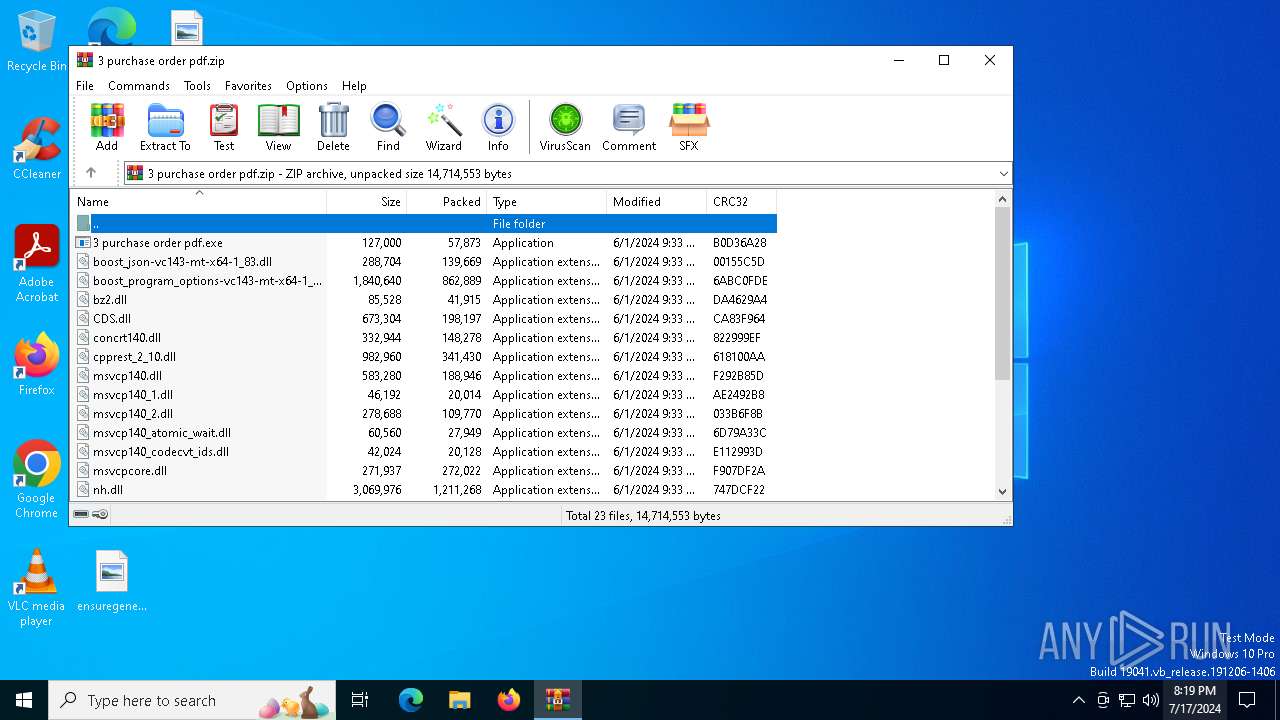
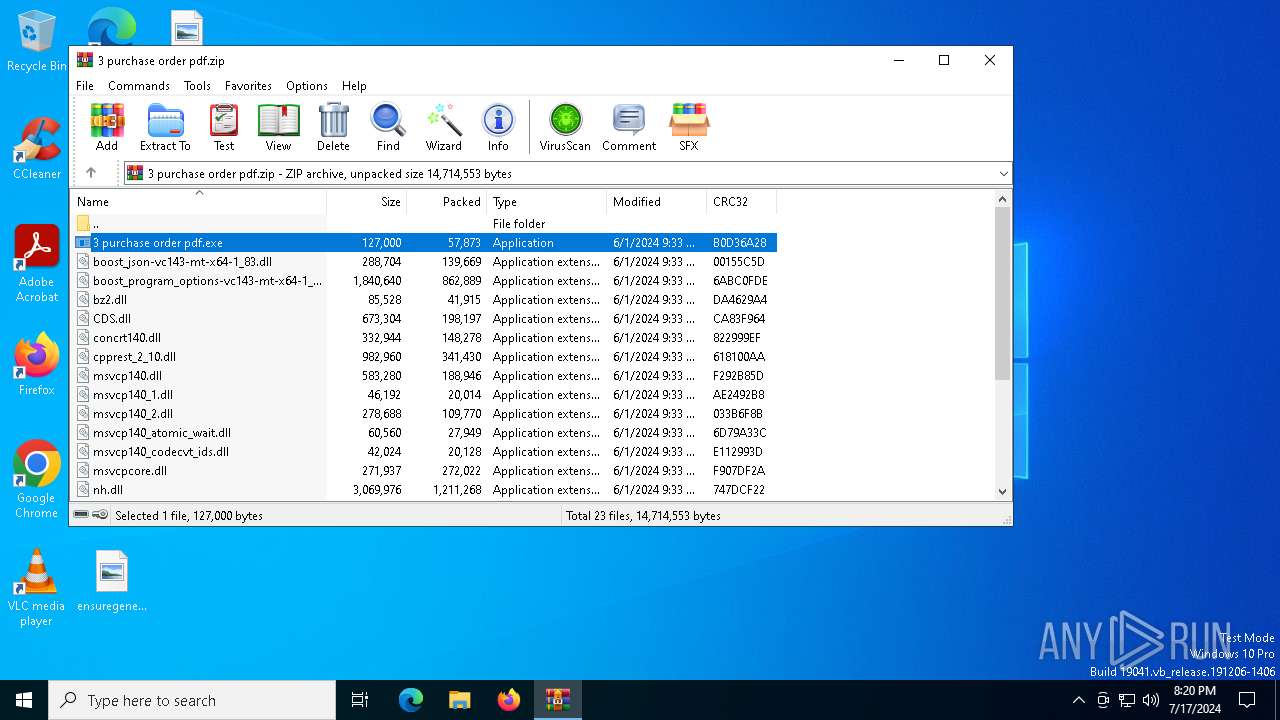
| File name: | 3 purchase order pdf.zip |
| Full analysis: | https://app.any.run/tasks/ef05a08e-5519-4bbd-abbf-176983012a29 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 17, 2024, 20:19:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0CD7C60ADD215A4C965914F4F525BBB6 |
| SHA1: | 626F5153D1AA19BBFB7C94B9ED6DA93CAB409F65 |
| SHA256: | 8C301FFE8EF0B54EF616B0705EDA116301EFA779B8CB34C8893523EF675A6BAE |
| SSDEEP: | 98304:9PEwdSnDA9WrEeUiqFBHUaYIy9ymDNnnbP/at9S/EWInMBoQG7Qt7o7Bv/gz9XzE:YvVFRO |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6340)
FORMBOOK has been detected (YARA)
- UserAccountControlSettings.exe (PID: 5584)
Connects to the CnC server
- WinRAR.exe (PID: 6340)
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 6340)
Stealers network behavior
- WinRAR.exe (PID: 6340)
Actions looks like stealing of personal data
- UserAccountControlSettings.exe (PID: 5584)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6340)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6340)
Starts a Microsoft application from unusual location
- 3 purchase order pdf.exe (PID: 2212)
- 3 purchase order pdf.exe (PID: 6640)
Creates file in the systems drive root
- WinRAR.exe (PID: 6340)
The process executes VB scripts
- 3 purchase order pdf.exe (PID: 6640)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6340)
Checks supported languages
- 3 purchase order pdf.exe (PID: 2212)
- ngen.exe (PID: 3596)
- 3 purchase order pdf.exe (PID: 6640)
- vbc.exe (PID: 6864)
Reads the computer name
- 3 purchase order pdf.exe (PID: 2212)
- 3 purchase order pdf.exe (PID: 6640)
Reads security settings of Internet Explorer
- UserAccountControlSettings.exe (PID: 5584)
Create files in a temporary directory
- UserAccountControlSettings.exe (PID: 5584)
Manual execution by a user
- 3 purchase order pdf.exe (PID: 6640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(5584) UserAccountControlSettings.exe
C2www.loves777.net
Strings (160)+6NUqrti51cWEdb/OtPV
8OK1mc7r5cRVo0NBt+6U
Jh9Kjxi1VhavdLVxk4b0tF2fQRY=
aohZmwxDA0y7noMtw8DvZw==
1fJSAbd814NB6u+jh2A7cA==
93RWtN/ewFG5h0p8cgJo+ahcSvC9zA==
DASLtEcFCtpK
/bQZbG1cmVJiQnE=
3NoWHuLzl03/
966RUidXxTMUhEYomwnMFQ==
3xqIrwa1HR0se1bJ82M=
+HnP9Yd7IgORlA==
yoQLRdQoMfUbfWKRNA==
VNuSIBbIb8dUJ1i2y4mPWw==
lhFyejjo2HKFh4j/i4syphQ=
JYVAFE4/fkyX
Am1amyIOk/lJPgP/RuY=
OBKFU78oHwJo
i2hB+d/2b4rznw==
QiDlAeUJ/GtOeYj2/VX//lTybz69aw==
0wqF3MpjiBxeGTw=
mVrETb2OdUawR23YN/934A==
L9xJxP4kKef4UJwmPxKFXA==
9hkKaQVgCWy+1N7cxqN0YfegfMo=
R4bMbktPxfME2F5DWKwHAAa3tQ==
tFZ7GKaBT/mAfbI=
GT91bTeo+lBf
Ne6W8YqxEaBD8tSnF/DqMmwVOqId
NDU29wE+CFrBvXb9xGeY+w==
bnvuh1PLixQOFqZxcR7L9w==
mekg1aAxnvq8KJwuvuWQvts=
Ql8kVquPizq9DfqXGZE=
c3DAQoQ5KHVlFl+4cLL0wgA=
GWadfzIXG8N/dph8nxE=
/YRMurjTv3yBT8VTkw==
gCi28ed1s4kqdAKV7g==
unXXQ74JH1efDUEk3A==
B+ut6TyO1dVPIowg2kKO
XjapOVTEEg44/5BuHteSnv4Kpc8=
+Plk3TxWHFOVPoNyItVy
+jpQk4UB13icdA==
sxJwlPYd2AyzqhDsZ5NdNBMyUMM=
0LEFUM9jhbOQ1No=
vYaj7mrwcF8QRJb/P6+ITYxU
omDaqaGW5SGYfxl3tw==
VFa8PSIISAub9yutTt79
GE+mISa6Bsqn
o8BXUIm25DtR3W+QmuC8kw==
kk9Q5iboT0Zy
ST2VZDYPA4mhDo/DRrJ1
2p7b4JS0aeTSFscb3wMj
EsHQN/k5QAYkrt9fnIM=
drEiC4cd16CJ1UJBQzB6gPuo8QA=
uZff44PJrP4YO1bOVlk=
LAxzwGMXTICH9lIc5Bdn0ciXtAk=
vnHImUgmsMiiB1LkPiCh5a8hrv9i3g==
kKbTNXqq7sLpa0wPya4/tw==
EG2HA7fOcHmkjHmgIvA=
5dftibksCCKOsqqrXQ==
JmYr3umjd8IforGQ/xJWow==
/MRMbarYhkK3Oz153l8a5SggLg==
+BtqS/crXWoLKhd+
Z33RJHmmaoU/b9vEEw==
mJxBwFhXiN2WNxNBqILRnF8=
rMQ2UYv4yHgIM0LS7m9MWw==
UserAccountControlSettings.exe
proquota.exe
replace.exe
setupugc.exe
findstr.exe
icsunattend.exe
write.exe
rasdial.exe
wecutil.exe
cmmon32.exe
DpiScaling.exe
cmd.exe
kernel32.dll
advapi32.dll
ws2_32.dll
USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
COMPUTERNAME
ProgramFiles
/c copy "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Google\Chrome\User Data\Default\Login Data
SeShutdownPrivilege
\BaseNamedObjects
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control:
Origin: http://
Content-Type: application/x-www-form-urlencoded
Accept:
Referer: http://
Accept-Language:
Accept-Encoding:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
-noexit "& ""
PowerShell.exe
\Opera Software\Opera Stable
kernel32.dll
user32.dll
wininet.dll
rg.ini
Recovery
profiles.ini
guid
Connection: close
pass
token
email
login
signin
account
persistent
GET
GET
PUT
POST
OPTIONS
User-Agent:
API-
MS-W
_301 Moved
_302 Found
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:01 09:33:24 |
| ZipCRC: | 0xb0d36a28 |
| ZipCompressedSize: | 57873 |
| ZipUncompressedSize: | 127000 |
| ZipFileName: | 3 purchase order pdf.exe |
Total processes
147
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2212 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\3 purchase order pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\3 purchase order pdf.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Relaunch Outlook Exit code: 4294967295 Version: 1.2024.516.100 Modules
| |||||||||||||||
| 3596 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | 3 purchase order pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.8.9093.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 3660 | "C:\Program Files (x86)\Windows Mail\wab.exe" | C:\Program Files (x86)\Windows Mail\wab.exe | — | 3 purchase order pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 4216 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_wp.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_wp.exe | — | 3 purchase order pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_wp.exe Version: 4.8.9220.0 built by: NET481REL1LAST_C | |||||||||||||||
| 5584 | "C:\Windows\SysWOW64\UserAccountControlSettings.exe" | C:\Windows\SysWOW64\UserAccountControlSettings.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: UserAccountControlSettings Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
Formbook(PID) Process(5584) UserAccountControlSettings.exe C2www.loves777.net Strings (160)+6NUqrti51cWEdb/OtPV 8OK1mc7r5cRVo0NBt+6U Jh9Kjxi1VhavdLVxk4b0tF2fQRY= aohZmwxDA0y7noMtw8DvZw== 1fJSAbd814NB6u+jh2A7cA== 93RWtN/ewFG5h0p8cgJo+ahcSvC9zA== DASLtEcFCtpK /bQZbG1cmVJiQnE= 3NoWHuLzl03/ 966RUidXxTMUhEYomwnMFQ== 3xqIrwa1HR0se1bJ82M= +HnP9Yd7IgORlA== yoQLRdQoMfUbfWKRNA== VNuSIBbIb8dUJ1i2y4mPWw== lhFyejjo2HKFh4j/i4syphQ= JYVAFE4/fkyX Am1amyIOk/lJPgP/RuY= OBKFU78oHwJo i2hB+d/2b4rznw== QiDlAeUJ/GtOeYj2/VX//lTybz69aw== 0wqF3MpjiBxeGTw= mVrETb2OdUawR23YN/934A== L9xJxP4kKef4UJwmPxKFXA== 9hkKaQVgCWy+1N7cxqN0YfegfMo= R4bMbktPxfME2F5DWKwHAAa3tQ== tFZ7GKaBT/mAfbI= GT91bTeo+lBf Ne6W8YqxEaBD8tSnF/DqMmwVOqId NDU29wE+CFrBvXb9xGeY+w== bnvuh1PLixQOFqZxcR7L9w== mekg1aAxnvq8KJwuvuWQvts= Ql8kVquPizq9DfqXGZE= c3DAQoQ5KHVlFl+4cLL0wgA= GWadfzIXG8N/dph8nxE= /YRMurjTv3yBT8VTkw== gCi28ed1s4kqdAKV7g== unXXQ74JH1efDUEk3A== B+ut6TyO1dVPIowg2kKO XjapOVTEEg44/5BuHteSnv4Kpc8= +Plk3TxWHFOVPoNyItVy +jpQk4UB13icdA== sxJwlPYd2AyzqhDsZ5NdNBMyUMM= 0LEFUM9jhbOQ1No= vYaj7mrwcF8QRJb/P6+ITYxU omDaqaGW5SGYfxl3tw== VFa8PSIISAub9yutTt79 GE+mISa6Bsqn o8BXUIm25DtR3W+QmuC8kw== kk9Q5iboT0Zy ST2VZDYPA4mhDo/DRrJ1 2p7b4JS0aeTSFscb3wMj EsHQN/k5QAYkrt9fnIM= drEiC4cd16CJ1UJBQzB6gPuo8QA= uZff44PJrP4YO1bOVlk= LAxzwGMXTICH9lIc5Bdn0ciXtAk= vnHImUgmsMiiB1LkPiCh5a8hrv9i3g== kKbTNXqq7sLpa0wPya4/tw== EG2HA7fOcHmkjHmgIvA= 5dftibksCCKOsqqrXQ== JmYr3umjd8IforGQ/xJWow== /MRMbarYhkK3Oz153l8a5SggLg== +BtqS/crXWoLKhd+ Z33RJHmmaoU/b9vEEw== mJxBwFhXiN2WNxNBqILRnF8= rMQ2UYv4yHgIM0LS7m9MWw== UserAccountControlSettings.exe proquota.exe replace.exe setupugc.exe findstr.exe icsunattend.exe write.exe rasdial.exe wecutil.exe cmmon32.exe DpiScaling.exe cmd.exe kernel32.dll advapi32.dll ws2_32.dll USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP COMPUTERNAME ProgramFiles /c copy " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \Mail\ \Foxmail \Storage\ \Accounts\Account.rec0 \Data\AccCfg\Accounts.tdat \Google\Chrome\User Data\Default\Login Data SeShutdownPrivilege \BaseNamedObjects POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: Origin: http:// Content-Type: application/x-www-form-urlencoded Accept: Referer: http:// Accept-Language: Accept-Encoding: Set-ExecutionPolicy RemoteSigned -Scope CurrentUser -noexit "& "" PowerShell.exe \Opera Software\Opera Stable kernel32.dll user32.dll wininet.dll rg.ini Recovery profiles.ini guid Connection: close pass token email login signin account persistent GET GET PUT POST OPTIONS User-Agent: API- MS-W _301 Moved _302 Found InternetOpenA InternetConnectA HttpOpenRequestA HttpSendRequestA InternetReadFile InternetCloseHandle | |||||||||||||||
| 5880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 3 purchase order pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6340 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\3 purchase order pdf.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6640 | "C:\temp\3 purchase order pdf.exe" | C:\temp\3 purchase order pdf.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Relaunch Outlook Exit code: 4294967295 Version: 1.2024.516.100 Modules
| |||||||||||||||
| 6812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 3 purchase order pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6864 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | — | 3 purchase order pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.9037.0 Modules
| |||||||||||||||
Total events
7 409
Read events
7 378
Write events
31
Delete events
0
Modification events
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\3 purchase order pdf.zip | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
44
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\boost_program_options-vc143-mt-x64-1_83.dll | executable | |
MD5:77E040FD0C12D6B7BCCFD4DF71A016C1 | SHA256:BC63D4BCD55E3ABD6E8A983CC3737FD3506AE8278CF4CB9ECE6DFBF15D8DF05B | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\boost_json-vc143-mt-x64-1_83.dll | executable | |
MD5:ED3A8E7C94355E8602AA19FC7A071F42 | SHA256:83891B4D0196C72194F64522EA889D25D2308E3B4AB756E15D08BE35B72F7AA9 | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\msvcp140_2.dll | executable | |
MD5:864F1DD2877255152CBC350332529DD1 | SHA256:49CF4726950198ACD81EA227F9570547501051E7041C94E31C0F026BE9B518A4 | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\3 purchase order pdf.exe | executable | |
MD5:9556C9CE5194F7090B05211B460251C7 | SHA256:D8CA3CF209EEC87E8E9F1CE63917A2BCE05EA136FCE5F1E2B17FE80F02C914DD | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\msvcp140.dll | executable | |
MD5:1A469FACDC27FA0B4373F381F0B45D7E | SHA256:965F6C802E45B921B4B48F2AD6661DD847979805BCC7E5FA2A6EE70B629D0962 | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\concrt140.dll | executable | |
MD5:74FE183CA37A8ED96501222DAAF83845 | SHA256:6ED7024127918C9773E4387A433642FB068077815ABEE5C5EC77093DAED87D04 | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\msvcp140_1.dll | executable | |
MD5:9C0C08B94908FC226C486417F1A06AE4 | SHA256:6D6F9B38823924630C6C6F3DAEFC6E759279FFAA99FBDF849B84005FD7FBF755 | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\nh.dll | executable | |
MD5:E2DBCFBCAE1D8C7C8742FB8CC132466D | SHA256:18615A134C3EB906DF1001F40C4115B9F2C0376B890E940813666A43121E5551 | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\msvcp140_atomic_wait.dll | executable | |
MD5:A459E15F2010E2F03A128E23F46A2F32 | SHA256:D6F7ECDB4A3020F8F0B3E80A3E1F7745A2D0D919DCCDC73496B67A72C4ECB89C | |||
| 6340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6340.41345\msvcp140_codecvt_ids.dll | executable | |
MD5:00D856720E0FD11DBB46F8207D9939C7 | SHA256:0EFA94B059E6B87AA07C22DBFB9E41D2F7FFE82F816B341919E2CB8451753185 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
97
DNS requests
26
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4448 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4448 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6636 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
244 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
244 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6340 | WinRAR.exe | GET | 200 | 3.33.130.190:80 | http://www.poodlemum.com/9iv7/?n6S=aq4KOKETz46CQ1v8t4lWHT5H6OCeQpfOFbSSEj5SpS0jAe4teaMh2Gw4RZYK7LL3FQMfnjl9qqYlnZnqHQG3M78p7b9jvY79cJtJaGBK3xGG+OaixUXkY3ieCnZVNMvZGH8MvAQ=&TOl=huR6Iipqvlnb1ftj | unknown | — | — | whitelisted |
6340 | WinRAR.exe | POST | — | 3.33.130.190:80 | http://www.rejuvxd.services/3i0u/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1376 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4448 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4448 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4656 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5600 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
6340 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
25 ETPRO signatures available at the full report