| File name: | system-scan.msi |
| Full analysis: | https://app.any.run/tasks/3308282e-c290-409a-a940-a93b819bc8f5 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | August 24, 2024, 16:03:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
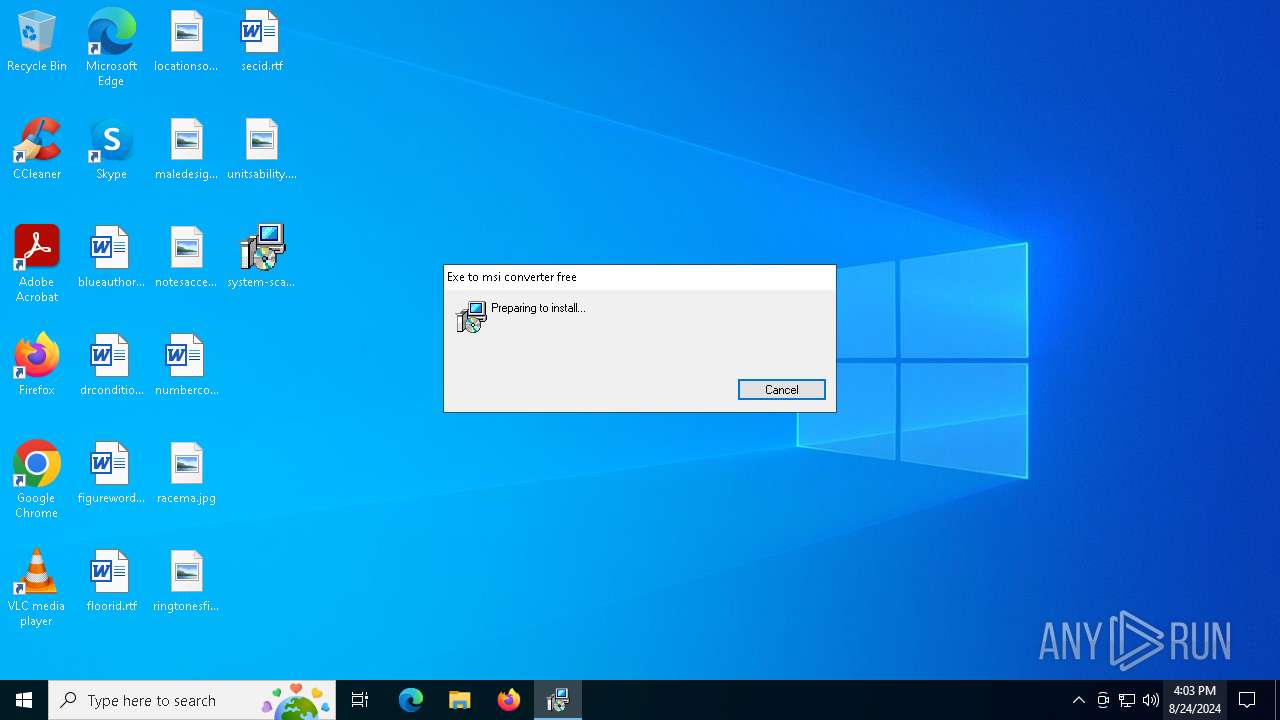
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Last Printed: Fri Sep 21 09:56:09 2012, Create Time/Date: Fri Sep 21 09:56:09 2012, Name of Creating Application: Windows Installer, Title: Exe to msi converter free, Author: www.exetomsi.com, Template: ;0, Last Saved By: devuser, Revision Number: {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E}, Last Saved Time/Date: Tue May 21 11:56:44 2013, Number of Pages: 100, Number of Words: 0, Security: 0 |
| MD5: | 85E87BEE47AA51159F27118E742CB643 |
| SHA1: | 645701E8934E7C4261F001AC029114D74A8DEB36 |
| SHA256: | 8FD972EEDB519A22A8B2FA8E705833F603B7FABC2DB1818CFA2D18380982B788 |
| SSDEEP: | 3072:1EHq5DlfEHcMYMcelfwD2lmJ7TMftdT72yddlKCL52632wx9MtEPPX16N11+bkbY:1EHWDuHweCy6GtdTisdjNfkQoaaRm |
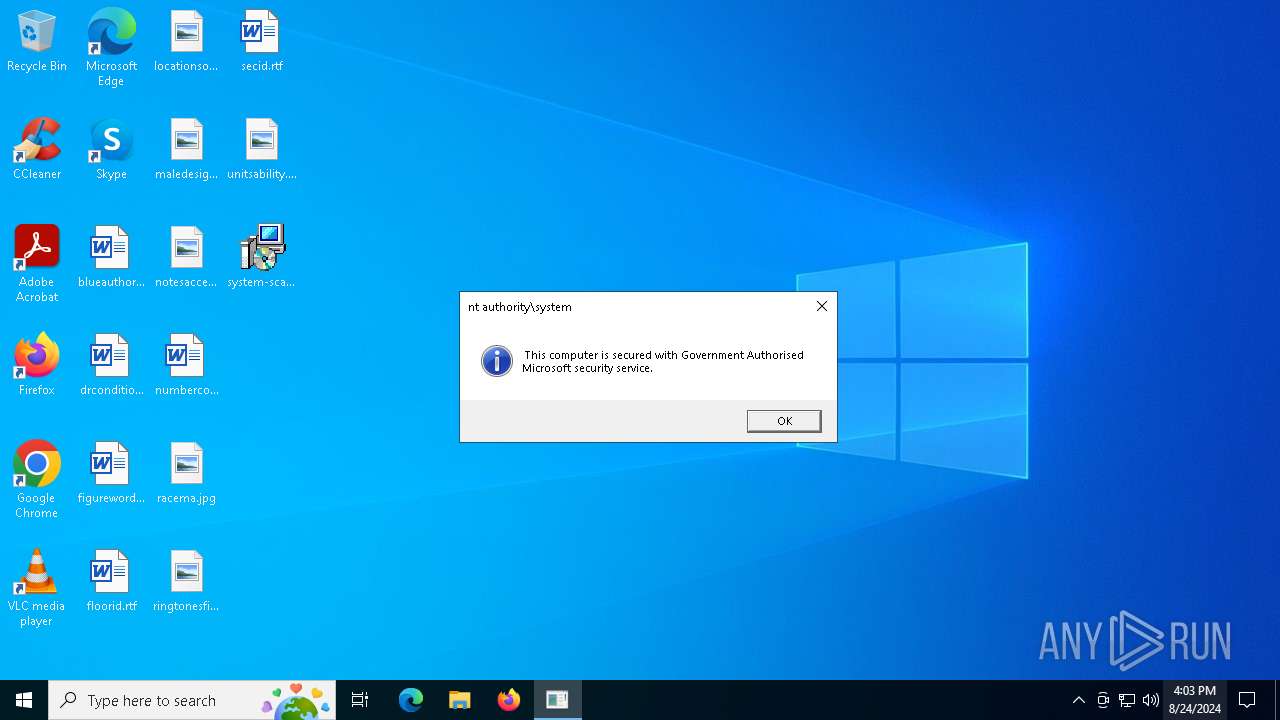
MALICIOUS
Changes powershell execution policy (Bypass)
- MSI23EC.tmp (PID: 1356)
Run PowerShell with an invisible window
- powershell.exe (PID: 3184)
Bypass execution policy to execute commands
- powershell.exe (PID: 3184)
Disables Windows Defender
- reg.exe (PID: 5552)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 6124)
ASYNCRAT has been detected (YARA)
- Realtek Hd Audio Manager.exe (PID: 3292)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6876)
Drops the executable file immediately after the start
- msiexec.exe (PID: 6728)
- msiexec.exe (PID: 6828)
- powershell.exe (PID: 3184)
- audio-driver.exe (PID: 6688)
Drops the ExeToMSI Application
- msiexec.exe (PID: 6828)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6828)
Executable content was dropped or overwritten
- powershell.exe (PID: 3184)
- audio-driver.exe (PID: 6688)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 3184)
Starts POWERSHELL.EXE for commands execution
- MSI23EC.tmp (PID: 1356)
The process executes Powershell scripts
- MSI23EC.tmp (PID: 1356)
Uses ATTRIB.EXE to modify file attributes
- powershell.exe (PID: 3184)
Reads security settings of Internet Explorer
- audio-driver.exe (PID: 6688)
Reads the date of Windows installation
- audio-driver.exe (PID: 6688)
Starts CMD.EXE for commands execution
- audio-driver.exe (PID: 6688)
Executing commands from a ".bat" file
- audio-driver.exe (PID: 6688)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3840)
The executable file from the user directory is run by the CMD process
- Realtek Hd Audio Manager.exe (PID: 3292)
Identifying current user with WHOAMI command
- powershell.exe (PID: 3184)
Potential Corporate Privacy Violation
- powershell.exe (PID: 3184)
INFO
Checks supported languages
- msiexec.exe (PID: 6828)
- H.exe (PID: 360)
- H.exe (PID: 1020)
- audio-driver.exe (PID: 6688)
- MSI23EC.tmp (PID: 1356)
- Realtek Hd Audio Manager.exe (PID: 3292)
Reads the computer name
- msiexec.exe (PID: 6828)
- audio-driver.exe (PID: 6688)
- Realtek Hd Audio Manager.exe (PID: 3292)
Starts application with an unusual extension
- msiexec.exe (PID: 6828)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6828)
Disables trace logs
- powershell.exe (PID: 3184)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3184)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3184)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3184)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3184)
Process checks computer location settings
- audio-driver.exe (PID: 6688)
Create files in a temporary directory
- audio-driver.exe (PID: 6688)
Creates files or folders in the user directory
- audio-driver.exe (PID: 6688)
Reads the machine GUID from the registry
- audio-driver.exe (PID: 6688)
- Realtek Hd Audio Manager.exe (PID: 3292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3292) Realtek Hd Audio Manager.exe
C2 (3)127.0.0.1
tech11.ddns.net
tech22.ddns.net
Ports (1)9119
Version0.5.8
BotnetENC
Options
AutoRuntrue
Mutex2mrNAWQOEEMm
InstallFolder%AppData%
BSoDtrue
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQALlhsKYTwQ/uwpo3xpnnGTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjQwMzI0MTExNzQxWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIx8eB29B2DrgV9IOkrX7plC1dEHnkUAAcCRgSrK8BikmdzzKMLZzAu0pFJnFIid+gB8uJ2ySkHJ...
Server_SignatureILhmYgY6DjekULh1UdtsBLo1ILbfA4CZMUgplGpGT1oJvpCWobWmdsWBUr2r6K3W3nzmd/vh5RXjrStneShV/BhRbPfaWeR9ddjZChqxeHyIxvmaf6bDylgnKNDulVxS5zw4O3dPaQ8AxZUw9vsz1iQwZn22t9+iD9m0ACYaCaTcrh3f9WaTNE9wmLdqluWKf5ZNyTQNl4pXWtHbtnxbZfs9DlhF0wiX/8aZtQv1Oemz0+lFEVQcV3cjzm+hxpCGFqSYF0Es4IUXZ7ULqS1BlwEhwxgAW+PLHPHQjfyy37yk...
Keys
AESfab2d612fe03de05c3c4e25c3b4327d67797fc41070fd69566d7691a55432679
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| LastPrinted: | 2012:09:21 09:56:09 |
| CreateDate: | 2012:09:21 09:56:09 |
| Software: | Windows Installer |
| Title: | Exe to msi converter free |
| Subject: | - |
| Author: | www.exetomsi.com |
| Keywords: | - |
| Comments: | - |
| Template: | ;0 |
| LastModifiedBy: | devuser |
| RevisionNumber: | {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E} |
| ModifyDate: | 2013:05:21 11:56:44 |
| Pages: | 100 |
| Words: | - |
| Security: | None |
Total processes
148
Monitored processes
22
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\subsystem\H.exe" -i c:\subsystem\1.reg -m decrypt -k c:\subsystem\1 | C:\subsystem\H.exe | — | powershell.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1020 | "C:\subsystem\H.exe" -i audio-driver.exe -m decrypt -ks UBF9d81l1LGA#%xC@2XRYVTaGU4f!Ym | C:\subsystem\H.exe | — | powershell.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1356 | "C:\WINDOWS\Installer\MSI23EC.tmp" /s | C:\Windows\Installer\MSI23EC.tmp | — | msiexec.exe | |||||||||||
User: admin Company: TODO: <Company name> Integrity Level: MEDIUM Description: TODO: <File description> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3184 | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -file "C:\Users\admin\AppData\Local\Temp\ps241A.tmp.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | MSI23EC.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3292 | "C:\Users\admin\AppData\Roaming\Realtek Hd Audio Manager.exe" | C:\Users\admin\AppData\Roaming\Realtek Hd Audio Manager.exe | cmd.exe | ||||||||||||
User: SYSTEM Company: Realtek Integrity Level: SYSTEM Description: Audio Driver Version: 9.7.0.0 Modules
AsyncRat(PID) Process(3292) Realtek Hd Audio Manager.exe C2 (3)127.0.0.1 tech11.ddns.net tech22.ddns.net Ports (1)9119 Version0.5.8 BotnetENC Options AutoRuntrue Mutex2mrNAWQOEEMm InstallFolder%AppData% BSoDtrue AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQALlhsKYTwQ/uwpo3xpnnGTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjQwMzI0MTExNzQxWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIx8eB29B2DrgV9IOkrX7plC1dEHnkUAAcCRgSrK8BikmdzzKMLZzAu0pFJnFIid+gB8uJ2ySkHJ... Server_SignatureILhmYgY6DjekULh1UdtsBLo1ILbfA4CZMUgplGpGT1oJvpCWobWmdsWBUr2r6K3W3nzmd/vh5RXjrStneShV/BhRbPfaWeR9ddjZChqxeHyIxvmaf6bDylgnKNDulVxS5zw4O3dPaQ8AxZUw9vsz1iQwZn22t9+iD9m0ACYaCaTcrh3f9WaTNE9wmLdqluWKf5ZNyTQNl4pXWtHbtnxbZfs9DlhF0wiX/8aZtQv1Oemz0+lFEVQcV3cjzm+hxpCGFqSYF0Es4IUXZ7ULqS1BlwEhwxgAW+PLHPHQjfyy37yk... Keys AESfab2d612fe03de05c3c4e25c3b4327d67797fc41070fd69566d7691a55432679 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 3840 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp67F9.tmp.bat"" | C:\Windows\SysWOW64\cmd.exe | — | audio-driver.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | schtasks /create /f /sc onlogon /rl highest /tn "Realtek Hd Audio Manager" /tr '"C:\Users\admin\AppData\Roaming\Realtek Hd Audio Manager.exe"' | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 553
Read events
16 300
Write events
234
Delete events
19
Modification events
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000C5FE50283FF6DA01AC1A0000CC1A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000C5FE50283FF6DA01AC1A0000CC1A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000000DA29F283FF6DA01AC1A0000CC1A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000000DA29F283FF6DA01AC1A0000CC1A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000EF04A2283FF6DA01AC1A0000CC1A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000BB30A9283FF6DA01AC1A0000CC1A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000063D19293FF6DA01AC1A0000CC1A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BEA11B293FF6DA01AC1A0000981B0000E80300000100000000000000000000002E1081B2FE457B42AB48A19BE9E40E7900000000000000000000000000000000 | |||
| (PID) Process: | (6876) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000E4CD22293FF6DA01DC1A0000101B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
22
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6828 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6828 | msiexec.exe | C:\Windows\Installer\12218a.msi | executable | |
MD5:85E87BEE47AA51159F27118E742CB643 | SHA256:8FD972EEDB519A22A8B2FA8E705833F603B7FABC2DB1818CFA2D18380982B788 | |||
| 6828 | msiexec.exe | C:\Windows\Installer\MSI237E.tmp | binary | |
MD5:FBFF8FB852D80263B51B364ED00CC020 | SHA256:6B86D3A282C2C15265CCB27817D347FE5F597F57C2EF6CD74164DD5EF0FF3D19 | |||
| 6828 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:0DB8093046F4457193EB314FCE71D7B7 | SHA256:A4405CF359D1BFAD63AAA300BBDA12BE68016562BF983EBA0195D3924EA91B84 | |||
| 6828 | msiexec.exe | C:\Windows\Installer\MSI23EC.tmp | executable | |
MD5:F3C2AB7113AC26675995F3D4FC5C87B2 | SHA256:838F4689740AF3B692E3E2060690FB65EE4C1921593AB6FEB4C840FF6EBF90FD | |||
| 6828 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:D13AF1C8E0225CFF70DAF0C1E8C41EFC | SHA256:3FCC43E520059D082BDA7119BD0113E8AEBD09D112494D645CE469DA90C30EE9 | |||
| 1356 | MSI23EC.tmp | C:\Users\admin\AppData\Local\Temp\ps241A.tmp | text | |
MD5:985D54664DCCE4666E49CA661063B925 | SHA256:BF8E98B473ADAC13902B7557D3CBA744402A5996A137B952E40CC87FAC037B2B | |||
| 6828 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{b281102e-45fe-427b-ab48-a19be9e40e79}_OnDiskSnapshotProp | binary | |
MD5:0DB8093046F4457193EB314FCE71D7B7 | SHA256:A4405CF359D1BFAD63AAA300BBDA12BE68016562BF983EBA0195D3924EA91B84 | |||
| 6828 | msiexec.exe | C:\Windows\Temp\~DFAB0D64E9F4CBA12E.TMP | binary | |
MD5:D13AF1C8E0225CFF70DAF0C1E8C41EFC | SHA256:3FCC43E520059D082BDA7119BD0113E8AEBD09D112494D645CE469DA90C30EE9 | |||
| 6828 | msiexec.exe | C:\Windows\Temp\~DF3DBEDF3A6E04AFB1.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
18
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3184 | powershell.exe | GET | 200 | 91.92.244.233:80 | http://subsystem.servehttp.com/SETUP/1.reg | unknown | — | — | unknown |
3184 | powershell.exe | GET | 200 | 91.92.244.233:80 | http://subsystem.servehttp.com/SETUP/1 | unknown | — | — | unknown |
3184 | powershell.exe | GET | 200 | 91.92.244.233:80 | http://subsystem.servehttp.com/SETUP/audio-driver.exe | unknown | — | — | unknown |
3184 | powershell.exe | GET | 200 | 91.92.244.233:80 | http://subsystem.servehttp.com/SETUP/H.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1360 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1616 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3184 | powershell.exe | 91.92.244.233:80 | subsystem.servehttp.com | Natskovi & Sie Ltd. | BG | unknown |
2344 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
subsystem.servehttp.com |
| unknown |
tech22.ddns.net |
| malicious |
tech11.ddns.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
3184 | powershell.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.servehttp .com Domain |
3184 | powershell.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.servehttp .com Domain |
3184 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3184 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3184 | powershell.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
3184 | powershell.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.servehttp .com Domain |
3184 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3184 | powershell.exe | Misc activity | ET INFO Packed Executable Download |
3184 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2 ETPRO signatures available at the full report