| File name: | PornHub.zip |
| Full analysis: | https://app.any.run/tasks/808969e0-d1ea-4d7e-9b2c-29086c1970c9 |
| Verdict: | Malicious activity |
| Threats: | Netwire is an advanced RAT — it is a malware that takes control of infected PCs and allows its operators to perform various actions. Unlike many RATs, this one can target every major operating system, including Windows, Linux, and MacOS. |
| Analysis date: | December 18, 2018, 07:20:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | ADE95C472F5C3ED647B23C85612ED2C7 |
| SHA1: | 7E58C8243AC48B38307CC9A78A21976E5FDBC4C5 |
| SHA256: | 8E99B33873493FB9DD266C082827835BF09C9EE42EB0FAD48CCAD993D7E4A813 |
| SSDEEP: | 12288:yOhM6K035OykxtFGQZjGmd2FXOjKUQ6hwwmS5kMtnlg0WpGGsbhEd3Gs2g6VUcYm:Tlpe/FG4h0wK7Gwwp5gTsbWd3z7hIp |
MALICIOUS
Application was dropped or rewritten from another process
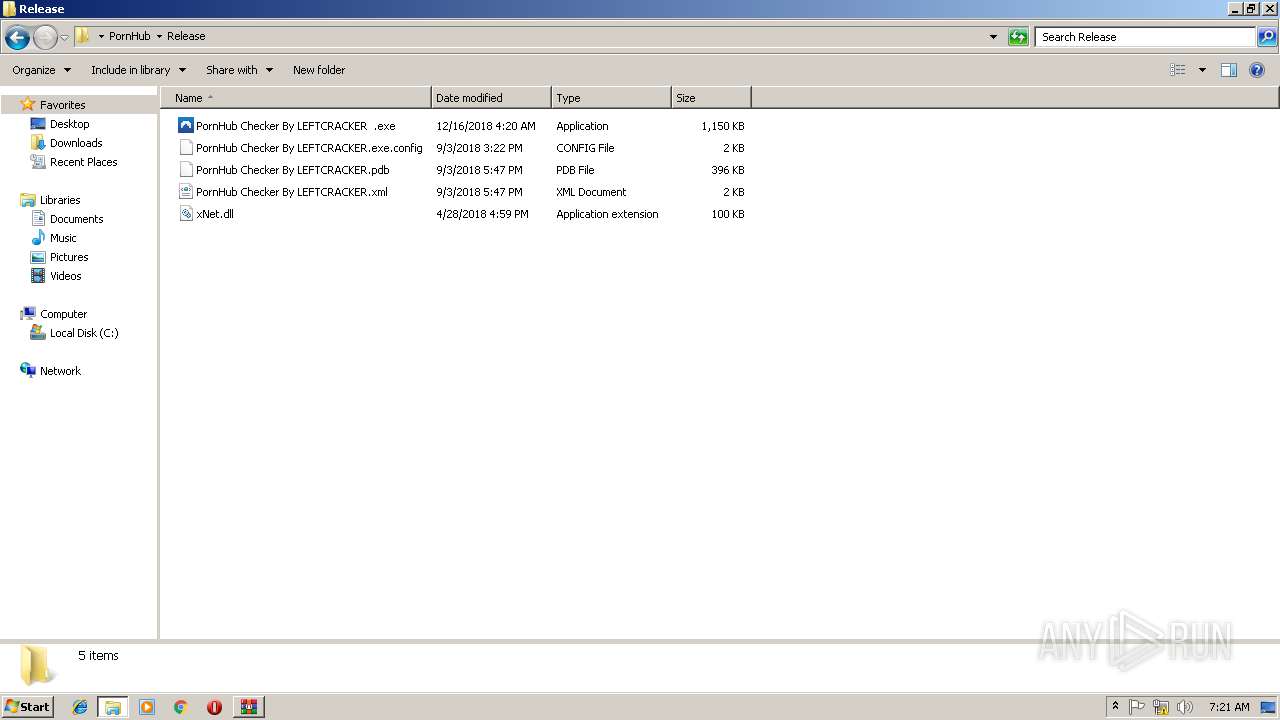
- PornHub Checker By LEFTCRACKER.exe (PID: 3300)
- pornhub.exe (PID: 3536)
- svchost.exe (PID: 3612)
- svchost.exe (PID: 2560)
- svchost.exe (PID: 2712)
- pornhub.exe (PID: 2580)
NETWIRE was detected
- svchost.exe (PID: 2712)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1472)
- PornHub Checker By LEFTCRACKER.exe (PID: 3300)
Changes the autorun value in the registry
- svchost.exe (PID: 2712)
SUSPICIOUS
Executable content was dropped or overwritten
- PornHub Checker By LEFTCRACKER .exe (PID: 1316)
- pornhub.exe (PID: 2580)
Connects to unusual port
- svchost.exe (PID: 2712)
Creates files in the user directory
- svchost.exe (PID: 2712)
- pornhub.exe (PID: 2580)
Creates executable files which already exist in Windows
- pornhub.exe (PID: 2580)
Application launched itself
- pornhub.exe (PID: 3536)
- svchost.exe (PID: 3612)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:12:16 05:33:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | PornHub/ |
Total processes
40
Monitored processes
10
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1316 | "C:\Users\admin\Desktop\PornHub\Release\PornHub Checker By LEFTCRACKER .exe" | C:\Users\admin\Desktop\PornHub\Release\PornHub Checker By LEFTCRACKER .exe | PornHub Checker By LEFTCRACKER .exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1472 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\AppData\Roaming\Microsoft\Network\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Network\svchost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Local\Temp\pornhub.exe" 0 | C:\Users\admin\AppData\Local\Temp\pornhub.exe | pornhub.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2712 | "C:\Users\admin\AppData\Roaming\Microsoft\Network\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Network\svchost.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3204 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PornHub.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3300 | "C:\Users\admin\AppData\Local\Temp\PornHub Checker By LEFTCRACKER.exe" 0 | C:\Users\admin\AppData\Local\Temp\PornHub Checker By LEFTCRACKER.exe | — | PornHub Checker By LEFTCRACKER .exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: PornHub Checker By LEFTCRACKER Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3532 | "C:\Users\admin\Desktop\PornHub\Release\PornHub Checker By LEFTCRACKER .exe" | C:\Users\admin\Desktop\PornHub\Release\PornHub Checker By LEFTCRACKER .exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3536 | "C:\Users\admin\AppData\Local\Temp\pornhub.exe" 0 | C:\Users\admin\AppData\Local\Temp\pornhub.exe | — | PornHub Checker By LEFTCRACKER .exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3612 | "C:\Users\admin\AppData\Roaming\Microsoft\Network\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Network\svchost.exe | — | pornhub.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 104
Read events
1 089
Write events
15
Delete events
0
Modification events
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PornHub.zip | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1472) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1472) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msxml3r.dll,-1 |
Value: XML Document | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3204.16624\PornHub\Release\PornHub Checker By LEFTCRACKER .exe | — | |
MD5:— | SHA256:— | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3204.16624\PornHub\Release\PornHub Checker By LEFTCRACKER.exe.config | — | |
MD5:— | SHA256:— | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3204.16624\PornHub\Release\PornHub Checker By LEFTCRACKER.pdb | — | |
MD5:— | SHA256:— | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3204.16624\PornHub\Release\PornHub Checker By LEFTCRACKER.xml | — | |
MD5:— | SHA256:— | |||
| 3204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3204.16624\PornHub\Release\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 1316 | PornHub Checker By LEFTCRACKER .exe | C:\Users\admin\AppData\Local\Temp\PornHub Checker By LEFTCRACKER.exe | executable | |
MD5:— | SHA256:— | |||
| 1316 | PornHub Checker By LEFTCRACKER .exe | C:\Users\admin\AppData\Local\Temp\PornHub Checker By LEFTCRACKER.pdb | pdb | |
MD5:— | SHA256:— | |||
| 1316 | PornHub Checker By LEFTCRACKER .exe | C:\Users\admin\AppData\Local\Temp\PornHub Checker By LEFTCRACKER.xml | xml | |
MD5:— | SHA256:— | |||
| 1316 | PornHub Checker By LEFTCRACKER .exe | C:\Users\admin\AppData\Local\Temp\pornhub.exe | executable | |
MD5:— | SHA256:— | |||
| 2712 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Network\Settings.ini | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2712 | svchost.exe | 37.228.134.84:8999 | playhardgopro.life | Mike Kaldig | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
playhardgopro.life |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2712 | svchost.exe | A Network Trojan was detected | SC SPYWARE Spyware Weecnaw Win32 |
2712 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Netwire.RAT |