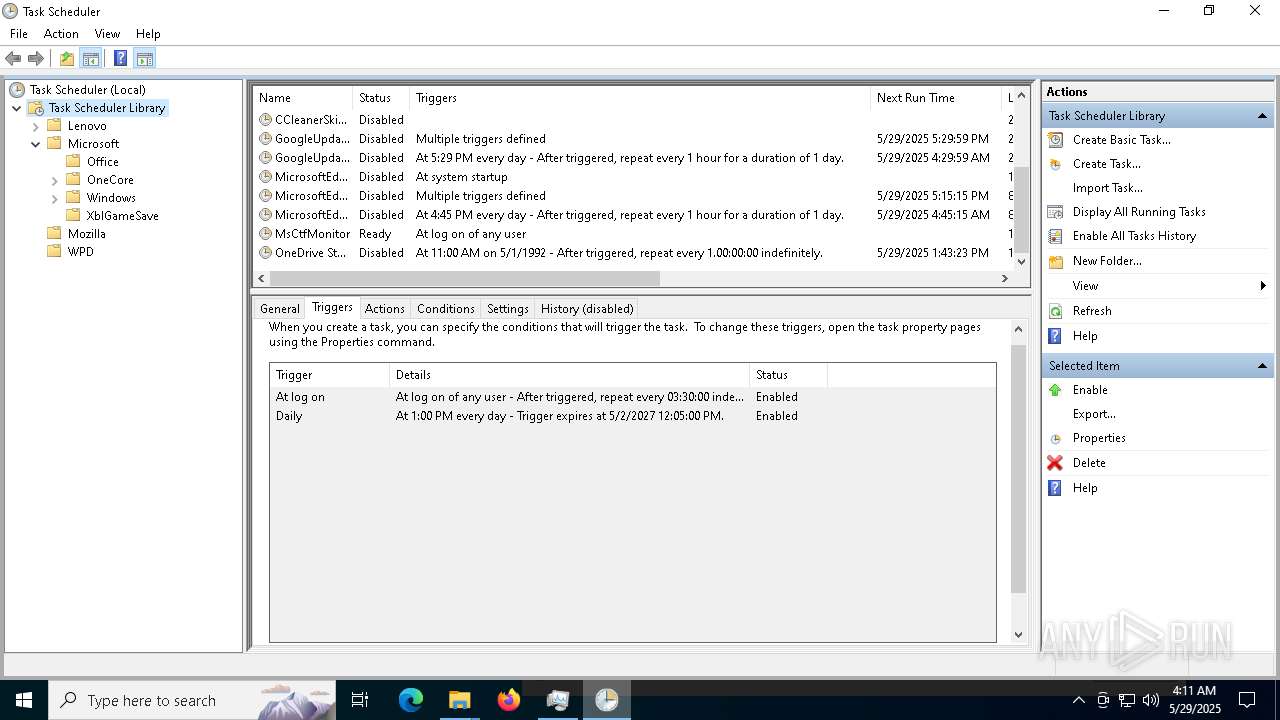
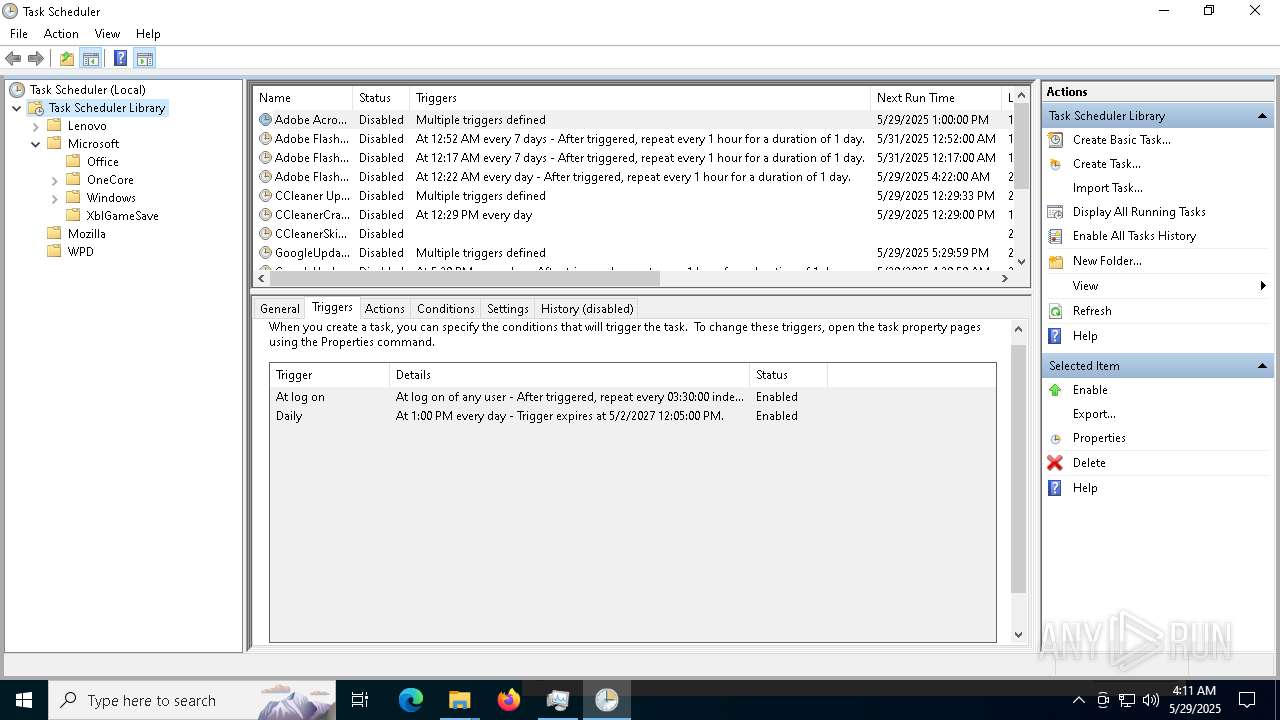
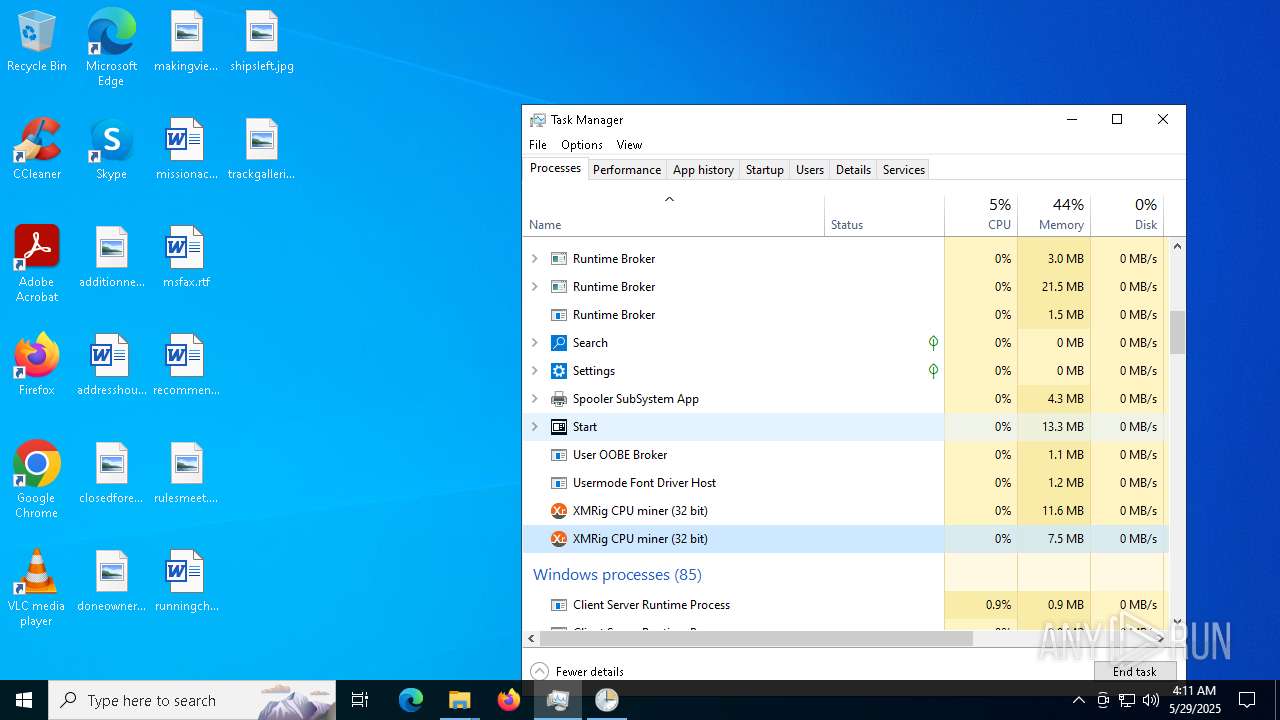
| File name: | Photo.scr |
| Full analysis: | https://app.any.run/tasks/1be272db-a31f-43aa-9ccc-fd7e6868035e |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
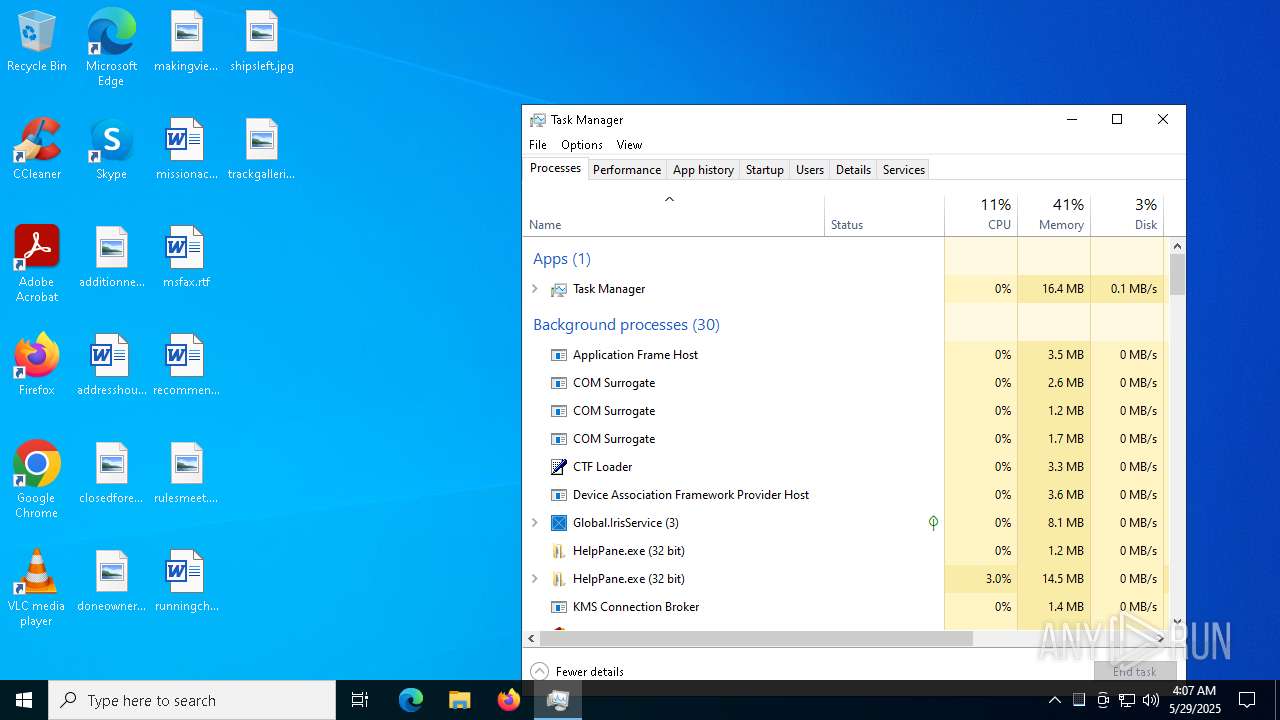
| Analysis date: | May 29, 2025, 04:07:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 5616A3471565D34D779B5B3D0520BB70 |
| SHA1: | 42DF726156BEE4A54EA328BD72A659602AB7D03E |
| SHA256: | 9194B57673209C8534888F61B0CDEFA34F463AE50CD78F72AB2B3348220BAAF9 |
| SSDEEP: | 98304:dqMq5w41tP2IHHAHuw4lUSlulY+fWEoOB/xsmCDGID95NM+x48rzPH9ATnVlYLYv:heuGME+pGoSYe4k |
MALICIOUS
BITTORRENT has been detected (SURICATA)
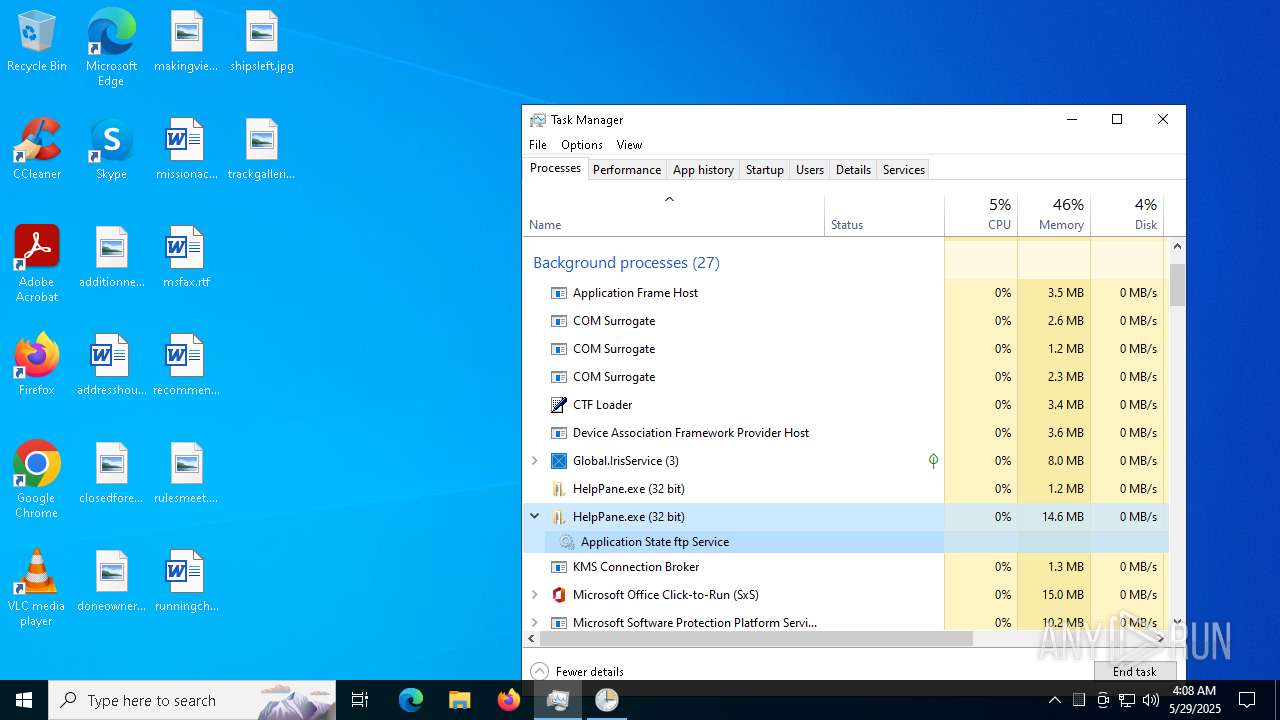
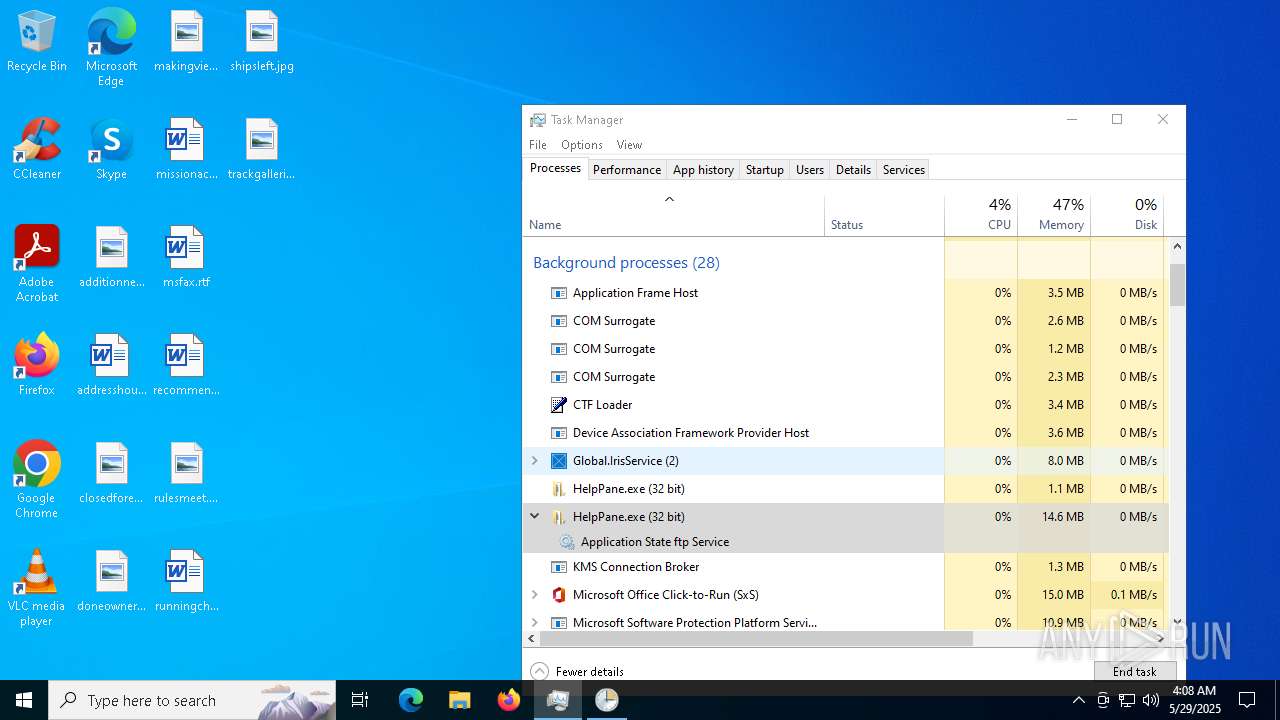
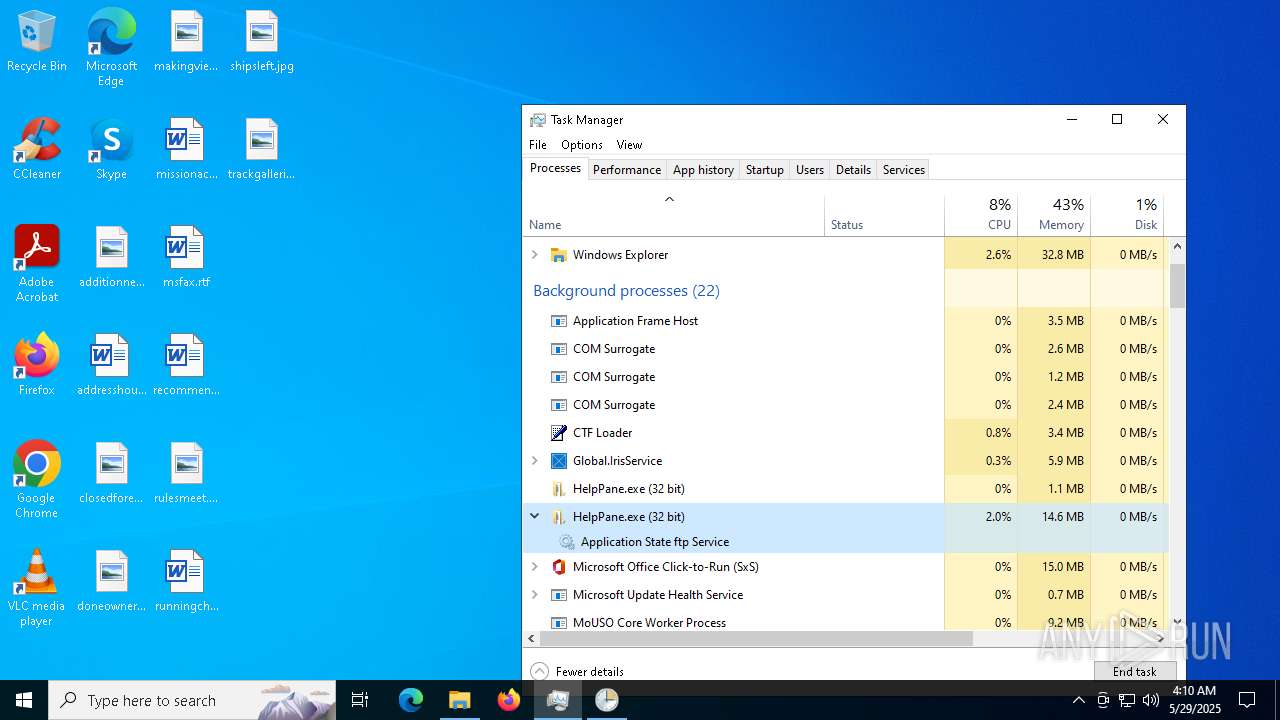
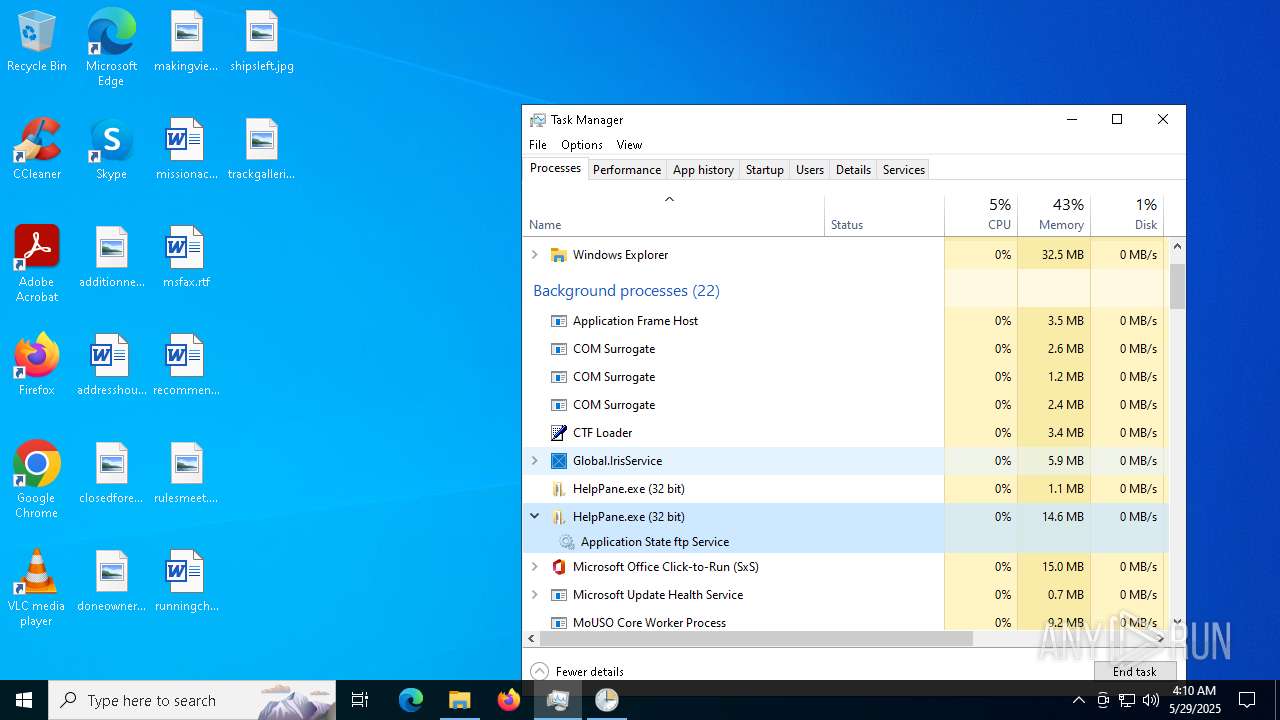
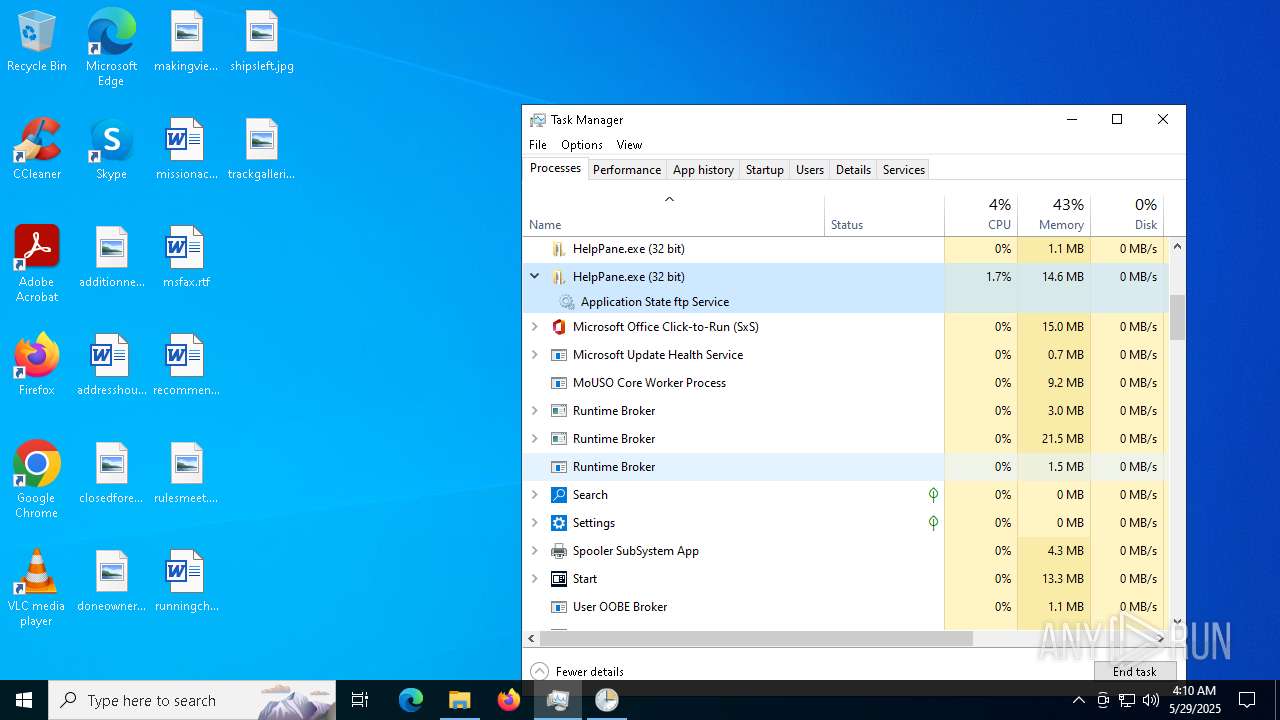
- HelpPane.exe (PID: 2516)
MOZI has been detected (SURICATA)
- HelpPane.exe (PID: 2516)
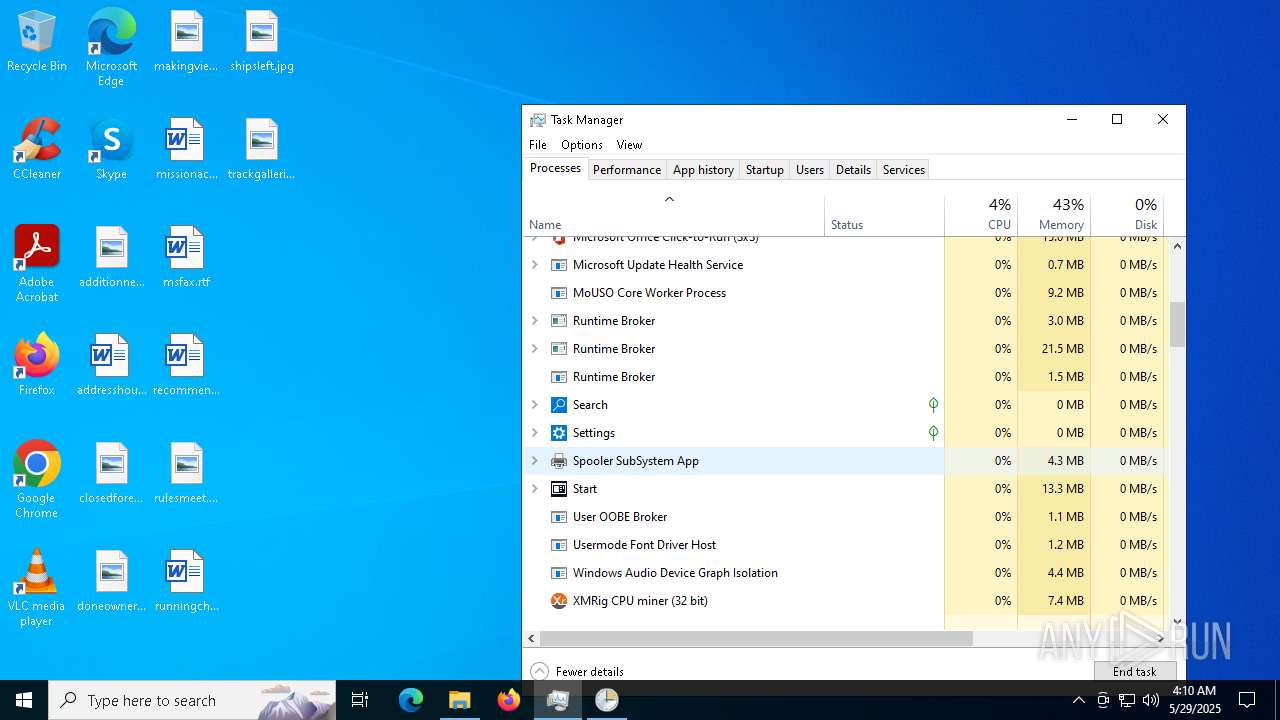
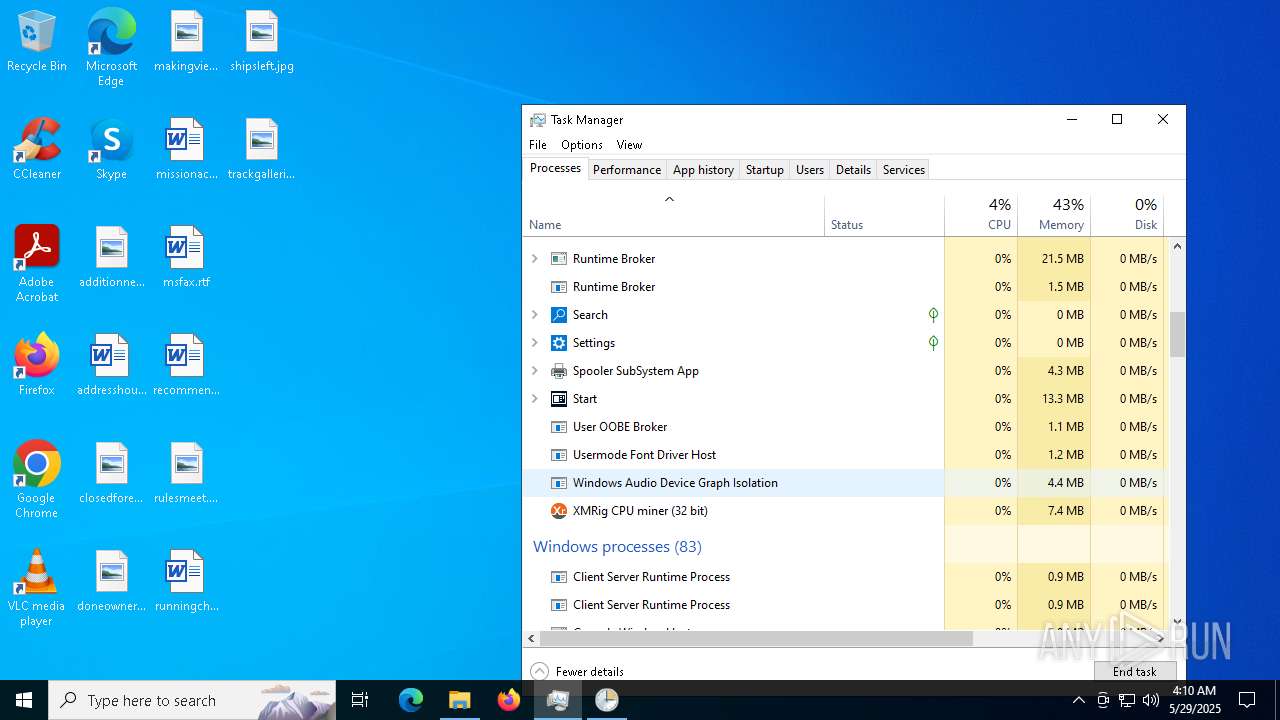
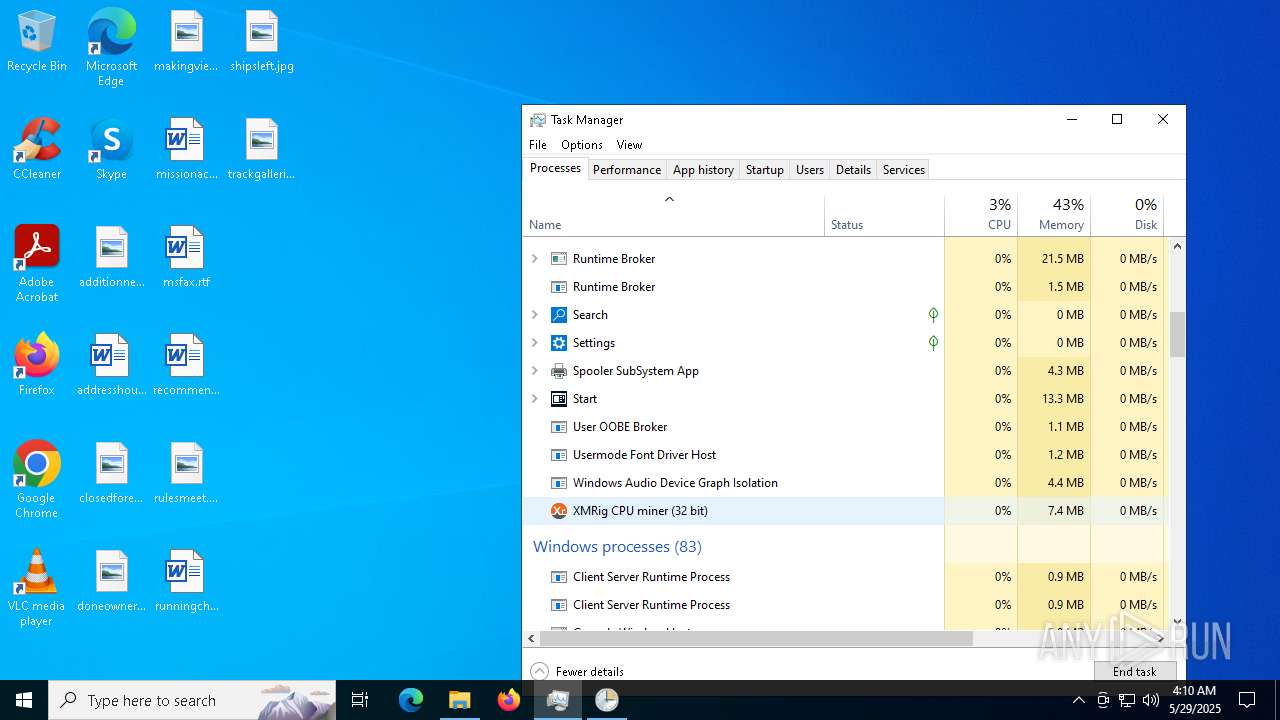
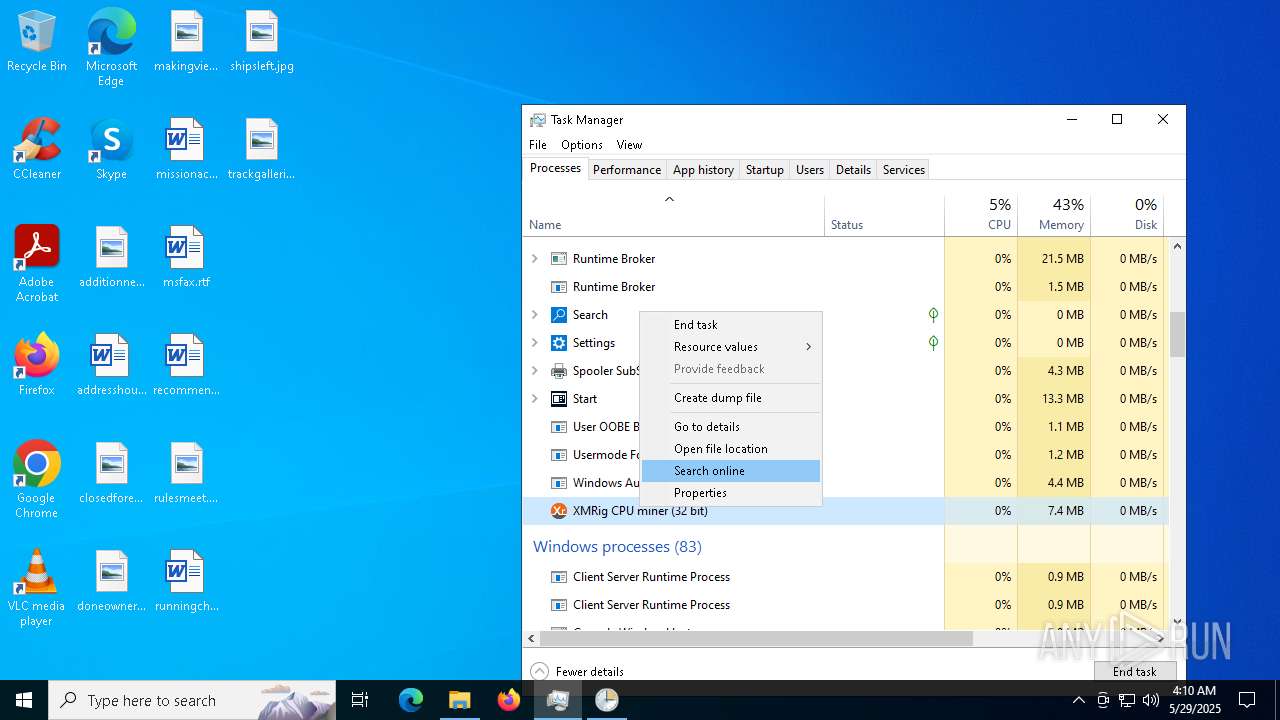
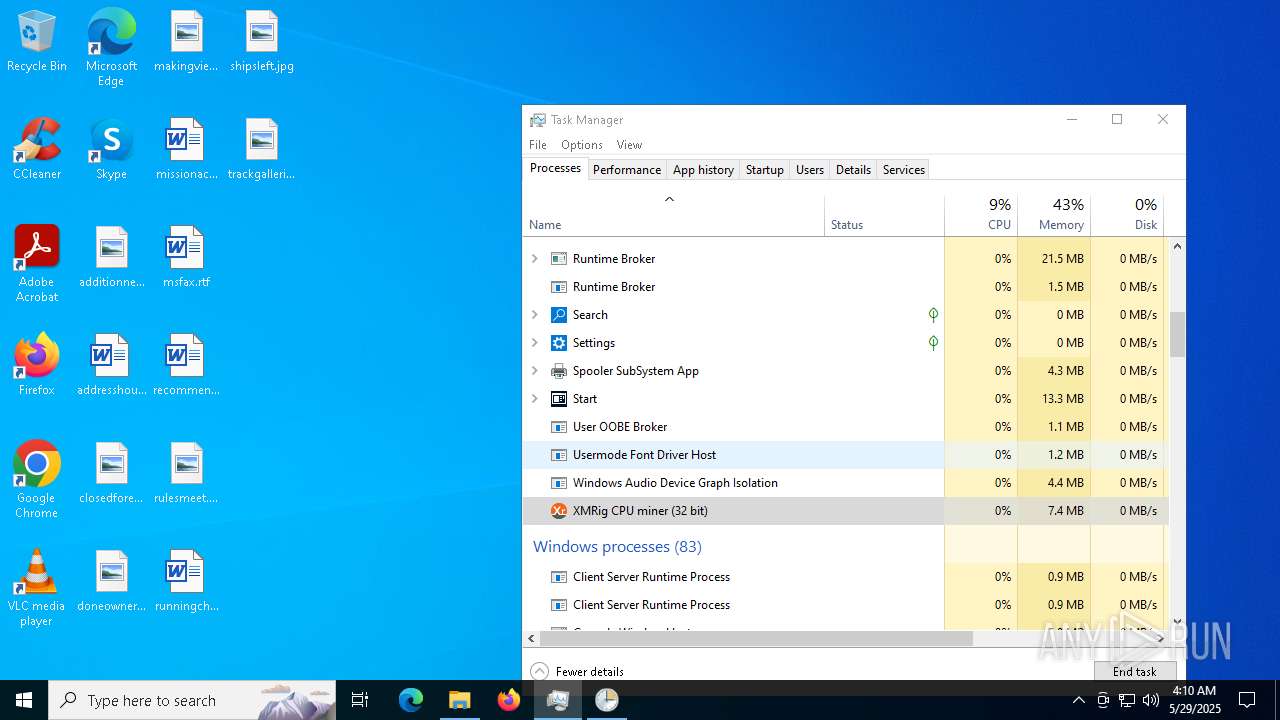
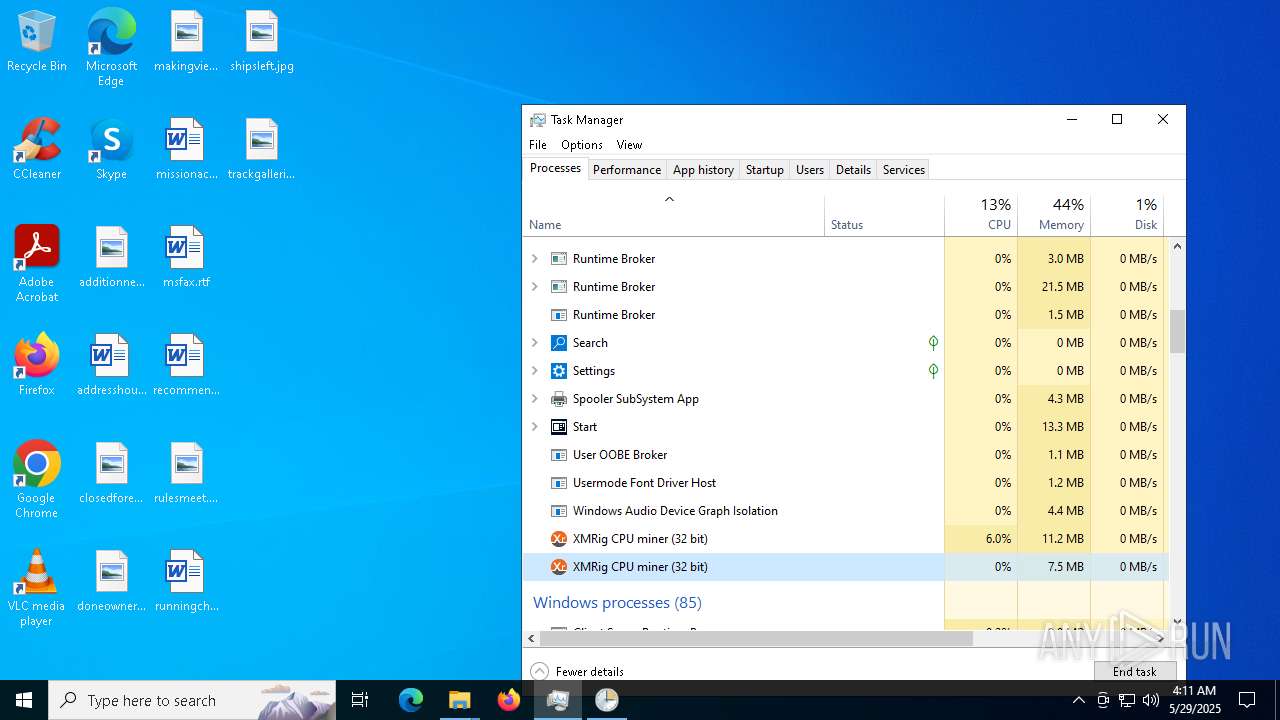
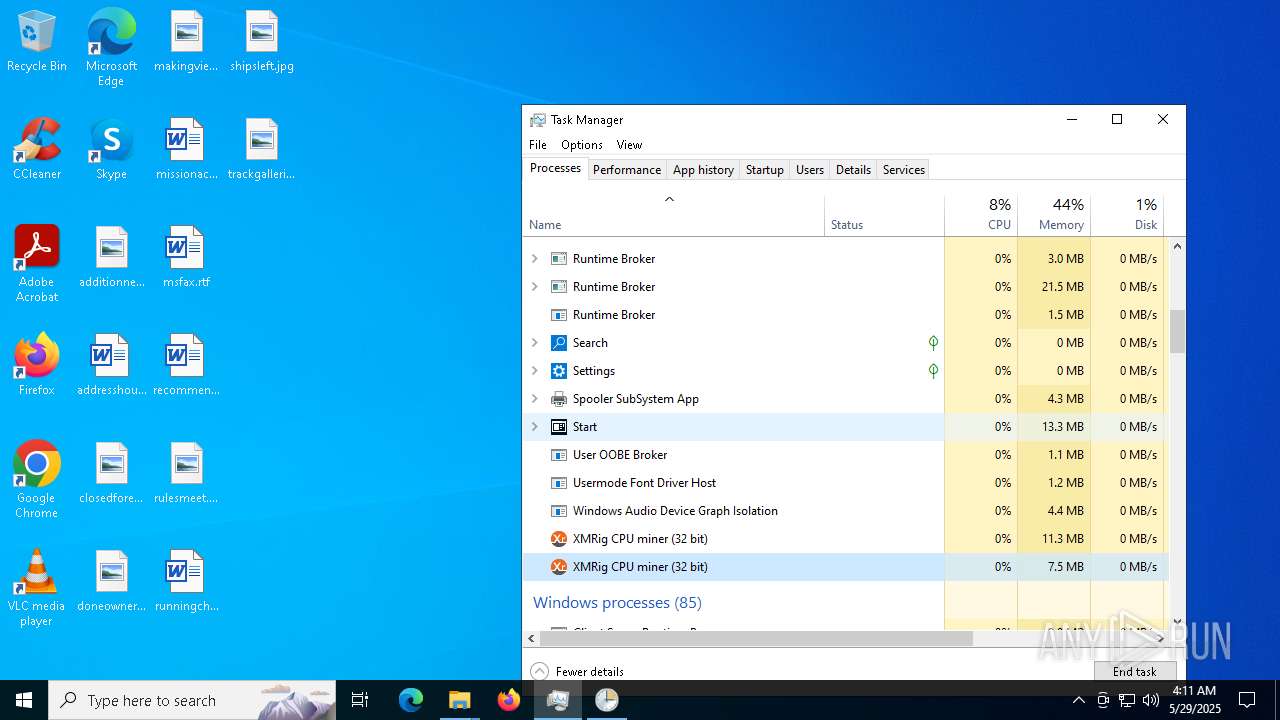
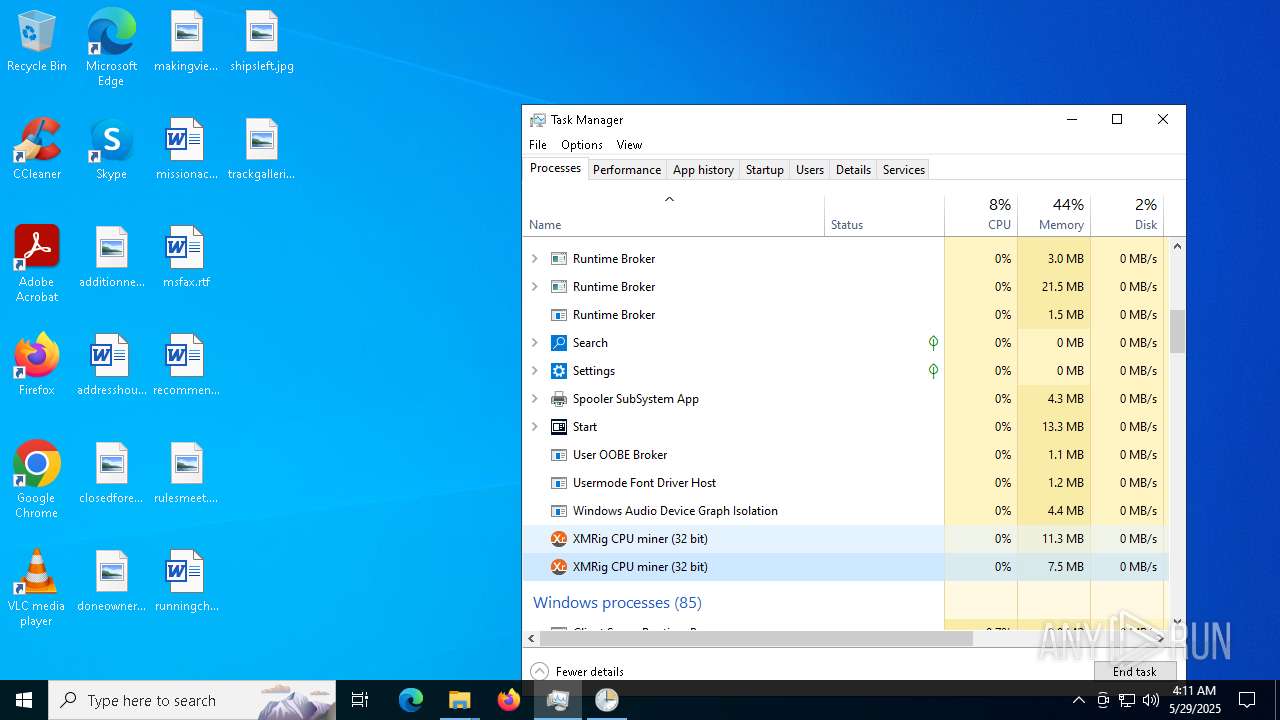
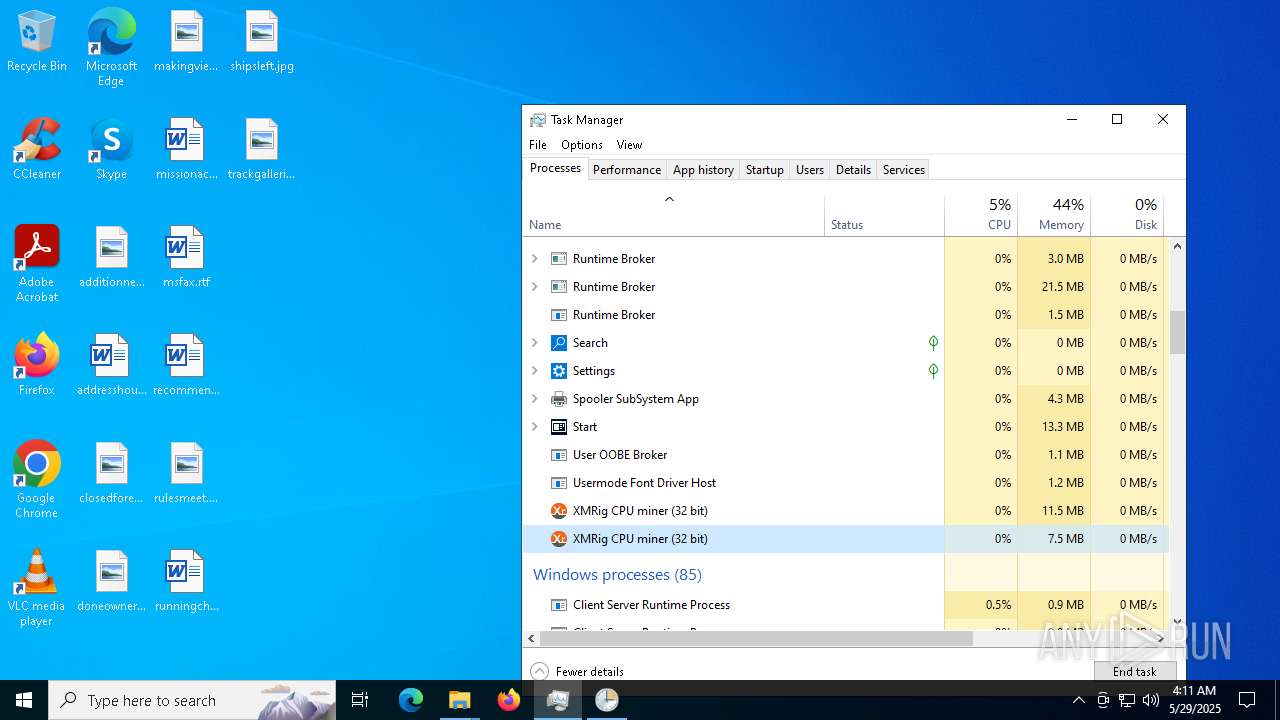
XMRIG has been detected (YARA)
- xmrig.exe (PID: 2320)
- xmrig.exe (PID: 8152)
- xmrig.exe (PID: 6700)
SUSPICIOUS
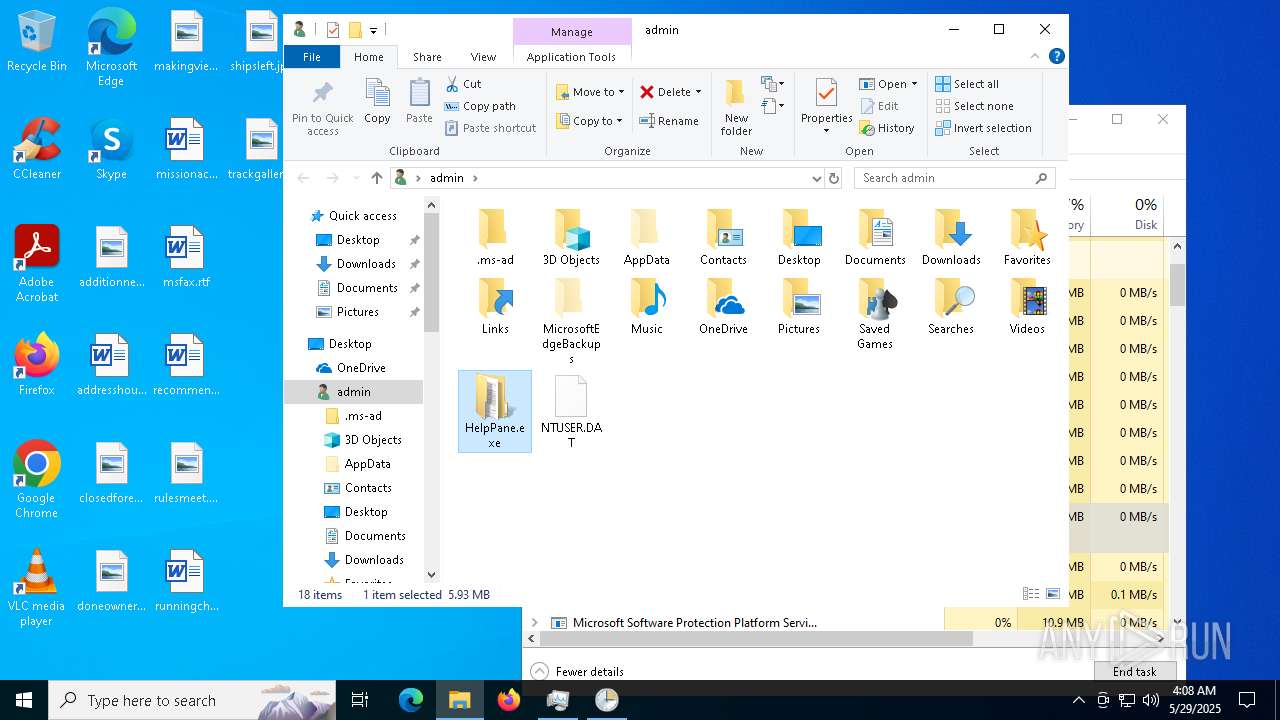
Process drops legitimate windows executable
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1228)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
- Photo.scr.exe (PID: 8000)
- Photo.scr.exe (PID: 7840)
Process drops python dynamic module
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1228)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
- Photo.scr.exe (PID: 8000)
- Photo.scr.exe (PID: 7840)
Executable content was dropped or overwritten
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1228)
- cmd.exe (PID: 1116)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 5408)
- cmd.exe (PID: 5176)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
- Photo.scr.exe (PID: 8000)
- Photo.scr.exe (PID: 7840)
Application launched itself
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1812)
- Photo.scr.exe (PID: 1228)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 1120)
- HelpPane.exe (PID: 7828)
- Photo.scr.exe (PID: 7840)
- Photo.scr.exe (PID: 2084)
- Photo.scr.exe (PID: 8000)
The process drops C-runtime libraries
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1228)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
- Photo.scr.exe (PID: 8000)
- Photo.scr.exe (PID: 7840)
Reads security settings of Internet Explorer
- Photo.scr.exe (PID: 1812)
- HelpPane.exe (PID: 1120)
Starts CMD.EXE for commands execution
- Photo.scr.exe (PID: 6992)
- HelpPane.exe (PID: 2516)
- Photo.scr.exe (PID: 4404)
- HelpPane.exe (PID: 7860)
The executable file from the user directory is run by the CMD process
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 6516)
Executes as Windows Service
- HelpPane.exe (PID: 5408)
- spoolsv.exe (PID: 5380)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 680)
Uses NETSH.EXE to add a firewall rule or allowed programs
- HelpPane.exe (PID: 2516)
Contacting a server suspected of hosting an CnC
- HelpPane.exe (PID: 2516)
Potential Corporate Privacy Violation
- HelpPane.exe (PID: 2516)
There is functionality for taking screenshot (YARA)
- HelpPane.exe (PID: 2516)
Connects to FTP
- HelpPane.exe (PID: 2516)
Connects to unusual port
- HelpPane.exe (PID: 2516)
INFO
Create files in a temporary directory
- Photo.scr.exe (PID: 4120)
- HelpPane.exe (PID: 4776)
- Photo.scr.exe (PID: 1228)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
Checks supported languages
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1812)
- Photo.scr.exe (PID: 1228)
- Photo.scr.exe (PID: 6992)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 7048)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 4724)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 2516)
- xmrig.exe (PID: 2320)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
- HelpPane.exe (PID: 1120)
- HelpPane.exe (PID: 7860)
The sample compiled with english language support
- Photo.scr.exe (PID: 4120)
- Photo.scr.exe (PID: 1228)
- HelpPane.exe (PID: 4776)
- HelpPane.exe (PID: 6516)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 616)
- HelpPane.exe (PID: 7828)
- Photo.scr.exe (PID: 7840)
- Photo.scr.exe (PID: 8000)
Reads the machine GUID from the registry
- Photo.scr.exe (PID: 1812)
- Photo.scr.exe (PID: 6992)
- HelpPane.exe (PID: 7048)
- HelpPane.exe (PID: 4724)
- HelpPane.exe (PID: 2516)
- HelpPane.exe (PID: 1120)
- HelpPane.exe (PID: 7860)
Reads the computer name
- Photo.scr.exe (PID: 1812)
- Photo.scr.exe (PID: 6992)
- HelpPane.exe (PID: 7048)
- HelpPane.exe (PID: 4724)
- HelpPane.exe (PID: 2516)
- xmrig.exe (PID: 2320)
- HelpPane.exe (PID: 1120)
- HelpPane.exe (PID: 7860)
Process checks computer location settings
- Photo.scr.exe (PID: 1812)
- HelpPane.exe (PID: 1120)
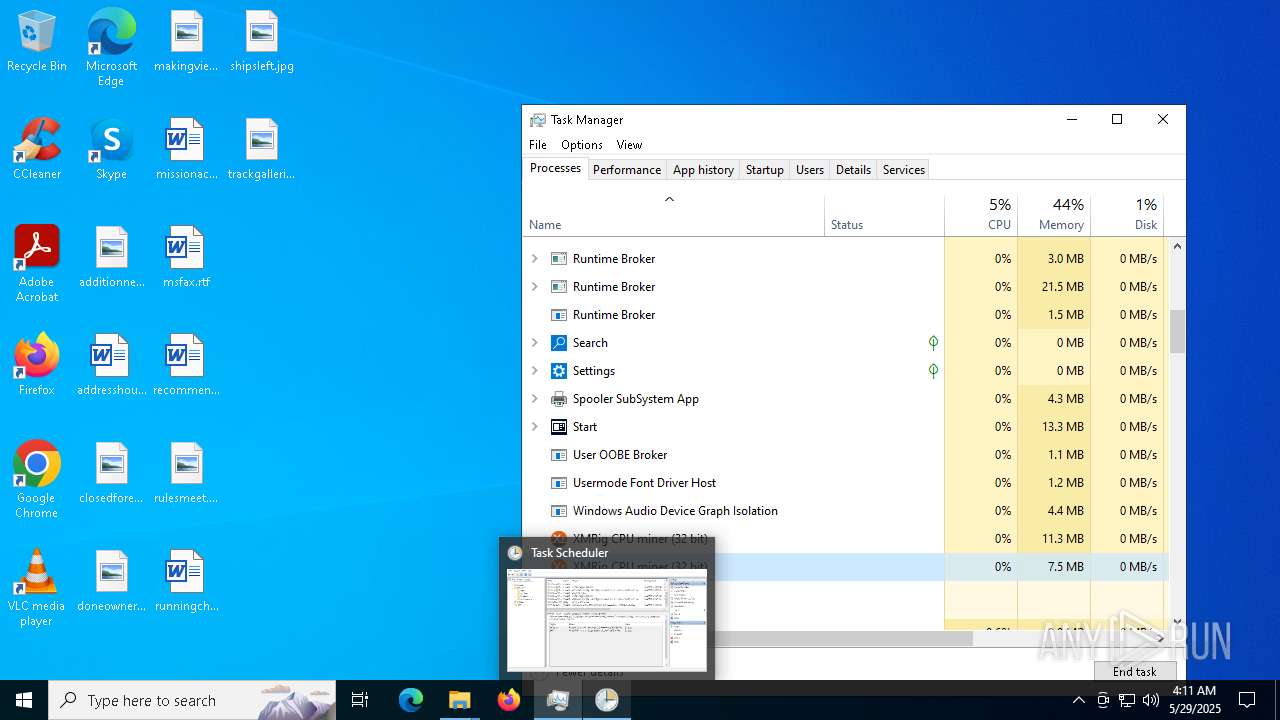
Manual execution by a user
- Taskmgr.exe (PID: 304)
- Taskmgr.exe (PID: 2616)
- mmc.exe (PID: 656)
- mmc.exe (PID: 4736)
- HelpPane.exe (PID: 616)
- Photo.scr.exe (PID: 7840)
- xmrig.exe (PID: 8152)
- xmrig.exe (PID: 6700)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 2616)
- mmc.exe (PID: 656)
PyInstaller has been detected (YARA)
- HelpPane.exe (PID: 5408)
- HelpPane.exe (PID: 2516)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2108)
Reads the software policy settings
- slui.exe (PID: 780)
UPX packer has been detected
- HelpPane.exe (PID: 2516)
- xmrig.exe (PID: 2320)
- xmrig.exe (PID: 6700)
- xmrig.exe (PID: 8152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:04 14:43:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 125952 |
| InitializedDataSize: | 122368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x79d3 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
193
Monitored processes
55
Malicious processes
11
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\HelpPane.exe --startup auto install | C:\Windows\SysWOW64\cmd.exe | — | Photo.scr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Users\admin\HelpPane.exe" | C:\Users\admin\HelpPane.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 656 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | C:\WINDOWS\system32\cmd.exe /c taskkill /pid 2732 /f | C:\Windows\SysWOW64\cmd.exe | — | HelpPane.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\HelpPane.exe start | C:\Windows\SysWOW64\cmd.exe | — | Photo.scr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
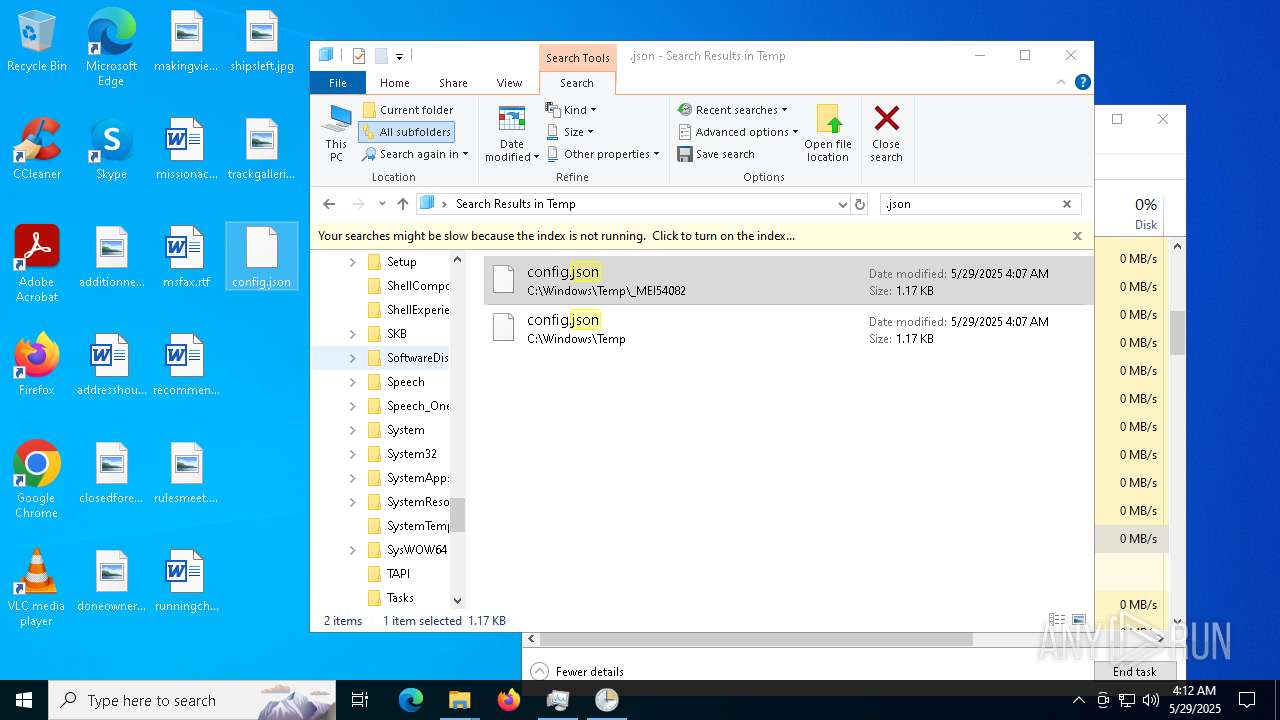
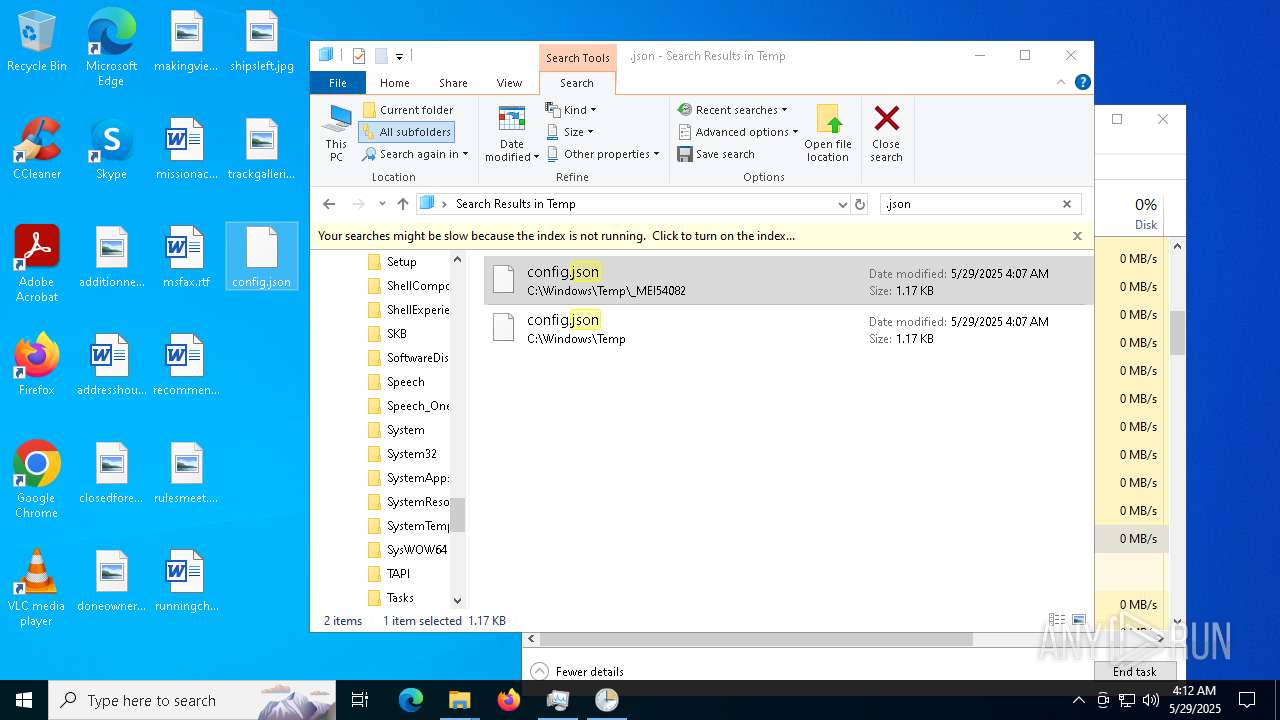
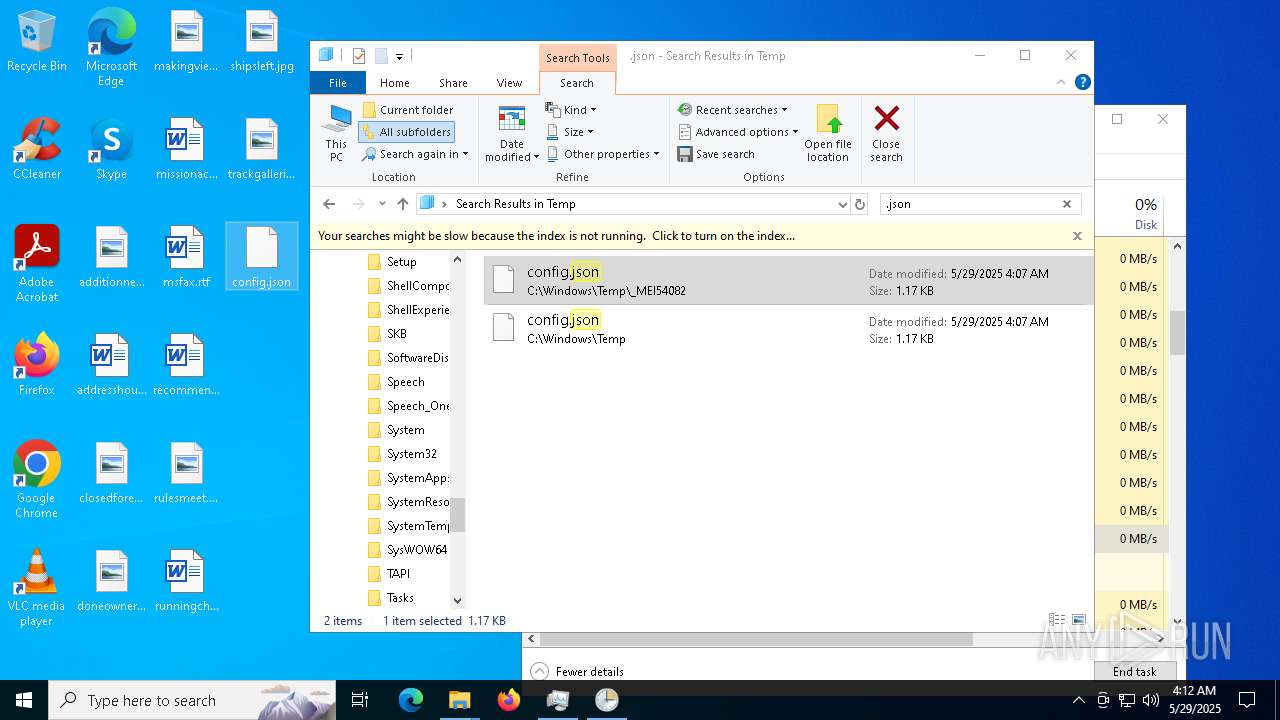
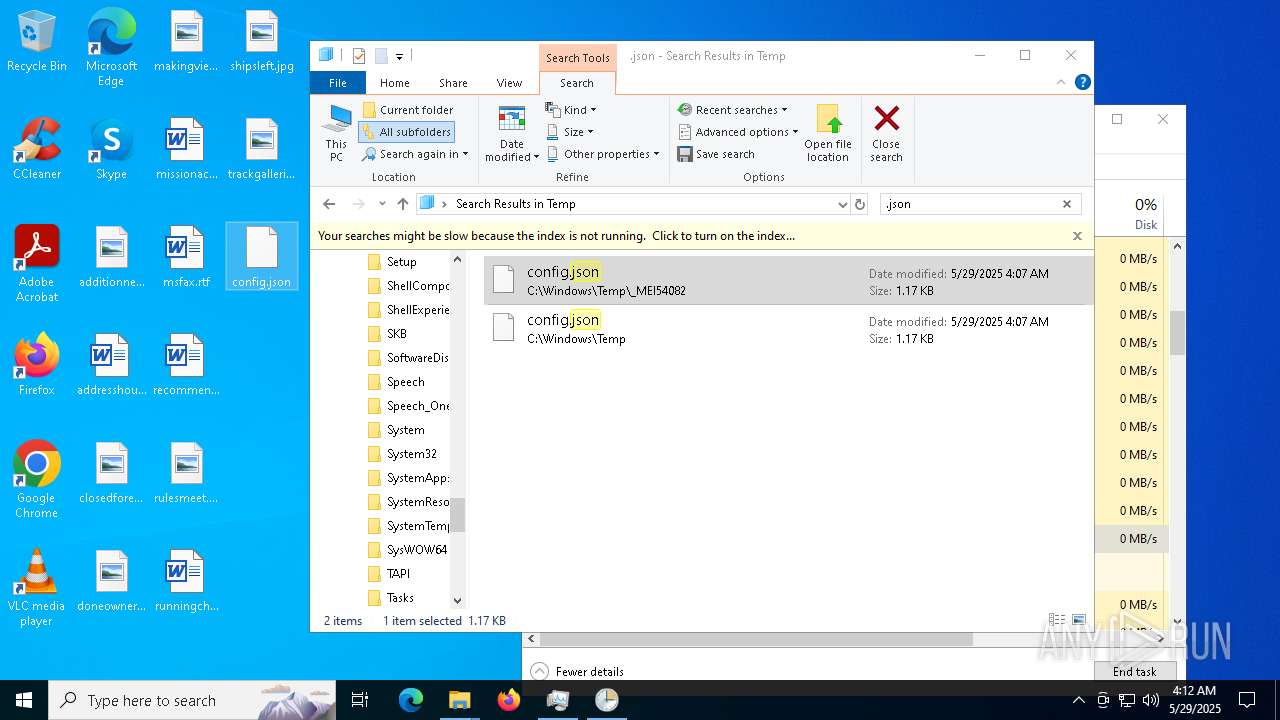
| 1056 | C:\WINDOWS\system32\cmd.exe /c copy /y C:\WINDOWS\TEMP\_MEI54~1\\config.json C:\WINDOWS\TEMP\config.json | C:\Windows\SysWOW64\cmd.exe | — | HelpPane.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | C:\WINDOWS\system32\cmd.exe /c copy /y C:\Users\admin\AppData\Local\Temp\Photo.scr.exe C:\Users\admin\HelpPane.exe | C:\Windows\SysWOW64\cmd.exe | Photo.scr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | "C:\Users\admin\HelpPane.exe" | C:\Users\admin\HelpPane.exe | — | HelpPane.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
10 404
Read events
10 320
Write events
83
Delete events
1
Modification events
| (PID) Process: | (2616) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (2616) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA043AF67F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AA043AF67F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA043AF67F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA043AF67F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB043AF67F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB043AF67F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB043AF67F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AA043AF67F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB043AF67F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB043AF67F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB043AF67F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB043AF67F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB043AF67F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC043AF67F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA043AF67F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA043AF67F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC043AF67F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC043AF67F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC043AF67F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC043AF67F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC043AF67F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC043AF67F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB043AF67F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA043AF67F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD043AF67F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD043AF67F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD043AF67F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA043AF67F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB043AF67F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA043AF67F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB043AF67F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB043AF67F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB043AF67F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB043AF67F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA043AF67F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD043AF67F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE043AF67F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE043AF67F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE043AF67F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE043AF67F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (656) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\WINDOWS\Help\taskscheduler.chm | |||
| (PID) Process: | (656) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\WINDOWS\Help\taskscheduler.chm | |||
| (PID) Process: | (5380) spoolsv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Print\Printers |
| Operation: | write | Name: | DefaultSpoolDirectory |
Value: C:\Windows\system32\spool\PRINTERS | |||
| (PID) Process: | (5380) spoolsv.exe | Key: | HKEY_USERS\S-1-5-19\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Devices |
| Operation: | write | Name: | OneNote (Desktop) |
Value: winspool,nul: | |||
| (PID) Process: | (5380) spoolsv.exe | Key: | HKEY_USERS\S-1-5-19\SOFTWARE\Microsoft\Windows NT\CurrentVersion\PrinterPorts |
| Operation: | write | Name: | OneNote (Desktop) |
Value: winspool,nul:,15,45 | |||
| (PID) Process: | (5380) spoolsv.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Ports |
| Operation: | write | Name: | Ne00: |
Value: | |||
| (PID) Process: | (5380) spoolsv.exe | Key: | HKEY_USERS\S-1-5-19\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Devices |
| Operation: | write | Name: | Microsoft XPS Document Writer |
Value: winspool,Ne00: | |||
| (PID) Process: | (5380) spoolsv.exe | Key: | HKEY_USERS\S-1-5-19\SOFTWARE\Microsoft\Windows NT\CurrentVersion\PrinterPorts |
| Operation: | write | Name: | Microsoft XPS Document Writer |
Value: winspool,Ne00:,15,45 | |||
Executable files
227
Suspicious files
11
Text files
47
Unknown types
0
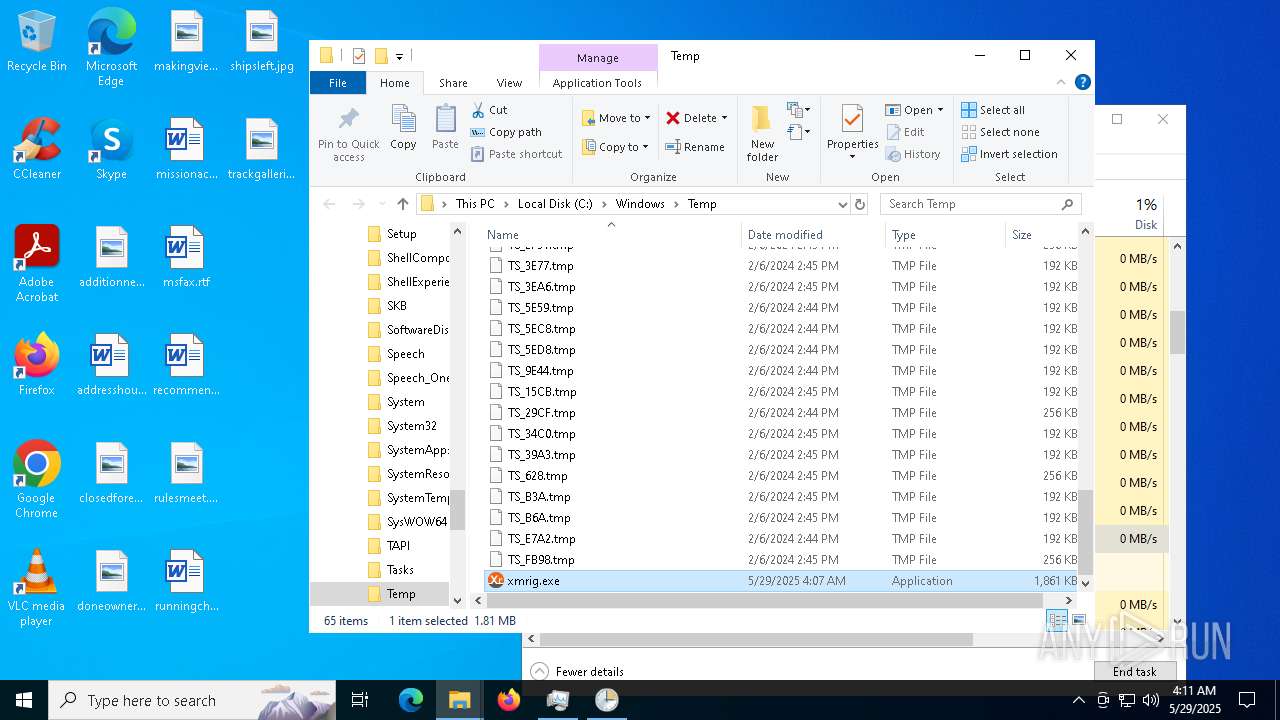
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\Microsoft.VC90.CRT.manifest | xml | |
MD5:BFB93876892CCA8E2AD0021585C34C8B | SHA256:0D060ED7C25159B7B75F16D449963BFD639C15B3C5280BC7897403268C2B9F35 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\_socket.pyd | executable | |
MD5:BE47363992C7DD90019276D35FA8DA76 | SHA256:BE10254B111713BEF20A13D561DE61CA3C74A34C64DDC5B10825C64AB2C46734 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\Crypto.Cipher._AES.pyd | executable | |
MD5:371397E80A55D432DA47311B8EF25317 | SHA256:C1A900615C9500C46B9602C30C53F299290B03632208EF1152AF8830AB73AD17 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\msvcm90.dll | executable | |
MD5:D34A527493F39AF4491B3E909DC697CA | SHA256:7A74DA389FBD10A710C294C2E914DC6F18E05F028F07958A2FA53AC44F0E4B90 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\_ctypes.pyd | executable | |
MD5:6CB8B560EFBC381651D2045F1571D7C8 | SHA256:6456FEA123E04BCEC8A8EED26160E1DF5482E69D187D3E1A0C428995472AC134 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\_win32sysloader.pyd | executable | |
MD5:B4A567D80CCC08FB1C7FBB765847AFDA | SHA256:DBB0F9C499A710BBC8BCDE4ECC3577A6C9548262D6CE4434ED5A0708CBC787DD | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\msvcp90.dll | executable | |
MD5:92EA2DB0E788894C43753C550216A886 | SHA256:9694756F43B20ABC50F95646C54E9E36CD6EDF8EED3DB846064567399F4E7566 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\perfmon.pyd | executable | |
MD5:EE813500A441B5FFDACD853E95BEE669 | SHA256:AC491704AF920BE0E503F0243D2D371E230622E213E9F082347B52C0A7B009C2 | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\ftpcrack.exe.manifest | xml | |
MD5:B5DEA49B86C5BB5D9CD8D64A09F70065 | SHA256:78B1160F6ADAB34D144AD19A0F4B83F83453F1E18460BBDFBE17AD354B62AF7D | |||
| 4120 | Photo.scr.exe | C:\Users\admin\AppData\Local\Temp\_MEI41202\bz2.pyd | executable | |
MD5:C9C00BC854A39E66B27787D188F9E8D7 | SHA256:29520DF660A5BBD704B9106A6650A66E4F5766B904D05F97146668D41DBF5839 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
403
DNS requests
85
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1388 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5344 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5796 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5796 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
dht.transmissionbt.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2516 | HelpPane.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT nodes reply |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |
2516 | HelpPane.exe | Malware Command and Control Activity Detected | ET MALWARE Mozi Botnet DHT Config Sent |