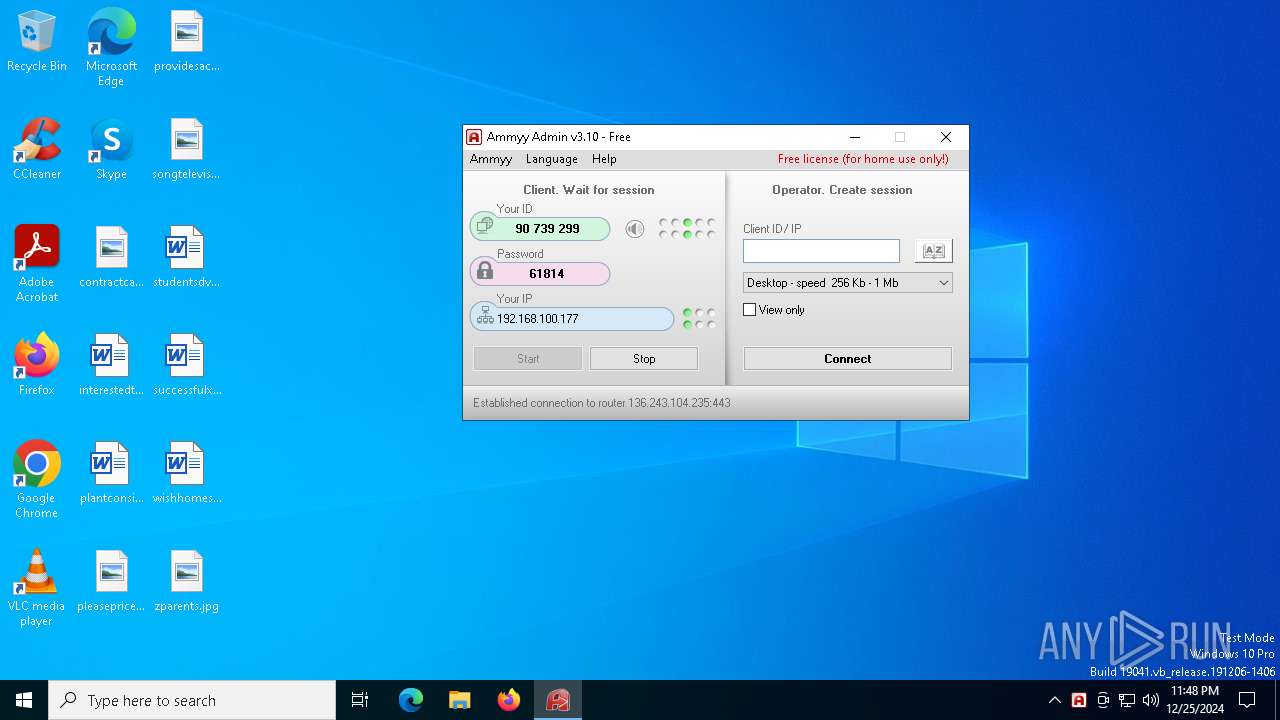
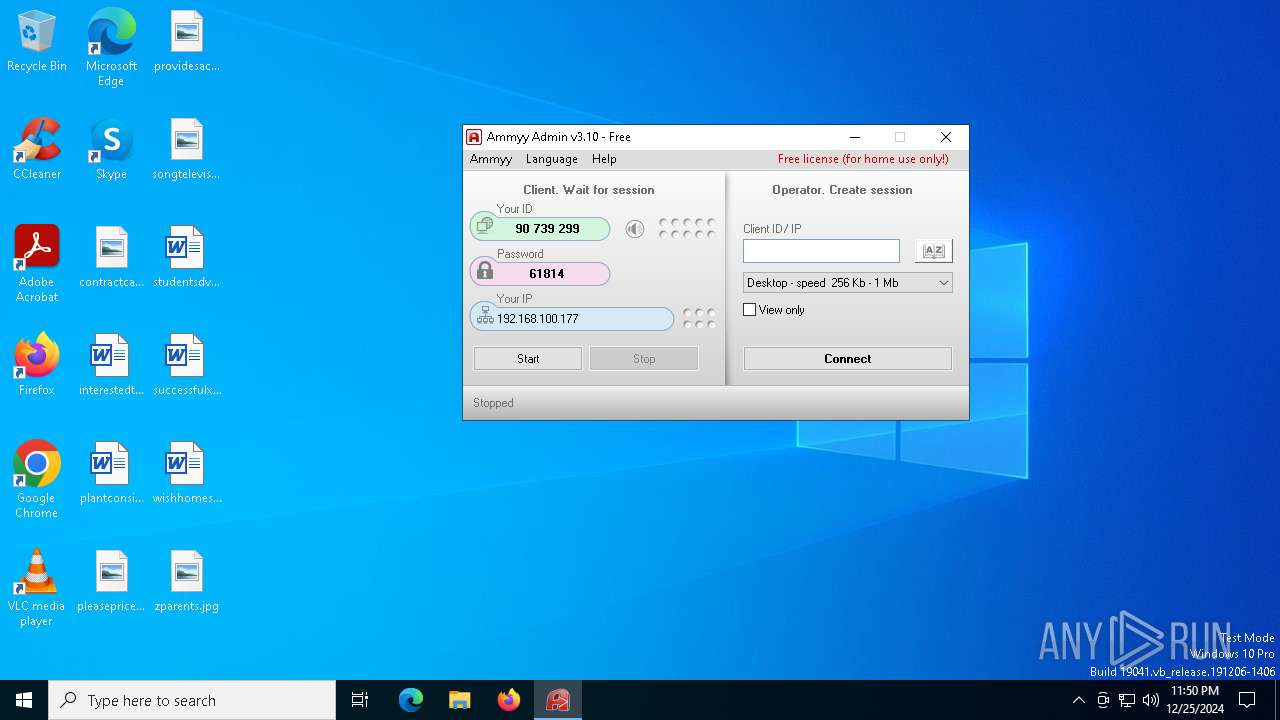
| File name: | AA_v3.exe |
| Full analysis: | https://app.any.run/tasks/5daf3285-e203-48ff-b910-243d77ffabc0 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 25, 2024, 23:48:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 3FA55A693BAE922AFE85688FA3A2FE9B |
| SHA1: | 45B1CFB8ED8A8FB6C2F05CD25C1023E307082F87 |
| SHA256: | 90BE232109392895DB0D0E0EA44300A546C190DA5C0C1DA39659A9701E16CEF9 |
| SSDEEP: | 98304:jJ8fZLihsTrX+VXwK2OobCygAi+WWd/6ykJaORJEvMN3iDEo4nUZEZvdXPDB+DvN:jOzfExPBB8k54ENo3p |
MALICIOUS
Uses Task Scheduler to run other applications
- atom.exe (PID: 6532)
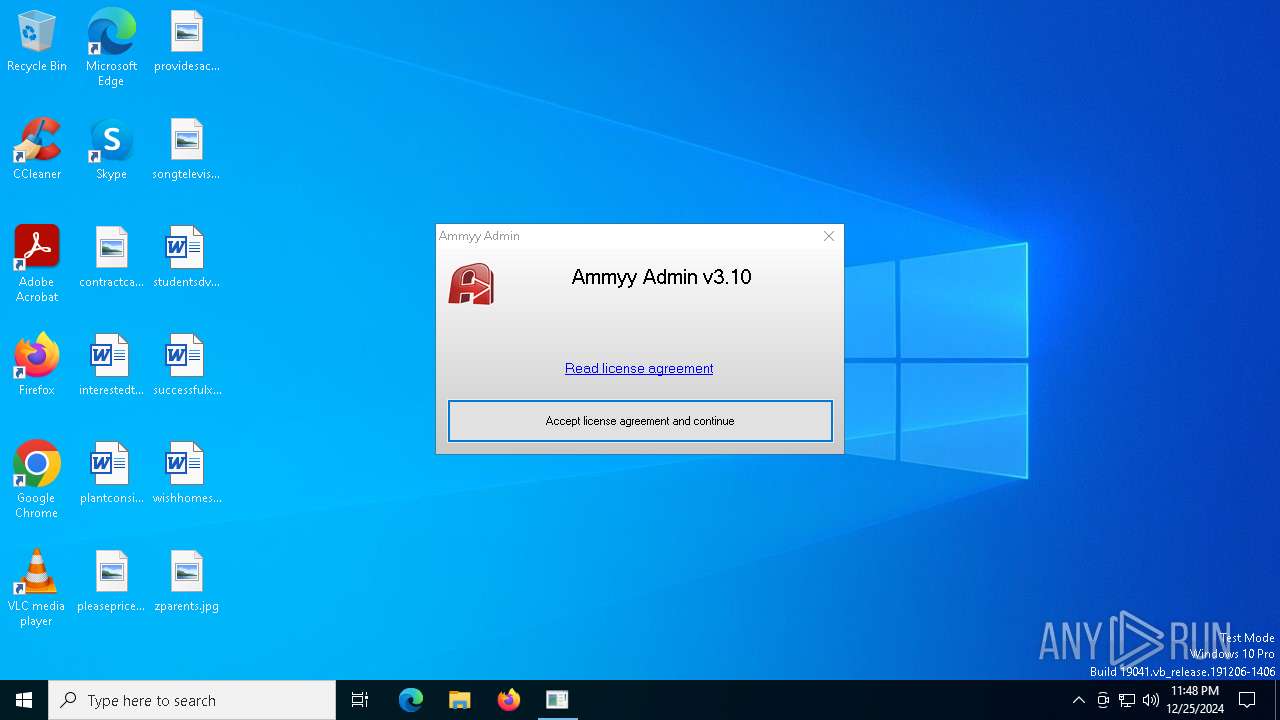
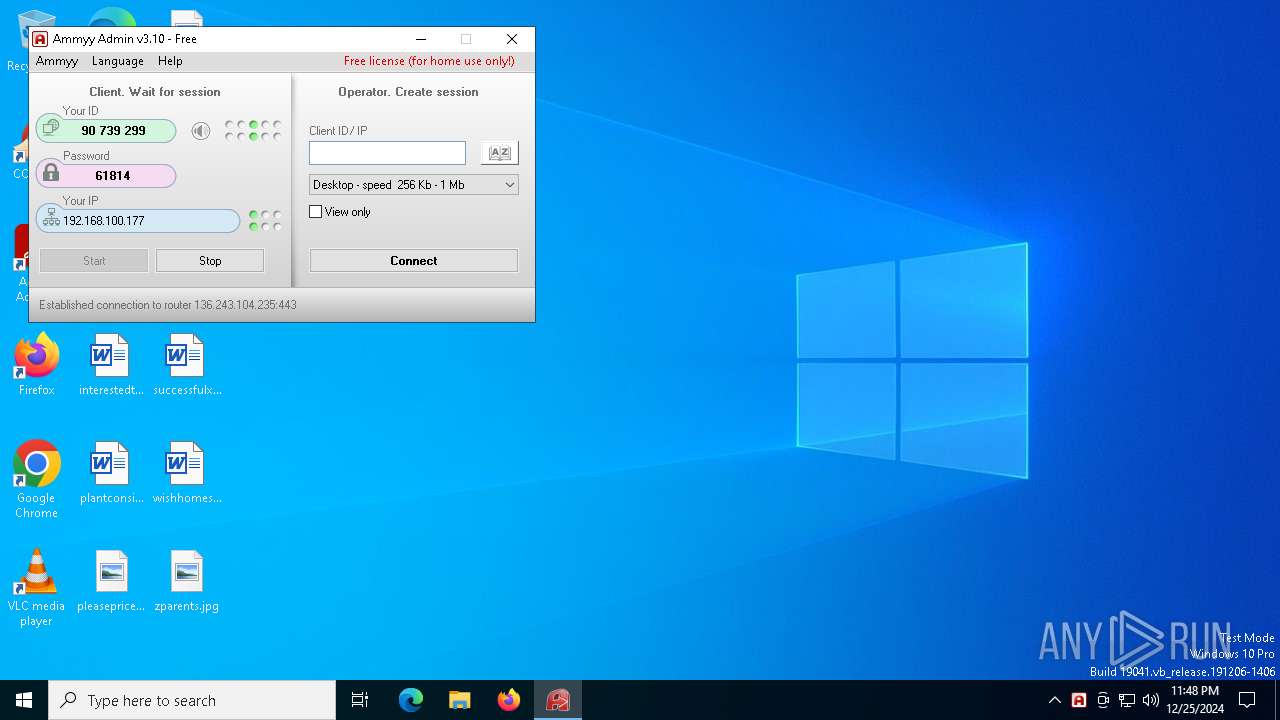
AMMYY has been detected (SURICATA)
- AA_v3.exe (PID: 6992)
Starts CMD.EXE for self-deleting
- atom.exe (PID: 6532)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 4488)
AMMYY has been detected (YARA)
- AA_v3.exe (PID: 6992)
Application was injected by another process
- svchost.exe (PID: 1068)
- winlogon.exe (PID: 684)
- svchost.exe (PID: 1276)
- dwm.exe (PID: 912)
- lsass.exe (PID: 760)
- svchost.exe (PID: 1076)
- svchost.exe (PID: 320)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1880)
- svchost.exe (PID: 1500)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 1424)
- svchost.exe (PID: 1564)
- svchost.exe (PID: 1452)
- svchost.exe (PID: 1660)
- svchost.exe (PID: 1776)
- svchost.exe (PID: 1768)
- svchost.exe (PID: 2064)
- svchost.exe (PID: 1908)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 2272)
- svchost.exe (PID: 1972)
- svchost.exe (PID: 2192)
- svchost.exe (PID: 1268)
- svchost.exe (PID: 2500)
- svchost.exe (PID: 2748)
- svchost.exe (PID: 2340)
- svchost.exe (PID: 2372)
- svchost.exe (PID: 2364)
- spoolsv.exe (PID: 2652)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 2892)
- svchost.exe (PID: 2852)
- OfficeClickToRun.exe (PID: 2884)
- svchost.exe (PID: 2944)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 3016)
- svchost.exe (PID: 3164)
- svchost.exe (PID: 2288)
- svchost.exe (PID: 2660)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 2360)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 3704)
- svchost.exe (PID: 3592)
- svchost.exe (PID: 3600)
- sihost.exe (PID: 1712)
- svchost.exe (PID: 3824)
- svchost.exe (PID: 3160)
- dasHost.exe (PID: 3896)
- explorer.exe (PID: 4488)
- svchost.exe (PID: 4168)
- svchost.exe (PID: 4176)
- svchost.exe (PID: 3668)
- RuntimeBroker.exe (PID: 4676)
- svchost.exe (PID: 4436)
- dllhost.exe (PID: 5164)
- svchost.exe (PID: 4696)
- RuntimeBroker.exe (PID: 4960)
- ctfmon.exe (PID: 4268)
- svchost.exe (PID: 2952)
- MoUsoCoreWorker.exe (PID: 4712)
- UserOOBEBroker.exe (PID: 3004)
- svchost.exe (PID: 3464)
- svchost.exe (PID: 1340)
- svchost.exe (PID: 3976)
- svchost.exe (PID: 4456)
- uhssvc.exe (PID: 2908)
- svchost.exe (PID: 812)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 1176)
- svchost.exe (PID: 1764)
- svchost.exe (PID: 376)
- dllhost.exe (PID: 1816)
- taskhostw.exe (PID: 2324)
- dllhost.exe (PID: 5904)
- RuntimeBroker.exe (PID: 5820)
- ApplicationFrameHost.exe (PID: 6108)
- svchost.exe (PID: 4200)
- svchost.exe (PID: 3032)
- RuntimeBroker.exe (PID: 6708)
- svchost.exe (PID: 1916)
- svchost.exe (PID: 4596)
- svchost.exe (PID: 5688)
- WerFault.exe (PID: 4840)
Runs injected code in another process
- dialer.exe (PID: 6568)
- dialer.exe (PID: 6700)
LUCASTEALER has been found (auto)
- AA_v3.exe (PID: 6672)
- HY21RP5CGY.exe (PID: 3224)
Connects to the CnC server
- AA_v3.exe (PID: 6672)
SUPREME has been detected (SURICATA)
- AA_v3.exe (PID: 6672)
RUSTYSTEALER has been detected (YARA)
- HY21RP5CGY.exe (PID: 3224)
Actions looks like stealing of personal data
- HY21RP5CGY.exe (PID: 3224)
XORed URL has been found (YARA)
- dialer.exe (PID: 7132)
XMRIG has been detected (YARA)
- dialer.exe (PID: 7132)
Steals credentials from Web Browsers
- HY21RP5CGY.exe (PID: 3224)
AMADEY has been detected (SURICATA)
- dialer.exe (PID: 7132)
SUSPICIOUS
Reads security settings of Internet Explorer
- AA_v3.exe (PID: 6460)
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6992)
- AA_v3.exe (PID: 6672)
Executable content was dropped or overwritten
- AA_v3.exe (PID: 6460)
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6992)
- java.exe (PID: 6696)
- AA_v3.exe (PID: 6672)
- dialer_java.exe (PID: 4528)
- HY21RP5CGY.exe (PID: 3224)
Starts itself from another location
- atom.exe (PID: 6532)
Potential Corporate Privacy Violation
- AA_v3.exe (PID: 6992)
- AA_v3.exe (PID: 6672)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6816)
Checks for external IP
- AA_v3.exe (PID: 6992)
- svchost.exe (PID: 2192)
Checks Windows Trust Settings
- AA_v3.exe (PID: 6992)
Starts CMD.EXE for commands execution
- atom.exe (PID: 6532)
- explorer.exe (PID: 4488)
Uses RUNDLL32.EXE to load library
- AA_v3.exe (PID: 6992)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 4488)
Stops a currently running service
- sc.exe (PID: 6764)
- sc.exe (PID: 6744)
- sc.exe (PID: 6948)
- sc.exe (PID: 6976)
- sc.exe (PID: 6812)
- sc.exe (PID: 2996)
- sc.exe (PID: 5892)
- sc.exe (PID: 6612)
- sc.exe (PID: 7008)
- sc.exe (PID: 7160)
Manipulates environment variables
- powershell.exe (PID: 5548)
- powershell.exe (PID: 1144)
There is functionality for taking screenshot (YARA)
- AA_v3.exe (PID: 6992)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 4488)
- HY21RP5CGY.exe (PID: 3224)
There is functionality for enable RDP (YARA)
- AA_v3.exe (PID: 6992)
Starts SC.EXE for service management
- cmd.exe (PID: 6864)
- cmd.exe (PID: 7164)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 6928)
- cmd.exe (PID: 6488)
The process executes via Task Scheduler
- dialer_java.exe (PID: 4528)
Block-list domains
- AA_v3.exe (PID: 6672)
Process requests binary or script from the Internet
- AA_v3.exe (PID: 6672)
Contacting a server suspected of hosting an CnC
- AA_v3.exe (PID: 6672)
Drops a system driver (possible attempt to evade defenses)
- dialer_java.exe (PID: 4528)
The process hide an interactive prompt from the user
- HY21RP5CGY.exe (PID: 3224)
The process hides Powershell's copyright startup banner
- HY21RP5CGY.exe (PID: 3224)
Detected use of alternative data streams (AltDS)
- HY21RP5CGY.exe (PID: 3224)
Adds/modifies Windows certificates
- lsass.exe (PID: 760)
The process bypasses the loading of PowerShell profile settings
- HY21RP5CGY.exe (PID: 3224)
Connects to unusual port
- dialer.exe (PID: 7132)
The process creates files with name similar to system file names
- WerFault.exe (PID: 4624)
Executes application which crashes
- rundll32.exe (PID: 3736)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- HY21RP5CGY.exe (PID: 3224)
INFO
Create files in a temporary directory
- AA_v3.exe (PID: 6460)
- java.exe (PID: 6696)
- dialer_java.exe (PID: 4528)
- HY21RP5CGY.exe (PID: 3224)
Reads the computer name
- AA_v3.exe (PID: 6460)
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6744)
- AA_v3.exe (PID: 6672)
- HY21RP5CGY.exe (PID: 3224)
Creates files or folders in the user directory
- AA_v3.exe (PID: 6460)
- AA_v3.exe (PID: 6992)
- java.exe (PID: 6696)
- dialer_java.exe (PID: 4528)
- HY21RP5CGY.exe (PID: 3224)
Process checks computer location settings
- AA_v3.exe (PID: 6460)
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6992)
- AA_v3.exe (PID: 6672)
Checks supported languages
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6460)
- AA_v3.exe (PID: 6672)
- java.exe (PID: 6696)
- AA_v3.exe (PID: 6744)
- AA_v3.exe (PID: 6992)
- dialer_java.exe (PID: 4528)
- HY21RP5CGY.exe (PID: 3224)
Reads CPU info
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6672)
Reads Environment values
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6672)
Reads product name
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6672)
The sample compiled with english language support
- AA_v3.exe (PID: 6460)
- svchost.exe (PID: 1340)
- java.exe (PID: 6696)
Creates files in the program directory
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6744)
- AA_v3.exe (PID: 6992)
- MoUsoCoreWorker.exe (PID: 4712)
- AA_v3.exe (PID: 6672)
- svchost.exe (PID: 1076)
- rundll32.exe (PID: 3736)
- svchost.exe (PID: 5688)
The process uses the downloaded file
- atom.exe (PID: 6532)
- AA_v3.exe (PID: 6460)
- AA_v3.exe (PID: 6672)
Reads the software policy settings
- lsass.exe (PID: 760)
- AA_v3.exe (PID: 6992)
- HY21RP5CGY.exe (PID: 3224)
- WerFault.exe (PID: 4624)
Checks proxy server information
- AA_v3.exe (PID: 6744)
- HY21RP5CGY.exe (PID: 3224)
Reads the machine GUID from the registry
- AA_v3.exe (PID: 6992)
- AA_v3.exe (PID: 6672)
Reads security settings of Internet Explorer
- RuntimeBroker.exe (PID: 6708)
Manual execution by a user
- powershell.exe (PID: 5548)
- cmd.exe (PID: 6864)
- cmd.exe (PID: 6928)
- dialer.exe (PID: 6568)
- powershell.exe (PID: 6600)
- schtasks.exe (PID: 5316)
- cmd.exe (PID: 1988)
- powershell.exe (PID: 1144)
- cmd.exe (PID: 7164)
- cmd.exe (PID: 6488)
- powershell.exe (PID: 6696)
- dialer.exe (PID: 6700)
- dialer.exe (PID: 6616)
- dialer.exe (PID: 7132)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5548)
- powershell.exe (PID: 6600)
- powershell.exe (PID: 1144)
- powershell.exe (PID: 6696)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5548)
- powershell.exe (PID: 1144)
Application based on Rust
- HY21RP5CGY.exe (PID: 3224)
The sample compiled with japanese language support
- dialer_java.exe (PID: 4528)
Drops encrypted VBS script (Microsoft Script Encoder)
- HY21RP5CGY.exe (PID: 3224)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 2884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
192
Monitored processes
148
Malicious processes
93
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 912 | "dwm.exe" | C:\Windows\System32\dwm.exe | winlogon.exe | ||||||||||||
User: DWM-1 Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s DsmSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe Add-MpPreference -ExclusionPath @($env:UserProfile, $env:ProgramFiles) -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
73 757
Read events
73 168
Write events
378
Delete events
211
Modification events
| (PID) Process: | (6460) AA_v3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6460) AA_v3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000010901EF8A46ECE11A7FF00AA003CA9F61D030000 | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02xqlfukoksyauhy |
| Operation: | write | Name: | Provision Wednesday, December 25, 2024 23:48:15 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAWRdTNVrr0USuwyEbtcyWIgAAAAACAAAAAAAQZgAAAAEAACAAAADYPka9SztJmIfCR2T+GiM9M+NvMElaXTNPDYDBxtddpQAAAAAOgAAAAAIAACAAAABKyUAj4s42SjhqGyV6PXp+lRj/NEgpQIsdlQmHgG0KbSAAAADIdtkQ6hg5GXBd4+E0CX9R+He9NLly0KaYe0qZB1X1A0AAAADMDeeBZr1qCpSw2Q6Ah3ErnC9yVq2Vgb8/W9dYampenhjrx46VM01N9cxx7kIxmYfu6W6uiPT7+oghm6byWCVq | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-21-1693682860-607145093-2874071422-1001\02czcbpcfgaxmfdi |
| Operation: | write | Name: | AppIdList |
Value: | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-21-1693682860-607145093-2874071422-1001\02czcbpcfgaxmfdi |
| Operation: | write | Name: | Reason |
Value: | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-21-1693682860-607145093-2874071422-1001 |
| Operation: | write | Name: | ValidDeviceId |
Value: | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02pezsyflofvcogf |
| Operation: | write | Name: | Provision Wednesday, December 25, 2024 23:48:15 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAjGVohzrf7U+SR6PsI8h7nAAAAAACAAAAAAAQZgAAAAEAACAAAACwFnJkyiZPDtbl1nRvtsVd9GAvYbRkpu/Seu4bS0G+JgAAAAAOgAAAAAIAACAAAAA9D8qJgWhIHEc6YSAckwO9wMSIo8joYGhMqpvzZcMWsiAAAACIzDZmULfW+XbrIfNNeUy2fPjNpbO5pKCgxxL2UT0BG0AAAABX/jd458uhqqrRMtkJsxp4ANSIaTLOEpTVhM4lcyvtV+IhwLBvqXbzdotZL+4kBwJTUgGCZPWvOVV0BtKLGlWf | |||
| (PID) Process: | (1176) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02uegznpmkonbnuh |
| Operation: | write | Name: | Provision Wednesday, December 25, 2024 23:48:16 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAjGVohzrf7U+SR6PsI8h7nAAAAAACAAAAAAAQZgAAAAEAACAAAACNVtKkTB50oJHme8IpPLW2xIOZdKWGVXbaRrrAY9fKbAAAAAAOgAAAAAIAACAAAADF4r3HW1sJntY6hHnl0DLoMdcNdHMEFDUMoylbup0OjiAAAAC/Go43W7gXbrNHvwiN9JXQoeUUfbcTTlXU5dzIR1jcr0AAAADOsf8gDrgFca2l99abHl1e/erfMtKCXECSmTzHgfl8stcbc7W5KzDEKtPHvJKipwqIsI69PRIhm6fKyQP89zx1 | |||
| (PID) Process: | (2908) uhssvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Remediation\LocalState\TelemetryUpdateHealthTools |
| Operation: | write | Name: | GlobalEventCounter |
Value: 2F00000000000000 | |||
| (PID) Process: | (1340) svchost.exe | Key: | \REGISTRY\A\{b2aa6275-6d9e-e035-3b88-af7204c7627b}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
Executable files
16
Suspicious files
76
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6460 | AA_v3.exe | C:\Users\admin\AppData\Local\Temp\nsm5CE9.tmp | — | |
MD5:— | SHA256:— | |||
| 5164 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\V01.chk | binary | |
MD5:9628937F1D0F7449C2BB18557D32ABBC | SHA256:B4F5910E457A3718E24C74BC67529F799CE881225673F938E9462A76F90C40C3 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\CONSENT.EXE-531BD9EA.pf | binary | |
MD5:D4EB4AB23C68E009FA8BDF9C788A702F | SHA256:0850E7B367F1F3AFC3E3E2D077EA82FAAE6F5D29D11F6CE495CC3688DD068F0C | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-2E4E3AC7.pf | binary | |
MD5:0CF5C69E4DFB2965AD6839C6429AA413 | SHA256:32ED1F621A53EF4B40890F75F1BD8C682F3750418E000F03976B615A7A168C69 | |||
| 6460 | AA_v3.exe | C:\Users\admin\AppData\Roaming\java.exe | executable | |
MD5:BDB4D5B582F8195142F8D2D1E9D44A8E | SHA256:852C76F75FC0DCC00A3DA2C4D1A36C82F901A8E5F9044F3603E836F8FEEF4FA4 | |||
| 1276 | svchost.exe | C:\Windows\System32\Tasks\EMECL9G5J5CRT7SBTJ | xml | |
MD5:945A7A1D36DCBF5436EAE9A3DBC67337 | SHA256:B10562DC5C5337F2A134B505A1310F38615EDF7AB4D59E16E3A0834BF5E70E60 | |||
| 6532 | atom.exe | C:\ProgramData\{I7YFPHOU-L1LR-99FH-W9YJHBO4K8HY}\AA_v3.exe:Zone.Identifier | text | |
MD5:9F22B5D78B010677142FFE4A66E02CB2 | SHA256:F0E0B1154B82AD66F9D3B1AA8CA4EAE94A138A55E17538392315EBF63D2C36FE | |||
| 6744 | AA_v3.exe | C:\ProgramData\AMMYY\settings3.bin | binary | |
MD5:B8946EDDA960DAD0F7438CD387BF1CF3 | SHA256:48149E6BED76634A06EA70DDC2CD48EA187CF4D6C98802FC31EE6291A82405B3 | |||
| 6460 | AA_v3.exe | C:\Users\admin\AppData\Roaming\AA_v3.exe | executable | |
MD5:90AADF2247149996AE443E2C82AF3730 | SHA256:EE573647477339784DCEF81024DE1BE1762833A20E5CC2B89A93E47D05B86B6A | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\ATOM.EXE-9C5DA23B.pf | binary | |
MD5:4BF37BC819067F341188F0F178578EED | SHA256:995A0ADF6FA9F0FB1B287023D3207C01AEAE732255B00D68E3290F1812435AED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
70
DNS requests
39
Threats
59
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6992 | AA_v3.exe | POST | 200 | 188.42.129.148:80 | http://rl.ammyy.com/ | unknown | — | — | malicious |
6992 | AA_v3.exe | GET | 301 | 136.243.18.118:80 | http://www.ammyy.com/files/v8/aans64y2.gz | unknown | — | — | malicious |
6992 | AA_v3.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6992 | AA_v3.exe | GET | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgSfBEjCuhCXdl7Defz8ipA09g%3D%3D | unknown | — | — | whitelisted |
5720 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6912 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2220 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
rl.ammyy.com |
| unknown |
www.ammyy.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6992 | AA_v3.exe | Potential Corporate Privacy Violation | ET POLICY IP Check (rl. ammyy. com) |
2192 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Query to SupremeBot Domain (silentlegion .duckdns .org) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2192 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
6672 | AA_v3.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.duckdns .org Domain |
6672 | AA_v3.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to DuckDNS Domain |
6672 | AA_v3.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to DuckDNS Domain |
6672 | AA_v3.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.duckdns .org Domain |
6672 | AA_v3.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.duckdns .org Domain |
6672 | AA_v3.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to DuckDNS Domain |
8 ETPRO signatures available at the full report