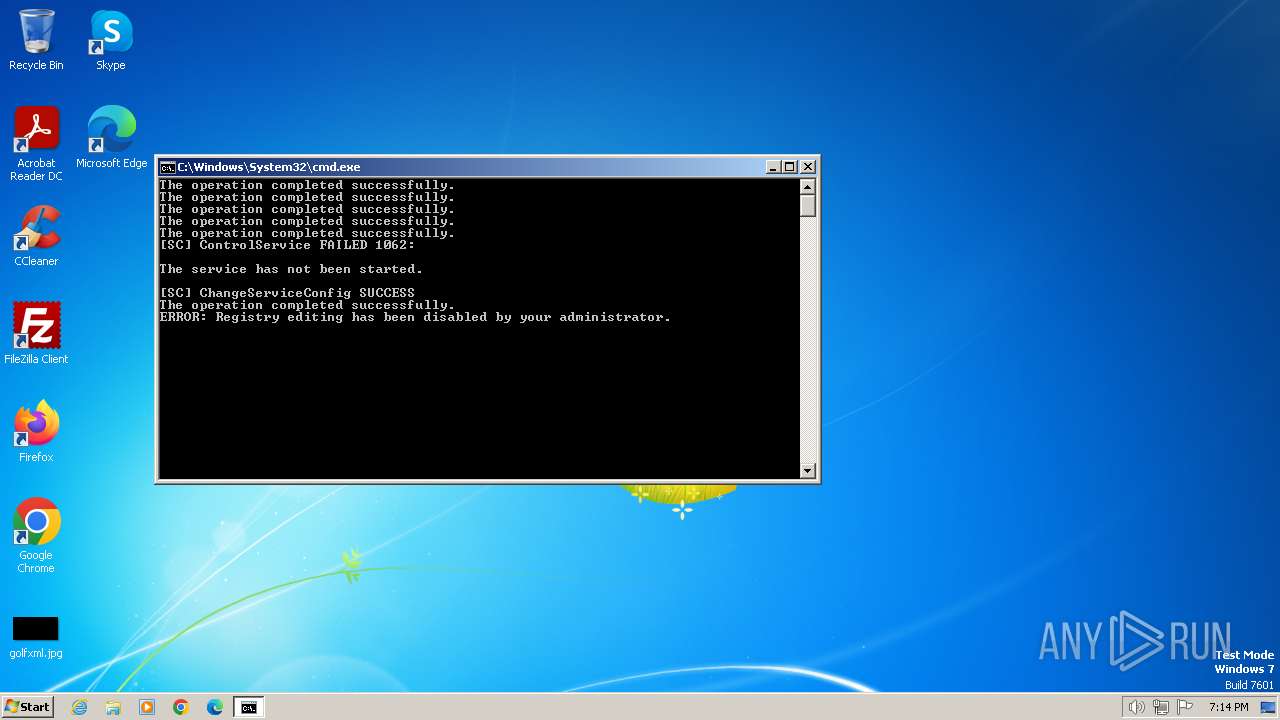
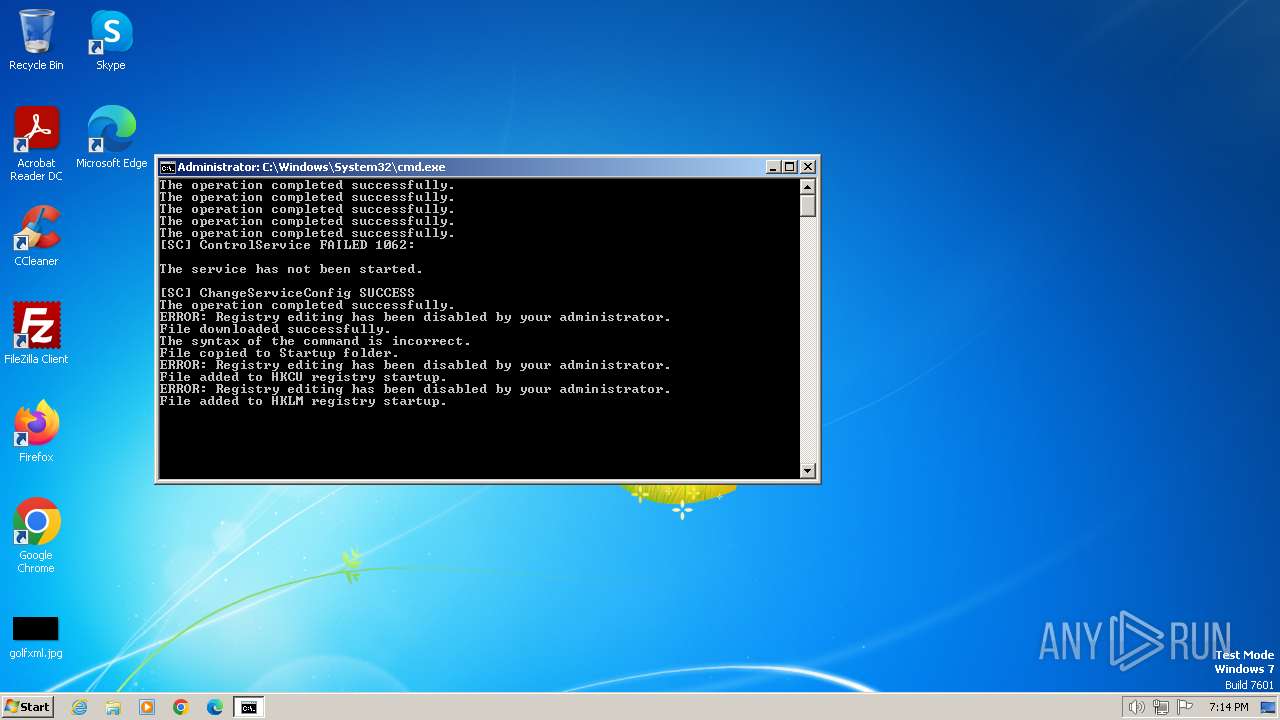
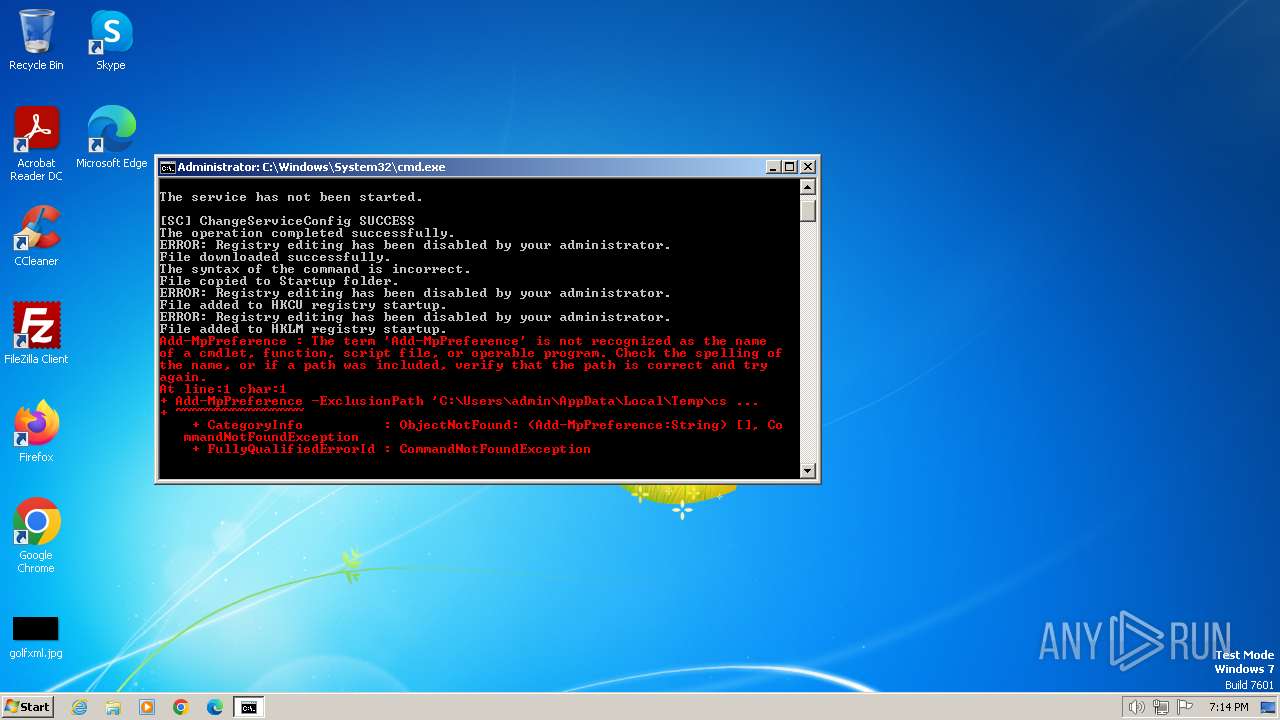
| File name: | FIXER.bat |
| Full analysis: | https://app.any.run/tasks/2d8cfce6-38af-4d43-84c6-664d1a798daa |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | July 21, 2024, 18:14:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | E9AF7ED5D74710776428005D41615075 |
| SHA1: | 9832D39FBDFF8D1F9689472BFBA835122CD81C5B |
| SHA256: | 8DEA64F33E65BFD67D8417EA7C08F36265B9383FE5C573896A9FBB708AEED3C2 |
| SSDEEP: | 96:VQI8Z08+3+0SM08k+pdzWLAjSp0GHnxGSc:VQI5L3+yyDHxGx |
MALICIOUS
Disables Windows Defender
- reg.exe (PID: 3696)
- reg.exe (PID: 3484)
- reg.exe (PID: 1980)
- reg.exe (PID: 996)
Drops the executable file immediately after the start
- powershell.exe (PID: 3476)
- csrss.exe (PID: 3088)
- WINCHECK.EXE (PID: 2760)
- ULTINJ.EXE (PID: 3116)
- WINDOWS UPDT.EXE (PID: 2796)
- csrss.exe (PID: 1756)
Starts SC.EXE for service management
- cmd.exe (PID: 1504)
Changes the autorun value in the registry
- WINCHECK.EXE (PID: 2760)
- WINDOWS UPDT.EXE (PID: 2796)
- csrss.exe (PID: 2740)
- csrss.exe (PID: 1756)
Changes the login/logoff helper path in the registry
- WINCHECK.EXE (PID: 2760)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 1504)
NjRAT is detected
- ULTINJ.EXE (PID: 3116)
- csrss.exe (PID: 1756)
Create files in the Startup directory
- csrss.exe (PID: 1756)
NANOCORE has been detected (YARA)
- WINDOWS UPDT.EXE (PID: 2796)
DARKCOMET has been detected (YARA)
- csrss.exe (PID: 2740)
NJRAT has been detected (YARA)
- csrss.exe (PID: 1756)
SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 3400)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3400)
- cmd.exe (PID: 1504)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 1504)
Starts SC.EXE for service management
- cmd.exe (PID: 1504)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1504)
Reads the Internet Settings
- cmd.exe (PID: 3400)
- wscript.exe (PID: 3428)
- powershell.exe (PID: 3476)
- csrss.exe (PID: 3088)
- WINCHECK.EXE (PID: 2760)
- powershell.exe (PID: 268)
- powershell.exe (PID: 1516)
- ULTINJ.EXE (PID: 3116)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3428)
- WINCHECK.EXE (PID: 2760)
Adds/modifies Windows certificates
- powershell.exe (PID: 3476)
The process creates files with name similar to system file names
- powershell.exe (PID: 3476)
- WINCHECK.EXE (PID: 2760)
- ULTINJ.EXE (PID: 3116)
Executable content was dropped or overwritten
- powershell.exe (PID: 3476)
- csrss.exe (PID: 3088)
- WINCHECK.EXE (PID: 2760)
- WINDOWS UPDT.EXE (PID: 2796)
- ULTINJ.EXE (PID: 3116)
- csrss.exe (PID: 1756)
The executable file from the user directory is run by the CMD process
- csrss.exe (PID: 3088)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1504)
Downloads file from URI
- powershell.exe (PID: 3476)
Reads security settings of Internet Explorer
- csrss.exe (PID: 3088)
- WINCHECK.EXE (PID: 2760)
- ULTINJ.EXE (PID: 3116)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2544)
- cmd.exe (PID: 3992)
Reads the date of Windows installation
- WINCHECK.EXE (PID: 2760)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 268)
- powershell.exe (PID: 1516)
Start notepad (likely ransomware note)
- csrss.exe (PID: 2740)
Starts itself from another location
- WINCHECK.EXE (PID: 2760)
- ULTINJ.EXE (PID: 3116)
Connects to unusual port
- WINDOWS UPDT.EXE (PID: 2796)
- csrss.exe (PID: 2740)
- csrss.exe (PID: 1756)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3428)
Executing commands from a ".bat" file
- wscript.exe (PID: 3428)
Uses NETSH.EXE to add a firewall rule or allowed programs
- csrss.exe (PID: 1756)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1504)
There is functionality for taking screenshot (YARA)
- csrss.exe (PID: 2740)
There is functionality for communication over UDP network (YARA)
- csrss.exe (PID: 2740)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3268)
- WINCHECK.EXE (PID: 2760)
- csrss.exe (PID: 3088)
- WINDOWS UPDT.EXE (PID: 2796)
- csrss.exe (PID: 2740)
- ULTINJ.EXE (PID: 3116)
- csrss.exe (PID: 1756)
Checks supported languages
- wmpnscfg.exe (PID: 3268)
- csrss.exe (PID: 3088)
- WINDOWS UPDT.EXE (PID: 2796)
- WINCHECK.EXE (PID: 2760)
- ULTINJ.EXE (PID: 3116)
- csrss.exe (PID: 2740)
- csrss.exe (PID: 1756)
Disables trace logs
- powershell.exe (PID: 3476)
Creates files or folders in the user directory
- csrss.exe (PID: 3088)
- WINDOWS UPDT.EXE (PID: 2796)
- ULTINJ.EXE (PID: 3116)
- csrss.exe (PID: 1756)
Reads the machine GUID from the registry
- WINCHECK.EXE (PID: 2760)
- WINDOWS UPDT.EXE (PID: 2796)
- ULTINJ.EXE (PID: 3116)
- csrss.exe (PID: 1756)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 268)
- powershell.exe (PID: 1516)
Creates files in the program directory
- WINDOWS UPDT.EXE (PID: 2796)
Process checks whether UAC notifications are on
- WINDOWS UPDT.EXE (PID: 2796)
Reads Environment values
- WINDOWS UPDT.EXE (PID: 2796)
- csrss.exe (PID: 1756)
UPX packer has been detected
- csrss.exe (PID: 2740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(2796) WINDOWS UPDT.EXE
BuildTime2024-07-07 19:08:34.420008
Version1.2.2.0
Mutex0408a841-44c1-40dc-87b4-2422bb58fa5d
DefaultGroupDefault
PrimaryConnectionHostjvjv2044duck33.duckdns.org
BackupConnectionHostjvjv2044duck33.duckdns.org
ConnectionPort8808
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
NjRat
(PID) Process(1756) csrss.exe
C2jvjv2044duck33.duckdns.org
Ports5552
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\0ce256616b847d6ba32935097dcc5537
Splitter|'|'|
Versionim523
Total processes
77
Monitored processes
32
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | powershell -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Local\Temp\csrss.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 996 | reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection" /v DisableBehaviorMonitoring /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Roaming\csrss.exe" "csrss.exe" ENABLE | C:\Windows\System32\netsh.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\FIXER.bat" | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1516 | powershell -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\csrss.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1756 | "C:\Users\admin\AppData\Roaming\csrss.exe" | C:\Users\admin\AppData\Roaming\csrss.exe | ULTINJ.EXE | ||||||||||||
User: admin Integrity Level: HIGH Modules
NjRat(PID) Process(1756) csrss.exe C2jvjv2044duck33.duckdns.org Ports5552 BotnetHacKed Options Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\0ce256616b847d6ba32935097dcc5537 Splitter|'|'| Versionim523 | |||||||||||||||
| 1980 | reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | sc stop WinDefend | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1062 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | sc config WinDefend start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2528 | attrib "C:\Users\admin\AppData\Roaming\WINCHECK.EXE" +s +h | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
26 459
Read events
26 202
Write events
255
Delete events
2
Modification events
| (PID) Process: | (3400) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3400) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3400) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3400) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3428) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3428) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3428) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3428) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1980) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (2580) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection |
| Operation: | write | Name: | DisableRealtimeMonitoring |
Value: 1 | |||
Executable files
8
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 3476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\02c12f1q.dfi.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ivrkuauv.dqq.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\v1nrqpaf.fwo.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2796 | WINDOWS UPDT.EXE | C:\Users\admin\AppData\Roaming\90059C37-1320-41A4-B58D-2B75A9850D2F\run.dat | binary | |
MD5:E7F111F3000BCEDBB7A9CC2408491582 | SHA256:C728465351D1D9A7940177467706642F2D9D1CA5B4A1BFA8E905835FDF520F07 | |||
| 268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\e0dbw5va.wvc.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1756 | csrss.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0ce256616b847d6ba32935097dcc5537.exe | executable | |
MD5:FDBDBBDD177068BE5407B463333646BC | SHA256:9D276C5382BD697BF7AE23831ADE6AA6DB48874472865DB34DCFF66BC1108004 | |||
| 1516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\neqr3kz0.co0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2796 | WINDOWS UPDT.EXE | C:\Program Files\TCP Monitor\tcpmon.exe | executable | |
MD5:15C30B1CA1E7FF0A779C350A19925B94 | SHA256:B7358F8AFF742EB85C89D1B7CF57DB1F0842DAB6E576AE68C959522EA6CB01B6 | |||
| 3088 | csrss.exe | C:\Users\admin\AppData\Roaming\WINCHECK.EXE | executable | |
MD5:C018FE852FFA46A996C7A742E71B1745 | SHA256:73977EED3E647ABB02D8C53FD758E2725E78E545643BC01C4002044921A49FA2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
16
DNS requests
11
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.32.238.144:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3476 | powershell.exe | 205.196.123.11:443 | download1323.mediafire.com | MEDIAFIRE | US | unknown |
2740 | csrss.exe | 78.177.68.243:1604 | jvjv2044duck33.duckdns.org | Turk Telekom | TR | unknown |
2796 | WINDOWS UPDT.EXE | 78.177.68.243:8808 | jvjv2044duck33.duckdns.org | Turk Telekom | TR | unknown |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 23.32.238.144:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
download1323.mediafire.com |
| whitelisted |
jvjv2044duck33.duckdns.org |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2796 | WINDOWS UPDT.EXE | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2796 | WINDOWS UPDT.EXE | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2796 | WINDOWS UPDT.EXE | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2796 | WINDOWS UPDT.EXE | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2796 | WINDOWS UPDT.EXE | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
csrss.exe | C:\Users\admin\AppData\Roaming\ULTINJ.EXE |
csrss.exe | C:\Users\admin\AppData\Roaming\WINCHECK.EXE |
csrss.exe | C:\Users\admin\AppData\Roaming\WINDOWS UPDT.EXE |