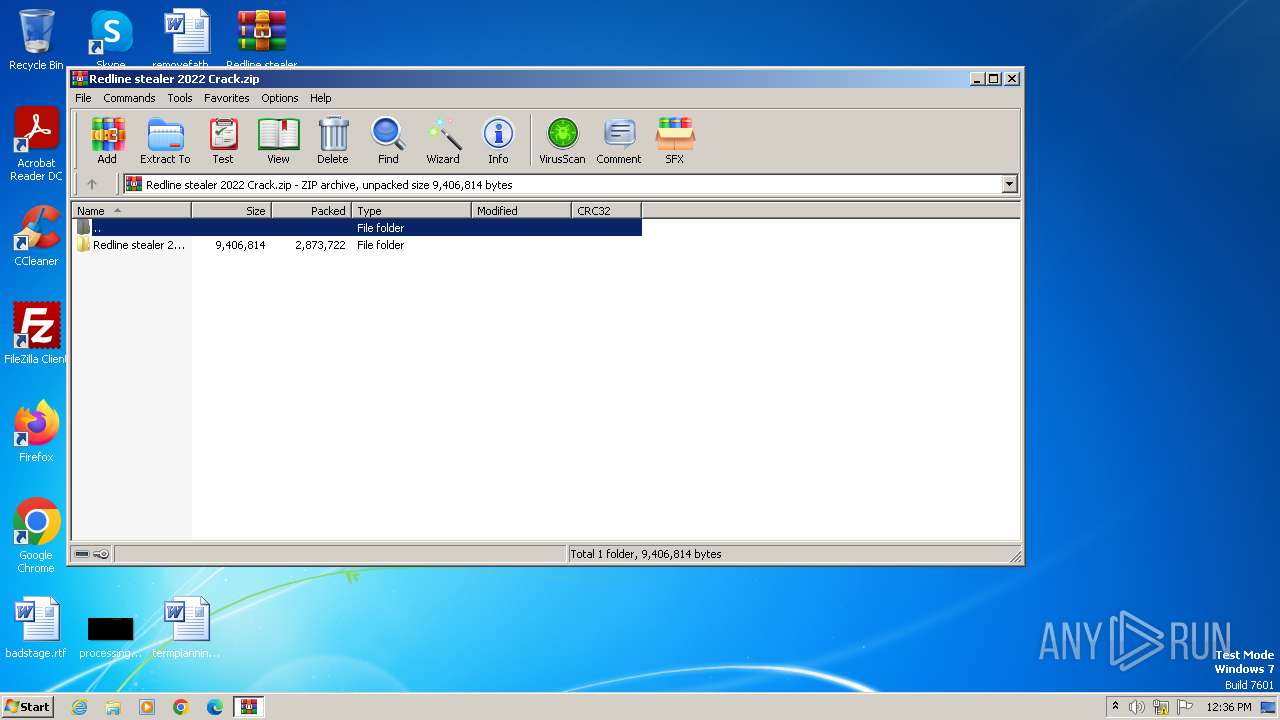
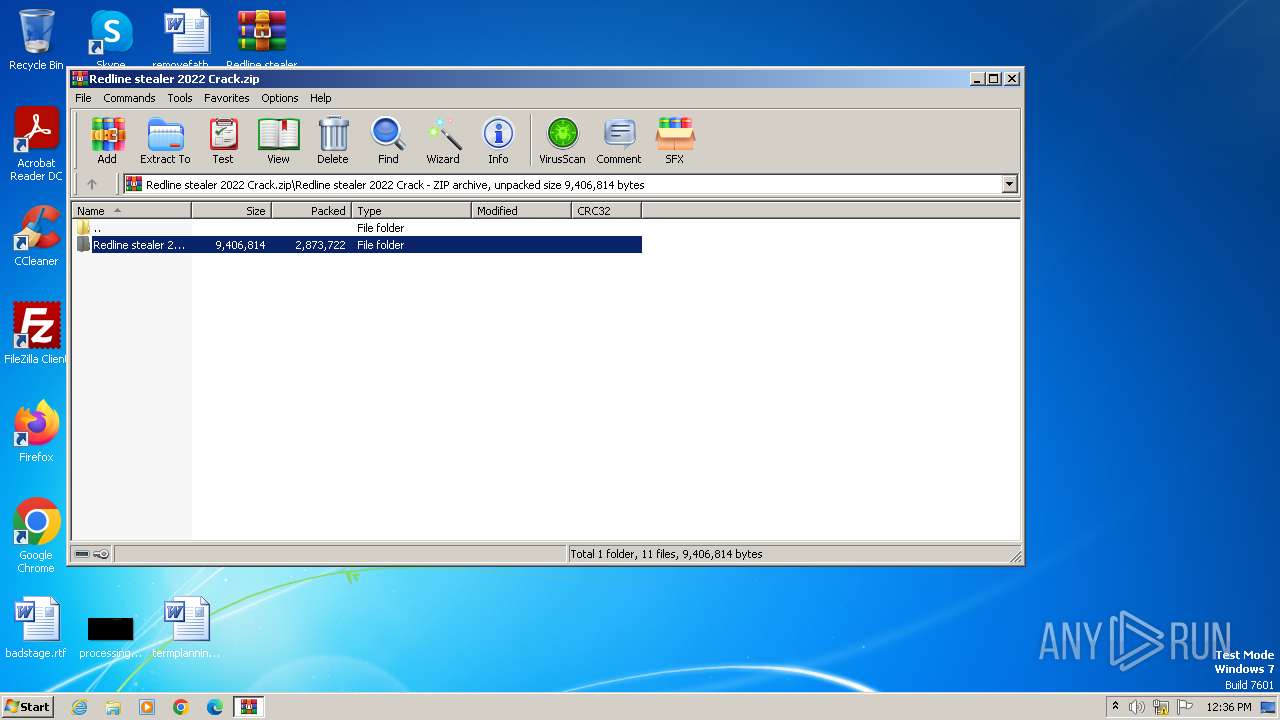
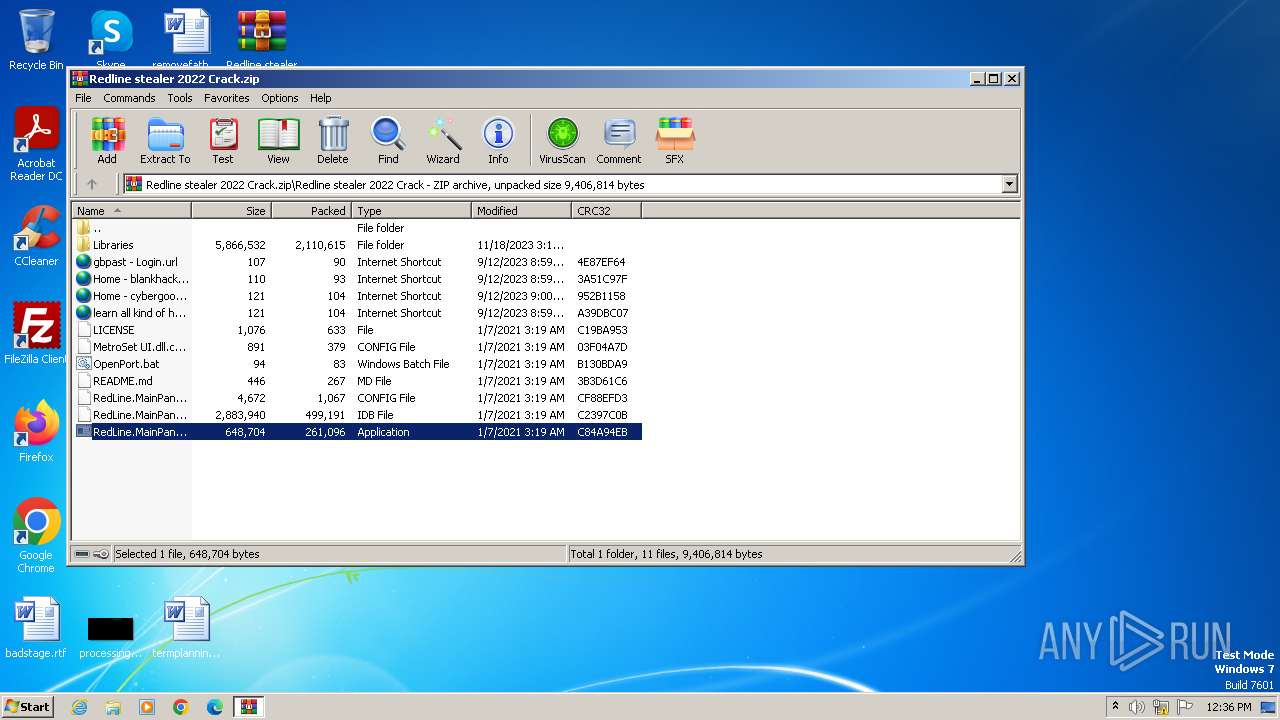
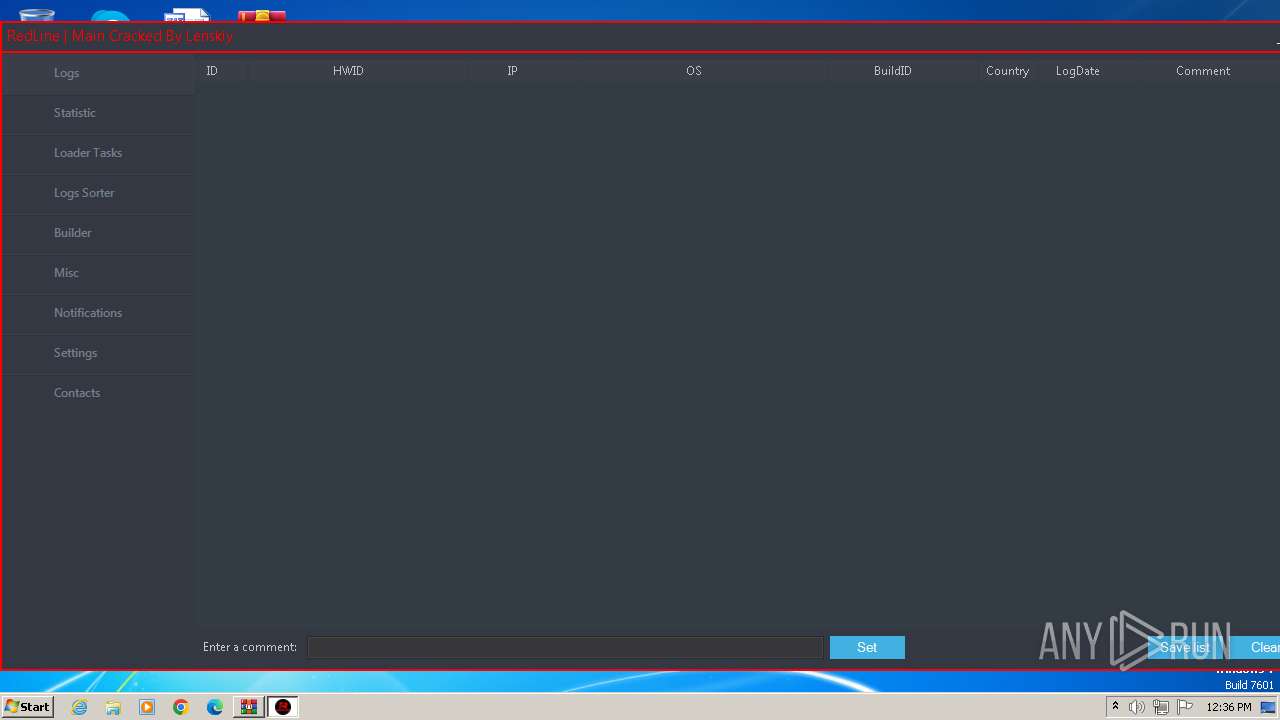
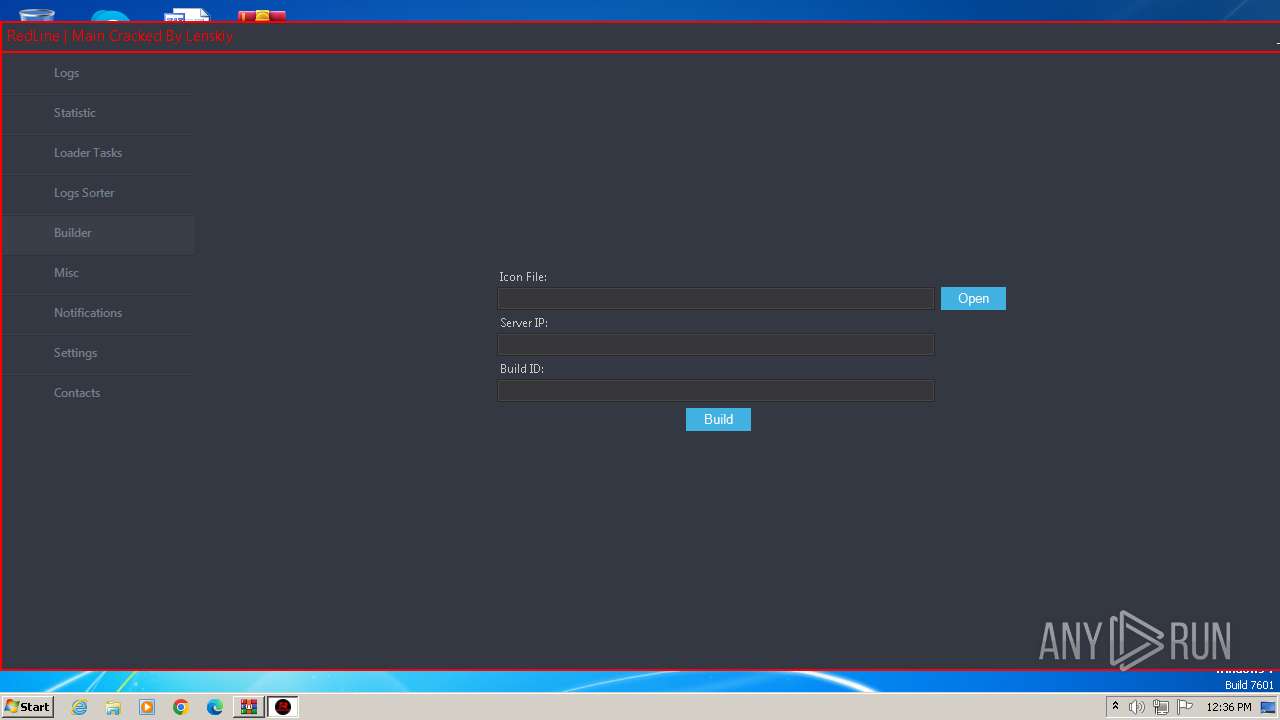
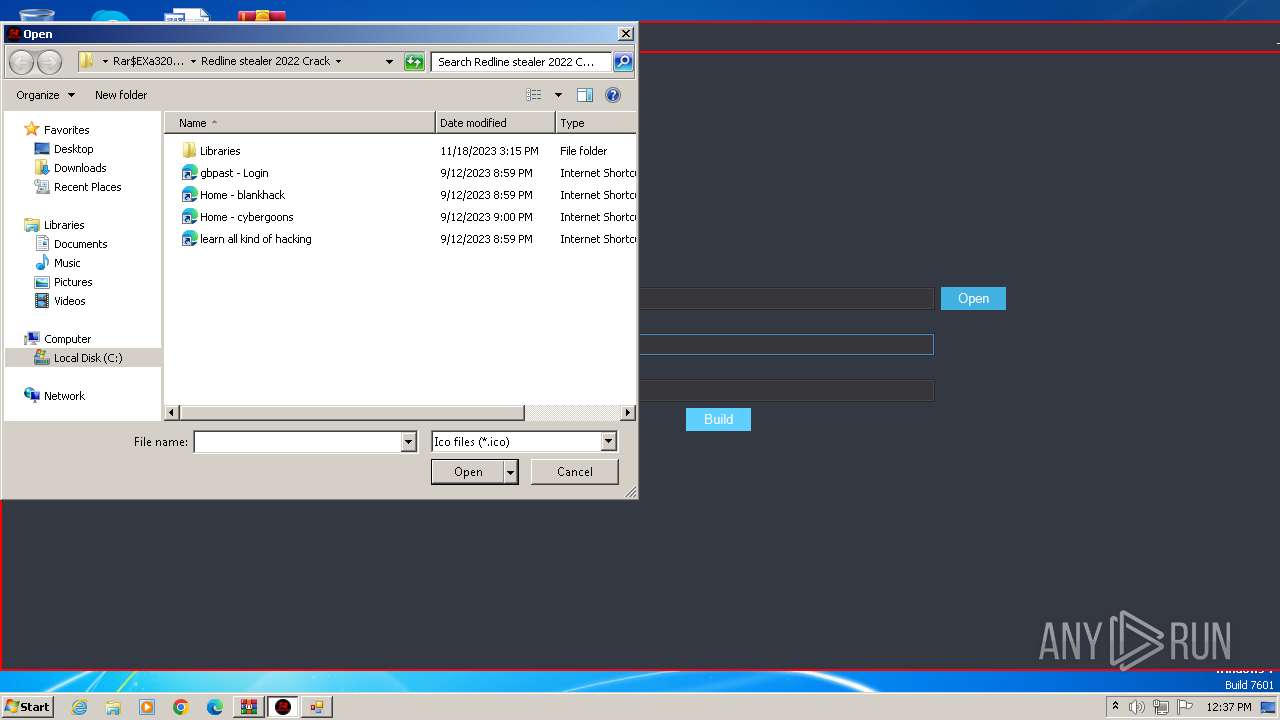
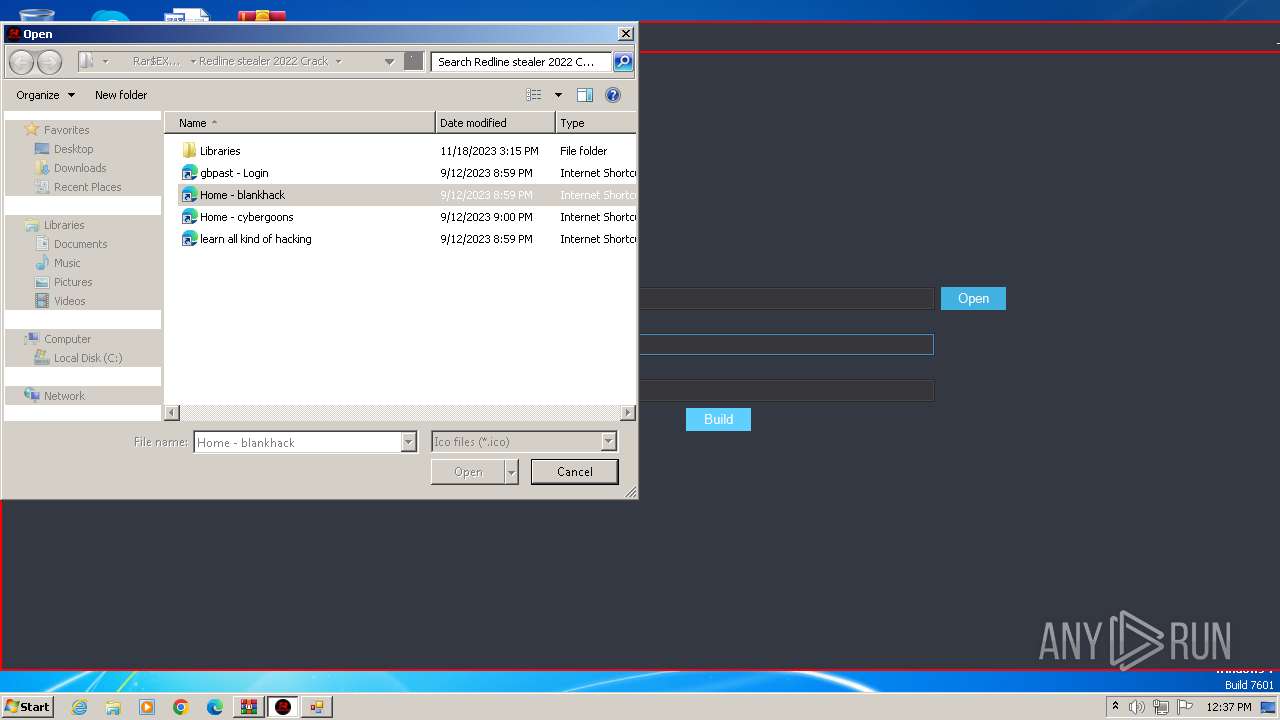
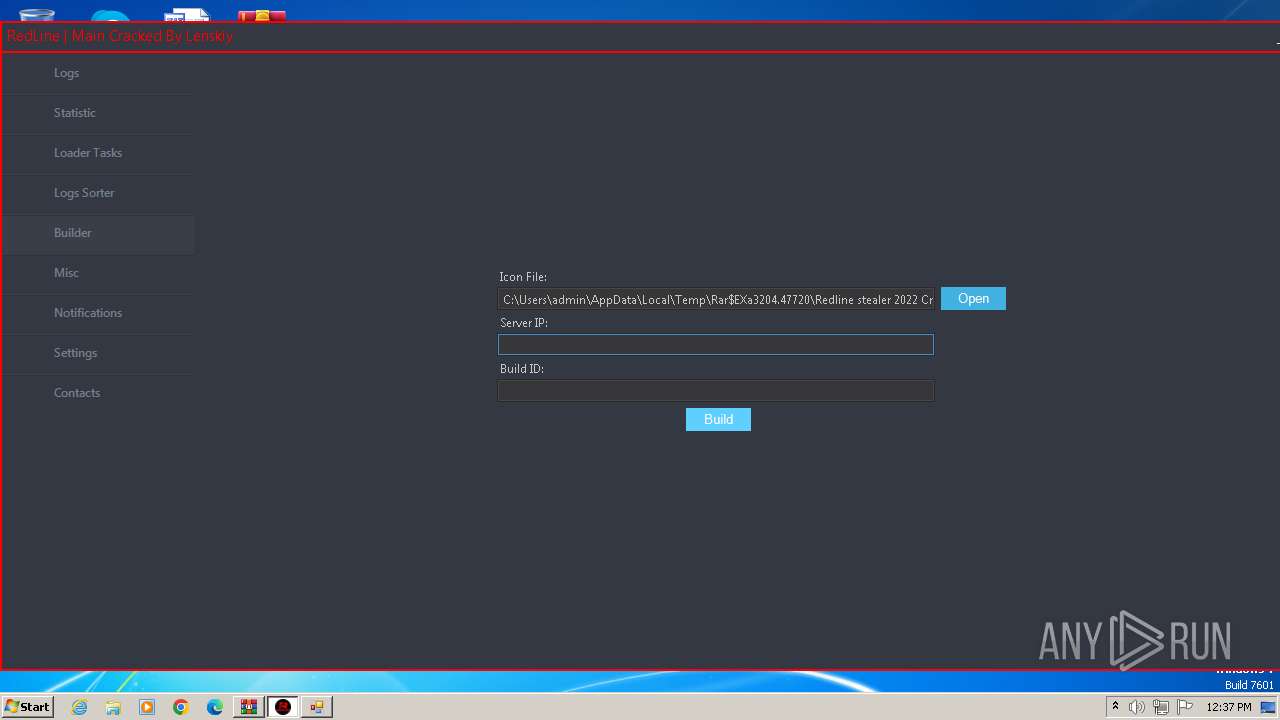
| File name: | Redline stealer 2022 Crack.zip |
| Full analysis: | https://app.any.run/tasks/bab428ab-9c27-4304-9c48-10006d9bdea6 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | November 23, 2023, 12:36:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9F2B4AFA22391D606B3577CB8DFAC6FE |
| SHA1: | 51F3E0D2CF684B8246F500534929706D61B6B842 |
| SHA256: | 91FDDF7CDF9462984D929296EB1F0ADD771532117E921EF85272FC12BC796C9E |
| SSDEEP: | 98304:w+T6a7NCbD+Zr3of0LNhXvJIXrAFqHnpsezuW33p4dfx+MkuVV84mzmP76Yf2nZz:QqHRRvkP |
MALICIOUS
REDLINE has been detected (YARA)
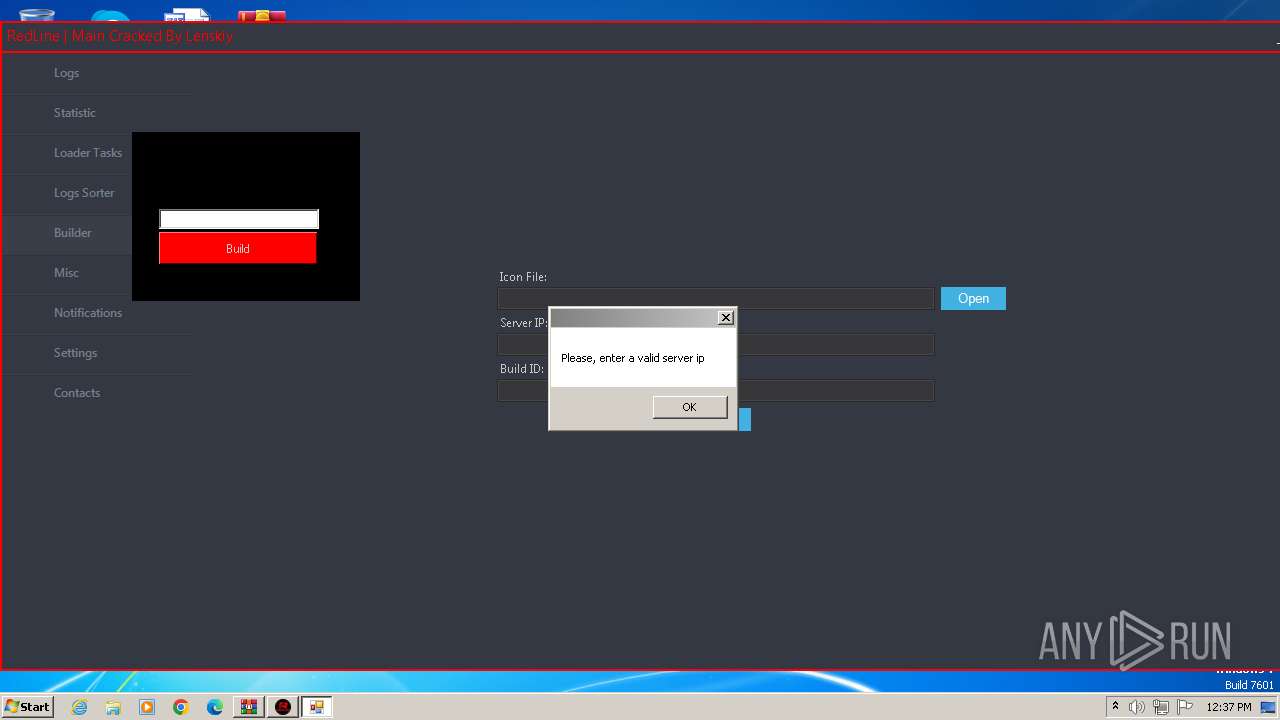
- RedLine.MainPanel-cracked.exe (PID: 3468)
SUSPICIOUS
Reads the Internet Settings
- RedLine.MainPanel-cracked.exe (PID: 3468)
INFO
Reads the machine GUID from the registry
- RedLine.MainPanel-cracked.exe (PID: 3468)
- wmpnscfg.exe (PID: 3576)
Checks supported languages
- RedLine.MainPanel-cracked.exe (PID: 3468)
- wmpnscfg.exe (PID: 3576)
- builder.exe (PID: 3660)
Reads the computer name
- RedLine.MainPanel-cracked.exe (PID: 3468)
- wmpnscfg.exe (PID: 3576)
- builder.exe (PID: 3660)
Manual execution by a user
- wmpnscfg.exe (PID: 3576)
Reads Environment values
- RedLine.MainPanel-cracked.exe (PID: 3468)
Checks proxy server information
- RedLine.MainPanel-cracked.exe (PID: 3468)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:09:12 20:59:58 |
| ZipCRC: | 0x4e87ef64 |
| ZipCompressedSize: | 90 |
| ZipUncompressedSize: | 107 |
| ZipFileName: | Redline stealer 2022 Crack/gbpast - Login.url |
Total processes
44
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3204 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Redline stealer 2022 Crack.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3468 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\RedLine.MainPanel-cracked.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\RedLine.MainPanel-cracked.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RedLinePanel Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3576 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
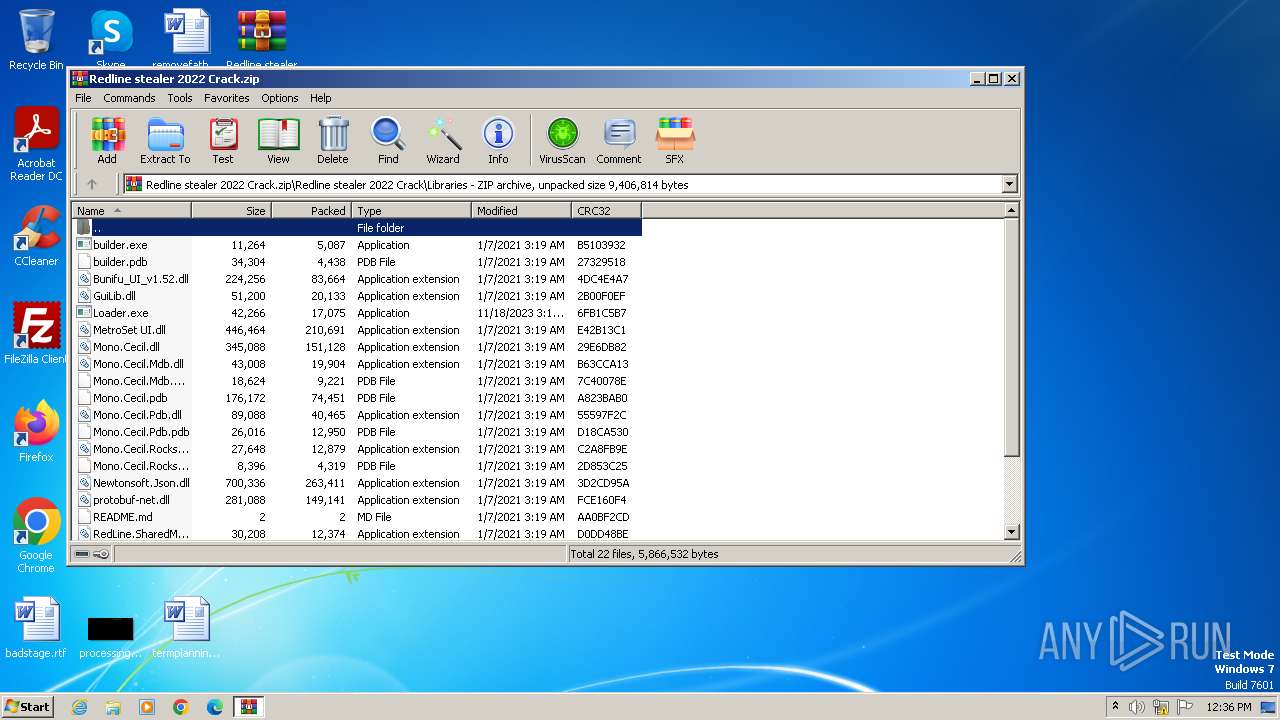
| 3660 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\builder.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\builder.exe | — | RedLine.MainPanel-cracked.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: builder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 988
Read events
3 928
Write events
56
Delete events
4
Modification events
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
16
Suspicious files
11
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
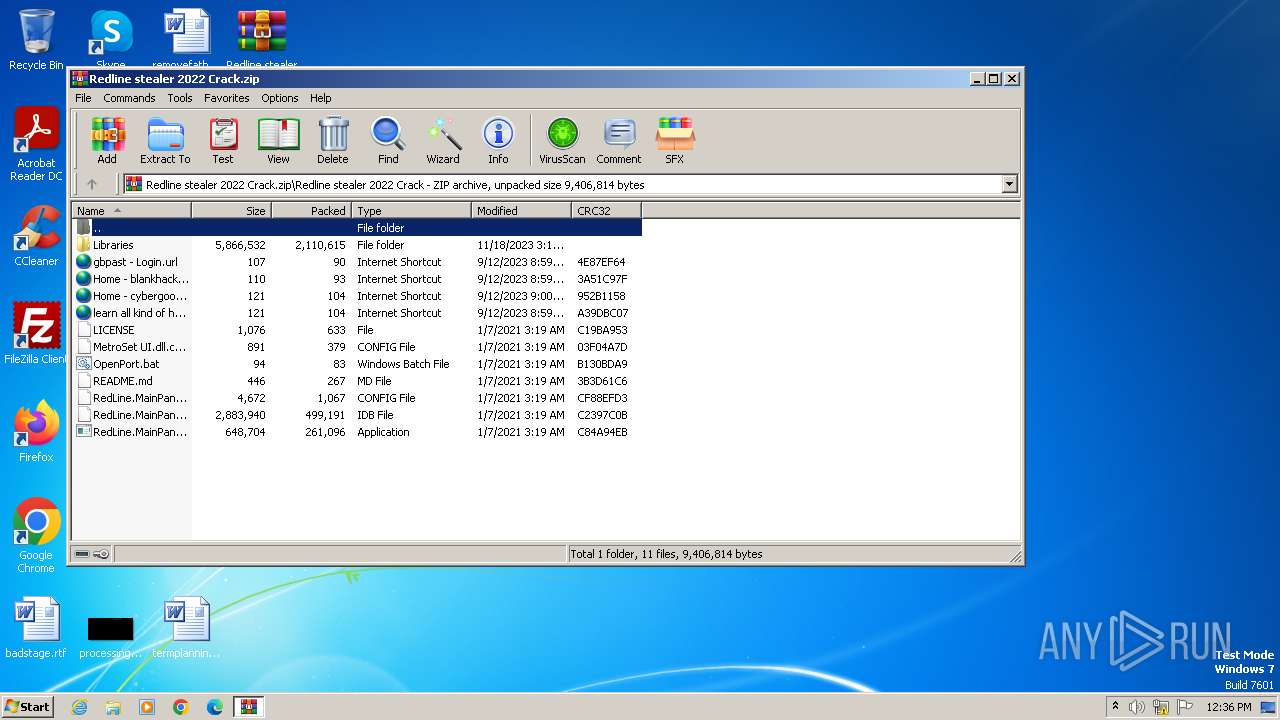
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Home - blankhack.url | binary | |
MD5:4A4418C24D2F2A9DEEE8046363BDD28F | SHA256:55DFE247F8FD6A8B0B66B3CB61FEEAE96D0B357338CD95771E89897AAC1A6839 | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\gbpast - Login.url | binary | |
MD5:4A4F5BE9370E206241BB73BFC2367F3C | SHA256:210F2EE620FE51ACDBE59BBA7BB4ACBDE397034818B09156F6F0874B016A5B18 | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\builder.pdb | binary | |
MD5:418DC008EF956465E179EC29D3C3C245 | SHA256:8C7E21B37540211D56C5FDBB7E731655A96945AA83F2988E33D5ADB8AA7C8DF1 | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\Mono.Cecil.Mdb.dll | executable | |
MD5:DC80F588F513D998A5DF1CA415EDB700 | SHA256:90CFC73BEFD43FC3FD876E23DCC3F5CE6E9D21D396BBB346513302E2215DB8C9 | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\learn all kind of hacking.url | binary | |
MD5:7ADE4A739CBD8F44D0EF52A2F1BC6E7B | SHA256:CC7649ED53C65E4851ACE414529564FE16801BB2BED4CB15588BFD6B4AC13616 | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\Bunifu_UI_v1.52.dll | executable | |
MD5:5ECA94D909F1BA4C5F3E35AC65A49076 | SHA256:DE0E530D46C803D85B8AEB6D18816F1B09CB3DAFEFB5E19FDFA15C9F41E0F474 | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\Loader.exe | executable | |
MD5:CFF63E16C0F61DA3CF1329EBCF462773 | SHA256:E3BD0202BA4C688CA4C5917BC6892808089246968FACF6FF8AF52028FB0FFF6E | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\MetroSet UI.dll | binary | |
MD5:F13DC3CFFEF729D26C4DA102674561CF | SHA256:D490C04E6E89462FD46099D3454985F319F57032176C67403B3B92C86CA58BCB | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Libraries\Mono.Cecil.dll | executable | |
MD5:7546ACEBC5A5213DEE2A5ED18D7EBC6C | SHA256:7744C9C84C28033BC3606F4DFCE2ADCD6F632E2BE7827893C3E2257100F1CF9E | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3204.47720\Redline stealer 2022 Crack\Home - cybergoons.url | binary | |
MD5:EF51820E228C5BBCF9AABE92E747782E | SHA256:59AC2D12EA4559253FA25F2D367F75B7689BB7B772965101903063F646AE9B4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
828 | svchost.exe | OPTIONS | — | 185.235.129.102:80 | http://blankhack.com/ | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 200 | 185.235.129.102:80 | http://blankhack.com/ | unknown | html | 35.5 Kb | unknown |
828 | svchost.exe | PROPFIND | 200 | 185.235.129.102:80 | http://blankhack.com/ | unknown | html | 35.5 Kb | unknown |
828 | svchost.exe | PROPFIND | 200 | 185.235.129.102:80 | http://blankhack.com/ | unknown | html | 35.5 Kb | unknown |
828 | svchost.exe | PROPFIND | 200 | 185.235.129.102:80 | http://blankhack.com/ | unknown | html | 35.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
828 | svchost.exe | 185.235.129.102:80 | blankhack.com | Zomro B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
blankhack.com |
| unknown |