| File name: | 9.z |
| Full analysis: | https://app.any.run/tasks/4e473207-f39e-48ee-afc9-d9038267896d |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | August 13, 2019, 12:55:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-lzh-compressed |
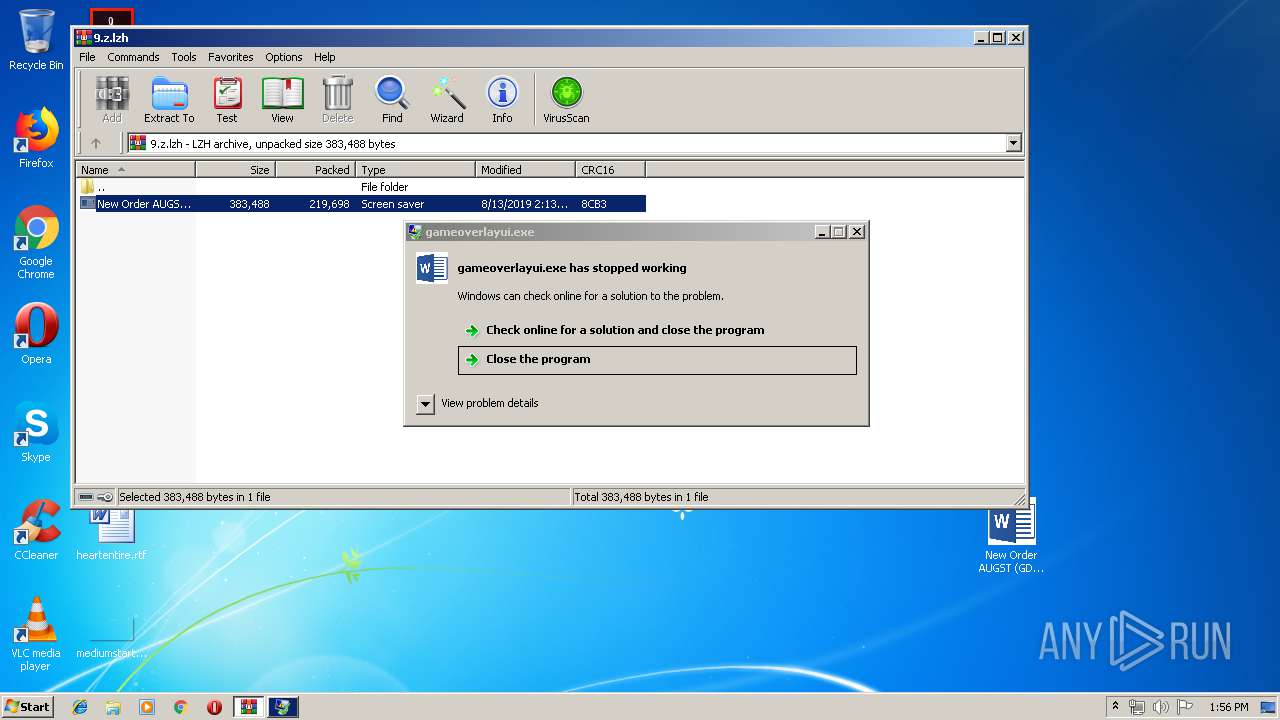
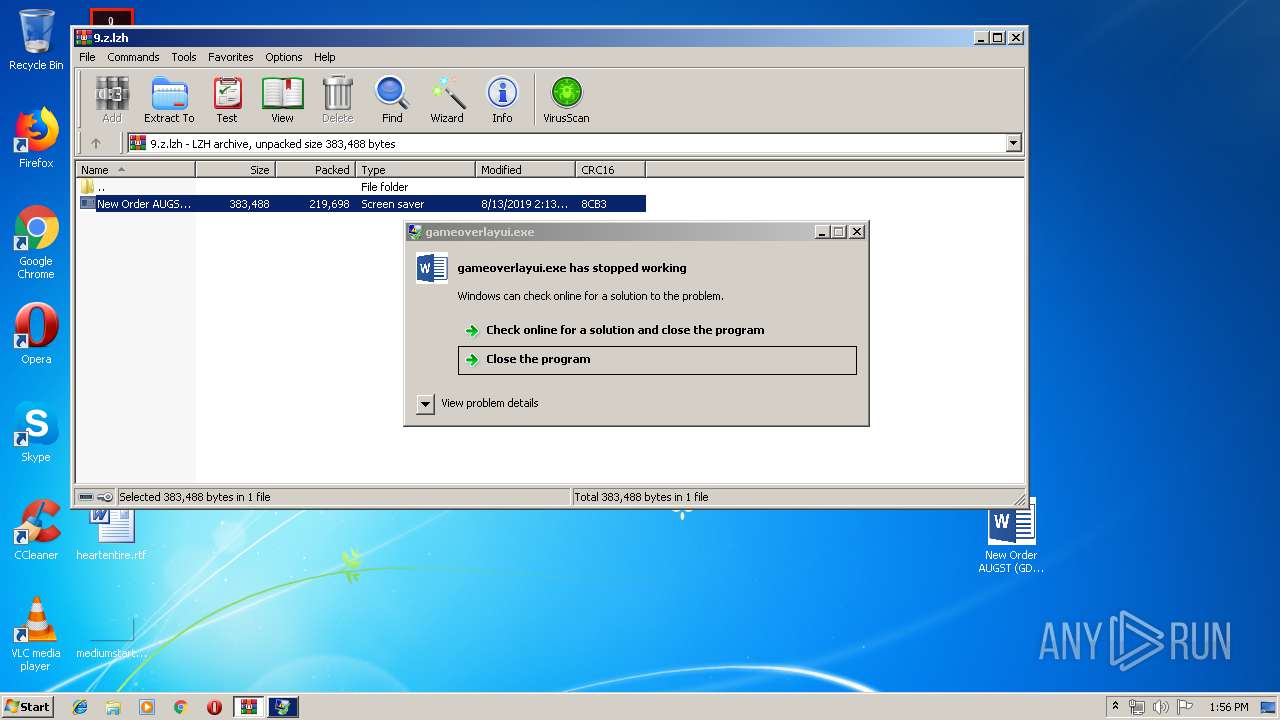
| File info: | LHa (2.x) archive data [lh5], with "New Order AUGST (GD-2607019)_Docx.scr" |
| MD5: | 9639E3561745563F1082ECCEAFB16FA1 |
| SHA1: | 6553F44B58002400D5C00492E009B9F3D1D8EBC9 |
| SHA256: | 8C4EF0EA5EEB5C1F43EA929ED187EE7D9A435DD85BBEE9F43198A9F3F4FB1DC7 |
| SSDEEP: | 6144:TG1DITLyz/LyOvoSFlNMVIalis0GZwGya66lv:mc8zFllNM7PZNy10v |
MALICIOUS
Application was dropped or rewritten from another process
- New Order AUGST (GD-2607019)_Docx.scr (PID: 4008)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 1208)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 956)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3728)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3588)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 2736)
Connects to CnC server
- New Order AUGST (GD-2607019)_Docx.scr (PID: 1208)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 956)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3588)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 2736)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3728)
AVEMARIA was detected
- New Order AUGST (GD-2607019)_Docx.scr (PID: 1208)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 956)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3728)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3588)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 2736)
SUSPICIOUS
Starts application with an unusual extension
- New Order AUGST (GD-2607019)_Docx.scr (PID: 4008)
Reads the machine GUID from the registry
- New Order AUGST (GD-2607019)_Docx.scr (PID: 1208)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 956)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3728)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3588)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 2736)
Connects to unusual port
- New Order AUGST (GD-2607019)_Docx.scr (PID: 1208)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 956)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3588)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 2736)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3728)
Application launched itself
- New Order AUGST (GD-2607019)_Docx.scr (PID: 4008)
INFO
Manual execution by user
- New Order AUGST (GD-2607019)_Docx.scr (PID: 4008)
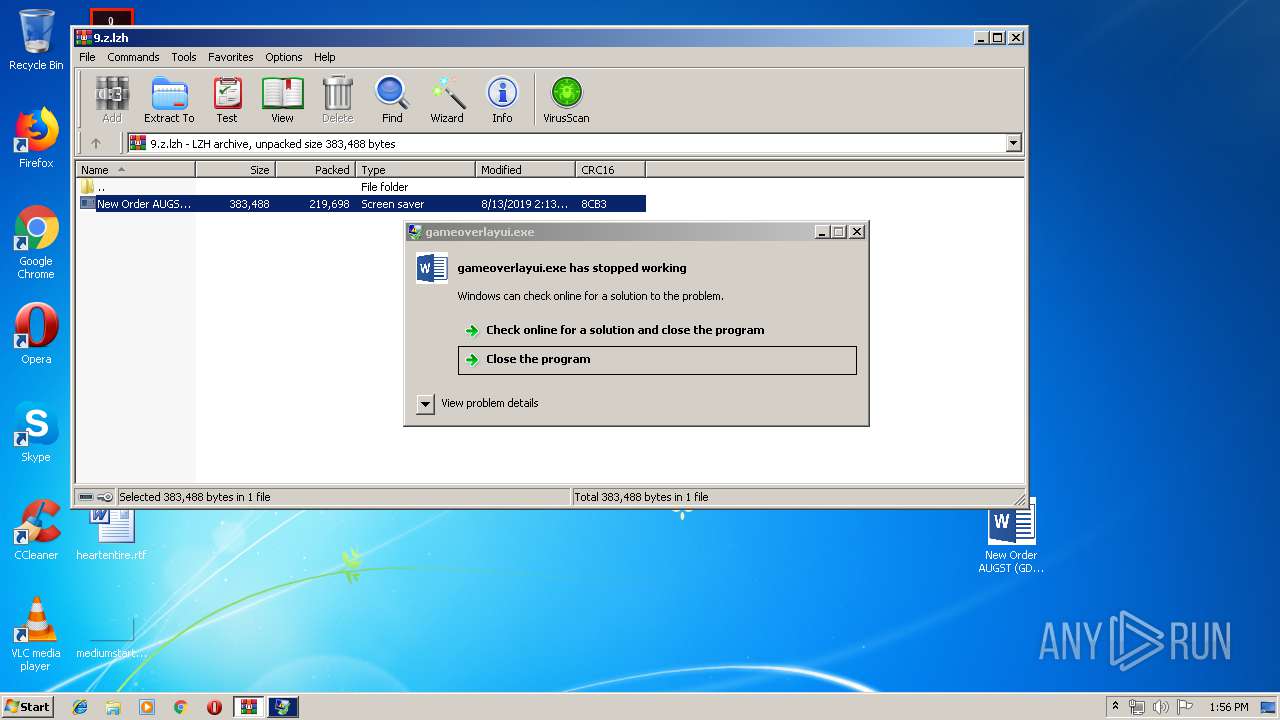
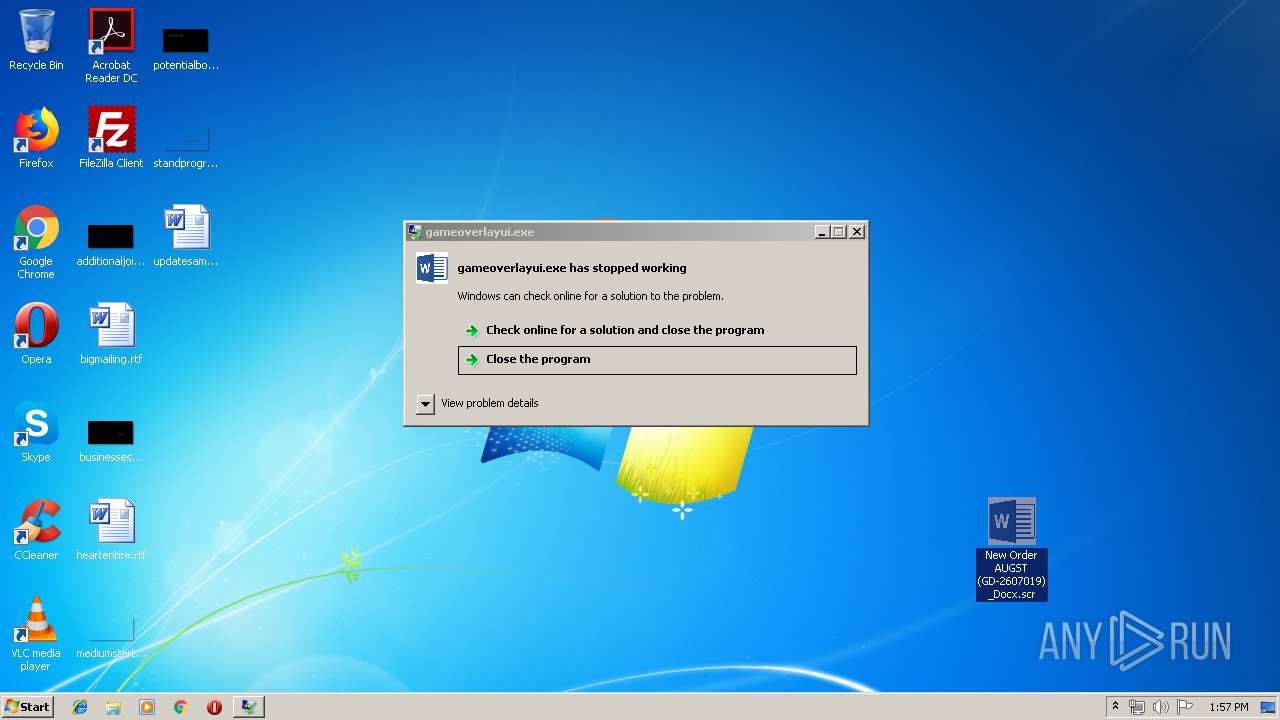
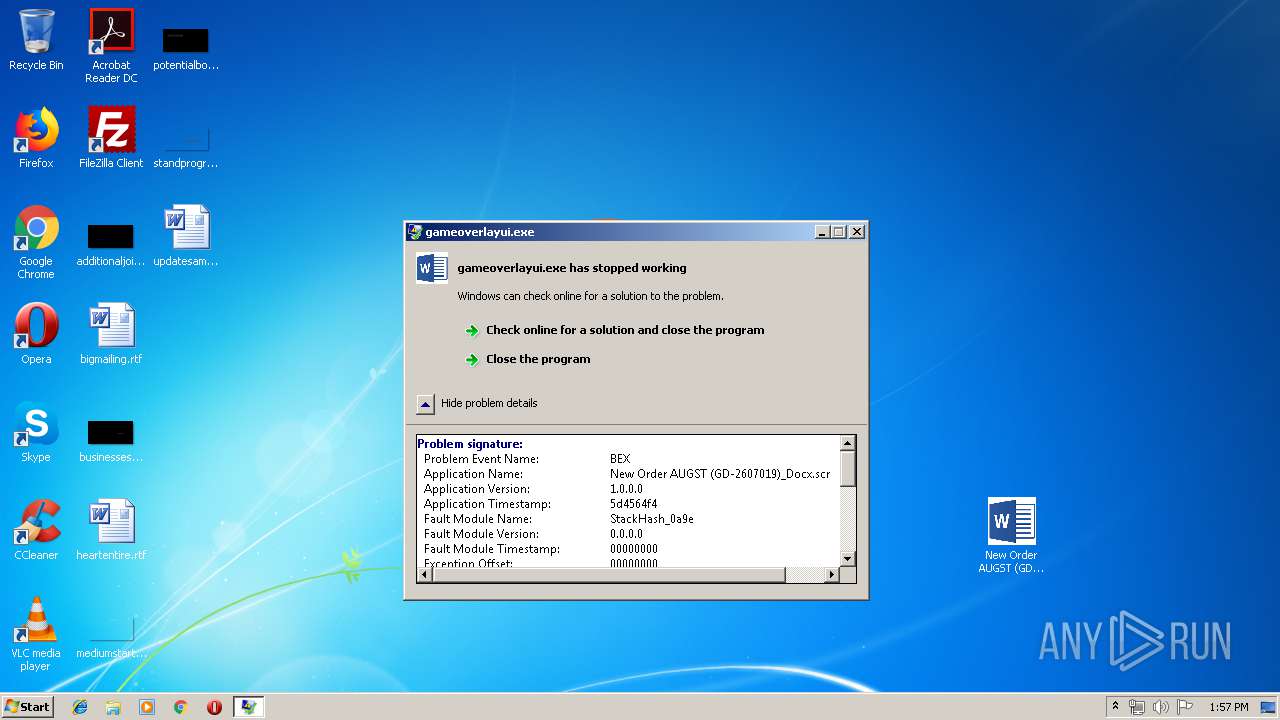
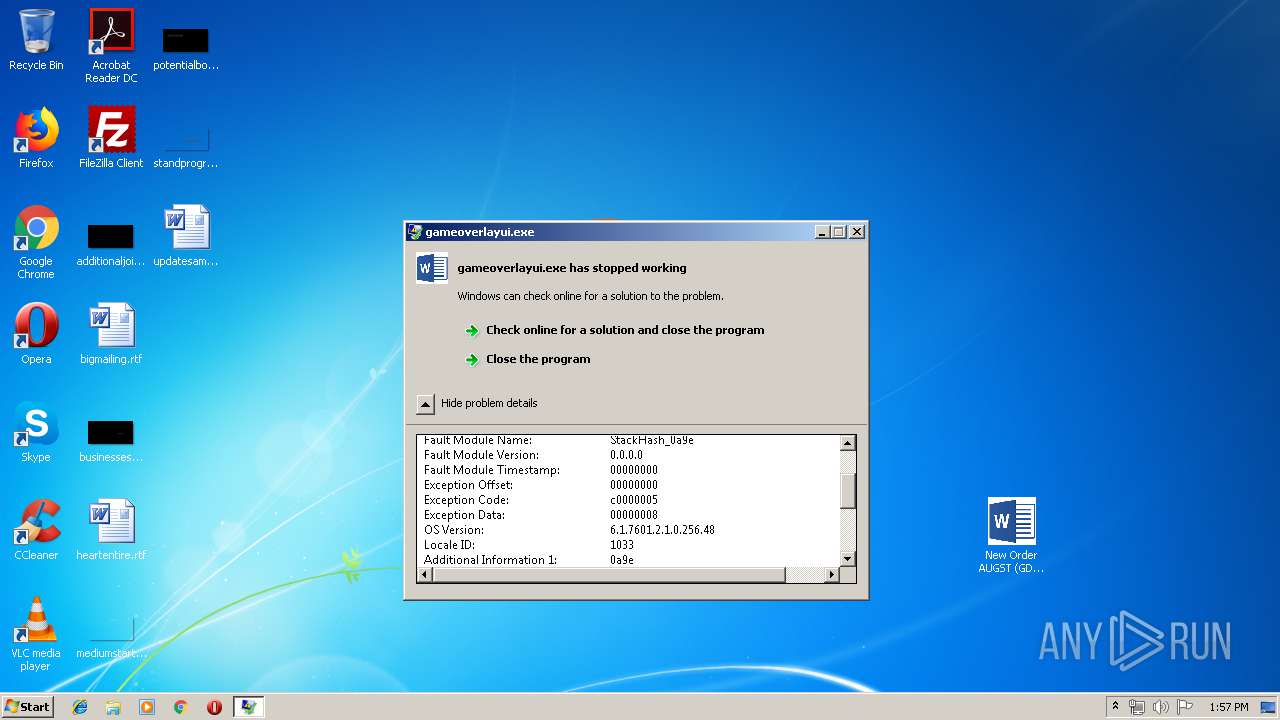
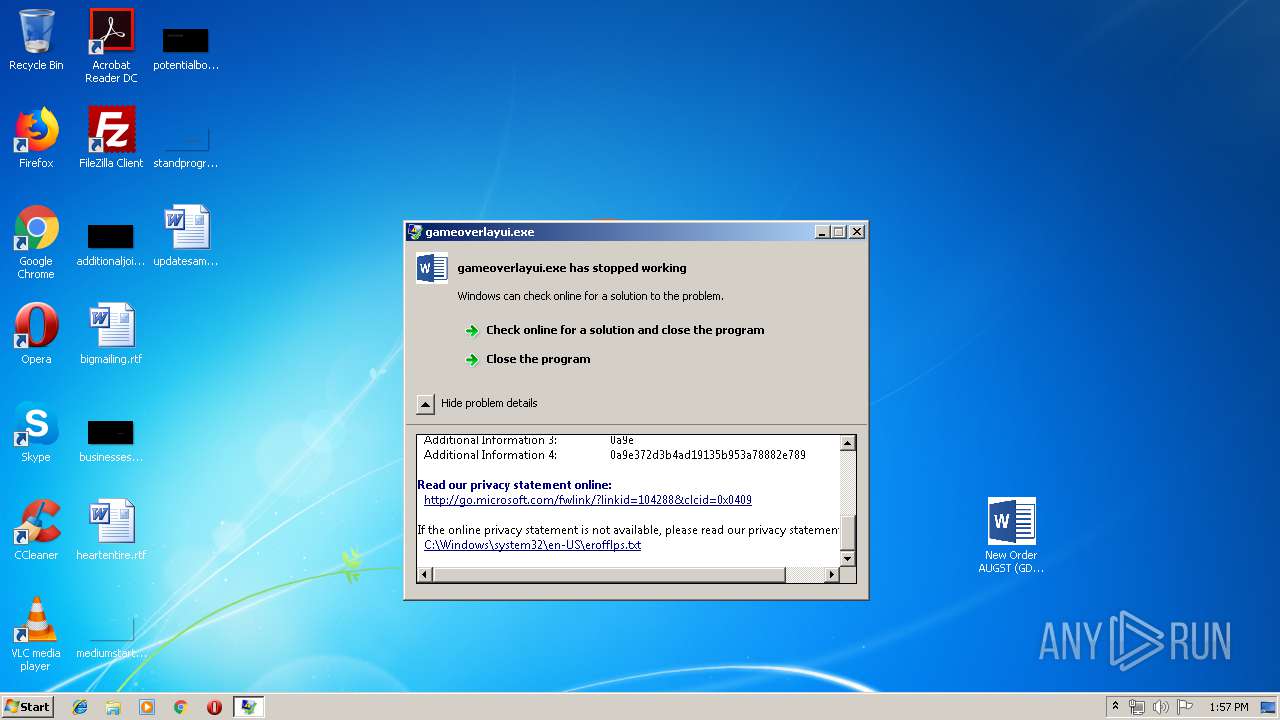
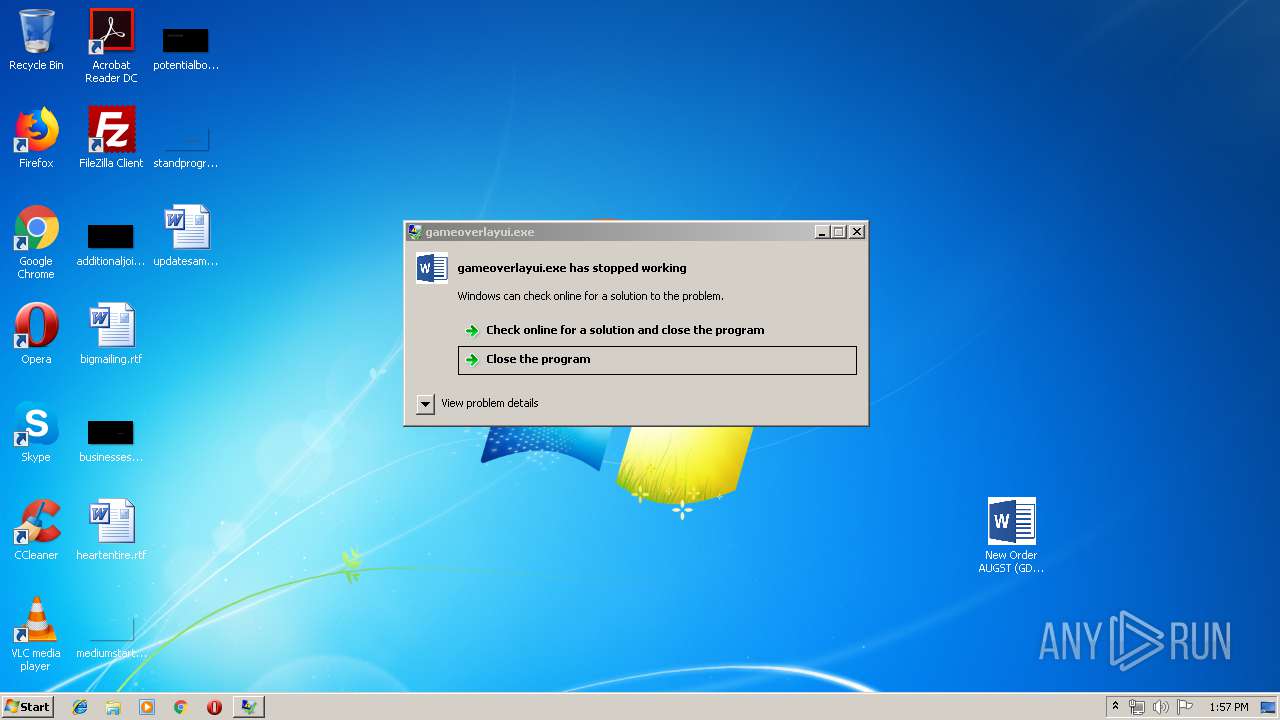
Application was crashed
- New Order AUGST (GD-2607019)_Docx.scr (PID: 1208)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 956)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3728)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 3588)
- New Order AUGST (GD-2607019)_Docx.scr (PID: 2736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lzh/lha | | | LHARC/LZARK compressed archive (generic) (100) |
|---|
Total processes
47
Monitored processes
7
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr" | C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr | New Order AUGST (GD-2607019)_Docx.scr | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameoverlayui.exe Exit code: 3221225477 Version: 05.05.99.96 Modules
| |||||||||||||||
| 1208 | "C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr" | C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr | New Order AUGST (GD-2607019)_Docx.scr | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameoverlayui.exe Exit code: 3221225477 Version: 05.05.99.96 Modules
| |||||||||||||||
| 2612 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\9.z.lzh" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2736 | "C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr" | C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr | New Order AUGST (GD-2607019)_Docx.scr | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameoverlayui.exe Exit code: 0 Version: 05.05.99.96 Modules
| |||||||||||||||
| 3588 | "C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr" | C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr | New Order AUGST (GD-2607019)_Docx.scr | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameoverlayui.exe Exit code: 3221225477 Version: 05.05.99.96 Modules
| |||||||||||||||
| 3728 | "C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr" | C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr | New Order AUGST (GD-2607019)_Docx.scr | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameoverlayui.exe Exit code: 3221225477 Version: 05.05.99.96 Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr" /S | C:\Users\admin\Desktop\New Order AUGST (GD-2607019)_Docx.scr | explorer.exe | ||||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: gameoverlayui.exe Exit code: 0 Version: 05.05.99.96 Modules
| |||||||||||||||
Total events
546
Read events
515
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\9.z.lzh | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2612) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
| (PID) Process: | (1208) New Order AUGST (GD-2607019)_Docx.scr | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | MaxConnectionsPer1_0Server |
Value: 10 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2612.44564\New Order AUGST (GD-2607019)_Docx.scr | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
2
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1208 | New Order AUGST (GD-2607019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
956 | New Order AUGST (GD-2607019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
3588 | New Order AUGST (GD-2607019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
3728 | New Order AUGST (GD-2607019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
2736 | New Order AUGST (GD-2607019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ndubaba45.warzonedns.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1208 | New Order AUGST (GD-2607019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
956 | New Order AUGST (GD-2607019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
3728 | New Order AUGST (GD-2607019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
3588 | New Order AUGST (GD-2607019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
2736 | New Order AUGST (GD-2607019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
New Order AUGST (GD-2607019)_Docx.scr |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|