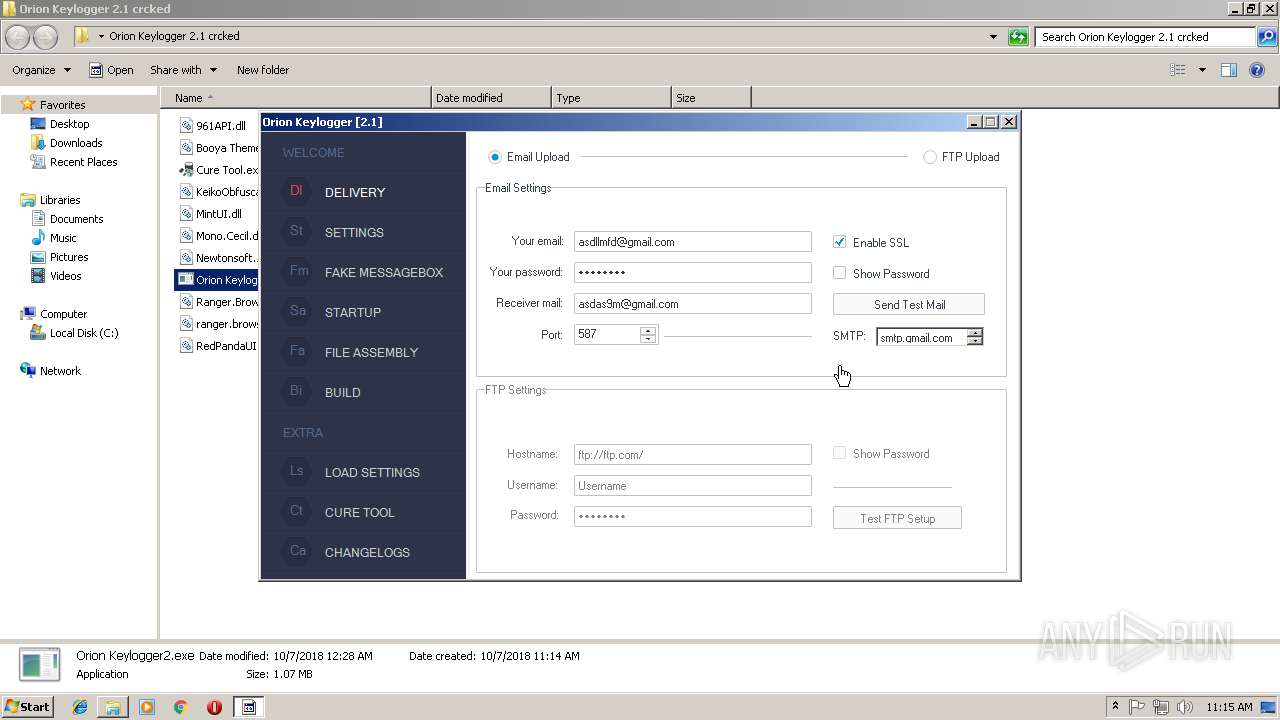
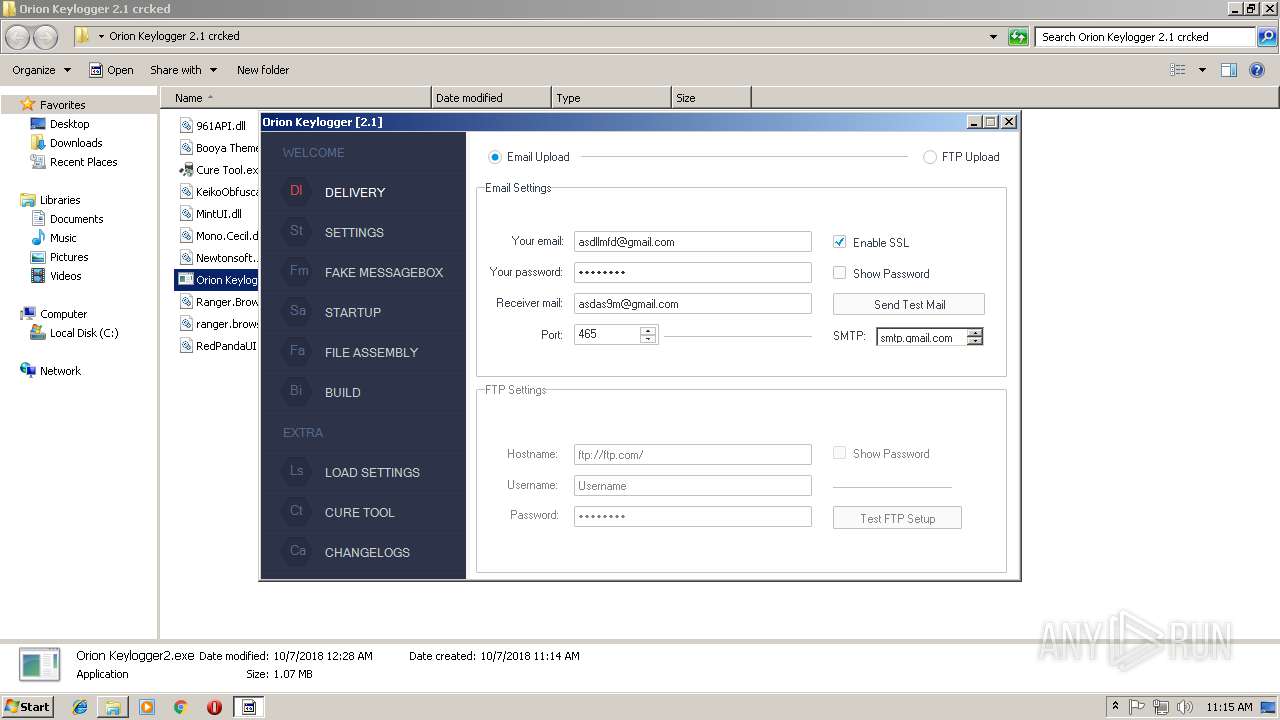
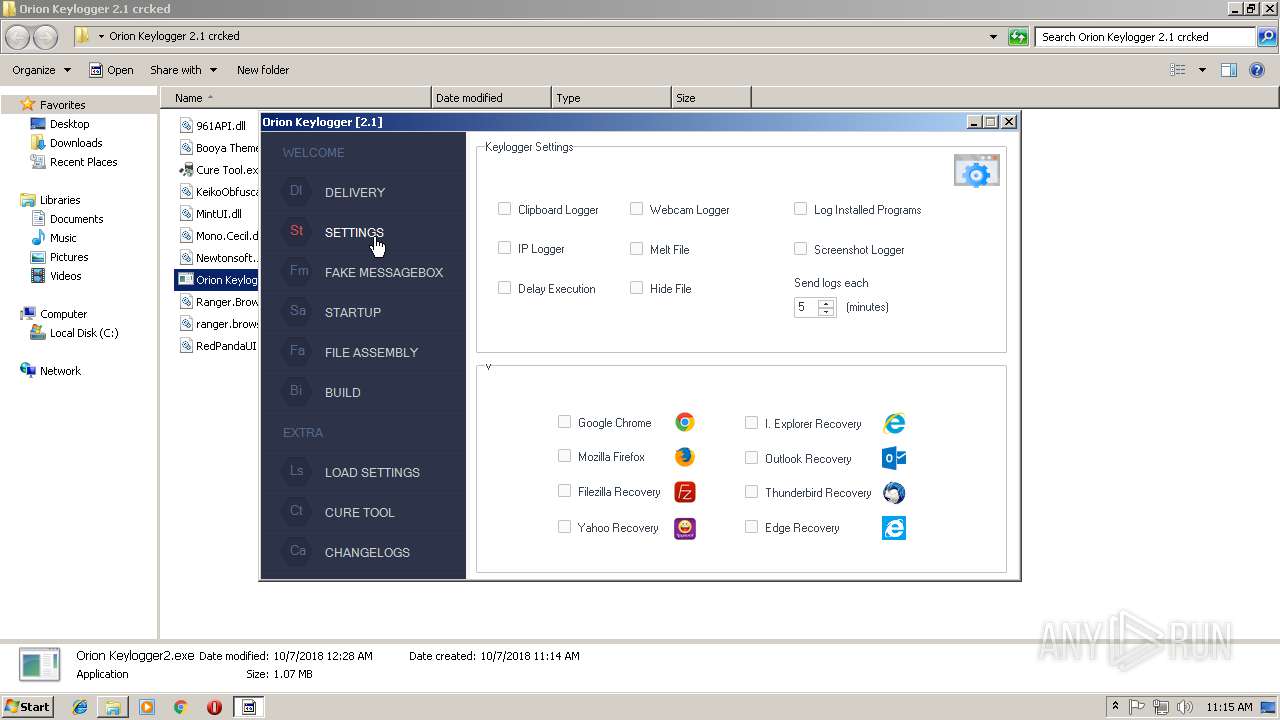
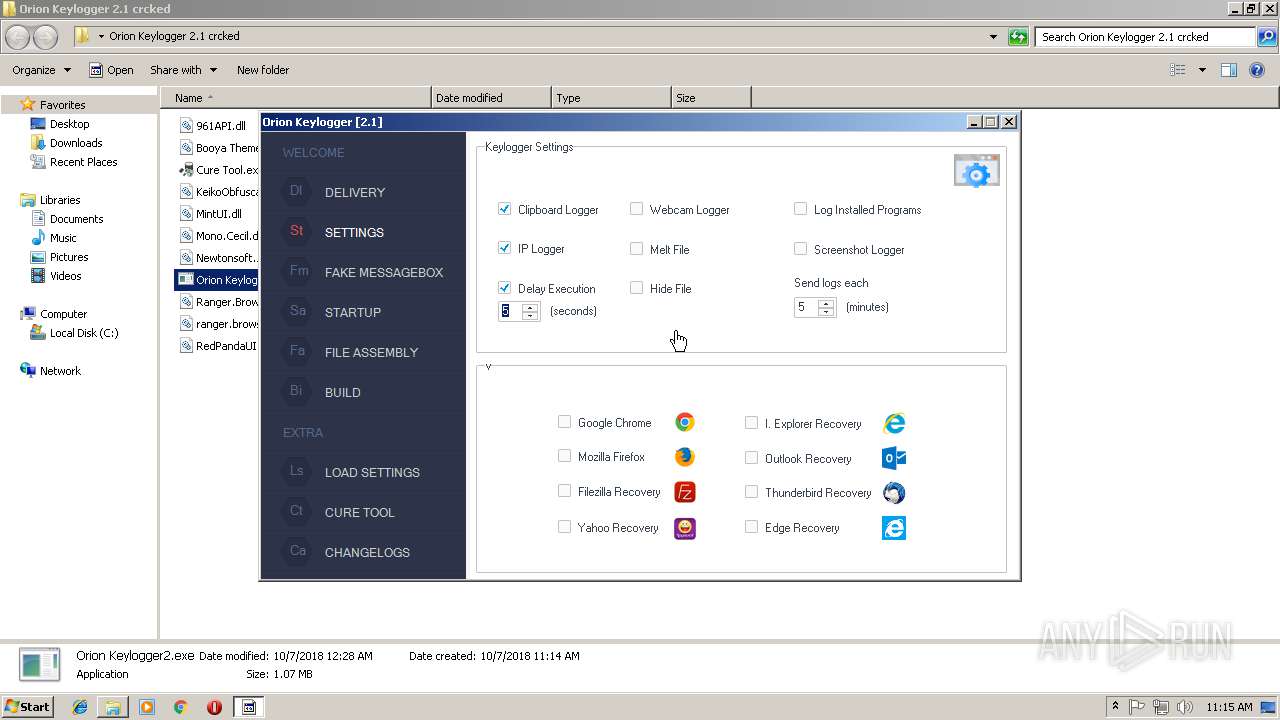
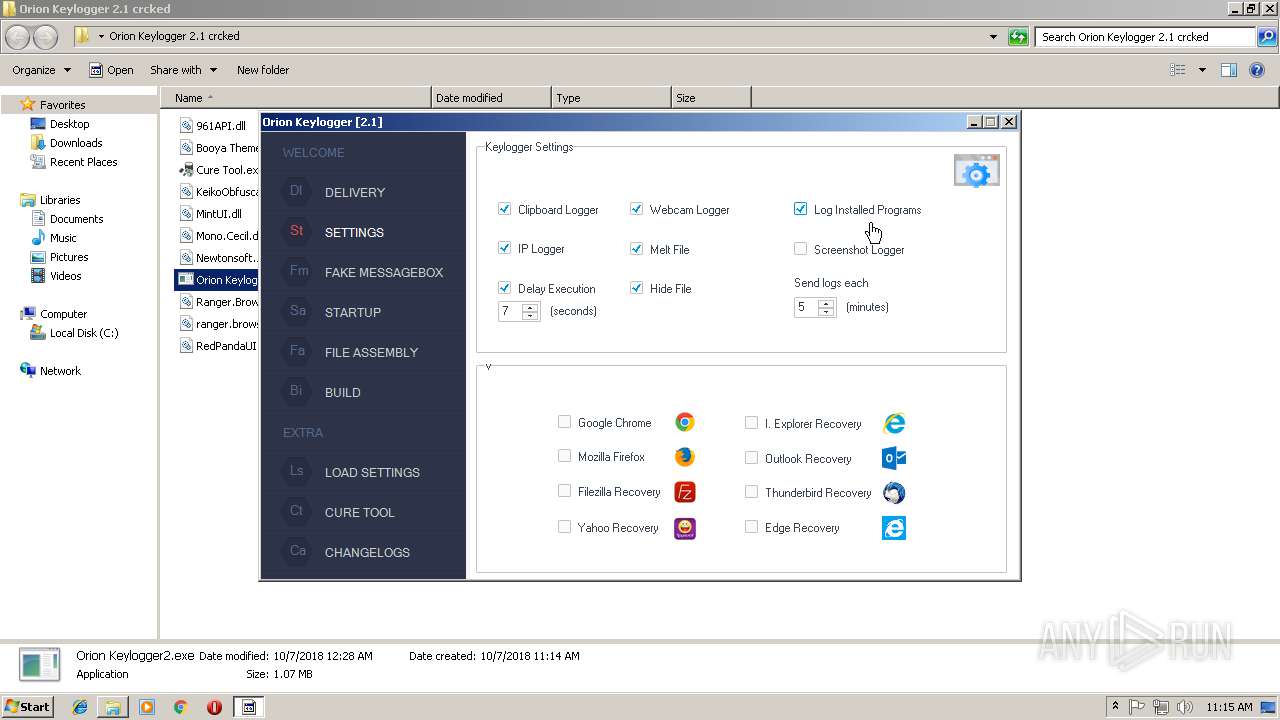
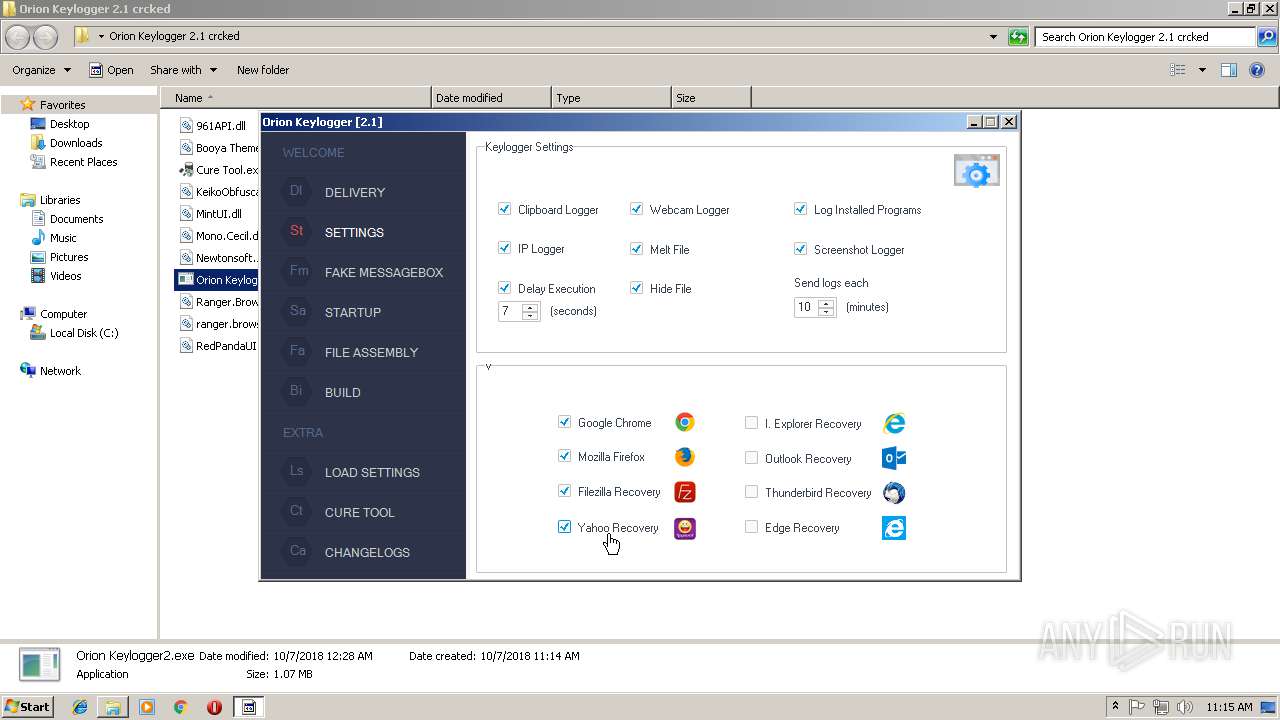
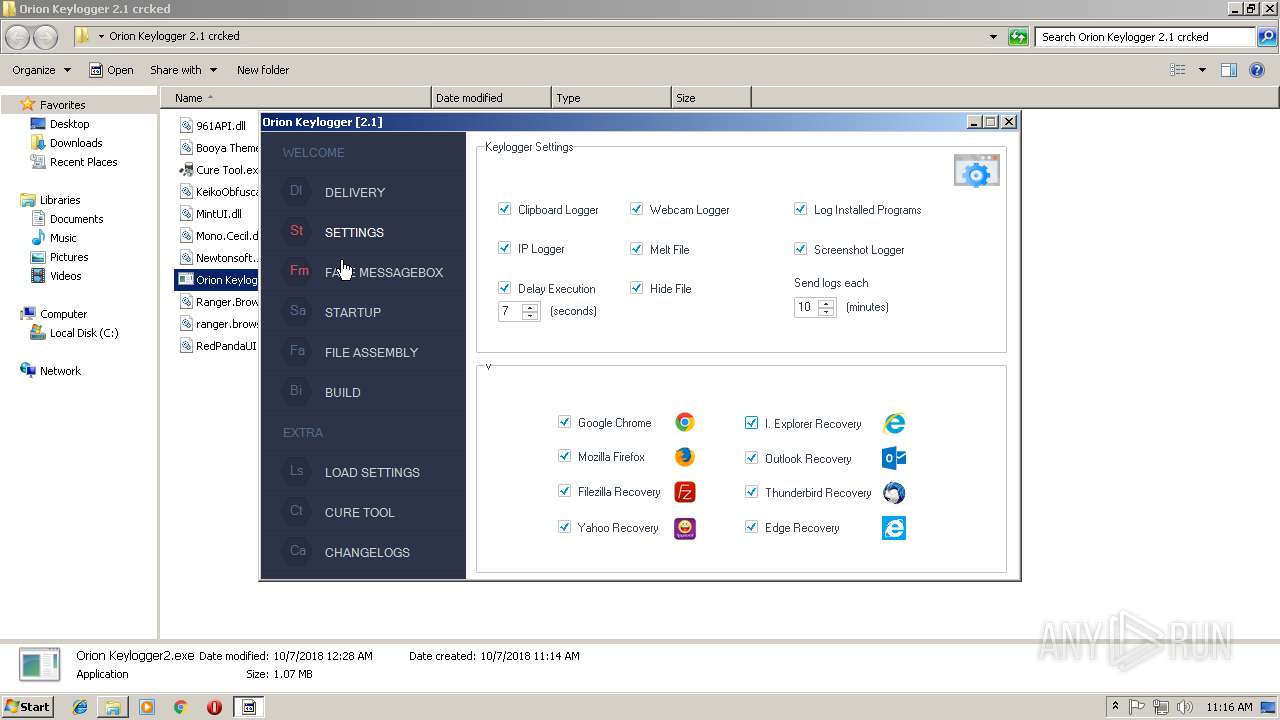
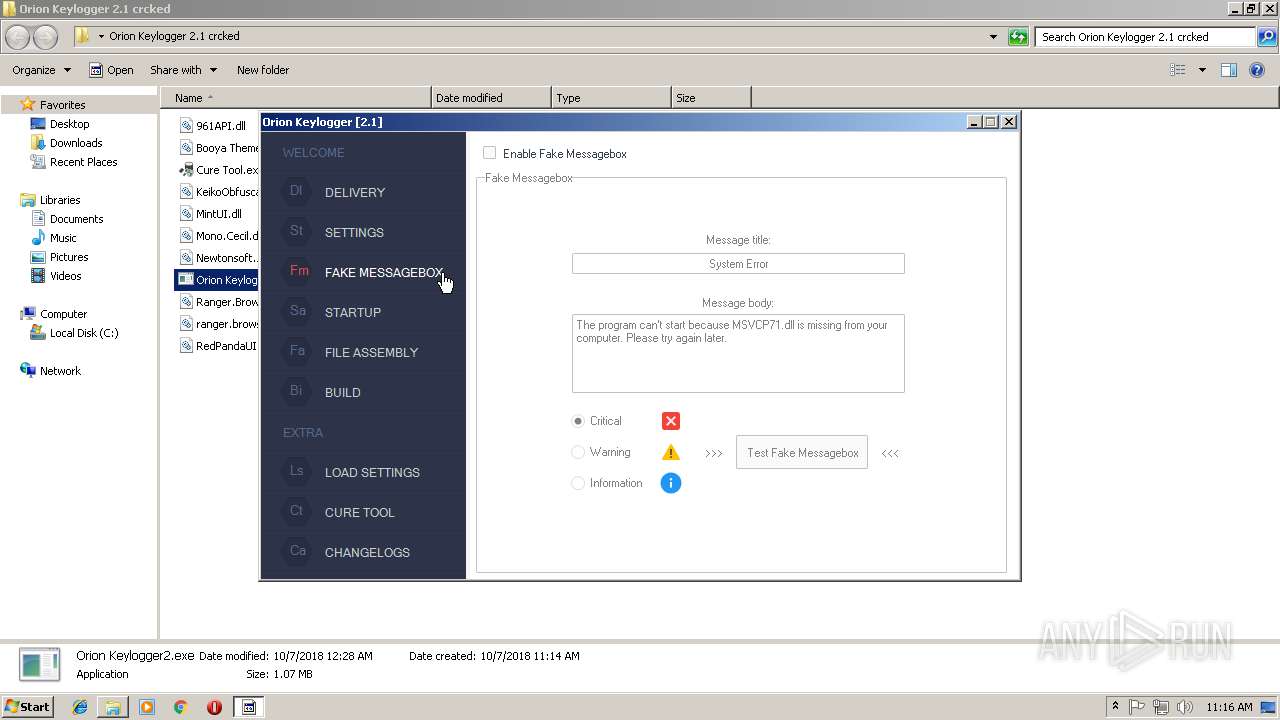
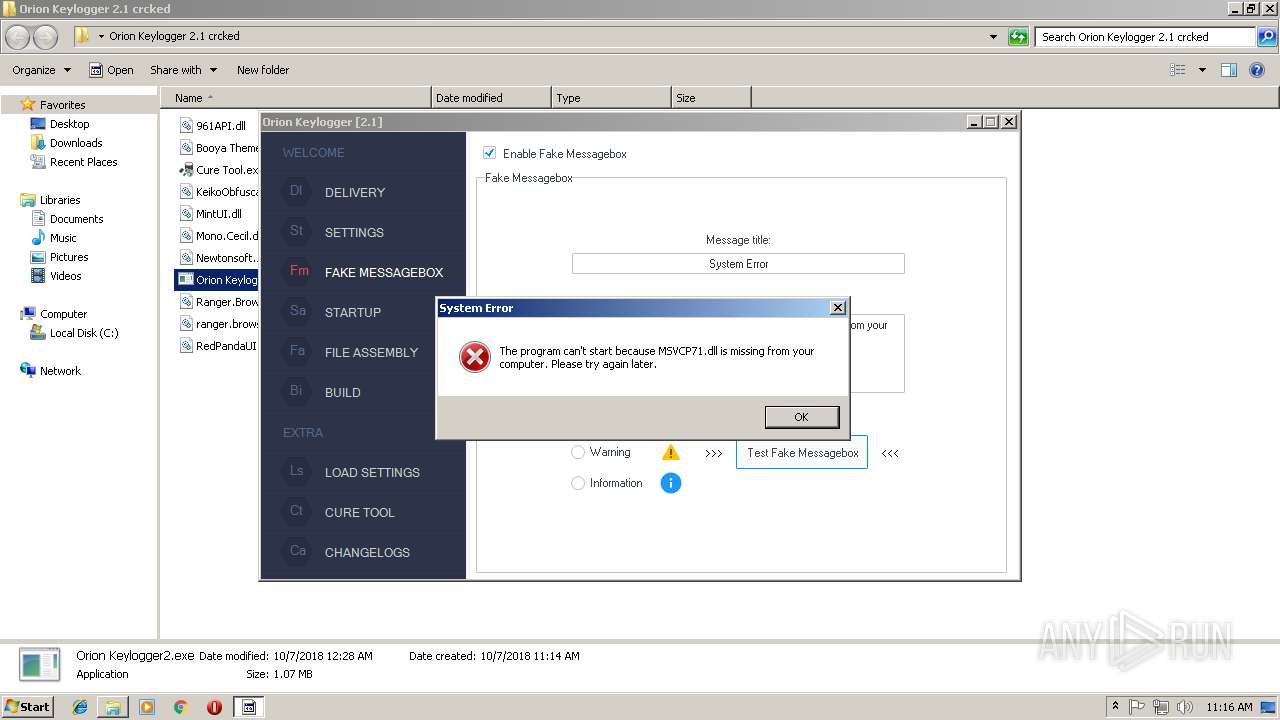
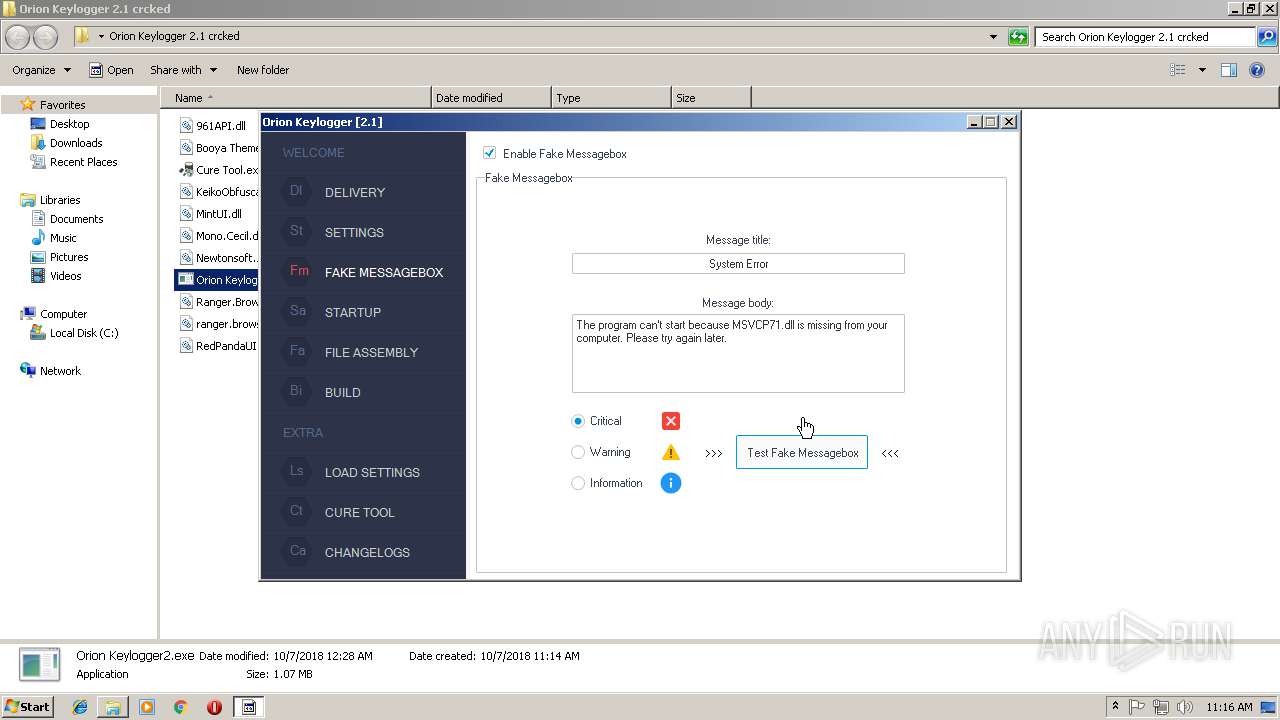
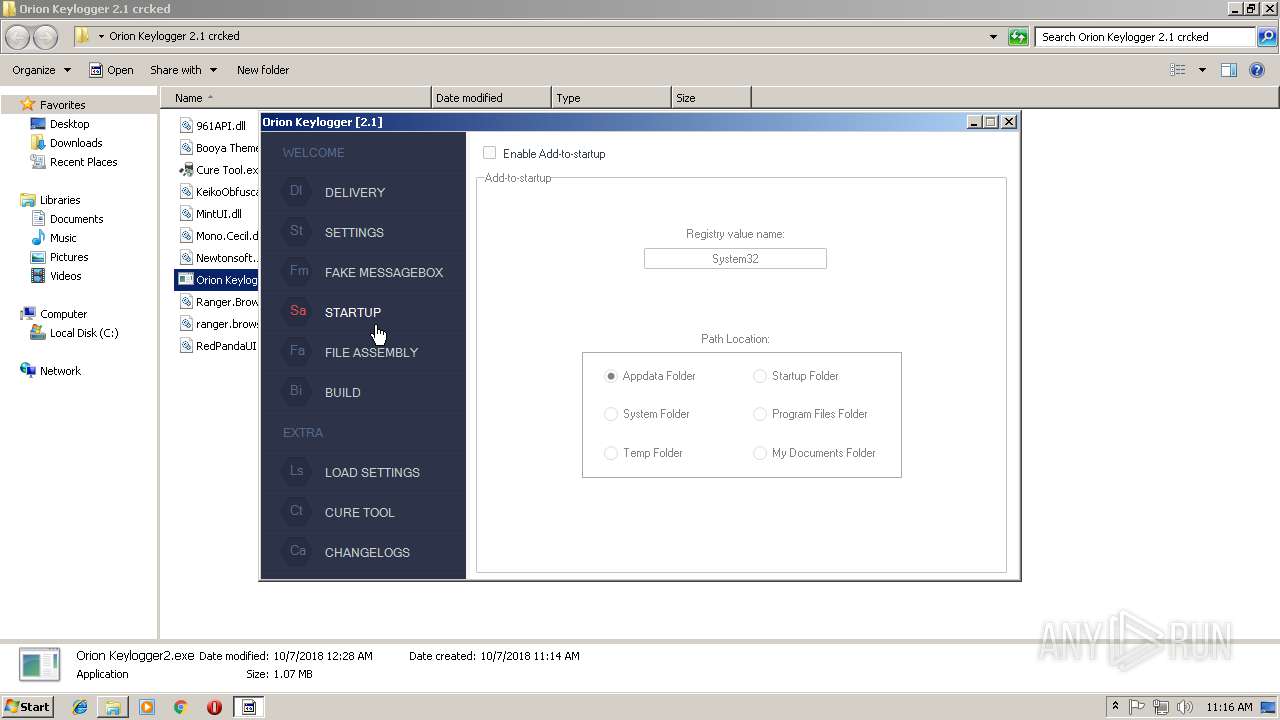
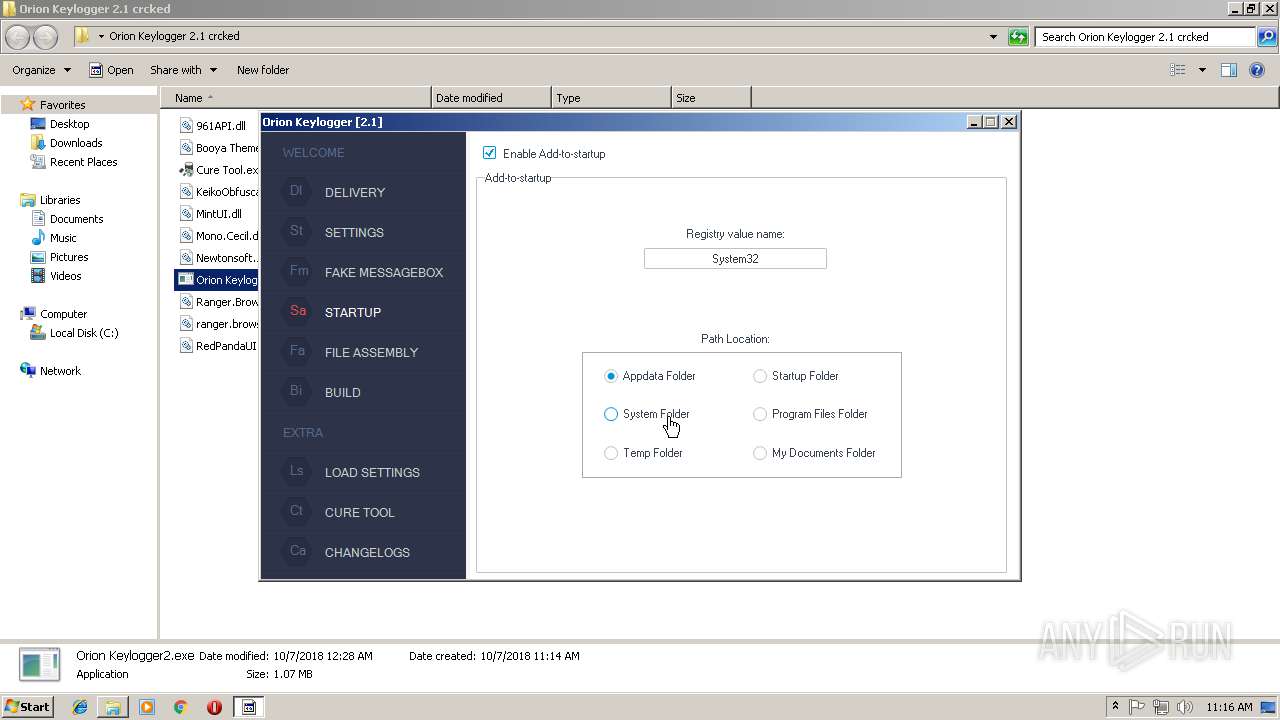
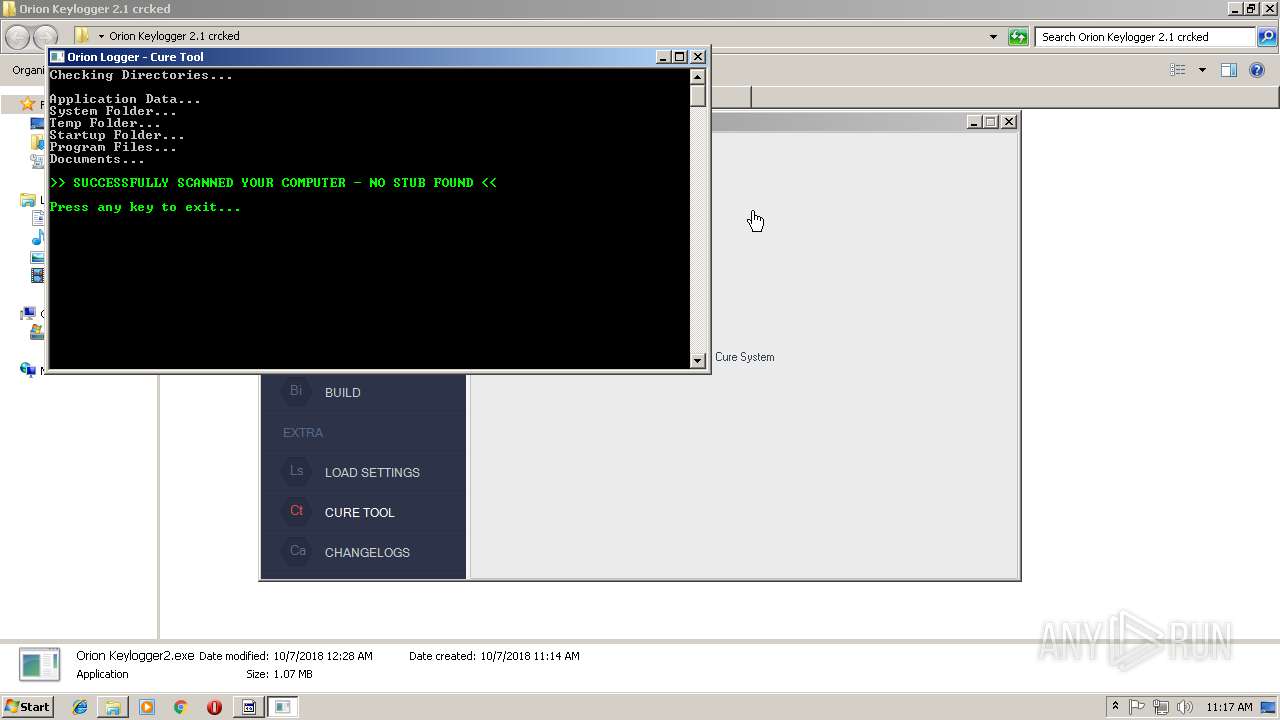
| download: | Orion%20Keylogger%202.1%20crcked.zip |
| Full analysis: | https://app.any.run/tasks/52576bab-9fc5-4cdf-8189-fabbfea48138 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | October 07, 2018, 10:14:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A91CF1BF6927737E7F4D5CE1C50C4A55 |
| SHA1: | E67239F97DBCF6763588C9E5669228D3C081240F |
| SHA256: | 8F25770ADFB0401FC602C1E21067F3B5756A40B68B582F9E495708B8366CCA03 |
| SSDEEP: | 24576:hYWqwIHX84J7vh3afq04GJaPiaoariRlSzPifWVeiWRPtVyY4XJFuGcLoVHxn7AT:PZIHzva+GG//ri3STifKvAPt85dR7sIC |
MALICIOUS
Connects to CnC server
- Orion Keylogger2.exe (PID: 1260)
- twvrsvc.exe (PID: 2052)
- Regasm.exe (PID: 3720)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3740)
- HQUHlwGxWA.exe (PID: 3372)
- bfsvc.exe (PID: 2116)
- HQUHlwGxWA.exe (PID: 2020)
Application was dropped or rewritten from another process
- Cure Tool.exe (PID: 1300)
- tvsxwrc.exe (PID: 544)
- 1115.exe (PID: 1684)
- twvrsvc.exe (PID: 2052)
- HQUHlwGxWA.exe (PID: 3372)
- 1115.exe (PID: 364)
- bfsvc.exe (PID: 2116)
- HQUHlwGxWA.exe (PID: 2020)
- bfsvc.exe (PID: 2656)
Uses Task Scheduler to run other applications
- tvsxwrc.exe (PID: 544)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 716)
NJRAT was detected
- twvrsvc.exe (PID: 2052)
Looks like application has launched a miner
- twvrsvc.exe (PID: 2052)
MINER was detected
- Regasm.exe (PID: 3720)
Actions looks like stealing of personal data
- twvrsvc.exe (PID: 2052)
Changes the autorun value in the registry
- 1115.exe (PID: 364)
SUSPICIOUS
Executable content was dropped or overwritten
- Cure Tool.exe (PID: 3720)
- Orion Keylogger2.exe (PID: 1260)
- tvsxwrc.exe (PID: 544)
- 1115.exe (PID: 1684)
- bfsvc.exe (PID: 2116)
- 1115.exe (PID: 364)
Creates files in the user directory
- Orion Keylogger2.exe (PID: 1260)
- tvsxwrc.exe (PID: 544)
Starts itself from another location
- tvsxwrc.exe (PID: 544)
- 1115.exe (PID: 1684)
Connects to unusual port
- twvrsvc.exe (PID: 2052)
- Regasm.exe (PID: 3720)
Starts CMD.EXE for commands execution
- 1115.exe (PID: 1684)
- 1115.exe (PID: 364)
Searches for installed software
- 1115.exe (PID: 1684)
- 1115.exe (PID: 364)
Checks for external IP
- 1115.exe (PID: 1684)
- 1115.exe (PID: 364)
INFO
Reads settings of System Certificates
- twvrsvc.exe (PID: 2052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:10:06 22:29:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Orion Keylogger 2.1 crcked/ |
Total processes
65
Monitored processes
21
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Users\admin\Documents\1115.exe" C:\Users\admin\Desktop\Orion Keylogger 2.1 crcked\1115.exe | C:\Users\admin\Documents\1115.exe | 1115.exe | ||||||||||||
User: admin Company: Microsoft @ 2015 Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 544 | "C:\Users\admin\AppData\Local\Temp\tvsxwrc.exe" | C:\Users\admin\AppData\Local\Temp\tvsxwrc.exe | Cure Tool.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 716 | schtasks /create /f /sc ONLOGON /RL HIGHEST /tn LimeRAT-Admin /tr "'C:\Users\admin\AppData\Roaming\TeamViewer\twvrsvc.exe'" | C:\Windows\system32\schtasks.exe | — | tvsxwrc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1140 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES13EC.tmp" "c:\Users\admin\Desktop\Orion Keylogger 2.1 crcked\CSC3A1C521C28F4BBBBAA5D5581A56AF2.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52512.0 built by: VSWINSERVICING Modules
| |||||||||||||||
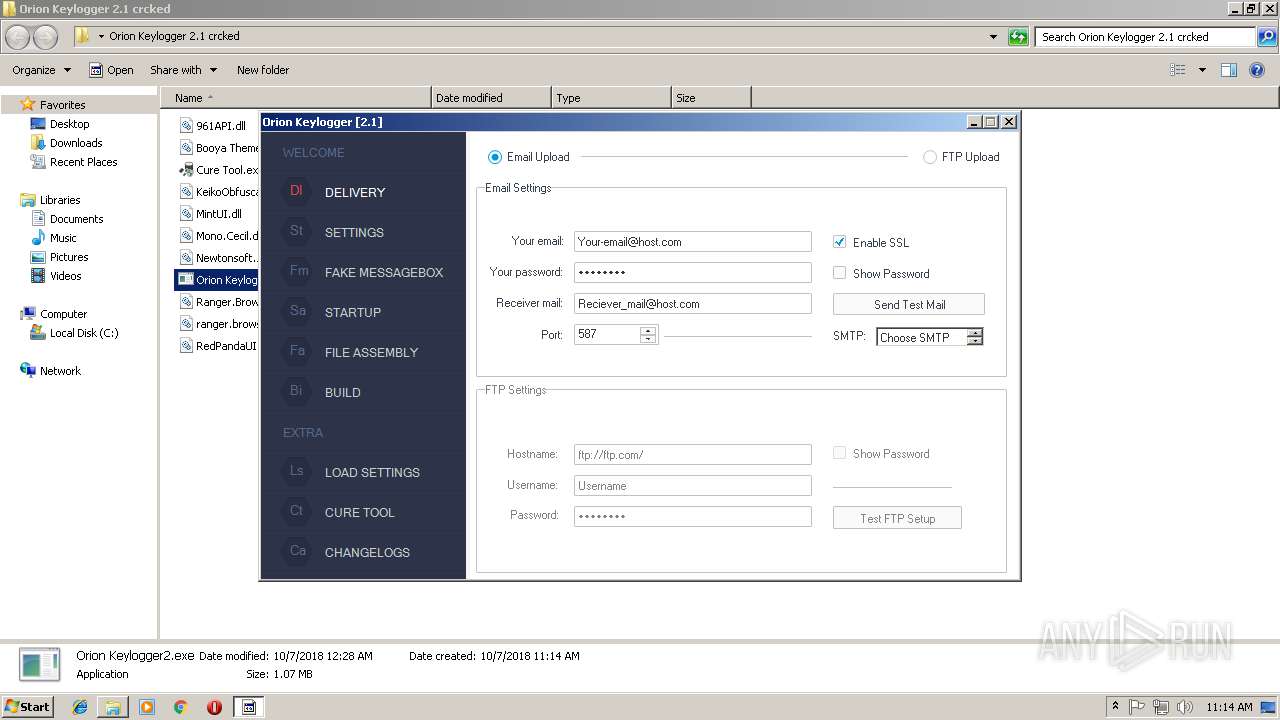
| 1260 | "C:\Users\admin\Desktop\Orion Keylogger 2.1 crcked\Orion Keylogger2.exe" | C:\Users\admin\Desktop\Orion Keylogger 2.1 crcked\Orion Keylogger2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Orion Keylogger Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1300 | "C:\Users\admin\AppData\Local\Temp\Cure Tool.exe" | C:\Users\admin\AppData\Local\Temp\Cure Tool.exe | — | Cure Tool.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Cure Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1684 | "C:\Users\admin\Desktop\Orion Keylogger 2.1 crcked\1115.exe" | C:\Users\admin\Desktop\Orion Keylogger 2.1 crcked\1115.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft @ 2015 Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\95505b2e-f2bf-4b2e-b402-c82bea2a8b92.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\AppData\Local\Temp\HQUHlwGxWA.exe" | C:\Users\admin\AppData\Local\Temp\HQUHlwGxWA.exe | — | 1115.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.6473.36168 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\AppData\Roaming\TeamViewer\twvrsvc.exe" | C:\Users\admin\AppData\Roaming\TeamViewer\twvrsvc.exe | tvsxwrc.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
11 068
Read events
10 856
Write events
207
Delete events
5
Modification events
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\95505b2e-f2bf-4b2e-b402-c82bea2a8b92.zip | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1744) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
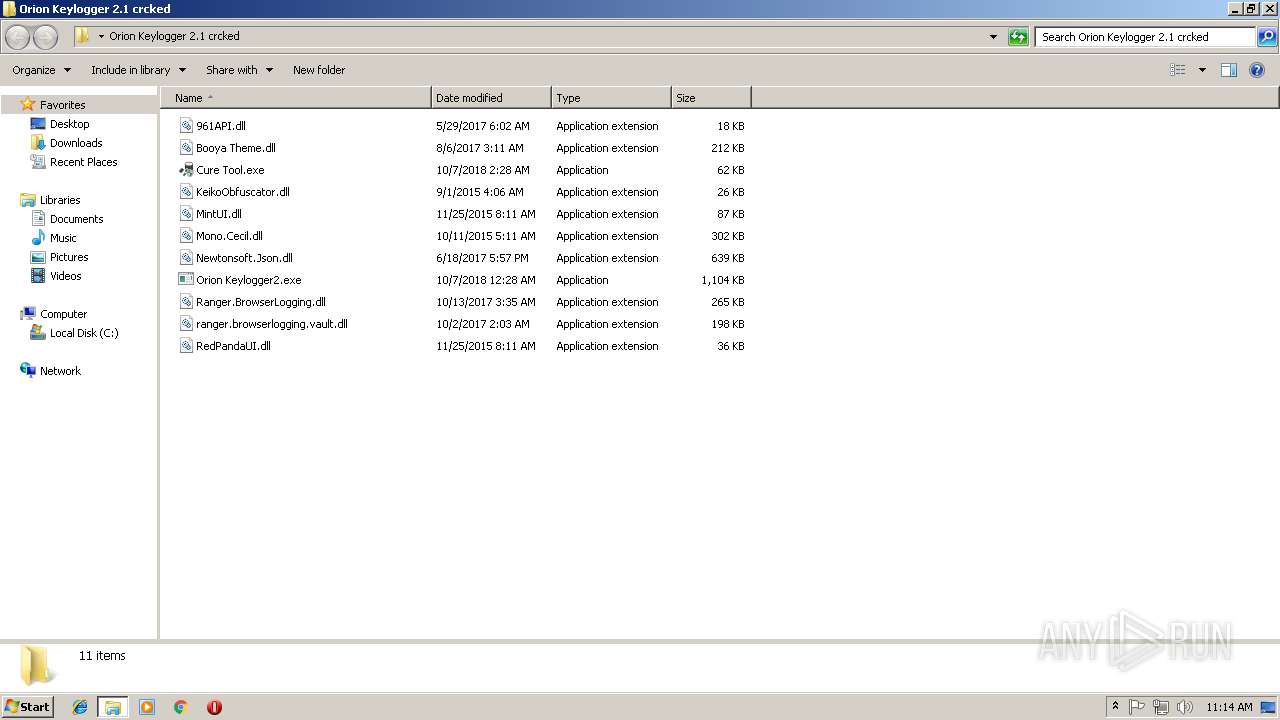
Executable files
15
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\961API.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\Booya Theme.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\Cure Tool.exe | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\KeikoObfuscator.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\MintUI.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\Mono.Cecil.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\Newtonsoft.Json.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\Orion Keylogger2.exe | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\Ranger.BrowserLogging.dll | — | |
MD5:— | SHA256:— | |||
| 1744 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1744.45860\Orion Keylogger 2.1 crcked\ranger.browserlogging.vault.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
12
DNS requests
6
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
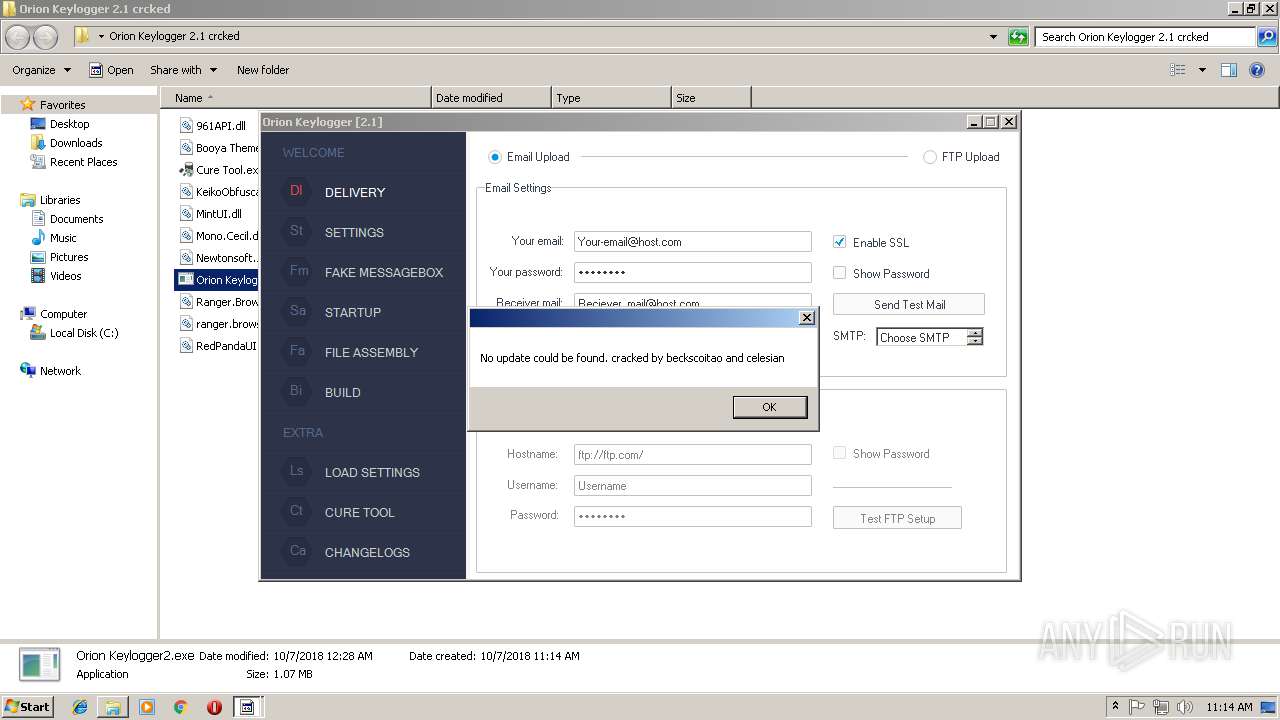
1260 | Orion Keylogger2.exe | GET | — | 198.54.117.200:80 | http://www.orionkeylogger.com/update/CurrentVersion.txt | US | — | — | malicious |
1260 | Orion Keylogger2.exe | GET | — | 198.54.117.200:80 | http://www.orionkeylogger.com/update/CurrentVersion.txt | US | — | — | malicious |
364 | 1115.exe | GET | 200 | 104.24.28.29:80 | http://puu.sh/jMSLc.txt | US | text | 28 b | shared |
364 | 1115.exe | GET | 200 | 147.75.40.2:80 | http://icanhazip.com/ | US | text | 16 b | shared |
1684 | 1115.exe | GET | 200 | 104.24.28.29:80 | http://puu.sh/jMSLc.txt | US | text | 28 b | shared |
1684 | 1115.exe | GET | 200 | 147.75.40.2:80 | http://icanhazip.com/ | US | text | 16 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1260 | Orion Keylogger2.exe | 198.54.117.200:80 | www.orionkeylogger.com | Namecheap, Inc. | US | malicious |
2052 | twvrsvc.exe | 104.20.208.21:443 | pastebin.com | Cloudflare Inc | US | shared |
1684 | 1115.exe | 104.24.28.29:80 | puu.sh | Cloudflare Inc | US | shared |
1684 | 1115.exe | 147.75.40.2:80 | icanhazip.com | Packet Host, Inc. | US | suspicious |
364 | 1115.exe | 104.24.28.29:80 | puu.sh | Cloudflare Inc | US | shared |
2656 | bfsvc.exe | 104.24.28.29:443 | puu.sh | Cloudflare Inc | US | shared |
364 | 1115.exe | 147.75.40.2:80 | icanhazip.com | Packet Host, Inc. | US | suspicious |
2116 | bfsvc.exe | 104.24.28.29:443 | puu.sh | Cloudflare Inc | US | shared |
3720 | Regasm.exe | 94.130.64.225:45700 | xmr.pool.minergate.com | Hetzner Online GmbH | DE | suspicious |
2052 | twvrsvc.exe | 201.26.98.80:4782 | uipapai.duckdns.org | TELEFÔNICA BRASIL S.A | BR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.orionkeylogger.com |
| malicious |
pastebin.com |
| malicious |
uipapai.duckdns.org |
| malicious |
puu.sh |
| shared |
xmr.pool.minergate.com |
| suspicious |
icanhazip.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1260 | Orion Keylogger2.exe | A Network Trojan was detected | ET CNC Zeus Tracker Reported CnC Server group 11 |
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1684 | 1115.exe | A Network Trojan was detected | MALWARE [PTsecurity] Posible Upatre puu.sh double encoded base64 artifact |
1056 | svchost.exe | A Network Trojan was detected | ET POLICY Monero Mining Pool DNS Lookup |
3720 | Regasm.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
3720 | Regasm.exe | Misc activity | SUSPICIOUS [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
3720 | Regasm.exe | Misc activity | SUSPICIOUS [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3720 | Regasm.exe | Misc activity | SUSPICIOUS [PTsecurity] Risktool.W32.coinminer!c |
3720 | Regasm.exe | Misc activity | SUSPICIOUS [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3720 | Regasm.exe | Misc activity | SUSPICIOUS [PTsecurity] Risktool.W32.coinminer!c |
4 ETPRO signatures available at the full report