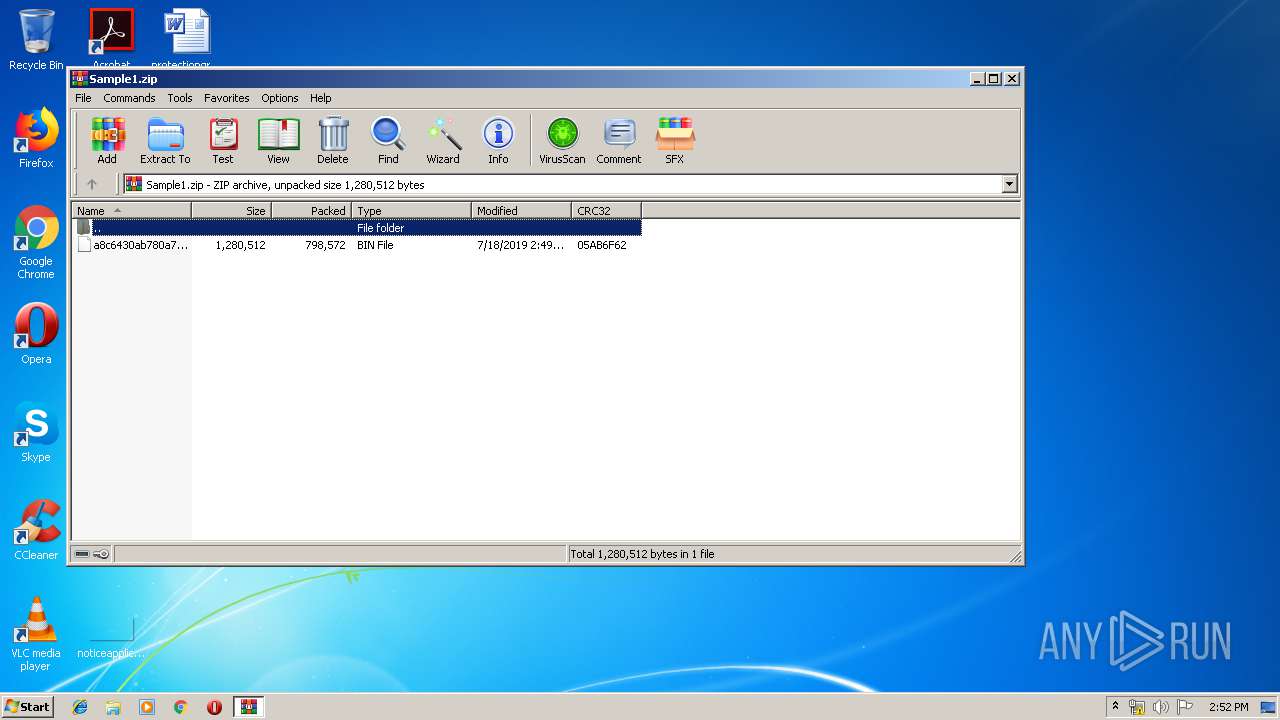
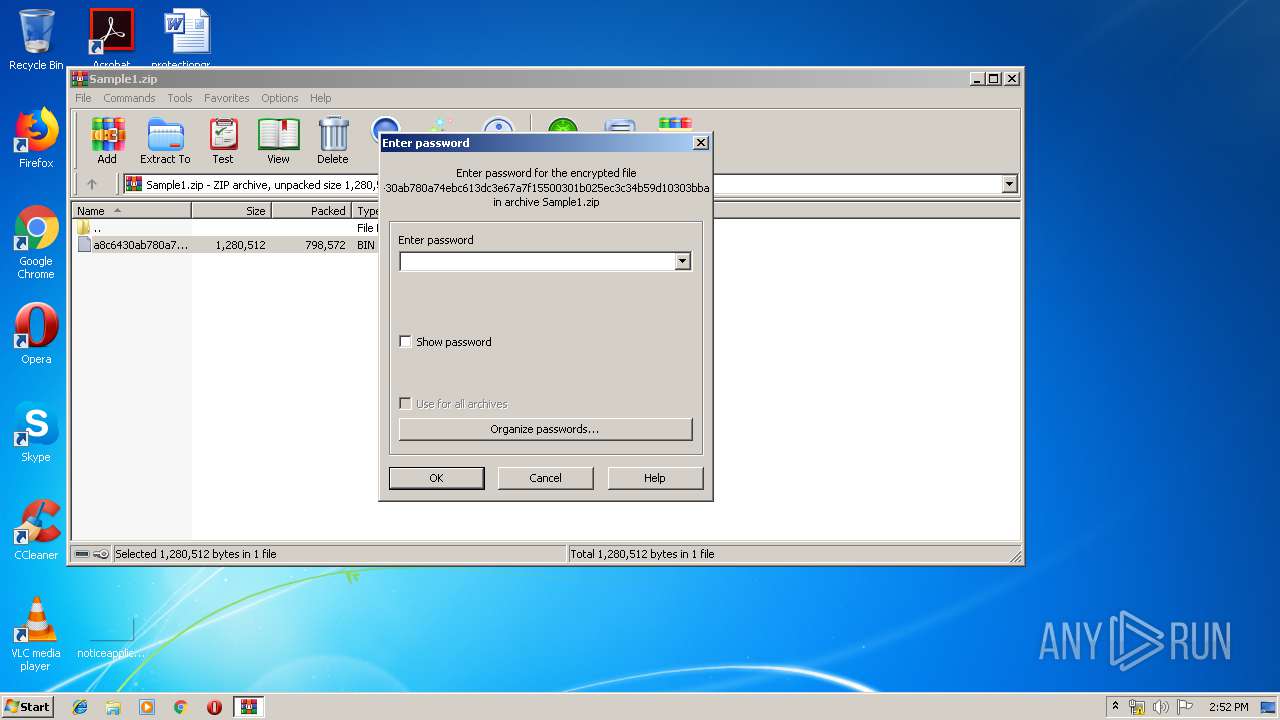
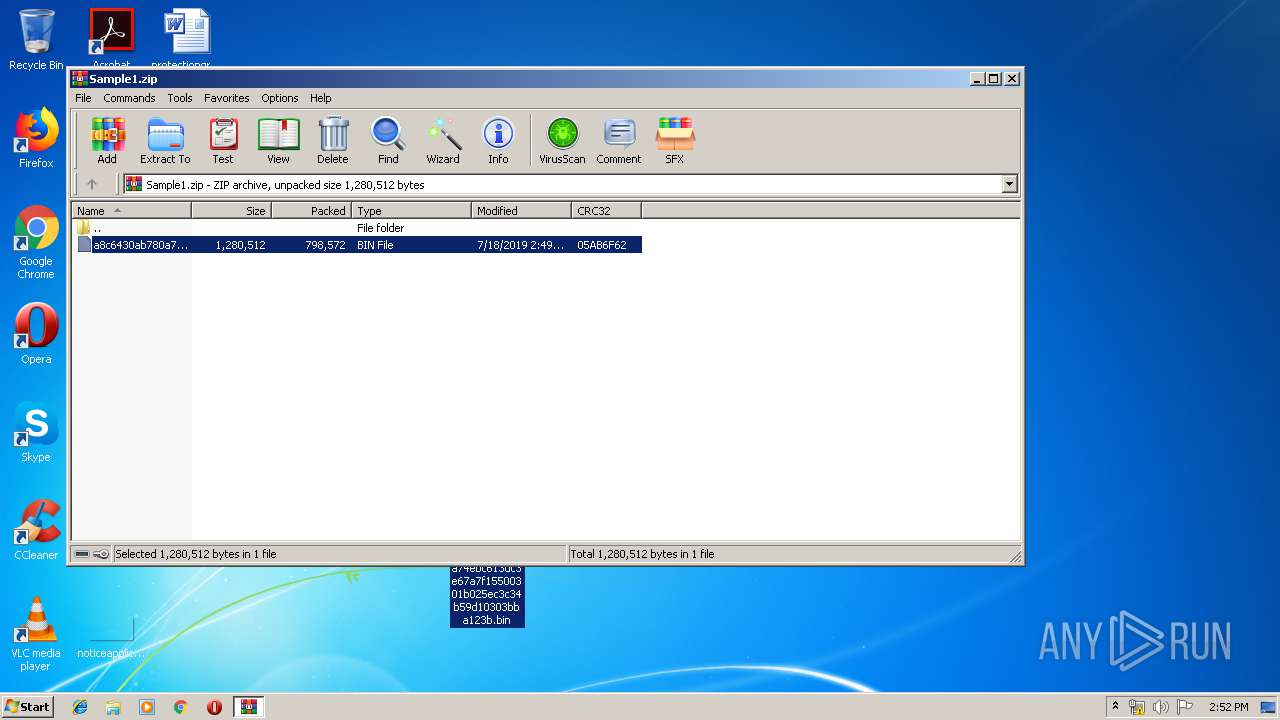
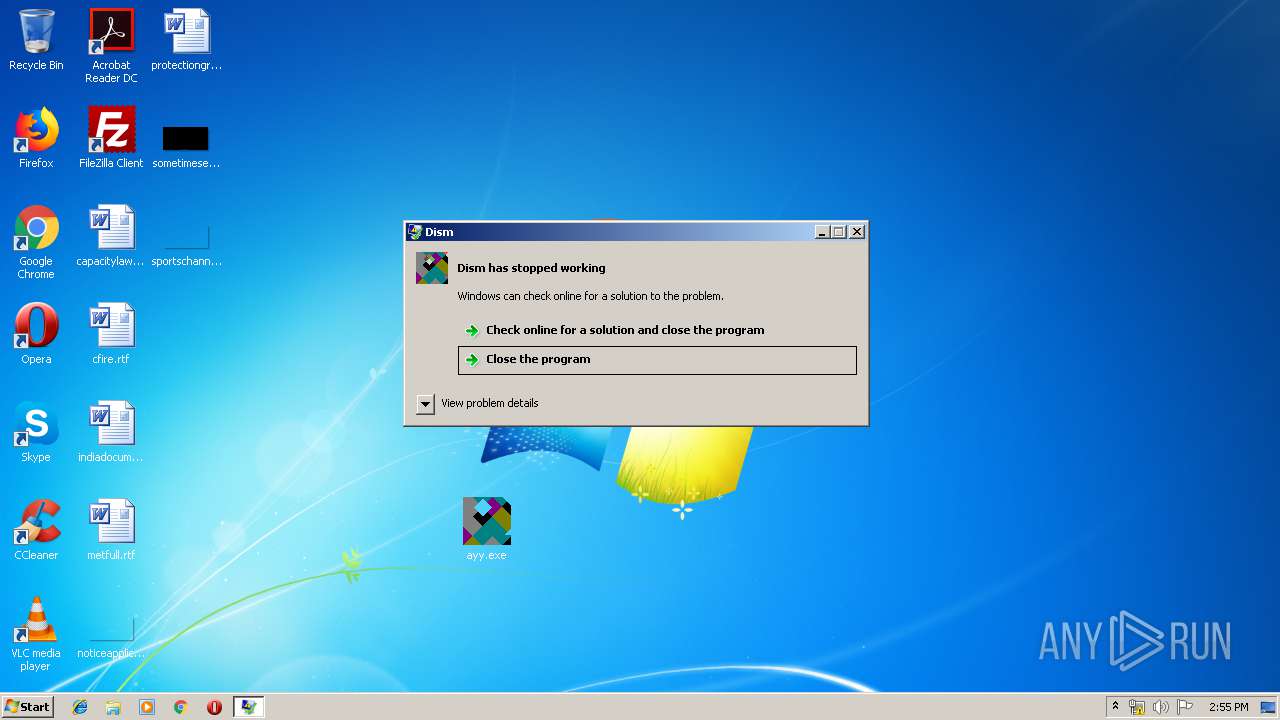
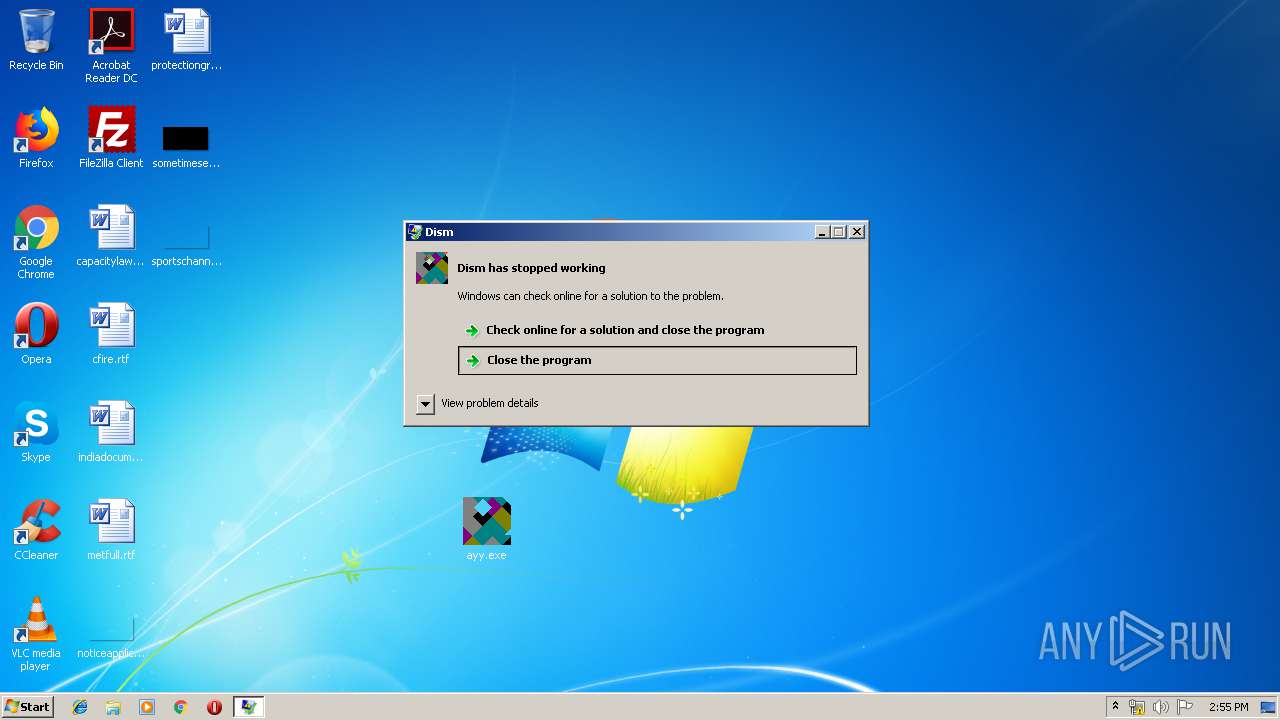
| File name: | Sample1.zip |
| Full analysis: | https://app.any.run/tasks/4719dfb2-30c8-4cfb-9b10-526122b68410 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 18, 2019, 13:51:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A0C6D990462AC9CC0B6E3C24AAEE0739 |
| SHA1: | F55C51D24466F5879513111BC9FCE3817BB518A9 |
| SHA256: | 8EA2888DBD5D09954FC81E6BF9E60C5E15F632A0691E7773B74C11127CB60ED8 |
| SSDEEP: | 24576:kju0tZyEpqN2DQ6HS+UNLJnNSzjcgwjQLnsciAq:wGNgD5MLNgcjotiV |
MALICIOUS
Changes the autorun value in the registry
- ayy.exe (PID: 2712)
- mstsc.exe (PID: 2352)
- utylw4f4hd.exe (PID: 3020)
Application was dropped or rewritten from another process
- ayy.exe (PID: 3760)
- ayy.exe (PID: 1940)
- ayy.exe (PID: 2256)
- ayy.exe (PID: 1996)
- ayy.exe (PID: 1844)
- ayy.exe (PID: 3848)
- ayy.exe (PID: 2712)
- ayy.exe (PID: 2776)
- ayy.exe (PID: 3504)
- ayy.exe (PID: 312)
- ayy.exe (PID: 2948)
- ayy.exe (PID: 1980)
- ayy.exe (PID: 3572)
- ayy.exe (PID: 2704)
- ayy.exe (PID: 3704)
- ayy.exe (PID: 3392)
- utylw4f4hd.exe (PID: 3020)
- ayy.exe (PID: 1468)
- utylw4f4hd.exe (PID: 2252)
- utylw4f4hd.exe (PID: 2432)
- utylw4f4hd.exe (PID: 4040)
- utylw4f4hd.exe (PID: 2128)
- utylw4f4hd.exe (PID: 952)
- utylw4f4hd.exe (PID: 1104)
- ayy.exe (PID: 592)
- ayy.exe (PID: 3240)
- ayy.exe (PID: 3836)
- ayy.exe (PID: 3764)
- ayy.exe (PID: 3432)
- ayy.exe (PID: 2516)
- ayy.exe (PID: 3972)
- ayy.exe (PID: 3952)
- ayy.exe (PID: 1868)
- ayy.exe (PID: 3328)
- ayy.exe (PID: 3252)
- ayy.exe (PID: 3588)
- ayy.exe (PID: 2816)
- ayy.exe (PID: 2912)
FORMBOOK was detected
- explorer.exe (PID: 292)
Connects to CnC server
- explorer.exe (PID: 292)
Formbook was detected
- mstsc.exe (PID: 2352)
- Firefox.exe (PID: 4008)
Actions looks like stealing of personal data
- mstsc.exe (PID: 2352)
Stealing of credential data
- mstsc.exe (PID: 2352)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3852)
- ayy.exe (PID: 2712)
- DllHost.exe (PID: 2260)
- explorer.exe (PID: 292)
Suspicious files were dropped or overwritten
- ayy.exe (PID: 2712)
Creates files in the user directory
- mstsc.exe (PID: 2352)
Executed via COM
- DllHost.exe (PID: 2260)
Creates files in the program directory
- DllHost.exe (PID: 2260)
Executes scripts
- explorer.exe (PID: 292)
Loads DLL from Mozilla Firefox
- mstsc.exe (PID: 2352)
Application launched itself
- utylw4f4hd.exe (PID: 3020)
- ayy.exe (PID: 2712)
Starts CMD.EXE for commands execution
- mstsc.exe (PID: 2352)
INFO
Manual execution by user
- wuapp.exe (PID: 3112)
- ayy.exe (PID: 2712)
- rdpclip.exe (PID: 3456)
- autoconv.exe (PID: 3040)
- msg.exe (PID: 1476)
- mstsc.exe (PID: 2352)
Creates files in the user directory
- Firefox.exe (PID: 4008)
Application was crashed
- utylw4f4hd.exe (PID: 3020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:18 13:49:17 |
| ZipCRC: | 0x05ab6f62 |
| ZipCompressedSize: | 798572 |
| ZipUncompressedSize: | 1280512 |
| ZipFileName: | a8c6430ab780a74ebc613dc3e67a7f15500301b025ec3c34b59d10303bba123b.bin |
Total processes
99
Monitored processes
59
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Windows\System32\cmmon32.exe" | C:\Windows\System32\cmmon32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Monitor Exit code: 0 Version: 7.02.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 292 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | "C:\Users\admin\Desktop\ayy.exe" | C:\Users\admin\Desktop\ayy.exe | — | ayy.exe | |||||||||||
User: admin Company: diskraid Integrity Level: MEDIUM Description: Dism Exit code: 0 Version: 422.642.997.65 Modules
| |||||||||||||||
| 592 | "C:\Users\admin\Desktop\ayy.exe" | C:\Users\admin\Desktop\ayy.exe | — | ayy.exe | |||||||||||
User: admin Company: diskraid Integrity Level: MEDIUM Description: Dism Exit code: 0 Version: 422.642.997.65 Modules
| |||||||||||||||
| 804 | "C:\Windows\System32\wscript.exe" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Wkhylq\utylw4f4hd.exe" | C:\Program Files\Wkhylq\utylw4f4hd.exe | — | utylw4f4hd.exe | |||||||||||
User: admin Company: diskraid Integrity Level: MEDIUM Description: Dism Exit code: 0 Version: 422.642.997.65 Modules
| |||||||||||||||
| 1104 | "C:\Program Files\Wkhylq\utylw4f4hd.exe" | C:\Program Files\Wkhylq\utylw4f4hd.exe | — | utylw4f4hd.exe | |||||||||||
User: admin Company: diskraid Integrity Level: MEDIUM Description: Dism Exit code: 0 Version: 422.642.997.65 Modules
| |||||||||||||||
| 1372 | "C:\Windows\System32\services.exe" | C:\Windows\System32\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1468 | "C:\Users\admin\Desktop\ayy.exe" | C:\Users\admin\Desktop\ayy.exe | — | ayy.exe | |||||||||||
User: admin Company: diskraid Integrity Level: MEDIUM Description: Dism Exit code: 0 Version: 422.642.997.65 Modules
| |||||||||||||||
| 1476 | "C:\Windows\System32\msg.exe" | C:\Windows\System32\msg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Message Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 260
Read events
2 212
Write events
48
Delete events
0
Modification events
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Sample1.zip | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (292) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (292) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
6
Suspicious files
73
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 292 | explorer.exe | C:\Users\admin\Desktop\a8c6430ab780a74ebc613dc3e67a7f15500301b025ec3c34b59d10303bba123b.bin | executable | |
MD5:— | SHA256:— | |||
| 292 | explorer.exe | C:\Users\admin\AppData\Local\Temp\Wkhylq\utylw4f4hd.exe | executable | |
MD5:— | SHA256:— | |||
| 2352 | mstsc.exe | C:\Users\admin\AppData\Roaming\OM718DVE\OM7logim.jpeg | image | |
MD5:— | SHA256:— | |||
| 4008 | Firefox.exe | C:\Users\admin\AppData\Roaming\OM718DVE\OM7logrf.ini | binary | |
MD5:— | SHA256:— | |||
| 2352 | mstsc.exe | C:\Users\admin\AppData\Roaming\OM718DVE\OM7logri.ini | binary | |
MD5:D63A82E5D81E02E399090AF26DB0B9CB | SHA256:EAECE2EBA6310253249603033C744DD5914089B0BB26BDE6685EC9813611BAAE | |||
| 2352 | mstsc.exe | C:\Users\admin\AppData\Roaming\OM718DVE\OM7logrc.ini | binary | |
MD5:— | SHA256:— | |||
| 2712 | ayy.exe | C:\Users\Public\NeYQCBOkZD.vbs | text | |
MD5:— | SHA256:— | |||
| 2712 | ayy.exe | C:\Users\admin\AppData\Local\Temp\ActionCenterCPL\at.bat | executable | |
MD5:— | SHA256:— | |||
| 2260 | DllHost.exe | C:\Program Files\Wkhylq\utylw4f4hd.exe | executable | |
MD5:— | SHA256:— | |||
| 2352 | mstsc.exe | C:\Users\admin\AppData\Roaming\OM718DVE\OM7logrv.ini | binary | |
MD5:BA3B6BC807D4F76794C4B81B09BB9BA5 | SHA256:6EEBF968962745B2E9DE2CA969AF7C424916D4E3FE3CC0BB9B3D414ABFCE9507 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
17
DNS requests
6
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
292 | explorer.exe | GET | — | 162.215.255.133:80 | http://www.dducargo-vancouver.com/ki/?yVftqxDh=mM20bzQXHsnD3wKkmRZxih6GLVXnjRmY6kFRMh8bCXjRIQjwiJpWRc6F3caD/2adGz5fkw==&1b3=o8TpZlH&sql=1 | US | — | — | malicious |
292 | explorer.exe | POST | — | 91.184.0.100:80 | http://www.zorgeloosontruimen.com/ki/ | NL | — | — | malicious |
292 | explorer.exe | GET | 404 | 91.184.0.100:80 | http://www.zorgeloosontruimen.com/ki/?yVftqxDh=wplG0/9dvDGY5iUrxjBRxUnVFYbT692W7AlK5Bp4Cm37hopIlAgv4Nv5M4nhR3xgVBKtSA==&1b3=o8TpZlH&sql=1 | NL | html | 201 b | malicious |
292 | explorer.exe | POST | — | 162.215.255.133:80 | http://www.dducargo-vancouver.com/ki/ | US | — | — | malicious |
292 | explorer.exe | POST | — | 91.184.0.100:80 | http://www.zorgeloosontruimen.com/ki/ | NL | — | — | malicious |
292 | explorer.exe | GET | 403 | 107.154.192.178:80 | http://www.xf6900.com/ki/?yVftqxDh=8vdrInXG4N3PWtPuwUHbTlb7crQLhHSvXYnRadqvPDximIIly4DY77YIaRWIXONSRshcNg==&1b3=o8TpZlH&sql=1 | US | html | 807 b | malicious |
292 | explorer.exe | POST | — | 162.215.255.133:80 | http://www.dducargo-vancouver.com/ki/ | US | — | — | malicious |
292 | explorer.exe | POST | — | 107.154.192.178:80 | http://www.xf6900.com/ki/ | US | — | — | malicious |
292 | explorer.exe | GET | 404 | 199.192.30.91:80 | http://www.kerxbin.com/ki/?yVftqxDh=GUMbK9e7bDYWx5MZ5V13d8s+uoH9vku2W3mWGD6q3wUU6ffBAJF9lZjfFyLQx5Fwqvjy9Q==&1b3=o8TpZlH | US | html | 326 b | malicious |
292 | explorer.exe | POST | — | 54.36.26.9:80 | http://www.paycatch.com/ki/ | FR | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
292 | explorer.exe | 199.192.30.91:80 | www.kerxbin.com | — | US | malicious |
— | — | 91.184.0.100:80 | www.zorgeloosontruimen.com | Hostnet B.V. | NL | malicious |
292 | explorer.exe | 162.215.255.133:80 | www.dducargo-vancouver.com | Krypt Technologies | US | malicious |
292 | explorer.exe | 91.184.0.100:80 | www.zorgeloosontruimen.com | Hostnet B.V. | NL | malicious |
292 | explorer.exe | 107.154.192.178:80 | www.xf6900.com | Incapsula Inc | US | malicious |
292 | explorer.exe | 54.36.26.9:80 | www.paycatch.com | OVH SAS | FR | malicious |
— | — | 54.36.26.9:80 | www.paycatch.com | OVH SAS | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kerxbin.com |
| malicious |
www.zorgeloosontruimen.com |
| malicious |
www.dducargo-vancouver.com |
| malicious |
www.xf6900.com |
| malicious |
www.paycatch.com |
| malicious |
www.easyvegefruits.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
12 ETPRO signatures available at the full report