| File name: | avira.dll |
| Full analysis: | https://app.any.run/tasks/bd984337-0f81-4f74-881f-734296304981 |
| Verdict: | Malicious activity |
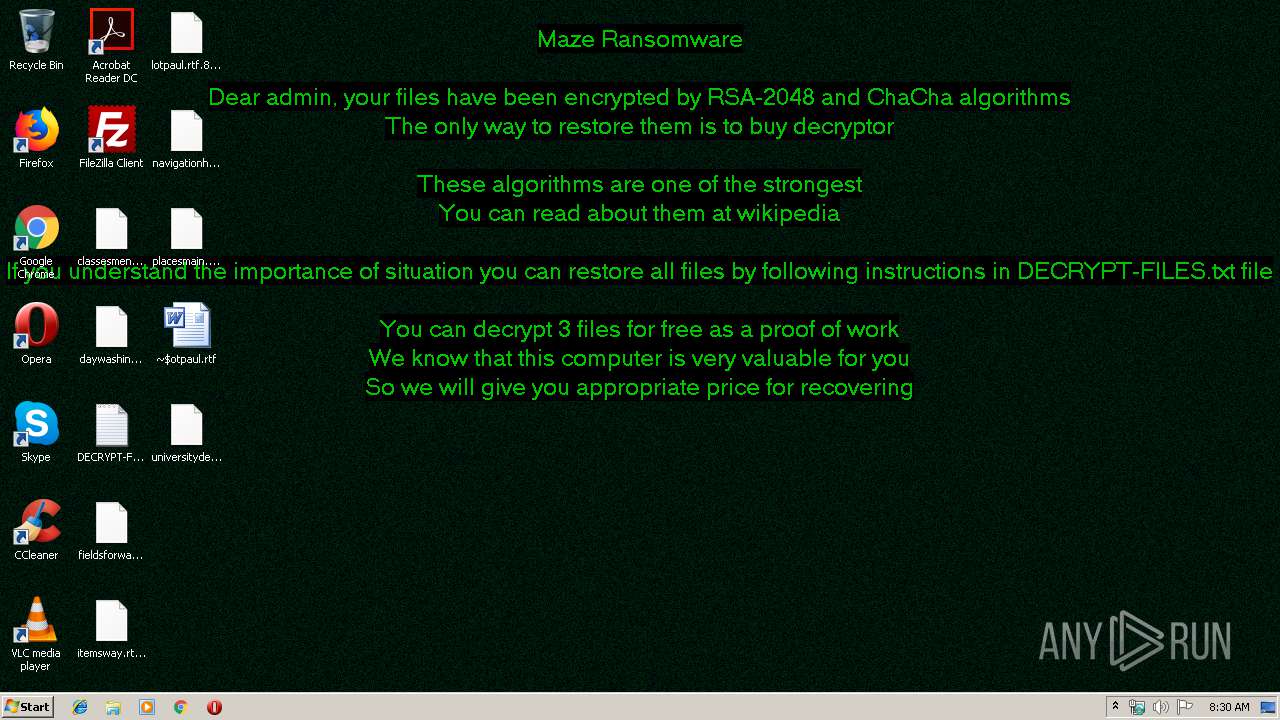
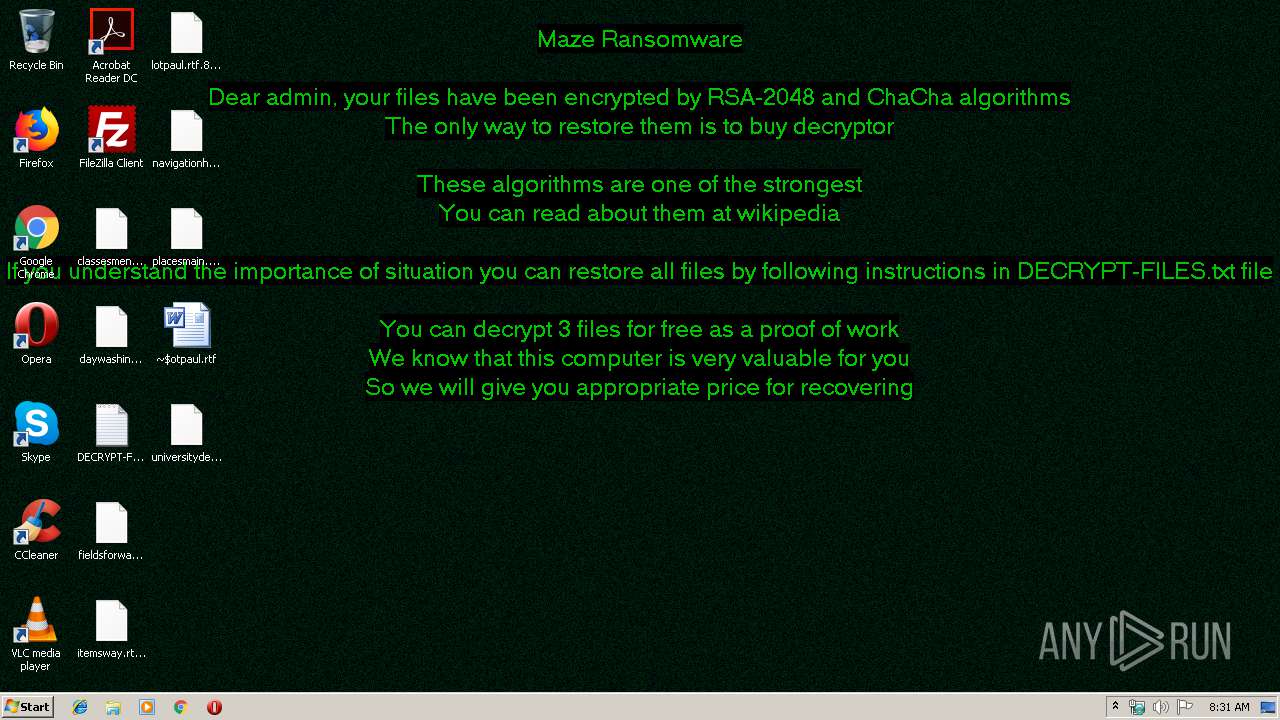
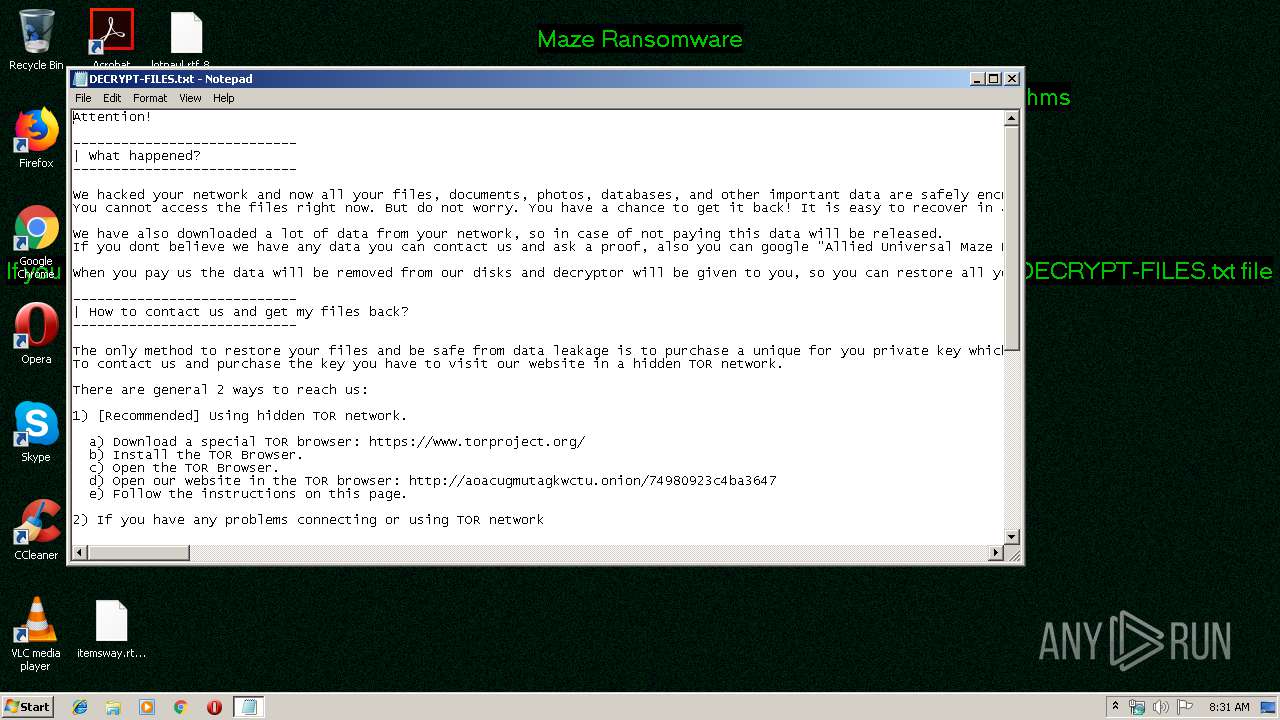
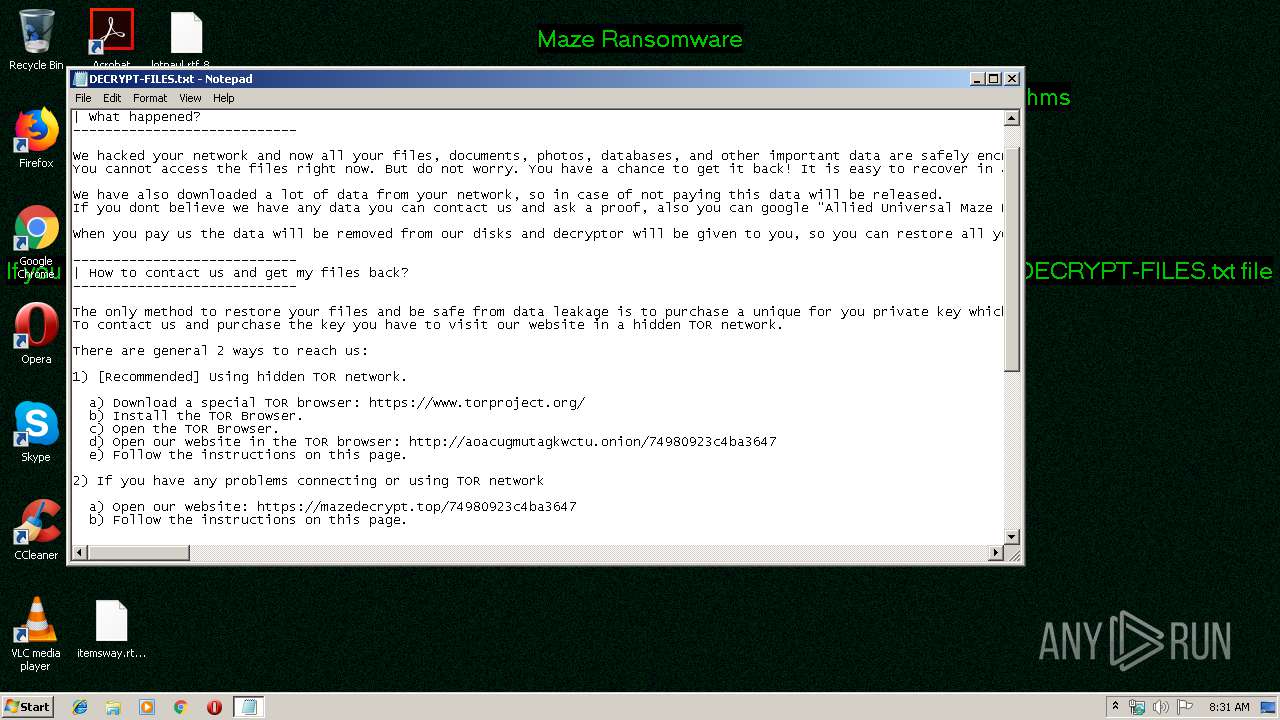
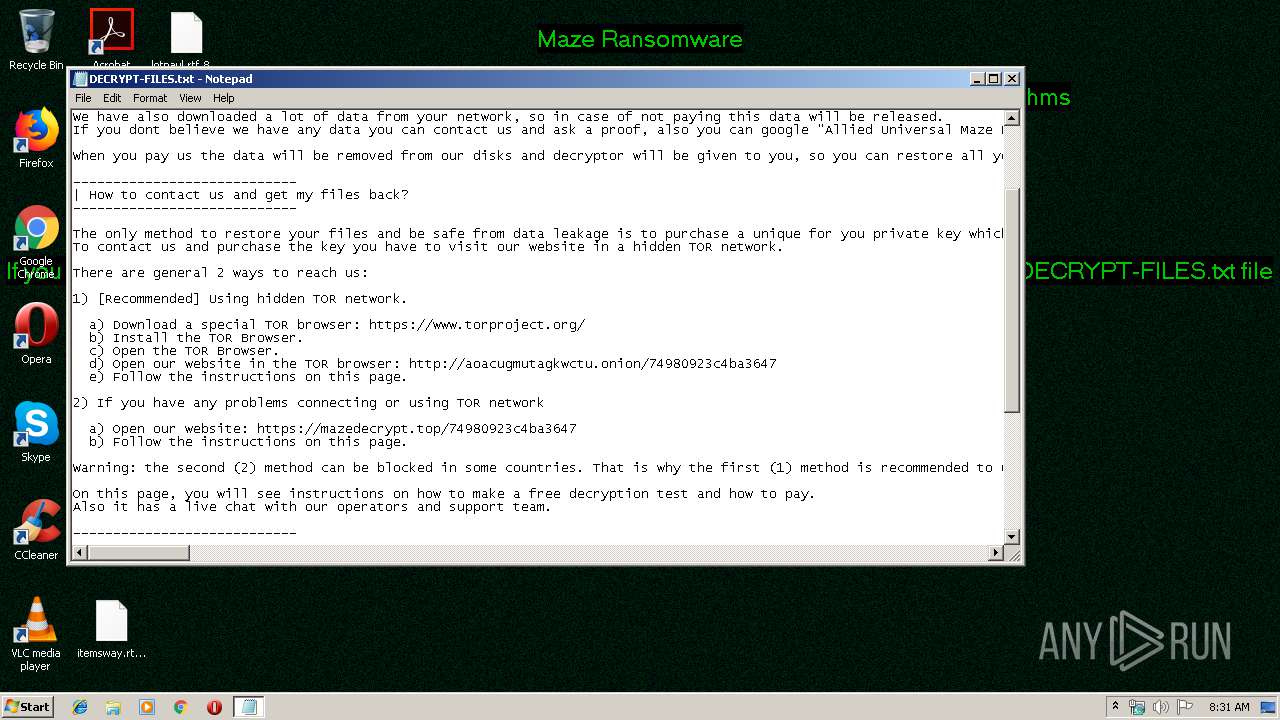
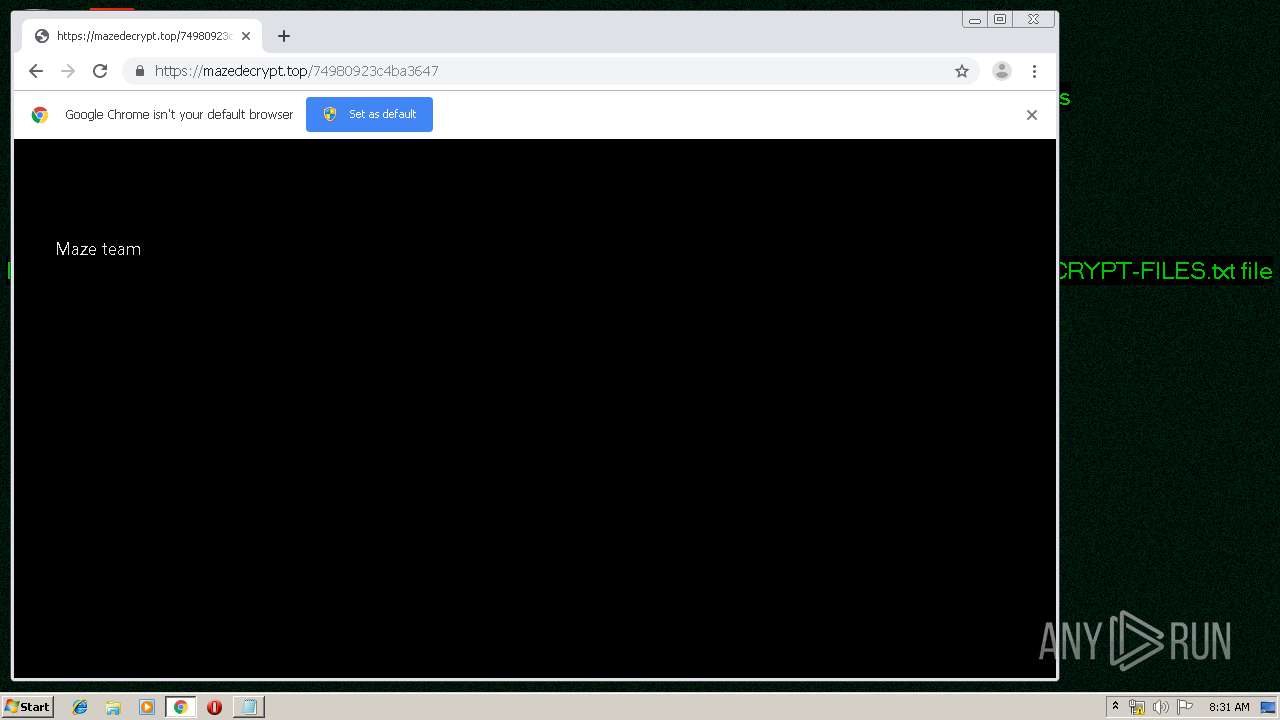
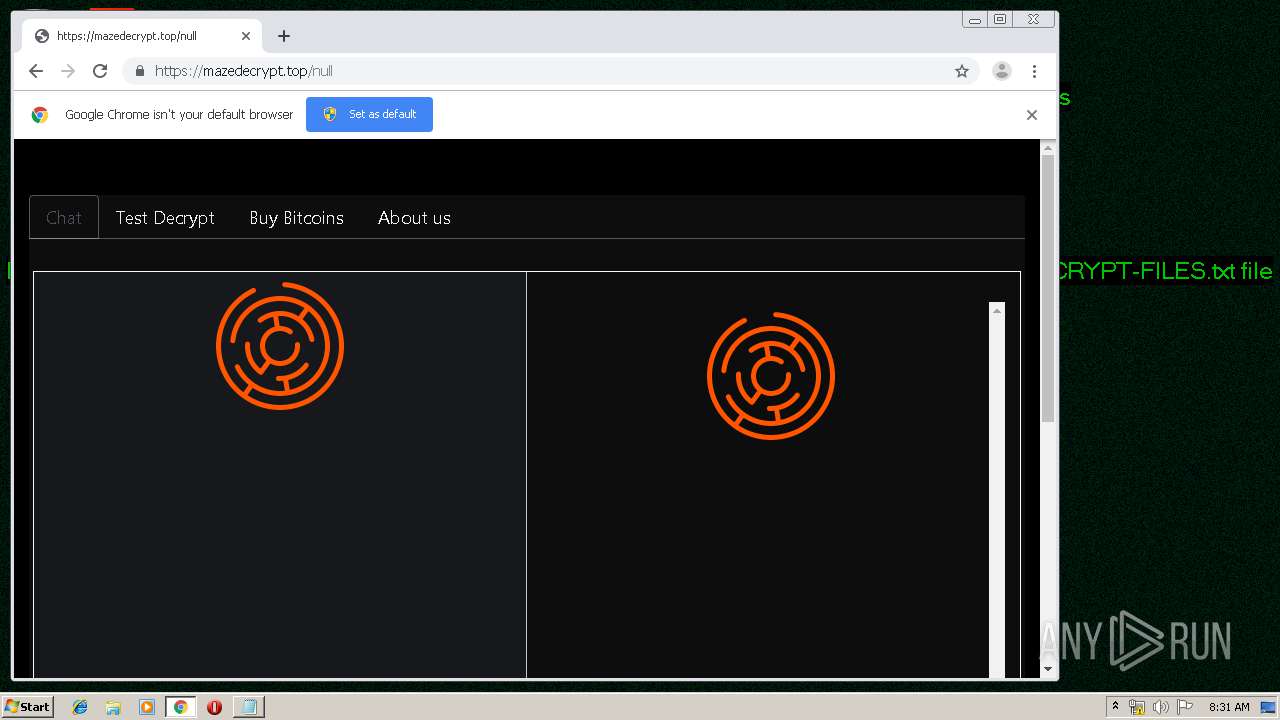
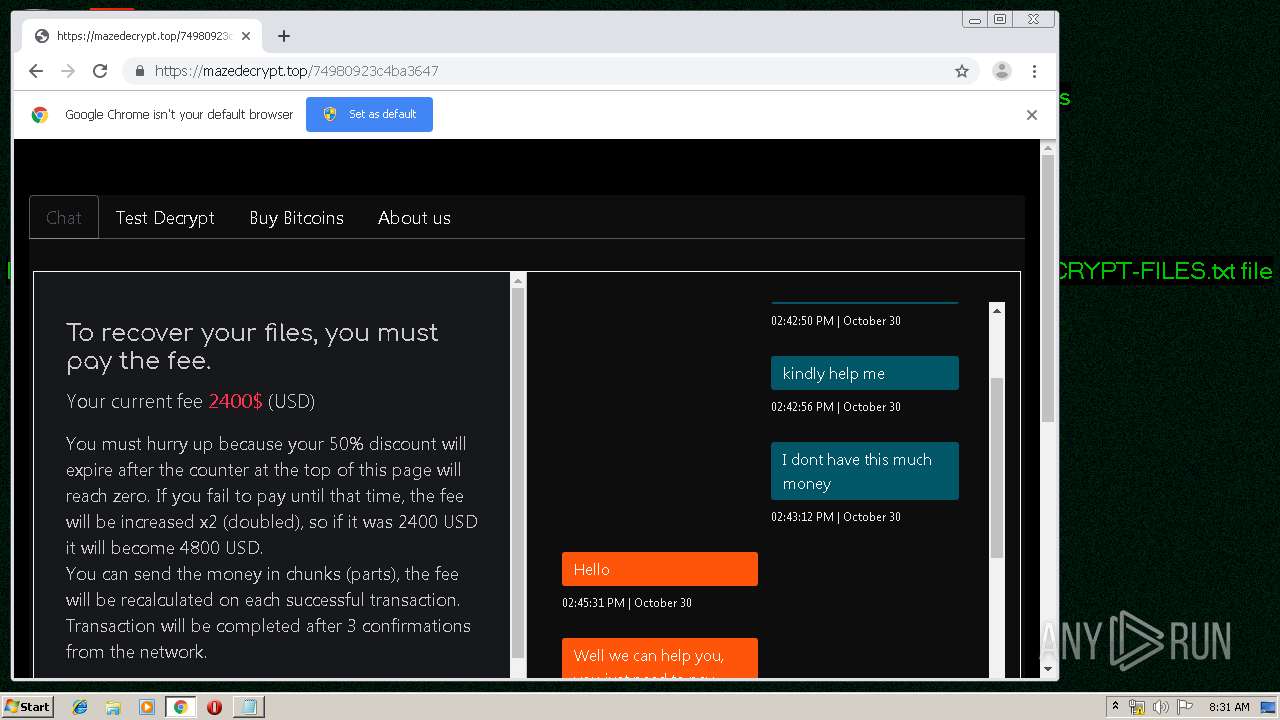
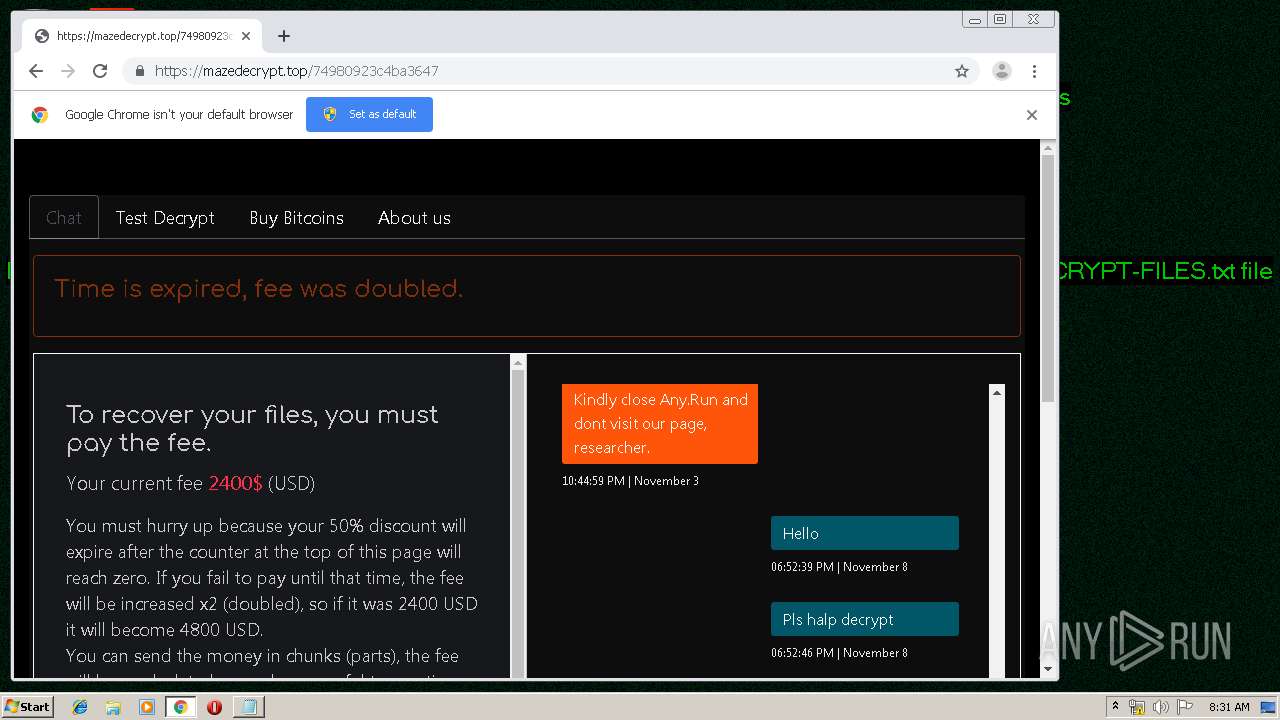
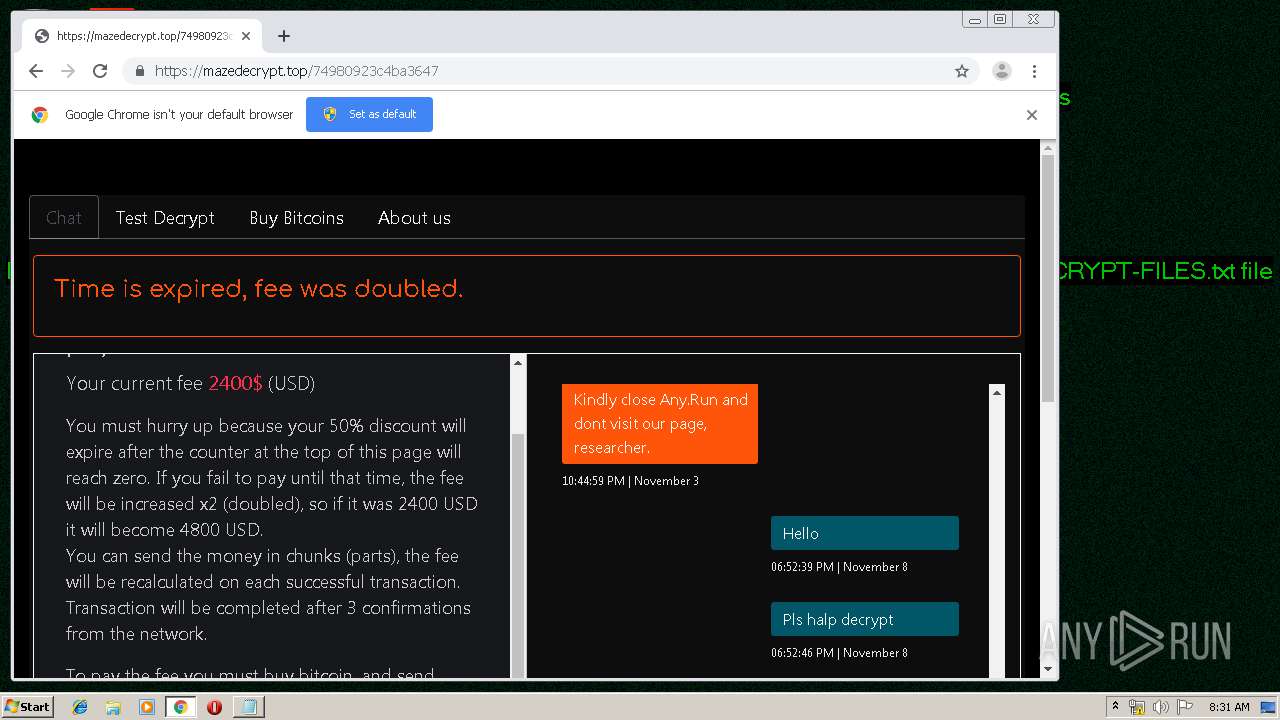
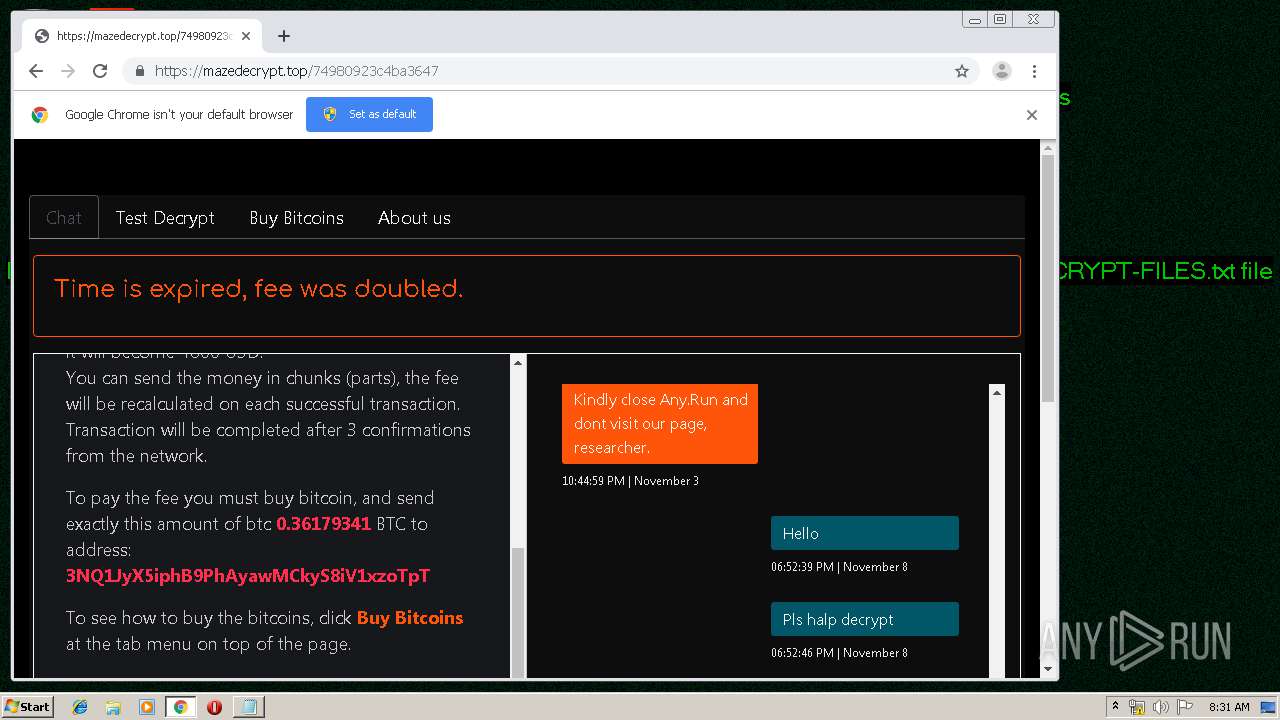
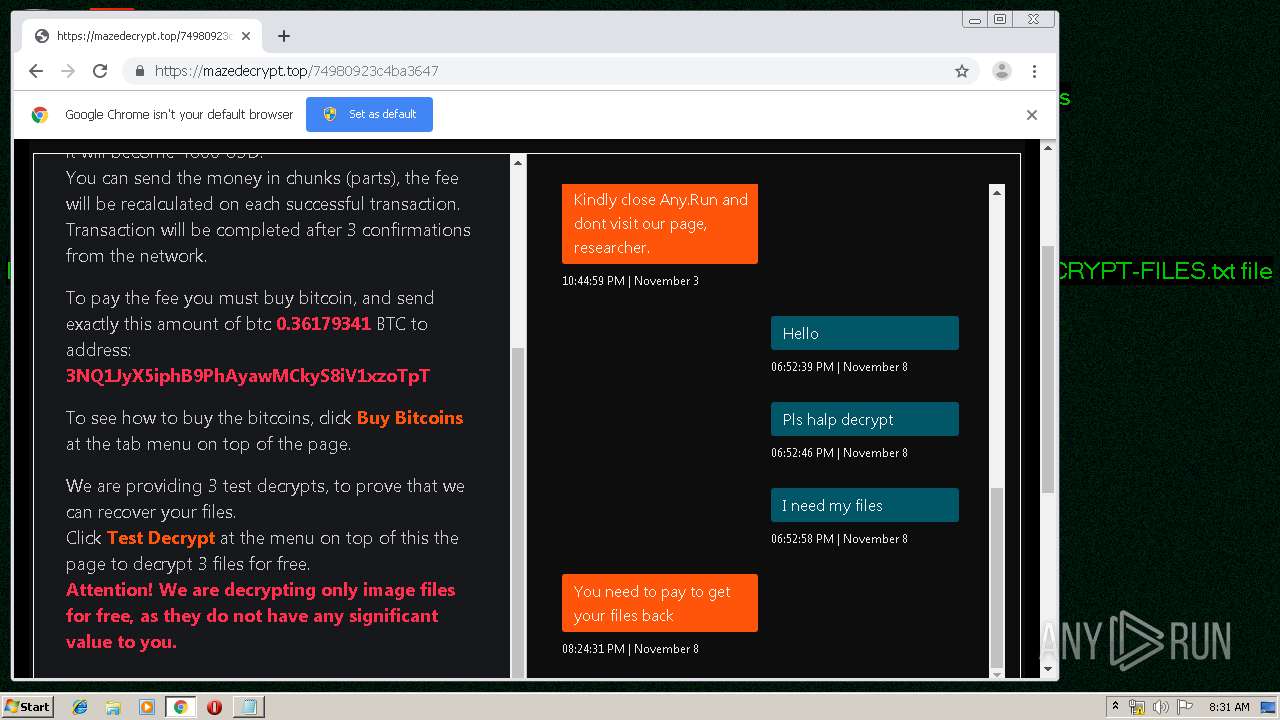
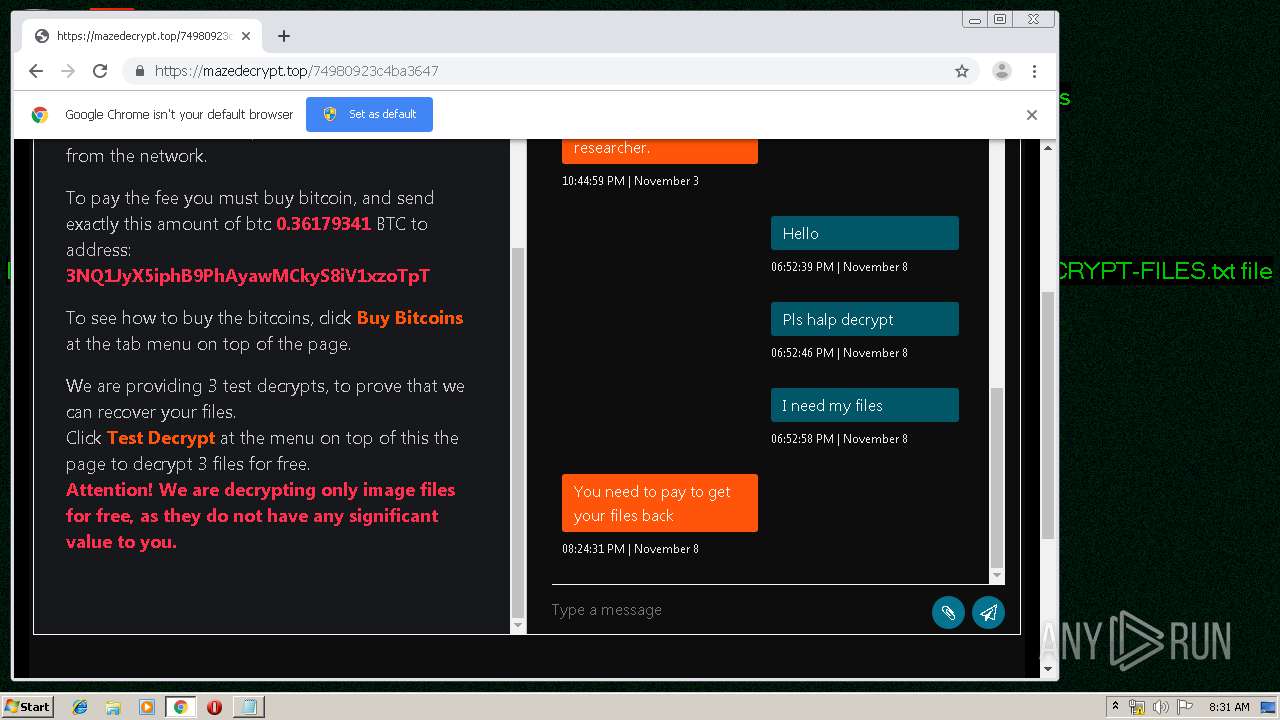
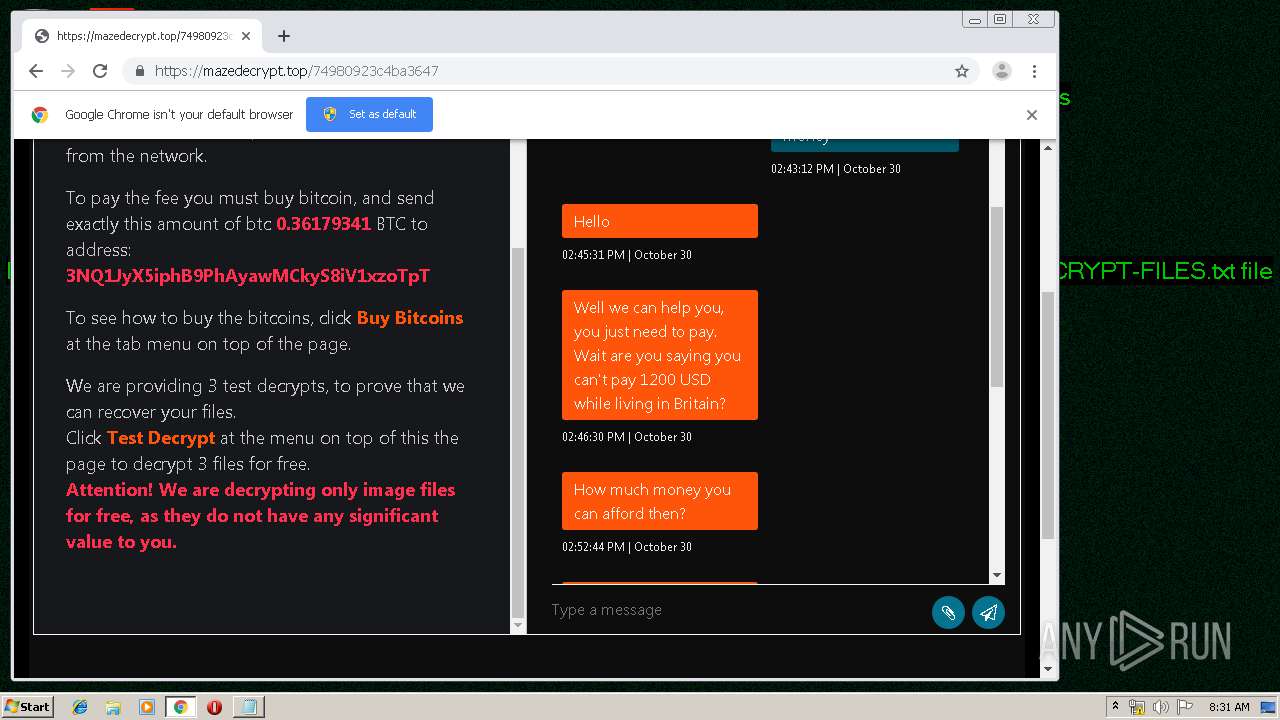
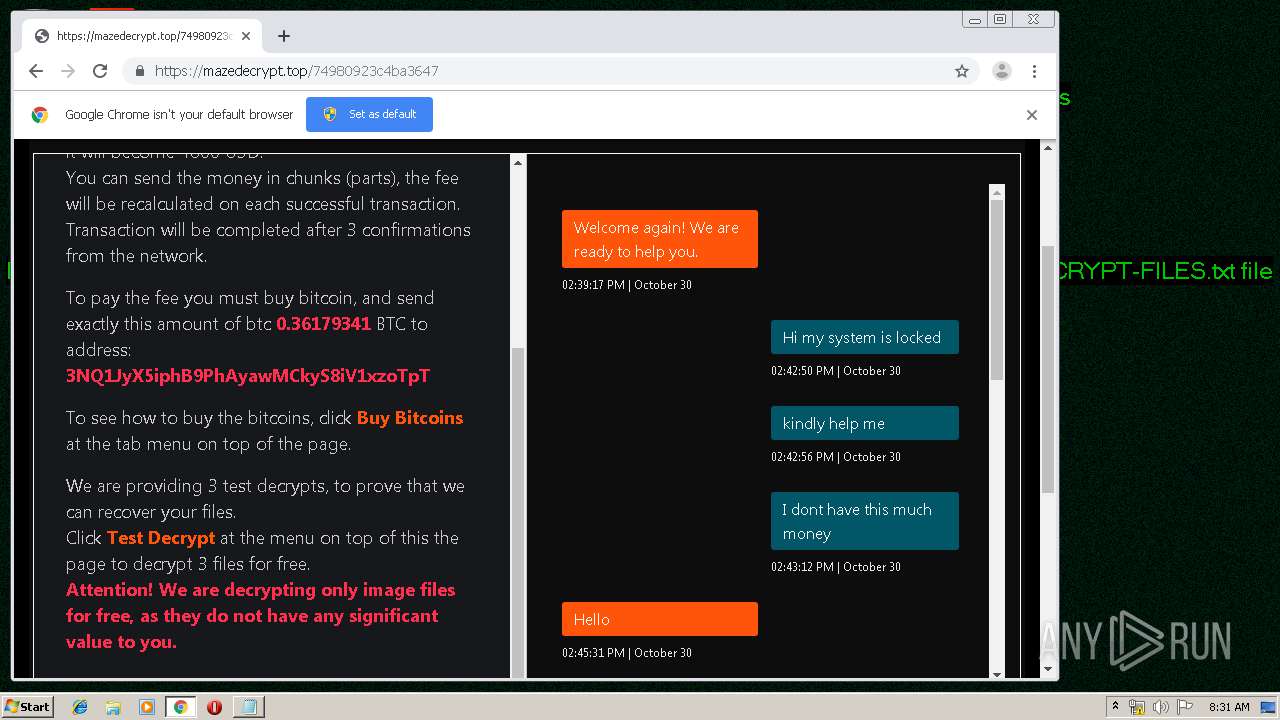
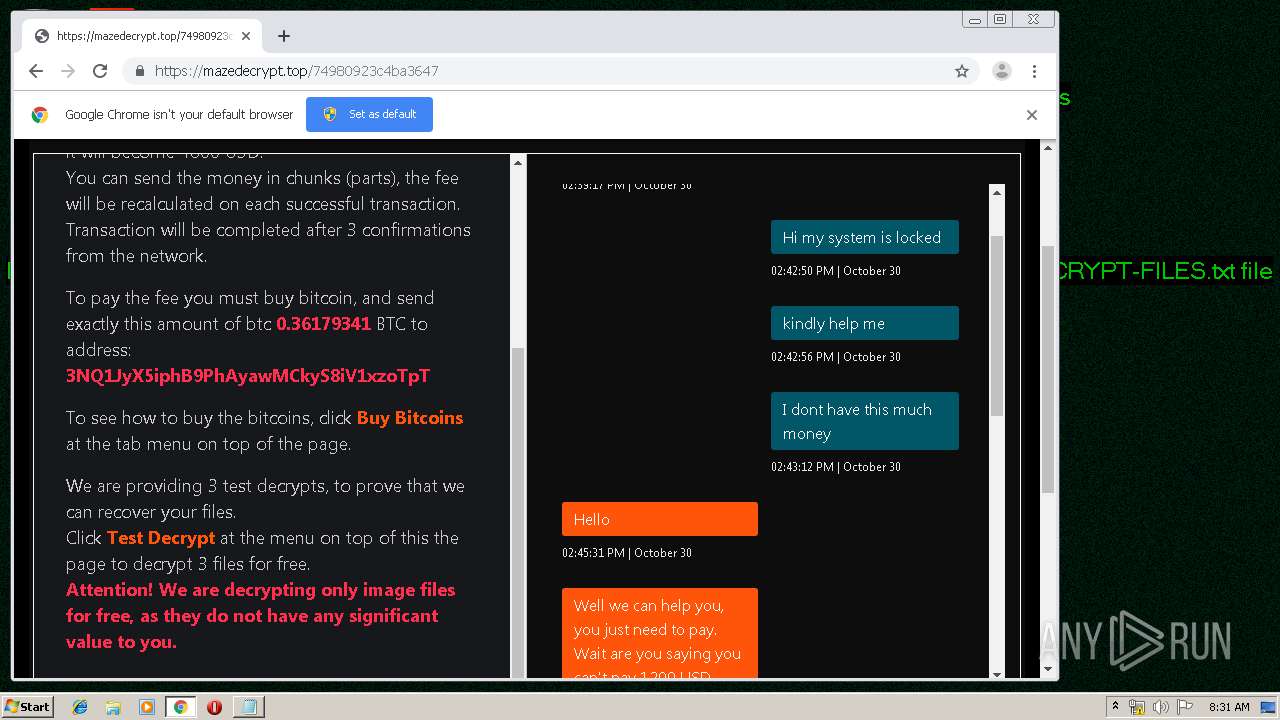
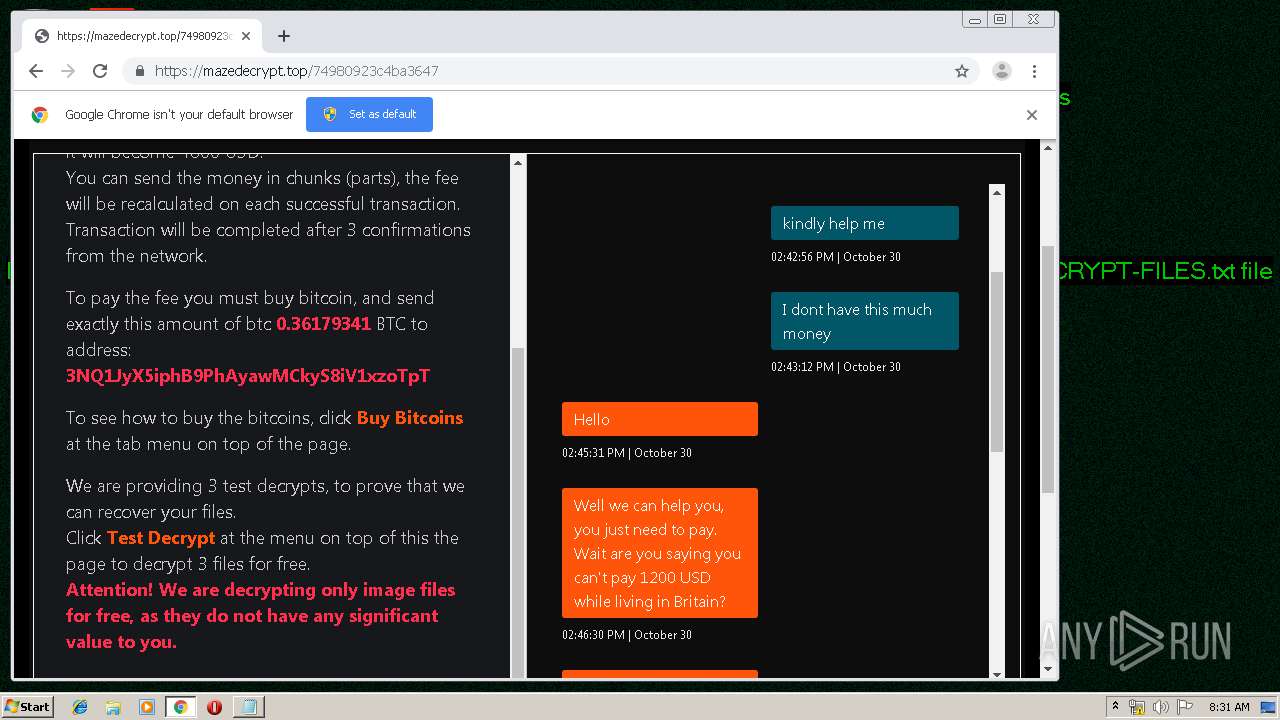
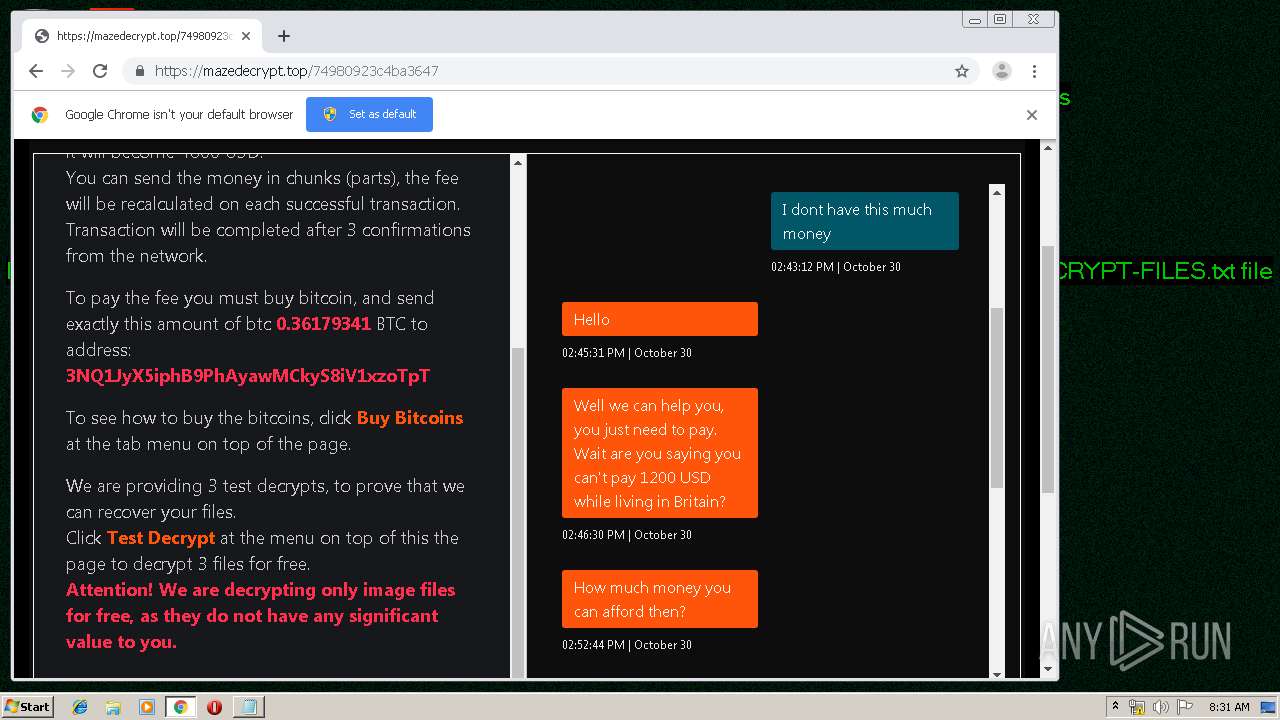
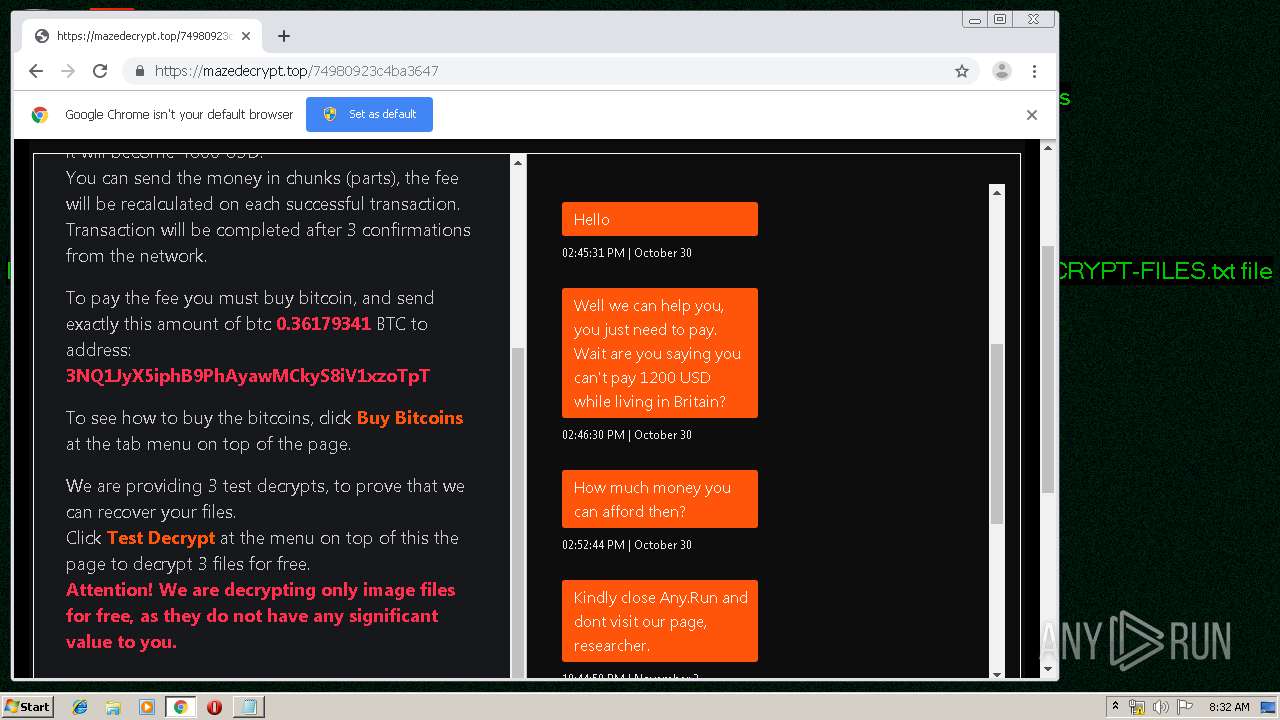
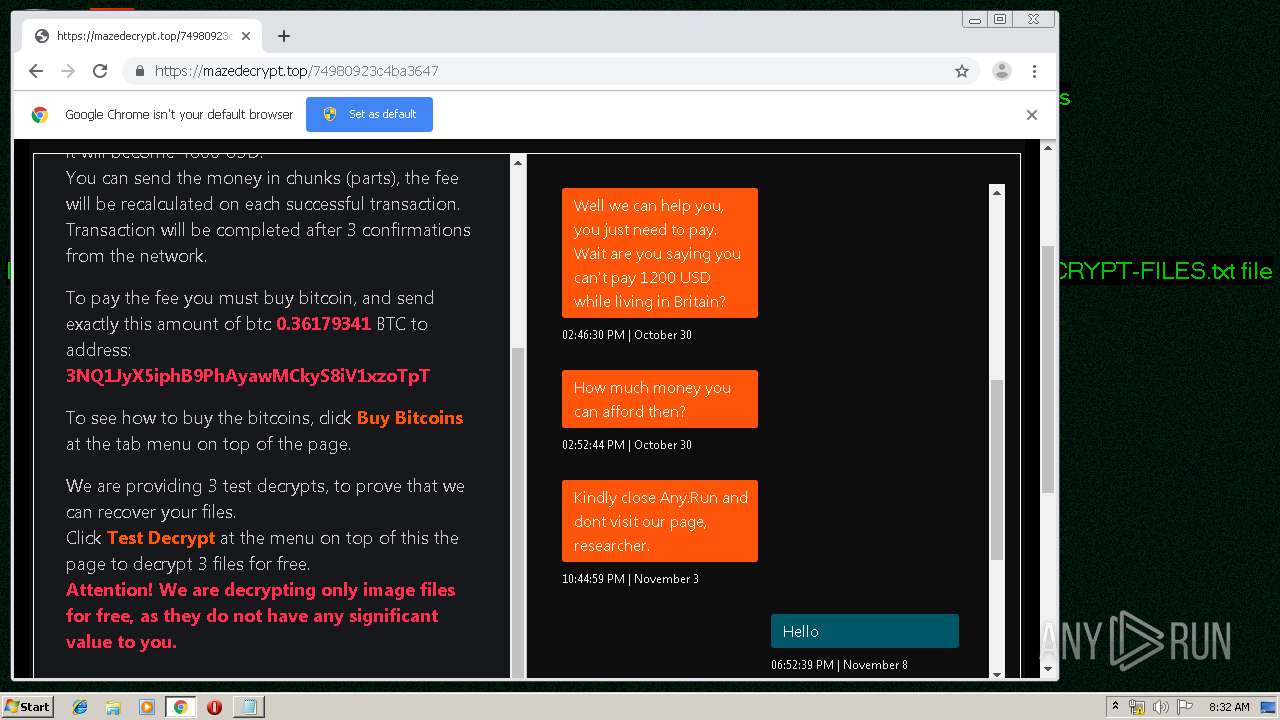
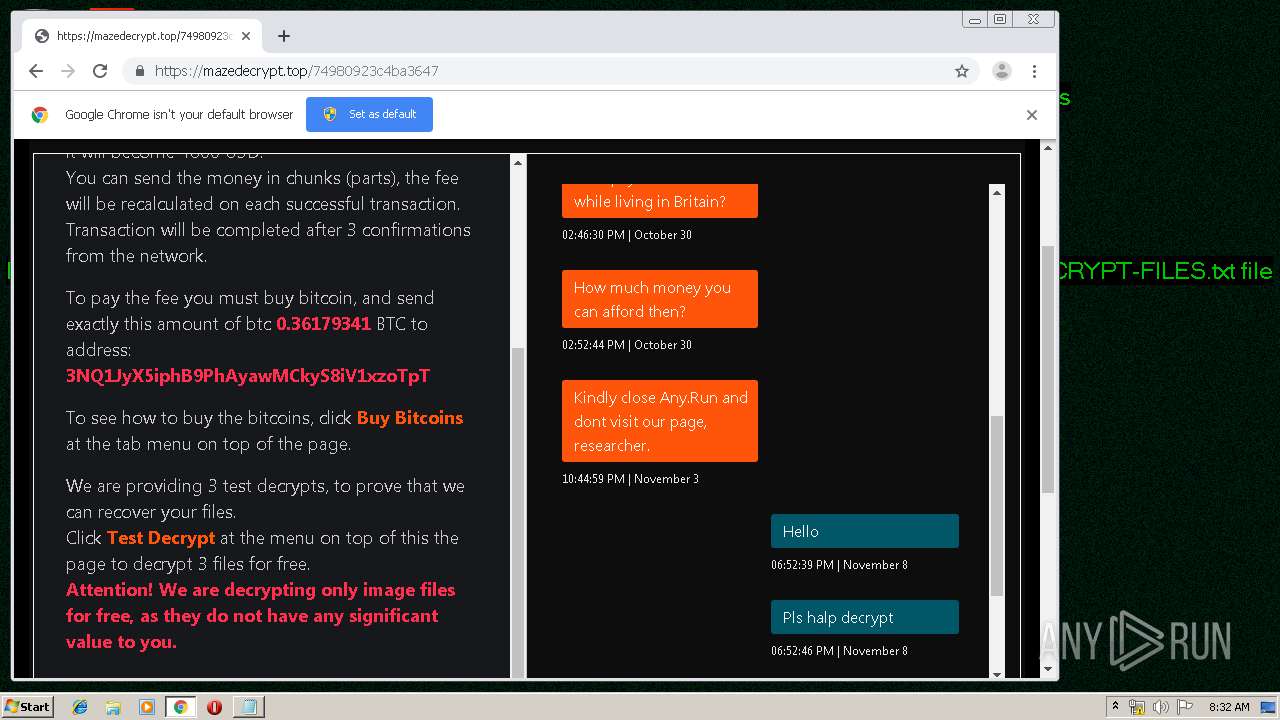
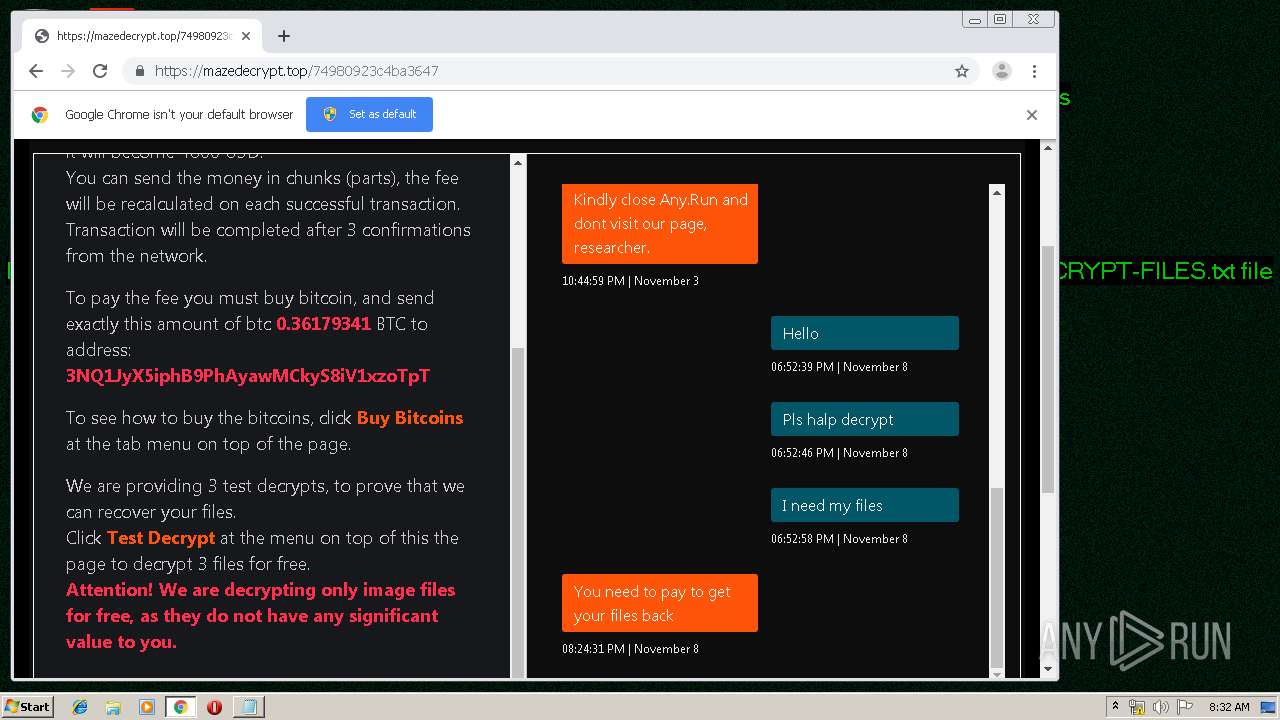
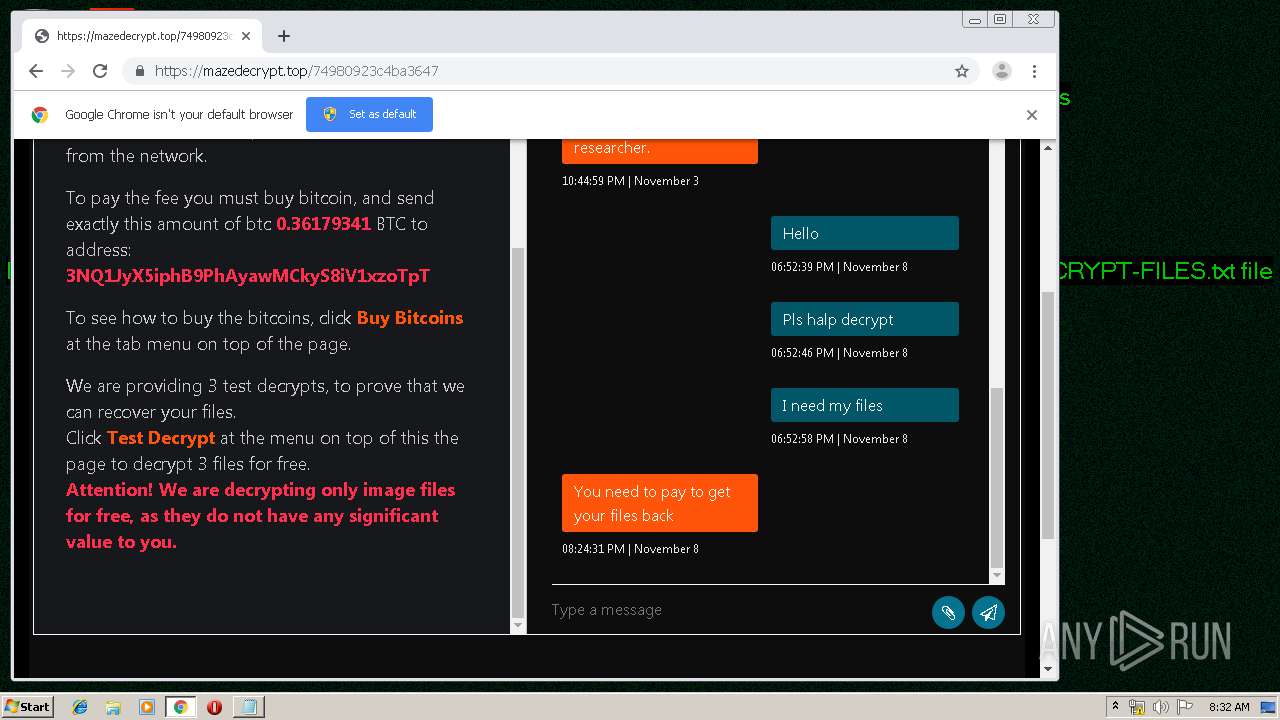
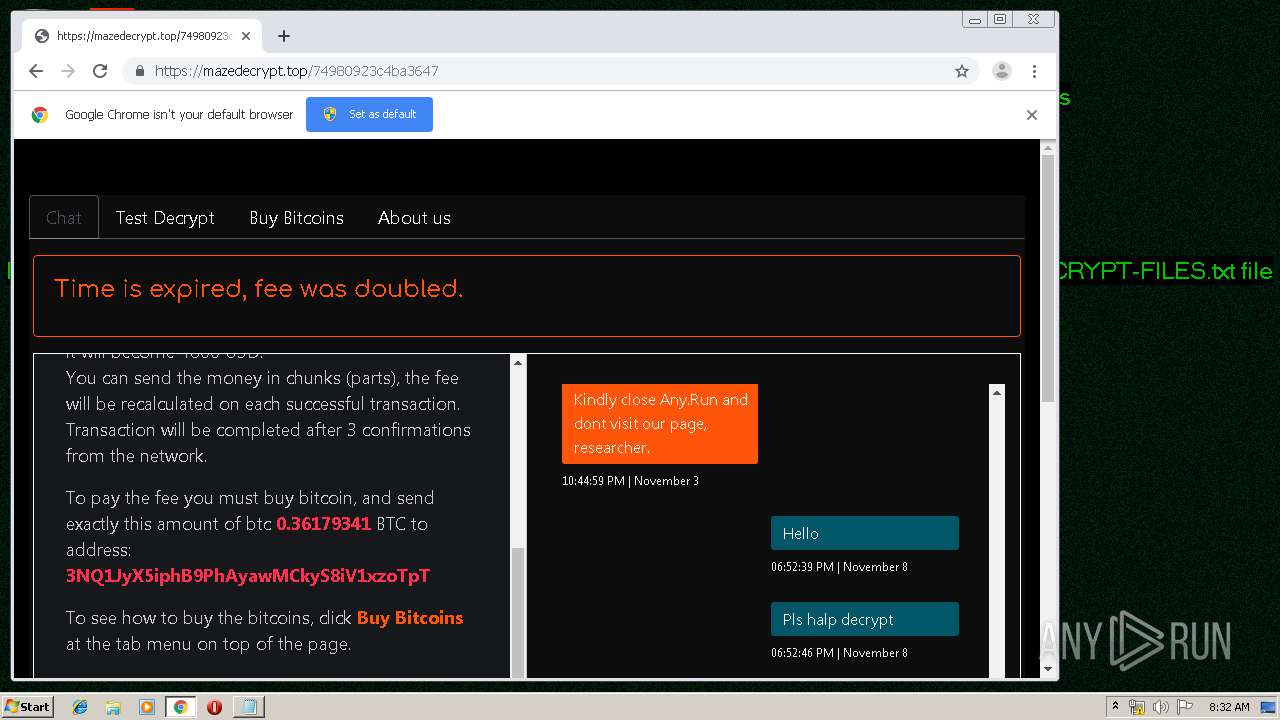
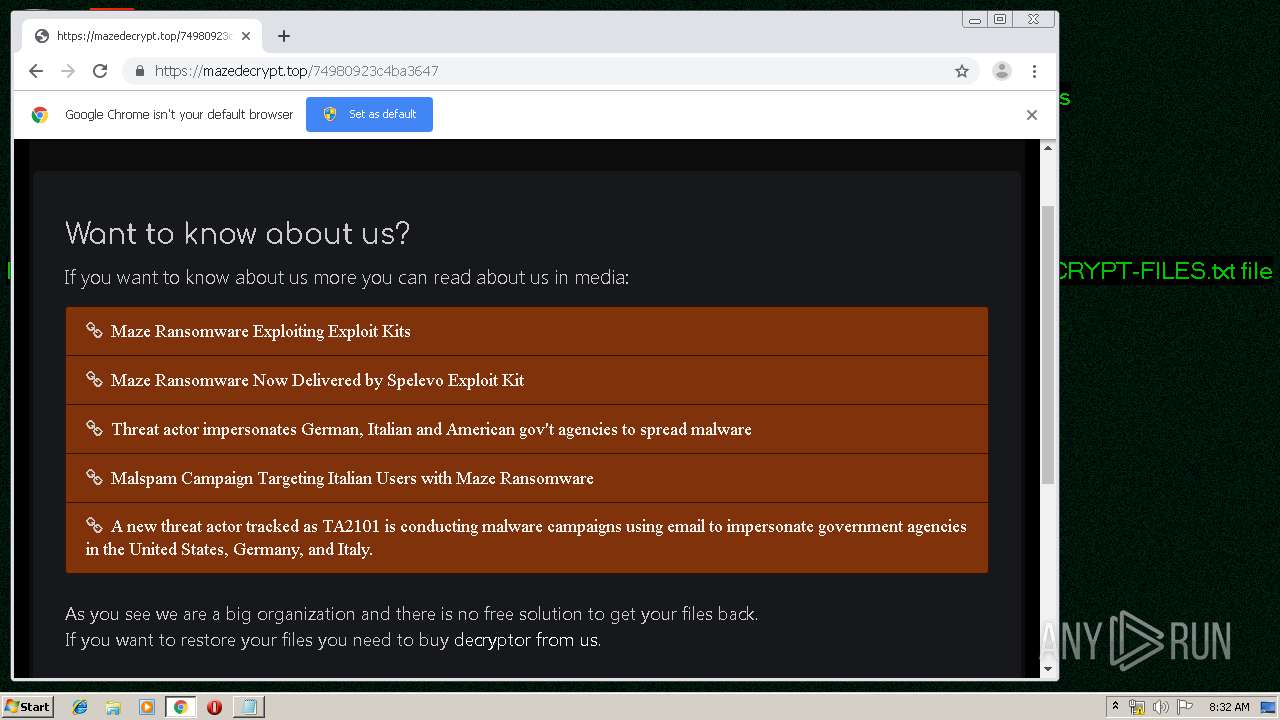
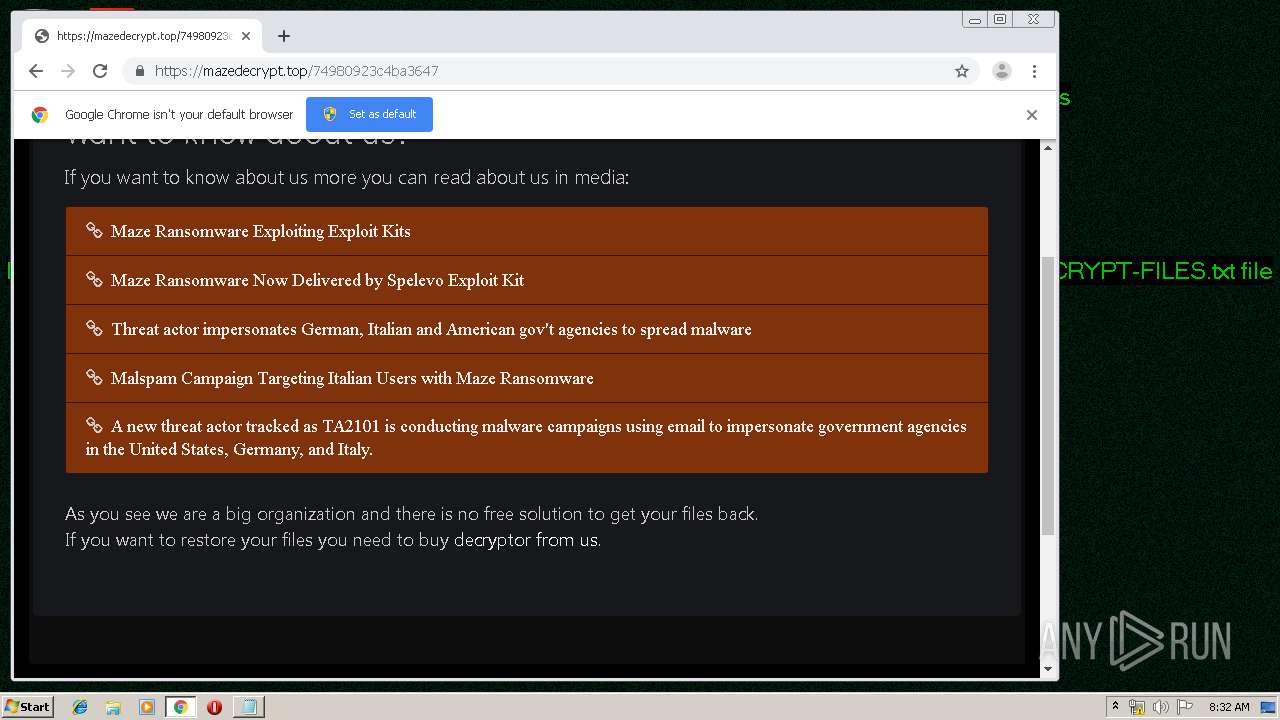
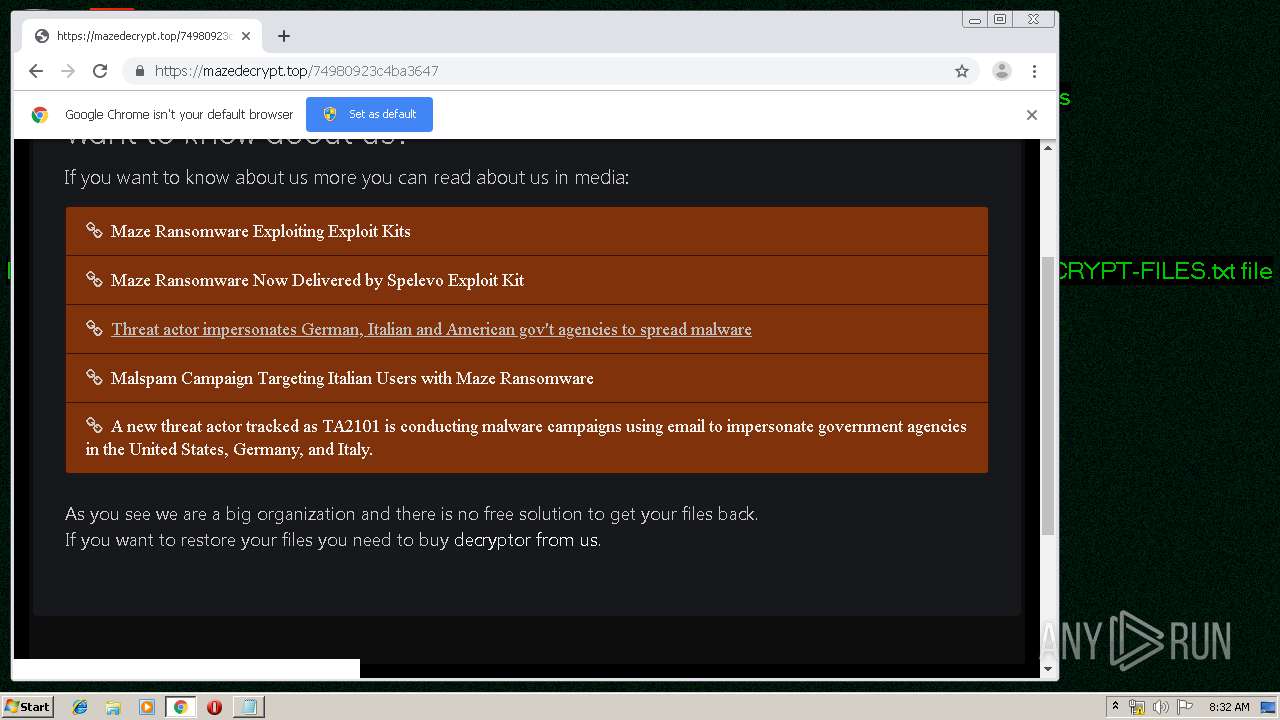
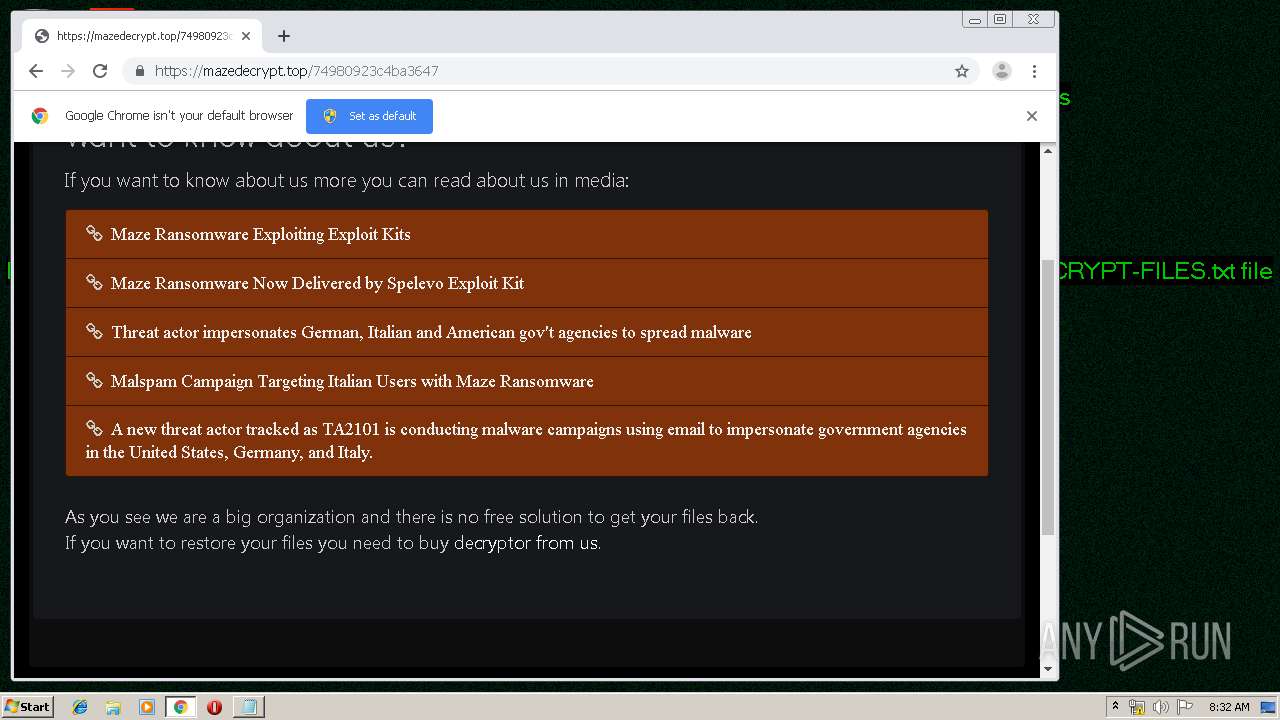
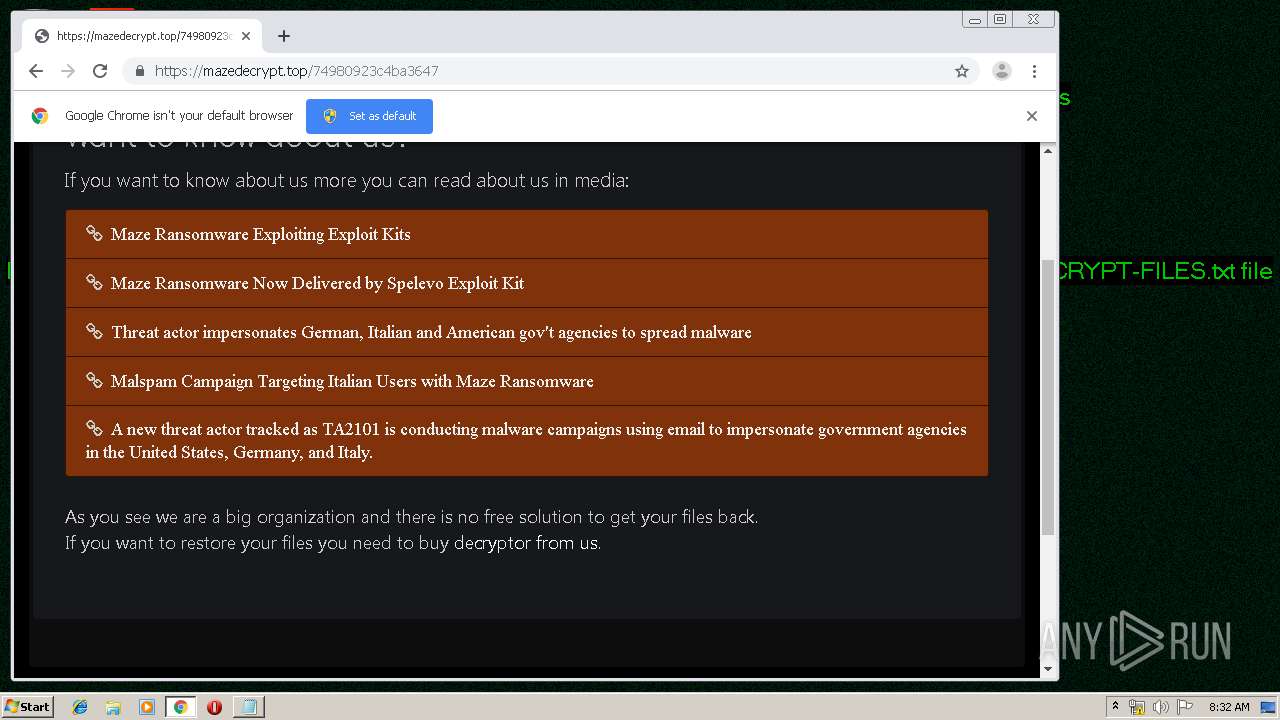
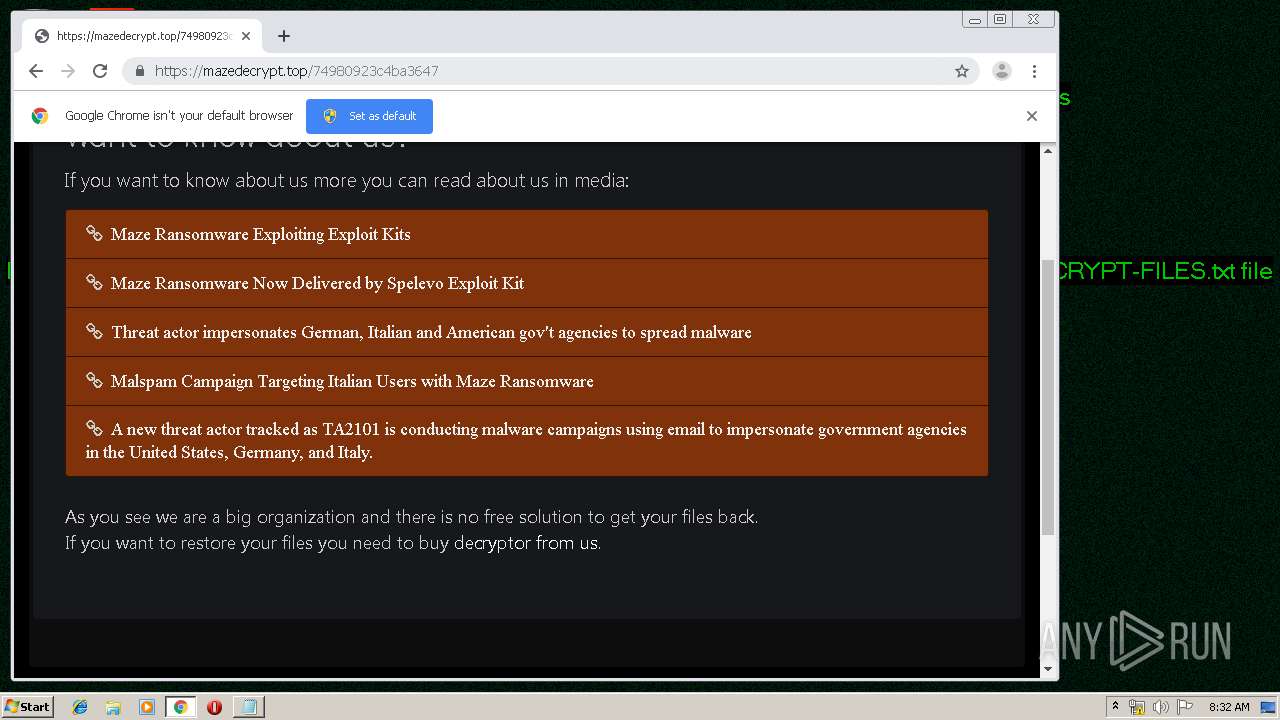
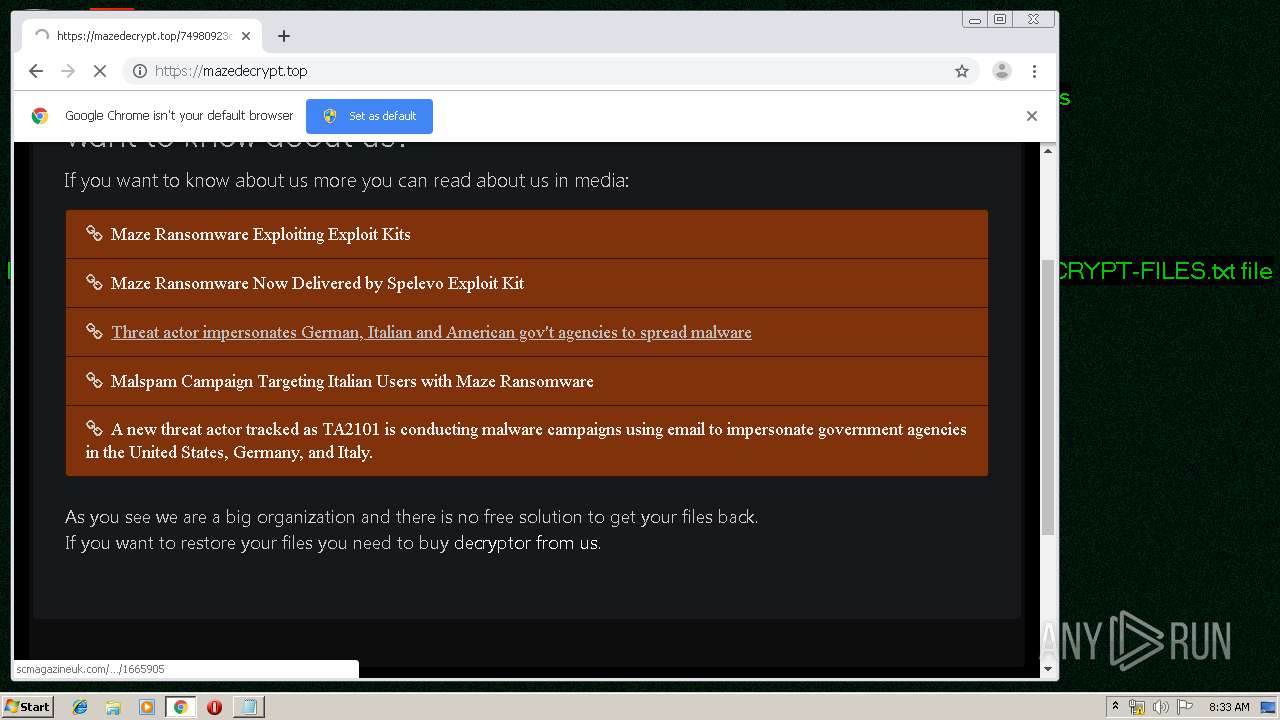
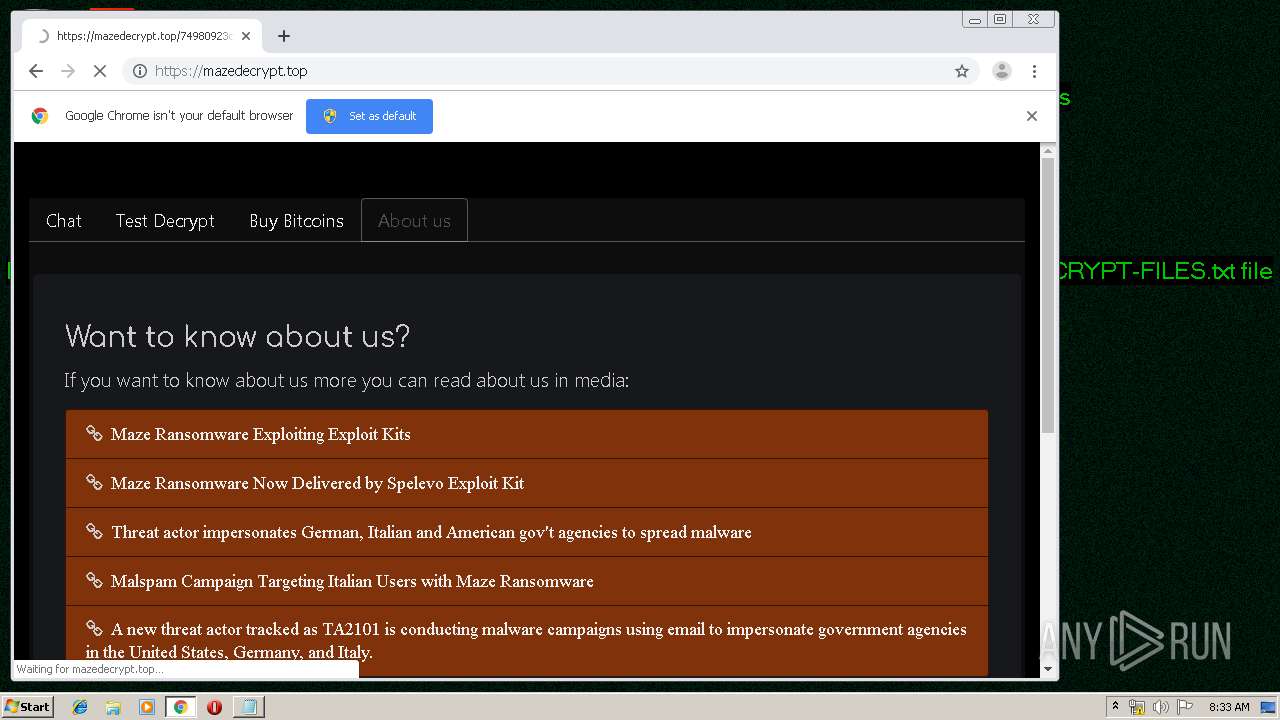
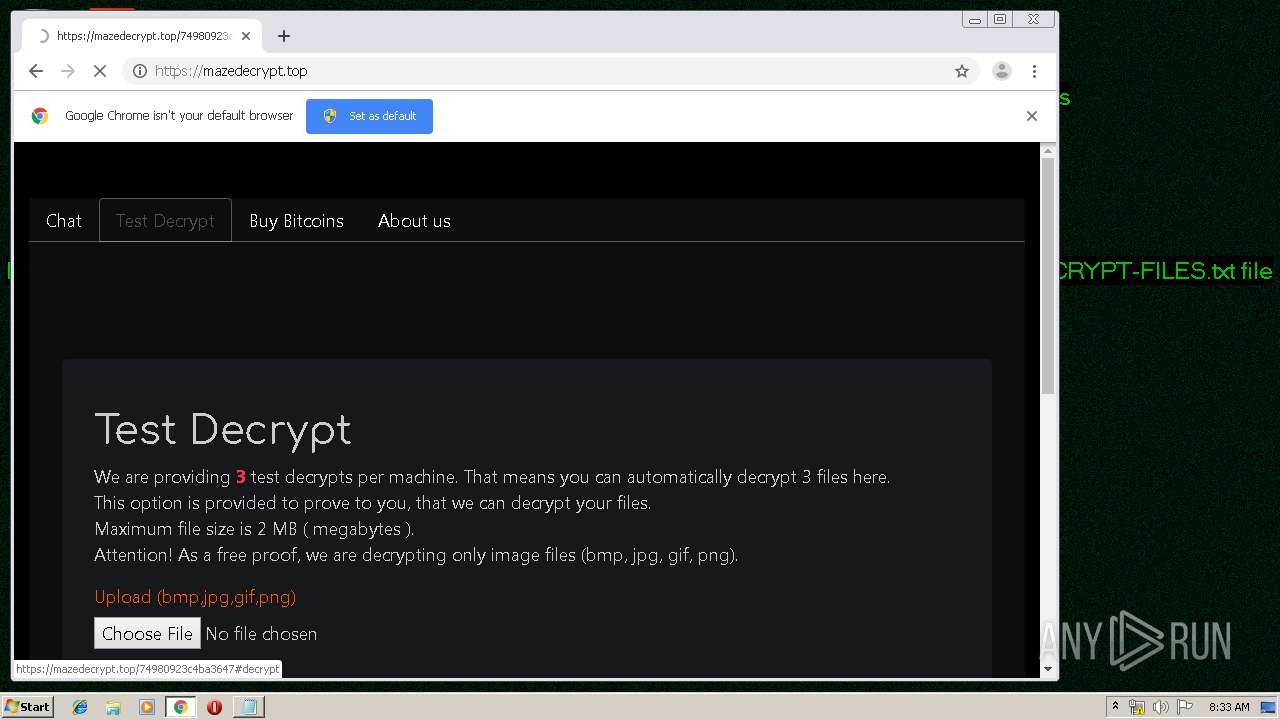
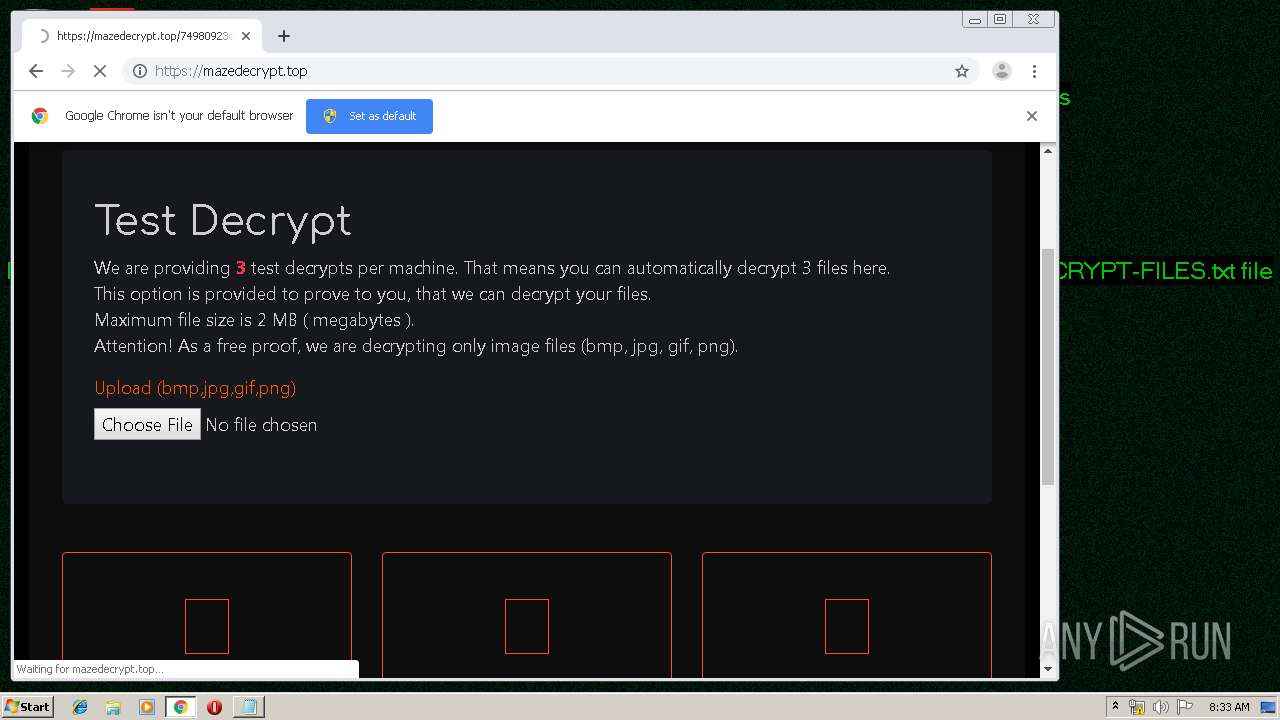
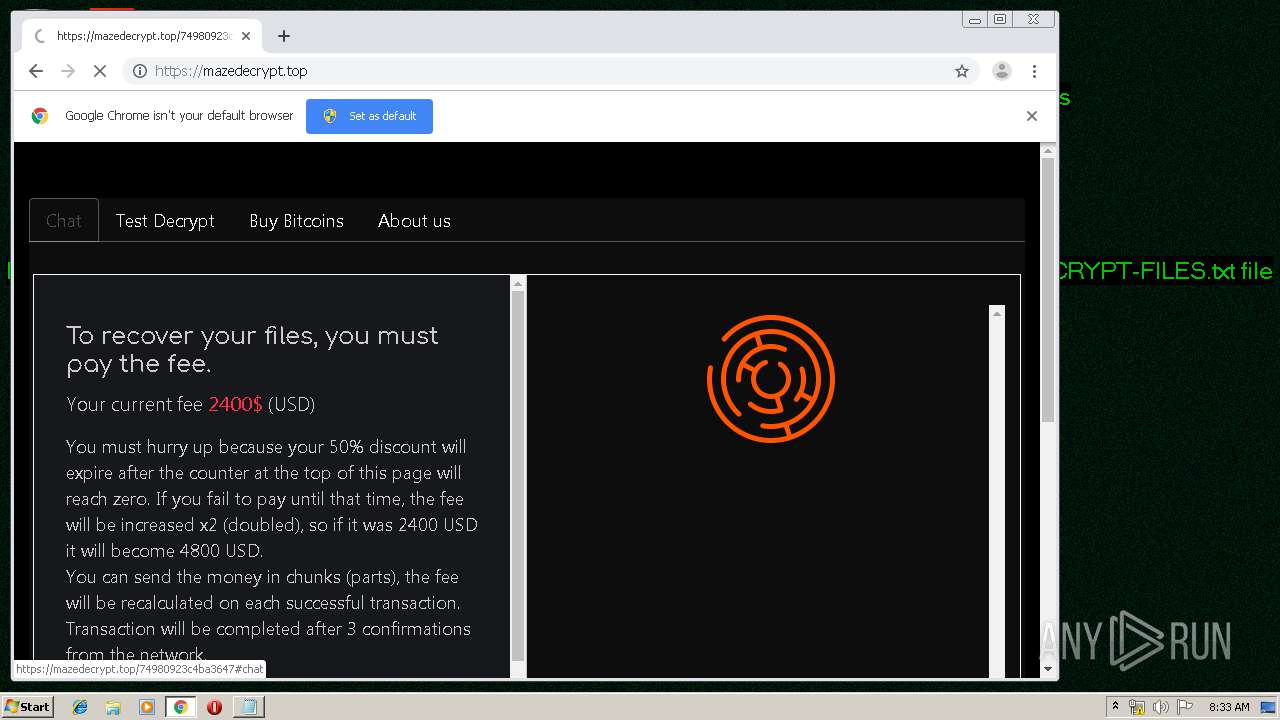
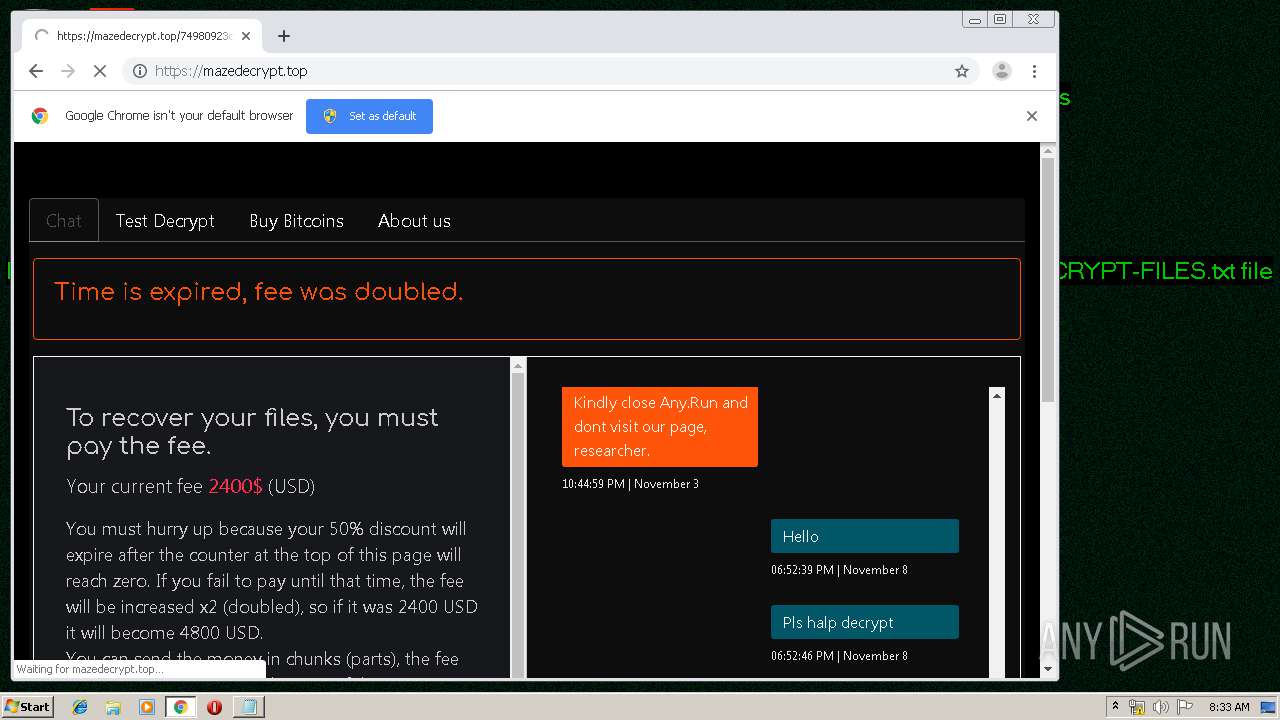
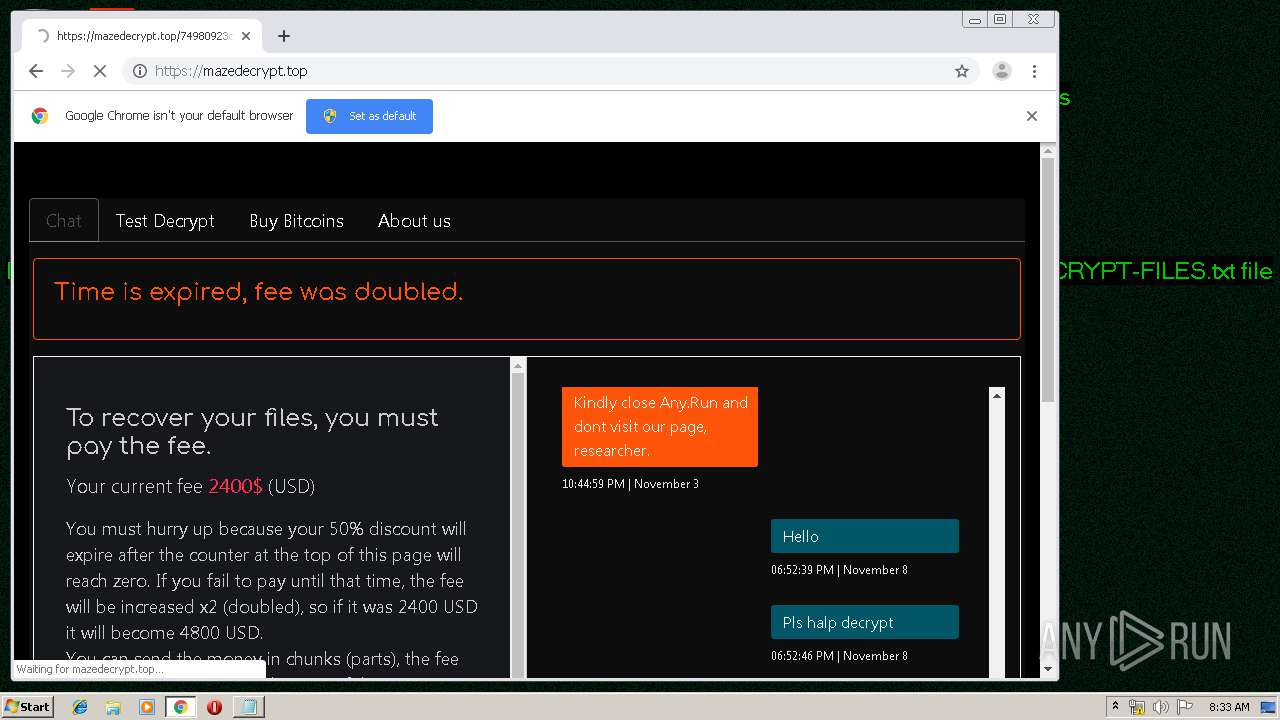
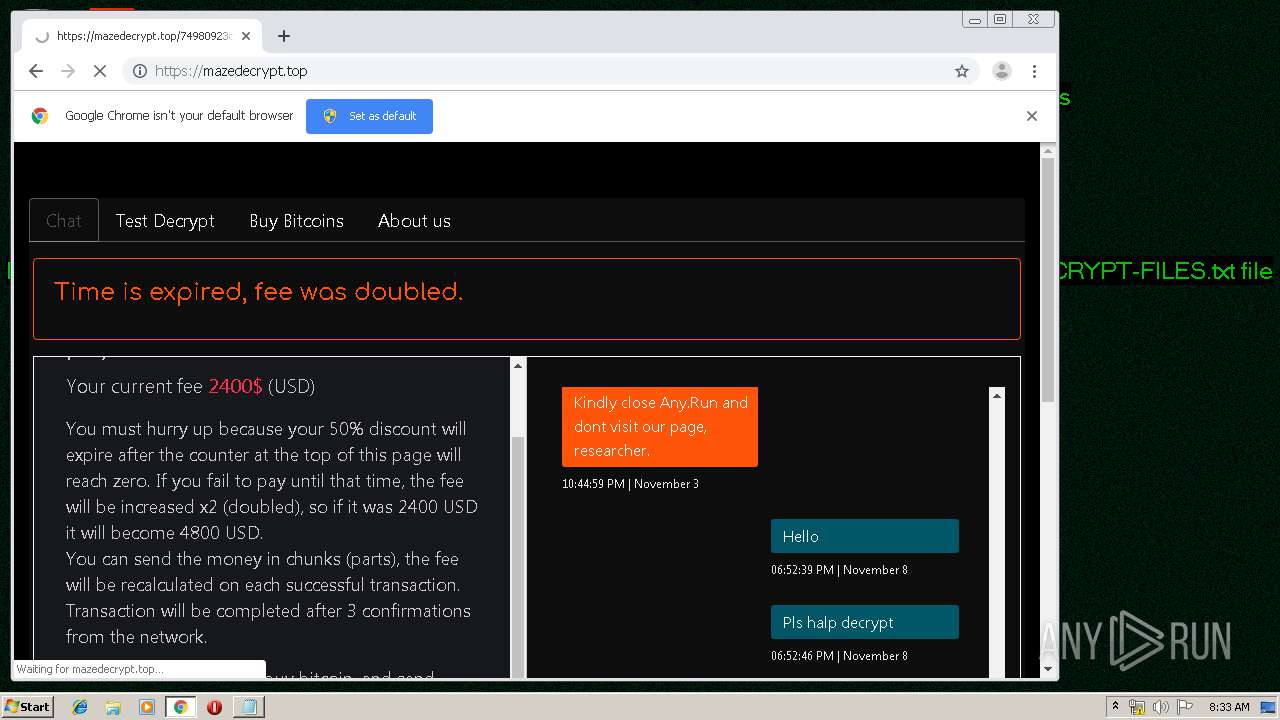
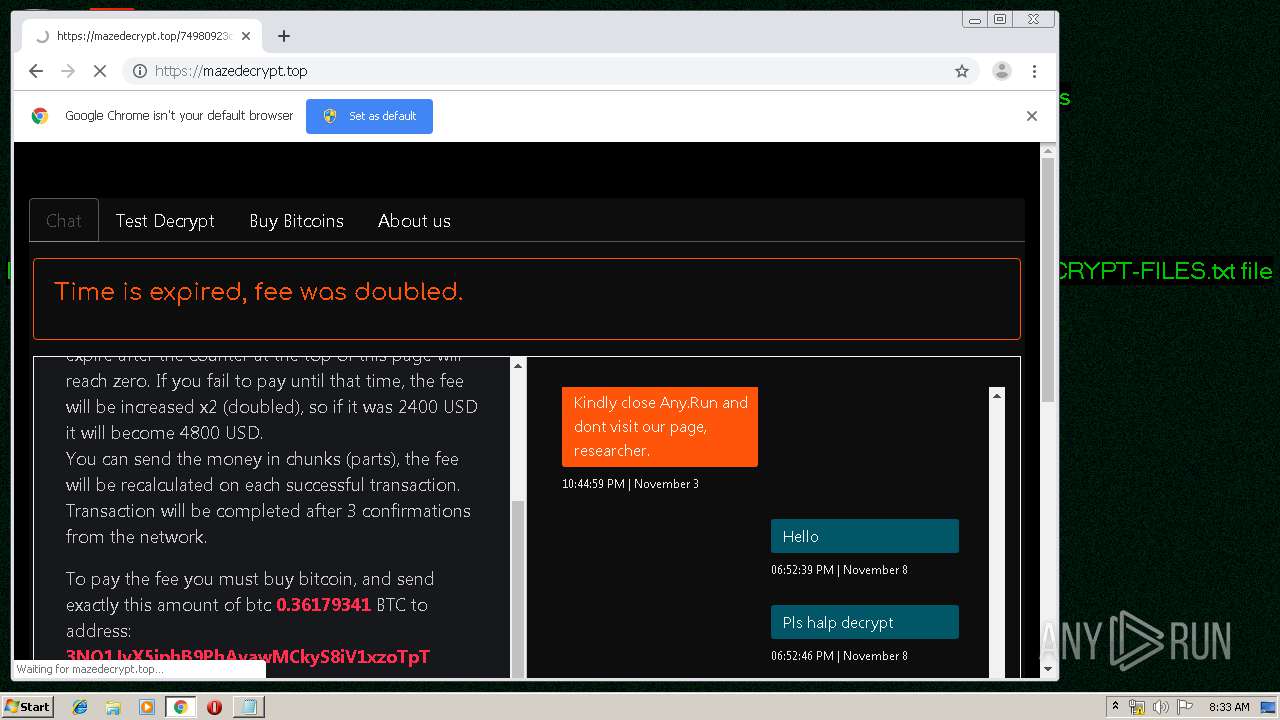
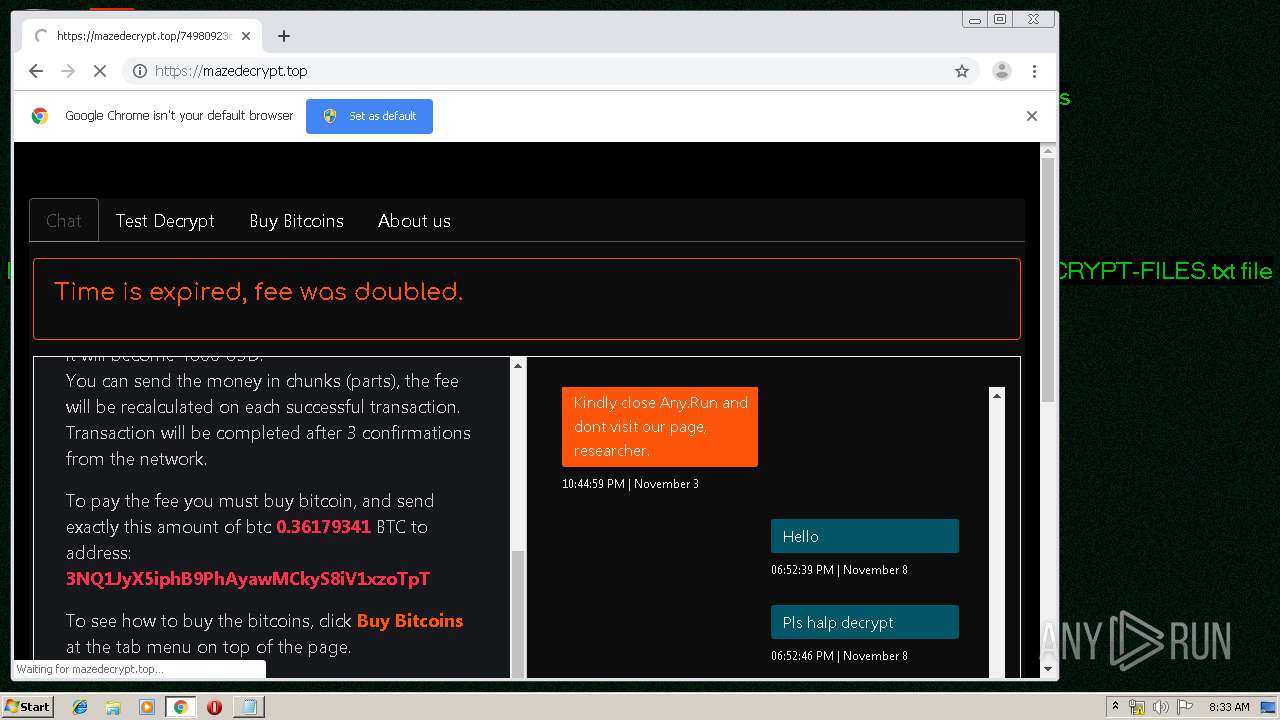
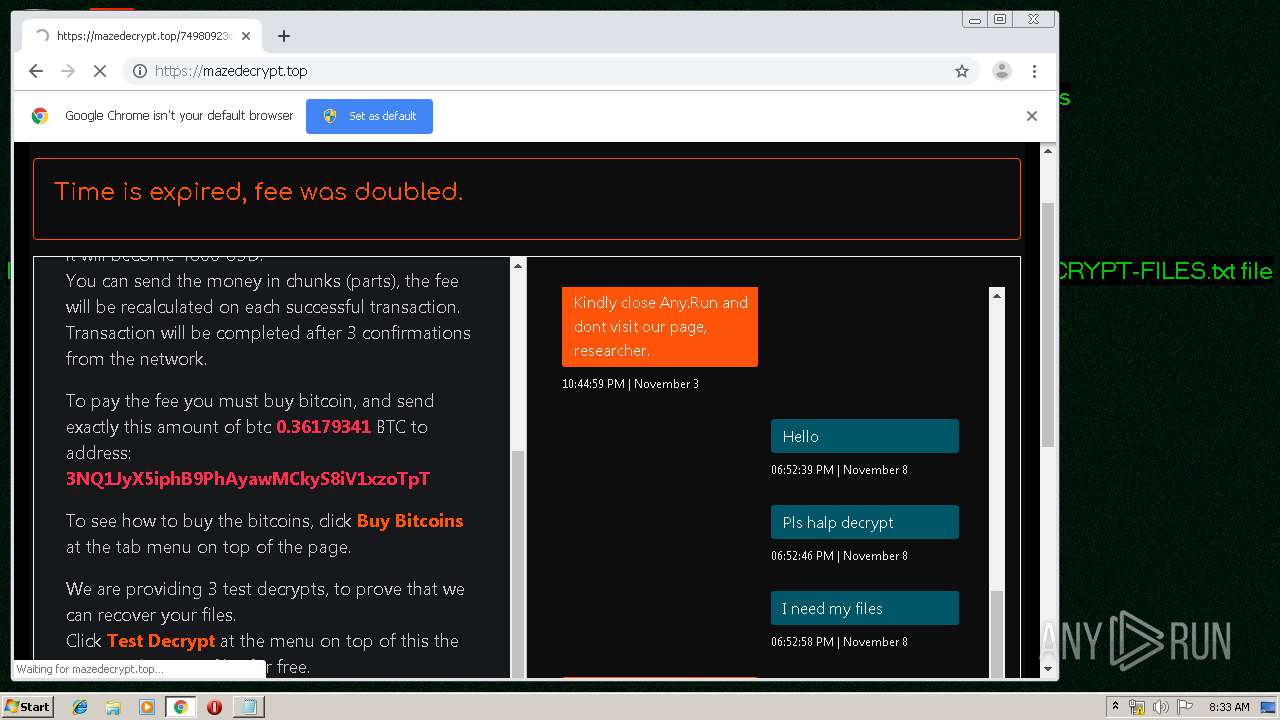
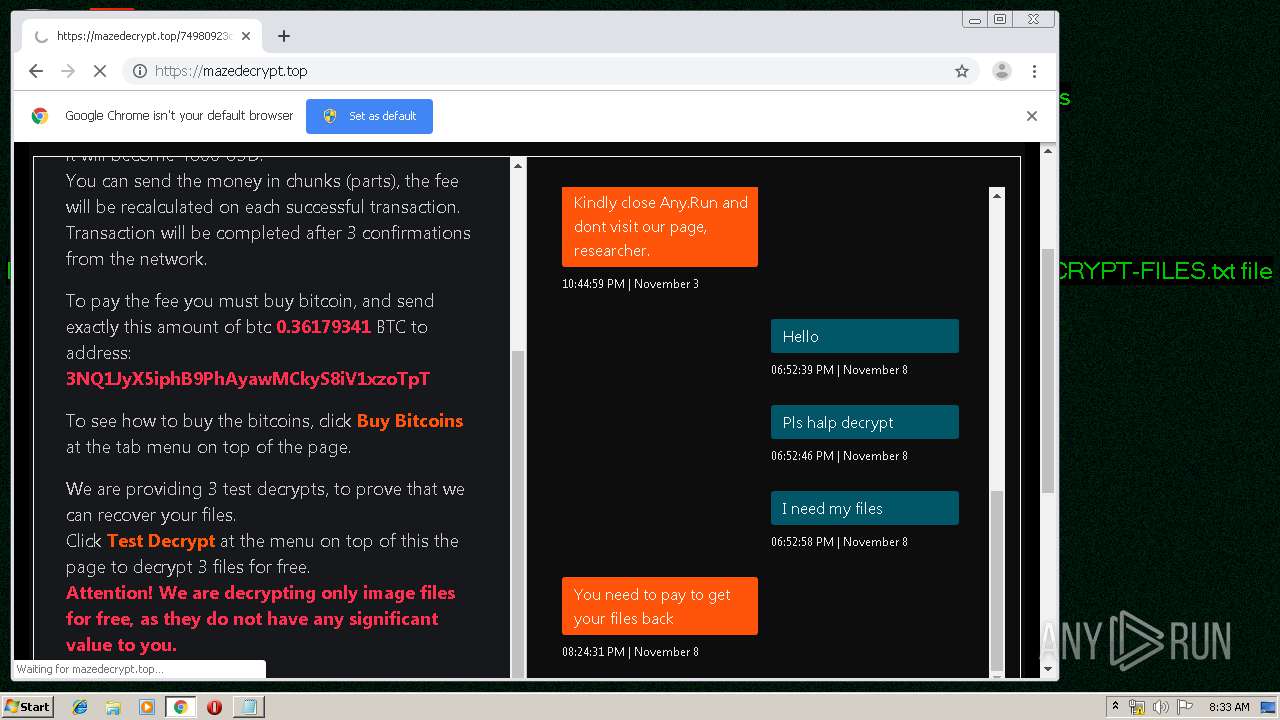
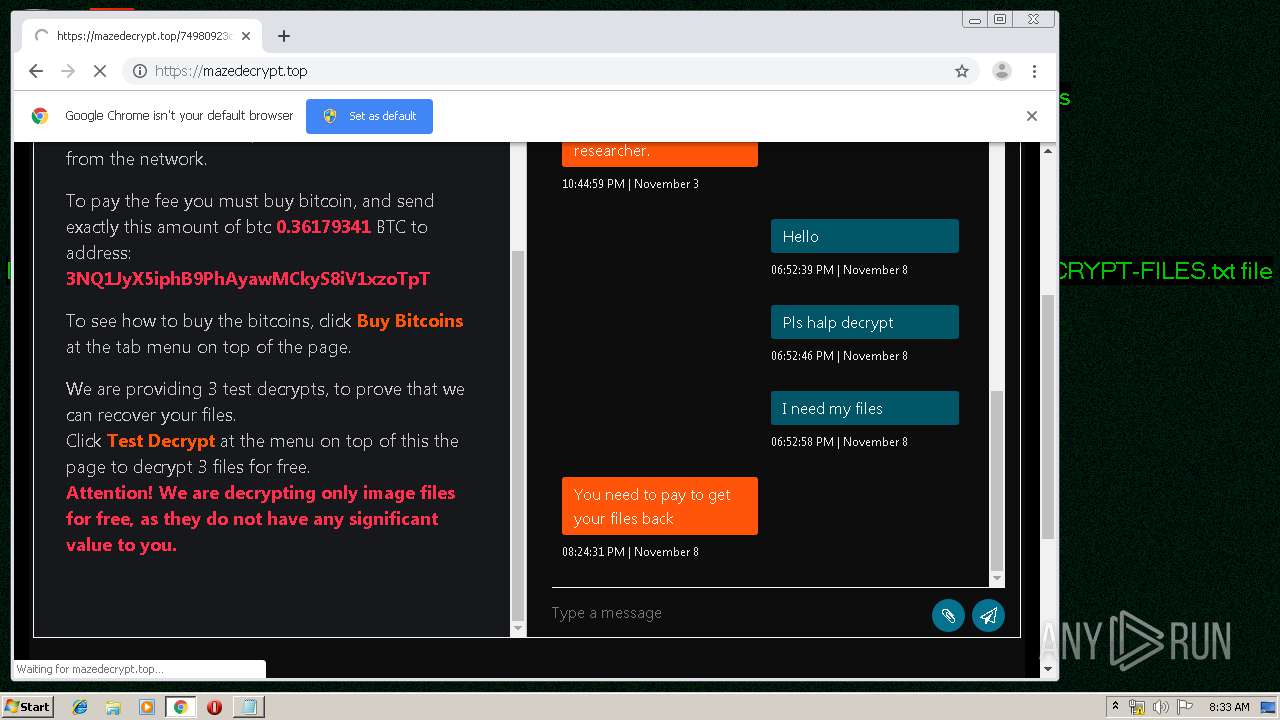
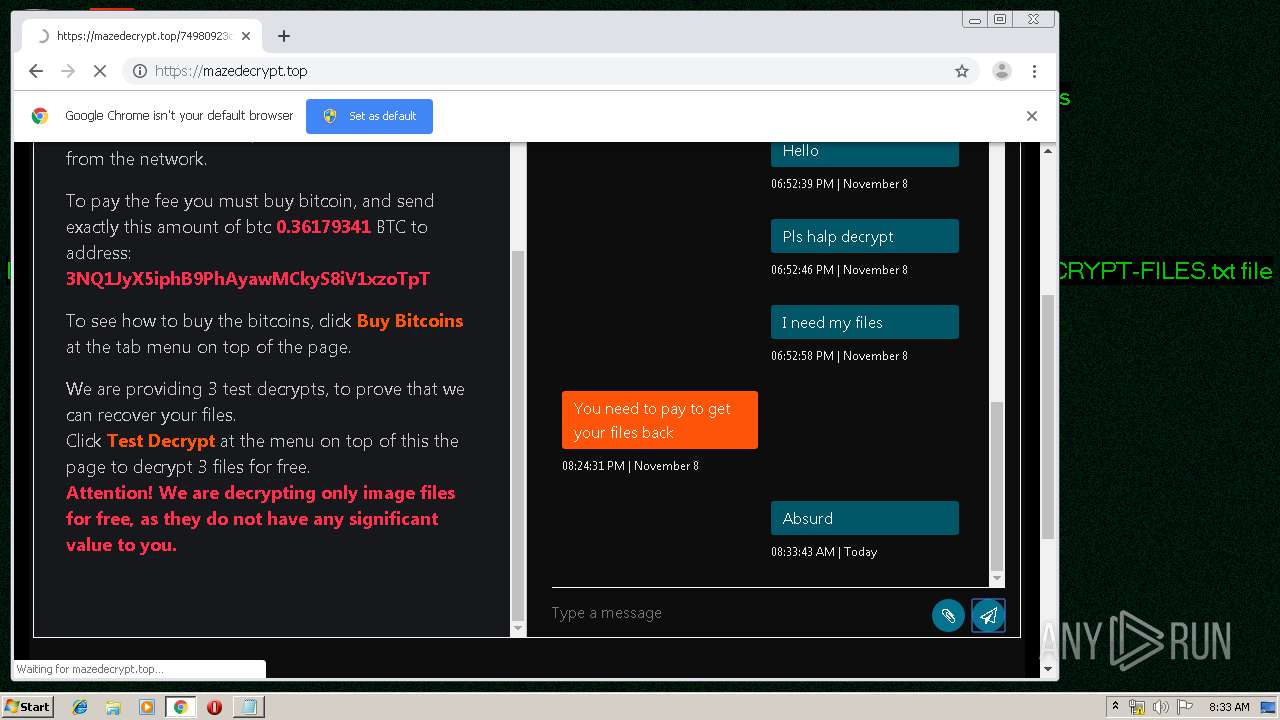
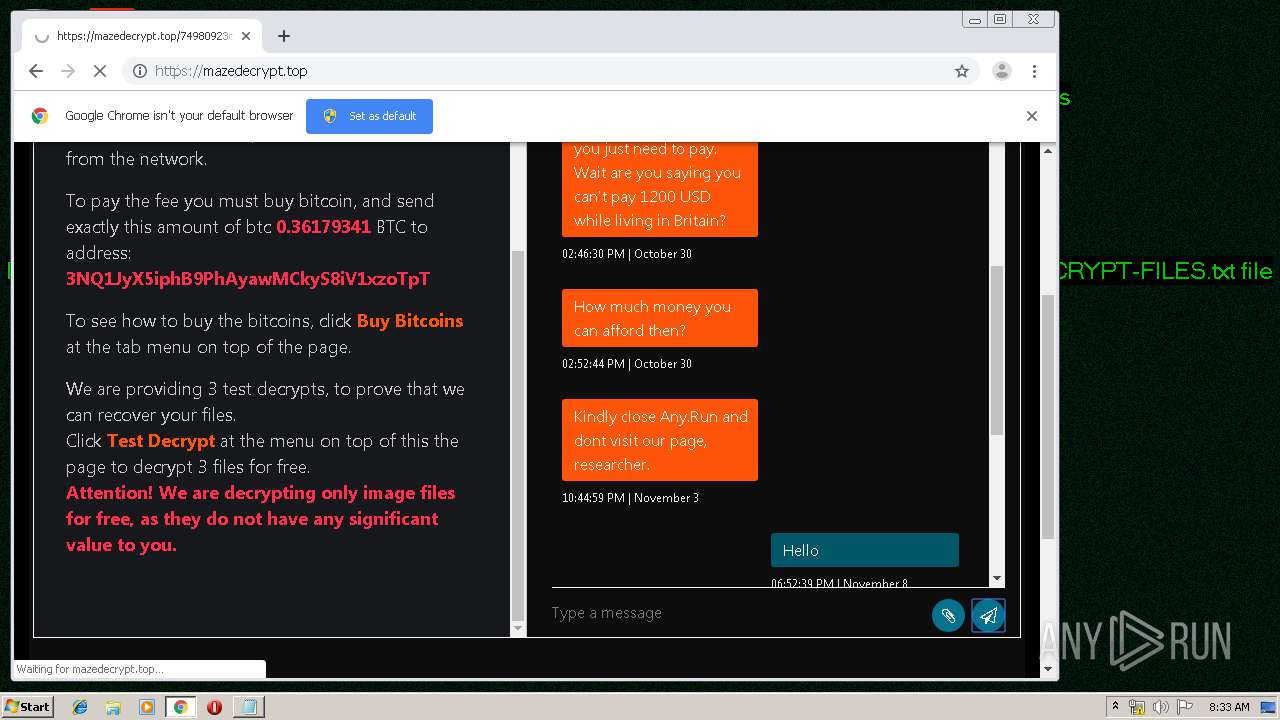
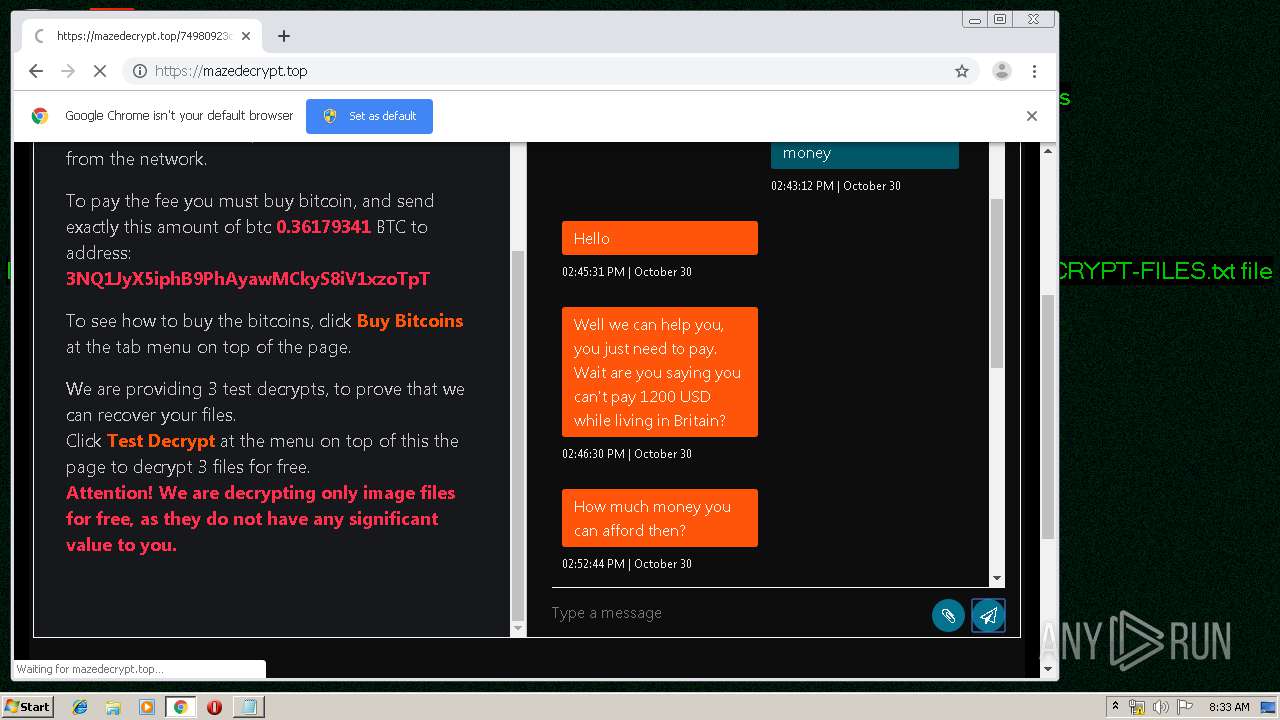
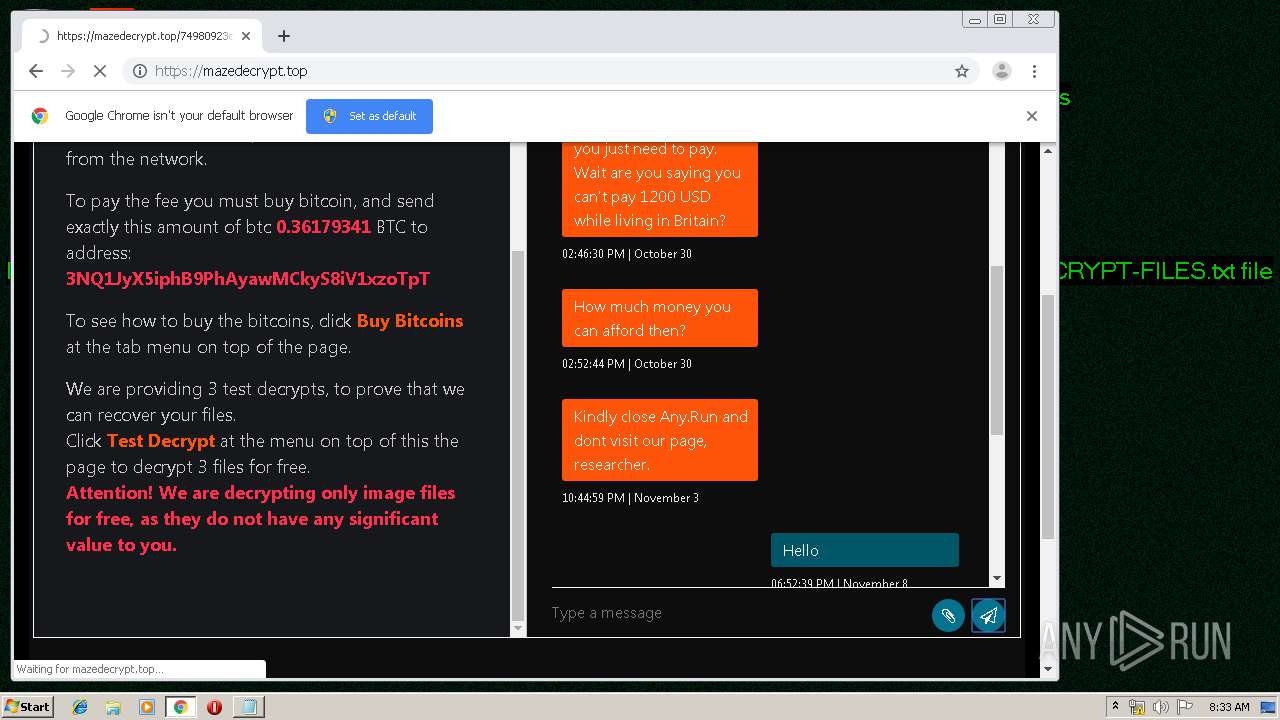
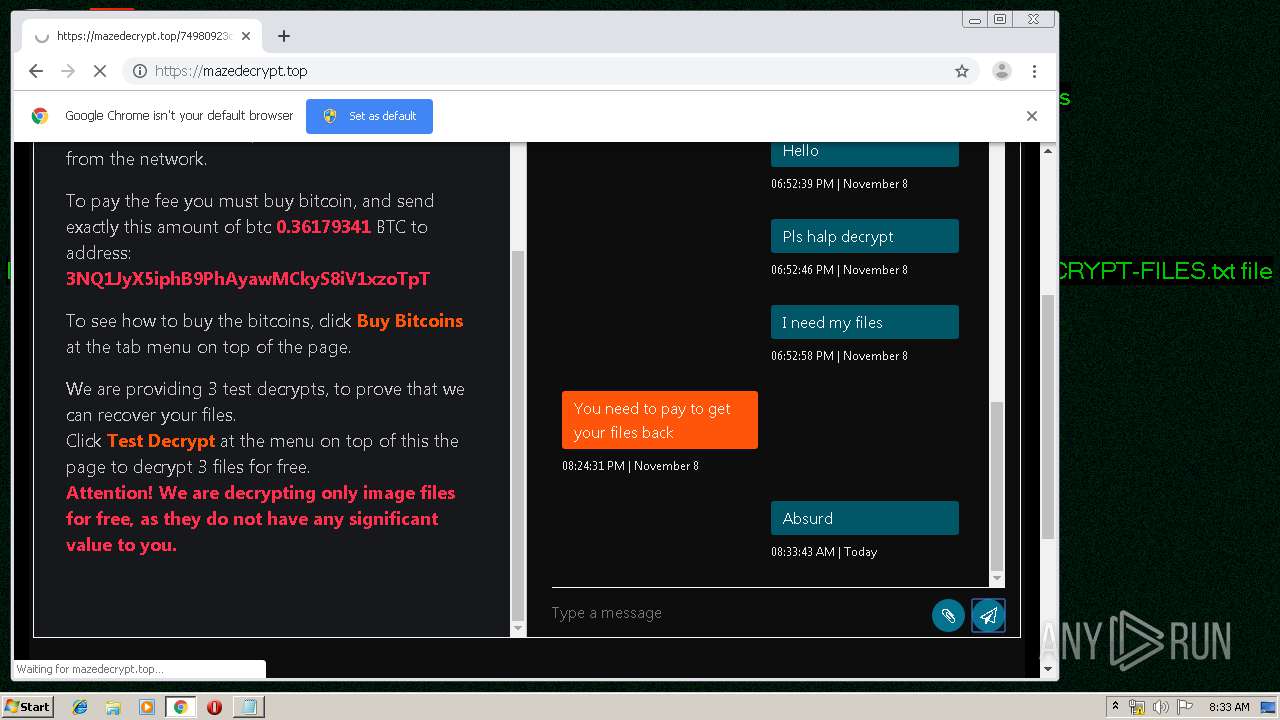
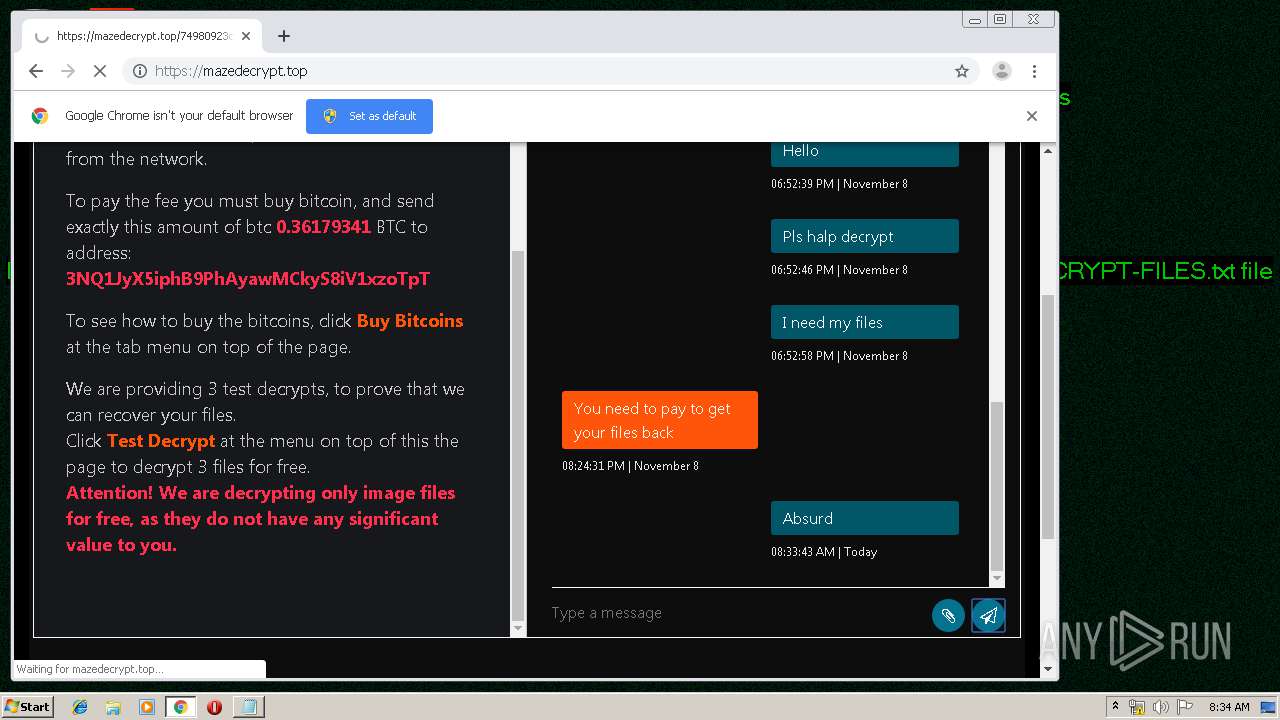
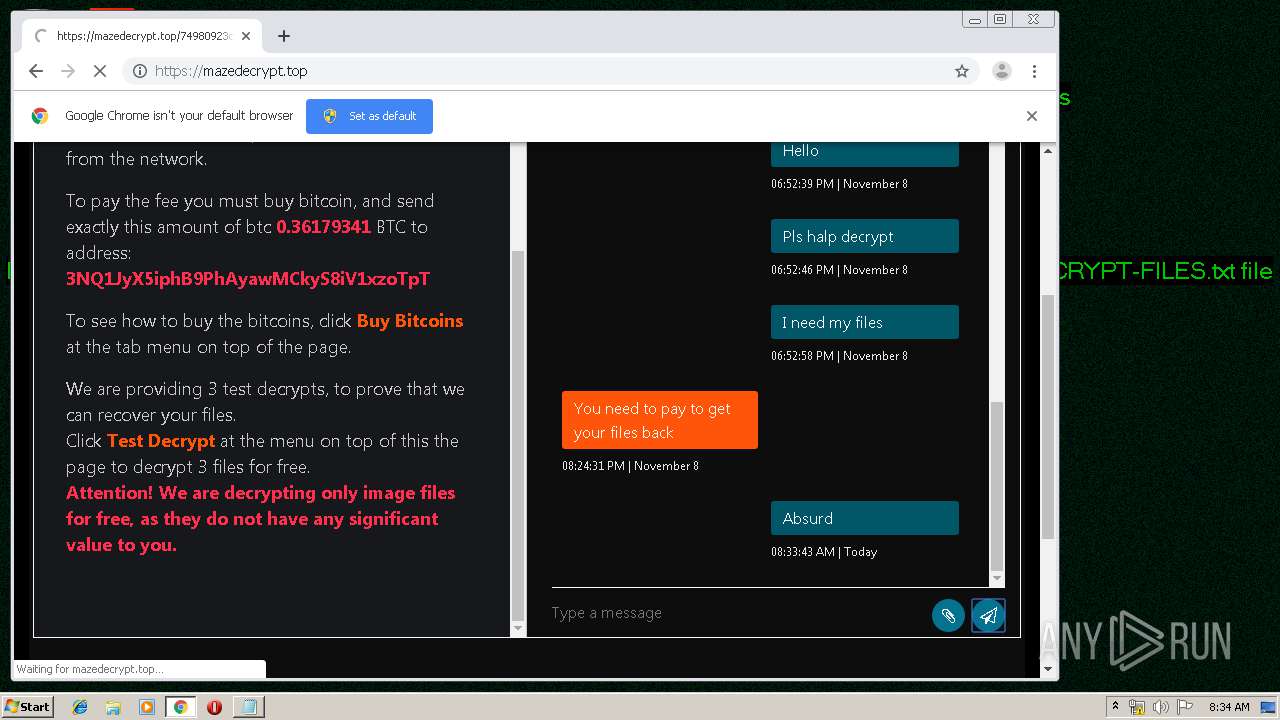
| Threats: | Maze is ransomware — a malware type that encrypts the victim’s files and restores the data in exchange for a ransom payment. One of the most distinguishable features of Maze is that it is one of the first malware of the kind to publicly release stolen data. |
| Analysis date: | December 18, 2019, 08:30:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | 993CC270015305A11D908629CF73CE60 |
| SHA1: | 76A4E518B83B24B49290EBD009F94D404278D925 |
| SHA256: | 8D995102E28D96BB93016E3ABBB38B4597B9E497668FA7A0E10CF28DB105516B |
| SSDEEP: | 12288:uswRjz8P8qhV6NWhWh2R3+7Jruvw1Dhzsi9:uRjCLhyWhWh8+7duYLzsi |
MALICIOUS
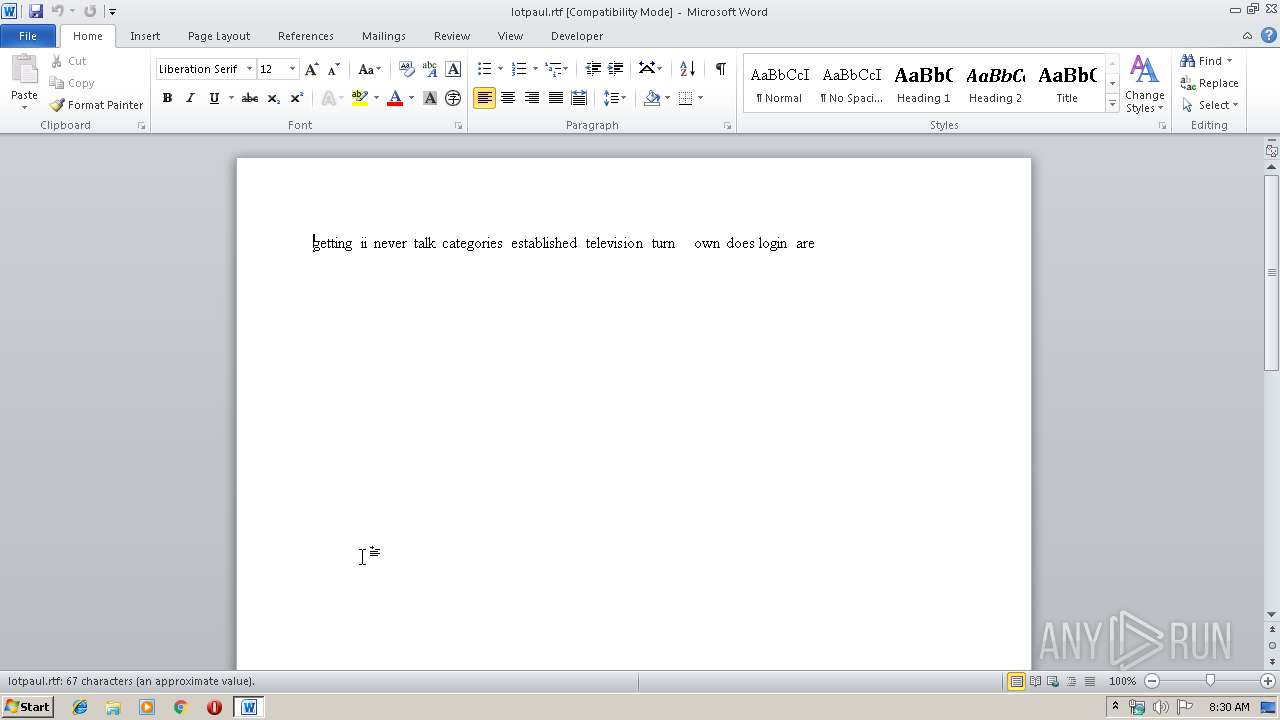
Writes file to Word startup folder
- rundll32.exe (PID: 964)
Actions looks like stealing of personal data
- rundll32.exe (PID: 964)
Deletes shadow copies
- rundll32.exe (PID: 964)
Writes to a start menu file
- rundll32.exe (PID: 964)
Dropped file may contain instructions of ransomware
- rundll32.exe (PID: 964)
Renames files like Ransomware
- rundll32.exe (PID: 964)
MAZE was detected
- rundll32.exe (PID: 964)
Connects to CnC server
- rundll32.exe (PID: 964)
SUSPICIOUS
Creates files in the program directory
- rundll32.exe (PID: 964)
Reads the cookies of Mozilla Firefox
- rundll32.exe (PID: 964)
Connects to server without host name
- rundll32.exe (PID: 964)
Creates files like Ransomware instruction
- rundll32.exe (PID: 964)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 2788)
Reads internet explorer settings
- CLVIEW.EXE (PID: 1944)
Modifies files in Chrome extension folder
- chrome.exe (PID: 920)
Creates files in the user directory
- rundll32.exe (PID: 964)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2436)
- WINWORD.EXE (PID: 2788)
- CLVIEW.EXE (PID: 1944)
Loads main object executable
- rundll32.exe (PID: 964)
Manual execution by user
- WINWORD.EXE (PID: 2436)
- WINWORD.EXE (PID: 2788)
- NOTEPAD.EXE (PID: 2196)
- chrome.exe (PID: 920)
Creates files in the user directory
- WINWORD.EXE (PID: 2436)
- WINWORD.EXE (PID: 2788)
Reads the hosts file
- chrome.exe (PID: 920)
- chrome.exe (PID: 2280)
Changes settings of System certificates
- chrome.exe (PID: 2280)
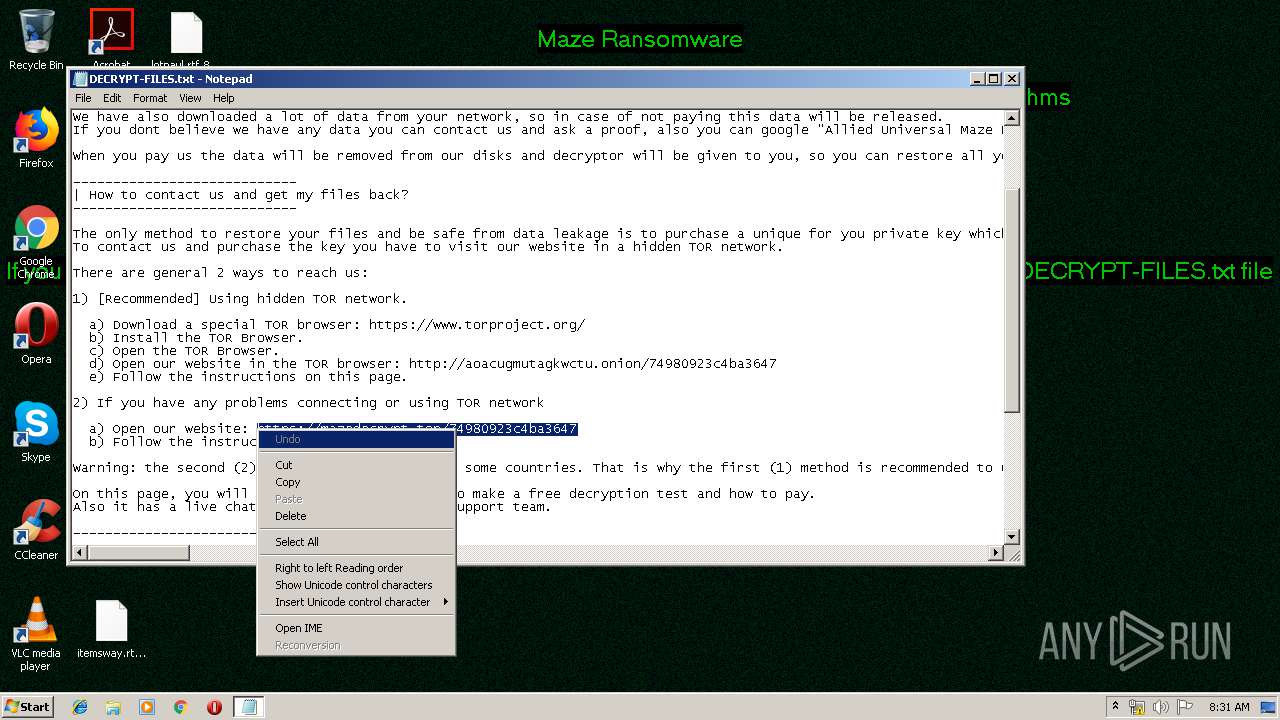
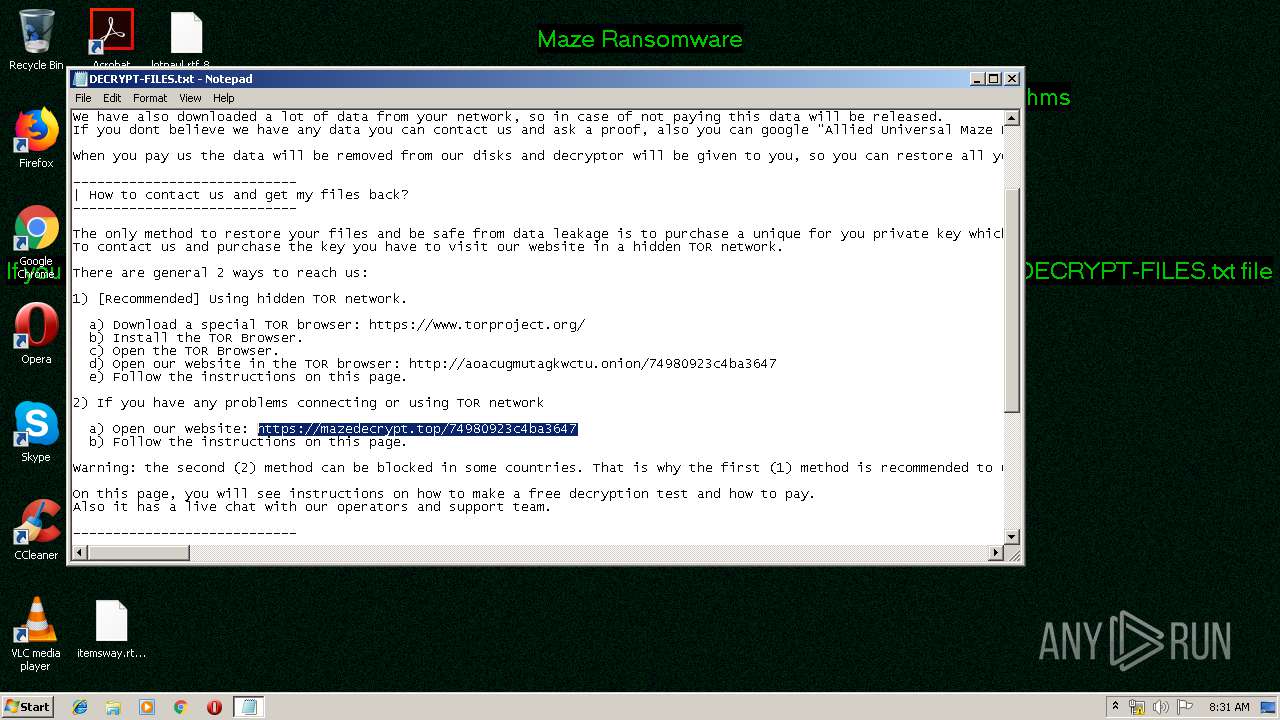
Dropped object may contain TOR URL's
- rundll32.exe (PID: 964)
Application launched itself
- chrome.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:12:01 23:27:05+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 47616 |
| InitializedDataSize: | 413184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2992 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Dec-2019 22:27:05 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 01-Dec-2019 22:27:05 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000B936 | 0x0000BA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.66342 |
.rdata | 0x0000D000 | 0x0000469E | 0x00004800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.53309 |
.data | 0x00012000 | 0x0005F520 | 0x0005D800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99186 |
.rsrc | 0x00072000 | 0x000001E0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.71141 |
.reloc | 0x00073000 | 0x00000CC4 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.32835 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
2 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
KERNEL32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
DllInstall | 1 | 0x000027F7 |
DllRegisterServer | 2 | 0x00002808 |
DllUnregisterServer | 3 | 0x00002808 |
work | 4 | 0x00002754 |
Total processes
81
Monitored processes
42
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16738931572062515830 --mojo-platform-channel-handle=4204 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 640 | "C:\o\..\Windows\nh\at\ix\..\..\..\system32\bknm\jcp\ax\..\..\..\wbem\jl\el\..\..\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15082741091399537271 --mojo-platform-channel-handle=3088 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 964 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\AppData\Local\Temp\avira.dll", DllInstall | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3089085906263552545 --mojo-platform-channel-handle=2820 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6161746216844165658 --mojo-platform-channel-handle=3488 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2444653372046480693 --mojo-platform-channel-handle=3300 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16936653746944952617 --mojo-platform-channel-handle=1044 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,15414113256178248837,8780698667535941067,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14230199317402747472 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=572 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 530
Read events
2 589
Write events
534
Delete events
407
Modification events
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | >yb |
Value: 3E79620084090000010000000000000000000000 | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2436) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1334968383 | |||
Executable files
0
Suspicious files
427
Text files
502
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2436 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB5BE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2436 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{82FFF2DB-9CB1-42D4-9A7B-9F4BAEA8D374}.tmp | — | |
MD5:— | SHA256:— | |||
| 2436 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{53A4EE63-D8F3-4CF7-A817-AE5543392C29}.tmp | — | |
MD5:— | SHA256:— | |||
| 2436 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{BDB498A1-BC7A-43A4-8B0E-E6797E9E088B}.tmp | — | |
MD5:— | SHA256:— | |||
| 964 | rundll32.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 964 | rundll32.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 964 | rundll32.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 2436 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 964 | rundll32.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
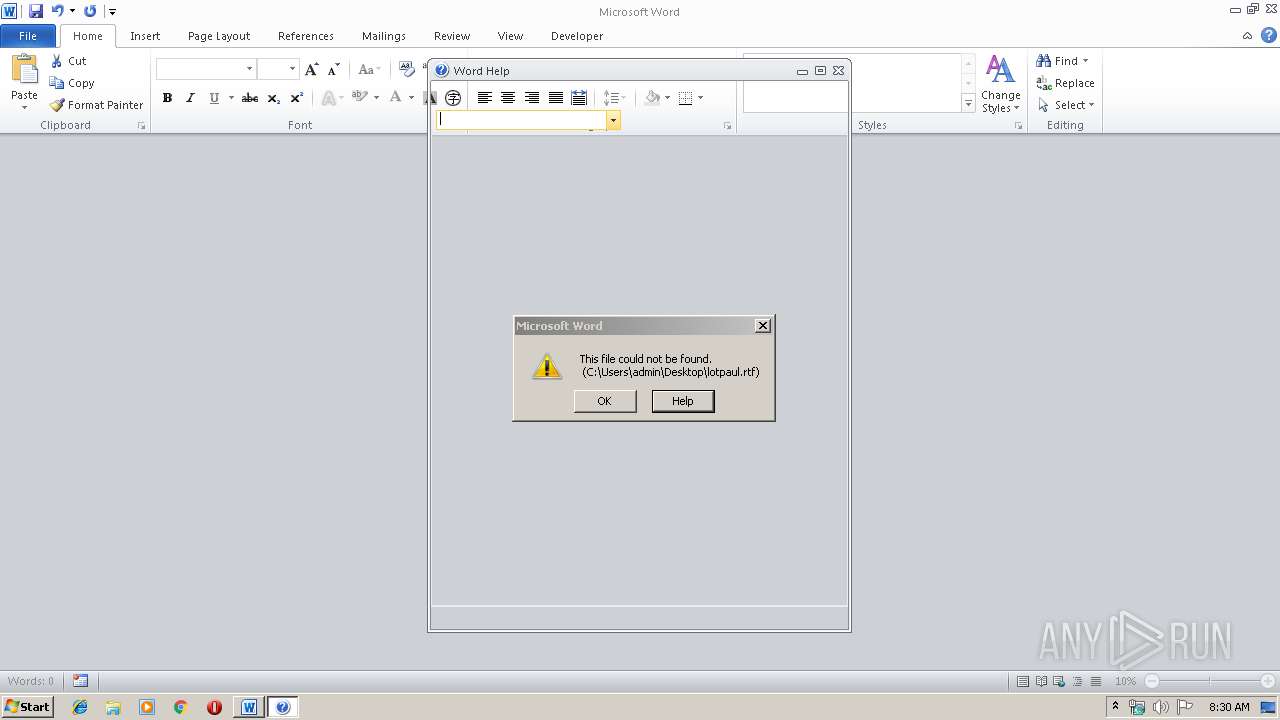
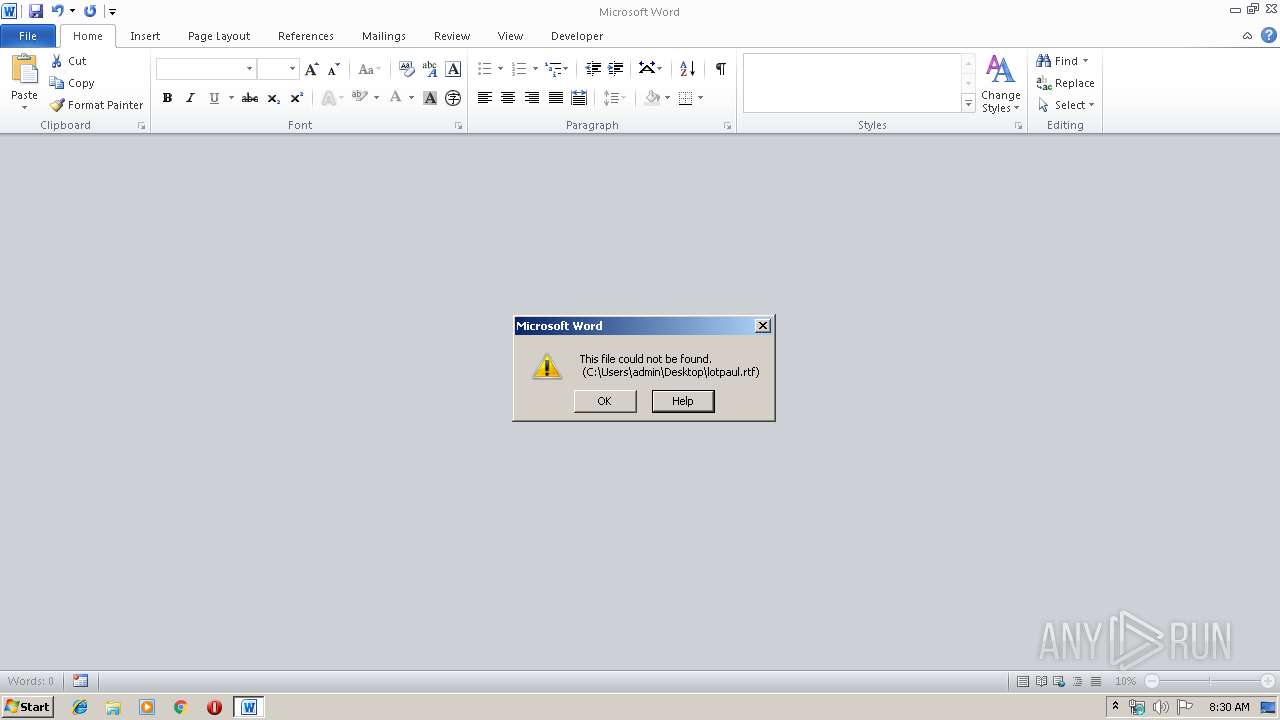
| 2436 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\lotpaul.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
144
DNS requests
69
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
964 | rundll32.exe | POST | — | 91.218.114.11:80 | http://91.218.114.11/wire/payout/svg.cgi?bokn=618537l&ms=5t87&jsq=48g7m0x&glq=wi7 | RU | — | — | malicious |
964 | rundll32.exe | POST | — | 91.218.114.26:80 | http://91.218.114.26/wg.action?f=eot | RU | — | — | malicious |
964 | rundll32.exe | POST | — | 91.218.114.25:80 | http://91.218.114.25/hdtqkqla.cgi?xso=5jwkyx&aug=32nq15 | RU | — | — | malicious |
964 | rundll32.exe | POST | — | 91.218.114.4:80 | http://91.218.114.4/webaccess/view/bpwthce.cgi | RU | — | — | malicious |
964 | rundll32.exe | POST | 404 | 91.218.114.4:80 | http://91.218.114.4/webaccess/view/bpwthce.cgi | RU | html | 224 b | malicious |
964 | rundll32.exe | POST | — | 91.218.114.31:80 | http://91.218.114.31/account/view/ye.html?k=8c | RU | — | — | malicious |
964 | rundll32.exe | POST | 404 | 91.218.114.11:80 | http://91.218.114.11/wire/payout/svg.cgi?bokn=618537l&ms=5t87&jsq=48g7m0x&glq=wi7 | RU | html | 296 b | malicious |
964 | rundll32.exe | POST | 404 | 91.218.114.26:80 | http://91.218.114.26/wg.action?f=eot | RU | html | 286 b | malicious |
964 | rundll32.exe | POST | 404 | 91.218.114.11:80 | http://91.218.114.11/forum/ticket/iw.jsp | RU | html | 296 b | malicious |
964 | rundll32.exe | POST | — | 91.218.114.25:80 | http://91.218.114.25/r.php | RU | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.218.114.4:80 | — | Mir Telematiki Ltd | RU | malicious |
964 | rundll32.exe | 91.218.114.4:80 | — | Mir Telematiki Ltd | RU | malicious |
964 | rundll32.exe | 91.218.114.11:80 | — | Mir Telematiki Ltd | RU | malicious |
— | — | 91.218.114.25:80 | — | Mir Telematiki Ltd | RU | malicious |
964 | rundll32.exe | 91.218.114.25:80 | — | Mir Telematiki Ltd | RU | malicious |
— | — | 91.218.114.26:80 | — | Mir Telematiki Ltd | RU | malicious |
964 | rundll32.exe | 91.218.114.31:80 | — | Mir Telematiki Ltd | RU | malicious |
964 | rundll32.exe | 91.218.114.77:80 | — | Mir Telematiki Ltd | RU | malicious |
964 | rundll32.exe | 91.218.114.79:80 | — | Mir Telematiki Ltd | RU | malicious |
— | — | 91.218.114.79:80 | — | Mir Telematiki Ltd | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
mazedecrypt.top |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
964 | rundll32.exe | A Network Trojan was detected | RANSOMWARE [PTsecurity] Maze |
4 ETPRO signatures available at the full report