| File name: | SolaraV3.exe |
| Full analysis: | https://app.any.run/tasks/3a9d00a7-68a8-4e45-829f-e84d67100d2c |
| Verdict: | Malicious activity |
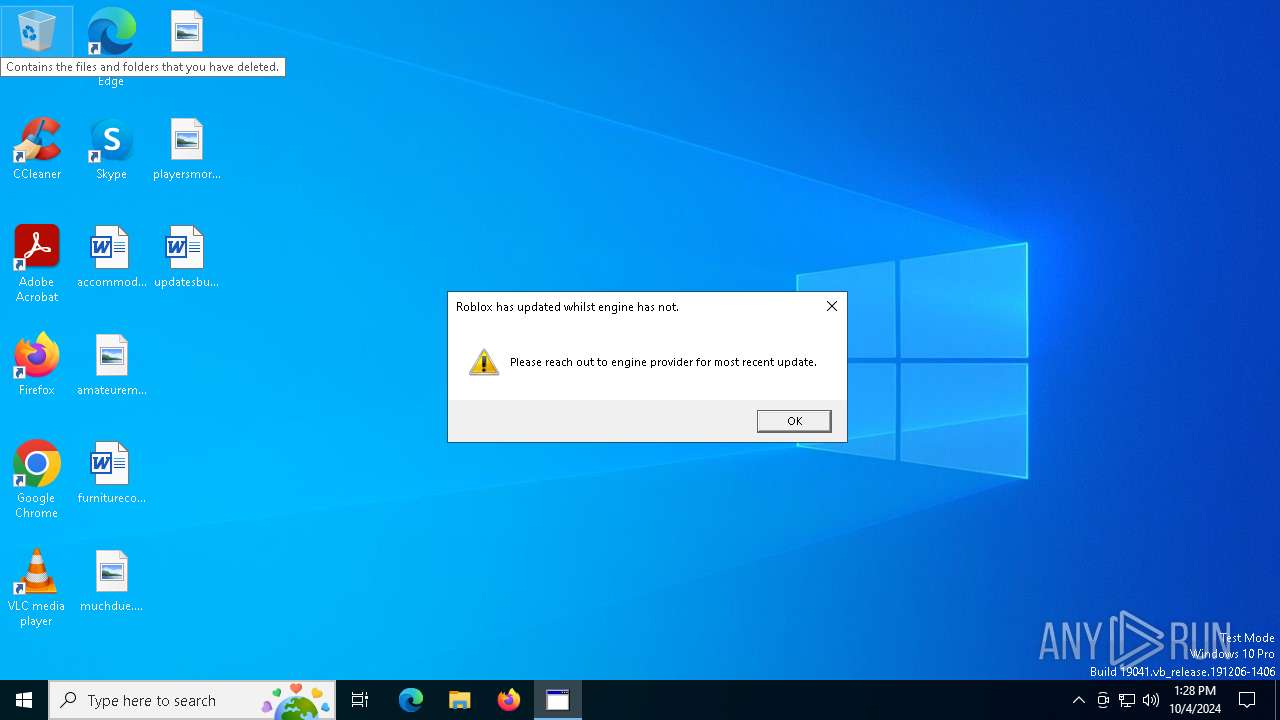
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | October 04, 2024, 13:27:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 11B6557986DA2FE9BB31DC3A72170D6F |
| SHA1: | C6964F84EF1AA1E09D2DB5A83F44819D6294D91F |
| SHA256: | 8D43C698222164B663D8BCF46EAA82947A7DF712984570472EB31F81BF167C9E |
| SSDEEP: | 98304:b6CeTRk+yQq4ANCz0dz3MCF7mbEelmPuxKS1HmTdozujquT3Jb3klaS/bXGYwcn7:9Q/V1ppxy27bv |
MALICIOUS
BlankGrabber has been detected
- SolaraV3.exe (PID: 6704)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 2128)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3356)
- SolaraV3.exe (PID: 6152)
- cmd.exe (PID: 6344)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 5796)
- MpCmdRun.exe (PID: 7600)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 5796)
Bypass execution policy to execute commands
- powershell.exe (PID: 7368)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3852)
DISCORDGRABBER has been detected (YARA)
- SolaraV3.exe (PID: 6152)
GROWTOPIA has been detected (YARA)
- SolaraV3.exe (PID: 6152)
Starts CMD.EXE for self-deleting
- SolaraV3.exe (PID: 6152)
Stealers network behavior
- SolaraV3.exe (PID: 6152)
BLANKGRABBER has been detected (SURICATA)
- SolaraV3.exe (PID: 6152)
SUSPICIOUS
Starts a Microsoft application from unusual location
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 872)
- SolaraV3.exe (PID: 400)
- SolaraV3.exe (PID: 6152)
Process drops legitimate windows executable
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 400)
- SolaraV3.exe (PID: 6152)
Process drops python dynamic module
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 400)
Executable content was dropped or overwritten
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 400)
- SolaraV3.exe (PID: 6152)
- csc.exe (PID: 7752)
Application launched itself
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 400)
The process drops C-runtime libraries
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 400)
Starts CMD.EXE for commands execution
- SolaraV3.exe (PID: 872)
- SolaraV3.exe (PID: 6152)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4804)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 3300)
Found strings related to reading or modifying Windows Defender settings
- SolaraV3.exe (PID: 872)
- SolaraV3.exe (PID: 6152)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 2816)
- cmd.exe (PID: 2804)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3356)
- cmd.exe (PID: 6344)
Get information on the list of running processes
- SolaraV3.exe (PID: 6152)
- cmd.exe (PID: 1252)
- cmd.exe (PID: 6776)
- cmd.exe (PID: 3116)
- cmd.exe (PID: 1084)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3356)
- cmd.exe (PID: 4100)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 5796)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 7920)
- cmd.exe (PID: 3836)
- cmd.exe (PID: 5760)
- cmd.exe (PID: 7596)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 5796)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6264)
- cmd.exe (PID: 4712)
- cmd.exe (PID: 7240)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 2868)
- cmd.exe (PID: 7032)
- cmd.exe (PID: 5688)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 4920)
Script disables Windows Defender's IPS
- cmd.exe (PID: 5796)
Starts application with an unusual extension
- cmd.exe (PID: 1008)
- cmd.exe (PID: 7284)
- cmd.exe (PID: 7808)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7952)
- cmd.exe (PID: 3836)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 6496)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 3852)
Base64-obfuscated command line is found
- cmd.exe (PID: 3852)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3852)
Possible usage of Discord/Telegram API has been detected (YARA)
- SolaraV3.exe (PID: 6152)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 1020)
Checks for external IP
- svchost.exe (PID: 2256)
- SolaraV3.exe (PID: 6152)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6504)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 5676)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 5144)
Hides command output
- cmd.exe (PID: 8144)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8144)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7752)
INFO
Create files in a temporary directory
- SolaraV3.exe (PID: 6704)
- SolaraV3.exe (PID: 872)
Reads the computer name
- SolaraV3.exe (PID: 6704)
Checks supported languages
- SolaraV3.exe (PID: 872)
- SolaraV3.exe (PID: 6704)
The Powershell gets current clipboard
- powershell.exe (PID: 7248)
PyInstaller has been detected (YARA)
- SolaraV3.exe (PID: 400)
- SolaraV3.exe (PID: 6152)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 7768)
UPX packer has been detected
- SolaraV3.exe (PID: 6152)
Attempting to use instant messaging service
- SolaraV3.exe (PID: 6152)
- svchost.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6152) SolaraV3.exe
Discord-Webhook-Tokens (1)1290002102000554126/KOOwGK23t6uheX7Oni3YuTk6tczcIbEx3wL-l8amzq5-zGZMSOI5nhiSdaM6SQkKAuJJ
Discord-Info-Links
1290002102000554126/KOOwGK23t6uheX7Oni3YuTk6tczcIbEx3wL-l8amzq5-zGZMSOI5nhiSdaM6SQkKAuJJ
Get Webhook Infohttps://discord.com/api/webhooks/1290002102000554126/KOOwGK23t6uheX7Oni3YuTk6tczcIbEx3wL-l8amzq5-zGZMSOI5nhiSdaM6SQkKAuJJ
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:29 17:28:37+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 172032 |
| InitializedDataSize: | 94208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcdb0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.4355 |
| ProductVersionNumber: | 10.0.19041.4355 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Windows Diagnosis and Recovery |
| FileVersion: | 10.0.19041.4355 (WinBuild.160101.0800) |
| InternalName: | RelPost.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | RelPost.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.4355 |
Total processes
277
Monitored processes
143
Malicious processes
7
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\WINDOWS\system32\ComputerDefaults.exe" --nouacbypass | C:\Windows\System32\ComputerDefaults.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Set Program Access and Computer Defaults Control Panel Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | "C:\Users\admin\AppData\Local\Temp\SolaraV3.exe" | C:\Users\admin\AppData\Local\Temp\SolaraV3.exe | ComputerDefaults.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Diagnosis and Recovery Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\Users\admin\AppData\Local\Temp\SolaraV3.exe" | C:\Users\admin\AppData\Local\Temp\SolaraV3.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Diagnosis and Recovery Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | C:\WINDOWS\system32\cmd.exe /c "tree /A /F" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | C:\WINDOWS\system32\cmd.exe /c "netsh wlan show profile" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | SolaraV3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
61 040
Read events
61 027
Write events
9
Delete events
4
Modification events
| (PID) Process: | (5520) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (2128) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2128) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2128) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2128) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5164) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5164) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5164) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5164) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6152) SolaraV3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Multimedia\DrawDib |
| Operation: | write | Name: | 1280x720x32(BGR 0) |
Value: 31,31,31,31 | |||
Executable files
38
Suspicious files
9
Text files
51
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_ctypes.pyd | executable | |
MD5:FA360B7044312E7404704E1A485876D2 | SHA256:F06C3491438F6685938789C319731DDF64BA1DA02CD71F43AB8829AF0E3F4E2F | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_hashlib.pyd | executable | |
MD5:3A4A3A99A4A4ADAF60B9FAAF6A3EDBDA | SHA256:26EED7AAC1C142A83A236C5B35523A0922F14D643F6025DC3886398126DAE492 | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_lzma.pyd | executable | |
MD5:BAD668BBF4F0D15429F66865AF4C117B | SHA256:45B1FCDF4F3F97F9881AAA98B00046C4045B897F4095462C0BC4631DBADAC486 | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_queue.pyd | executable | |
MD5:326E66D3CF98D0FA1DB2E4C9F1D73E31 | SHA256:BF6A8C5872D995EDAB5918491FA8721E7D1B730F66C8404EE760C1E30CB1F40E | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_ssl.pyd | executable | |
MD5:E33BF2BC6C19BF37C3CC8BAC6843D886 | SHA256:E3532D3F8C5E54371F827B9E6D0FEE175AD0B2B17E25C26FDFB4EFD5126B7288 | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\libssl-3.dll | executable | |
MD5:264BE59FF04E5DCD1D020F16AAB3C8CB | SHA256:358B59DA9580E7102ADFC1BE9400ACEA18BC49474DB26F2F8BACB4B8839CE49D | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_decimal.pyd | executable | |
MD5:B7012443C9C31FFD3AED70FE89AA82A0 | SHA256:3B92D5CA6268A5AD0E92E5E403C621C56B17933DEF9D8C31E69AB520C30930D9 | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_sqlite3.pyd | executable | |
MD5:5F31F58583D2D1F7CB54DB8C777D2B1E | SHA256:FAD9FFCD3002CEC44C3DA9D7D48CE890D6697C0384B4C7DACAB032B42A5AC186 | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\libffi-8.dll | executable | |
MD5:08B000C3D990BC018FCB91A1E175E06E | SHA256:135C772B42BA6353757A4D076CE03DBF792456143B42D25A62066DA46144FECE | |||
| 6704 | SolaraV3.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\libcrypto-3.dll | executable | |
MD5:7F1B899D2015164AB951D04EBB91E9AC | SHA256:41201D2F29CF3BC16BF32C8CECF3B89E82FEC3E5572EB38A578AE0FB0C5A2986 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
47
DNS requests
22
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3528 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5092 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6152 | SolaraV3.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
6152 | SolaraV3.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
7284 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7284 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2356 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6152 | SolaraV3.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | shared |
696 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
blank-bpqng.in |
| unknown |
ip-api.com |
| shared |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
gstatic.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6152 | SolaraV3.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6152 | SolaraV3.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6152 | SolaraV3.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6152 | SolaraV3.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |