| File name: | 2969467.eml |
| Full analysis: | https://app.any.run/tasks/9e982fc9-e04d-46ef-81af-9dfa064432d1 |
| Verdict: | Malicious activity |
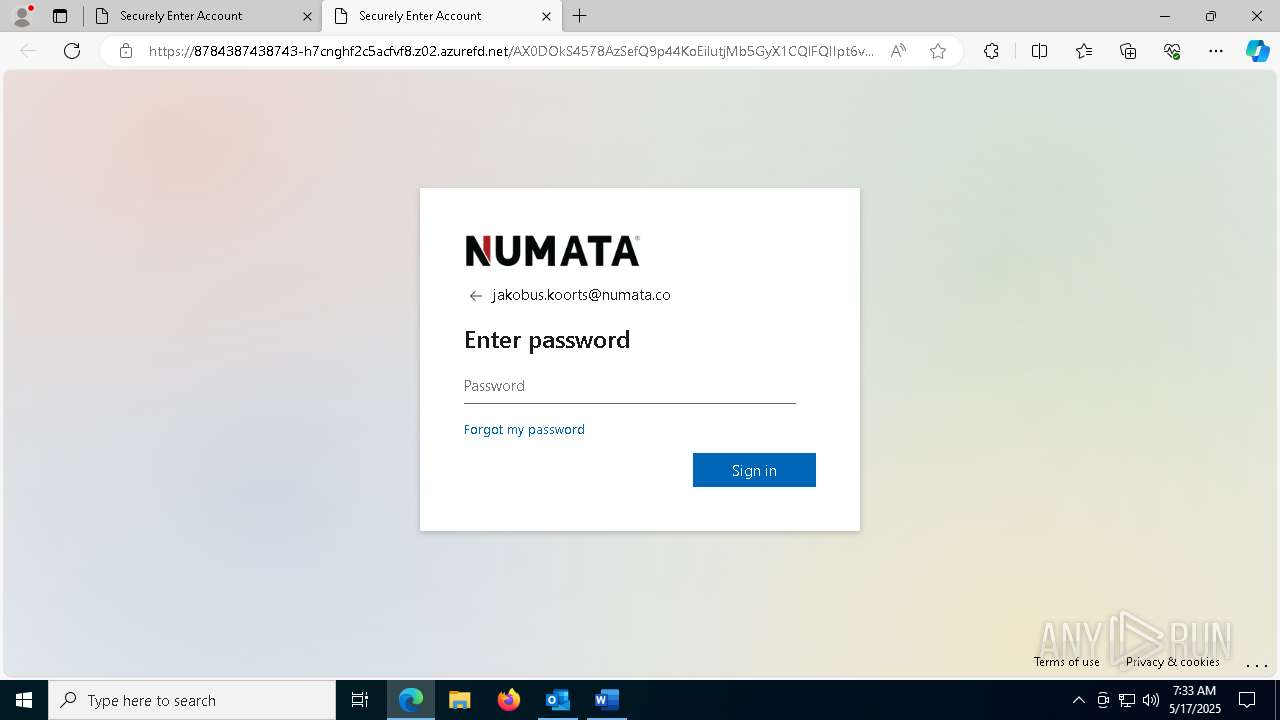
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | May 17, 2025, 07:31:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines (359), with CRLF line terminators |
| MD5: | 4929120E03BEF68941D85FDAFD850F5D |
| SHA1: | 7650337248A3D348DE2CE36A989E3DEA34C898D5 |
| SHA256: | 9016D695BC3E3EE6FC2009DE76D0273C8AFD1D05115269179FD545B499498A58 |
| SSDEEP: | 1536:mGqO1MNgFm3gDthD52JMNkCwuwuuPPnJfX+j0t1LphqvfaOXcU+:mfgDthndQJfXFt1L3kq |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 668)
SUSPICIOUS
Possibly a phishing URL contains email has been detected
- msedge.exe (PID: 736)
- msedge.exe (PID: 5188)
INFO
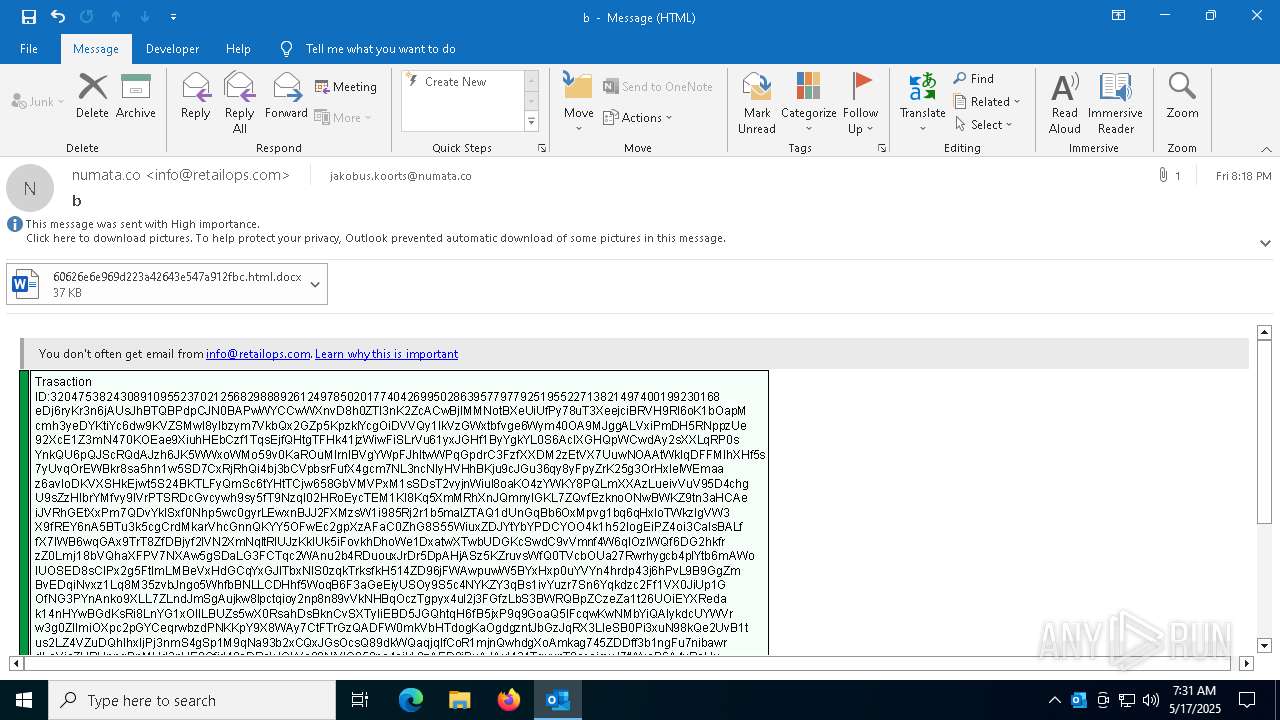
Email with attachments
- OUTLOOK.EXE (PID: 2384)
Reads the software policy settings
- slui.exe (PID: 5156)
- slui.exe (PID: 1240)
Application launched itself
- msedge.exe (PID: 736)
Reads the computer name
- identity_helper.exe (PID: 7920)
Checks supported languages
- identity_helper.exe (PID: 7920)
Checks proxy server information
- slui.exe (PID: 1240)
Reads Environment values
- identity_helper.exe (PID: 7920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
188
Monitored processes
50
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2572 --field-trial-handle=2456,i,3056751024956898620,14508313991535819774,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
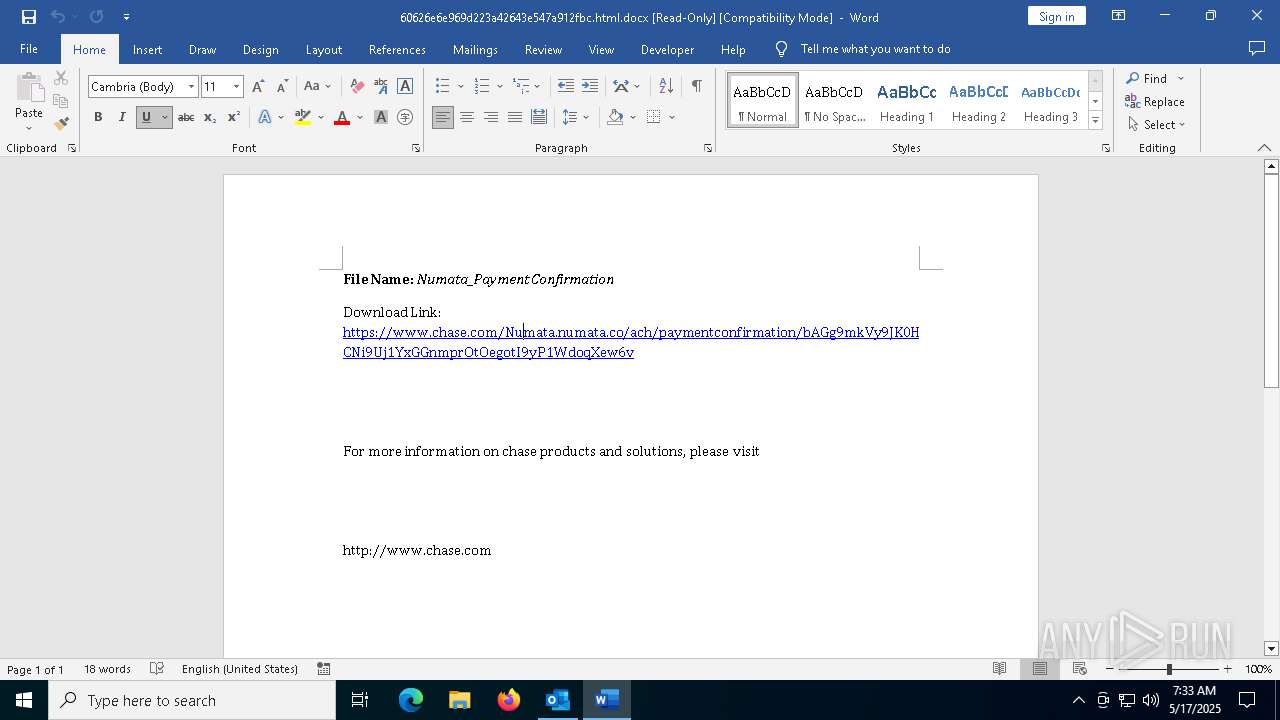
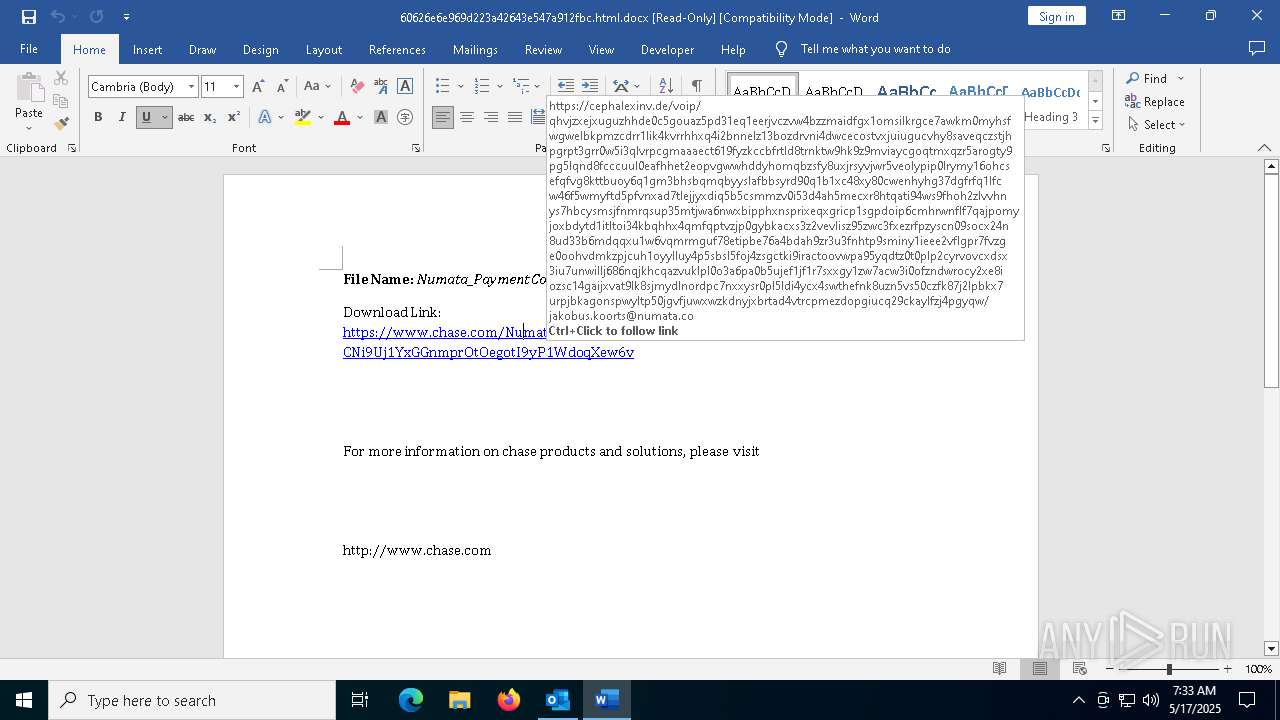
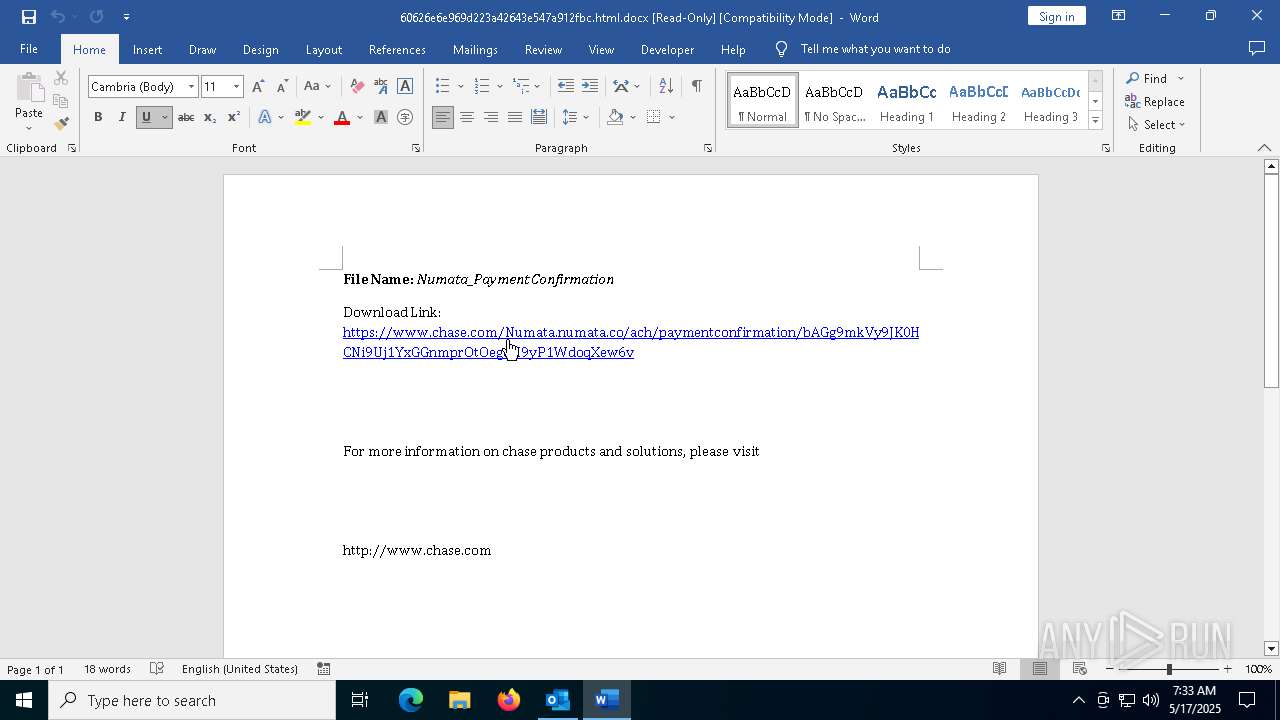
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://cephalexinv.de/voip/QHVjzXEjxUGUzhHde0C5goUaz5Pd31eq1EERjvcZvW4BzZMAIDFGx1oMSIlkRGcE7AwKM0MyhsfwGWELBKpMzCdrR1LIK4kvrRHhxq4I2bNNelZ13BOzdRvNi4dWcEcOsTvxJuIUGucVHy8SAvEqczsTjHpGrpT3Grr0W5i3qLvRpcgmAaaeCt619FYZkccBfrtld8trnKTW9hk9z9mVIaYcGOQtmXqzR5AROGTy9PG5Lqnd8fccCuul0eaFHHET2eOpVGwWHddyhOMQBZSFY8uxJrSYvjWr5VeoLyPIP0lrYmy16OHCSEfQfVg8kttBUOY6Q1GM3bHSBQmqBYyslaFbBSYrD90Q1b1XC48xY80cweNhyhg37dGfrfq1LfCw46f5WmYftD5pfvnXad7TLEjJyxDIQ5b5CsMMZV0i53D4ah5MEcxR8HtqatI94ws9fhOh2zlVvhnys7HBcySMSjfNMRQsuP35mTJwa6nwxBIPpHxNsPRixEQxgRIcp1sGPdOip6CmHrWnfLf7QAJPOMyJoXbdYTD1ItltOi34kbqHhx4QmFqpTVZJp0gYBKACxS3Z2vEVliSz95Zwc3fXezrFPzYScN09SOCx24n8UD33b6MDqqXU1W6VqMRmgUf78eTIpBE76a4bDah9ZR3u3FNhtp9SMInY1iEEe2vfLGpr7FvzGE0oohVDmKZPJCUh1OYYlLuY4p5SBSL5FoJ4ZsgCtkI9irACTOoVwpA95YQDtz0t0plp2cYrVoVCxDSX3iU7UnWiLLJ686nqjkHCqazvuKlpl0o3a6PA0B5UJeF1JF1r7SXxgY1ZW7Acw3i0OfZnDwRocy2Xe8IoZSc14GAijxVaT9LK8sjmydlNORDPc7nxxYSr0pL5LdI4ycx4SwtHEFNK8Uzn5Vs50CZFk87j2lPbkx7uRPJbKAGONSPwyltP50jgVfjuwXwZKDNYjXbRTaD4VTRCPmEZdOPgIUcq29ckaylFZJ4pgYqW/jakobus.koorts@numata.co | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3512 --field-trial-handle=2456,i,3056751024956898620,14508313991535819774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6680 --field-trial-handle=2456,i,3056751024956898620,14508313991535819774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1240 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "7DFBD6DD-F9AA-4E3A-9EAF-37C366EE53B5" "7440C902-C1B8-46B2-BFEA-5B12453AFE5D" "6068" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 2284 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4184 --field-trial-handle=2456,i,3056751024956898620,14508313991535819774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5152 --field-trial-handle=2456,i,3056751024956898620,14508313991535819774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2340 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=900 --field-trial-handle=2456,i,3056751024956898620,14508313991535819774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2384 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\2969467.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
29 923
Read events
28 240
Write events
1 483
Delete events
200
Modification events
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\2384 |
| Operation: | write | Name: | 0 |
Value: 0B0E101E1AF516F4EAE44D81CC1933290D77242300468BC3D1B1DBDFF1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D012D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (2384) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
40
Suspicious files
316
Text files
73
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:EB812F479D857BE947D5CF33586A328D | SHA256:862E365DC7DAE72CBA494D85111160DD8B71B416EB13E19D316514A5BD1B4020 | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:EAD590E3B3F9CA9312BA470013A34653 | SHA256:E10662FC87C04B5F2DD078472FBBB9561D310D93B4367FD41EF69B9F6AF08A39 | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:BBCCB4A46D7B23B32D62177D0EB57725 | SHA256:DF548A41E5DC649D50E25F846D318A3D1201A9BA6216AF73C2FF672511D402DC | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\8AAAF9D5-E23A-4550-9F13-ADD0359A41F2 | xml | |
MD5:CE1D264F4F66E53908ED3477F48889F6 | SHA256:C6BC96E6C5CD146A9CD14D67A04682BCF2F1A66E9EDFC79285C57EA71D615B94 | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:B30913869C8F4DFC32059ADDDF4D6021 | SHA256:0226985266D6ED117DD26D74C84651DB4C5F10909670CE50F8113C0AE0FC5325 | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:6BC4072E0E55B15FC9681F1DA3BD25E2 | SHA256:3E8B8B163497BAADD4A10B0523E55583B68F790E9E9A1331E2ECCAD5594C1F77 | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:3011EB8F1B7A4EFDEB421302F41B2F86 | SHA256:79B8E926E62D2C1EBB690D9D023A7AA5016C9B9D48DAB96480751EE1A411687D | |||
| 2384 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_E3E03240F1C6044EAEDBAA99420DE837.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
132
DNS requests
108
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2384 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2384 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2092 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2092 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6068 | WINWORD.EXE | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6068 | WINWORD.EXE | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6068 | WINWORD.EXE | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2384 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2384 | OUTLOOK.EXE | 52.123.243.219:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2384 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
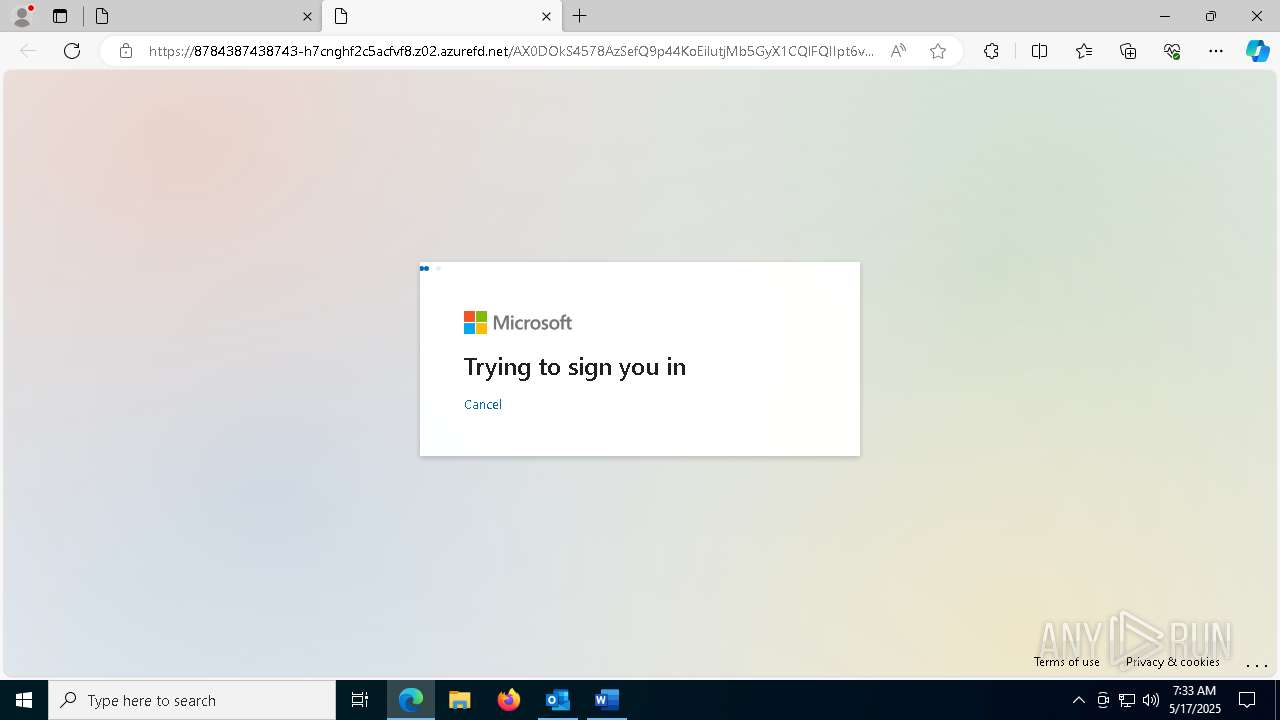
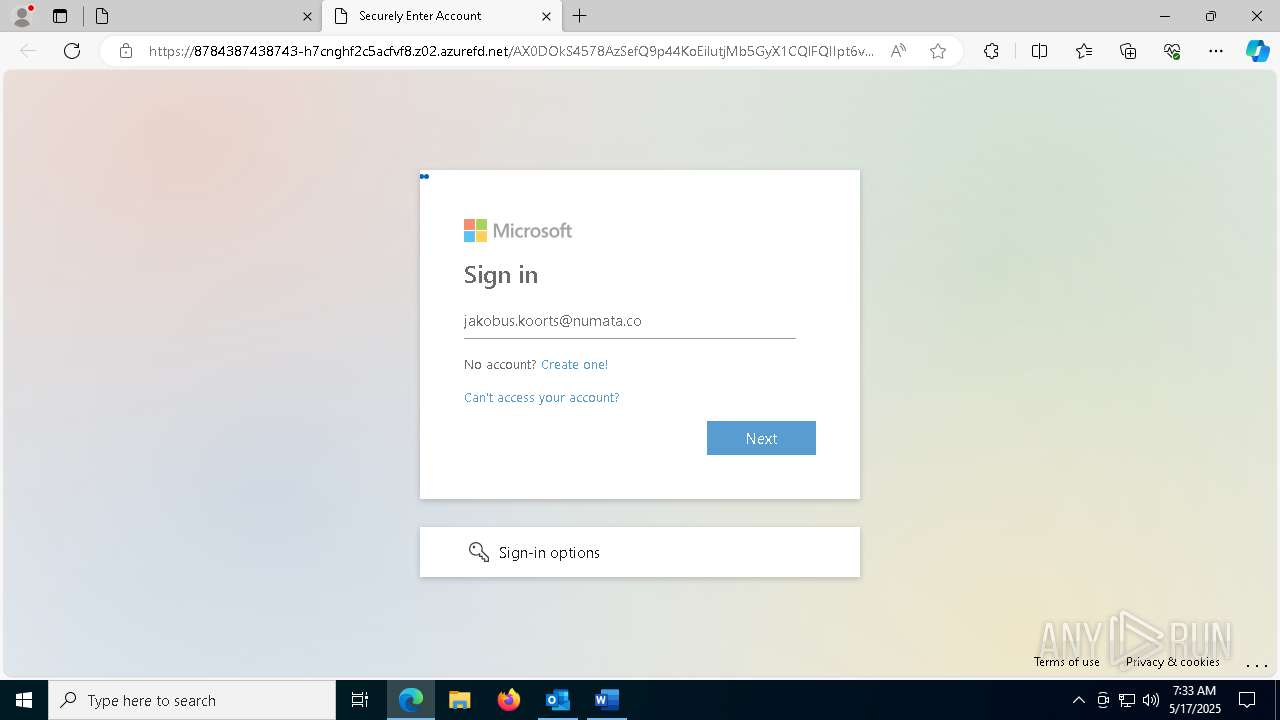
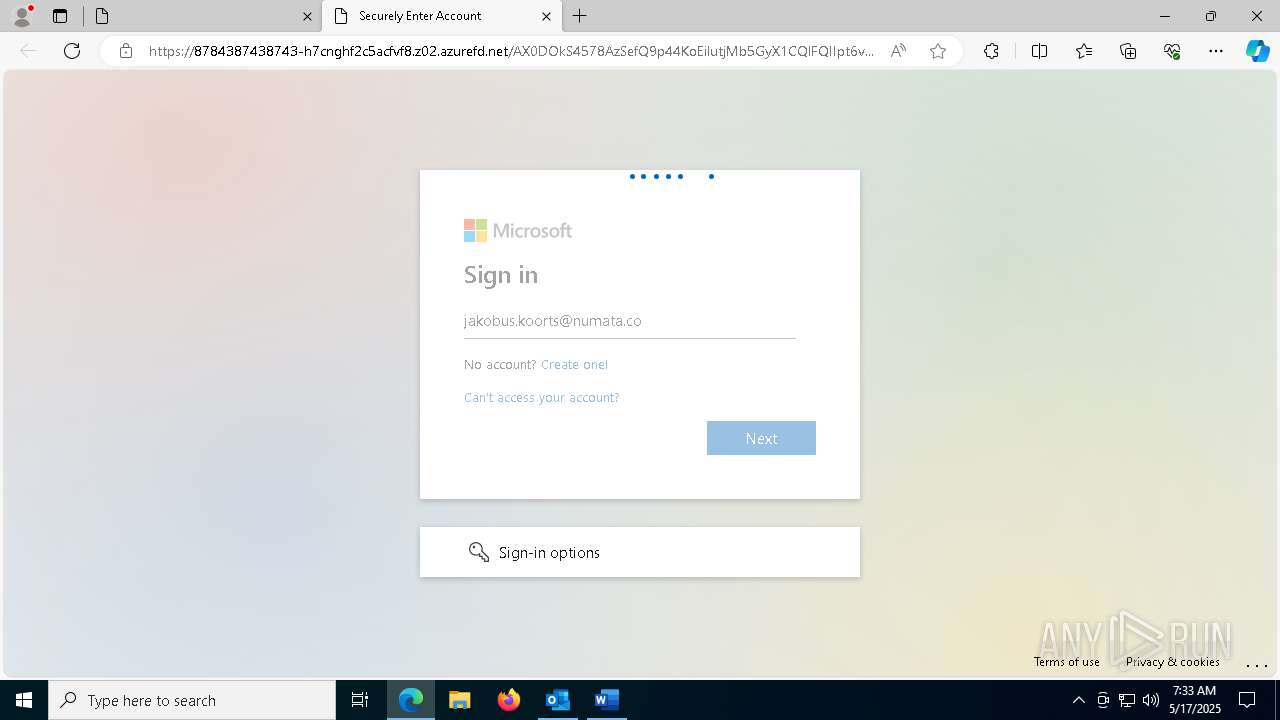
668 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Possible Domain chain identified as Phishing (authisnotlogin) |
668 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Fake Microsoft Sign-In Page (Login w/o Signin) |