| File name: | [_Correo Sospechoso_] UN ANUNCIO MUY IMPORTANTE.eml |
| Full analysis: | https://app.any.run/tasks/aafd85af-14b4-4b1c-8675-306d79097751 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 15, 2025, 21:55:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | A4DC4E72B088273FE6D46A3F8173432D |
| SHA1: | 039F1B25FE828BC817E698EFFD6EC52C91BDF6BA |
| SHA256: | 8FF0C936012061D67DC4AD452CB0F6C6C3C2F94329A4349A8C0239D0527ED158 |
| SSDEEP: | 24576:ei6L7OywY87GT82LSuct5mPg2mnnx1hSevjbK:e048qoucTuox1R/K |
MALICIOUS
Actions looks like stealing of personal data
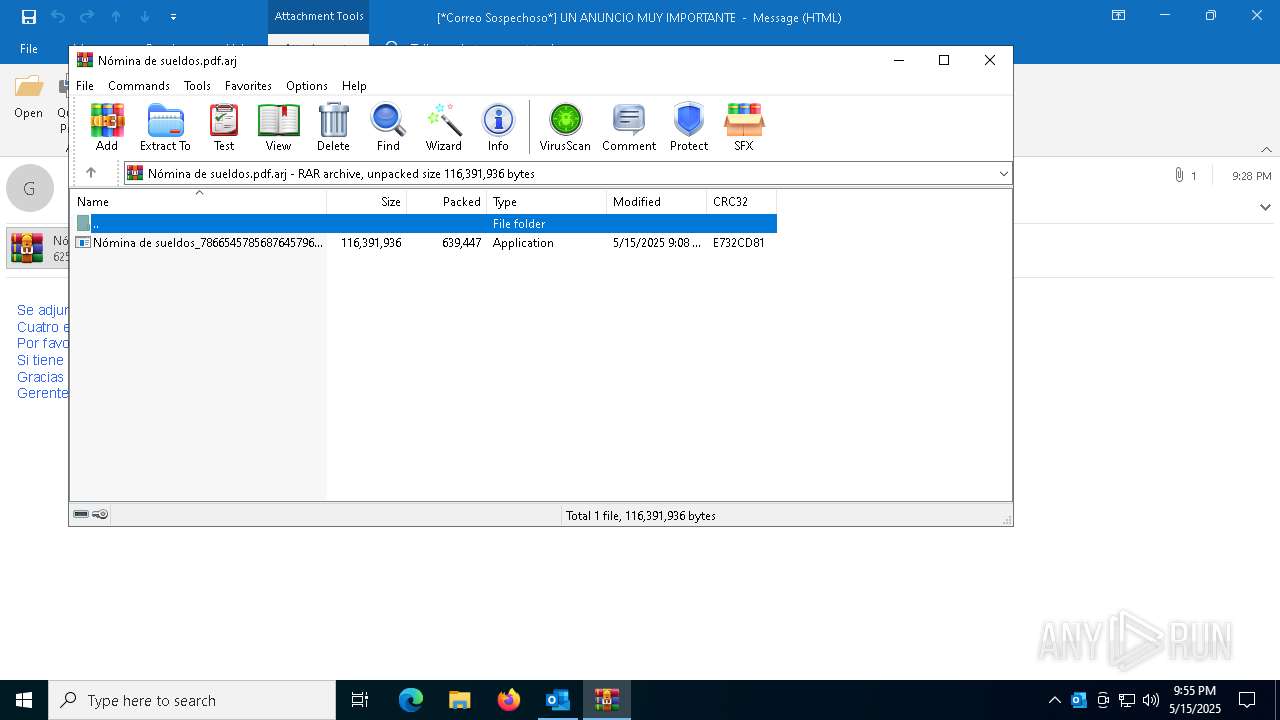
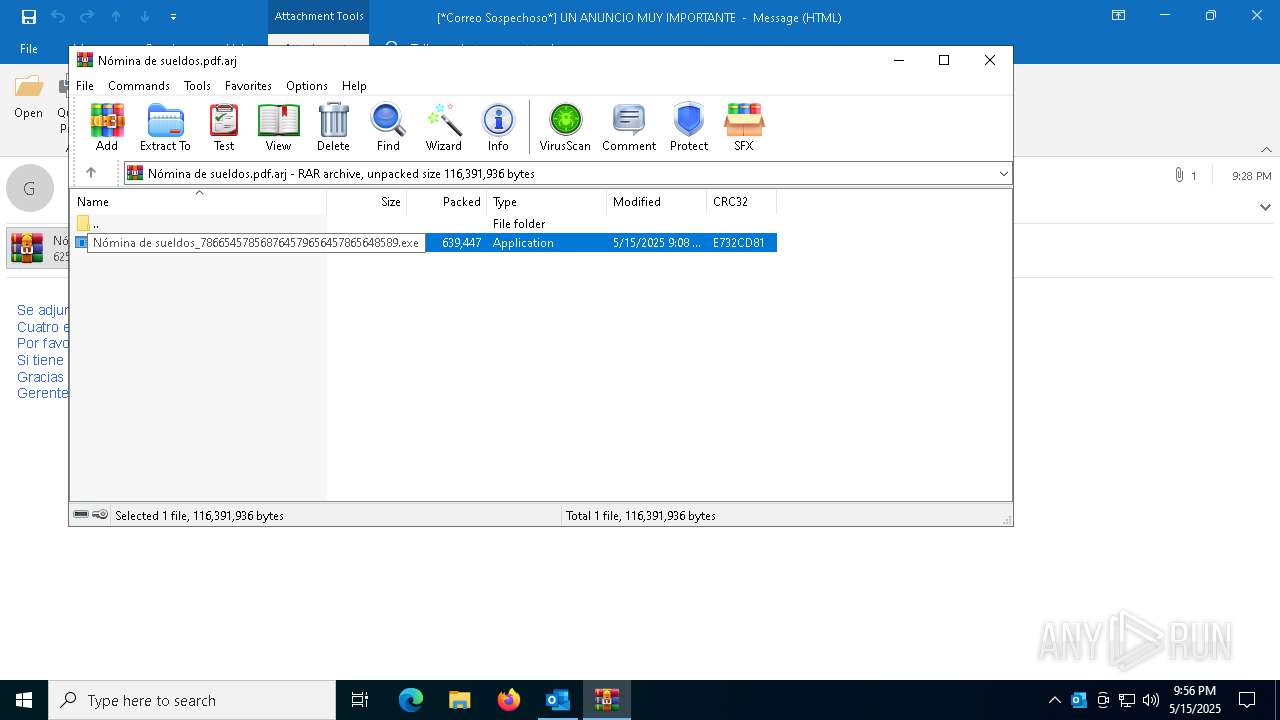
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Steals credentials from Web Browsers
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
AGENTTESLA has been detected (SURICATA)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7664)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
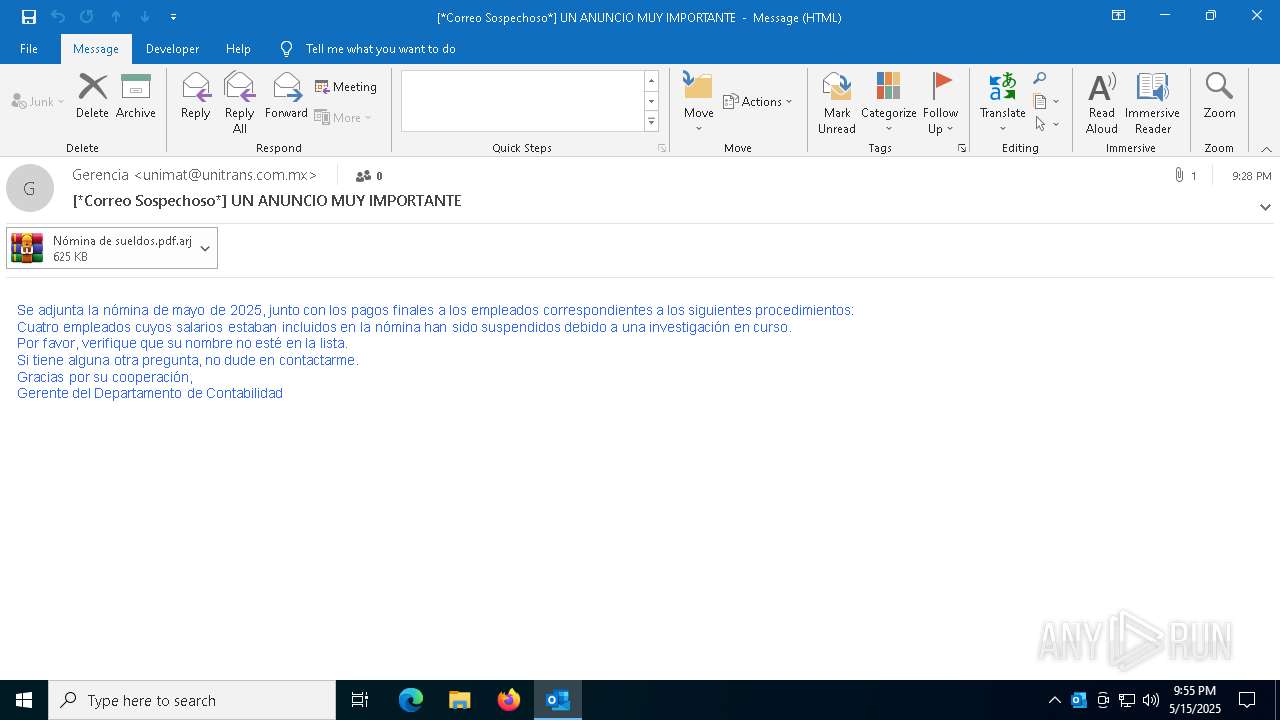
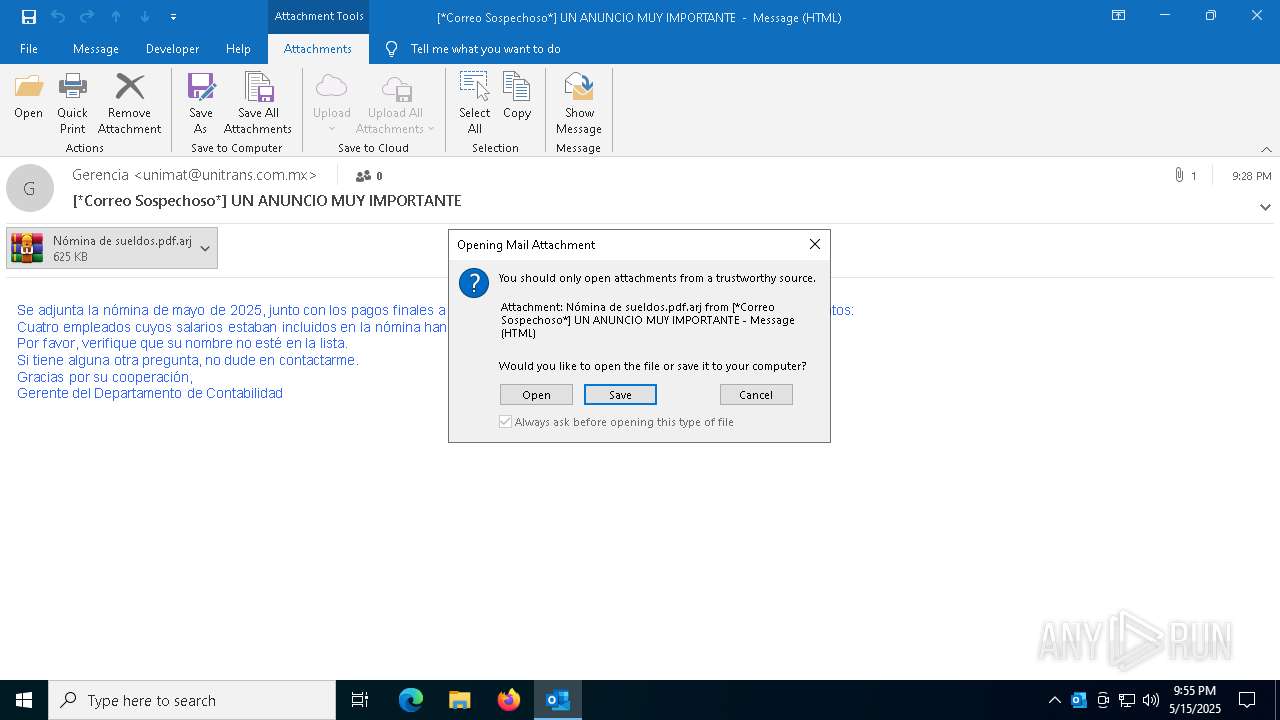
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7148)
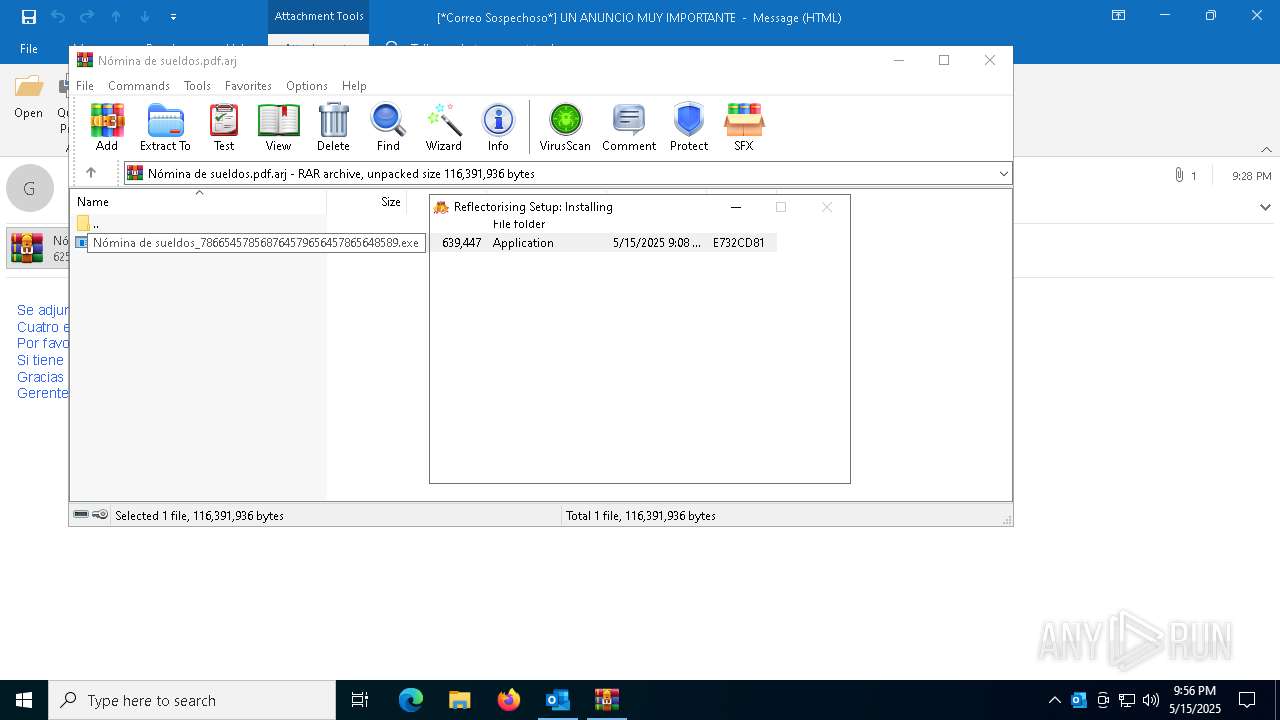
The process creates files with name similar to system file names
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
Malware-specific behavior (creating "System.dll" in Temp)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
Executable content was dropped or overwritten
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
Application launched itself
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
Connects to the server without a host name
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Checks for external IP
- svchost.exe (PID: 2196)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Connects to SMTP port
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Contacting a server suspected of hosting an CnC
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 7148)
Reads the computer name
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Creates files or folders in the user directory
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
Checks supported languages
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Create files in a temporary directory
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7808)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8080)
Checks proxy server information
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Reads the machine GUID from the registry
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Disables trace logs
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 7928)
- Nómina de sueldos_786654578568764579656457865648589.exe (PID: 8116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
139
Monitored processes
10
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6876 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\[_Correo Sospechoso_] UN ANUNCIO MUY IMPORTANTE.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7336 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "A0CA12D1-CB71-4613-A9AE-DC2218199904" "89EF9D71-88D0-40B8-AED2-505A7159F346" "7148" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
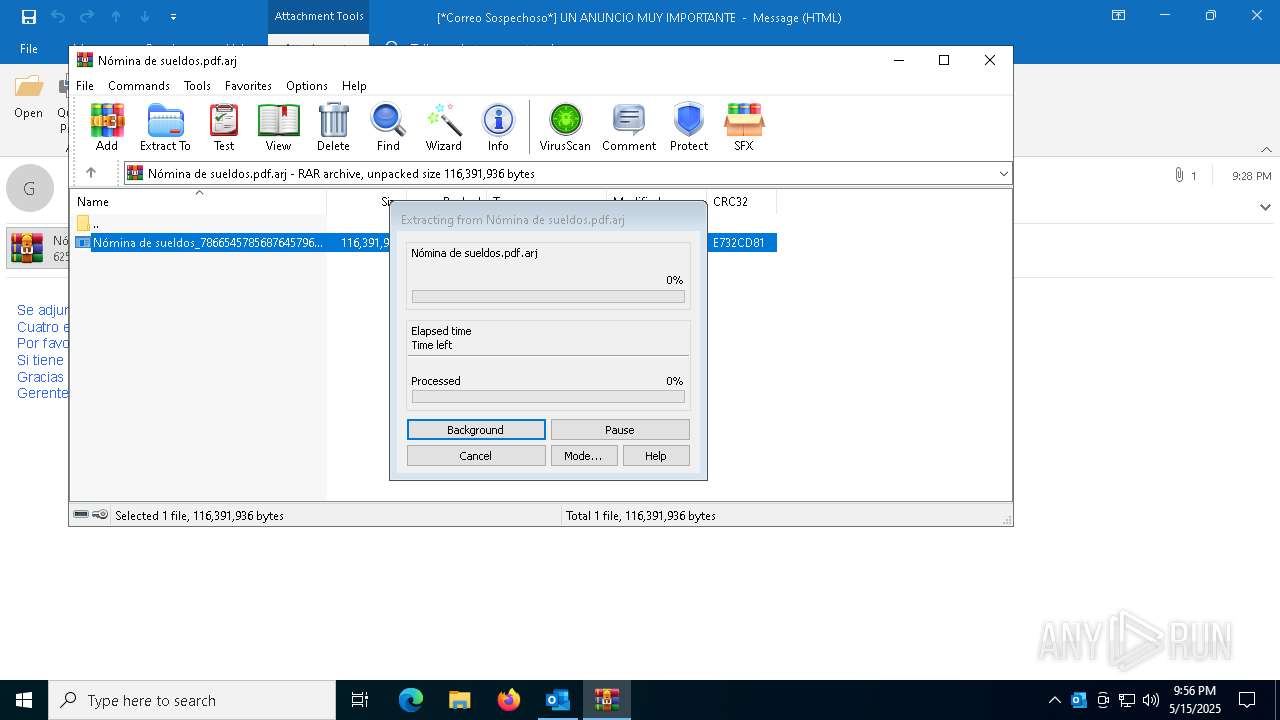
| 7664 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\TFSGDX3H\Nómina de sueldos.pdf.arj" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
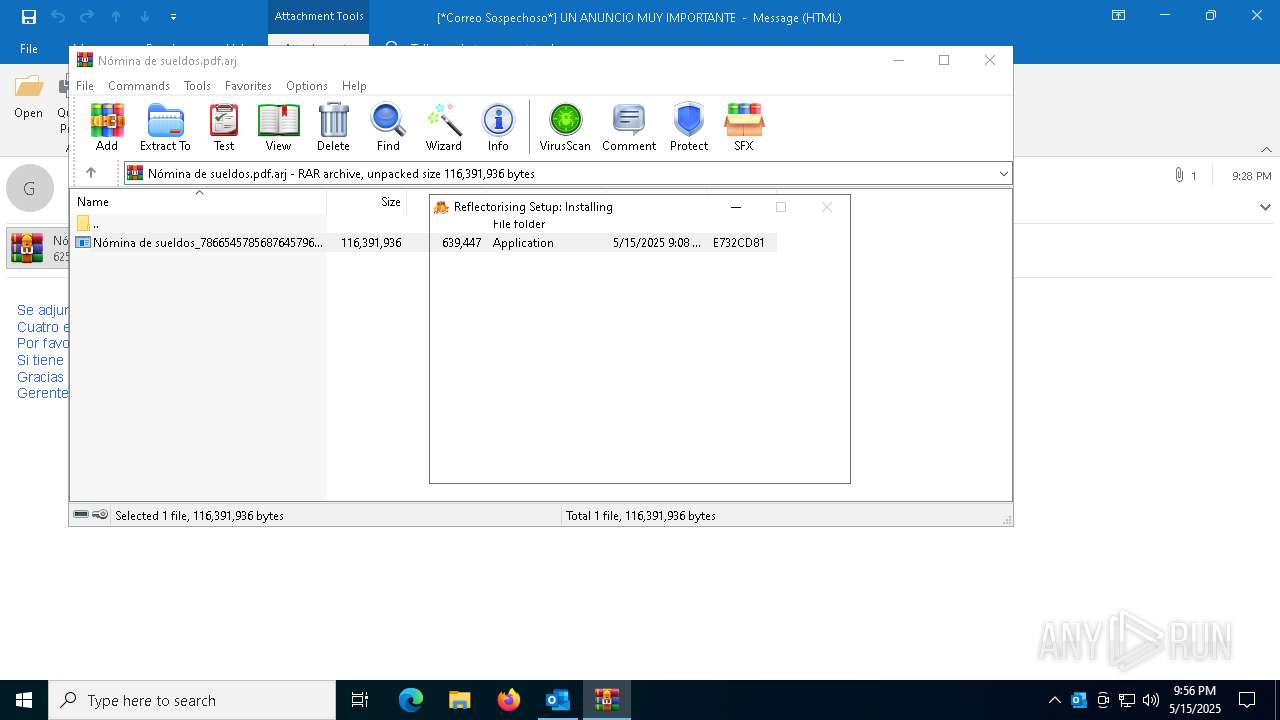
| 7808 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.47172\Nómina de sueldos_786654578568764579656457865648589.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.47172\Nómina de sueldos_786654578568764579656457865648589.exe | WinRAR.exe | ||||||||||||
User: admin Company: onychomalacia Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7928 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.47172\Nómina de sueldos_786654578568764579656457865648589.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.47172\Nómina de sueldos_786654578568764579656457865648589.exe | Nómina de sueldos_786654578568764579656457865648589.exe | ||||||||||||
User: admin Company: onychomalacia Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 8080 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.49205\Nómina de sueldos_786654578568764579656457865648589.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.49205\Nómina de sueldos_786654578568764579656457865648589.exe | WinRAR.exe | ||||||||||||
User: admin Company: onychomalacia Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 8116 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.49205\Nómina de sueldos_786654578568764579656457865648589.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.49205\Nómina de sueldos_786654578568764579656457865648589.exe | Nómina de sueldos_786654578568764579656457865648589.exe | ||||||||||||
User: admin Company: onychomalacia Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
18 257
Read events
16 138
Write events
1 998
Delete events
121
Modification events
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | SessionId |
Value: AD385C32-CC70-4FFF-A786-3374EC09BDC0 | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Preferences |
| Operation: | delete value | Name: | ChangeProfileOnRestart |
Value: | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 09000000 | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030397 |
Value: 60000000 | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | FilePath |
Value: officeclient.microsoft.com\0408DD4C-6842-4A0D-8C0E-420CAD95FA5C | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | StartDate |
Value: C0182E1CE4C5DB01 | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | EndDate |
Value: C0D89746ADC6DB01 | |||
| (PID) Process: | (7148) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{02CAC15F-D4BE-400E-9127-D54982AA4AE9} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
2
Suspicious files
14
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7148 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7664 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7664.47172\Nómina de sueldos_786654578568764579656457865648589.exe | — | |
MD5:— | SHA256:— | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:9772D66BAA075FBF7F040801B3A6CD80 | SHA256:8C532A0F097C4B99A5B6BA8D29CD740C2017076029B7ABB5369A51D074826115 | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:20040A76FE2C215709B81F1B168FB360 | SHA256:091EE0ED2F7FCBBFB9E595ED93036D17C6C7D7E57402FD1D5EF31D2D1E3C636E | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkD69B.tmp | binary | |
MD5:7E60721059AFCCEB9690ED46372AA709 | SHA256:F1E81C0BC6A2AF781F24D994CE396983AAACA637A7D12B7623258A383A7A7B99 | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\0408DD4C-6842-4A0D-8C0E-420CAD95FA5C | xml | |
MD5:136AED2D77D13E6CF8E7CD4008F16F4C | SHA256:B6930B9488295119B387AFC32CF800034F200A27C6740F87CDE88E84FA370A40 | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:AE74FD9FF00B66BDF6C7EE79E5405E46 | SHA256:1B689C8FEBC3D0DE773A7C5527EA8E63347E5C04A74C67A4D06F0F77C0E288FD | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:2FF0AC2E8A788B7A6BAC7A4DDEAF2F3C | SHA256:545E719DC5523C941D3AD50F44C4ECED99762E765FE62CA552567D75174CEBCF | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_282DA3197C86E94FA20C5EBD2346C496.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 7148 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:CBF8314B2A8B40129DC12E85375E106A | SHA256:259F3B2C25D0A17B988A8021BC6F37D58C3EB4A637657519CC442BE17B7FED80 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
35
DNS requests
23
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7148 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7148 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | GET | 200 | 198.12.83.90:80 | http://198.12.83.90/sSRMUAsYfyWZW31.bin | unknown | — | — | unknown |
7844 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
8116 | Nómina de sueldos_786654578568764579656457865648589.exe | GET | 200 | 198.12.83.90:80 | http://198.12.83.90/sSRMUAsYfyWZW31.bin | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.139:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7148 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7148 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7148 | OUTLOOK.EXE | 52.109.28.47:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7148 | OUTLOOK.EXE | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | Malware Command and Control Activity Detected | ET MALWARE MSIL/Kryptik.XSY Data Exfil via SMTP |
7928 | Nómina de sueldos_786654578568764579656457865648589.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration SMTP (Base64 encoded) |
8116 | Nómina de sueldos_786654578568764579656457865648589.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
8116 | Nómina de sueldos_786654578568764579656457865648589.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |