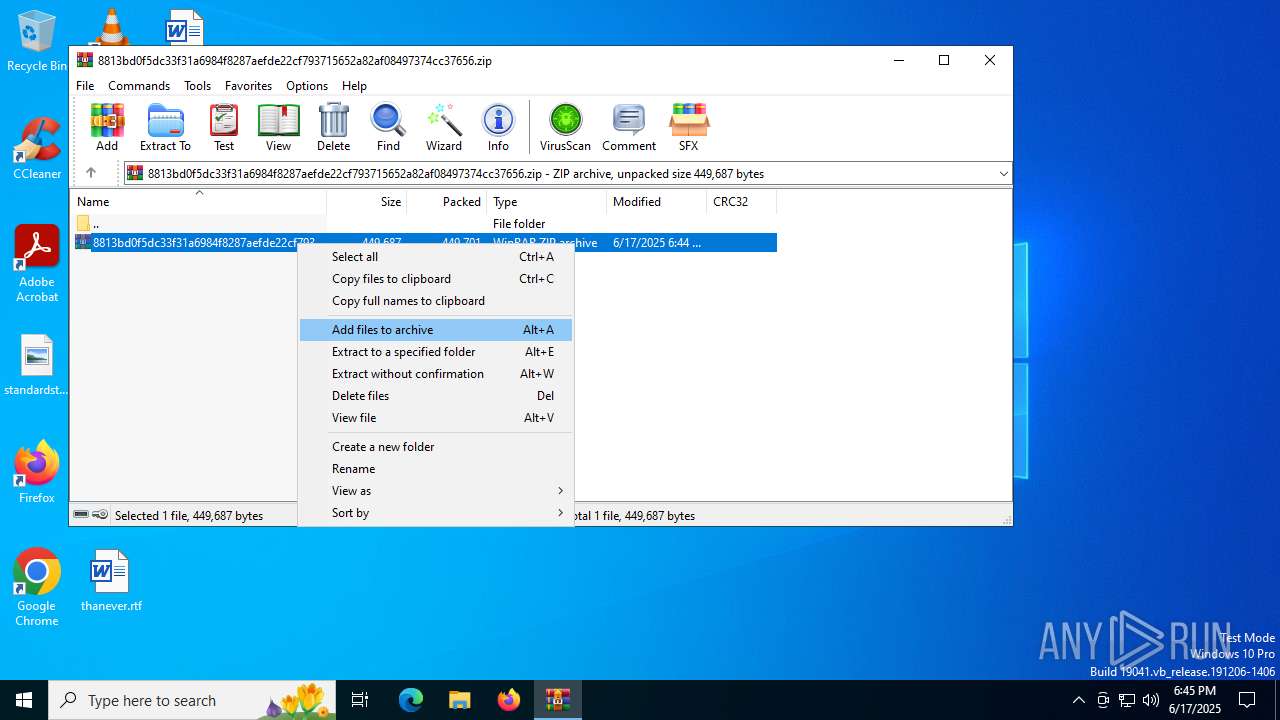
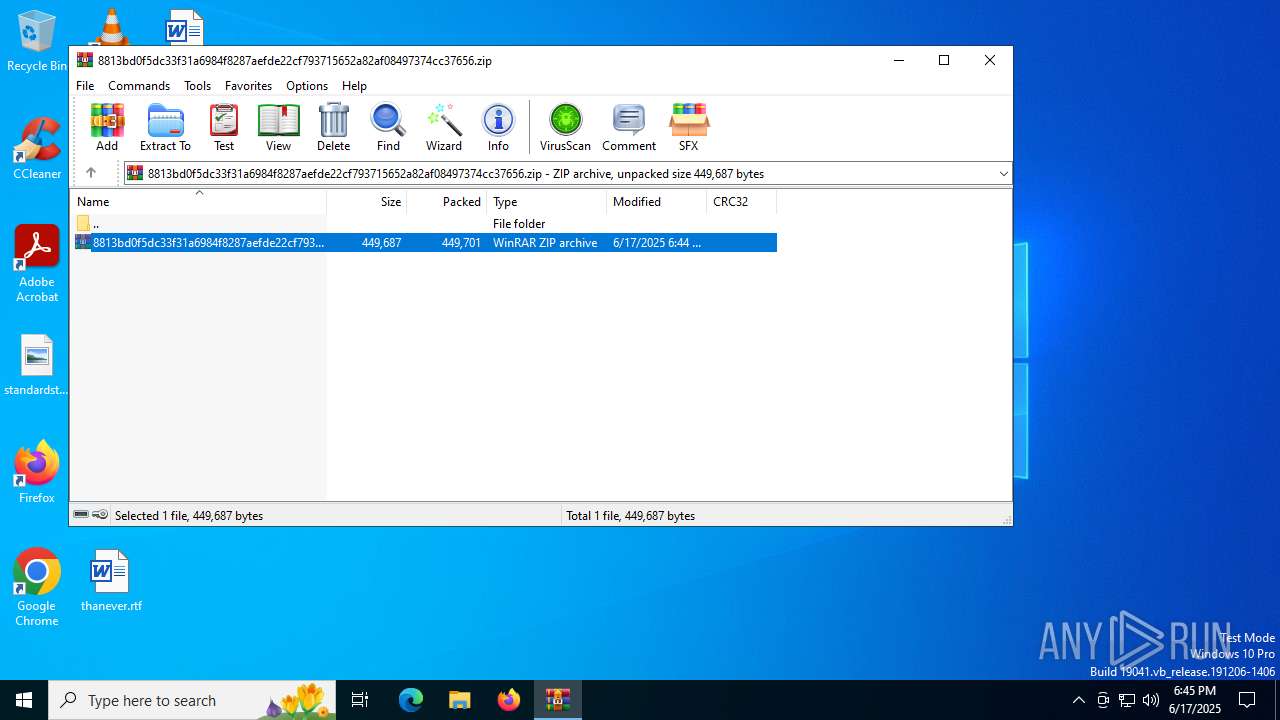
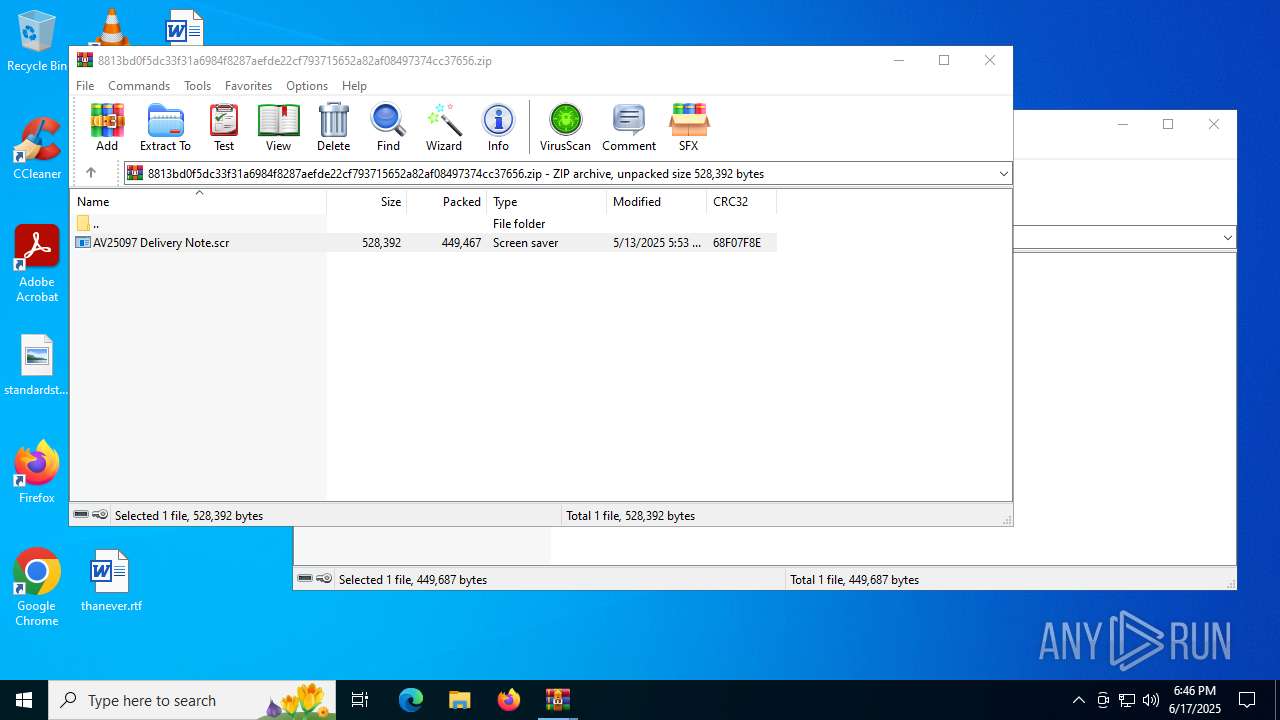
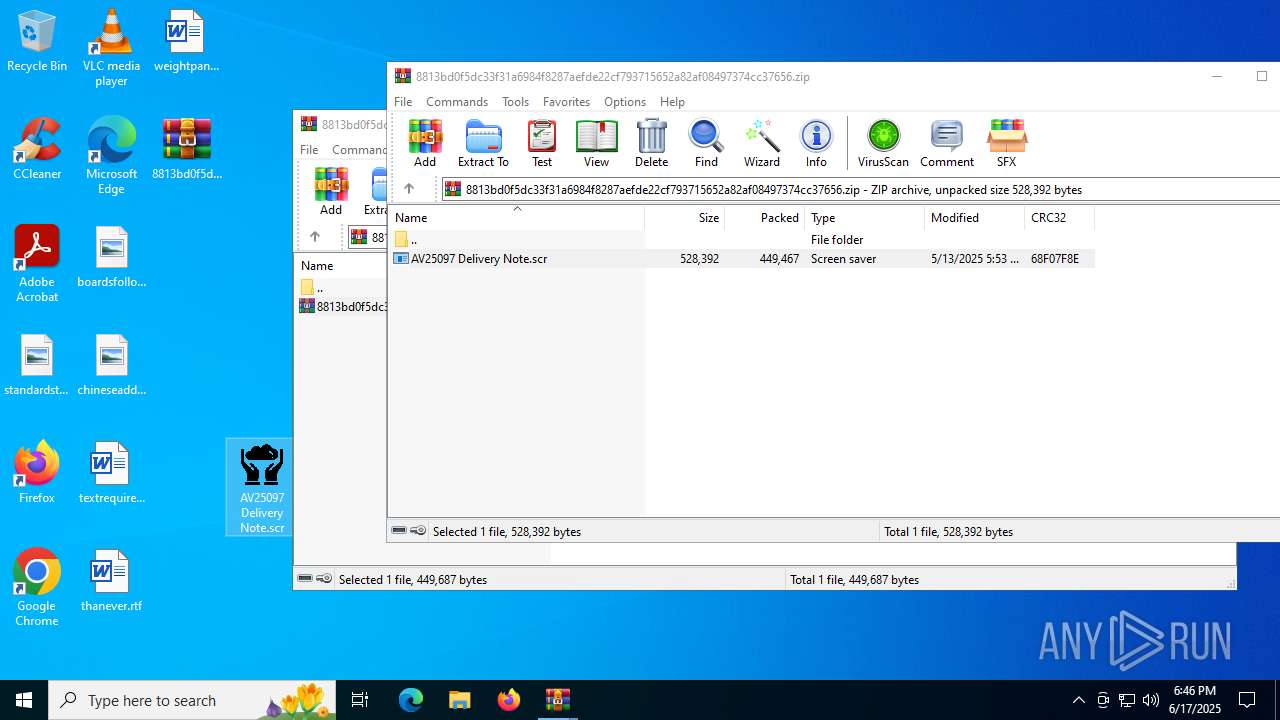
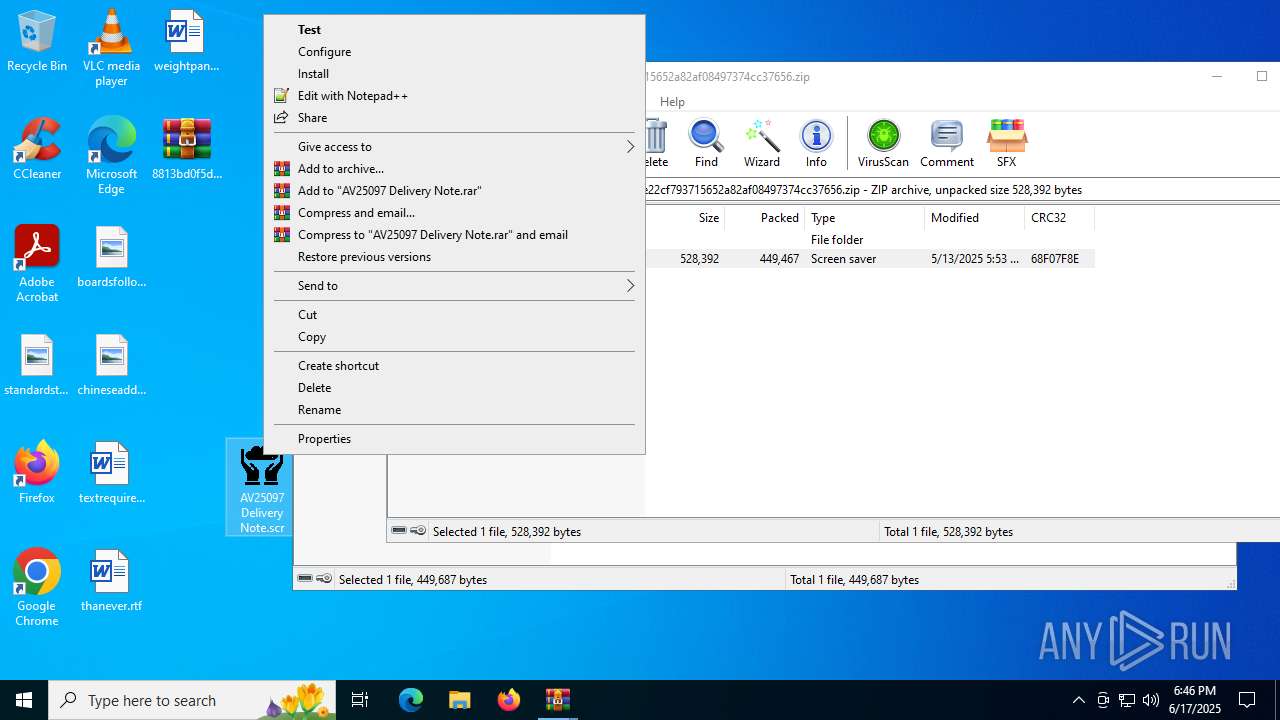
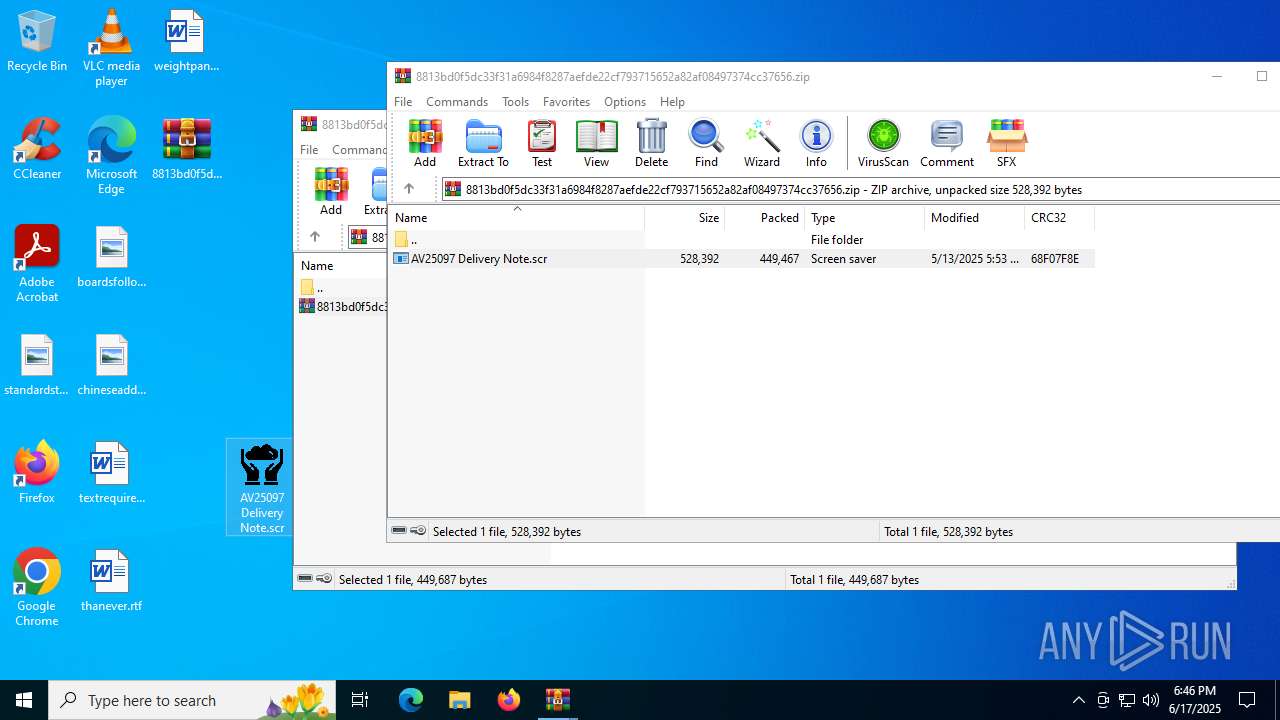
| File name: | 8813bd0f5dc33f31a6984f8287aefde22cf793715652a82af08497374cc37656.zip |
| Full analysis: | https://app.any.run/tasks/ac49412a-31f0-44b2-9dec-b70b87b17f1f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 17, 2025, 18:45:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
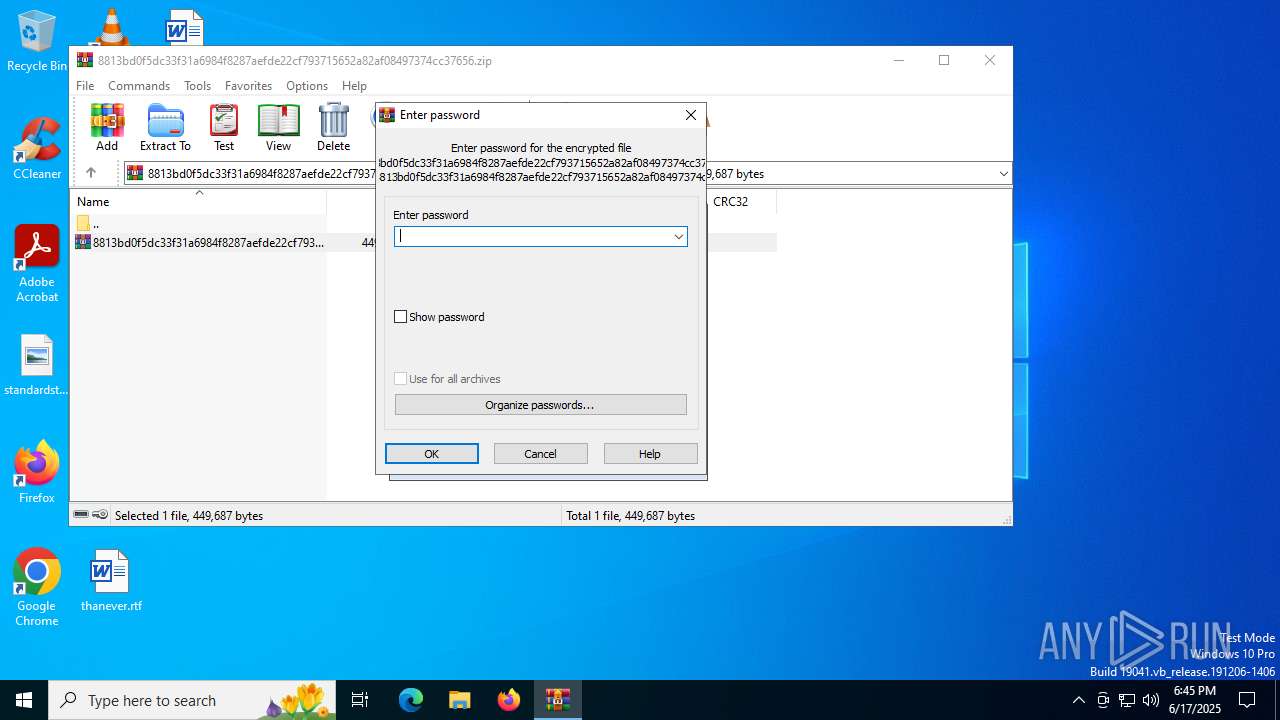
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 437E701EC10BA5C92945530BB063495B |
| SHA1: | C21344CD5A0578331F74031E2B417F45E689B034 |
| SHA256: | 8F4C095292D2F032BC7FB36EF508B4EE878015A1DC66E5081E10D53BCB9D1F9A |
| SSDEEP: | 24576:cfxxjdqavaHqKztmrMjhwtksYJoQLrMzKeivutX8VIPgNx8K:cfxBdqavaHqKztmrMjhwOsYJ5vsKeivX |
MALICIOUS
ASYNCRAT has been found (auto)
- WinRAR.exe (PID: 6344)
- WinRAR.exe (PID: 3752)
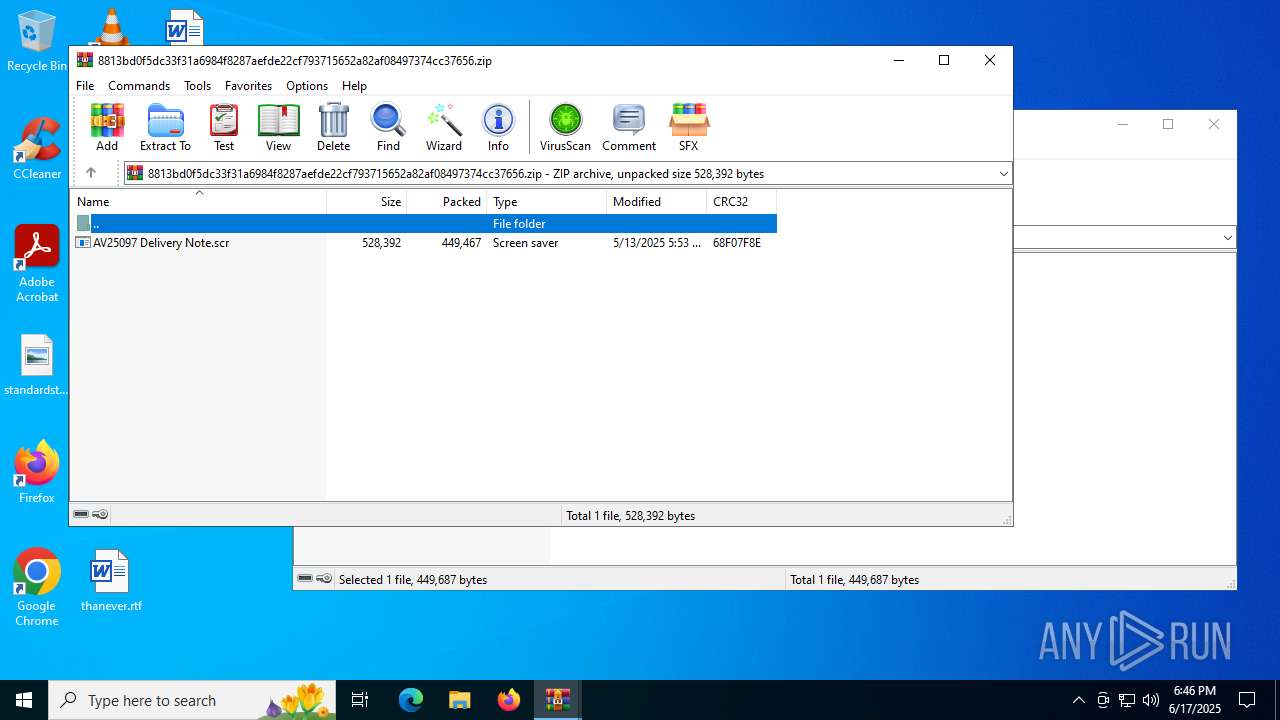
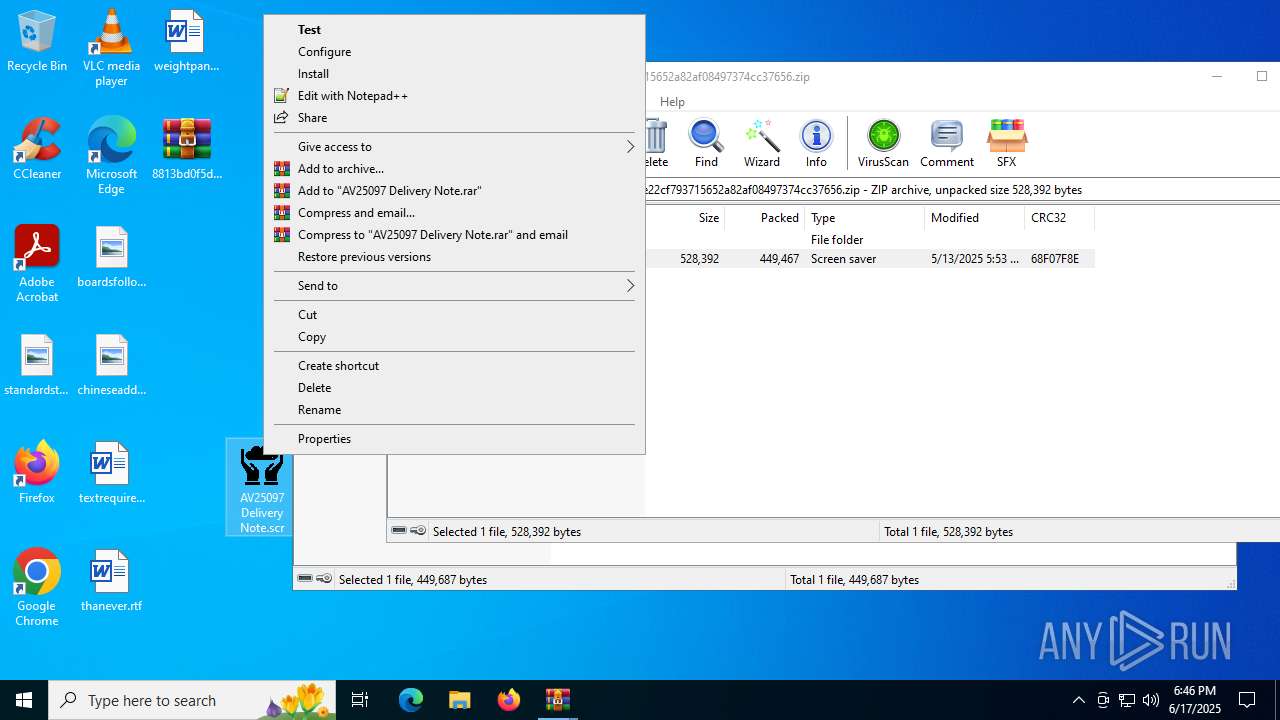
- AV25097 Delivery Note.scr (PID: 6492)
Generic archive extractor
- WinRAR.exe (PID: 3752)
Uses Task Scheduler to run other applications
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 4892)
- AV25097 Delivery Note.scr (PID: 6612)
- AV25097 Delivery Note.scr (PID: 728)
XWORM has been detected (YARA)
- RegSvcs.exe (PID: 3936)
Create files in the Startup directory
- RegSvcs.exe (PID: 3936)
SUSPICIOUS
Reads security settings of Internet Explorer
- AV25097 Delivery Note.scr (PID: 6492)
- WinRAR.exe (PID: 6344)
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 6612)
- AV25097 Delivery Note.scr (PID: 728)
- AV25097 Delivery Note.scr (PID: 4892)
Executable content was dropped or overwritten
- AV25097 Delivery Note.scr (PID: 6492)
- RegSvcs.exe (PID: 3936)
Connects to unusual port
- RegSvcs.exe (PID: 3936)
Starts application with an unusual extension
- WinRAR.exe (PID: 6344)
INFO
Manual execution by a user
- AV25097 Delivery Note.scr (PID: 6492)
- WinRAR.exe (PID: 6344)
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 6612)
- AV25097 Delivery Note.scr (PID: 3588)
- AV25097 Delivery Note.scr (PID: 4892)
Checks supported languages
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 4892)
- AV25097 Delivery Note.scr (PID: 6612)
- RegSvcs.exe (PID: 3936)
- AV25097 Delivery Note.scr (PID: 728)
- AV25097 Delivery Note.scr (PID: 3588)
- RegSvcs.exe (PID: 5012)
- RegSvcs.exe (PID: 6264)
- RegSvcs.exe (PID: 6700)
- RegSvcs.exe (PID: 4052)
- RegSvcs.exe (PID: 4888)
- RegSvcs.exe (PID: 5060)
Reads the machine GUID from the registry
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 4892)
- RegSvcs.exe (PID: 3936)
- AV25097 Delivery Note.scr (PID: 3588)
- AV25097 Delivery Note.scr (PID: 728)
- RegSvcs.exe (PID: 6264)
- RegSvcs.exe (PID: 5012)
- RegSvcs.exe (PID: 6700)
- RegSvcs.exe (PID: 4052)
- RegSvcs.exe (PID: 4888)
- RegSvcs.exe (PID: 5060)
- AV25097 Delivery Note.scr (PID: 6612)
Reads the computer name
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 4892)
- AV25097 Delivery Note.scr (PID: 6612)
- RegSvcs.exe (PID: 3936)
- AV25097 Delivery Note.scr (PID: 728)
- RegSvcs.exe (PID: 5012)
- RegSvcs.exe (PID: 6264)
- RegSvcs.exe (PID: 6700)
- RegSvcs.exe (PID: 4052)
- RegSvcs.exe (PID: 4888)
- RegSvcs.exe (PID: 5060)
- AV25097 Delivery Note.scr (PID: 3588)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6344)
.NET Reactor protector has been detected
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 1812)
Create files in a temporary directory
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 4892)
- AV25097 Delivery Note.scr (PID: 6612)
- AV25097 Delivery Note.scr (PID: 728)
Process checks computer location settings
- AV25097 Delivery Note.scr (PID: 6492)
- AV25097 Delivery Note.scr (PID: 1812)
- AV25097 Delivery Note.scr (PID: 4832)
- AV25097 Delivery Note.scr (PID: 4544)
- AV25097 Delivery Note.scr (PID: 4892)
- AV25097 Delivery Note.scr (PID: 6612)
- AV25097 Delivery Note.scr (PID: 728)
Creates files or folders in the user directory
- AV25097 Delivery Note.scr (PID: 6492)
- RegSvcs.exe (PID: 3936)
Launching a file from the Startup directory
- RegSvcs.exe (PID: 3936)
Checks proxy server information
- slui.exe (PID: 2216)
Reads the software policy settings
- slui.exe (PID: 2216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(3936) RegSvcs.exe
C2196.251.87.81:7040
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
Mutexvc0DI1nBHFOhuBXk
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:06:17 18:44:24 |
| ZipCRC: | 0x5a645fbb |
| ZipCompressedSize: | 449701 |
| ZipUncompressedSize: | 449687 |
| ZipFileName: | 8813bd0f5dc33f31a6984f8287aefde22cf793715652a82af08497374cc37656.zip |
Total processes
170
Monitored processes
35
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa6344.31281\AV25097 Delivery Note.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa6344.31281\AV25097 Delivery Note.scr | — | WinRAR.exe | |||||||||||
User: admin Company: Crescendo Visualworks Integrity Level: MEDIUM Description: Allegro Graph • Symphony Edition Exit code: 0 Version: 4.2.1845.62 Modules
| |||||||||||||||
| 1028 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | AV25097 Delivery Note.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1232 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\cRXmQXIhUkHn" /XML "C:\Users\admin\AppData\Local\Temp\tmp9D25.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | AV25097 Delivery Note.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\cRXmQXIhUkHn" /XML "C:\Users\admin\AppData\Local\Temp\tmpD8D7.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | AV25097 Delivery Note.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\Desktop\AV25097 Delivery Note.scr" /S | C:\Users\admin\Desktop\AV25097 Delivery Note.scr | — | explorer.exe | |||||||||||
User: admin Company: Crescendo Visualworks Integrity Level: MEDIUM Description: Allegro Graph • Symphony Edition Exit code: 0 Version: 4.2.1845.62 Modules
| |||||||||||||||
| 1944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | AV25097 Delivery Note.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2216 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2664 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | AV25097 Delivery Note.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
8 382
Read events
8 349
Write events
20
Delete events
13
Modification events
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\8813bd0f5dc33f31a6984f8287aefde22cf793715652a82af08497374cc37656.zip | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
4
Suspicious files
1
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6344.28464\AV25097 Delivery Note.scr | executable | |
MD5:54A08AFB7D4946DFDD48D907BD2AF047 | SHA256:CA081D2E9E512E1516EDC180262C4309DDA83AD714A281ABD26FC1A658BCED01 | |||
| 6344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6344.31281\AV25097 Delivery Note.scr | executable | |
MD5:54A08AFB7D4946DFDD48D907BD2AF047 | SHA256:CA081D2E9E512E1516EDC180262C4309DDA83AD714A281ABD26FC1A658BCED01 | |||
| 1812 | AV25097 Delivery Note.scr | C:\Users\admin\AppData\Local\Temp\tmpAE4C.tmp | xml | |
MD5:268472AEA210321442C3A2878FCF1F7A | SHA256:6CD87E6B81810988638D6B97A43DB1735391B756B1C9859D9B7501EEA5F9EFA8 | |||
| 6492 | AV25097 Delivery Note.scr | C:\Users\admin\AppData\Local\Temp\tmp9D25.tmp | xml | |
MD5:268472AEA210321442C3A2878FCF1F7A | SHA256:6CD87E6B81810988638D6B97A43DB1735391B756B1C9859D9B7501EEA5F9EFA8 | |||
| 4832 | AV25097 Delivery Note.scr | C:\Users\admin\AppData\Local\Temp\tmpB8FA.tmp | xml | |
MD5:268472AEA210321442C3A2878FCF1F7A | SHA256:6CD87E6B81810988638D6B97A43DB1735391B756B1C9859D9B7501EEA5F9EFA8 | |||
| 4892 | AV25097 Delivery Note.scr | C:\Users\admin\AppData\Local\Temp\tmpDA7C.tmp | xml | |
MD5:268472AEA210321442C3A2878FCF1F7A | SHA256:6CD87E6B81810988638D6B97A43DB1735391B756B1C9859D9B7501EEA5F9EFA8 | |||
| 6492 | AV25097 Delivery Note.scr | C:\Users\admin\AppData\Roaming\cRXmQXIhUkHn.exe | executable | |
MD5:54A08AFB7D4946DFDD48D907BD2AF047 | SHA256:CA081D2E9E512E1516EDC180262C4309DDA83AD714A281ABD26FC1A658BCED01 | |||
| 3936 | RegSvcs.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\XClean.lnk | lnk | |
MD5:ED96231E2BC6D97E6EF97CC30208BC59 | SHA256:7901057598C1A87D047ADEF9C61248334B08C63FDFF3A366324A341342FC92A2 | |||
| 3936 | RegSvcs.exe | C:\Users\admin\AppData\Roaming\XClean.exe | executable | |
MD5:6279D136310C22894F605938B4CB93D8 | SHA256:FB7D514B3322810463655473D2D7C704D3405C1C9DD81F0D4D423518EF416987 | |||
| 3752 | WinRAR.exe | C:\Users\admin\Desktop\8813bd0f5dc33f31a6984f8287aefde22cf793715652a82af08497374cc37656.zip | compressed | |
MD5:A0623D758A0D22681AED299D7C9A3B92 | SHA256:8813BD0F5DC33F31A6984F8287AEFDE22CF793715652A82AF08497374CC37656 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
34
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1200 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1636 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1636 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4544 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1200 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1200 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |