| URL: | http://dl.drp.su/17-online/DriverPack-17-Online.exe |
| Full analysis: | https://app.any.run/tasks/5f59646a-d601-4da5-a1a9-802df8aa98b5 |
| Verdict: | Malicious activity |
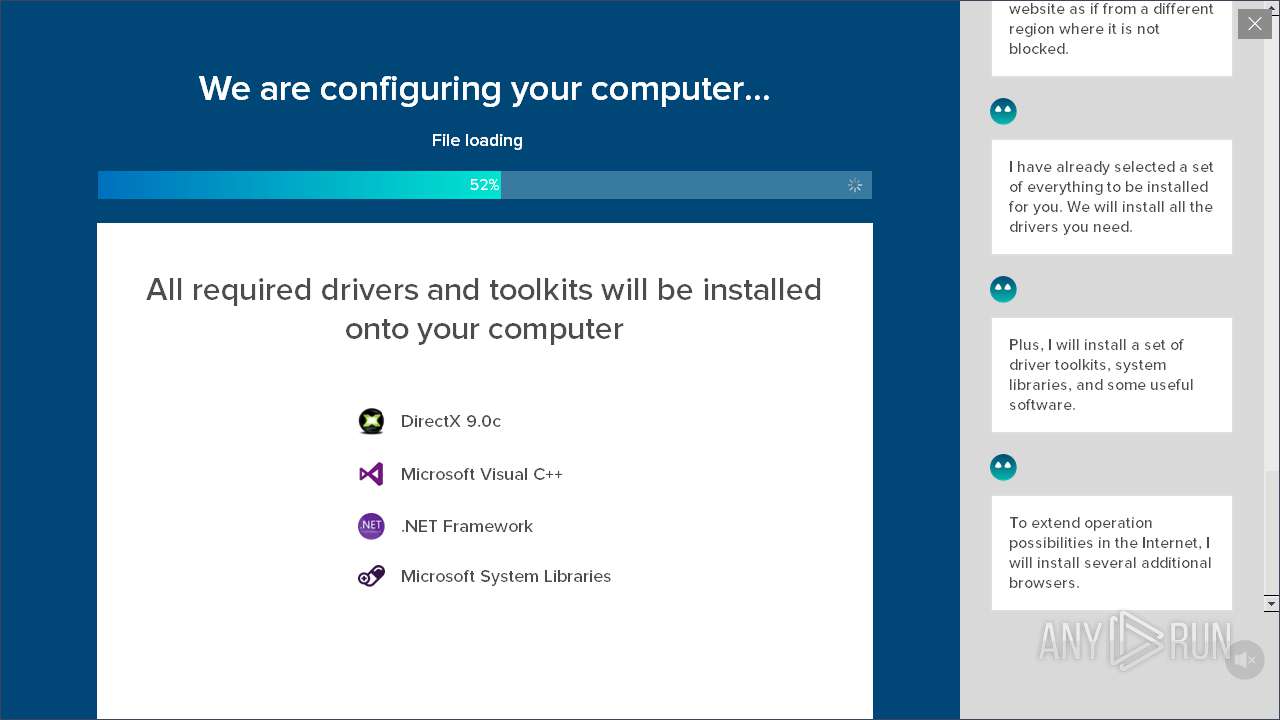
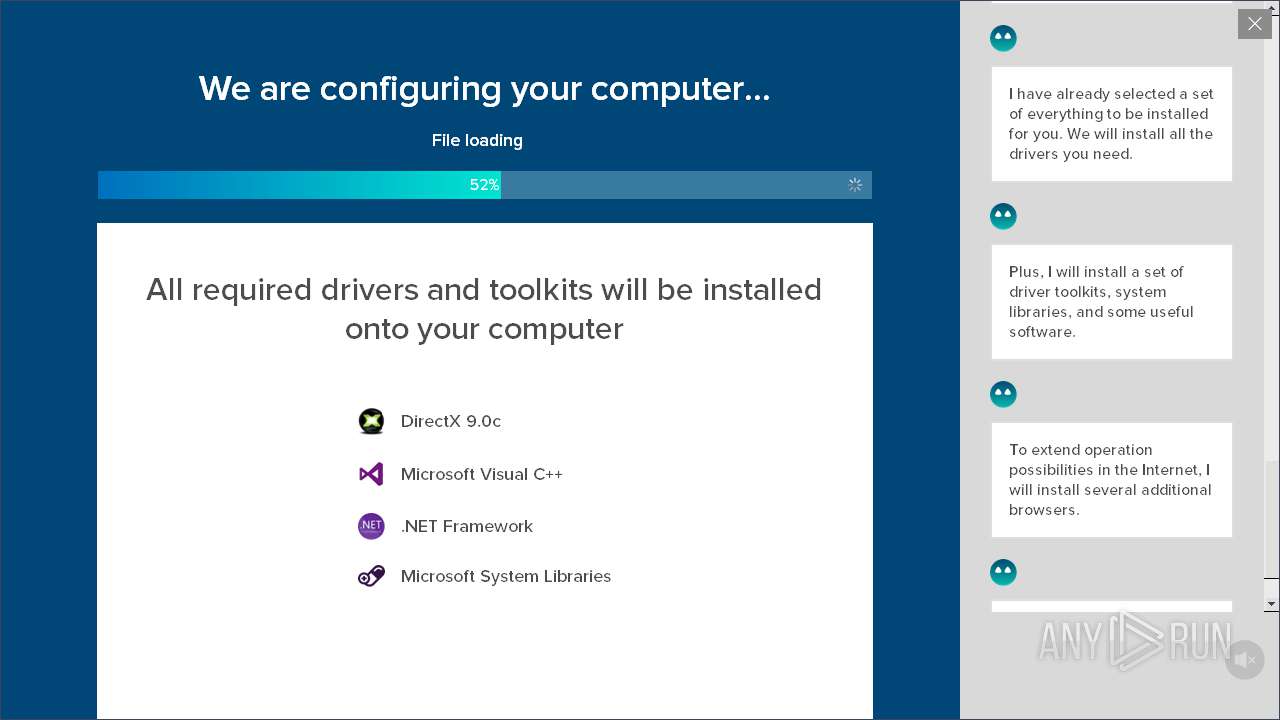
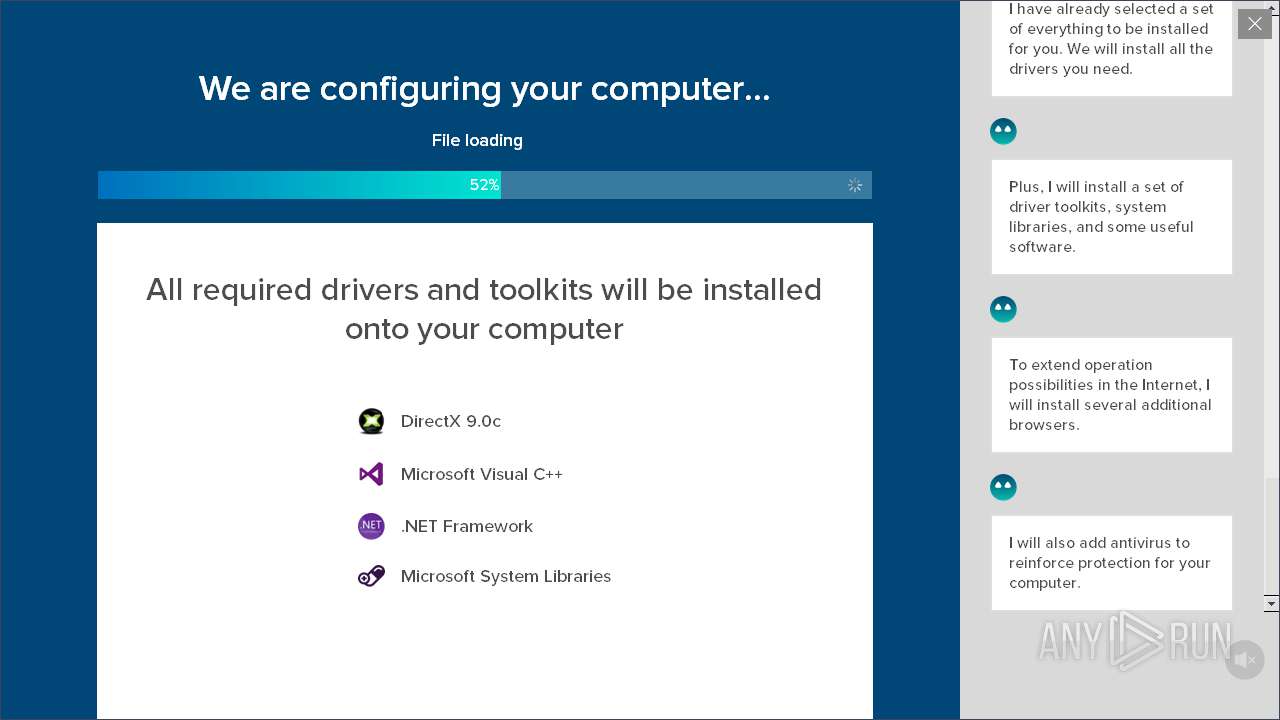
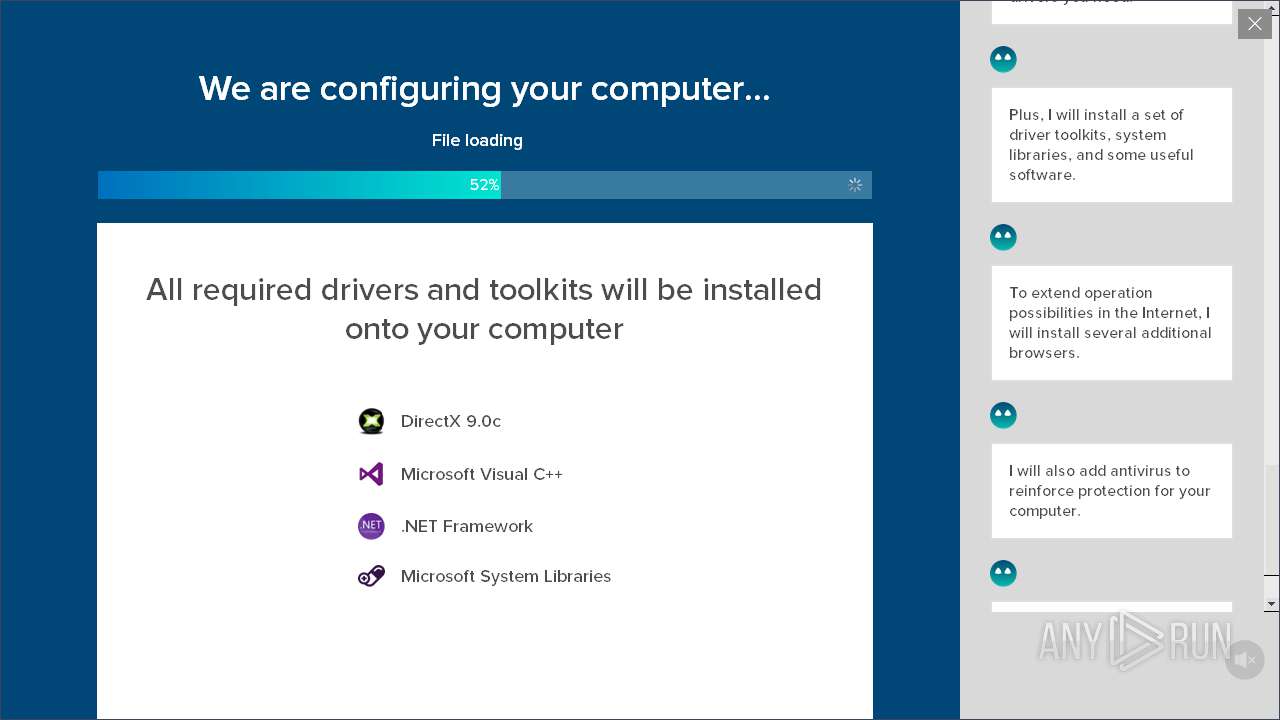
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | January 16, 2020, 05:14:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3485D8868E721ABB8F3F4D08C82139B8 |
| SHA1: | 272052EE859BC73846D9988C9023957C0D9EFFBB |
| SHA256: | 8FE4310B83279F710740331F3A2485F79C4ECA6E7DCEB7386BDD205B7D247D5B |
| SSDEEP: | 3:N1KaJdAQPSIWQbkAn:CaJdA8STAn |
MALICIOUS
Application was dropped or rewritten from another process
- DriverPack-17-Online.exe (PID: 896)
- DriverPack-17-Online.exe (PID: 2120)
- aria2c.exe (PID: 3264)
- aria2c.exe (PID: 2112)
- aria2c.exe (PID: 1764)
- aria2c.exe (PID: 3800)
- driverpack-7za.exe (PID: 3172)
- devcon.exe (PID: 3352)
- driverpack-7za.exe (PID: 584)
- DriverPack-Alice.exe (PID: 3496)
- RuntimePack.exe (PID: 2628)
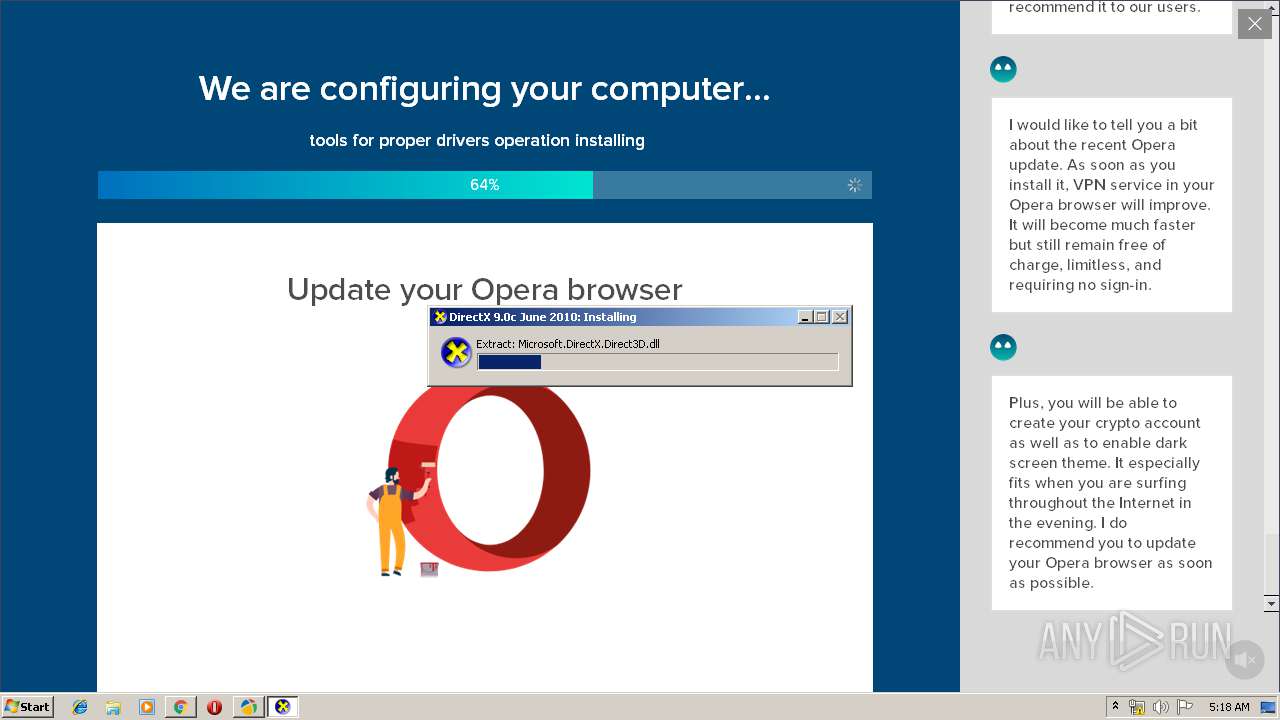
- DirectX.exe (PID: 2840)
Loads dropped or rewritten executable
- DriverPack-17-Online.exe (PID: 2120)
- devcon.exe (PID: 3352)
- DrvInst.exe (PID: 388)
- regsvr32.exe (PID: 2156)
- regsvr32.exe (PID: 2756)
- regsvr32.exe (PID: 2292)
- regsvr32.exe (PID: 1544)
- regsvr32.exe (PID: 2864)
- regsvr32.exe (PID: 3712)
- regsvr32.exe (PID: 3272)
- regsvr32.exe (PID: 3992)
- regsvr32.exe (PID: 3508)
- regsvr32.exe (PID: 2796)
- regsvr32.exe (PID: 520)
- regsvr32.exe (PID: 584)
- regsvr32.exe (PID: 3272)
- regsvr32.exe (PID: 2216)
- regsvr32.exe (PID: 3268)
- regsvr32.exe (PID: 1252)
- regsvr32.exe (PID: 3836)
- regsvr32.exe (PID: 592)
- regsvr32.exe (PID: 1908)
- regsvr32.exe (PID: 2244)
- regsvr32.exe (PID: 1908)
- regsvr32.exe (PID: 3100)
- regsvr32.exe (PID: 3916)
- DirectX.exe (PID: 2840)
- regsvr32.exe (PID: 3892)
- regsvr32.exe (PID: 3208)
- regsvr32.exe (PID: 324)
- regsvr32.exe (PID: 2284)
- regsvr32.exe (PID: 2992)
- regsvr32.exe (PID: 3548)
- regsvr32.exe (PID: 3364)
- regsvr32.exe (PID: 3268)
- regsvr32.exe (PID: 2872)
- regsvr32.exe (PID: 4080)
- regsvr32.exe (PID: 2432)
- regsvr32.exe (PID: 3904)
- regsvr32.exe (PID: 3308)
- regsvr32.exe (PID: 1744)
- regsvr32.exe (PID: 3296)
- regsvr32.exe (PID: 3836)
- regsvr32.exe (PID: 2732)
- regsvr32.exe (PID: 1856)
- regsvr32.exe (PID: 2624)
- regsvr32.exe (PID: 2548)
- regsvr32.exe (PID: 4064)
- regsvr32.exe (PID: 1324)
- regsvr32.exe (PID: 2184)
- regsvr32.exe (PID: 1896)
- regsvr32.exe (PID: 2180)
- regsvr32.exe (PID: 2988)
- regsvr32.exe (PID: 3156)
Downloads executable files from the Internet
- chrome.exe (PID: 1600)
- mshta.exe (PID: 2524)
- aria2c.exe (PID: 2112)
- aria2c.exe (PID: 1764)
- aria2c.exe (PID: 3264)
Executes PowerShell scripts
- cmd.exe (PID: 3396)
Changes settings of System certificates
- mshta.exe (PID: 2524)
Changes internet zones settings
- mshta.exe (PID: 2524)
Starts Visual C# compiler
- powershell.exe (PID: 2248)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 2976)
- RuntimePack.exe (PID: 2628)
- DirectX.exe (PID: 2840)
Changes the autorun value in the registry
- mshta.exe (PID: 2524)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2160)
- DriverPack-17-Online.exe (PID: 2120)
- mshta.exe (PID: 2524)
- chrome.exe (PID: 1600)
- driverpack-7za.exe (PID: 3172)
- aria2c.exe (PID: 2112)
- devcon.exe (PID: 3352)
- DrvInst.exe (PID: 1712)
- DrvInst.exe (PID: 388)
- aria2c.exe (PID: 1764)
- RuntimePack.exe (PID: 2628)
- xcopy.exe (PID: 2584)
- xcopy.exe (PID: 3620)
- cmd.exe (PID: 2976)
- DriverPack-Alice.exe (PID: 3496)
- DirectX.exe (PID: 2840)
Starts MSHTA.EXE for opening HTA or HTMLS files
- DriverPack-17-Online.exe (PID: 2120)
Creates files in the user directory
- mshta.exe (PID: 2524)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 3900)
- powershell.exe (PID: 2248)
- cmd.exe (PID: 3412)
- cmd.exe (PID: 2348)
- cmd.exe (PID: 1292)
- cmd.exe (PID: 1704)
- aria2c.exe (PID: 3264)
- aria2c.exe (PID: 3800)
- aria2c.exe (PID: 2112)
- aria2c.exe (PID: 1764)
- cmd.exe (PID: 3584)
- cmd.exe (PID: 2296)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 1852)
- cmd.exe (PID: 3912)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 2820)
- cmd.exe (PID: 2132)
- cmd.exe (PID: 1104)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 3744)
- DriverPack-Alice.exe (PID: 3496)
Uses REG.EXE to modify Windows registry
- DriverPack-17-Online.exe (PID: 2120)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 2524)
- cmd.exe (PID: 3584)
- RuntimePack.exe (PID: 2628)
Adds / modifies Windows certificates
- mshta.exe (PID: 2524)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3900)
- cmd.exe (PID: 3412)
- cmd.exe (PID: 2348)
- mshta.exe (PID: 2524)
Uses RUNDLL32.EXE to load library
- mshta.exe (PID: 2524)
- DrvInst.exe (PID: 1712)
Starts application with an unusual extension
- cmd.exe (PID: 2348)
- cmd.exe (PID: 3584)
Executed as Windows Service
- vssvc.exe (PID: 2332)
Starts SC.EXE for service management
- cmd.exe (PID: 1292)
Executed via COM
- DllHost.exe (PID: 2348)
- DrvInst.exe (PID: 1712)
- DrvInst.exe (PID: 388)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 3584)
Application launched itself
- cmd.exe (PID: 3584)
Removes files from Windows directory
- DrvInst.exe (PID: 1712)
- DrvInst.exe (PID: 388)
Creates files in the driver directory
- DrvInst.exe (PID: 1712)
- DrvInst.exe (PID: 388)
Creates files in the Windows directory
- DrvInst.exe (PID: 1712)
- DrvInst.exe (PID: 388)
- cmd.exe (PID: 2976)
- xcopy.exe (PID: 2584)
- xcopy.exe (PID: 3620)
- DirectX.exe (PID: 2840)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2160)
Creates COM task schedule object
- regsvr32.exe (PID: 1252)
- regsvr32.exe (PID: 3308)
- regsvr32.exe (PID: 3548)
- regsvr32.exe (PID: 2432)
- regsvr32.exe (PID: 1744)
- regsvr32.exe (PID: 2184)
- regsvr32.exe (PID: 4064)
- regsvr32.exe (PID: 2624)
- regsvr32.exe (PID: 1856)
- regsvr32.exe (PID: 2732)
- regsvr32.exe (PID: 1896)
- regsvr32.exe (PID: 1324)
- regsvr32.exe (PID: 3296)
- regsvr32.exe (PID: 3904)
- regsvr32.exe (PID: 3836)
- regsvr32.exe (PID: 2548)
- regsvr32.exe (PID: 3156)
- regsvr32.exe (PID: 2284)
- regsvr32.exe (PID: 2180)
- regsvr32.exe (PID: 2988)
- regsvr32.exe (PID: 2992)
- regsvr32.exe (PID: 3208)
- regsvr32.exe (PID: 3268)
- regsvr32.exe (PID: 3892)
- regsvr32.exe (PID: 3364)
- regsvr32.exe (PID: 324)
- regsvr32.exe (PID: 2872)
- regsvr32.exe (PID: 3836)
- regsvr32.exe (PID: 4080)
INFO
Reads the hosts file
- chrome.exe (PID: 1600)
- chrome.exe (PID: 2160)
- aria2c.exe (PID: 3800)
- aria2c.exe (PID: 2112)
- aria2c.exe (PID: 1764)
- aria2c.exe (PID: 3264)
Reads Internet Cache Settings
- chrome.exe (PID: 2160)
Reads internet explorer settings
- mshta.exe (PID: 2524)
Creates files in the user directory
- chrome.exe (PID: 2160)
Reads settings of System Certificates
- mshta.exe (PID: 2524)
- chrome.exe (PID: 1600)
Application launched itself
- chrome.exe (PID: 2160)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2332)
Searches for installed software
- DrvInst.exe (PID: 1712)
Dropped object may contain Bitcoin addresses
- DriverPack-Alice.exe (PID: 3496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
217
Monitored processes
151
Malicious processes
18
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | wmic.exe /Namespace:\\root\default Path SystemRestore Call CreateRestorePoint "DriverPack 17.11.25", 100, 10 | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | regsvr32 /s XAudio2_4.dll | C:\Windows\system32\regsvr32.exe | — | DirectX.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | DrvInst.exe "2" "211" "PCI\VEN_1AF4&DEV_1002&SUBSYS_00051AF4&REV_00\3&13C0B0C5&0&28" "C:\Windows\INF\oem4.inf" "balloon.inf:Standard.NTx86:BALLOON_Device:61.70.104.8100:pci\ven_1af4&dev_1002&subsys_00051af4&rev_00" "66c84179b" "000005D0" "000005F4" "000005F8" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=984,18050591135156919140,2177277621110513208,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17405205049380770312 --mojo-platform-channel-handle=1372 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=984,18050591135156919140,2177277621110513208,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15107301553094565450 --mojo-platform-channel-handle=876 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 520 | "C:\Windows\System32\regsvr32.exe" /S msflxgrd.ocx | C:\Windows\System32\regsvr32.exe | — | RuntimePack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 520 | bitsadmin /resume drp_bits_job | C:\Windows\system32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: BITS administration utility Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | tools\driverpack-7za.exe l "C:\Users\admin\AppData\Roaming\DRPSu\DRIVERS\KVM-FORCED-7x86-drp.zip" | C:\Users\admin\AppData\Local\Temp\DriverPack-2020011651524\tools\driverpack-7za.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
| 584 | "C:\Windows\System32\regsvr32.exe" /S mshflxgd.ocx | C:\Windows\System32\regsvr32.exe | — | RuntimePack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | "C:\Windows\System32\regsvr32.exe" /S richtx32.ocx | C:\Windows\System32\regsvr32.exe | — | RuntimePack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 107
Read events
2 991
Write events
3 804
Delete events
312
Modification events
| (PID) Process: | (2564) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2160-13223625308263250 |
Value: 259 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (2160) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
295
Suspicious files
133
Text files
6 979
Unknown types
65
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\95ed2809-6162-45c1-b950-db45e7d48c13.tmp | — | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF39a581.TMP | text | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF39a5c0.TMP | text | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\MANIFEST-000001 | — | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2160 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF39a5df.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
322
TCP/UDP connections
285
DNS requests
46
Threats
518
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1600 | chrome.exe | GET | 200 | 87.117.231.157:80 | http://dl.drp.su/17-online/DriverPack-17-Online.exe | GB | executable | 6.44 Mb | whitelisted |
2524 | mshta.exe | GET | 301 | 104.27.186.38:80 | http://allfont.ru/allfont.css?fonts=lucida-console | US | html | 552 b | whitelisted |
2524 | mshta.exe | GET | 200 | 81.94.192.167:80 | http://download.drp.su/updates/beetle/driverpack-wget.exe | GB | executable | 392 Kb | malicious |
2524 | mshta.exe | GET | 200 | 37.9.8.75:80 | http://update.drp.su/ | RU | html | 141 b | malicious |
2524 | mshta.exe | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | text | 24 b | malicious |
2524 | mshta.exe | GET | 200 | 216.58.207.46:80 | http://www.google-analytics.com/collect?v=1&ds=hta&tid=UA-68879973-26&cid=255848950.0784551087&t=event&ec=driverpack%20online&ea=application%20opened&el=17.11.25%20online&ul=&z=7890334220540347&sc=start&cd1=255848950.0784551087&cd2=17.11.25%20Online&cd3=7%20x86&cd4=SP%201&cd5=Windows%207%20Professional%20&cd6=(not%20set) | US | image | 35 b | whitelisted |
2524 | mshta.exe | GET | 200 | 216.58.207.46:80 | http://www.google-analytics.com/collect?v=1&ds=hta&tid=UA-69093127-16&cid=255848950.0784551087&t=event&ec=driverpack%20online&ea=application%20opened&el=17.11.25%20online&ul=&z=9207208540545999&sc=start&cd1=255848950.0784551087&cd2=17.11.25%20Online&cd3=7%20x86&cd4=SP%201&cd5=Windows%207%20Professional%20&cd6=(not%20set) | US | image | 35 b | whitelisted |
2524 | mshta.exe | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | text | 24 b | malicious |
2524 | mshta.exe | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | text | 24 b | malicious |
2524 | mshta.exe | POST | 202 | 37.9.8.75:80 | http://update.drp.su/api/logs | RU | text | 24 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1600 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1600 | chrome.exe | 87.117.231.157:80 | dl.drp.su | iomart Cloud Services Limited. | GB | malicious |
1600 | chrome.exe | 216.58.208.46:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1600 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
1600 | chrome.exe | 172.217.16.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1600 | chrome.exe | 216.58.208.36:443 | www.google.com | Google Inc. | US | whitelisted |
2524 | mshta.exe | 104.27.186.38:80 | allfont.ru | Cloudflare Inc | US | unknown |
2524 | mshta.exe | 178.162.204.5:80 | auth.drp.su | Leaseweb Deutschland GmbH | DE | suspicious |
2524 | mshta.exe | 77.88.21.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
2524 | mshta.exe | 37.9.8.75:80 | update.drp.su | Dominanta CTV Ltd | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
dl.drp.su |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
allfont.ru |
| whitelisted |
auth.drp.su |
| suspicious |
mc.yandex.ru |
| whitelisted |
update.drp.su |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1600 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
1600 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2524 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2524 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2524 | mshta.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2524 | mshta.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
82 ETPRO signatures available at the full report
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|