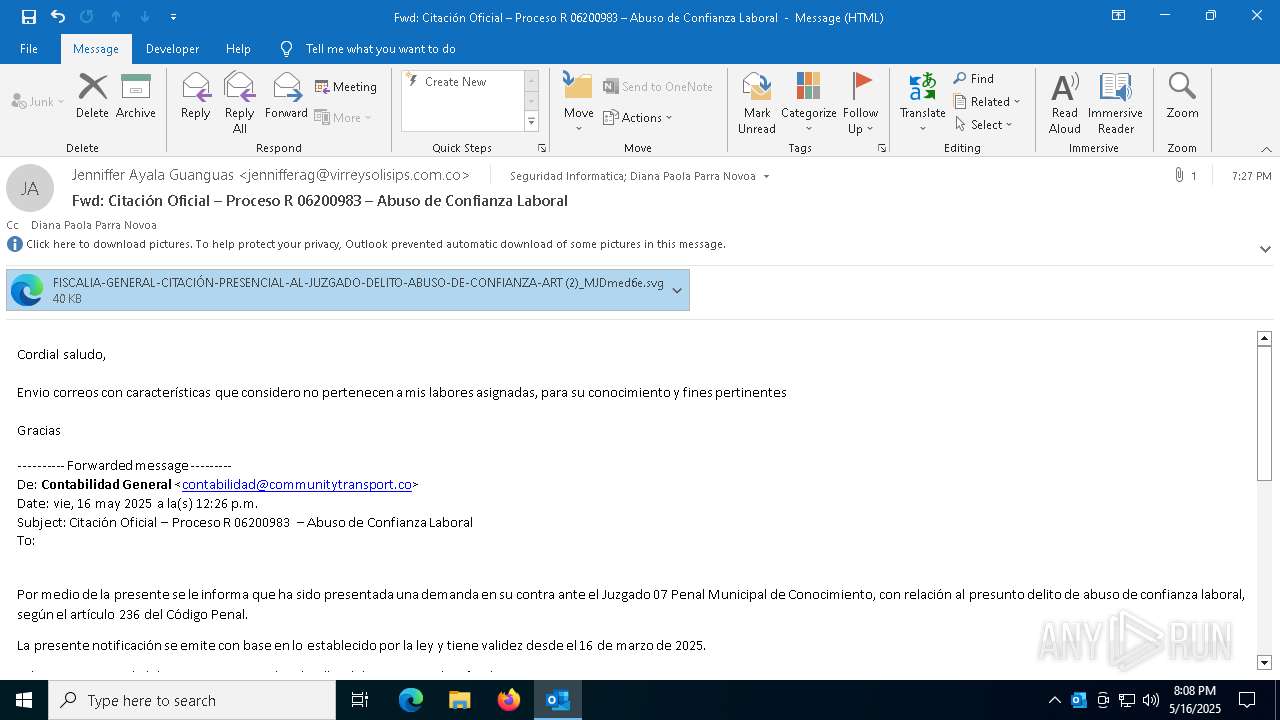
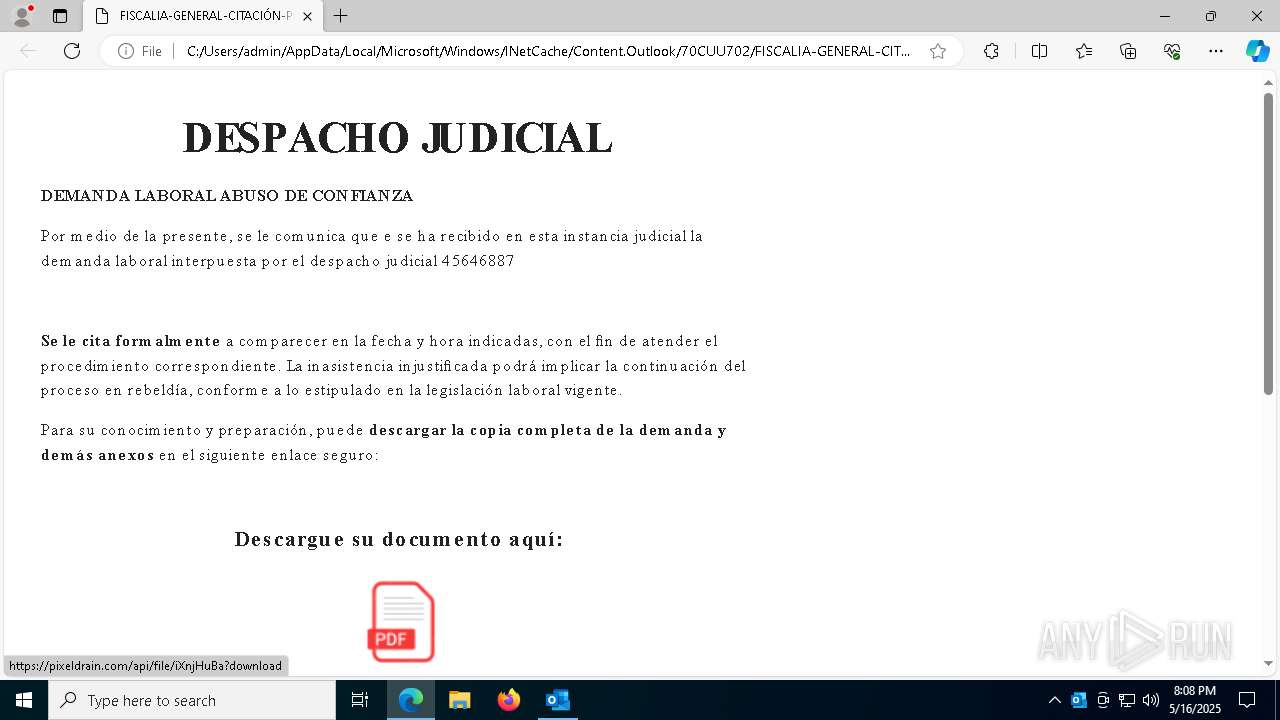
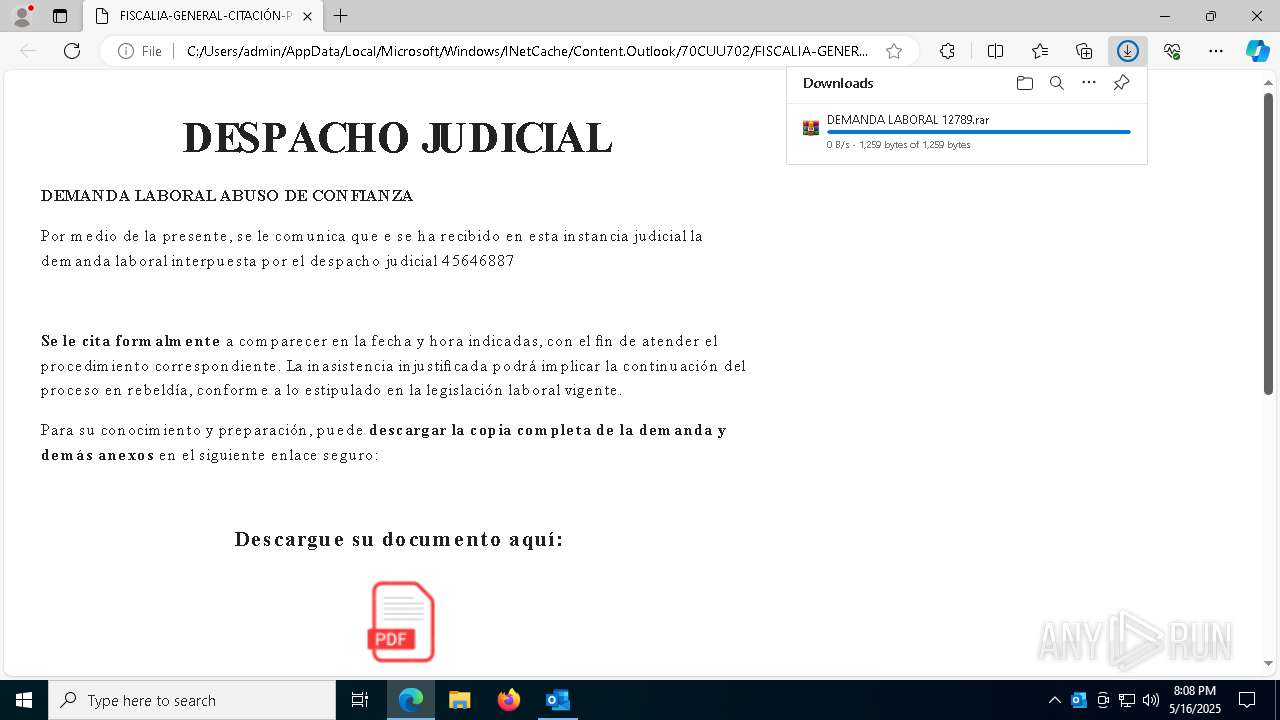
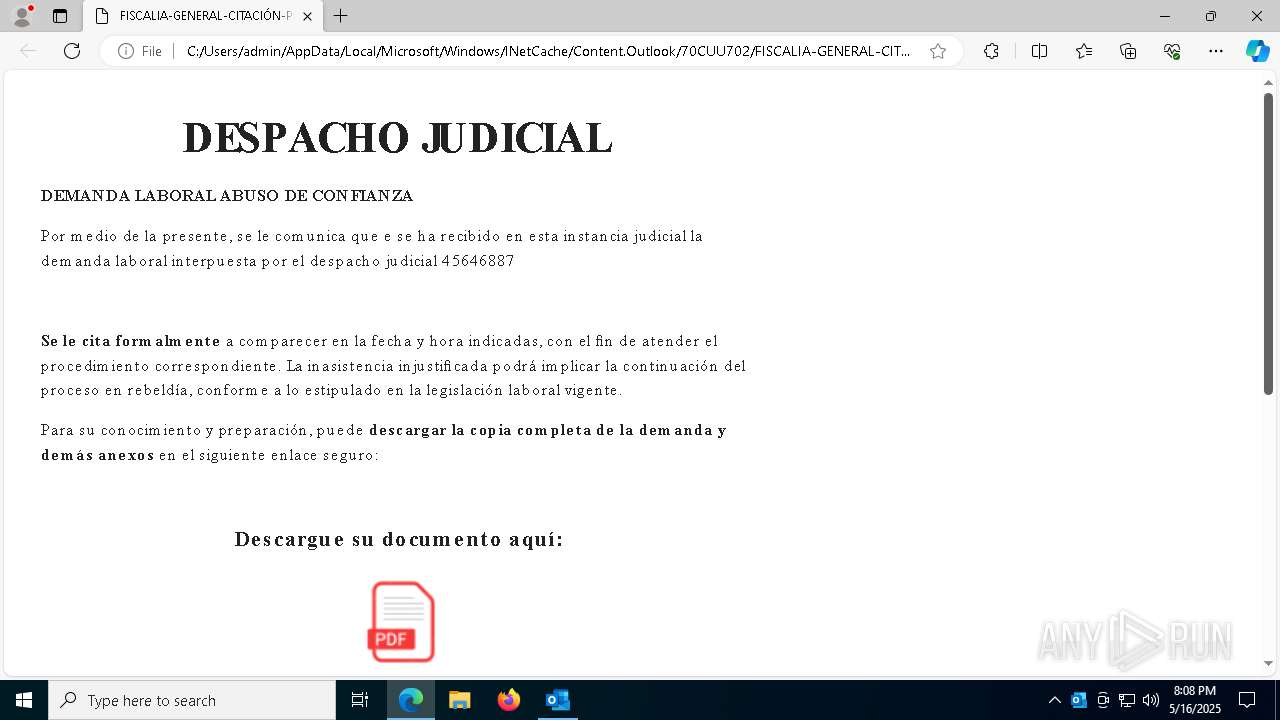
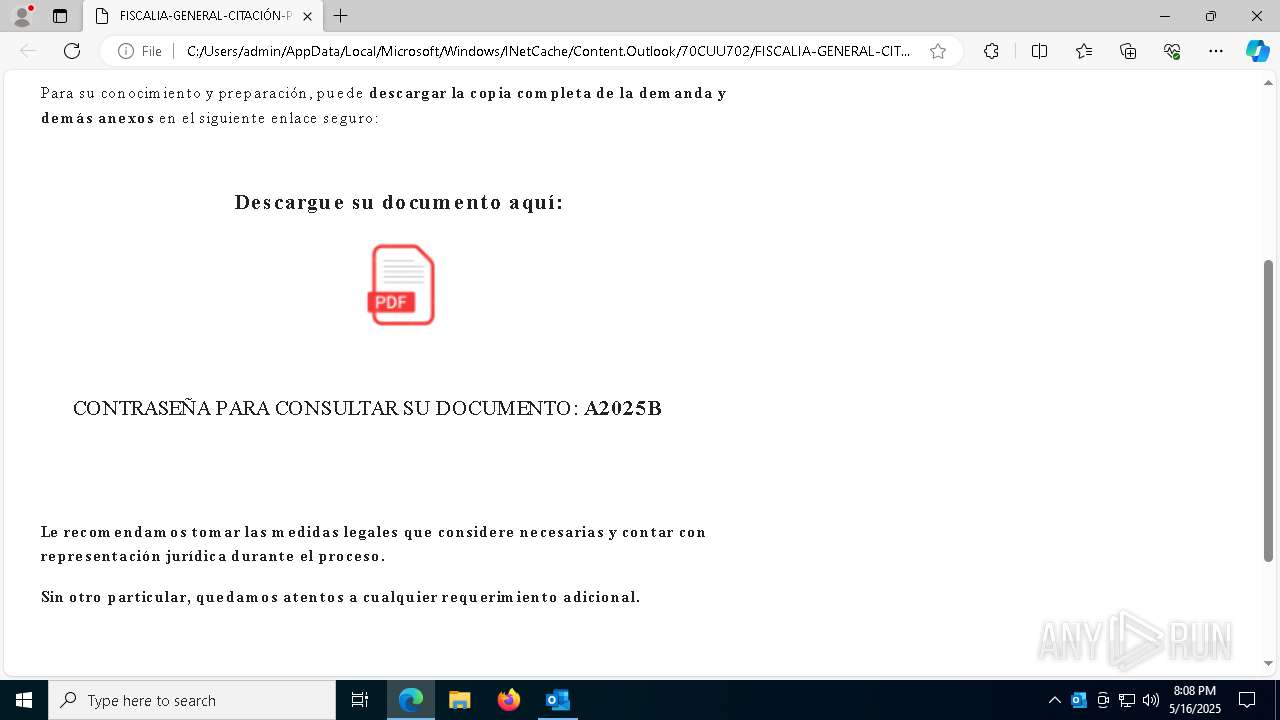
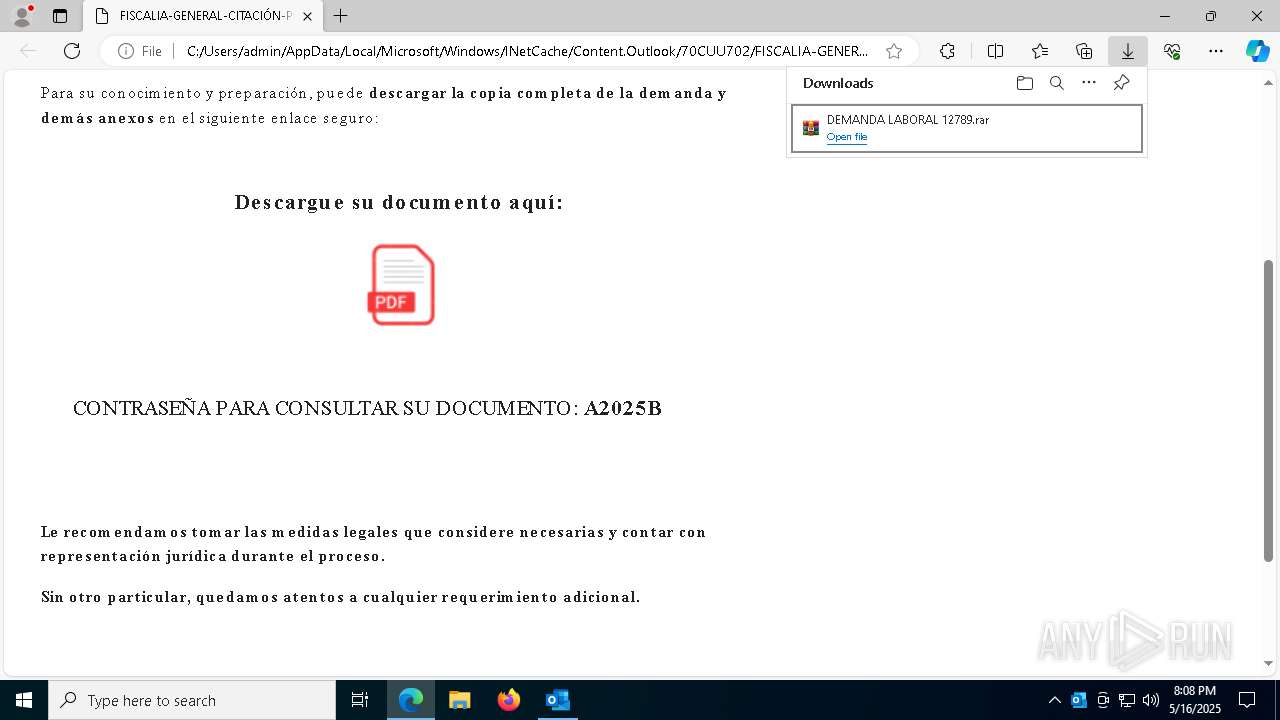
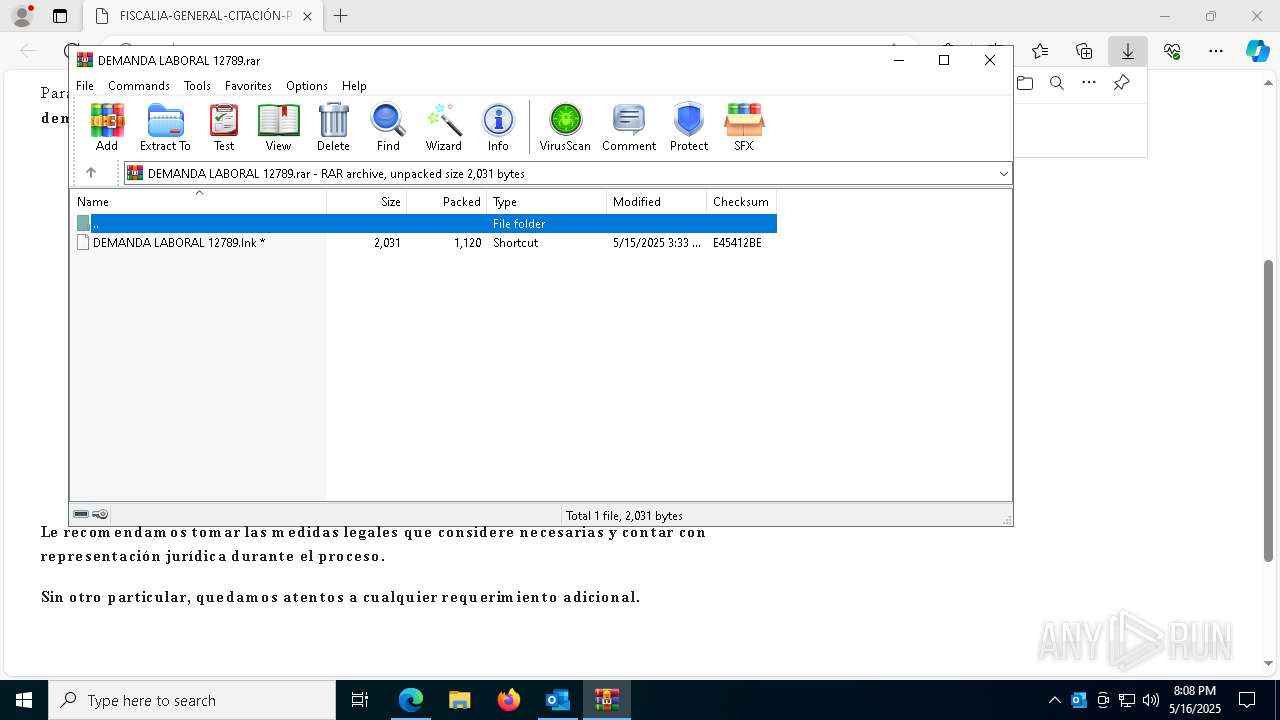
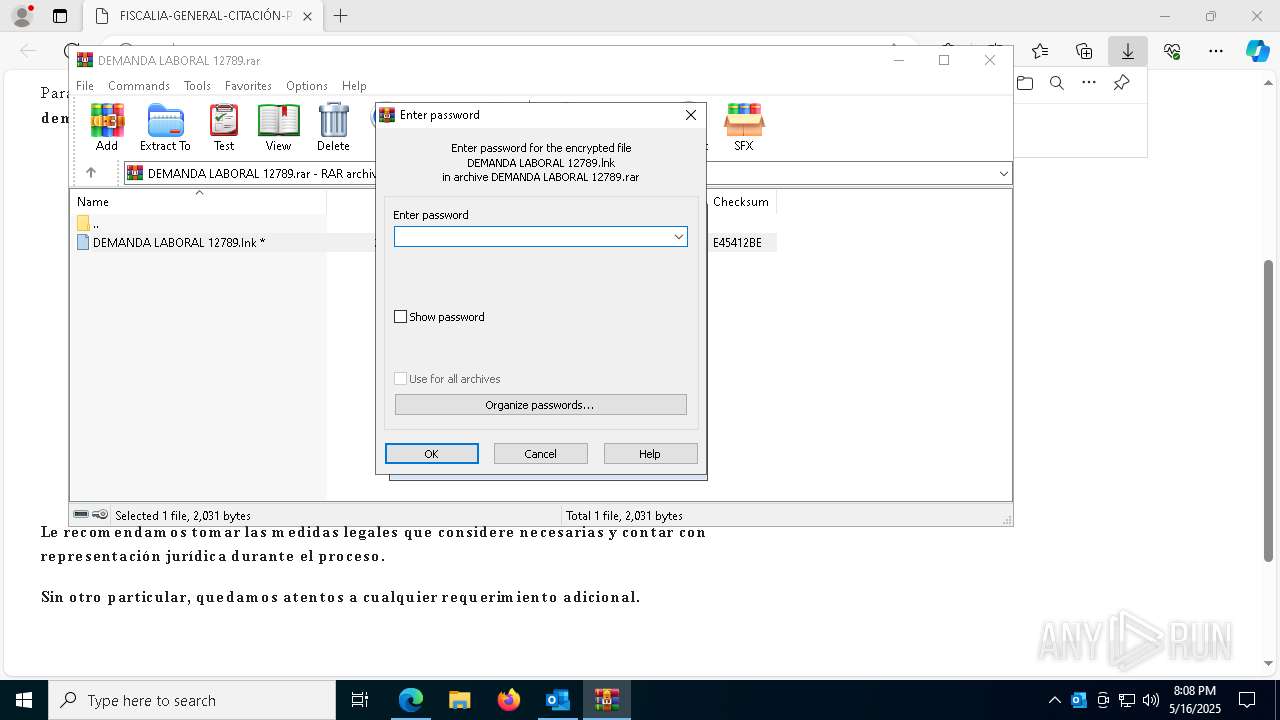
| File name: | Citación Oficial – Proceso R 06200983 – Abuso de Confianza Laboral.eml |
| Full analysis: | https://app.any.run/tasks/a5d15553-cabc-4ccd-a9c5-d9612a6bcd80 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | May 16, 2025, 20:07:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 91BFEF7533509046DCADCDEE3A858D81 |
| SHA1: | 640348F4F4796541A1D165B992F4315B018213B5 |
| SHA256: | 91B20D660815E3866B5B26EE48F7AB5F619DF2FB12BC1082E6C7678365F7E3C4 |
| SSDEEP: | 1536:X8l9Lm0ZPzNBbc/nyldUeSSeme7c5uGsA/VBbc07HU:x0pNKTc5uGx/VBQOHU |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6512)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6512)
Executing a file with an untrusted certificate
- IBuilder.exe (PID: 5800)
- IBuilder.exe (PID: 744)
- XPFix.exe (PID: 7936)
HIJACKLOADER has been detected (YARA)
- IBuilder.exe (PID: 5800)
REMCOS has been detected (YARA)
- PrismCli32.exe (PID: 6640)
REMCOS has been detected (SURICATA)
- PrismCli32.exe (PID: 6640)
Connects to the CnC server
- PrismCli32.exe (PID: 6640)
Signed with known abused certificate
- IBuilder.exe (PID: 5800)
SUSPICIOUS
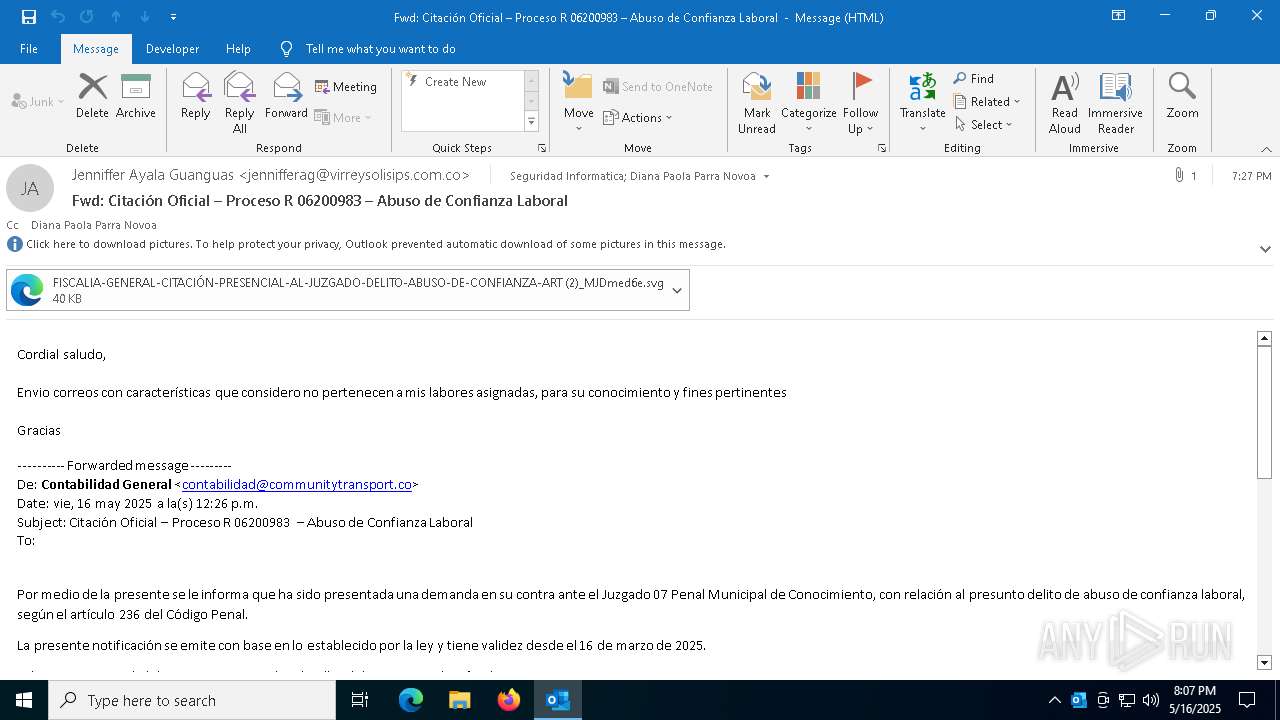
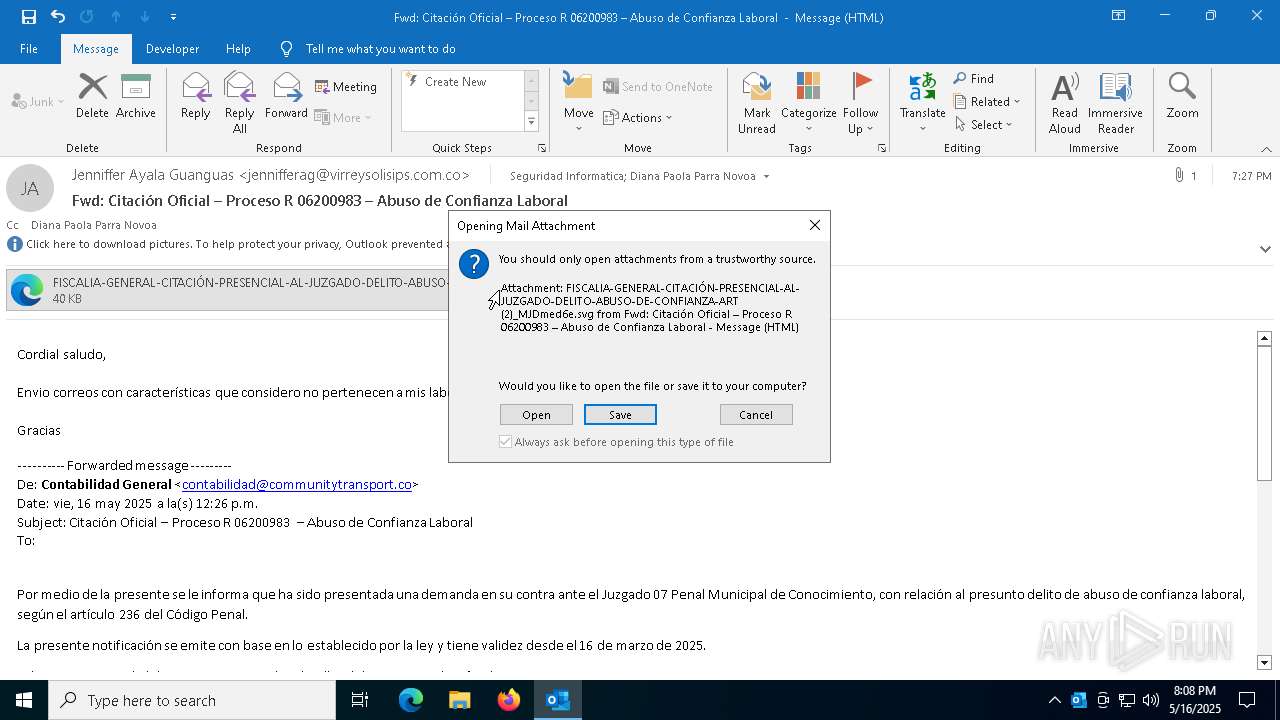
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7420)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7544)
- f9047.exe (PID: 1196)
Probably download files using WebClient
- WinRAR.exe (PID: 7544)
Executable content was dropped or overwritten
- powershell.exe (PID: 6512)
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 744)
- IBuilder.exe (PID: 5800)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 7544)
Process drops legitimate windows executable
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 744)
The process drops C-runtime libraries
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 744)
Starts itself from another location
- IBuilder.exe (PID: 744)
Executes application which crashes
- PrismCli32.exe (PID: 6640)
There is functionality for taking screenshot (YARA)
- PrismCli32.exe (PID: 6640)
Contacting a server suspected of hosting an CnC
- PrismCli32.exe (PID: 6640)
Connects to unusual port
- PrismCli32.exe (PID: 6640)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 7420)
Checks supported languages
- identity_helper.exe (PID: 6640)
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 5800)
- IBuilder.exe (PID: 744)
- PrismCli32.exe (PID: 6640)
- XPFix.exe (PID: 7936)
Application launched itself
- msedge.exe (PID: 4560)
Reads the computer name
- identity_helper.exe (PID: 6640)
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 5800)
- IBuilder.exe (PID: 744)
- PrismCli32.exe (PID: 6640)
- XPFix.exe (PID: 7936)
Reads Environment values
- identity_helper.exe (PID: 6640)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4560)
Disables trace logs
- powershell.exe (PID: 6512)
Checks proxy server information
- powershell.exe (PID: 6512)
Create files in a temporary directory
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 5800)
The executable file from the user directory is run by the Powershell process
- f9047.exe (PID: 1196)
The sample compiled with english language support
- f9047.exe (PID: 1196)
- IBuilder.exe (PID: 744)
- msedge.exe (PID: 5244)
- IBuilder.exe (PID: 5800)
Creates files in the program directory
- IBuilder.exe (PID: 744)
Creates files or folders in the user directory
- IBuilder.exe (PID: 5800)
- WerFault.exe (PID: 6940)
The sample compiled with chinese language support
- IBuilder.exe (PID: 5800)
Process checks computer location settings
- f9047.exe (PID: 1196)
Reads the software policy settings
- slui.exe (PID: 7648)
Executable content was dropped or overwritten
- msedge.exe (PID: 5244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(6640) PrismCli32.exe
C2 (1)masterdabha02.kozow.com:6565
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_fileremcos.exe
Startup_valueFalse
Hide_fileFalse
Mutex_nameRmc-X383GL
Keylog_flag0
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path1
Audio_dirMicRecords
Connect_delay0
Copy_dirRemcos
Keylog_dirremcos
TRiD
| .eml | | | E-Mail message (Var. 7) (100) |
|---|
Total processes
265
Monitored processes
96
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6640 -s 1228 | C:\Windows\SysWOW64\WerFault.exe | — | PrismCli32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6288 --field-trial-handle=2332,i,9903762861643649832,17940475779238580611,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5896 --field-trial-handle=2332,i,9903762861643649832,17940475779238580611,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 728 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3500 --field-trial-handle=2332,i,9903762861643649832,17940475779238580611,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 744 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\IBuilder.exe" | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\IBuilder.exe | f9047.exe | ||||||||||||
User: admin Company: TechSmith Corporation Integrity Level: MEDIUM Description: Camtasia MenuMaker Author Exit code: 0 Version: 8.1.2.1327 Modules
| |||||||||||||||
| 864 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6640 -s 1300 | C:\Windows\SysWOW64\WerFault.exe | — | PrismCli32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6112 --field-trial-handle=2332,i,9903762861643649832,17940475779238580611,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6640 -s 908 | C:\Windows\SysWOW64\WerFault.exe | — | PrismCli32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6660 --field-trial-handle=2332,i,9903762861643649832,17940475779238580611,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\AppData\Local\Temp\f9047.exe" | C:\Users\admin\AppData\Local\Temp\f9047.exe | powershell.exe | ||||||||||||
User: admin Company: Oleg N. Scherbakov Integrity Level: MEDIUM Description: 7z Setup SFX (x86) Exit code: 0 Version: 1.6.0.2712 Modules
| |||||||||||||||
Total events
75 641
Read events
74 386
Write events
1 107
Delete events
148
Modification events
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 09000000 | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030397 |
Value: 60000000 | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7420 |
| Operation: | write | Name: | 0 |
Value: 0B0E10496BEB01C86F48489A186833F555C966230046E5FE8A96E3D3F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511FC39D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7420) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
Executable files
28
Suspicious files
495
Text files
135
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7420 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7420 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:35DF0FB3A4DBD9283330D0CE4B235292 | SHA256:D38211CEF056DDA649AA9366D6FBC2BAC4E9623FC53A70DB954168AE300E4E00 | |||
| 7420 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:E1BEA511FF5E9B35DE13C424ABF031B4 | SHA256:587755615DCE492353036E2B6FFC9E693DEF99BF86CE9007A637B33046729574 | |||
| 7420 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:4BD897CD943F0E5B2CD9F88A032052D0 | SHA256:5F7DA220218FFF3361F21CA1FF50FA62E2010234D1606C4F1FF77B2CE26F150A | |||
| 4560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 7420 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:B30913869C8F4DFC32059ADDDF4D6021 | SHA256:0226985266D6ED117DD26D74C84651DB4C5F10909670CE50F8113C0AE0FC5325 | |||
| 4560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10fb3a.TMP | — | |
MD5:— | SHA256:— | |||
| 4560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10fb3a.TMP | — | |
MD5:— | SHA256:— | |||
| 7420 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_3C8B85F996BF6C4897C70B99795FEC82.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 4560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
65
DNS requests
68
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7420 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7420 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7928 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7928 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5400 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1747938459&P2=404&P3=2&P4=H51Ak30q8ROqbDdoXE6xx%2fJK6EzniZ9IAVdwQ%2fEVPMkcuzGJbrzaWE9bN24yeeqszDCITurXpeliyjBGVd0G%2fg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1747938459&P2=404&P3=2&P4=H51Ak30q8ROqbDdoXE6xx%2fJK6EzniZ9IAVdwQ%2fEVPMkcuzGJbrzaWE9bN24yeeqszDCITurXpeliyjBGVd0G%2fg%3d%3d | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ef98485-cbad-4d99-b4c2-cd4abac73fb4?P1=1747938459&P2=404&P3=2&P4=H51Ak30q8ROqbDdoXE6xx%2fJK6EzniZ9IAVdwQ%2fEVPMkcuzGJbrzaWE9bN24yeeqszDCITurXpeliyjBGVd0G%2fg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4996 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7420 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7420 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7420 | OUTLOOK.EXE | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3884 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
3884 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
3884 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
3884 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
6512 | powershell.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.kozow .com Domain |
6640 | PrismCli32.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
6640 | PrismCli32.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
6640 | PrismCli32.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |