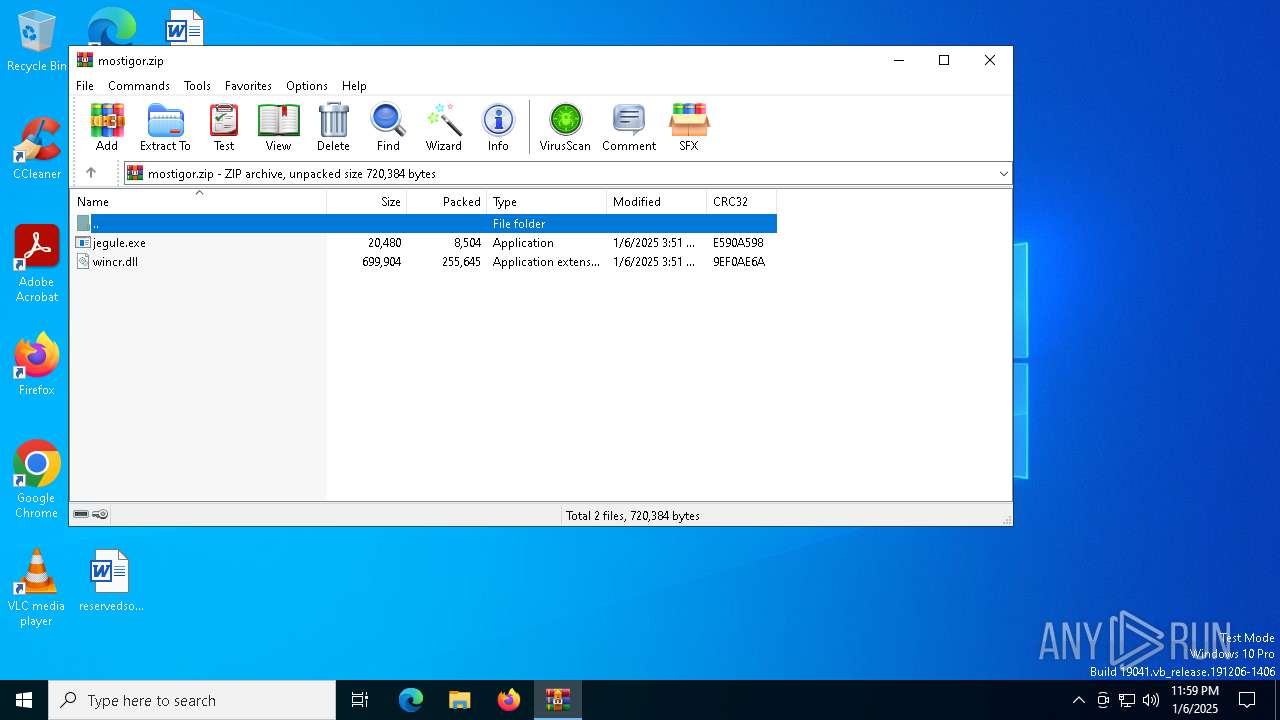
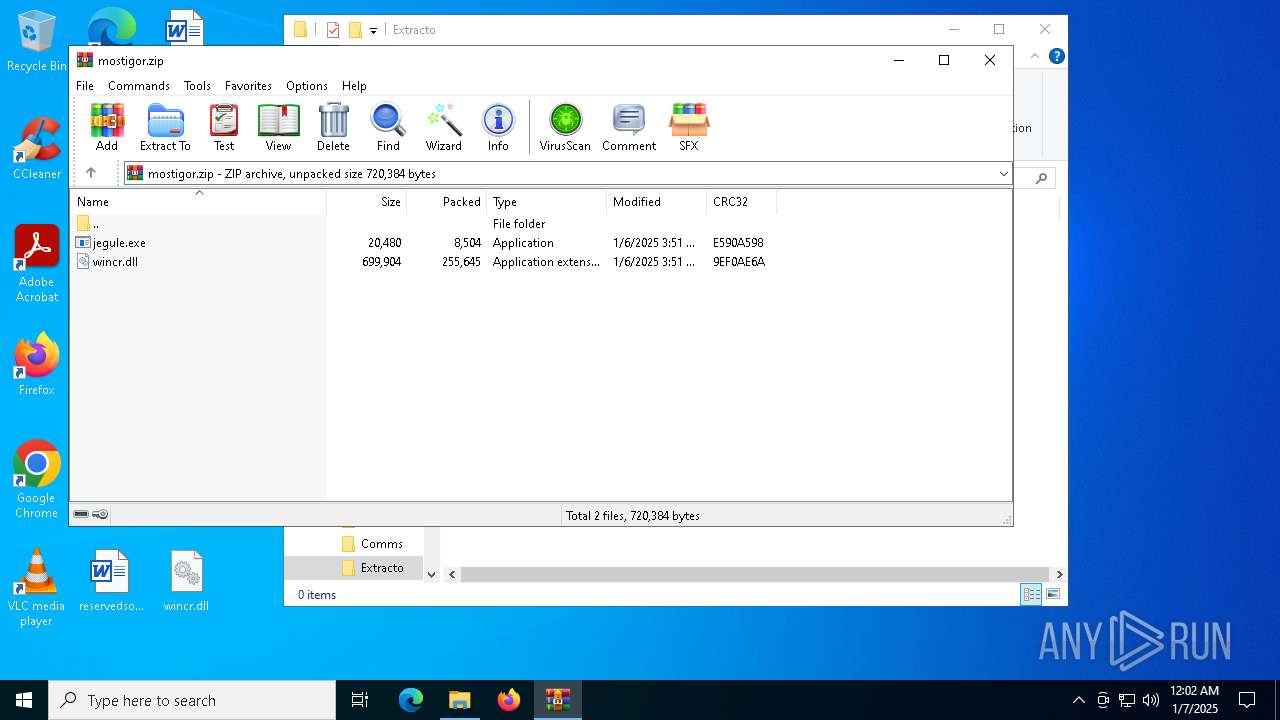
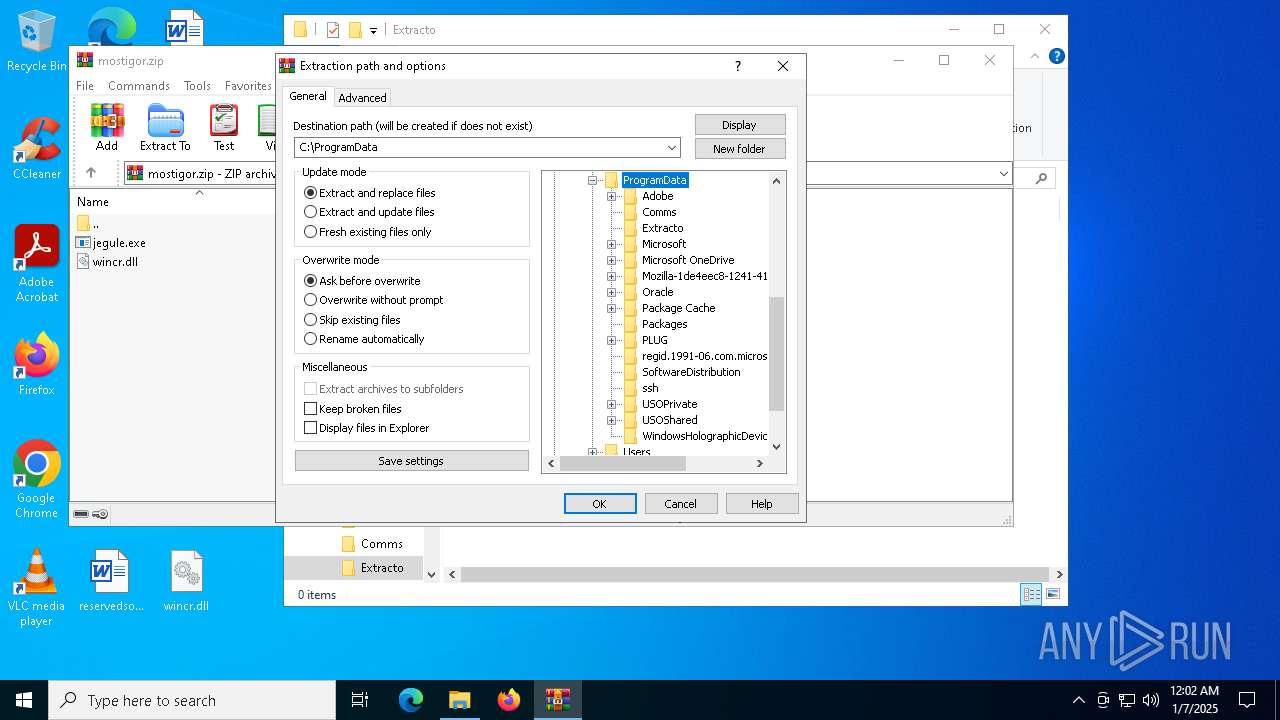
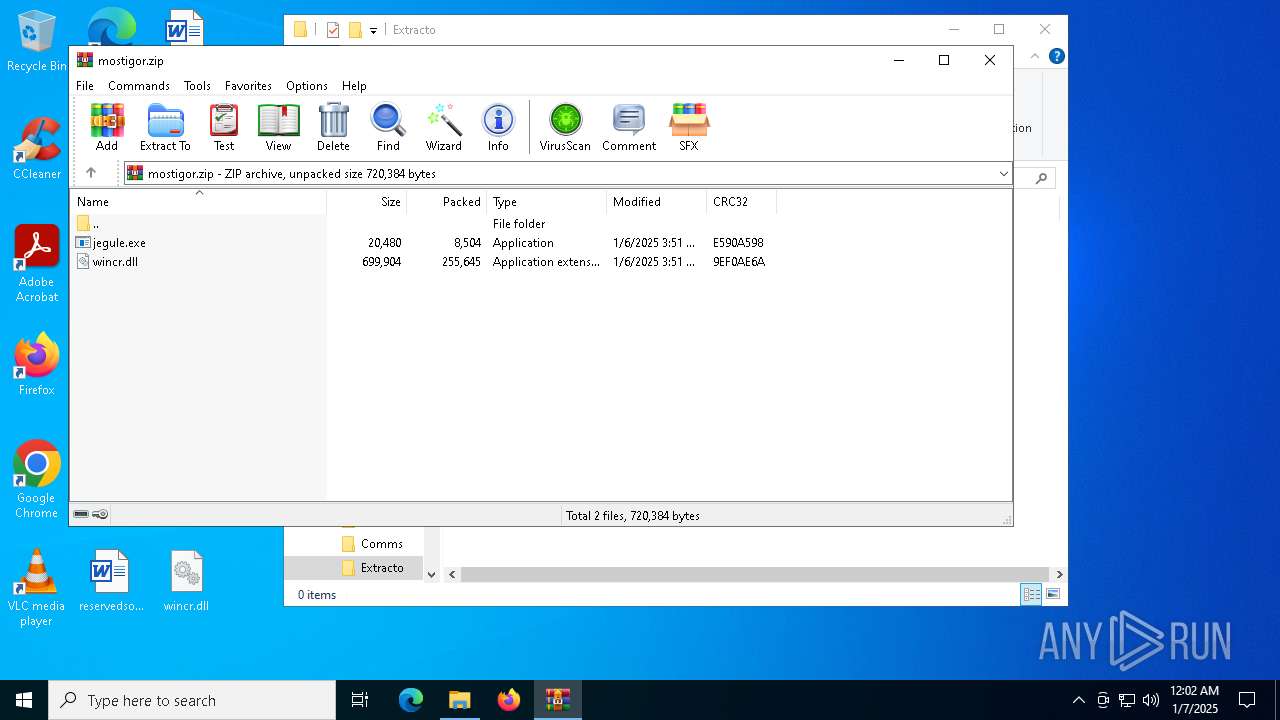
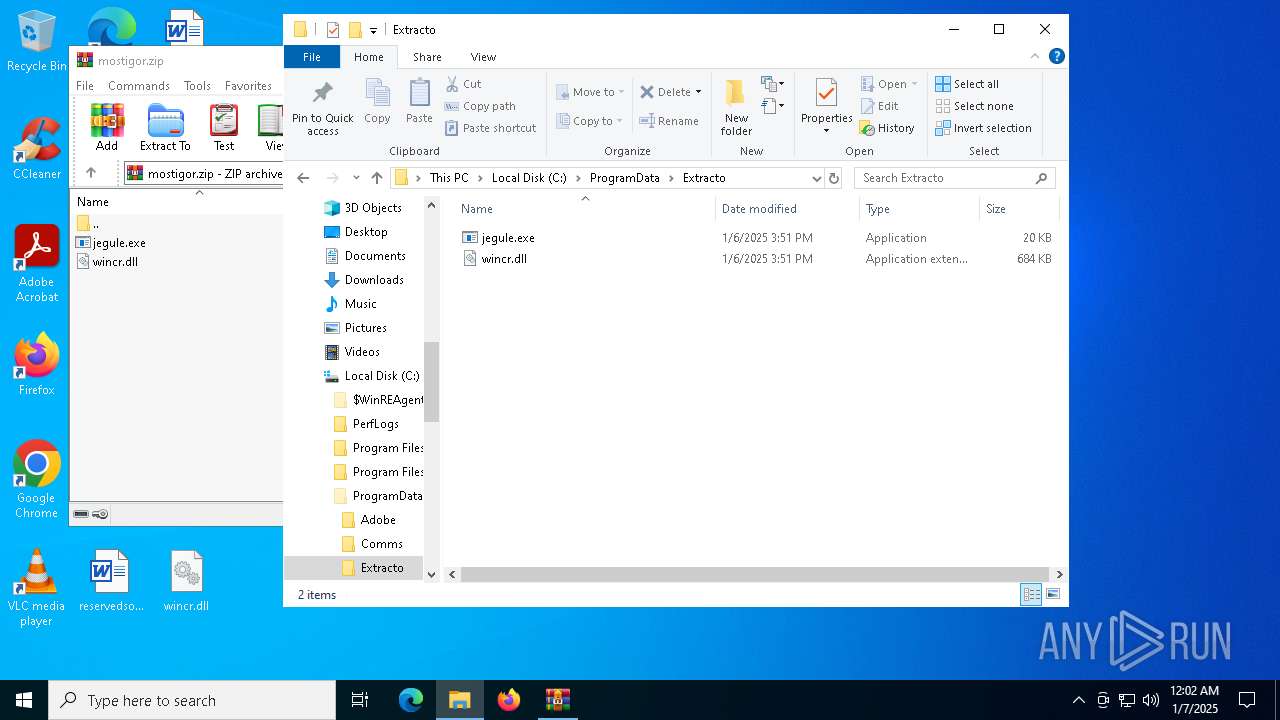
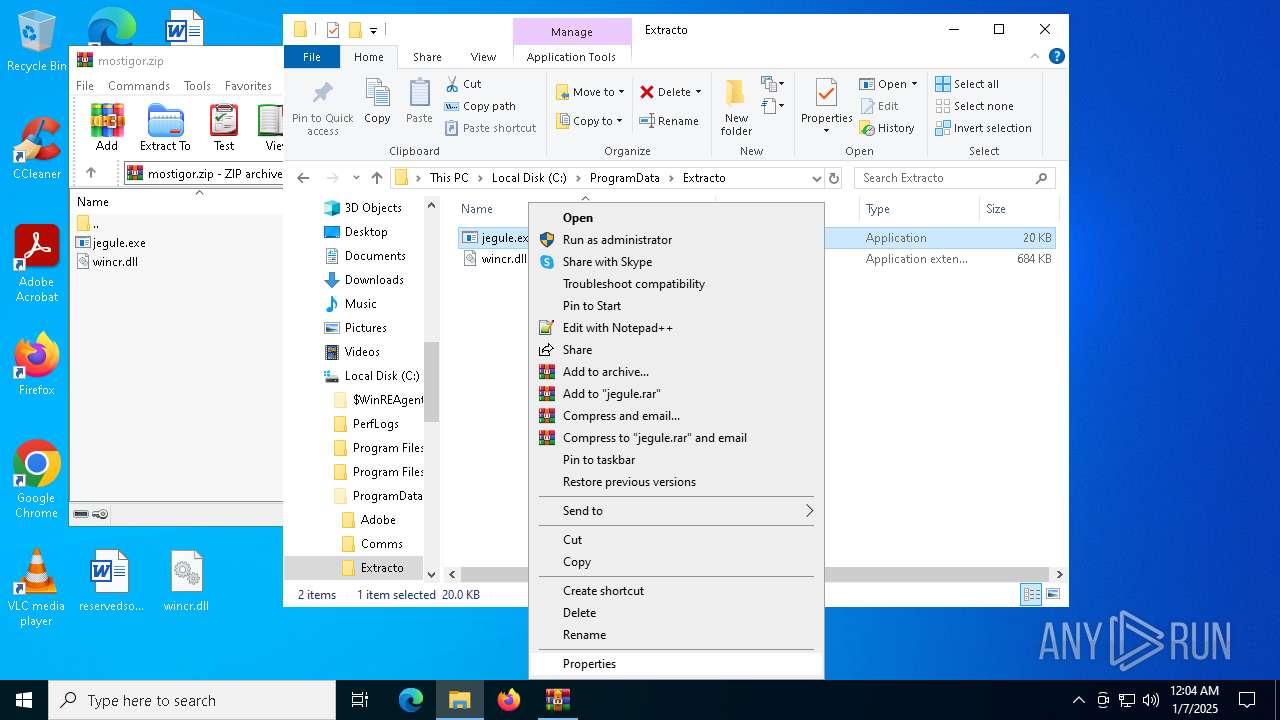
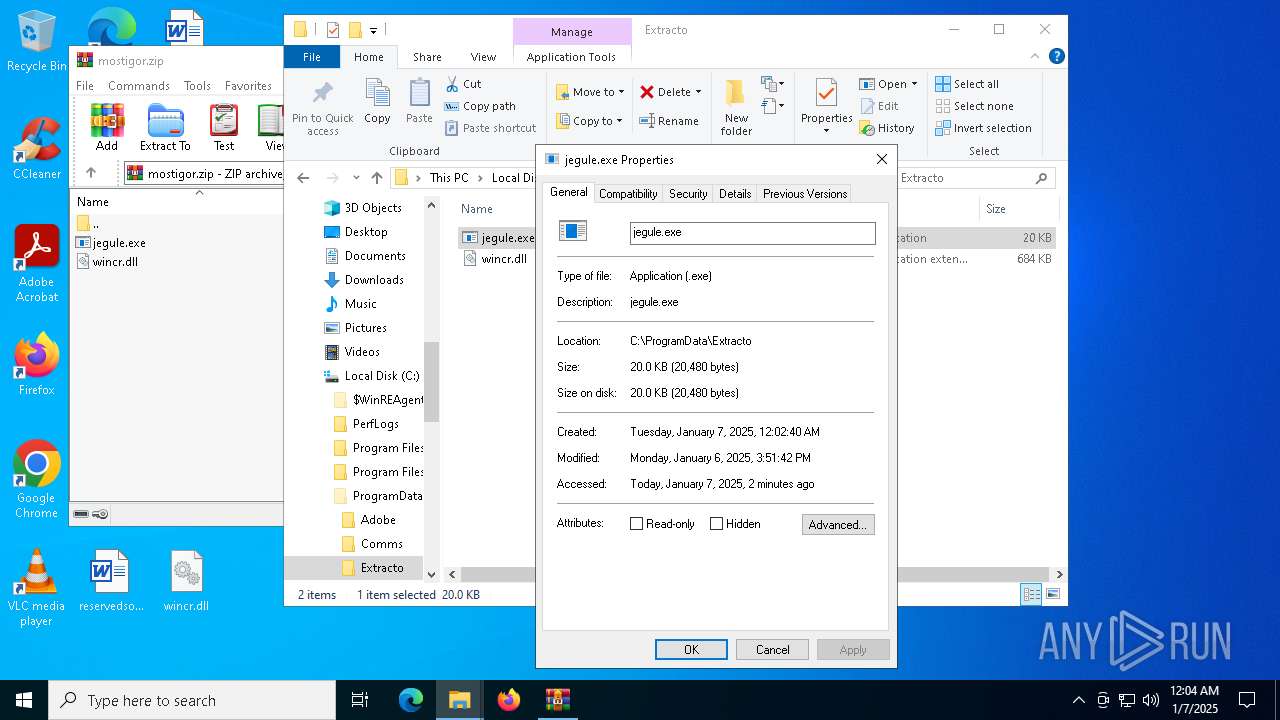
| File name: | mostigor.zip |
| Full analysis: | https://app.any.run/tasks/f2149e25-4a22-4800-bee0-b0a4dd58dc79 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 06, 2025, 23:59:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
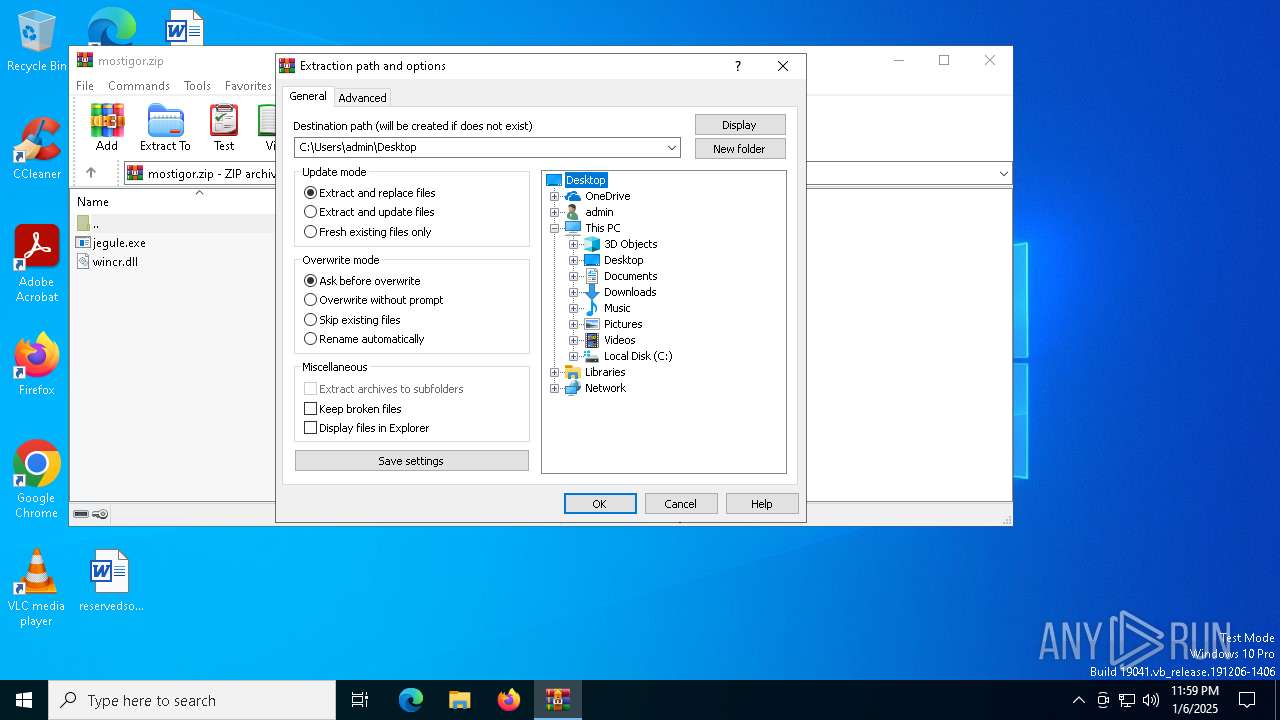
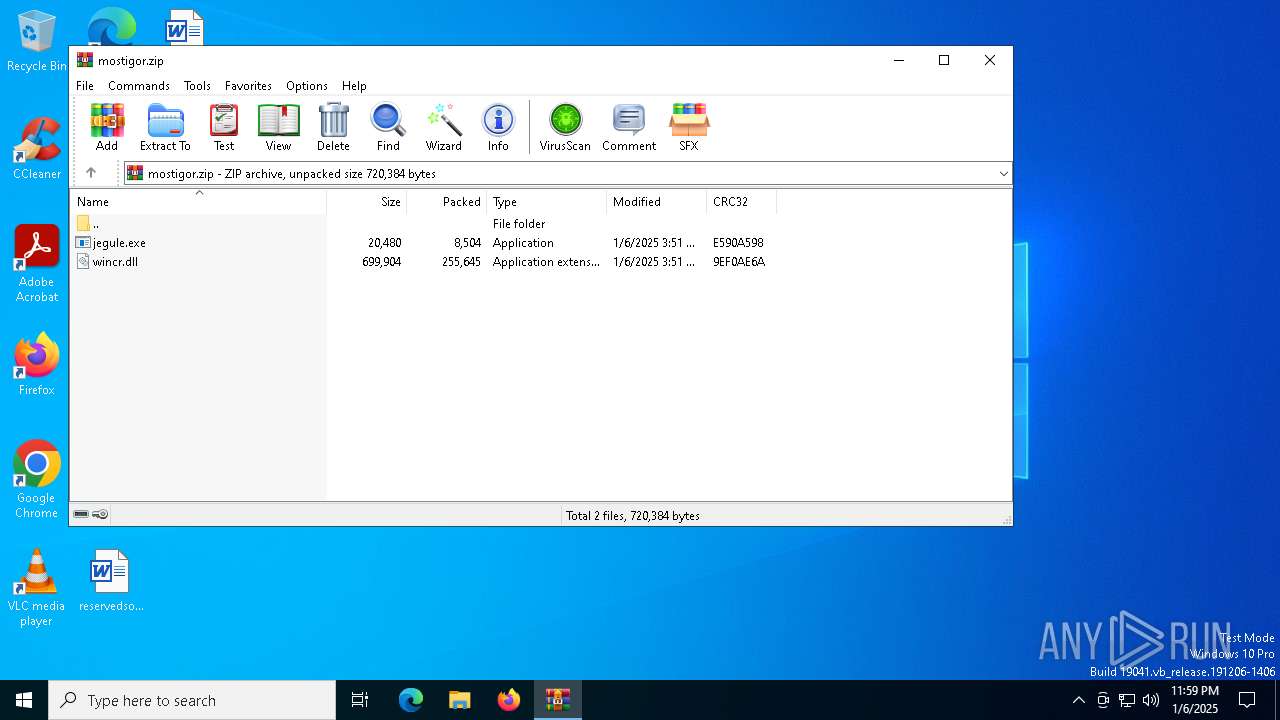
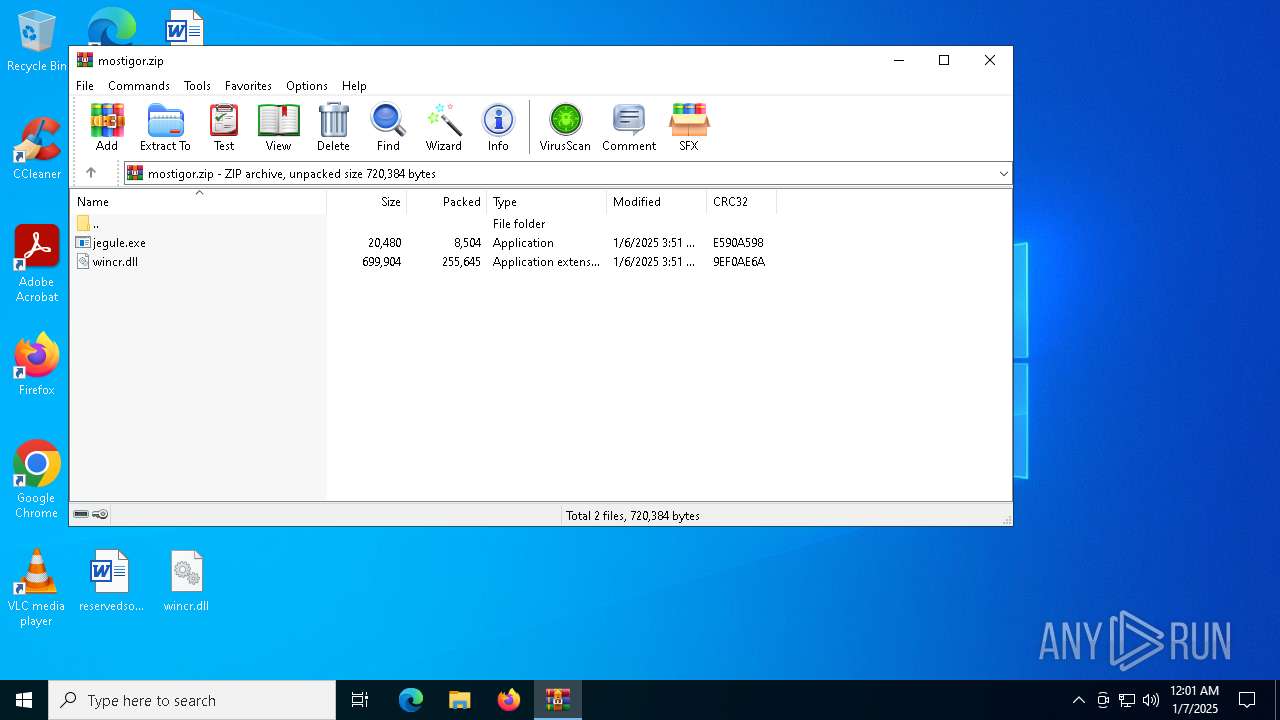
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6C836FB0BEC5752E3B3DB7B3C995366B |
| SHA1: | 56A84AA424305BA8911987DD900099577D308FD4 |
| SHA256: | 8E8CCD8A9C7AC82CC858E4823680945F9CD243727DF50587E581EA9BB662296A |
| SSDEEP: | 6144:q+sgUE1YsNzYk/IFWqrjU3sgsF/bLiOoWlrItV2HJwWAHlOMXUBQiGI05FD:VUE1YsdDIFeZ2/bHtdJc4MzinuFD |
MALICIOUS
Actions looks like stealing of personal data
- jegule.exe (PID: 7096)
- jegule.exe (PID: 3172)
LUMMA has been detected (SURICATA)
- jegule.exe (PID: 7096)
- jegule.exe (PID: 3172)
LUMMA mutex has been found
- jegule.exe (PID: 3172)
- jegule.exe (PID: 7096)
Steals credentials from Web Browsers
- jegule.exe (PID: 3172)
- jegule.exe (PID: 7096)
LUMMA has been detected (YARA)
- jegule.exe (PID: 7096)
SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 3612)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3612)
The process uses the downloaded file
- WinRAR.exe (PID: 3612)
Checks supported languages
- jegule.exe (PID: 7096)
- jegule.exe (PID: 3172)
Manual execution by a user
- jegule.exe (PID: 7096)
- jegule.exe (PID: 3172)
Reads the software policy settings
- jegule.exe (PID: 7096)
- jegule.exe (PID: 3172)
Creates files in the program directory
- WinRAR.exe (PID: 3612)
Reads the computer name
- jegule.exe (PID: 3172)
- jegule.exe (PID: 7096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:06 18:51:42 |
| ZipCRC: | 0xe590a598 |
| ZipCompressedSize: | 8504 |
| ZipUncompressedSize: | 20480 |
| ZipFileName: | jegule.exe |
Total processes
133
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3172 | "C:\ProgramData\Extracto\jegule.exe" | C:\ProgramData\Extracto\jegule.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3612 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\mostigor.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4640 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7096 | "C:\Users\admin\Desktop\jegule.exe" | C:\Users\admin\Desktop\jegule.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
3 666
Read events
3 626
Write events
15
Delete events
25
Modification events
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\mostigor.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3612 | WinRAR.exe | C:\Users\admin\Desktop\wincr.dll | executable | |
MD5:E41E2B47FE05AA5155CB079C4118CCDC | SHA256:196696B311241FEBE7F706082BBCE27BA0657C604F4FB54C83000D7454D537DD | |||
| 3612 | WinRAR.exe | C:\Users\admin\Desktop\jegule.exe | executable | |
MD5:FA97A6F9D73A5DF050E0DB6ACB82C478 | SHA256:C7C7CED1B2FA62AA6C504B0BA04031DC804EE7A35B5D9A99DF37FBF25A6CB86F | |||
| 3612 | WinRAR.exe | C:\ProgramData\Extracto\wincr.dll | executable | |
MD5:E41E2B47FE05AA5155CB079C4118CCDC | SHA256:196696B311241FEBE7F706082BBCE27BA0657C604F4FB54C83000D7454D537DD | |||
| 3612 | WinRAR.exe | C:\ProgramData\Extracto\jegule.exe | executable | |
MD5:FA97A6F9D73A5DF050E0DB6ACB82C478 | SHA256:C7C7CED1B2FA62AA6C504B0BA04031DC804EE7A35B5D9A99DF37FBF25A6CB86F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
43
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1016 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6340 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1016 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
healbewilk.cyou |
| unknown |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7096 | jegule.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
3172 | jegule.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |