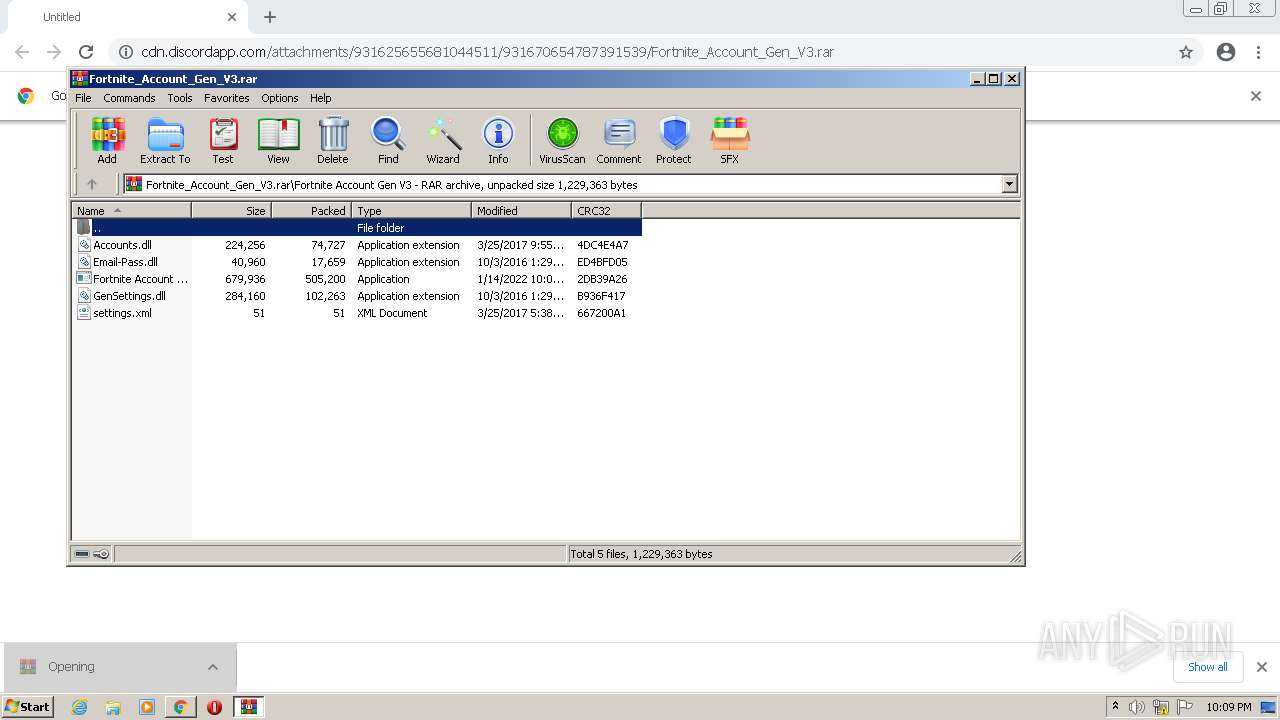
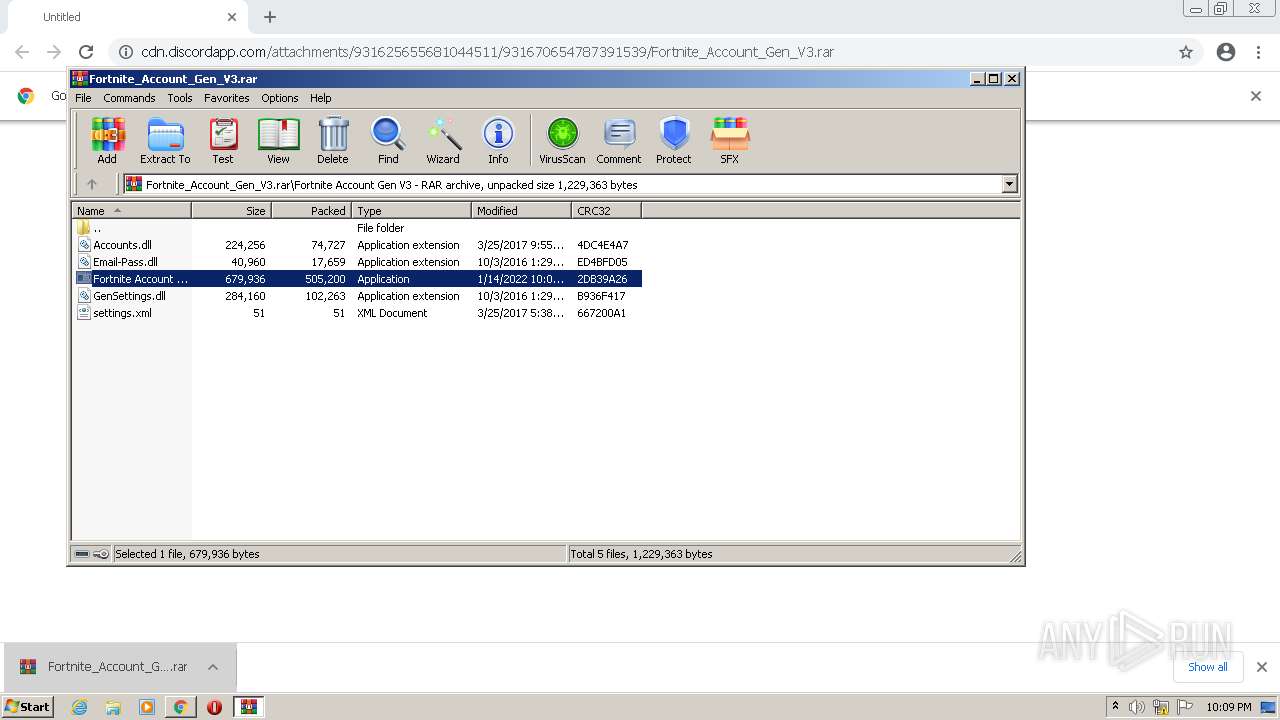
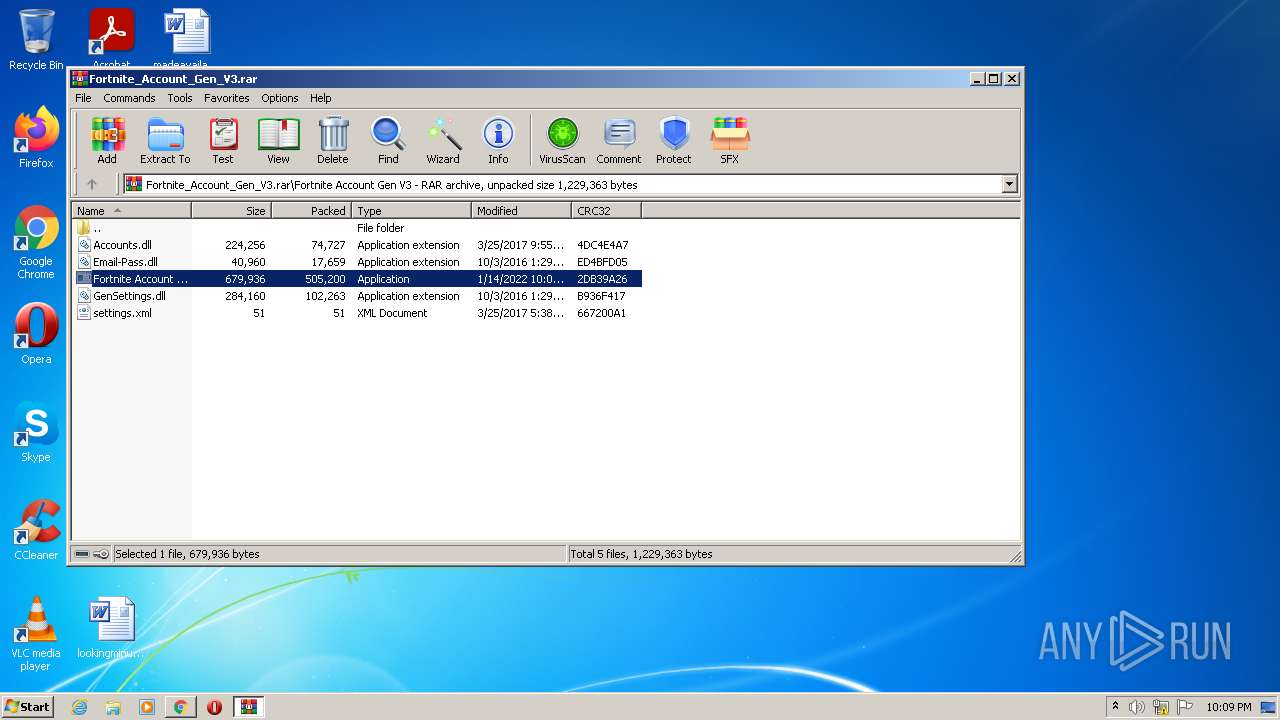
| URL: | https://cdn.discordapp.com/attachments/931625655681044511/931670654787391539/Fortnite_Account_Gen_V3.rar |
| Full analysis: | https://app.any.run/tasks/15801e34-119f-41c4-aacd-337b6b35eb53 |
| Verdict: | Malicious activity |
| Threats: | NanoCore is a Remote Access Trojan or RAT. This malware is highly customizable with plugins which allow attackers to tailor its functionality to their needs. Nanocore is created with the .NET framework and it’s available for purchase for just $25 from its “official” website. |
| Analysis date: | January 14, 2022, 22:08:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7F5AD8346277ECD335F0F015F9BE906A |
| SHA1: | B3DC4336711ADDBA4CCB07AD2250176B67AA6869 |
| SHA256: | 91C8D940BDFCA4EC00381EFE64BB4EFF3E41CEB973F3FD34F3FA795D72600CA6 |
| SSDEEP: | 3:N8cCWdy6//nMQTFGetbWcxdROLUXn:2cry6XnRhfb7MLUXn |
MALICIOUS
Application was dropped or rewritten from another process
- Fortnite Account Gen V3.exe (PID: 3540)
- Fortnite Account Gen V3.exe (PID: 2592)
- Fortnite Account Gen V3.exe (PID: 2624)
- Fortnite Account Gen V3.exe (PID: 2576)
- Fortnite Account Gen V3.exe (PID: 2252)
- Fortnite Account Gen V3.exe (PID: 4032)
- Fortnite Account Gen V3.exe (PID: 1268)
- Fortnite Account Gen V3.exe (PID: 396)
- Fortnite Account Gen V3.exe (PID: 3988)
- Fortnite Account Gen V3.exe (PID: 628)
- Fortnite Account Gen V3.exe (PID: 2964)
- Fortnite Account Gen V3.exe (PID: 2428)
- Fortnite Account Gen V3.exe (PID: 3204)
- Fortnite Account Gen V3.exe (PID: 660)
- Fortnite Account Gen V3.exe (PID: 1948)
- Fortnite Account Gen V3.exe (PID: 3140)
- Fortnite Account Gen V3.exe (PID: 2388)
- Fortnite Account Gen V3.exe (PID: 3492)
- Fortnite Account Gen V3.exe (PID: 2632)
- Fortnite Account Gen V3.exe (PID: 1752)
- Fortnite Account Gen V3.exe (PID: 3368)
- Fortnite Account Gen V3.exe (PID: 3868)
- Fortnite Account Gen V3.exe (PID: 2204)
- Fortnite Account Gen V3.exe (PID: 656)
- Fortnite Account Gen V3.exe (PID: 832)
- Fortnite Account Gen V3.exe (PID: 3872)
- Fortnite Account Gen V3.exe (PID: 2184)
- Fortnite Account Gen V3.exe (PID: 836)
- Fortnite Account Gen V3.exe (PID: 3484)
- Fortnite Account Gen V3.bat (PID: 2192)
- Fortnite Account Gen V3.exe (PID: 2536)
- Fortnite Account Gen V3.exe (PID: 1940)
- Fortnite Account Gen V3.exe (PID: 4016)
- Fortnite Account Gen V3.bat (PID: 2084)
- Fortnite Account Gen V3.exe (PID: 3412)
- Fortnite Account Gen V3.exe (PID: 2820)
- Fortnite Account Gen V3.exe (PID: 2668)
- Fortnite Account Gen V3.exe (PID: 2488)
- Fortnite Account Gen V3.exe (PID: 2404)
- Fortnite Account Gen V3.exe (PID: 188)
- Fortnite Account Gen V3.exe (PID: 2652)
- Fortnite Account Gen V3.exe (PID: 304)
- Fortnite Account Gen V3.exe (PID: 3336)
- Fortnite Account Gen V3.exe (PID: 2920)
- Fortnite Account Gen V3.exe (PID: 1264)
- Fortnite Account Gen V3.exe (PID: 1260)
- Fortnite Account Gen V3.exe (PID: 656)
- Fortnite Account Gen V3.exe (PID: 2080)
- Fortnite Account Gen V3.exe (PID: 528)
- Fortnite Account Gen V3.exe (PID: 1092)
Uses Task Scheduler to run other applications
- Fortnite Account Gen V3.exe (PID: 3540)
- Fortnite Account Gen V3.exe (PID: 2592)
- Fortnite Account Gen V3.exe (PID: 2624)
- Fortnite Account Gen V3.exe (PID: 2964)
- Fortnite Account Gen V3.exe (PID: 2252)
- Fortnite Account Gen V3.exe (PID: 2632)
- Fortnite Account Gen V3.exe (PID: 396)
- Fortnite Account Gen V3.exe (PID: 3988)
- Fortnite Account Gen V3.exe (PID: 628)
- Fortnite Account Gen V3.exe (PID: 3204)
- Fortnite Account Gen V3.exe (PID: 2428)
- Fortnite Account Gen V3.exe (PID: 1948)
- Fortnite Account Gen V3.exe (PID: 3140)
- Fortnite Account Gen V3.exe (PID: 2388)
- Fortnite Account Gen V3.bat (PID: 2192)
- Fortnite Account Gen V3.exe (PID: 836)
- Fortnite Account Gen V3.exe (PID: 2536)
- Fortnite Account Gen V3.exe (PID: 1940)
- Fortnite Account Gen V3.exe (PID: 4016)
- Fortnite Account Gen V3.exe (PID: 3412)
- Fortnite Account Gen V3.exe (PID: 188)
- Fortnite Account Gen V3.exe (PID: 304)
- Fortnite Account Gen V3.exe (PID: 2652)
- Fortnite Account Gen V3.exe (PID: 1260)
- Fortnite Account Gen V3.exe (PID: 2080)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2224)
- schtasks.exe (PID: 576)
- schtasks.exe (PID: 2452)
- schtasks.exe (PID: 2928)
- schtasks.exe (PID: 2988)
- schtasks.exe (PID: 2860)
- schtasks.exe (PID: 2260)
- schtasks.exe (PID: 2836)
- schtasks.exe (PID: 2252)
- schtasks.exe (PID: 2224)
- schtasks.exe (PID: 2468)
- schtasks.exe (PID: 2916)
- schtasks.exe (PID: 3764)
- schtasks.exe (PID: 2284)
- schtasks.exe (PID: 2168)
- schtasks.exe (PID: 480)
- schtasks.exe (PID: 2760)
- schtasks.exe (PID: 1380)
- schtasks.exe (PID: 3152)
- schtasks.exe (PID: 3628)
- schtasks.exe (PID: 1300)
- schtasks.exe (PID: 692)
- schtasks.exe (PID: 3212)
- schtasks.exe (PID: 3640)
- schtasks.exe (PID: 1680)
Connects to CnC server
- Fortnite Account Gen V3.exe (PID: 2576)
NANOCORE was detected
- Fortnite Account Gen V3.exe (PID: 2576)
Drops executable file immediately after starts
- chrome.exe (PID: 3212)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2072)
- Fortnite Account Gen V3.exe (PID: 3540)
- Fortnite Account Gen V3.exe (PID: 2592)
- Fortnite Account Gen V3.exe (PID: 2624)
- Fortnite Account Gen V3.exe (PID: 2576)
- Fortnite Account Gen V3.exe (PID: 2964)
- Fortnite Account Gen V3.exe (PID: 2252)
- Fortnite Account Gen V3.exe (PID: 2632)
- Fortnite Account Gen V3.exe (PID: 4032)
- Fortnite Account Gen V3.exe (PID: 1268)
- Fortnite Account Gen V3.exe (PID: 396)
- Fortnite Account Gen V3.exe (PID: 3988)
- Fortnite Account Gen V3.exe (PID: 628)
- Fortnite Account Gen V3.exe (PID: 3204)
- Fortnite Account Gen V3.exe (PID: 2428)
- Fortnite Account Gen V3.exe (PID: 660)
- Fortnite Account Gen V3.exe (PID: 1948)
- Fortnite Account Gen V3.exe (PID: 3140)
- Fortnite Account Gen V3.exe (PID: 2388)
- Fortnite Account Gen V3.exe (PID: 3492)
- Fortnite Account Gen V3.exe (PID: 1752)
- notepad++.exe (PID: 3172)
- Fortnite Account Gen V3.exe (PID: 3368)
- Fortnite Account Gen V3.exe (PID: 3868)
- Fortnite Account Gen V3.exe (PID: 2204)
- Fortnite Account Gen V3.exe (PID: 832)
- Fortnite Account Gen V3.exe (PID: 656)
- Fortnite Account Gen V3.exe (PID: 3872)
- Fortnite Account Gen V3.exe (PID: 2184)
- Fortnite Account Gen V3.exe (PID: 3484)
- Fortnite Account Gen V3.bat (PID: 2192)
- Fortnite Account Gen V3.exe (PID: 2536)
- Fortnite Account Gen V3.exe (PID: 1940)
- Fortnite Account Gen V3.exe (PID: 4016)
- Fortnite Account Gen V3.exe (PID: 836)
- Fortnite Account Gen V3.bat (PID: 2084)
- Fortnite Account Gen V3.exe (PID: 3412)
- Fortnite Account Gen V3.exe (PID: 2668)
- Fortnite Account Gen V3.exe (PID: 2820)
- Fortnite Account Gen V3.exe (PID: 2404)
- Fortnite Account Gen V3.exe (PID: 2488)
- Fortnite Account Gen V3.exe (PID: 188)
- Fortnite Account Gen V3.exe (PID: 2652)
- Fortnite Account Gen V3.exe (PID: 304)
- Fortnite Account Gen V3.exe (PID: 3336)
- Fortnite Account Gen V3.exe (PID: 1264)
- Fortnite Account Gen V3.exe (PID: 1260)
- Fortnite Account Gen V3.exe (PID: 528)
- Fortnite Account Gen V3.exe (PID: 2920)
- Fortnite Account Gen V3.exe (PID: 656)
- Fortnite Account Gen V3.exe (PID: 1092)
- Fortnite Account Gen V3.exe (PID: 2080)
Reads the computer name
- WinRAR.exe (PID: 2072)
- Fortnite Account Gen V3.exe (PID: 3540)
- Fortnite Account Gen V3.exe (PID: 2592)
- Fortnite Account Gen V3.exe (PID: 2624)
- Fortnite Account Gen V3.exe (PID: 2576)
- Fortnite Account Gen V3.exe (PID: 2964)
- Fortnite Account Gen V3.exe (PID: 2252)
- Fortnite Account Gen V3.exe (PID: 2632)
- Fortnite Account Gen V3.exe (PID: 4032)
- Fortnite Account Gen V3.exe (PID: 1268)
- Fortnite Account Gen V3.exe (PID: 396)
- Fortnite Account Gen V3.exe (PID: 3988)
- Fortnite Account Gen V3.exe (PID: 628)
- Fortnite Account Gen V3.exe (PID: 3204)
- Fortnite Account Gen V3.exe (PID: 660)
- Fortnite Account Gen V3.exe (PID: 2428)
- Fortnite Account Gen V3.exe (PID: 1948)
- Fortnite Account Gen V3.exe (PID: 3140)
- Fortnite Account Gen V3.exe (PID: 2388)
- Fortnite Account Gen V3.exe (PID: 1752)
- Fortnite Account Gen V3.exe (PID: 3368)
- Fortnite Account Gen V3.exe (PID: 3868)
- Fortnite Account Gen V3.exe (PID: 2204)
- Fortnite Account Gen V3.exe (PID: 656)
- Fortnite Account Gen V3.exe (PID: 832)
- Fortnite Account Gen V3.exe (PID: 3872)
- Fortnite Account Gen V3.exe (PID: 2184)
- Fortnite Account Gen V3.exe (PID: 3484)
- notepad++.exe (PID: 3172)
- Fortnite Account Gen V3.bat (PID: 2192)
- Fortnite Account Gen V3.exe (PID: 836)
- Fortnite Account Gen V3.exe (PID: 2536)
- Fortnite Account Gen V3.exe (PID: 1940)
- Fortnite Account Gen V3.exe (PID: 4016)
- Fortnite Account Gen V3.exe (PID: 3412)
- Fortnite Account Gen V3.exe (PID: 3492)
- Fortnite Account Gen V3.exe (PID: 2820)
- Fortnite Account Gen V3.bat (PID: 2084)
- Fortnite Account Gen V3.exe (PID: 2668)
- Fortnite Account Gen V3.exe (PID: 2488)
- Fortnite Account Gen V3.exe (PID: 2404)
- Fortnite Account Gen V3.exe (PID: 188)
- Fortnite Account Gen V3.exe (PID: 2652)
- Fortnite Account Gen V3.exe (PID: 304)
- Fortnite Account Gen V3.exe (PID: 3336)
- Fortnite Account Gen V3.exe (PID: 2920)
- Fortnite Account Gen V3.exe (PID: 1260)
- Fortnite Account Gen V3.exe (PID: 1264)
- Fortnite Account Gen V3.exe (PID: 528)
- Fortnite Account Gen V3.exe (PID: 656)
- Fortnite Account Gen V3.exe (PID: 2080)
- Fortnite Account Gen V3.exe (PID: 1092)
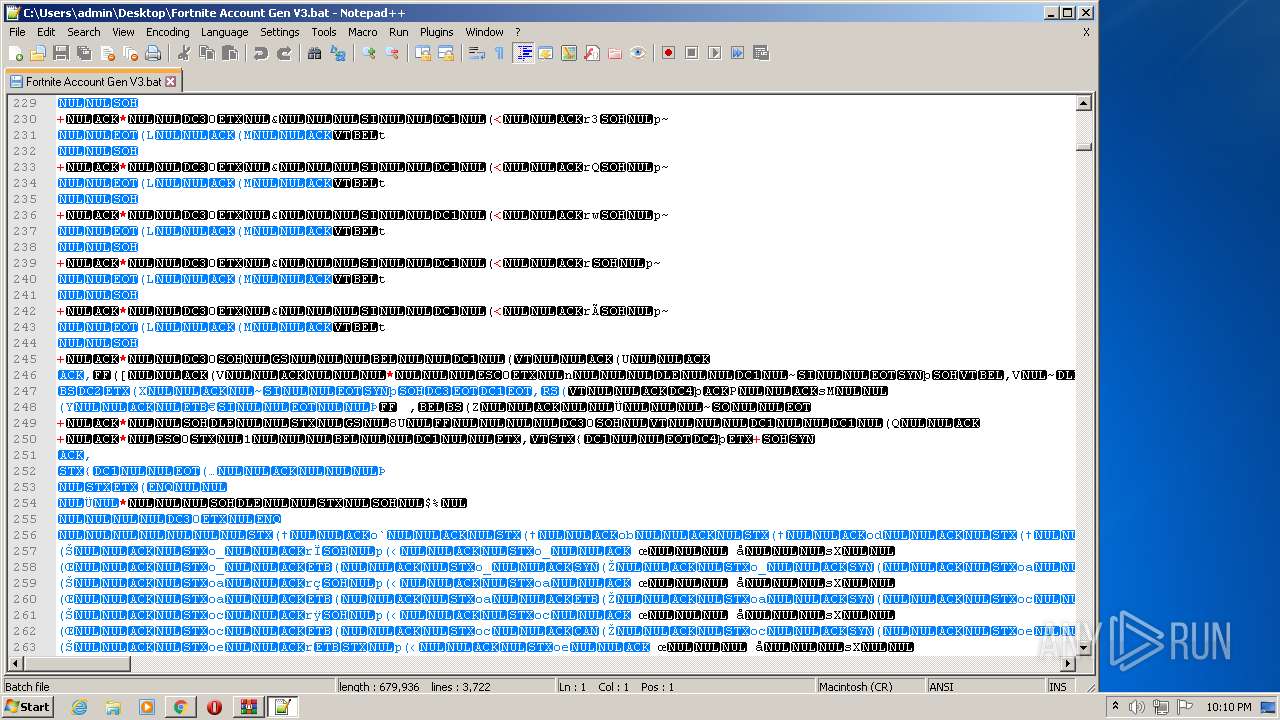
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2072)
- Fortnite Account Gen V3.exe (PID: 3540)
- notepad++.exe (PID: 3172)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2072)
- Fortnite Account Gen V3.exe (PID: 3540)
- notepad++.exe (PID: 3172)
- chrome.exe (PID: 3212)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2072)
- chrome.exe (PID: 3212)
Creates files in the user directory
- Fortnite Account Gen V3.exe (PID: 3540)
- Fortnite Account Gen V3.exe (PID: 2576)
Application launched itself
- Fortnite Account Gen V3.exe (PID: 3540)
- Fortnite Account Gen V3.exe (PID: 2592)
- Fortnite Account Gen V3.exe (PID: 2624)
- Fortnite Account Gen V3.exe (PID: 2964)
- Fortnite Account Gen V3.exe (PID: 2252)
- Fortnite Account Gen V3.exe (PID: 2632)
- Fortnite Account Gen V3.exe (PID: 396)
- Fortnite Account Gen V3.exe (PID: 3988)
- Fortnite Account Gen V3.exe (PID: 628)
- Fortnite Account Gen V3.exe (PID: 3204)
- Fortnite Account Gen V3.exe (PID: 2428)
- Fortnite Account Gen V3.exe (PID: 3140)
- Fortnite Account Gen V3.exe (PID: 2388)
- Fortnite Account Gen V3.exe (PID: 1948)
- Fortnite Account Gen V3.exe (PID: 836)
- Fortnite Account Gen V3.bat (PID: 2192)
- Fortnite Account Gen V3.exe (PID: 1940)
- Fortnite Account Gen V3.exe (PID: 2536)
- Fortnite Account Gen V3.exe (PID: 4016)
- Fortnite Account Gen V3.exe (PID: 3412)
- Fortnite Account Gen V3.exe (PID: 188)
- Fortnite Account Gen V3.exe (PID: 304)
- Fortnite Account Gen V3.exe (PID: 2652)
- Fortnite Account Gen V3.exe (PID: 1260)
- Fortnite Account Gen V3.exe (PID: 2080)
Reads Environment values
- Fortnite Account Gen V3.exe (PID: 2576)
Suspicious files were dropped or overwritten
- notepad++.exe (PID: 3172)
Starts application with an unusual extension
- Fortnite Account Gen V3.bat (PID: 2192)
Starts Internet Explorer
- Fortnite Account Gen V3.exe (PID: 2576)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3988)
INFO
Checks supported languages
- chrome.exe (PID: 1640)
- chrome.exe (PID: 444)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 3420)
- chrome.exe (PID: 2812)
- chrome.exe (PID: 2432)
- chrome.exe (PID: 2508)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 2800)
- chrome.exe (PID: 1524)
- chrome.exe (PID: 968)
- chrome.exe (PID: 440)
- chrome.exe (PID: 2304)
- chrome.exe (PID: 1336)
- schtasks.exe (PID: 2224)
- chrome.exe (PID: 396)
- schtasks.exe (PID: 576)
- schtasks.exe (PID: 2452)
- schtasks.exe (PID: 2928)
- chrome.exe (PID: 3464)
- schtasks.exe (PID: 2988)
- schtasks.exe (PID: 2860)
- schtasks.exe (PID: 2260)
- schtasks.exe (PID: 2836)
- schtasks.exe (PID: 2252)
- schtasks.exe (PID: 2916)
- schtasks.exe (PID: 2224)
- schtasks.exe (PID: 2468)
- schtasks.exe (PID: 2284)
- schtasks.exe (PID: 3764)
- explorer.exe (PID: 3956)
- schtasks.exe (PID: 2168)
- chrome.exe (PID: 2972)
- schtasks.exe (PID: 480)
- schtasks.exe (PID: 2760)
- chrome.exe (PID: 3212)
- schtasks.exe (PID: 1380)
- schtasks.exe (PID: 3152)
- chrome.exe (PID: 1136)
- chrome.exe (PID: 2224)
- schtasks.exe (PID: 3628)
- chrome.exe (PID: 2088)
- iexplore.exe (PID: 276)
- chrome.exe (PID: 1876)
- schtasks.exe (PID: 1300)
- iexplore.exe (PID: 3988)
- schtasks.exe (PID: 3212)
- schtasks.exe (PID: 692)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 2588)
- chrome.exe (PID: 428)
- schtasks.exe (PID: 3640)
- schtasks.exe (PID: 1680)
Reads the computer name
- chrome.exe (PID: 1640)
- chrome.exe (PID: 444)
- chrome.exe (PID: 2508)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 968)
- chrome.exe (PID: 440)
- chrome.exe (PID: 1336)
- chrome.exe (PID: 2304)
- schtasks.exe (PID: 2224)
- chrome.exe (PID: 396)
- schtasks.exe (PID: 576)
- schtasks.exe (PID: 2452)
- schtasks.exe (PID: 2928)
- schtasks.exe (PID: 2860)
- schtasks.exe (PID: 2260)
- schtasks.exe (PID: 2836)
- schtasks.exe (PID: 2252)
- schtasks.exe (PID: 2916)
- schtasks.exe (PID: 2224)
- schtasks.exe (PID: 2468)
- schtasks.exe (PID: 2284)
- schtasks.exe (PID: 3764)
- explorer.exe (PID: 3956)
- schtasks.exe (PID: 2988)
- schtasks.exe (PID: 480)
- schtasks.exe (PID: 2168)
- schtasks.exe (PID: 2760)
- schtasks.exe (PID: 1380)
- schtasks.exe (PID: 3152)
- schtasks.exe (PID: 3628)
- iexplore.exe (PID: 276)
- iexplore.exe (PID: 3988)
- schtasks.exe (PID: 1300)
- schtasks.exe (PID: 3212)
- schtasks.exe (PID: 692)
- schtasks.exe (PID: 3640)
- schtasks.exe (PID: 1680)
Reads settings of System Certificates
- chrome.exe (PID: 444)
- iexplore.exe (PID: 276)
Reads the hosts file
- chrome.exe (PID: 3548)
- chrome.exe (PID: 444)
Application launched itself
- chrome.exe (PID: 3548)
- iexplore.exe (PID: 276)
Manual execution by user
- Fortnite Account Gen V3.exe (PID: 2592)
- Fortnite Account Gen V3.exe (PID: 2624)
- Fortnite Account Gen V3.exe (PID: 2964)
- Fortnite Account Gen V3.exe (PID: 2252)
- Fortnite Account Gen V3.exe (PID: 2632)
- Fortnite Account Gen V3.exe (PID: 396)
- Fortnite Account Gen V3.exe (PID: 3988)
- Fortnite Account Gen V3.exe (PID: 628)
- Fortnite Account Gen V3.exe (PID: 3204)
- Fortnite Account Gen V3.exe (PID: 2428)
- Fortnite Account Gen V3.exe (PID: 1948)
- Fortnite Account Gen V3.exe (PID: 3140)
- Fortnite Account Gen V3.exe (PID: 2388)
- notepad++.exe (PID: 3172)
- Fortnite Account Gen V3.bat (PID: 2192)
- Fortnite Account Gen V3.exe (PID: 836)
- explorer.exe (PID: 3956)
- Fortnite Account Gen V3.exe (PID: 2536)
- Fortnite Account Gen V3.exe (PID: 4016)
- Fortnite Account Gen V3.exe (PID: 1940)
- Fortnite Account Gen V3.exe (PID: 3412)
- Fortnite Account Gen V3.exe (PID: 2652)
- Fortnite Account Gen V3.exe (PID: 304)
- Fortnite Account Gen V3.exe (PID: 188)
- Fortnite Account Gen V3.exe (PID: 1260)
- Fortnite Account Gen V3.exe (PID: 2080)
Reads the date of Windows installation
- chrome.exe (PID: 2304)
- iexplore.exe (PID: 276)
Changes internet zones settings
- iexplore.exe (PID: 276)
Reads internet explorer settings
- iexplore.exe (PID: 3988)
Checks Windows Trust Settings
- iexplore.exe (PID: 276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
177
Monitored processes
105
Malicious processes
26
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\Desktop\Fortnite Account Gen V3.exe" | C:\Users\admin\Desktop\Fortnite Account Gen V3.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Kee IT Integrity Level: MEDIUM Description: Leaky_Boat Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 276 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.hackforums.net/member.php?action=profile&uid=2290236 | C:\Program Files\Internet Explorer\iexplore.exe | Fortnite Account Gen V3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 304 | "C:\Users\admin\Desktop\Fortnite Account Gen V3.exe" | C:\Users\admin\Desktop\Fortnite Account Gen V3.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Kee IT Integrity Level: MEDIUM Description: Leaky_Boat Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1024,3328210667617841295,10993956849637173344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1788 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 396 | "C:\Users\admin\Desktop\Fortnite Account Gen V3.exe" | C:\Users\admin\Desktop\Fortnite Account Gen V3.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Kee IT Integrity Level: MEDIUM Description: Leaky_Boat Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1024,3328210667617841295,10993956849637173344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1024,3328210667617841295,10993956849637173344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1024,3328210667617841295,10993956849637173344,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1256 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 480 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\KENUxRVLzjj" /XML "C:\Users\admin\AppData\Local\Temp\tmp151B.tmp" | C:\Windows\System32\schtasks.exe | — | Fortnite Account Gen V3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 528 | "{path}" | C:\Users\admin\Desktop\Fortnite Account Gen V3.exe | — | Fortnite Account Gen V3.exe | |||||||||||
User: admin Company: Kee IT Integrity Level: MEDIUM Description: Leaky_Boat Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
28 101
Read events
27 603
Write events
490
Delete events
8
Modification events
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3548) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
8
Suspicious files
57
Text files
156
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61E1F463-DDC.pma | — | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a45998a0-867f-4539-8962-6fb7c502635b.tmp | text | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RFe27c7.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RFe28e0.TMP | text | |
MD5:109A25C32EE1132ECD6D9F3ED9ADF01A | SHA256:DA6028DB9485C65E683643658326F02B1D0A1566DE14914EF28E5248EB94F0DD | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFe27a8.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old | text | |
MD5:5202CA4D6AF0C37DAEC0D528CC7F2986 | SHA256:8F5B8FF94B14C36EA0CBE8FA0A4D165A632B45F834BBB7239E1A6CF6685F256C | |||
| 3548 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
38
DNS requests
24
Threats
148
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
872 | svchost.exe | HEAD | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/p6tdgdqb2yivlossrf26vulw4q_2763/jflookgnkcckhobaglndicnbbgbonegd_2763_all_arglytk4g4e7ivpqlqt2zfg3sy.crx3 | US | — | — | whitelisted |
872 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/p6tdgdqb2yivlossrf26vulw4q_2763/jflookgnkcckhobaglndicnbbgbonegd_2763_all_arglytk4g4e7ivpqlqt2zfg3sy.crx3 | US | — | — | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 43.5 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 9.71 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 358 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 20.9 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 398 Kb | whitelisted |
872 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 178 Kb | whitelisted |
872 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/p6tdgdqb2yivlossrf26vulw4q_2763/jflookgnkcckhobaglndicnbbgbonegd_2763_all_arglytk4g4e7ivpqlqt2zfg3sy.crx3 | US | crx | 25.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
444 | chrome.exe | 162.159.135.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
444 | chrome.exe | 142.250.186.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
444 | chrome.exe | 162.159.130.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
872 | svchost.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
444 | chrome.exe | 142.250.185.206:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
2576 | Fortnite Account Gen V3.exe | 107.182.237.15:61529 | — | Hosting Services, Inc. | US | malicious |
444 | chrome.exe | 142.250.184.195:443 | update.googleapis.com | Google Inc. | US | whitelisted |
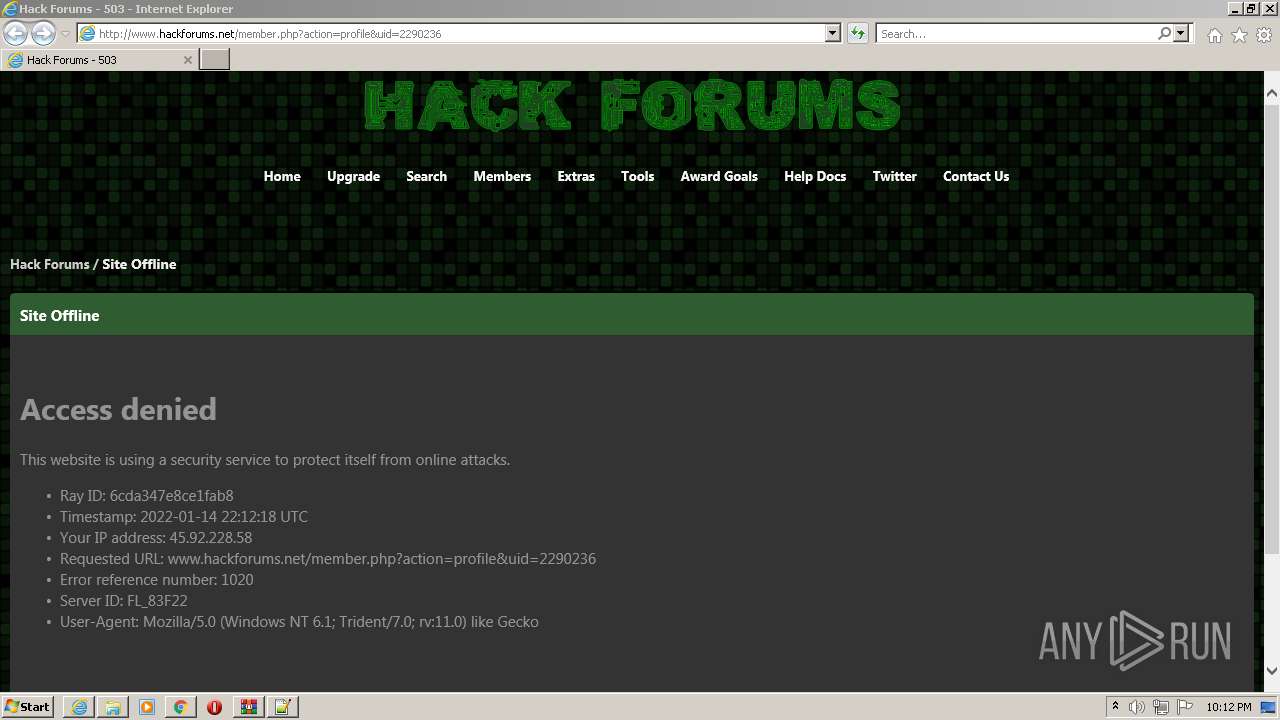
3988 | iexplore.exe | 104.23.128.79:80 | www.hackforums.net | Cloudflare Inc | US | suspicious |
276 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
276 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
cdn.discordapp.com |
| shared |
clients2.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
safebrowsing.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.hackforums.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
2576 | Fortnite Account Gen V3.exe | A Network Trojan was detected | ET TROJAN Possible NanoCore C2 60B |
140 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|