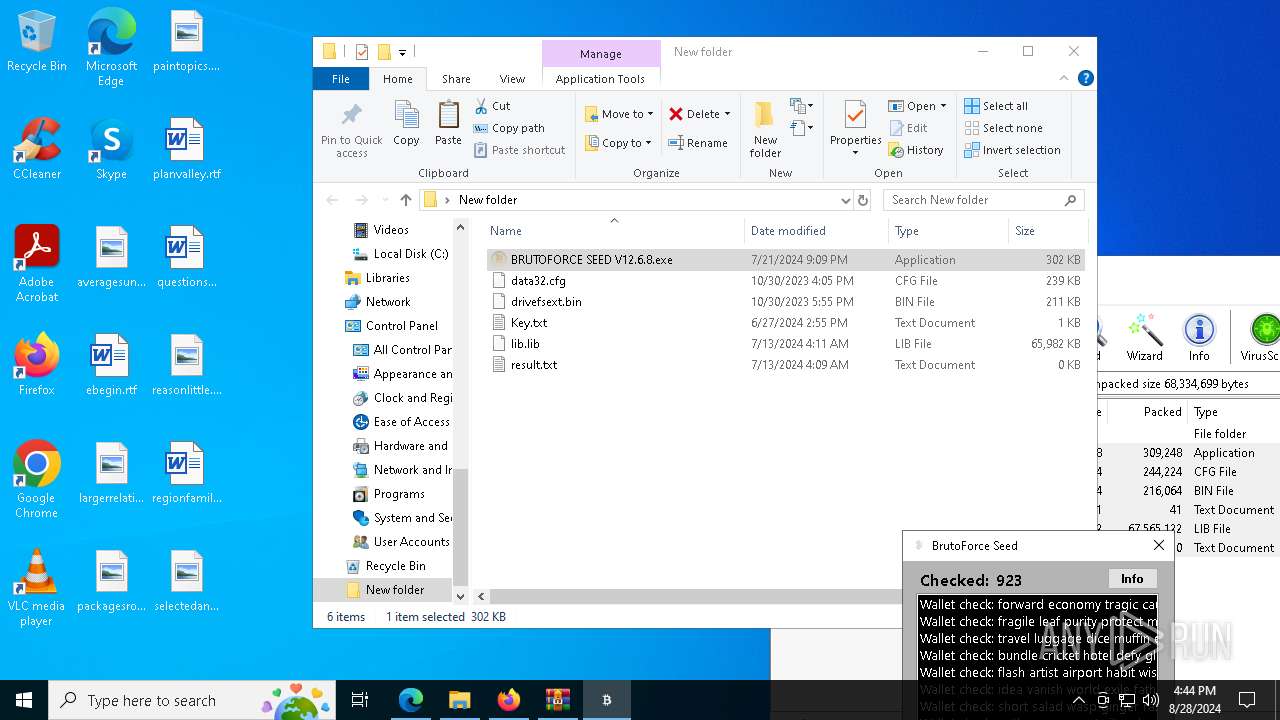
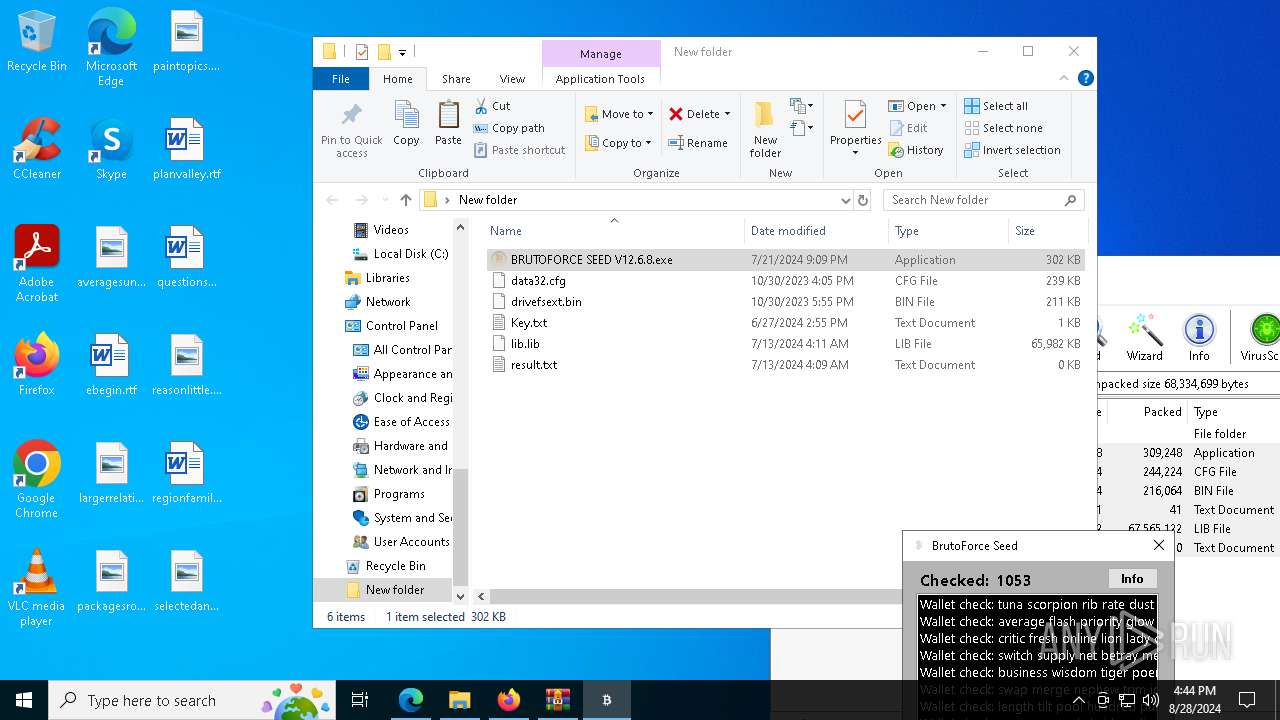
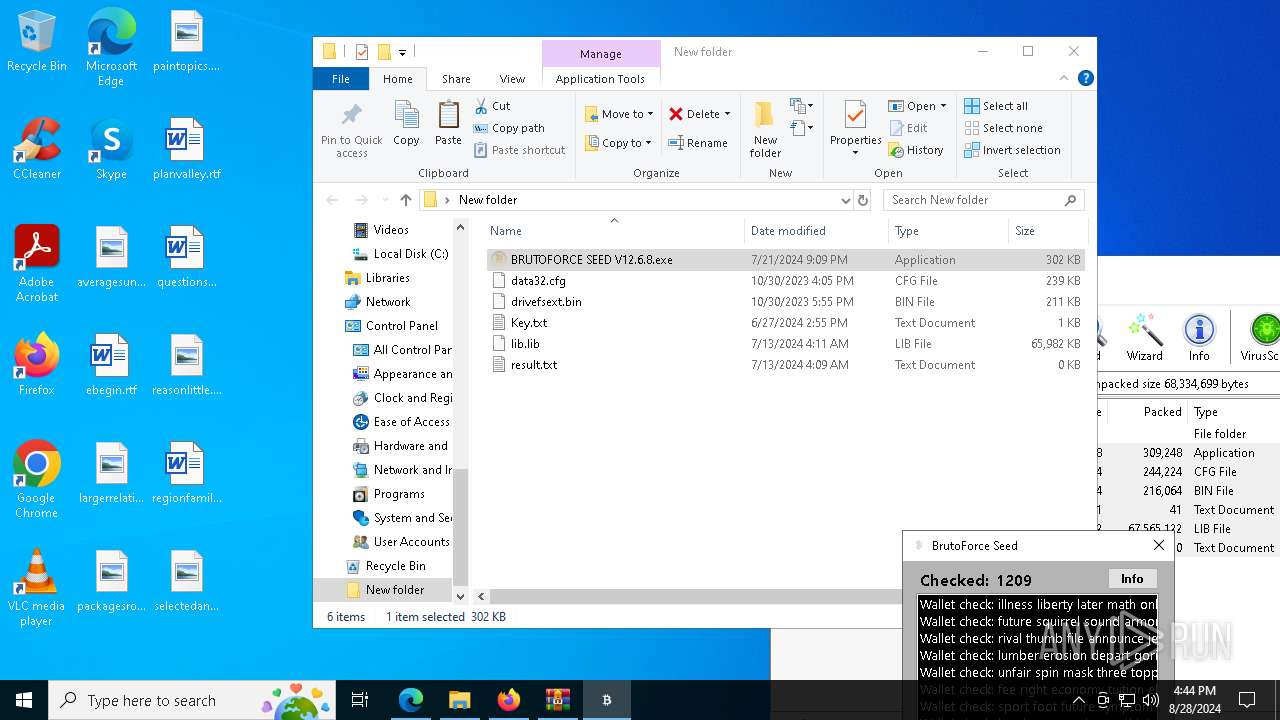
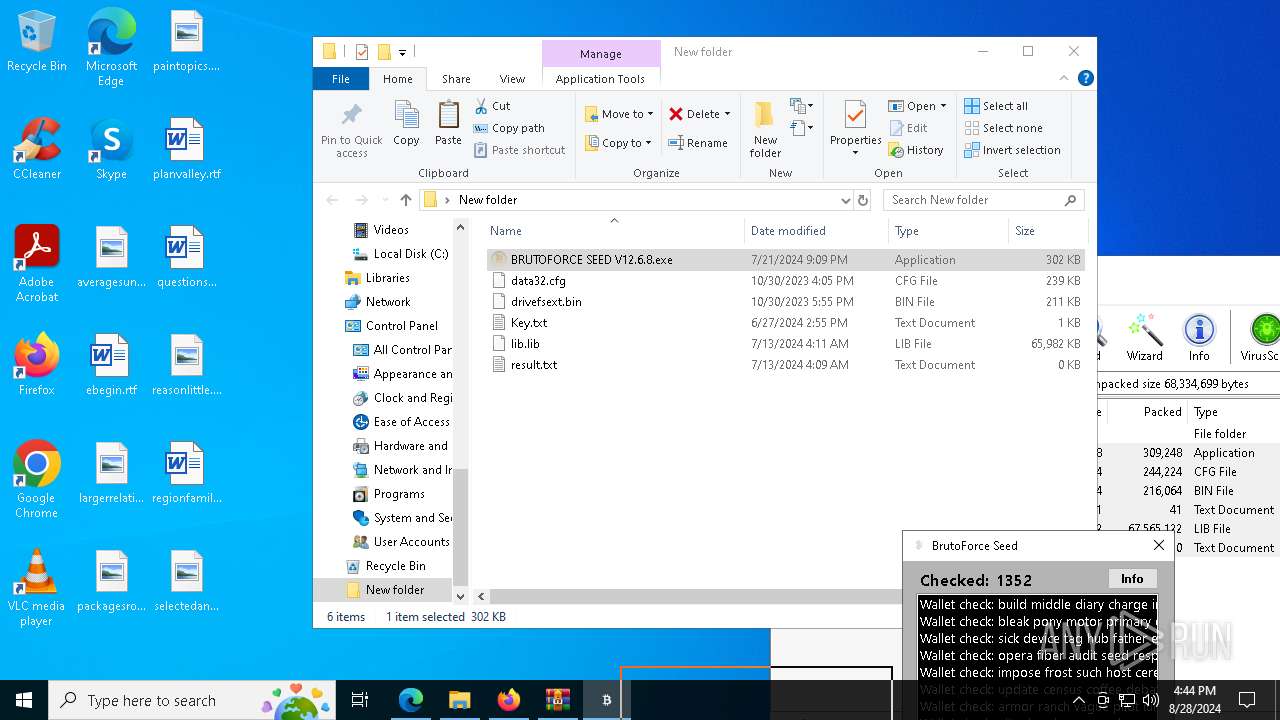
MALICIOUS
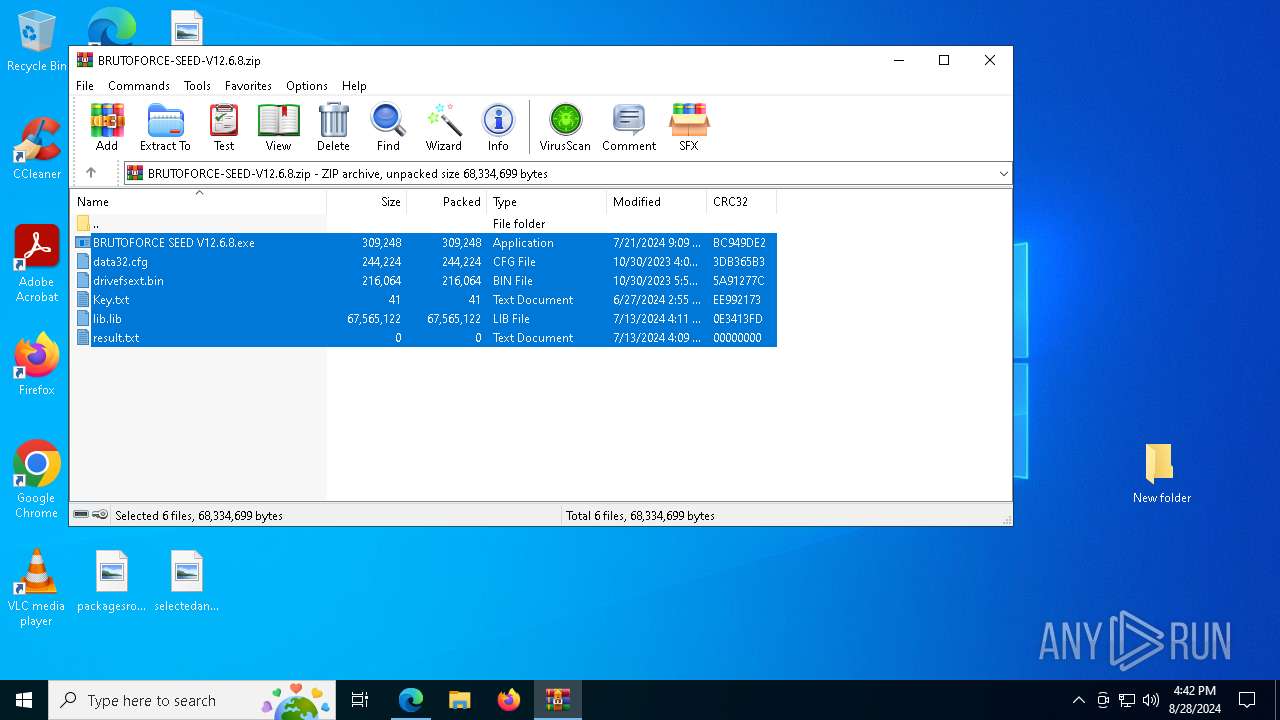
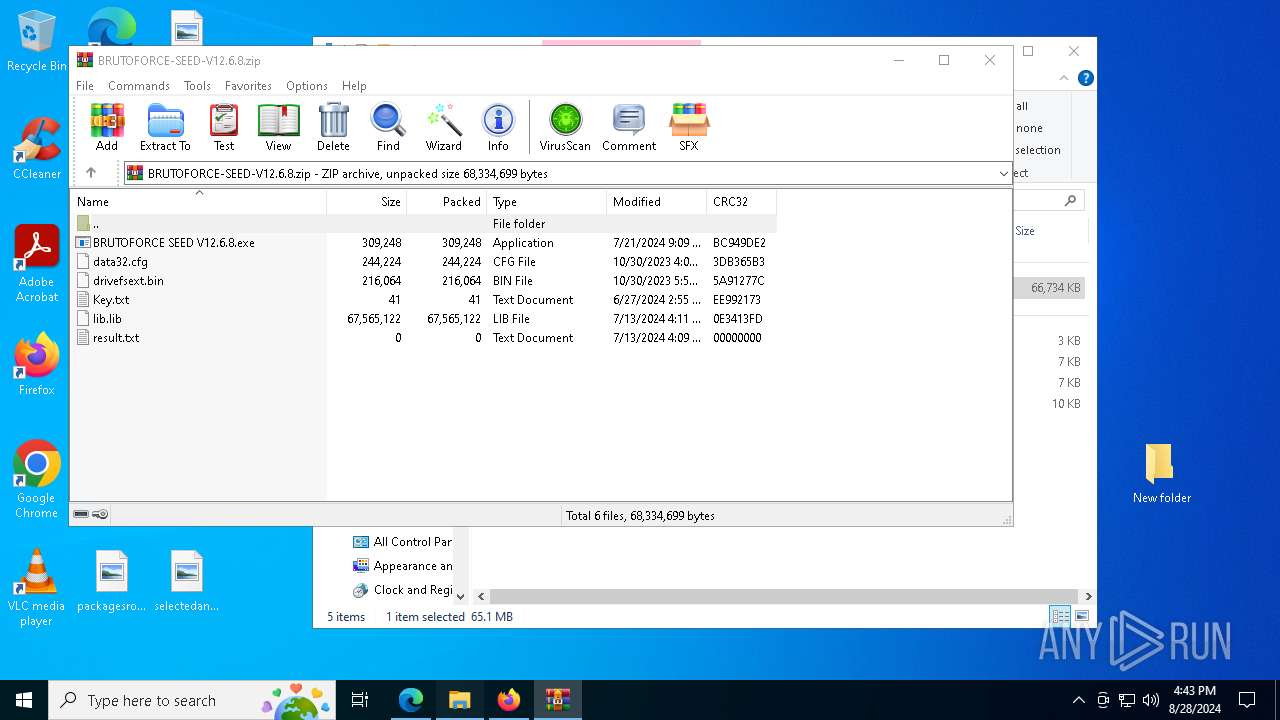
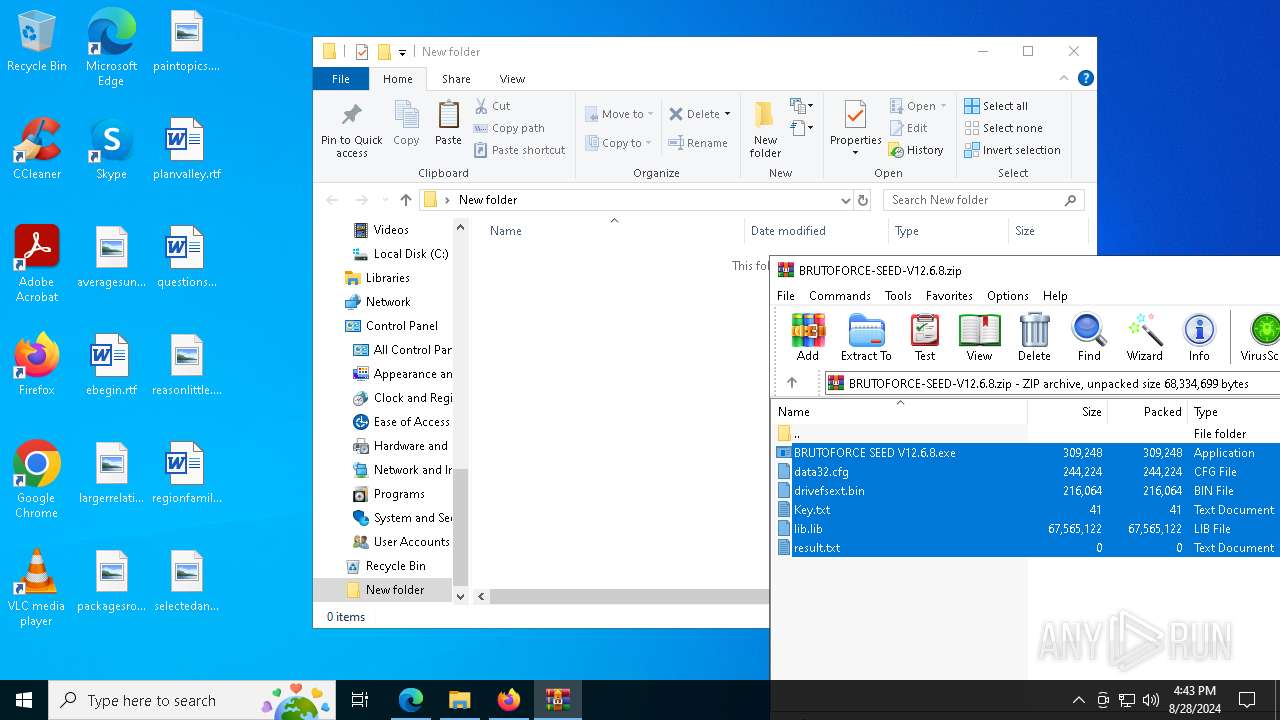
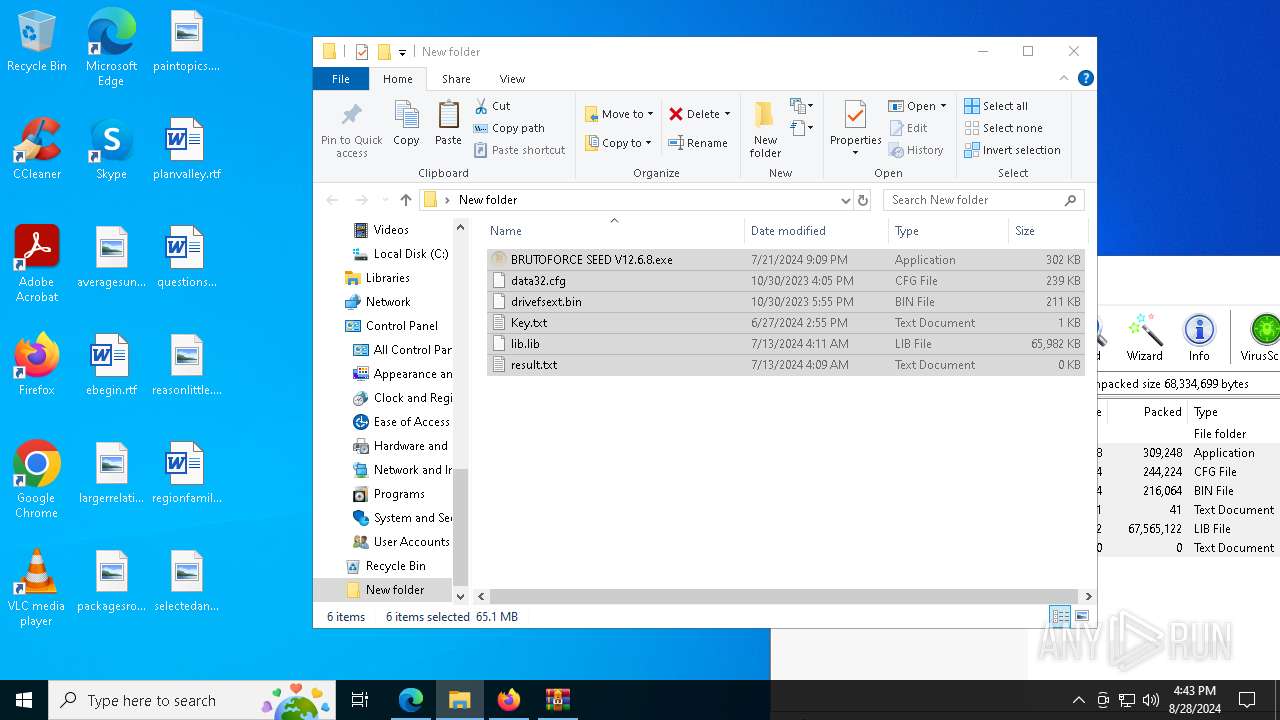
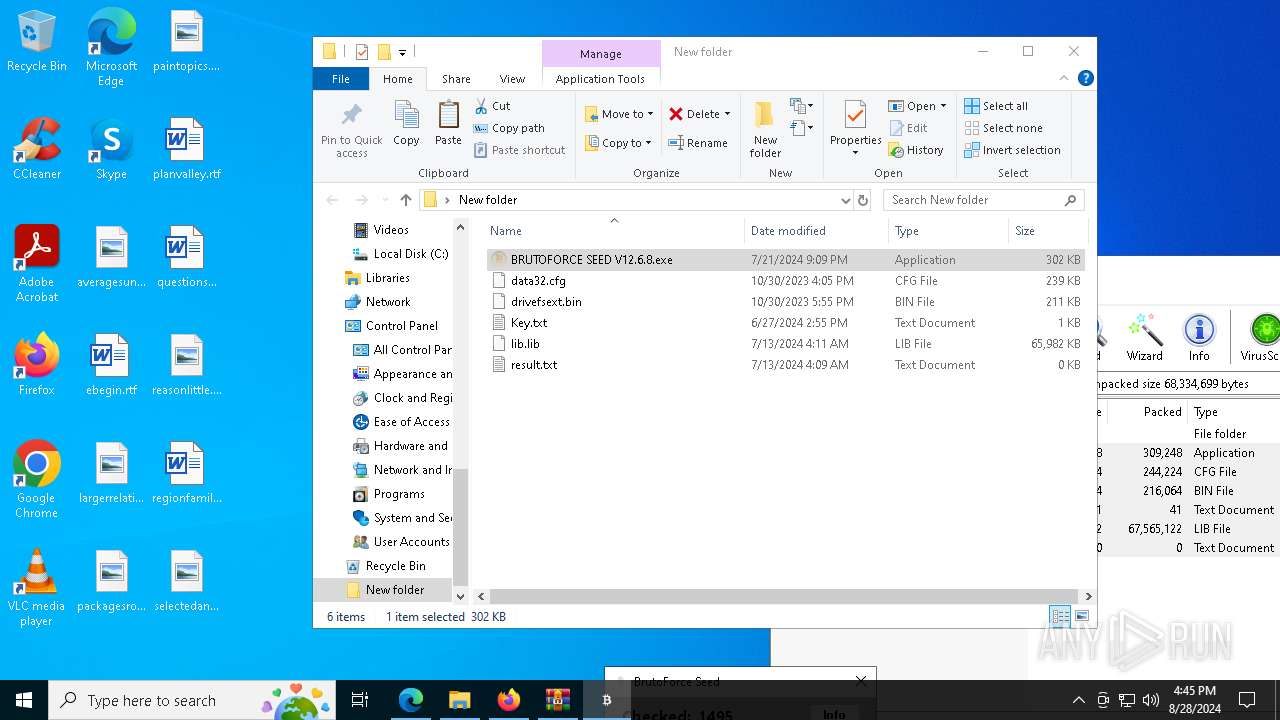
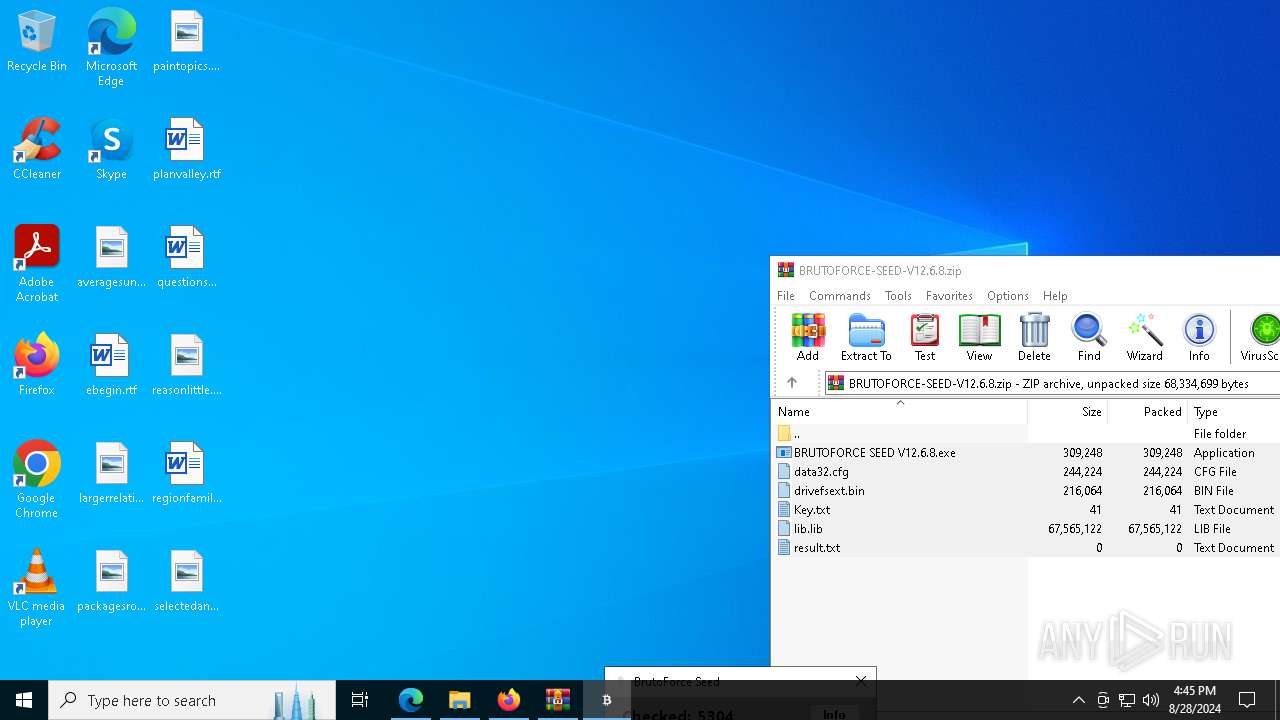
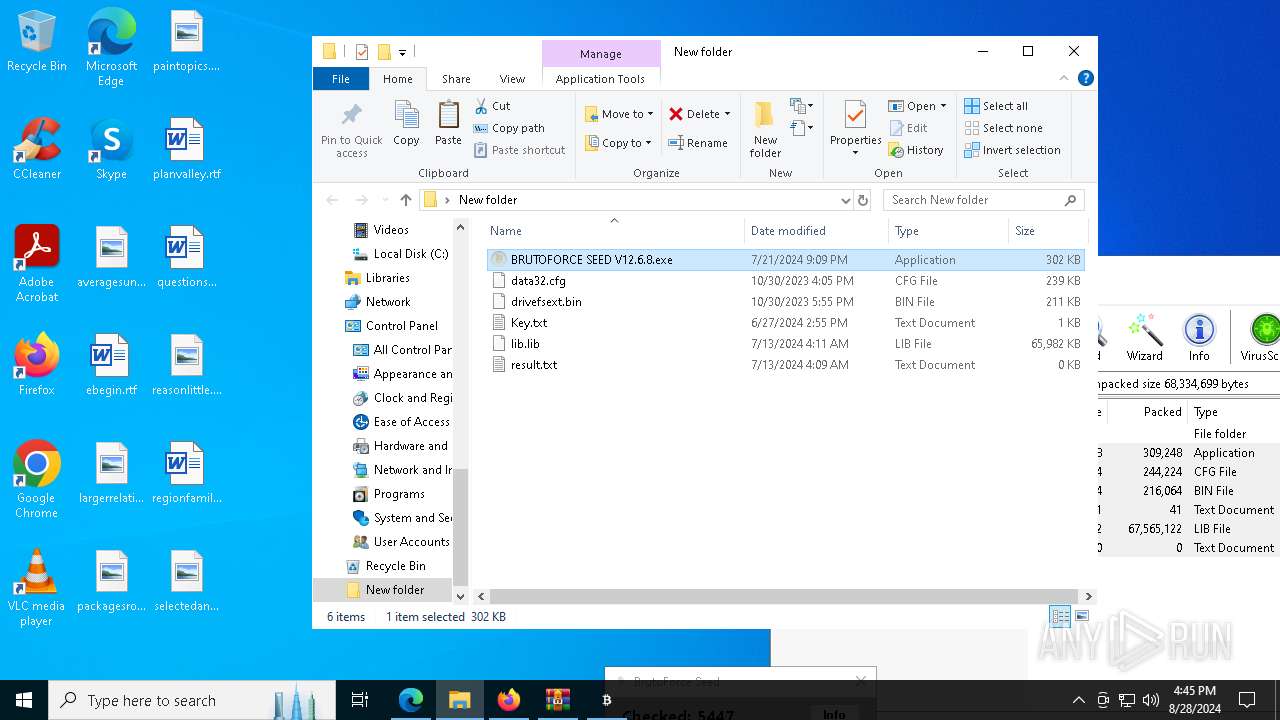
Create files in the Startup directory
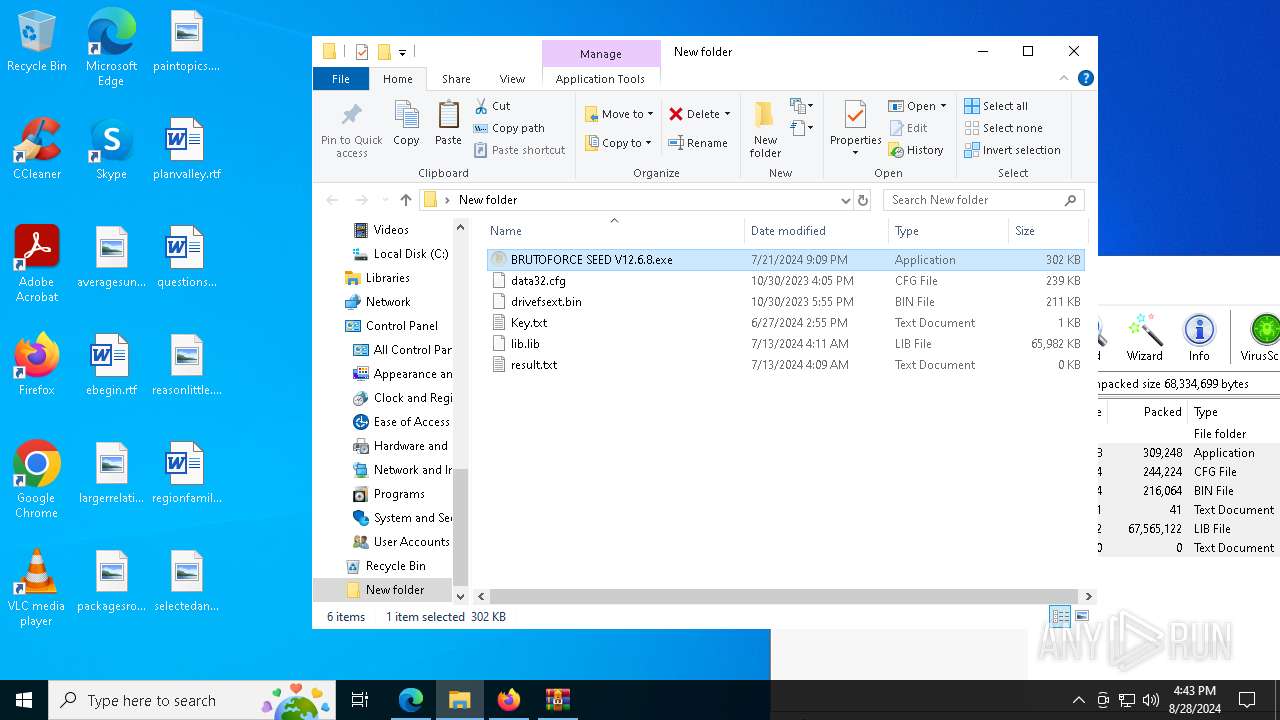
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
SUSPICIOUS
The process creates files with name similar to system file names
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
Executable content was dropped or overwritten
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
- lib.lib (PID: 7892)
Drops the executable file immediately after the start
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
- lib.lib (PID: 7892)
Starts application with an unusual extension
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
Access to an unwanted program domain was detected
- winst.exe (PID: 7916)
Reads the date of Windows installation
- lib.lib (PID: 7892)
Reads security settings of Internet Explorer
- lib.lib (PID: 7892)
- BRUTOFORCE SEED.EXE (PID: 3652)
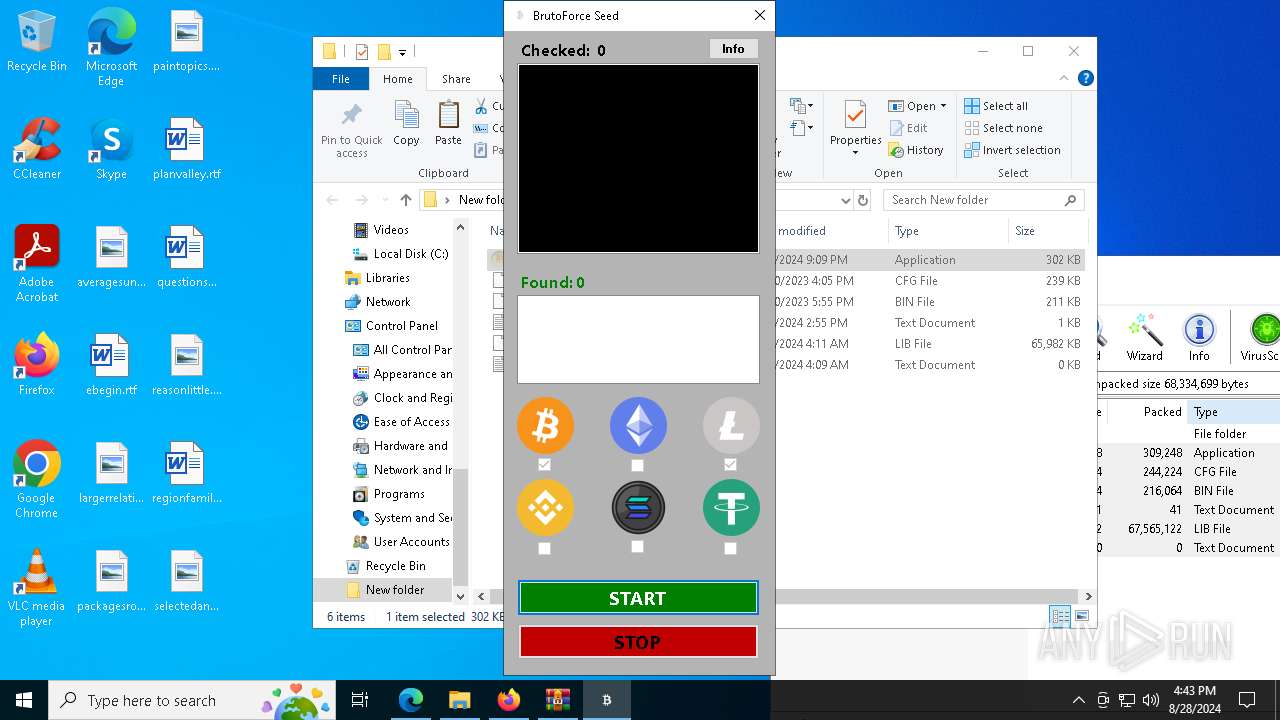
Found regular expressions for crypto-addresses (YARA)
- vshost.exe (PID: 3352)
Reads Internet Explorer settings
- BRUTOFORCE SEED.EXE (PID: 3652)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 3660)
- firefox.exe (PID: 2508)
- BRUTOFORCE SEED.EXE (PID: 3652)
Reads the computer name
- identity_helper.exe (PID: 5044)
- winst.exe (PID: 7916)
- lib.lib (PID: 7892)
- BRUTOFORCE SEED.EXE (PID: 3652)
Manual execution by a user
- firefox.exe (PID: 2148)
- WinRAR.exe (PID: 7984)
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
Checks supported languages
- identity_helper.exe (PID: 5044)
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
- lib.lib (PID: 7892)
- winst.exe (PID: 7916)
- BRUTOFORCE SEED.EXE (PID: 3652)
- vshost.exe (PID: 3352)
Application launched itself
- firefox.exe (PID: 2148)
- firefox.exe (PID: 2508)
- msedge.exe (PID: 3660)
Reads Environment values
- identity_helper.exe (PID: 5044)
Reads the software policy settings
- slui.exe (PID: 7784)
- slui.exe (PID: 3208)
- winst.exe (PID: 7916)
Creates files or folders in the user directory
- BRUTOFORCE SEED V12.6.8.exe (PID: 6104)
Checks proxy server information
- slui.exe (PID: 3208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7984)
Create files in a temporary directory
- lib.lib (PID: 7892)
- BRUTOFORCE SEED.EXE (PID: 3652)
Process checks computer location settings
- lib.lib (PID: 7892)
Creates files in the program directory
- BRUTOFORCE SEED.EXE (PID: 3652)
Attempting to use instant messaging service
- msedge.exe (PID: 5092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
204
Monitored processes
70
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5496 --field-trial-handle=2340,i,16376824385261717178,16272616985479104077,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 236 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5944 --field-trial-handle=2340,i,16376824385261717178,16272616985479104077,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 940 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=7588 --field-trial-handle=2340,i,16376824385261717178,16272616985479104077,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1924 -parentBuildID 20240213221259 -prefsHandle 1856 -prefMapHandle 1848 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {3a795ad7-4053-4bbb-a02e-38474e0ac813} 2508 "\\.\pipe\gecko-crash-server-pipe.2508" 12fae4e6010 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5620 -childID 4 -isForBrowser -prefsHandle 5564 -prefMapHandle 5560 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f8ee8049-e4c7-420d-b5b1-76d53aa1da95} 2508 "\\.\pipe\gecko-crash-server-pipe.2508" 12fb603bbd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2292 -parentBuildID 20240213221259 -prefsHandle 2284 -prefMapHandle 2280 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {431ef370-e912-4363-bcf8-87c3fac5b199} 2508 "\\.\pipe\gecko-crash-server-pipe.2508" 12fa1a80510 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1436 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=5492 --field-trial-handle=2340,i,16376824385261717178,16272616985479104077,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4660 -childID 2 -isForBrowser -prefsHandle 4656 -prefMapHandle 4652 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1536376d-5e12-464e-82d8-78908fa53f82} 2508 "\\.\pipe\gecko-crash-server-pipe.2508" 12fb5649850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
40 945
Read events
40 703
Write events
234
Delete events
8
Modification events
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 585145519 | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31127913 | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3036) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
8
Suspicious files
452
Text files
170
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12a967.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12a977.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12a986.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12a9d5.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF12a9e4.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
205
DNS requests
200
Threats
51
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8048 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
8048 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/39120fc9-de56-4074-ab8a-7c851c15af3c?P1=1725440022&P2=404&P3=2&P4=eNZ9WQ8KFOcKYWyfy6Xe5sXSU%2fiTpa5P2zf0LfFjxfPjpkSEyHVFSw%2f%2btgidOK7WQu%2fXExf7UoCaPTxIgPQOOg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4316 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6268 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3660 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 31.216.145.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | whitelisted |
— | — | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
mega.nz |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
— | — | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
4 ETPRO signatures available at the full report