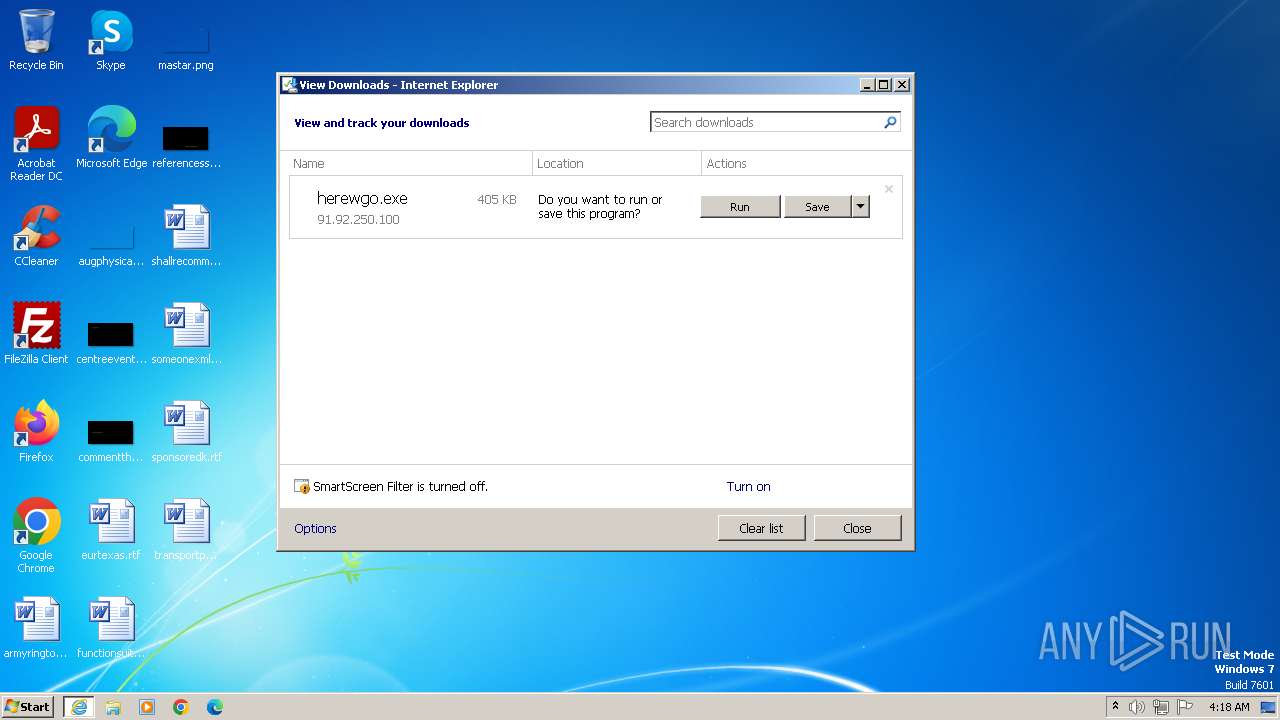
| URL: | http://91.92.250.100/herewgo.exe |
| Full analysis: | https://app.any.run/tasks/e4ab5d23-c8f6-4248-9746-a5b9d4a57de6 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | December 02, 2023, 04:17:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F2473B0C1A189F868032D59B1F5C754F |
| SHA1: | 0342999CEAFBB01ABFFE364E21F767730BF5CD46 |
| SHA256: | 8D36C96D843EC90BCF389C2766EB342DB13974488026EE207E4FF9A4D552A588 |
| SSDEEP: | 3:N1K0lNdQAC:C0XnC |
MALICIOUS
Drops the executable file immediately after the start
- herewgo.exe (PID: 2964)
Steals credentials from Web Browsers
- doubbdi.exe (PID: 1152)
Actions looks like stealing of personal data
- doubbdi.exe (PID: 1152)
Connects to the CnC server
- doubbdi.exe (PID: 1152)
AGENTTESLA has been detected (SURICATA)
- doubbdi.exe (PID: 1152)
AGENTTESLA has been detected (YARA)
- doubbdi.exe (PID: 1152)
SUSPICIOUS
Application launched itself
- doubbdi.exe (PID: 2600)
Reads the Internet Settings
- doubbdi.exe (PID: 1152)
Connects to FTP
- doubbdi.exe (PID: 1152)
Connects to unusual port
- doubbdi.exe (PID: 1152)
Accesses Microsoft Outlook profiles
- doubbdi.exe (PID: 1152)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 3816)
- iexplore.exe (PID: 3060)
Application launched itself
- iexplore.exe (PID: 3060)
Manual execution by a user
- wmpnscfg.exe (PID: 2632)
Checks supported languages
- wmpnscfg.exe (PID: 2632)
- doubbdi.exe (PID: 1152)
- doubbdi.exe (PID: 2600)
- herewgo.exe (PID: 2964)
Reads the computer name
- wmpnscfg.exe (PID: 2632)
- herewgo.exe (PID: 2964)
- doubbdi.exe (PID: 1152)
- doubbdi.exe (PID: 2600)
The process uses the downloaded file
- iexplore.exe (PID: 3060)
Create files in a temporary directory
- herewgo.exe (PID: 2964)
Reads Environment values
- doubbdi.exe (PID: 1152)
Reads the machine GUID from the registry
- doubbdi.exe (PID: 1152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(1152) doubbdi.exe
Protocolftp
Hostftp://ftp.elquijotebanquetes.com
Usernamehusband@elquijotebanquetes.com
PasswordkFxADjwNBm$_
Total processes
43
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1152 | "C:\Users\admin\AppData\Local\Temp\doubbdi.exe" | C:\Users\admin\AppData\Local\Temp\doubbdi.exe | doubbdi.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
AgentTesla(PID) Process(1152) doubbdi.exe Protocolftp Hostftp://ftp.elquijotebanquetes.com Usernamehusband@elquijotebanquetes.com PasswordkFxADjwNBm$_ | |||||||||||||||
| 2600 | "C:\Users\admin\AppData\Local\Temp\doubbdi.exe" | C:\Users\admin\AppData\Local\Temp\doubbdi.exe | — | herewgo.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\herewgo.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\herewgo.exe | — | iexplore.exe | |||||||||||
User: admin Company: pasture Integrity Level: MEDIUM Description: smoke Exit code: 0 Version: 1.9.8.8 Modules
| |||||||||||||||
| 3060 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://91.92.250.100/herewgo.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3816 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3060 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
13 212
Read events
13 157
Write events
55
Delete events
0
Modification events
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
8
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\herewgo[1].exe | executable | |
MD5:730C9CBF6BE3CCDE55618E0E47AB4134 | SHA256:83ED4E8912F569CB017EEC244E2CC21920B357F5BE64E6D95C7332025FD12422 | |||
| 3060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9DA1E5CEEC95E61586AED2C1564F1420 | SHA256:0C6934E96DD491589FE9CE19E6EA60B42F9D7BCC689EC3EAB48EE560256481CD | |||
| 2964 | herewgo.exe | C:\Users\admin\AppData\Local\Temp\doubbdi.exe | executable | |
MD5:5A1232108D4D199C99DE71A08C45F068 | SHA256:1EAF29F23168F7506F681545F3355EAFEFA715D574D7F5E68A5523B6B4D92F55 | |||
| 3060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{C70E0E7F-90C9-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:51B495EC8CD4A1DC15B0352B9FC19EB7 | SHA256:BDEC8F7CED4CDB42AFF91DA375CD65F6BDDAD2453FD98BC16CB946EE7857D21F | |||
| 3060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:2A69A0928017DEF69D83C26544FEBFAA | SHA256:BA34A528EFBEE2411E20299C594FEA42FBEBCB9A4EC73967AAF961B168796439 | |||
| 3816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\herewgo.exe.fj6uyr0.partial | executable | |
MD5:8BFD7886121330ACA3002B5B1E768740 | SHA256:03B950D316F2E66E637A9CFDD2F769D5A53296B0459DF9CB6ED0FC0D25282958 | |||
| 3060 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB5EDD5E8A3CE42F3.TMP | binary | |
MD5:C0C90BD54FD0C8B009E8A9CA0916DF27 | SHA256:88851E0506F373DEE5CADC49B13DED04DF227243E148FFE2C8ECD0BA1E73562F | |||
| 3060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\herewgo.exe | executable | |
MD5:8BFD7886121330ACA3002B5B1E768740 | SHA256:03B950D316F2E66E637A9CFDD2F769D5A53296B0459DF9CB6ED0FC0D25282958 | |||
| 3060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\herewgo.exe.fj6uyr0.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2964 | herewgo.exe | C:\Users\admin\AppData\Local\Temp\pxqopxxmqh.mzk | binary | |
MD5:043BDF6ECD9749B3947423BC584F7AF9 | SHA256:E53E05F266CA0F1E7E5F7C5FC91DF1C9801CC708BE3AE080F994AEF1C2EF011C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
15
DNS requests
7
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3816 | iexplore.exe | GET | 200 | 91.92.250.100:80 | http://91.92.250.100/herewgo.exe | unknown | executable | 405 Kb | unknown |
3060 | iexplore.exe | GET | 200 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?851c751b721441d0 | unknown | compressed | 4.66 Kb | unknown |
3060 | iexplore.exe | GET | 200 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7bb6036743caffca | unknown | compressed | 4.66 Kb | unknown |
3060 | iexplore.exe | GET | 200 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?89bed1f5828b50f8 | unknown | compressed | 4.66 Kb | unknown |
3060 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3816 | iexplore.exe | 91.92.250.100:80 | — | — | BG | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1152 | doubbdi.exe | 143.95.79.226:21 | ftp.elquijotebanquetes.com | ASMALLORANGE1 | US | unknown |
1152 | doubbdi.exe | 143.95.79.226:33782 | ftp.elquijotebanquetes.com | ASMALLORANGE1 | US | unknown |
3060 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3060 | iexplore.exe | 23.32.238.219:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3060 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ftp.elquijotebanquetes.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3816 | iexplore.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3816 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3816 | iexplore.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1152 | doubbdi.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
1152 | doubbdi.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
1152 | doubbdi.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
2 ETPRO signatures available at the full report