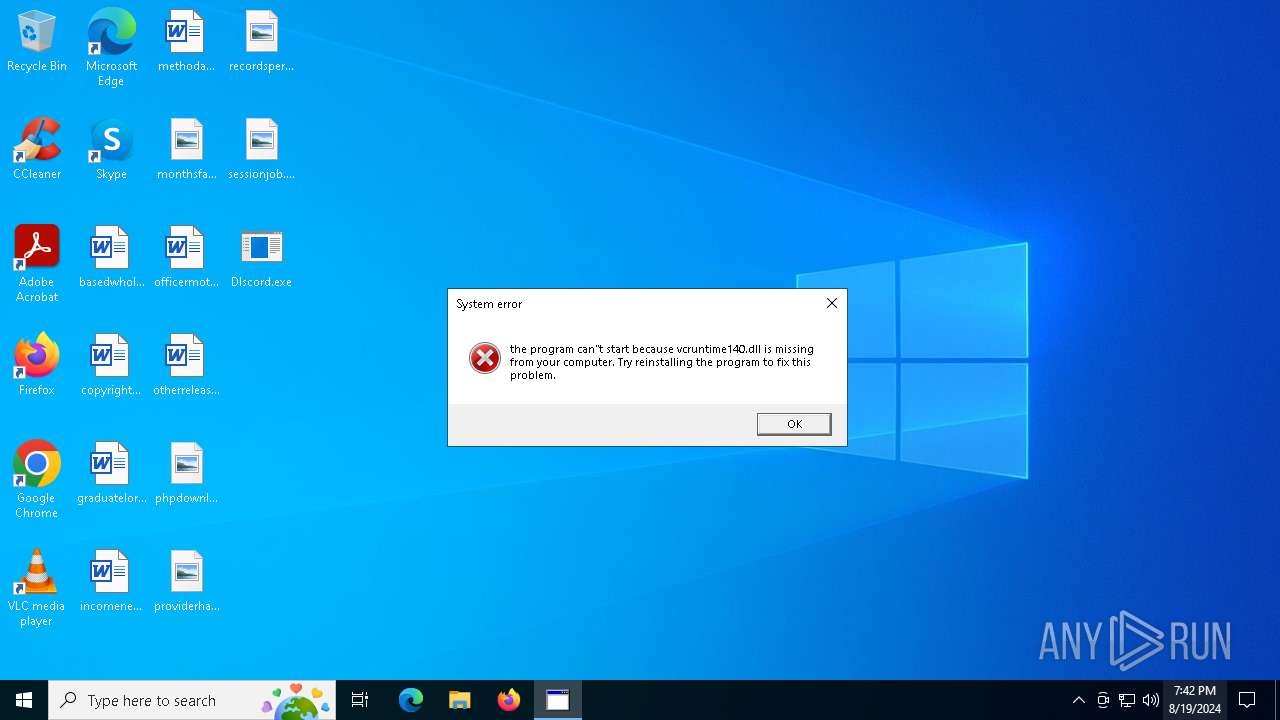
| File name: | Dlscord.exe |
| Full analysis: | https://app.any.run/tasks/e3d00097-f4f9-49fa-a399-5b1aef839998 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | August 19, 2024, 19:42:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 701261310F04AEB5EB7C4A755AD922E2 |
| SHA1: | 32A1332C3C2D687A26C3561F407CED82F867A343 |
| SHA256: | 8DF9E4634F675CC1F9256F0F432948470C64C42FA981C416AF686A98B94E959E |
| SSDEEP: | 98304:uEWcombJgjSGLR6Mhwv61cA/E3D4asIDlkWPSPQvJVfPVNbequajmAaryKNa4fZU:XJFrwd1O1Wa1 |
MALICIOUS
BlankGrabber has been detected
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 6632)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 6852)
- MpCmdRun.exe (PID: 7628)
Adds path to the Windows Defender exclusion list
- Dlscord.exe (PID: 6324)
- cmd.exe (PID: 6860)
- cmd.exe (PID: 6920)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 6852)
Create files in the Startup directory
- Dlscord.exe (PID: 6324)
Actions looks like stealing of personal data
- Dlscord.exe (PID: 6324)
Bypass execution policy to execute commands
- powershell.exe (PID: 7672)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7392)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 6940)
GROWTOPIA has been detected (YARA)
- Dlscord.exe (PID: 6324)
DISCORDGRABBER has been detected (YARA)
- Dlscord.exe (PID: 6324)
UMBRALSTEALER has been detected (YARA)
- Dlscord.exe (PID: 6324)
Stealers network behavior
- Dlscord.exe (PID: 6324)
Starts CMD.EXE for self-deleting
- Dlscord.exe (PID: 6324)
BLANKGRABBER has been detected (SURICATA)
- Dlscord.exe (PID: 6324)
SUSPICIOUS
Process drops legitimate windows executable
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
Drops the executable file immediately after the start
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
- csc.exe (PID: 7272)
The process drops C-runtime libraries
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
Starts a Microsoft application from unusual location
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
Process drops python dynamic module
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
Executable content was dropped or overwritten
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
- csc.exe (PID: 7272)
Application launched itself
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
Loads Python modules
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6324)
Starts CMD.EXE for commands execution
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6324)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6772)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 6180)
Found strings related to reading or modifying Windows Defender settings
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6324)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 2628)
- cmd.exe (PID: 6968)
Changes default file association
- reg.exe (PID: 6940)
Get information on the list of running processes
- Dlscord.exe (PID: 6324)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 6484)
- cmd.exe (PID: 6308)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6960)
- cmd.exe (PID: 1568)
- cmd.exe (PID: 7324)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6860)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 6920)
- cmd.exe (PID: 7152)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 6896)
- cmd.exe (PID: 7240)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 6756)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6860)
- cmd.exe (PID: 6920)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 3916)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 6500)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7132)
- WMIC.exe (PID: 6864)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 6964)
- WMIC.exe (PID: 6884)
- WMIC.exe (PID: 6632)
Script disables Windows Defender's IPS
- cmd.exe (PID: 6852)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 6852)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6896)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6472)
Starts application with an unusual extension
- cmd.exe (PID: 6728)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 7952)
- cmd.exe (PID: 8188)
- cmd.exe (PID: 8096)
- cmd.exe (PID: 7432)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7204)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7392)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7392)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7500)
Base64-obfuscated command line is found
- cmd.exe (PID: 7392)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7252)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6888)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 6872)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7412)
Checks for external IP
- svchost.exe (PID: 2256)
- Dlscord.exe (PID: 6324)
Hides command output
- cmd.exe (PID: 608)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 608)
INFO
Checks supported languages
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
- tree.com (PID: 7540)
- tree.com (PID: 7888)
- tree.com (PID: 7664)
- tree.com (PID: 6164)
- tree.com (PID: 8052)
- tree.com (PID: 8160)
- cvtres.exe (PID: 7448)
- rar.exe (PID: 7252)
- MpCmdRun.exe (PID: 7628)
- csc.exe (PID: 7272)
Reads the computer name
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
- MpCmdRun.exe (PID: 7628)
Create files in a temporary directory
- Dlscord.exe (PID: 6732)
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
- MpCmdRun.exe (PID: 7628)
- cvtres.exe (PID: 7448)
- rar.exe (PID: 7252)
- csc.exe (PID: 7272)
Reads the machine GUID from the registry
- Dlscord.exe (PID: 6752)
- Dlscord.exe (PID: 6324)
- rar.exe (PID: 7252)
- csc.exe (PID: 7272)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 6632)
- WMIC.exe (PID: 7132)
- WMIC.exe (PID: 6964)
- WMIC.exe (PID: 6884)
- WMIC.exe (PID: 7500)
- WMIC.exe (PID: 8152)
- WMIC.exe (PID: 6864)
- WMIC.exe (PID: 6632)
- WMIC.exe (PID: 6872)
Reads Microsoft Office registry keys
- ComputerDefaults.exe (PID: 6632)
Reads Internet Explorer settings
- mshta.exe (PID: 5156)
Creates files in the program directory
- Dlscord.exe (PID: 6324)
The Powershell gets current clipboard
- powershell.exe (PID: 7416)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5880)
- powershell.exe (PID: 6492)
- powershell.exe (PID: 6524)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6524)
- powershell.exe (PID: 5880)
- powershell.exe (PID: 6492)
- powershell.exe (PID: 7564)
- powershell.exe (PID: 7976)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 8144)
PyInstaller has been detected (YARA)
- Dlscord.exe (PID: 6508)
- Dlscord.exe (PID: 6324)
Found Base64 encoded reflection usage via PowerShell (YARA)
- Dlscord.exe (PID: 6324)
UPX packer has been detected
- Dlscord.exe (PID: 6324)
Attempting to use instant messaging service
- Dlscord.exe (PID: 6324)
- svchost.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:03 12:51:06+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 168960 |
| InitializedDataSize: | 93184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.1 |
| ProductVersionNumber: | 10.0.19041.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Paint |
| FileVersion: | 10.0.19041.1 (WinBuild.160101.0800) |
| InternalName: | MSPAINT |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | MSPAINT.EXE |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.1 |
Total processes
264
Monitored processes
140
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | C:\WINDOWS\system32\cmd.exe /c "ping localhost -n 3 > NUL && del /A H /F "C:\Users\admin\Desktop\Dlscord.exe"" | C:\Windows\System32\cmd.exe | — | Dlscord.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | ping localhost -n 3 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | C:\WINDOWS\system32\cmd.exe /c "powershell Get-ItemPropertyValue -Path 'HKLM:System\CurrentControlSet\Control\Session Manager\Environment' -Name PROCESSOR_IDENTIFIER" | C:\Windows\System32\cmd.exe | — | Dlscord.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\system32\cmd.exe /c "WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntivirusProduct Get displayName" | C:\Windows\System32\cmd.exe | — | Dlscord.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | C:\WINDOWS\system32\cmd.exe /c "wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /f:text" | C:\Windows\System32\cmd.exe | — | Dlscord.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | C:\WINDOWS\system32\cmd.exe /c "REG QUERY HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E968-E325-11CE-BFC1-08002BE10318}\0000\DriverDesc 2" | C:\Windows\System32\cmd.exe | — | Dlscord.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
71 216
Read events
71 187
Write events
25
Delete events
4
Modification events
| (PID) Process: | (6940) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (7060) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7060) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7060) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7060) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6632) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6632) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6632) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6260) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6260) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
38
Suspicious files
16
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_ssl.pyd | executable | |
MD5:081C878324505D643A70EFCC5A80A371 | SHA256:FCB70B58F94F5B0F9D027999CCE25E99DDCC8124E4DDCC521CB5B96A52FAAA66 | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_ctypes.pyd | executable | |
MD5:813FC3981CAE89A4F93BF7336D3DC5EF | SHA256:4AC7FB7B354069E71EBF7FCC193C0F99AF559010A0AD82A03B49A92DEB0F4D06 | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_bz2.pyd | executable | |
MD5:93FE6D3A67B46370565DB12A9969D776 | SHA256:92EC61CA9AC5742E0848A6BBB9B6B4CDA8E039E12AB0F17FB9342D082DDE471B | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_sqlite3.pyd | executable | |
MD5:BB4AA2D11444900C549E201EB1A4CDD6 | SHA256:F44D80AB16C27CA65DA23AE5FDA17EB842065F3E956F10126322B2EA3ECDF43F | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_queue.pyd | executable | |
MD5:0E7612FC1A1FAD5A829D4E25CFA87C4F | SHA256:9F6965EB89BBF60DF0C51EF0750BBD0655675110D6C42ECA0274D109BD9F18A8 | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_socket.pyd | executable | |
MD5:7A31BC84C0385590E5A01C4CBE3865C3 | SHA256:5614017765322B81CC57D841B3A63CBDC88678FF605E5D4C8FDBBF8F0AC00F36 | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\libcrypto-1_1.dll | executable | |
MD5:DAA2EED9DCEAFAEF826557FF8A754204 | SHA256:4DAB915333D42F071FE466DF5578FD98F38F9E0EFA6D9355E9B4445FFA1CA914 | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\_lzma.pyd | executable | |
MD5:6F810F46F308F7C6CCDDCA45D8F50039 | SHA256:39497259B87038E86C53E7A39A0B5BBBFCEBE00B2F045A148041300B31F33B76 | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\base_library.zip | compressed | |
MD5:F5B15AC0A24A122D69C41843DA5D463B | SHA256:EC3B8C865C6E3C5E35449B32DCB397DA665D6A10FBEE61284489A6C420C72A3B | |||
| 6732 | Dlscord.exe | C:\Users\admin\AppData\Local\Temp\_MEI67322\libffi-7.dll | executable | |
MD5:6F818913FAFE8E4DF7FEDC46131F201F | SHA256:3F94EE4F23F6C7702AB0CC12995A6457BF22183FA828C30CC12288ADF153AE56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
9
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6324 | Dlscord.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
— | — | GET | 204 | 142.250.186.35:443 | https://gstatic.com/generate_204 | unknown | — | — | unknown |
6324 | Dlscord.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
— | — | POST | 404 | 162.159.135.232:443 | https://discord.com/api/webhooks/1269273673685139456/UN9rTUpGrME_KVElyoBoKVAaGAVxygBPmqXWhFuAFkr2kIJurXS6QMDR55lDYTBArSvY | unknown | binary | 45 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3992 | svchost.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
5292 | RUXIMICS.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
3992 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6324 | Dlscord.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
6324 | Dlscord.exe | 142.250.185.163:443 | gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
blank-1mykb.in |
| unknown |
ip-api.com |
| shared |
gstatic.com |
| whitelisted |
discord.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6324 | Dlscord.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6324 | Dlscord.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6324 | Dlscord.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6324 | Dlscord.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |