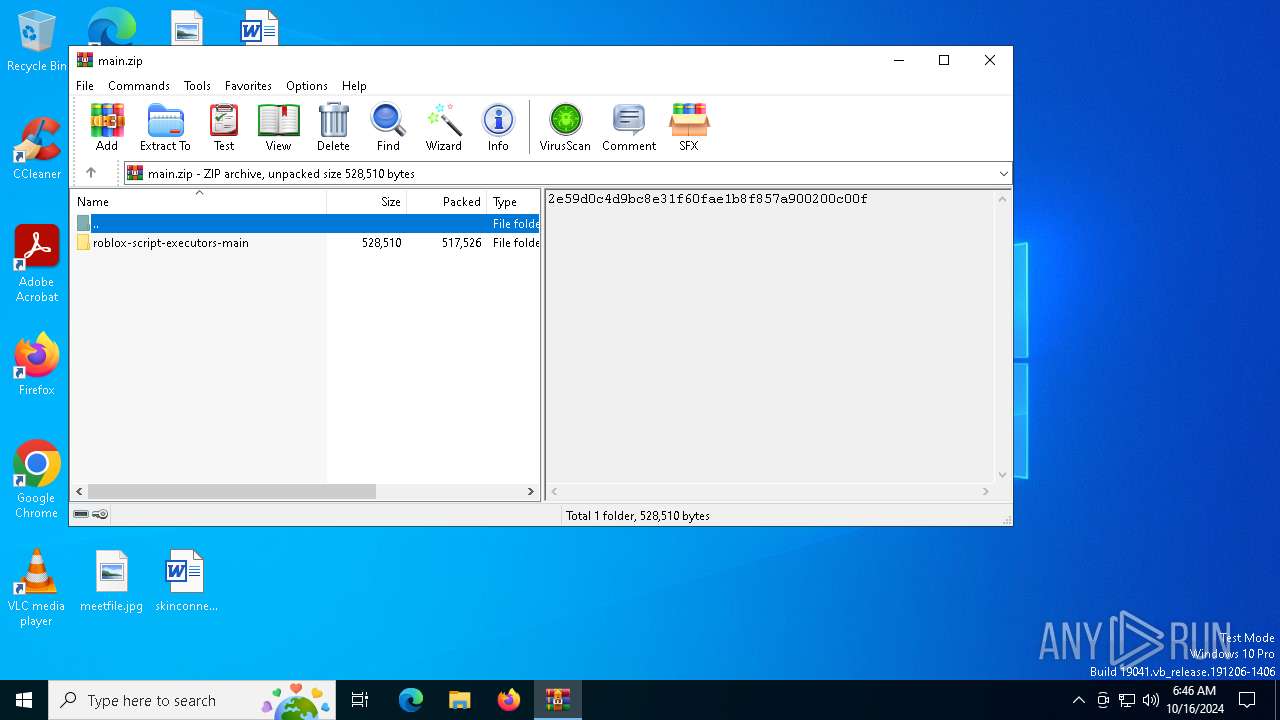
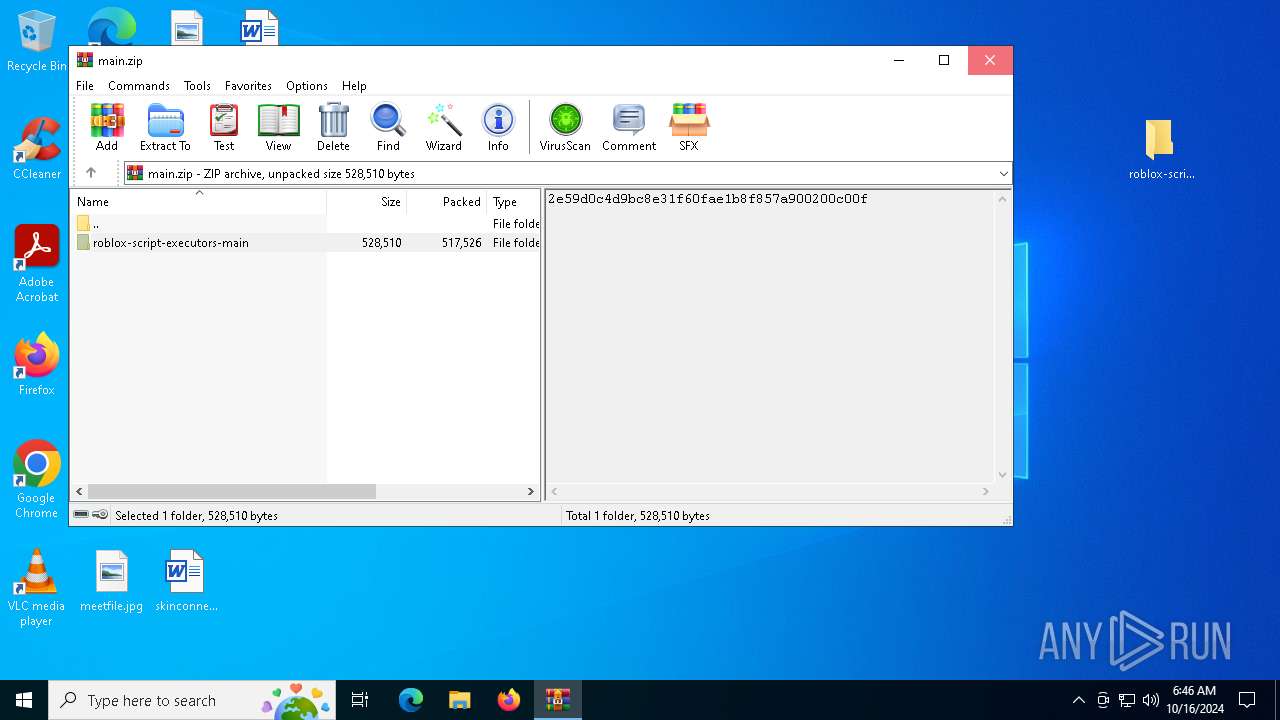
| download: | /WeLoveEmre/roblox-script-executors/archive/refs/heads/main.zip |
| Full analysis: | https://app.any.run/tasks/9d632d73-4498-402a-bb45-fe18626d0ba3 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 16, 2024, 06:46:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
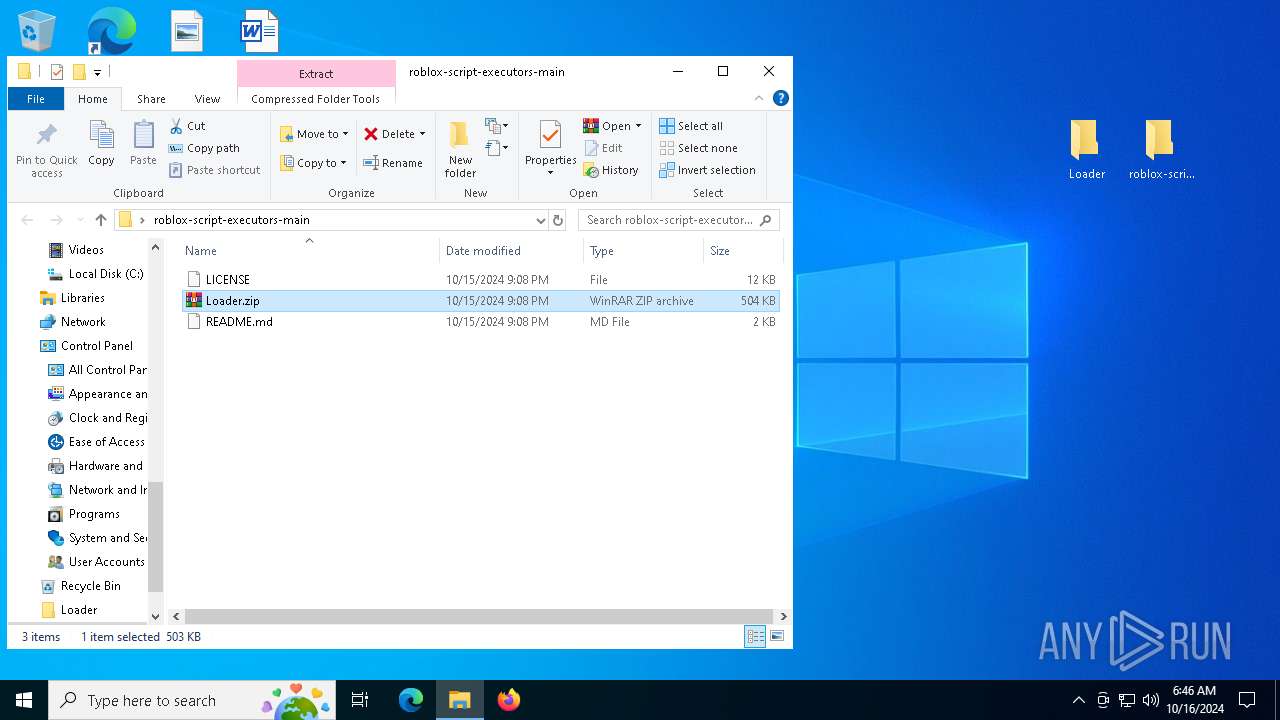
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 3A94B7D1C80DD95AD89D7256CE366987 |
| SHA1: | C195789114D4C752CEA00E995B95217A1C14FBF9 |
| SHA256: | 8DC179D69D5D762DAD8A1251FB0FB33F99F174C2B69064FABD96262816041F40 |
| SSDEEP: | 24576:X42aJzClr9ys9ZU6OrvA13yIYFwkx/WYveb47DHVncxI0E32B7rXACI:X42aJzClr9ys9G6OrvAZyIYFwkx/WYvP |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
- aspnet_regiis.exe (PID: 2224)
Connects to the CnC server
- svchost.exe (PID: 2172)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3128)
- WinRAR.exe (PID: 6176)
Executable content was dropped or overwritten
- Loader.exe (PID: 7088)
Contacting a server suspected of hosting an CnC
- aspnet_regiis.exe (PID: 2224)
- svchost.exe (PID: 2172)
INFO
Manual execution by a user
- Loader.exe (PID: 7088)
- WinRAR.exe (PID: 6176)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:15 14:08:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | roblox-script-executors-main/ |
Total processes
131
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe | Loader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regiis.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3128 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6176 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\roblox-script-executors-main\Loader.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
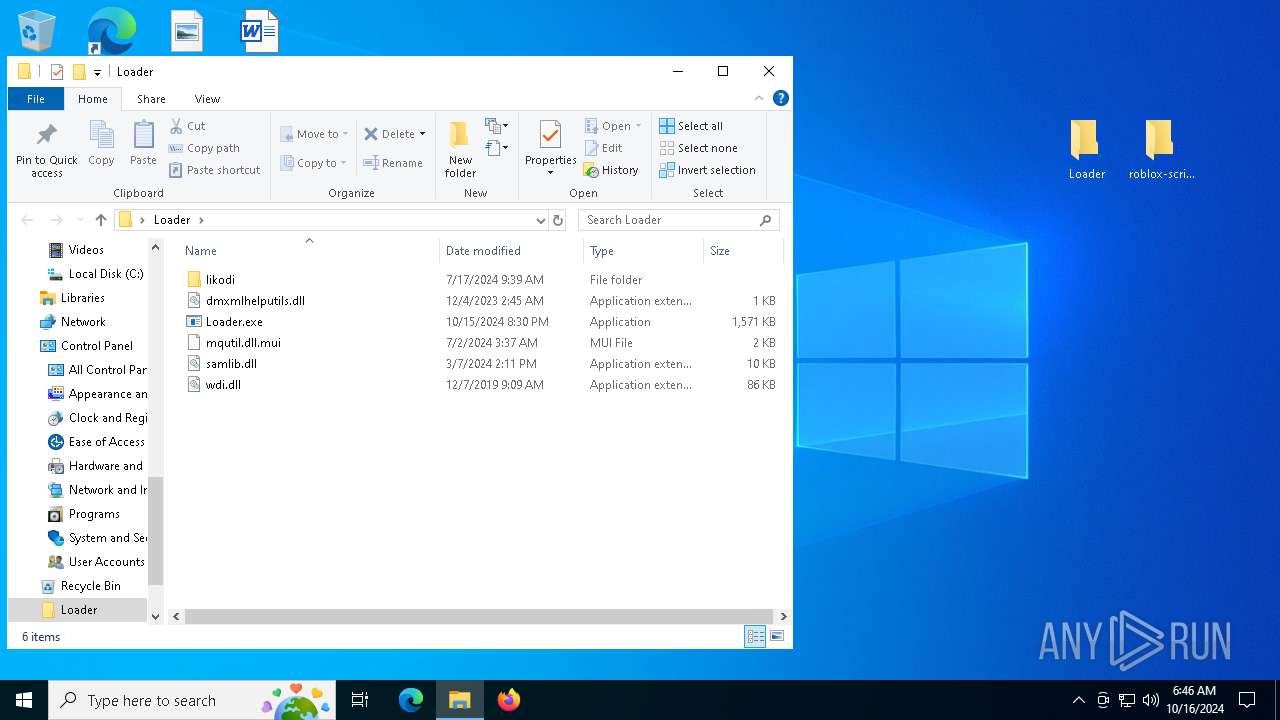
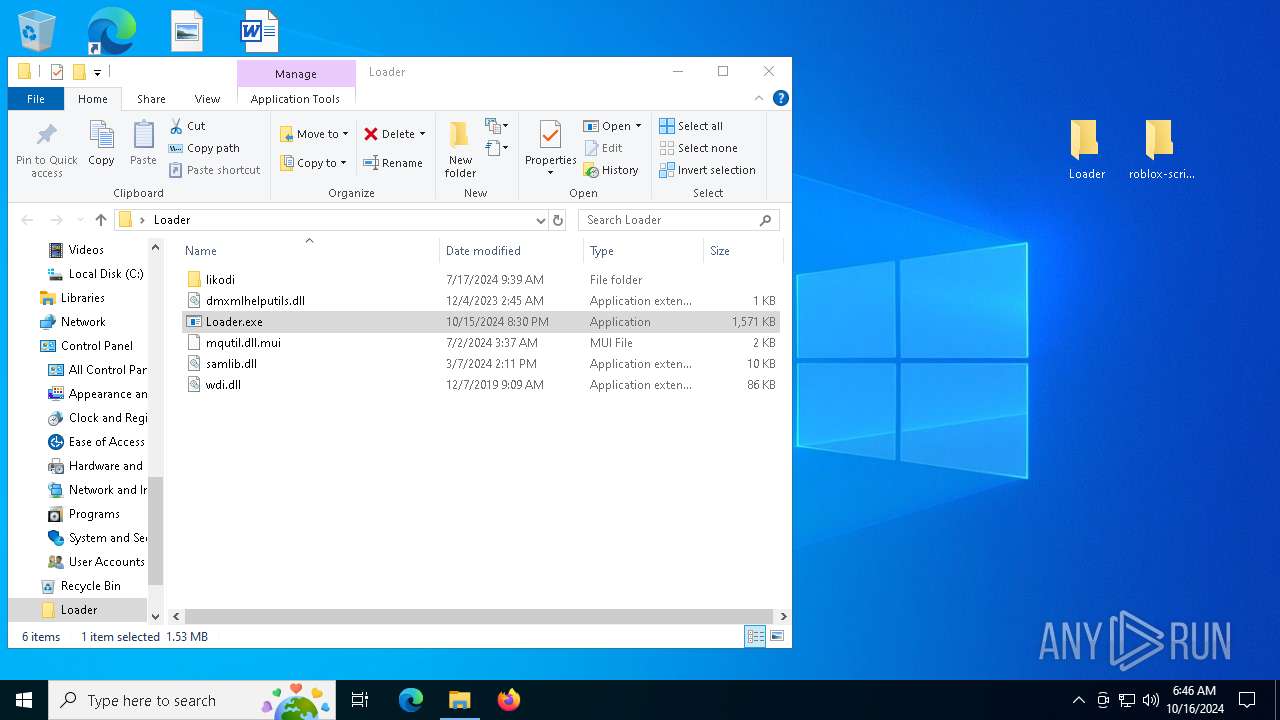
| 7088 | "C:\Users\admin\Desktop\Loader\Loader.exe" | C:\Users\admin\Desktop\Loader\Loader.exe | explorer.exe | ||||||||||||
User: admin Company: learn integrate computer Integrity Level: MEDIUM Description: connect database manage Exit code: 0 Version: 9.1.4.5 Modules
| |||||||||||||||
| 7156 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 271
Read events
3 237
Write events
34
Delete events
0
Modification events
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\main.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
4
Suspicious files
7
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6176.49755\Loader\likodi\SmiEngine.dll.mui | binary | |
MD5:A0DB1F60834E4CC834D87CE05449E86D | SHA256:0D8F35E8BDB5D7B9E705745C3D53E5AD009AF47ECEC5D05C73AE7196E2944CA2 | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6176.49755\Loader\mqutil.dll.mui | binary | |
MD5:CB3A5F54D475674A55D0A326A1CB1124 | SHA256:5A23C3E2186AF35842BE09ED51B3E073685B0C812E2CE671F084B38F5E894751 | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6176.49755\Loader\likodi\wfascim.dll.mui | binary | |
MD5:6DD6DCEF7B35588FE7F1EB40F6EB3027 | SHA256:329DFD52A5C9E01EA98625662241FCCC11E5F49074CFA7E429B6426245FC4BD5 | |||
| 3128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3128.48935\roblox-script-executors-main\Loader.zip | compressed | |
MD5:BE0DBA288940D0B94119CEDE7CDDBBD5 | SHA256:8ADE5A160413DE8BF618C06BA65E184FF7402AE41E6164D540BD27E5E7EC8EFD | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6176.49755\Loader\likodi\NotificationController.dll.mui | executable | |
MD5:5A940DB75A80C7571CC221CF3870EF78 | SHA256:D3E15411A49C52B69D00EA4C32A3EBA6EADB26DA7B7F294E90C75AA7D33F210F | |||
| 3128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3128.48935\roblox-script-executors-main\LICENSE | text | |
MD5:86D3F3A95C324C9479BD8986968F4327 | SHA256:C71D239DF91726FC519C6EB72D318EC65820627232B2F796219E87DCF35D0AB4 | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6176.49755\Loader\wdi.dll | executable | |
MD5:7D326B235AB064FF70376F1D015CC084 | SHA256:404DDA0BDF9A6C1C61653CF7E965F504B3A3A3B662F88C906AAA19A9C3DF160C | |||
| 7088 | Loader.exe | C:\Users\admin\AppData\Roaming\msvcp110.dll | executable | |
MD5:3D186BD3EF4BE6DEDAB38FAAEA8B5850 | SHA256:C5AFD252A3F1805A8D7A33FD58B8EDBF9C4A0A1867ED16BF9DFD12EA86EB7D6D | |||
| 6176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6176.49755\Loader\dmxmlhelputils.dll | binary | |
MD5:9ABD95D760A752257BCB7F5EE3C14008 | SHA256:D9050E97477CFE7BE44992A505C2CDAD8F0F43A3C0BF0E1E1A3D1F175D92AC51 | |||
| 3128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3128.48935\roblox-script-executors-main\README.md | text | |
MD5:82A7048A304EB667E630A19A7A07E5B9 | SHA256:2D209CD57CAA97D3D0FBD918CB45D31B85534D21E1D32B318CDF243E897A84BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
8
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1764 | RUXIMICS.exe | GET | 200 | 80.67.82.89:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 80.67.82.89:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 80.67.82.89:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1764 | RUXIMICS.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1764 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 23.53.243.4:443 | www.bing.com | Akamai International B.V. | US | whitelisted |
— | — | 80.67.82.89:80 | crl.microsoft.com | Akamai International B.V. | CH | whitelisted |
1764 | RUXIMICS.exe | 80.67.82.89:80 | crl.microsoft.com | Akamai International B.V. | CH | whitelisted |
— | — | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1764 | RUXIMICS.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
passimovrt.cfd |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (passimovrt .cfd) |
2224 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |
2224 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |
2224 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |
2224 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |
2224 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |
2224 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |