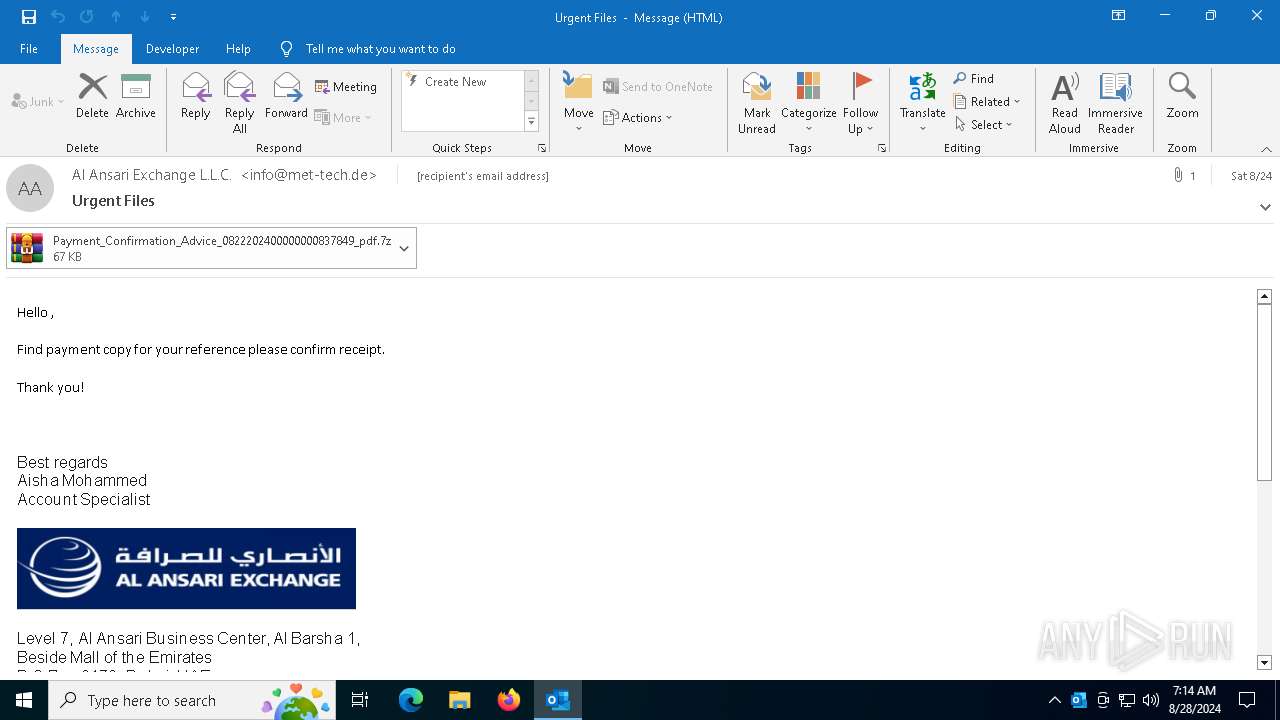
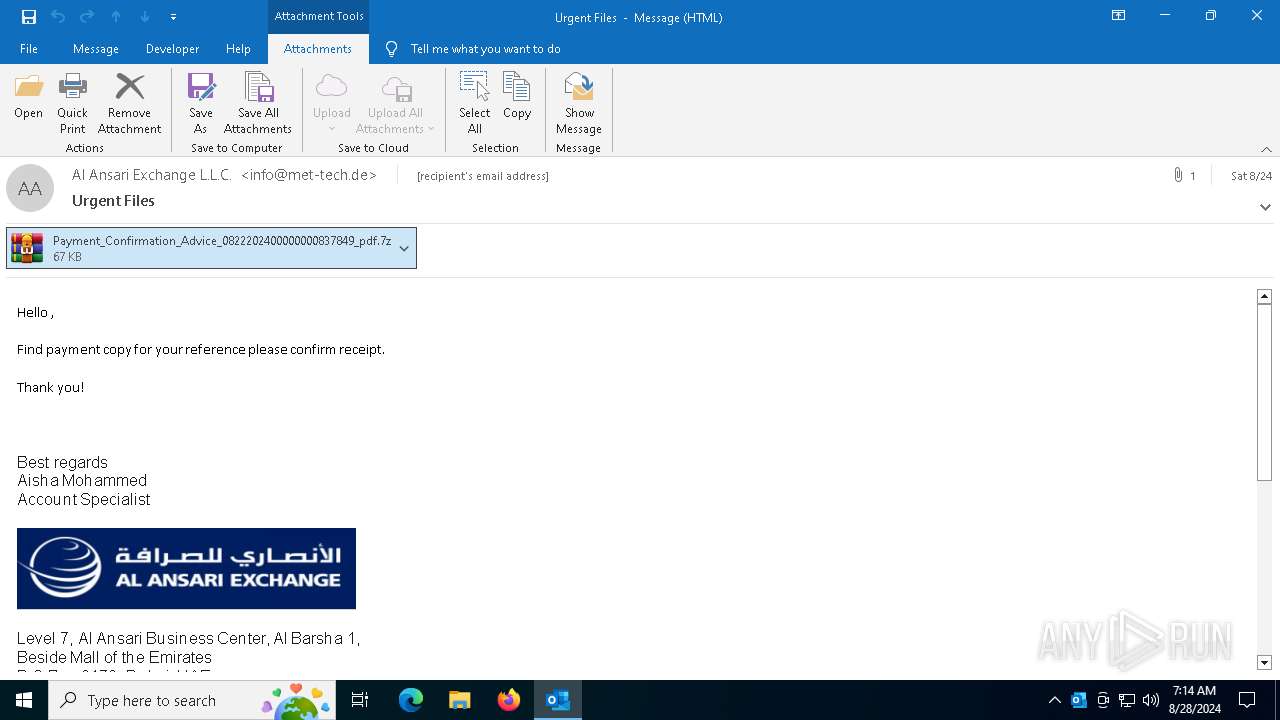
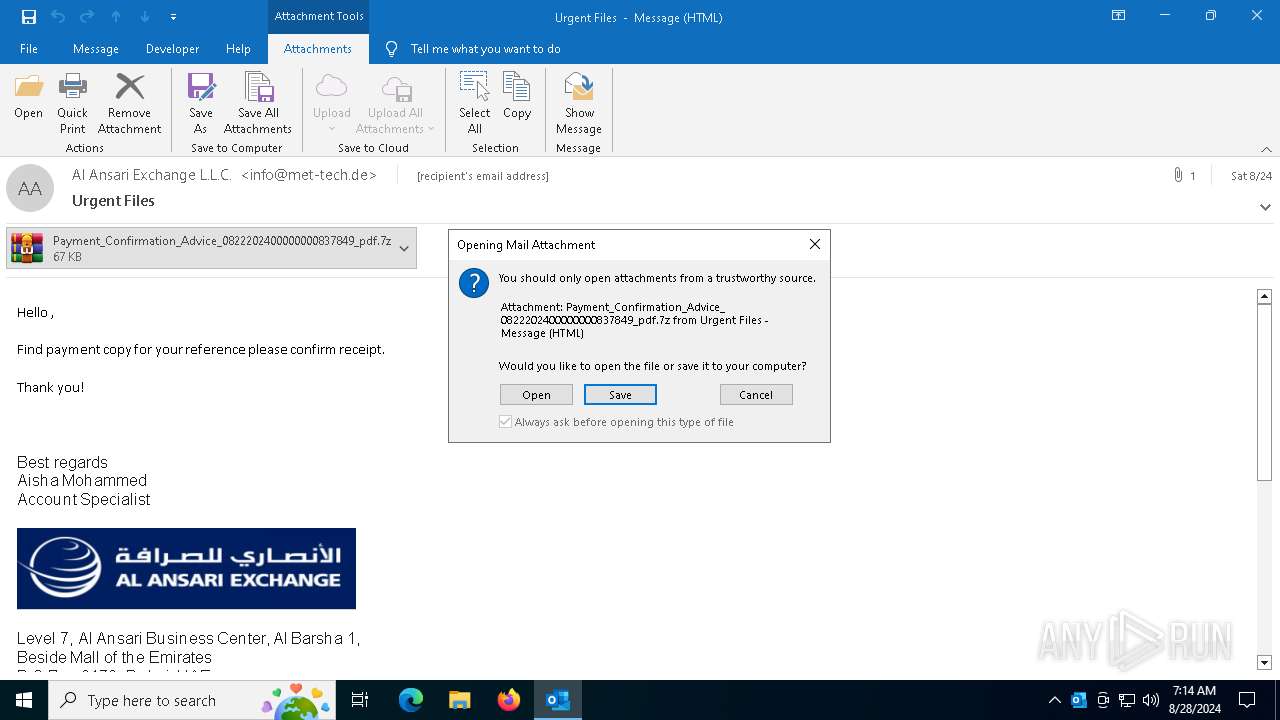
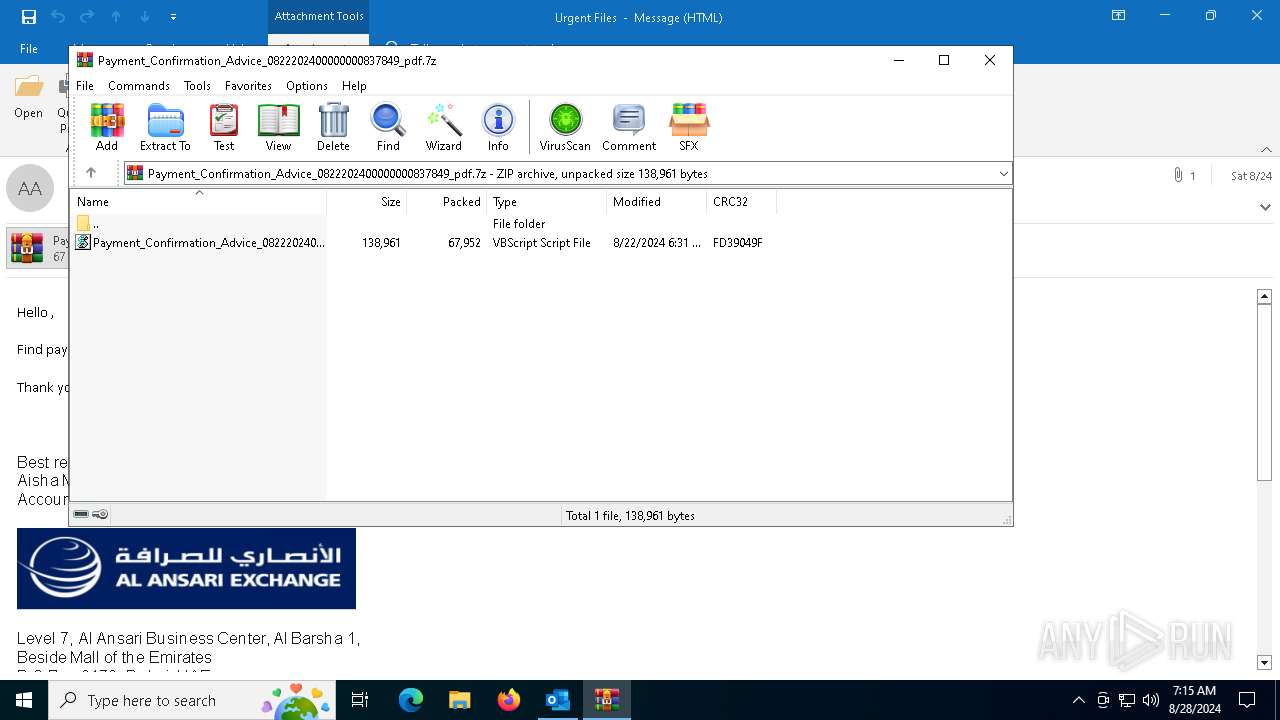
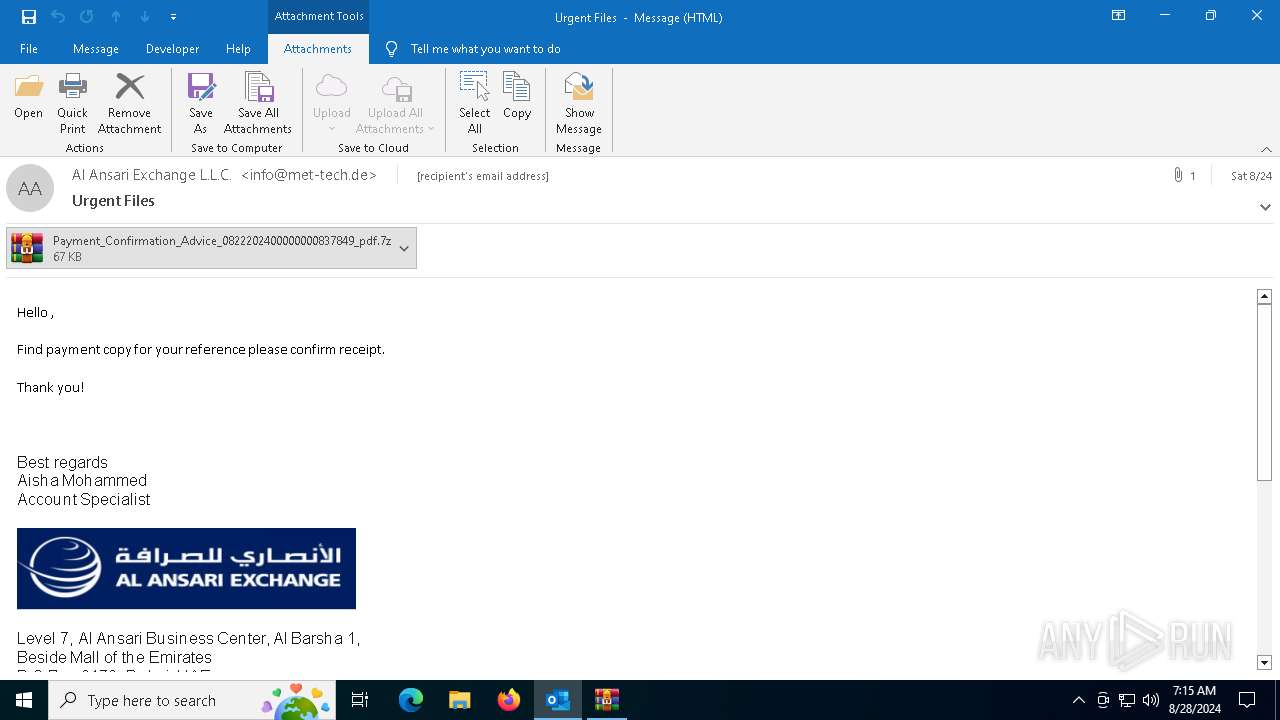
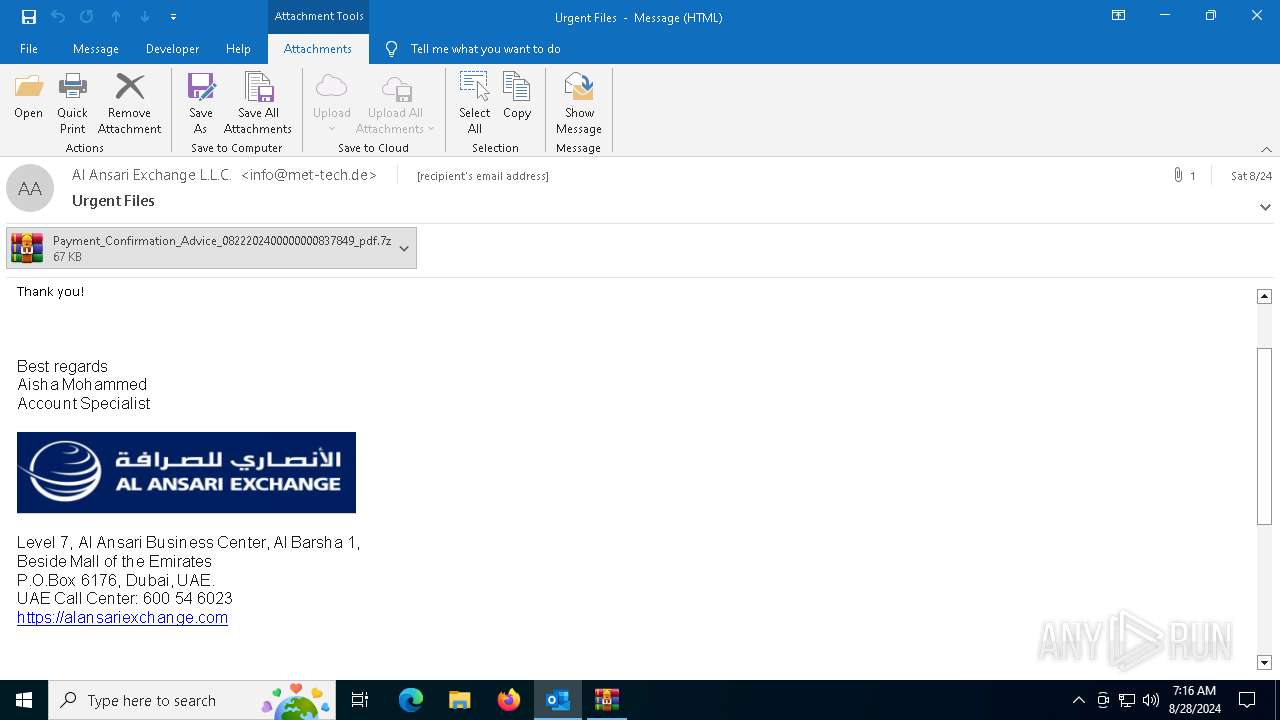
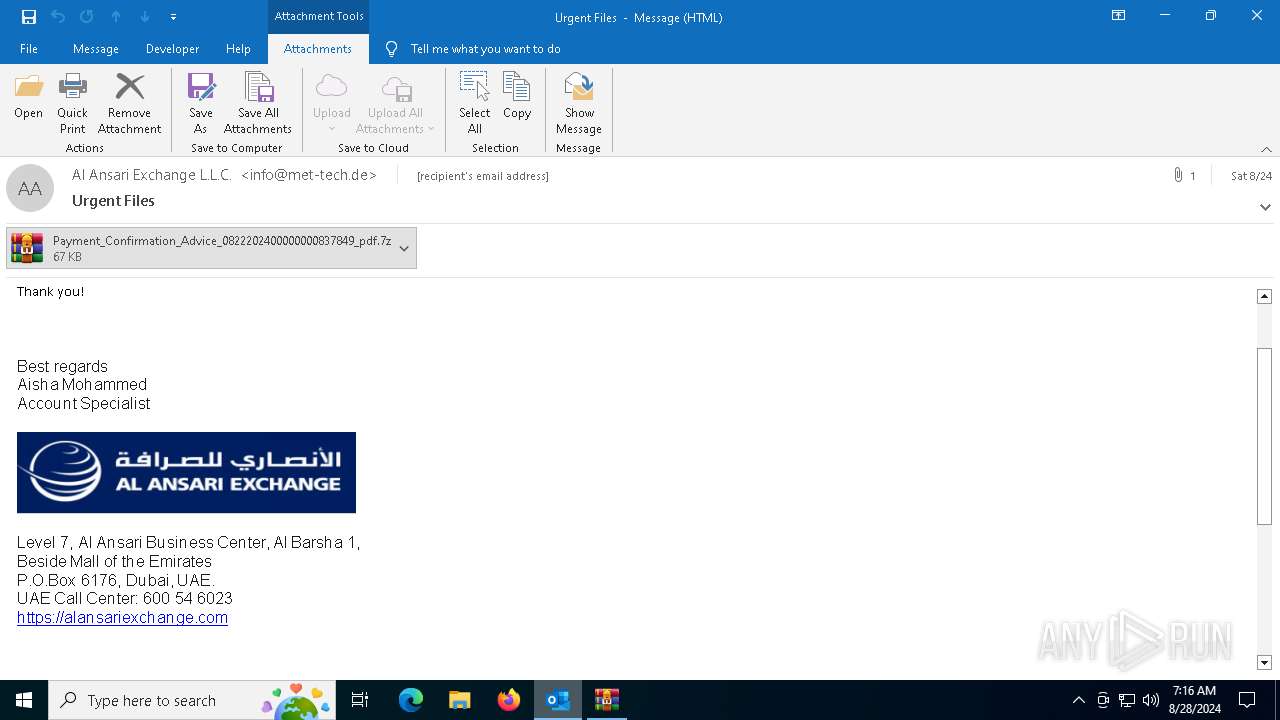
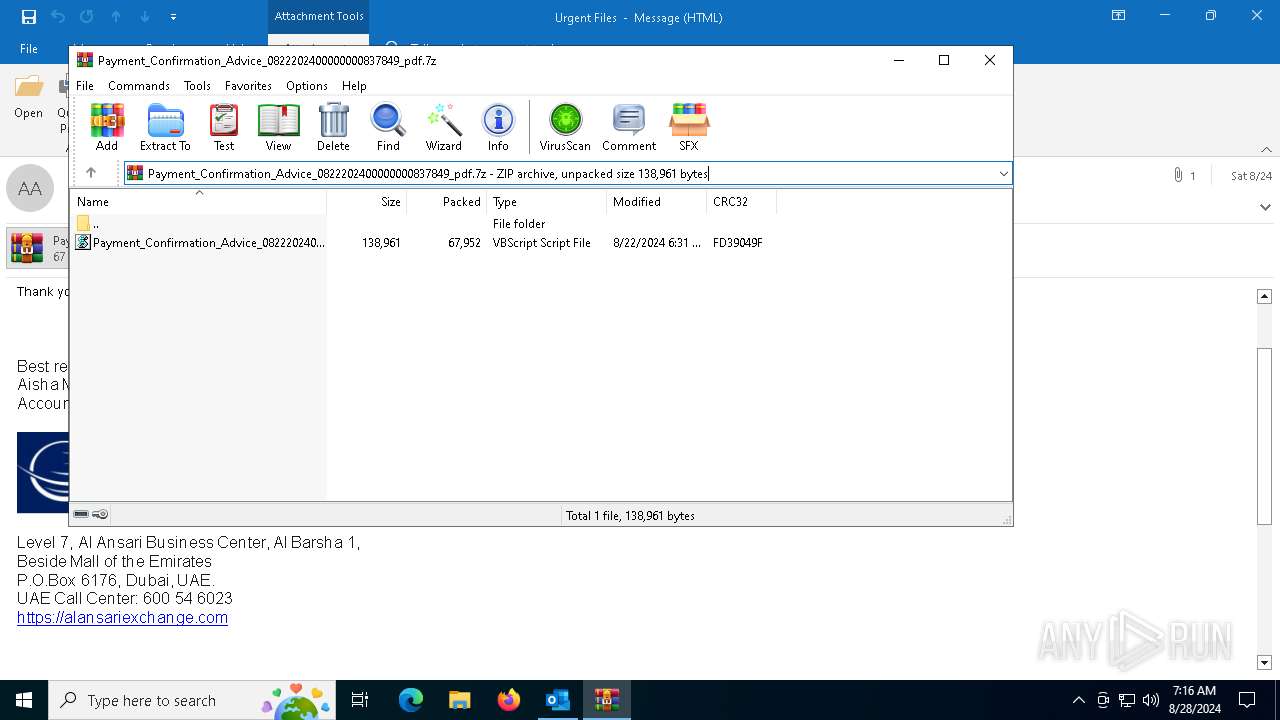
| File name: | 2024-08-24-GuLoader-for-Remcos-RAT-malspam-1614-UTC.eml |
| Full analysis: | https://app.any.run/tasks/d174ba55-68a4-4060-aac9-d85069b7a9f2 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | August 28, 2024, 07:14:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | F2182DDB031871721473E004828CC7EC |
| SHA1: | 115A283DA318A72A9C6F328F772DC94146ACC1AF |
| SHA256: | 91B1AABA570CF9ACA6DB024388B5AD5607C21B59EE9C1CC5D2B57FDB956E03B0 |
| SSDEEP: | 3072:Pobyd4RcT3aMnun+5kMtPHKcteesCZ4ScbNvC3wmCtYrQq:Abydfjnd2gqcpzZJ2DC0q |
MALICIOUS
GULOADER has been detected
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4996)
Changes the autorun value in the registry
- reg.exe (PID: 6324)
REMCOS has been detected
- wab.exe (PID: 6420)
- wab.exe (PID: 6420)
- wab.exe (PID: 6420)
Scans artifacts that could help determine the target
- wab.exe (PID: 3800)
Actions looks like stealing of personal data
- wab.exe (PID: 3800)
- wab.exe (PID: 1116)
- wab.exe (PID: 3568)
Steals credentials from Web Browsers
- wab.exe (PID: 3568)
Uses NirSoft utilities to collect credentials
- wab.exe (PID: 3568)
Connects to the CnC server
- wab.exe (PID: 6420)
REMCOS has been detected (SURICATA)
- wab.exe (PID: 6420)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6124)
- wab.exe (PID: 6420)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4996)
- powershell.exe (PID: 6372)
- wab.exe (PID: 6420)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2024)
- powershell.exe (PID: 6372)
The process executes VB scripts
- WinRAR.exe (PID: 6124)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2024)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4996)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4996)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 4996)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2368)
Reads the date of Windows installation
- wab.exe (PID: 6420)
Checks Windows Trust Settings
- wab.exe (PID: 6420)
Application launched itself
- wab.exe (PID: 6420)
Contacting a server suspected of hosting an CnC
- wab.exe (PID: 6420)
Writes files like Keylogger logs
- wab.exe (PID: 6420)
Checks for external IP
- wab.exe (PID: 6420)
Connects to unusual port
- wab.exe (PID: 6420)
INFO
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4996)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4996)
Disables trace logs
- powershell.exe (PID: 6372)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 4996)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 2024)
- powershell.exe (PID: 6372)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6124)
- wab.exe (PID: 3800)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4996)
Checks supported languages
- wab.exe (PID: 6420)
- wab.exe (PID: 1116)
- wab.exe (PID: 3568)
- wab.exe (PID: 3800)
Checks proxy server information
- wab.exe (PID: 6420)
- powershell.exe (PID: 6372)
Reads the computer name
- wab.exe (PID: 6420)
- wab.exe (PID: 3568)
- wab.exe (PID: 1116)
- wab.exe (PID: 3800)
Process checks computer location settings
- wab.exe (PID: 6420)
Reads the machine GUID from the registry
- wab.exe (PID: 6420)
- wab.exe (PID: 3568)
- wab.exe (PID: 1116)
Reads the software policy settings
- wab.exe (PID: 6420)
Reads Environment values
- wab.exe (PID: 6420)
Creates files or folders in the user directory
- wab.exe (PID: 6420)
Create files in a temporary directory
- wab.exe (PID: 1116)
- wab.exe (PID: 3568)
- wab.exe (PID: 3800)
Creates files in the program directory
- wab.exe (PID: 6420)
Mpress packer has been detected
- wab.exe (PID: 6420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
147
Monitored processes
17
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | "C:\Program Files (x86)\windows mail\wab.exe" /stext "C:\Users\admin\AppData\Local\Temp\rnqrkdkcbtvayl" | C:\Program Files (x86)\Windows Mail\wab.exe | wab.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\skaberevners.Dam && echo t" | C:\Windows\SysWOW64\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2024 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6124.9704\Payment_Confirmation_Advice_0822202400000000837849_pdf.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | "C:\Windows\System32\cmd.exe" /c REG ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /f /v "Startup key" /t REG_EXPAND_SZ /d "%Idigbo% -w 1 $Mycoprotein=(Get-ItemProperty -Path 'HKCU:\Oversanselig\').Penta;%Idigbo% ($Mycoprotein)" | C:\Windows\SysWOW64\cmd.exe | — | wab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "D418CEC6-01EB-4D54-BBE7-55753E3EBBBE" "430A3DC0-9A33-43EB-8488-76E6CD6536FD" "3448" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\2024-08-24-GuLoader-for-Remcos-RAT-malspam-1614-UTC.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3568 | "C:\Program Files (x86)\windows mail\wab.exe" /stext "C:\Users\admin\AppData\Local\Temp\xrfoqso" | C:\Program Files (x86)\Windows Mail\wab.exe | wab.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3784 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\skaberevners.Dam && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3800 | "C:\Program Files (x86)\windows mail\wab.exe" /stext "C:\Users\admin\AppData\Local\Temp\hllhrlzjol" | C:\Program Files (x86)\Windows Mail\wab.exe | wab.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
39 119
Read events
38 569
Write events
471
Delete events
79
Modification events
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\3448 |
| Operation: | write | Name: | 0 |
Value: 0B0E1067474C927461B544BF1323986FC3FF0B230046FA92E4839FA3BEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511F81AD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (3448) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
12
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\DBD81C9C.tmp | image | |
MD5:D91616DCBEC02160C89A2A4FBF58251B | SHA256:23C8AFD998C4B624EEB65FAC986EA1621F4A08DD277617FF9214A55A48099F85 | |||
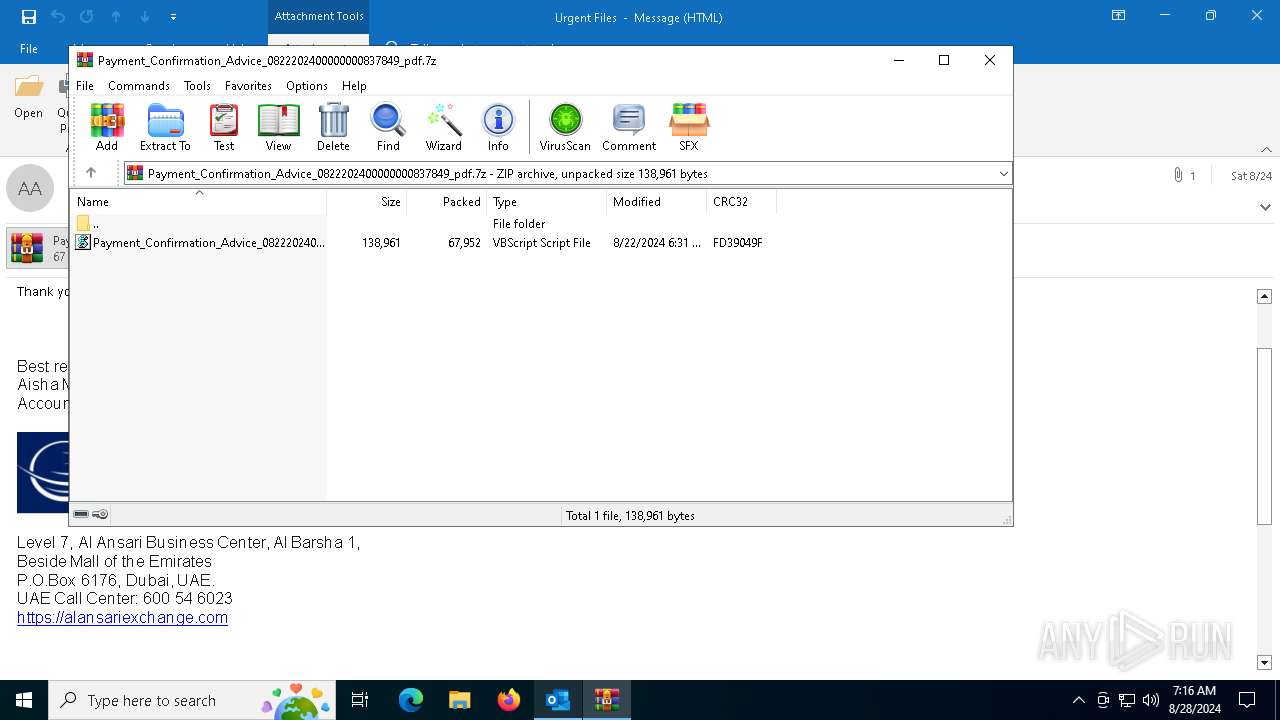
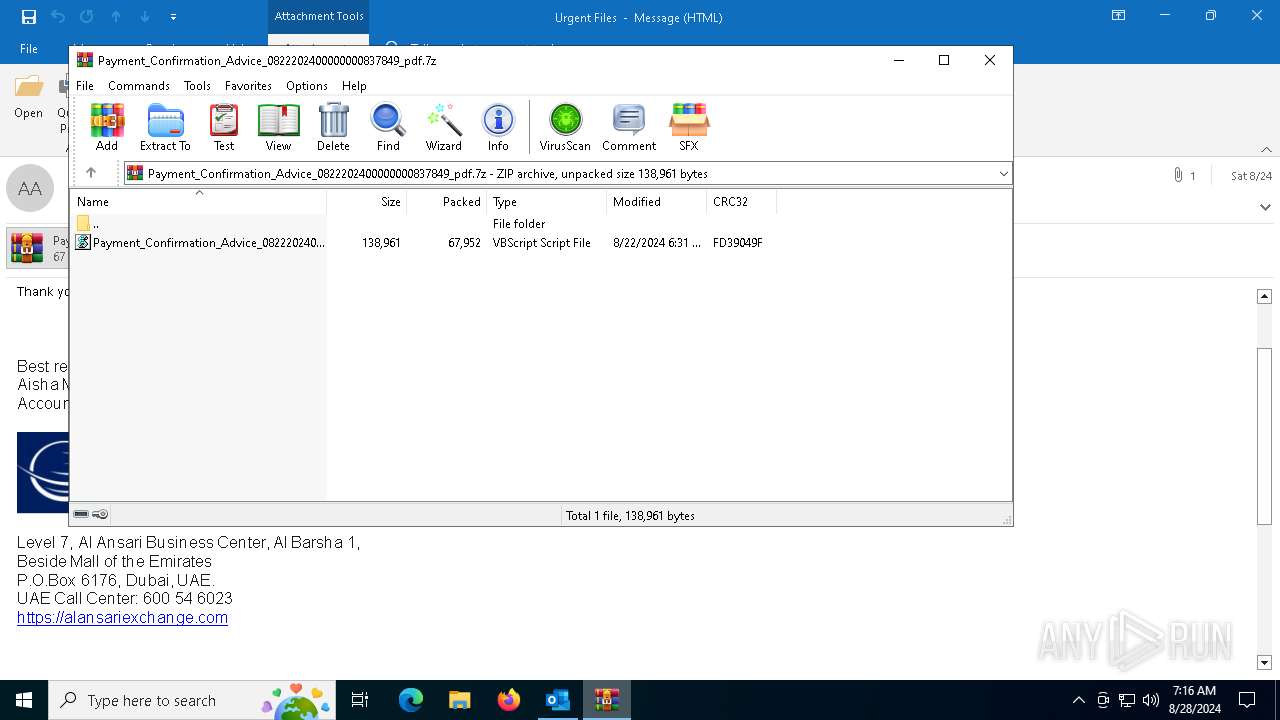
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\6DVF4MVO\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z | compressed | |
MD5:14E1E14803CA02BE8EC0742F012D96DD | SHA256:F1C480F30C73C638CC23C896DE021DAFA5568AE0D0169C8573F910CF2C1718F4 | |||
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_740CD612A979F545A139353E9881E108.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\6DVF4MVO\Payment_Confirmation_Advice_0822202400000000837849_pdf (002).7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\6DVF4MVO\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3568 | wab.exe | C:\Users\admin\AppData\Local\Temp\bhv6F96.tmp | — | |
MD5:— | SHA256:— | |||
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:365EC39B04CFAF3BBF5C5952ECEF7800 | SHA256:1162A6024042E0EF4795E7E318E52943DA3066AAB90E1E5CB23421BE5835D361 | |||
| 3448 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5ati5zjg.0de.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
130
DNS requests
43
Threats
43
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6964 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3448 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6964 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6420 | wab.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
3832 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 304 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6872 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6856 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3448 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6872 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3448 | OUTLOOK.EXE | 23.48.23.54:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
3448 | OUTLOOK.EXE | 52.111.236.4:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3448 | OUTLOOK.EXE | 13.89.179.11:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
softiq.ro |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
6420 | wab.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
6420 | wab.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
3 ETPRO signatures available at the full report