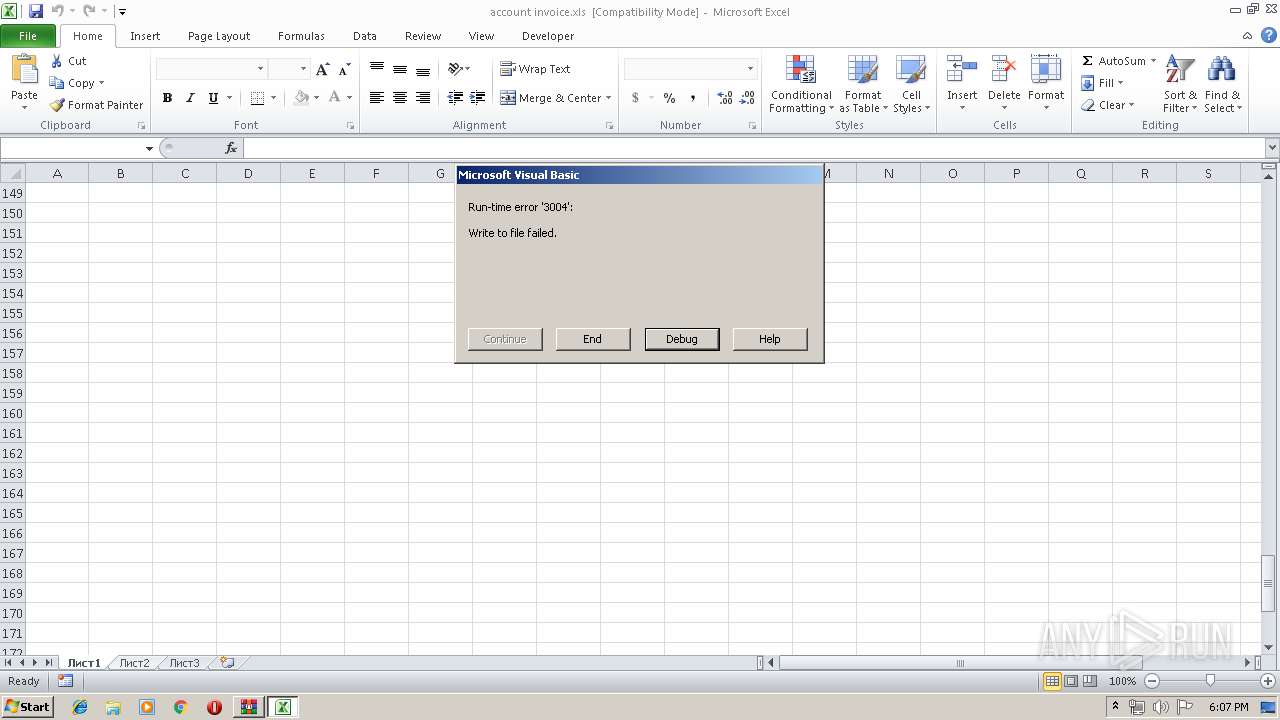
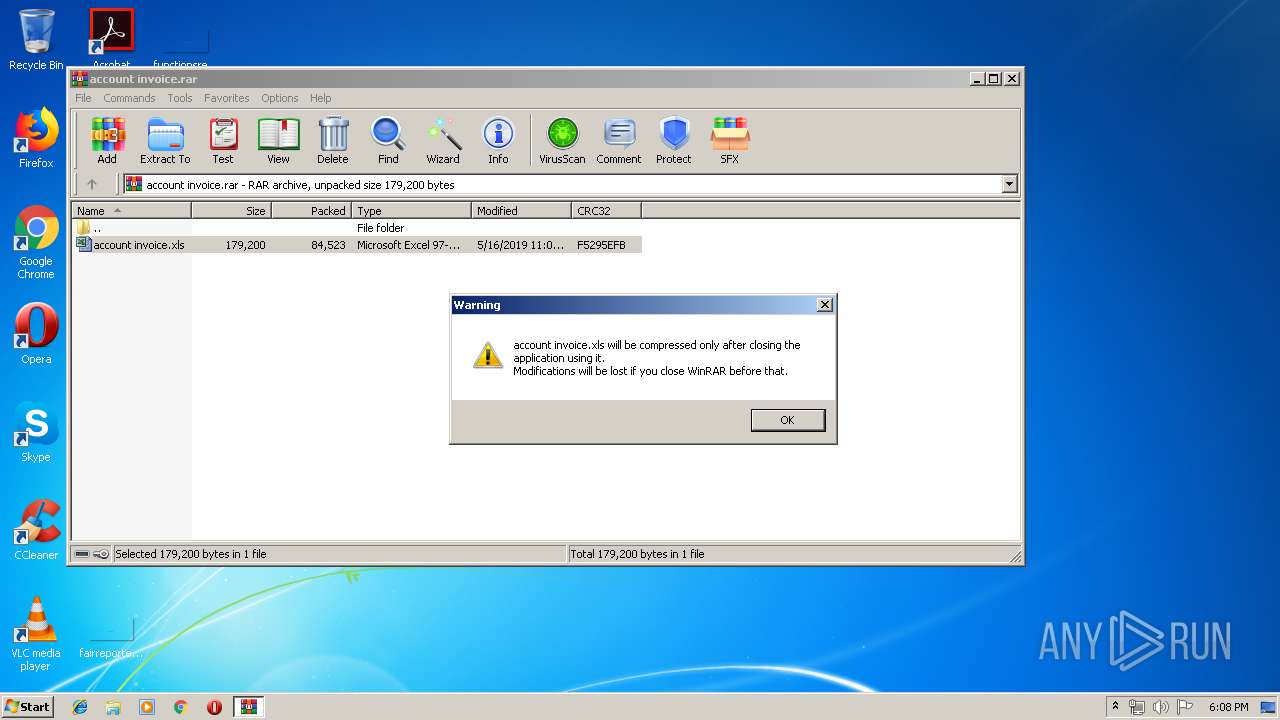
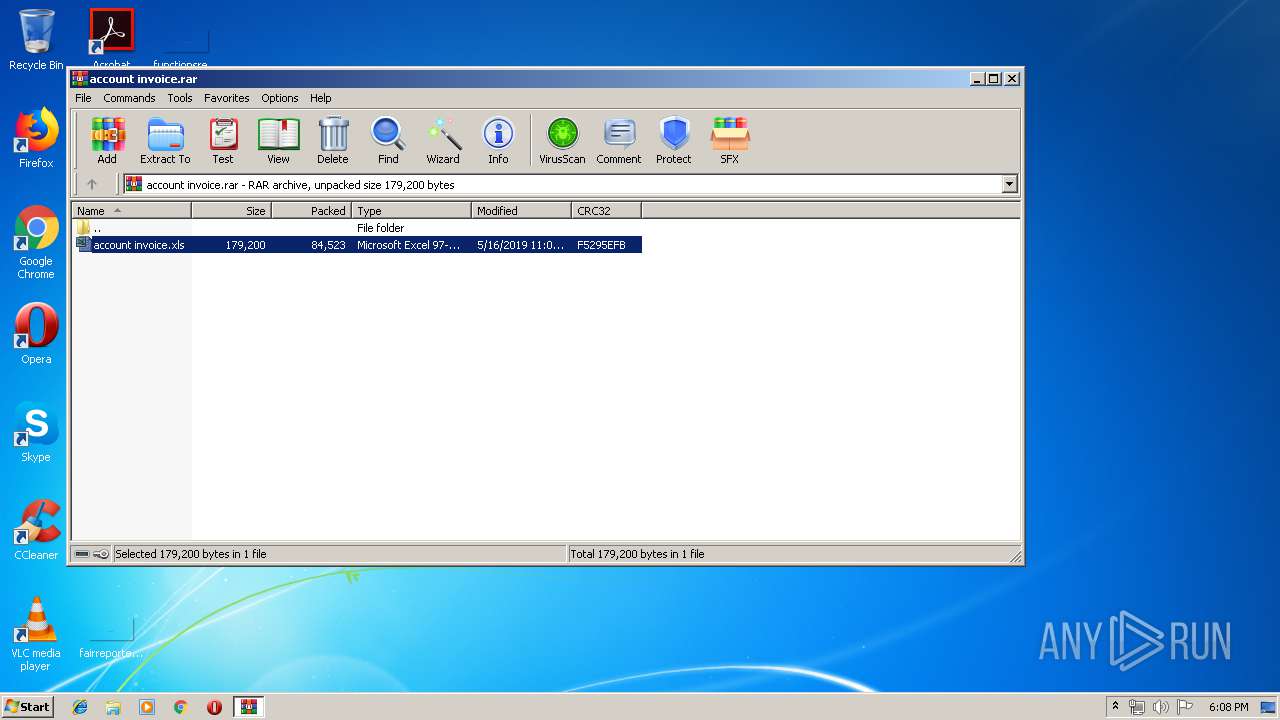
| File name: | account invoice.rar |
| Full analysis: | https://app.any.run/tasks/56940b1a-465f-47ce-bca2-da2ca7535384 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | May 20, 2019, 17:06:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CED62B57543D866F8C0989B5B51EDE94 |
| SHA1: | 764811D2C8C0CBA9C882409E5784D0140F15871F |
| SHA256: | 8F3F174C2441AFFD659BCE81D1B94B0D97D57EB0FACE1C21AF9269BEF336F35B |
| SSDEEP: | 1536:Syp8lWCtc8ySl8YIJHVmuCnbHDQGxXYqiWUWeLECwXmxl5TY622:S9tcLSldIJH9Cn/9QWUWuHYKEz2 |
MALICIOUS
Application was dropped or rewritten from another process
- rtegre.exe (PID: 392)
- wprgxyeqd79.exe (PID: 2520)
- uninstall.exe (PID: 2596)
- exit.exe (PID: 116)
- veter1605_MAPS_10cr0.exe (PID: 1584)
- exit.exe (PID: 1692)
- winserv.exe (PID: 2564)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3556)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 3556)
Changes the autorun value in the registry
- reg.exe (PID: 1720)
Loads dropped or rewritten executable
- taskkill.exe (PID: 3344)
- svchost.exe (PID: 2464)
- PING.EXE (PID: 2652)
- taskkill.exe (PID: 2908)
- conhost.exe (PID: 3260)
- taskkill.exe (PID: 344)
- EXCEL.EXE (PID: 3556)
- cmd.exe (PID: 3468)
- wprgxyeqd79.exe (PID: 2520)
- exit.exe (PID: 116)
- uninstall.exe (PID: 2596)
- cmd.exe (PID: 3480)
- taskkill.exe (PID: 1708)
- PING.EXE (PID: 1020)
- rtegre.exe (PID: 392)
- exit.exe (PID: 1692)
- taskkill.exe (PID: 3692)
- taskkill.exe (PID: 3508)
- taskkill.exe (PID: 4056)
- taskkill.exe (PID: 2128)
- taskkill.exe (PID: 1256)
- taskkill.exe (PID: 1556)
- taskkill.exe (PID: 3224)
- taskkill.exe (PID: 1492)
- taskkill.exe (PID: 808)
- taskkill.exe (PID: 2788)
- taskkill.exe (PID: 2948)
- taskkill.exe (PID: 3292)
- veter1605_MAPS_10cr0.exe (PID: 1584)
- WinRAR.exe (PID: 252)
- taskkill.exe (PID: 2924)
- taskkill.exe (PID: 3872)
- wmiprvse.exe (PID: 1472)
- winserv.exe (PID: 2564)
- taskkill.exe (PID: 3844)
- taskkill.exe (PID: 2436)
- taskkill.exe (PID: 3604)
- taskkill.exe (PID: 3724)
- taskkill.exe (PID: 1660)
- taskkill.exe (PID: 1356)
- taskkill.exe (PID: 3548)
- taskkill.exe (PID: 1648)
- taskkill.exe (PID: 3400)
- taskkill.exe (PID: 2176)
- taskkill.exe (PID: 288)
- taskkill.exe (PID: 3092)
- taskkill.exe (PID: 3880)
- taskkill.exe (PID: 2584)
- taskkill.exe (PID: 4024)
- taskkill.exe (PID: 3320)
- taskkill.exe (PID: 856)
- taskkill.exe (PID: 1216)
- taskkill.exe (PID: 4024)
- taskkill.exe (PID: 2588)
- taskkill.exe (PID: 1572)
- OSPPSVC.EXE (PID: 2316)
- conhost.exe (PID: 3132)
- taskkill.exe (PID: 2140)
- taskkill.exe (PID: 3264)
- taskkill.exe (PID: 4048)
- taskkill.exe (PID: 2864)
- taskkill.exe (PID: 1344)
- taskkill.exe (PID: 3532)
- taskkill.exe (PID: 3344)
- taskkill.exe (PID: 1708)
- taskkill.exe (PID: 3936)
- taskkill.exe (PID: 3696)
- taskkill.exe (PID: 1008)
- taskkill.exe (PID: 3252)
- reg.exe (PID: 1720)
- taskkill.exe (PID: 3624)
- taskkill.exe (PID: 3372)
- taskkill.exe (PID: 2644)
- taskkill.exe (PID: 2616)
- taskkill.exe (PID: 4064)
- taskkill.exe (PID: 2068)
- taskkill.exe (PID: 2744)
- taskkill.exe (PID: 3408)
- taskkill.exe (PID: 3048)
- taskkill.exe (PID: 4040)
- taskkill.exe (PID: 3976)
- taskkill.exe (PID: 2508)
- taskkill.exe (PID: 1704)
- taskkill.exe (PID: 2896)
- taskkill.exe (PID: 2872)
- taskkill.exe (PID: 1212)
- taskkill.exe (PID: 3136)
- taskkill.exe (PID: 3284)
- taskkill.exe (PID: 3372)
- taskkill.exe (PID: 1344)
- taskkill.exe (PID: 3016)
- taskkill.exe (PID: 3704)
- taskkill.exe (PID: 2720)
- taskkill.exe (PID: 1652)
- taskkill.exe (PID: 3616)
- taskkill.exe (PID: 3044)
- taskkill.exe (PID: 808)
- taskkill.exe (PID: 2872)
- taskkill.exe (PID: 3796)
- taskkill.exe (PID: 2816)
- taskkill.exe (PID: 3196)
- taskkill.exe (PID: 4064)
- taskkill.exe (PID: 3124)
- taskkill.exe (PID: 2220)
- taskkill.exe (PID: 2188)
- taskkill.exe (PID: 1748)
- taskkill.exe (PID: 3972)
- taskkill.exe (PID: 2488)
- taskkill.exe (PID: 2412)
- taskkill.exe (PID: 712)
- taskkill.exe (PID: 2904)
- taskkill.exe (PID: 1332)
- taskkill.exe (PID: 3960)
- taskkill.exe (PID: 4008)
- taskkill.exe (PID: 2900)
- taskkill.exe (PID: 3416)
- taskkill.exe (PID: 2896)
- taskkill.exe (PID: 3836)
- taskkill.exe (PID: 1476)
- taskkill.exe (PID: 3796)
- taskkill.exe (PID: 2952)
- taskkill.exe (PID: 856)
- taskkill.exe (PID: 3156)
- taskkill.exe (PID: 3048)
- taskkill.exe (PID: 2732)
- taskkill.exe (PID: 2380)
- taskkill.exe (PID: 3348)
- taskkill.exe (PID: 756)
- taskkill.exe (PID: 3656)
- taskkill.exe (PID: 2924)
- taskkill.exe (PID: 1300)
- taskkill.exe (PID: 2456)
- taskkill.exe (PID: 2300)
- taskkill.exe (PID: 3944)
- taskkill.exe (PID: 3164)
- taskkill.exe (PID: 2472)
- taskkill.exe (PID: 3568)
- taskkill.exe (PID: 3232)
- taskkill.exe (PID: 2832)
- taskkill.exe (PID: 2480)
- taskkill.exe (PID: 536)
- taskkill.exe (PID: 3984)
- taskkill.exe (PID: 2992)
- taskkill.exe (PID: 3836)
- taskkill.exe (PID: 2892)
- taskkill.exe (PID: 3824)
- taskkill.exe (PID: 2556)
- taskkill.exe (PID: 2292)
- taskkill.exe (PID: 116)
- taskkill.exe (PID: 2508)
- taskkill.exe (PID: 3520)
- taskkill.exe (PID: 3568)
- taskkill.exe (PID: 836)
- taskkill.exe (PID: 2156)
- taskkill.exe (PID: 3416)
- taskkill.exe (PID: 3848)
- taskkill.exe (PID: 2324)
- taskkill.exe (PID: 3012)
- taskkill.exe (PID: 2228)
- taskkill.exe (PID: 3080)
- taskkill.exe (PID: 3560)
- taskkill.exe (PID: 680)
- taskkill.exe (PID: 3388)
- taskkill.exe (PID: 1692)
- taskkill.exe (PID: 3968)
- taskkill.exe (PID: 3700)
- taskkill.exe (PID: 3944)
- taskkill.exe (PID: 2964)
- taskkill.exe (PID: 2740)
- taskkill.exe (PID: 2860)
- taskkill.exe (PID: 2148)
- taskkill.exe (PID: 2536)
- taskkill.exe (PID: 2628)
- taskkill.exe (PID: 3692)
- taskkill.exe (PID: 3296)
- taskkill.exe (PID: 3936)
- taskkill.exe (PID: 1528)
- taskkill.exe (PID: 2556)
- taskkill.exe (PID: 2776)
- taskkill.exe (PID: 1372)
- taskkill.exe (PID: 2744)
- taskkill.exe (PID: 3804)
- taskkill.exe (PID: 2128)
- taskkill.exe (PID: 3848)
- taskkill.exe (PID: 756)
- taskkill.exe (PID: 2196)
- taskkill.exe (PID: 2900)
- taskkill.exe (PID: 2480)
- taskkill.exe (PID: 2356)
- taskkill.exe (PID: 3120)
- taskkill.exe (PID: 2412)
- taskkill.exe (PID: 3312)
- taskkill.exe (PID: 3284)
- taskkill.exe (PID: 3388)
- taskkill.exe (PID: 3980)
- taskkill.exe (PID: 1660)
- taskkill.exe (PID: 4008)
- taskkill.exe (PID: 3928)
- taskkill.exe (PID: 2624)
- taskkill.exe (PID: 488)
- taskkill.exe (PID: 3592)
- taskkill.exe (PID: 724)
- taskkill.exe (PID: 2660)
- taskkill.exe (PID: 3992)
- taskkill.exe (PID: 2144)
- taskkill.exe (PID: 388)
- taskkill.exe (PID: 2596)
- taskkill.exe (PID: 2124)
- taskkill.exe (PID: 3972)
- taskkill.exe (PID: 2660)
- taskkill.exe (PID: 3732)
- taskkill.exe (PID: 3384)
- taskkill.exe (PID: 3980)
- taskkill.exe (PID: 3960)
- taskkill.exe (PID: 2068)
- taskkill.exe (PID: 1864)
- taskkill.exe (PID: 3608)
- taskkill.exe (PID: 2952)
- taskkill.exe (PID: 3504)
- taskkill.exe (PID: 3656)
- taskkill.exe (PID: 3708)
- taskkill.exe (PID: 2580)
- taskkill.exe (PID: 3272)
- taskkill.exe (PID: 3272)
- taskkill.exe (PID: 1520)
- taskkill.exe (PID: 1080)
- taskkill.exe (PID: 2088)
- taskkill.exe (PID: 2868)
- taskkill.exe (PID: 3348)
- taskkill.exe (PID: 3580)
- taskkill.exe (PID: 1864)
- taskkill.exe (PID: 2616)
- taskkill.exe (PID: 124)
- taskkill.exe (PID: 288)
- taskkill.exe (PID: 1528)
- taskkill.exe (PID: 636)
- taskkill.exe (PID: 2792)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 2808)
- taskkill.exe (PID: 1844)
- taskkill.exe (PID: 3628)
- taskkill.exe (PID: 3112)
- taskkill.exe (PID: 3300)
- taskkill.exe (PID: 3984)
- taskkill.exe (PID: 2788)
- taskkill.exe (PID: 1140)
- taskkill.exe (PID: 776)
- taskkill.exe (PID: 3892)
- taskkill.exe (PID: 2300)
- taskkill.exe (PID: 772)
- taskkill.exe (PID: 2608)
- taskkill.exe (PID: 1636)
- taskkill.exe (PID: 3492)
- taskkill.exe (PID: 2168)
- taskkill.exe (PID: 3636)
- taskkill.exe (PID: 3172)
- taskkill.exe (PID: 776)
- taskkill.exe (PID: 2776)
- taskkill.exe (PID: 2052)
- taskkill.exe (PID: 3540)
- taskkill.exe (PID: 1720)
- taskkill.exe (PID: 2668)
- taskkill.exe (PID: 1000)
- taskkill.exe (PID: 712)
- taskkill.exe (PID: 2908)
- taskkill.exe (PID: 2204)
- taskkill.exe (PID: 2084)
- taskkill.exe (PID: 3292)
- taskkill.exe (PID: 3500)
- taskkill.exe (PID: 2648)
- taskkill.exe (PID: 2796)
- taskkill.exe (PID: 2380)
- taskkill.exe (PID: 664)
- taskkill.exe (PID: 4048)
- taskkill.exe (PID: 3192)
- taskkill.exe (PID: 3732)
- taskkill.exe (PID: 3264)
- taskkill.exe (PID: 3940)
- taskkill.exe (PID: 4032)
- taskkill.exe (PID: 2948)
- taskkill.exe (PID: 3188)
- taskkill.exe (PID: 3528)
- taskkill.exe (PID: 460)
- taskkill.exe (PID: 2440)
- taskkill.exe (PID: 3484)
- taskkill.exe (PID: 3684)
- taskkill.exe (PID: 3956)
- taskkill.exe (PID: 2968)
- taskkill.exe (PID: 388)
- taskkill.exe (PID: 2208)
- taskkill.exe (PID: 1524)
- taskkill.exe (PID: 2176)
- taskkill.exe (PID: 636)
- taskkill.exe (PID: 1104)
- taskkill.exe (PID: 3708)
- taskkill.exe (PID: 2528)
- taskkill.exe (PID: 2456)
- taskkill.exe (PID: 1920)
- taskkill.exe (PID: 124)
- taskkill.exe (PID: 2752)
- taskkill.exe (PID: 2656)
- taskkill.exe (PID: 3012)
- taskkill.exe (PID: 3084)
- taskkill.exe (PID: 2460)
- taskkill.exe (PID: 3820)
- taskkill.exe (PID: 2216)
- taskkill.exe (PID: 3904)
- taskkill.exe (PID: 3080)
- taskkill.exe (PID: 2388)
- taskkill.exe (PID: 3016)
- taskkill.exe (PID: 4088)
- taskkill.exe (PID: 3196)
- taskkill.exe (PID: 2668)
- taskkill.exe (PID: 2588)
- taskkill.exe (PID: 1896)
- taskkill.exe (PID: 3200)
- taskkill.exe (PID: 3436)
- taskkill.exe (PID: 3952)
- taskkill.exe (PID: 2576)
- taskkill.exe (PID: 2308)
- taskkill.exe (PID: 3124)
- taskkill.exe (PID: 3112)
- taskkill.exe (PID: 3156)
- taskkill.exe (PID: 408)
- taskkill.exe (PID: 2220)
- taskkill.exe (PID: 3816)
- taskkill.exe (PID: 2432)
- taskkill.exe (PID: 1928)
- taskkill.exe (PID: 1904)
- taskkill.exe (PID: 3640)
- taskkill.exe (PID: 2304)
- taskkill.exe (PID: 3844)
- taskkill.exe (PID: 3712)
- taskkill.exe (PID: 1748)
- taskkill.exe (PID: 2760)
- taskkill.exe (PID: 3224)
- taskkill.exe (PID: 3200)
RMS RAT was detected
- winserv.exe (PID: 2564)
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 2316)
Stealing of credential data
- rtegre.exe (PID: 392)
SUSPICIOUS
Starts CMD.EXE for commands execution
- exit.exe (PID: 116)
- exit.exe (PID: 1692)
Executable content was dropped or overwritten
- wprgxyeqd79.exe (PID: 2520)
- cmd.exe (PID: 3468)
- uninstall.exe (PID: 2596)
- veter1605_MAPS_10cr0.exe (PID: 1584)
Starts Microsoft Office Application
- WinRAR.exe (PID: 252)
Creates files in the program directory
- uninstall.exe (PID: 2596)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3480)
Reads Environment values
- winserv.exe (PID: 2564)
Reads Windows Product ID
- winserv.exe (PID: 2564)
Reads the machine GUID from the registry
- winserv.exe (PID: 2564)
Creates files in the user directory
- winserv.exe (PID: 2564)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3480)
Loads DLL from Mozilla Firefox
- rtegre.exe (PID: 392)
INFO
Dropped object may contain Bitcoin addresses
- wprgxyeqd79.exe (PID: 2520)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3556)
Creates files in the user directory
- EXCEL.EXE (PID: 3556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
373
Monitored processes
342
Malicious processes
10
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\exit.exe" | C:\Users\admin\AppData\Local\Temp\exit.exe | — | wprgxyeqd79.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 116 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 124 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 124 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 252 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\account invoice.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 288 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 288 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 344 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 595
Read events
2 499
Write events
84
Delete events
12
Modification events
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\account invoice.rar | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (252) WinRAR.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | EXCELFiles |
Value: 1320419345 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | (15 |
Value: 28313500E40D0000010000000000000000000000 | |||
Executable files
11
Suspicious files
3
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR5518.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF1CEC949AFA27AC04.TMP | — | |
MD5:— | SHA256:— | |||
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF8A53A664ACC73C97.TMP | — | |
MD5:— | SHA256:— | |||
| 392 | rtegre.exe | C:\Users\admin\AppData\Local\Temp\{C2839792-91D4-4CCD-8102-3D8D2DEABED4}\839612059.dll | — | |
MD5:— | SHA256:— | |||
| 392 | rtegre.exe | C:\Users\admin\AppData\Local\Temp\{C2839792-91D4-4CCD-8102-3D8D2DEABED4}\log | — | |
MD5:— | SHA256:— | |||
| 252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa252.2994\account invoice.xls | document | |
MD5:— | SHA256:— | |||
| 2520 | wprgxyeqd79.exe | C:\Users\admin\AppData\Local\Temp\exit.exe | executable | |
MD5:— | SHA256:— | |||
| 2520 | wprgxyeqd79.exe | C:\Users\admin\AppData\Local\Temp\i.cmd | text | |
MD5:— | SHA256:— | |||
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\pasmmm[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3556 | EXCEL.EXE | C:\Users\Public\wprgxyeqd79.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
27
DNS requests
6
Threats
52
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | rtegre.exe | GET | — | 154.35.175.225:80 | http://154.35.175.225/tor/status-vote/current/consensus | US | — | — | malicious |
392 | rtegre.exe | GET | — | 199.249.230.119:80 | http://199.249.230.119/tor/server/fp/4352d58b2641e8c1787750efd3a07a88224967ac | US | — | — | suspicious |
392 | rtegre.exe | GET | — | 50.7.176.2:80 | http://50.7.176.2/tor/server/fp/3a8836b2549c55bd62b2137d14b743eea4ec0444 | NL | — | — | suspicious |
392 | rtegre.exe | GET | — | 174.138.18.84:80 | http://174.138.18.84/tor/server/fp/53680d4d82bc0d5cb8cc9547c2a027120b7a06d1 | SG | — | — | suspicious |
392 | rtegre.exe | GET | — | 37.220.36.240:80 | http://37.220.36.240/tor/server/fp/592031cfdba17dd46e1e365e6c60ad1f81655033 | NL | — | — | suspicious |
392 | rtegre.exe | GET | — | 178.17.171.114:80 | http://178.17.171.114/tor/server/fp/592031cfdba17dd46e1e365e6c60ad1f81655033 | MD | — | — | suspicious |
392 | rtegre.exe | GET | — | 185.73.220.8:80 | http://185.73.220.8/tor/server/fp/bc7acfac04854c77167c7d66b7e471314ed8c410 | NL | — | — | suspicious |
392 | rtegre.exe | GET | — | 81.174.231.18:80 | http://81.174.231.18/tor/server/fp/30ce61c1356c7cf996680f05ec9201dde898cfc6 | GB | — | — | suspicious |
392 | rtegre.exe | GET | — | 193.11.166.194:80 | http://193.11.166.194/tor/server/fp/f4c836a27bf192f3364a67166e8ee2b19693aed1 | SE | — | — | suspicious |
392 | rtegre.exe | GET | — | 66.175.223.104:80 | http://66.175.223.104/tor/server/fp/50f1d32b208a2d97f124882137c0a3bdb74edd09 | US | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
392 | rtegre.exe | 37.120.174.249:80 | — | netcup GmbH | DE | suspicious |
— | — | 217.12.201.159:5655 | — | ITL Company | NL | suspicious |
3556 | EXCEL.EXE | 47.245.58.124:443 | kentona.su | — | US | suspicious |
392 | rtegre.exe | 50.7.176.2:80 | — | Cogent Communications | NL | suspicious |
392 | rtegre.exe | 154.35.175.225:80 | — | Rethem Hosting LLC | US | malicious |
392 | rtegre.exe | 54.243.147.226:443 | api.ipify.org | Amazon.com, Inc. | US | malicious |
392 | rtegre.exe | 84.119.129.86:443 | — | Liberty Global Operations B.V. | DE | suspicious |
392 | rtegre.exe | 129.6.15.28:13 | time-a.nist.gov | National Bureau of Standards | US | unknown |
392 | rtegre.exe | 132.163.96.6:13 | time.nist.gov | National Bureau of Standards | US | unknown |
392 | rtegre.exe | 174.138.18.84:80 | — | Digital Ocean, Inc. | SG | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kentona.su |
| malicious |
www.cloudflare.com |
| whitelisted |
api.ipify.org |
| shared |
time-a.nist.gov |
| whitelisted |
time-a-g.nist.gov |
| unknown |
time.nist.gov |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1068 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
392 | rtegre.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 161 |
392 | rtegre.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
392 | rtegre.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
392 | rtegre.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 495 |
392 | rtegre.exe | Potential Corporate Privacy Violation | ET P2P Tor Get Server Request |
392 | rtegre.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 630 |
392 | rtegre.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 48 |
392 | rtegre.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 48 |
392 | rtegre.exe | Potential Corporate Privacy Violation | ET P2P Tor Get Server Request |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
winserv.exe | Error WTSQueryUserToken #1314 |
winserv.exe | 20-05-2019_18:07:26:426#T:Error #20 @2 |
winserv.exe | 20-05-2019_18:07:55:363#T:Msg Size: 104 |
winserv.exe | 20-05-2019_18:07:55:363#T:Msg code: 3 |
winserv.exe | 20-05-2019_18:07:55:363#T:MSG_KEEP_ALIVE |
winserv.exe | MSG_KEEP_ALIVE |
winserv.exe | 20-05-2019_18:08:25:769#T:Msg Size: 104 |
winserv.exe | 20-05-2019_18:08:25:769#T:Msg code: 3 |
winserv.exe | 20-05-2019_18:08:25:769#T:MSG_KEEP_ALIVE |
winserv.exe | MSG_KEEP_ALIVE |