| File name: | images.scr |
| Full analysis: | https://app.any.run/tasks/fc0c8b7b-118f-4a47-94f9-2d2d4ec2ea18 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | April 23, 2018, 09:45:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 3B367C3AA2426235679CD485DCFD6AE8 |
| SHA1: | 514D0C633D50157E74E976DF0C1B5DCF9F51ED24 |
| SHA256: | 8BEE95131AE47D9A5E3C8CCCCEAAAD7E5567EAC66AE7C0D875C9A57D3FC7ACEF |
| SSDEEP: | 98304:DuUaI9OMzejqikpYbAI7XLyhq6IvorAJKn6kD801cgl0+BhV1C8q0DBAd:28Oxy61y6g38ScglnBh20FW |
MALICIOUS
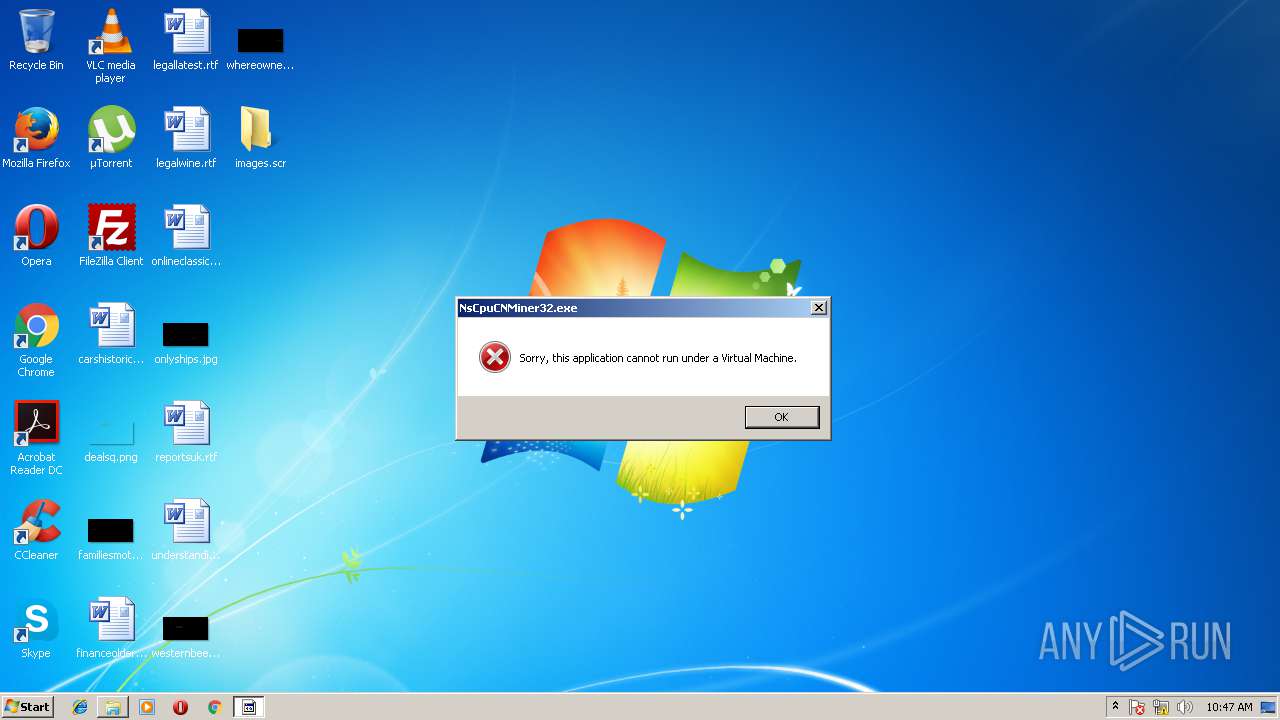
Looks like application has launched a miner
- image.exe (PID: 3172)
Application was dropped or rewritten from another process
- NsCpuCNMiner32.exe (PID: 4044)
Application loaded dropped or rewritten executable
- images.scr (PID: 432)
- image.exe (PID: 3172)
Writes to a start menu file
- image.exe (PID: 3172)
Changes the autorun value in the registry
- image.exe (PID: 3172)
SUSPICIOUS
Starts itself from another location
- images.scr (PID: 432)
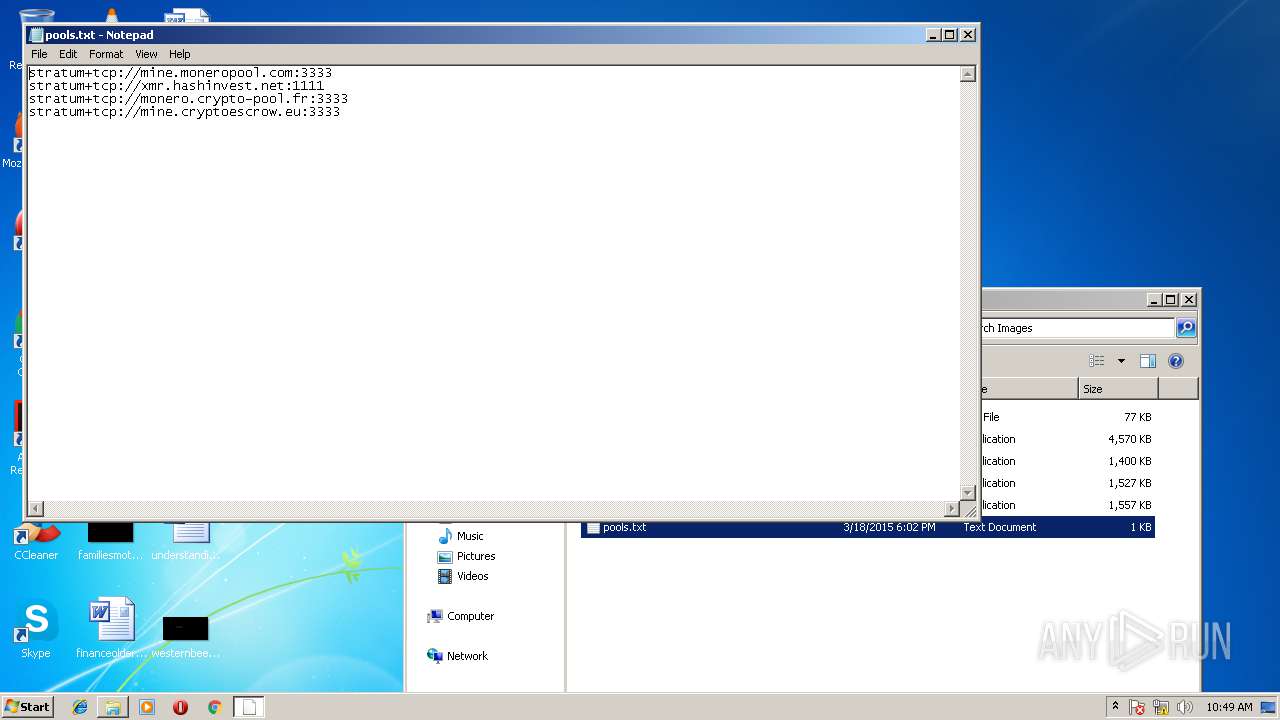
Dropped object may contain URLs of mainers pools
- image.exe (PID: 3172)
Creates files in the user directory
- image.exe (PID: 3172)
- images.scr (PID: 432)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 23:50:52+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.4 |
| ProductVersionNumber: | 2.0.0.4 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| Comments: | FOLDER |
| CompanyName: | |
| FileDescription: | Folder |
| FileVersion: | 0.4 |
| LegalCopyright: | Copyright © 2014 |
| LegalTrademarks: | |
| ProductName: | Images folder (x86-x64) |
| ProductVersion: | 0.2 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Dec-2009 22:50:52 |
| Detected languages: |
|
| Comments: | FOLDER |
| CompanyName: | - |
| FileDescription: | Folder |
| FileVersion: | 0.4 |
| LegalCopyright: | Copyright © 2014 |
| LegalTrademarks: | - |
| ProductName: | Images folder (x86-x64) |
| ProductVersion: | 0.2 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Dec-2009 22:50:52 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005C4C | 0x00005E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.44011 |
.rdata | 0x00007000 | 0x0000129C | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04684 |
.data | 0x00009000 | 0x00025C58 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.801 |
.ndata | 0x0002F000 | 0x0000B000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0003A000 | 0x0000DBE8 | 0x0000DC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.73459 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.20956 | 716 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.25726 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 4.82814 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 4.88878 | 3752 | UNKNOWN | English - United States | RT_ICON |
5 | 5.66607 | 2216 | UNKNOWN | English - United States | RT_ICON |
6 | 2.61351 | 1640 | UNKNOWN | English - United States | RT_ICON |
7 | 3.91485 | 1384 | UNKNOWN | English - United States | RT_ICON |
8 | 5.30461 | 1128 | UNKNOWN | English - United States | RT_ICON |
9 | 2.87102 | 744 | UNKNOWN | English - United States | RT_ICON |
10 | 2.92944 | 296 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
41
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Users\admin\Desktop\images.scr" /S | C:\Users\admin\Desktop\images.scr | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Folder Exit code: 2 Version: 0.4 Modules
| |||||||||||||||
| 896 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\Images\pools.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Roaming\Images\image.exe" SW_HIDE | C:\Users\admin\AppData\Roaming\Images\image.exe | images.scr | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Folder Exit code: 0 Version: 0.4 Modules
| |||||||||||||||
| 4044 | "C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner32.exe" -dbg -1 -o stratum+tcp://mine.moneropool.com:3333 -u 42NBK2ZZ1QgbgDeJPuFDjG3UKejbtay1wHdFbxq6pjvVYVG1rp85ucuJhoxtwf41dgV6G3LyfjaL3iXbiAwdtqLuB5DcrXv -p x | C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner32.exe | — | image.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3735929054 Modules
| |||||||||||||||
Total events
818
Read events
772
Write events
46
Delete events
0
Modification events
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (432) images.scr | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\images_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
7
Suspicious files
1
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3172 | image.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\image.lnk | lnk | |
MD5:— | SHA256:— | |||
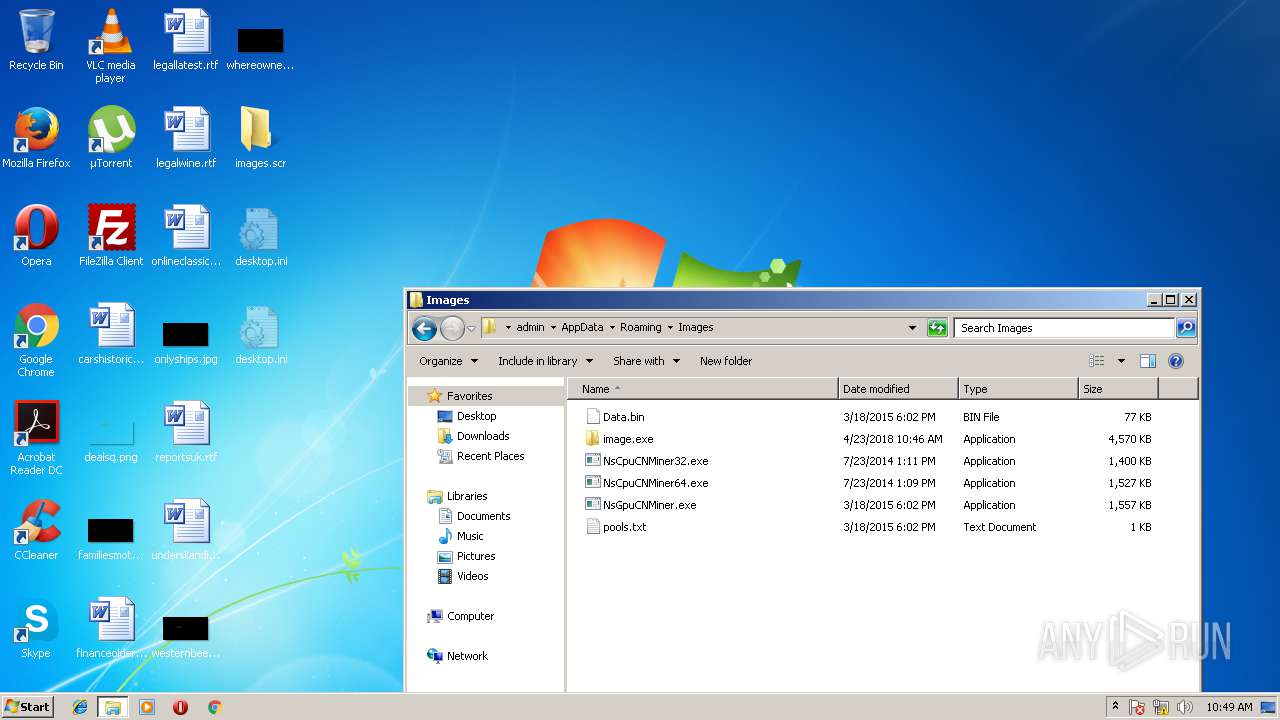
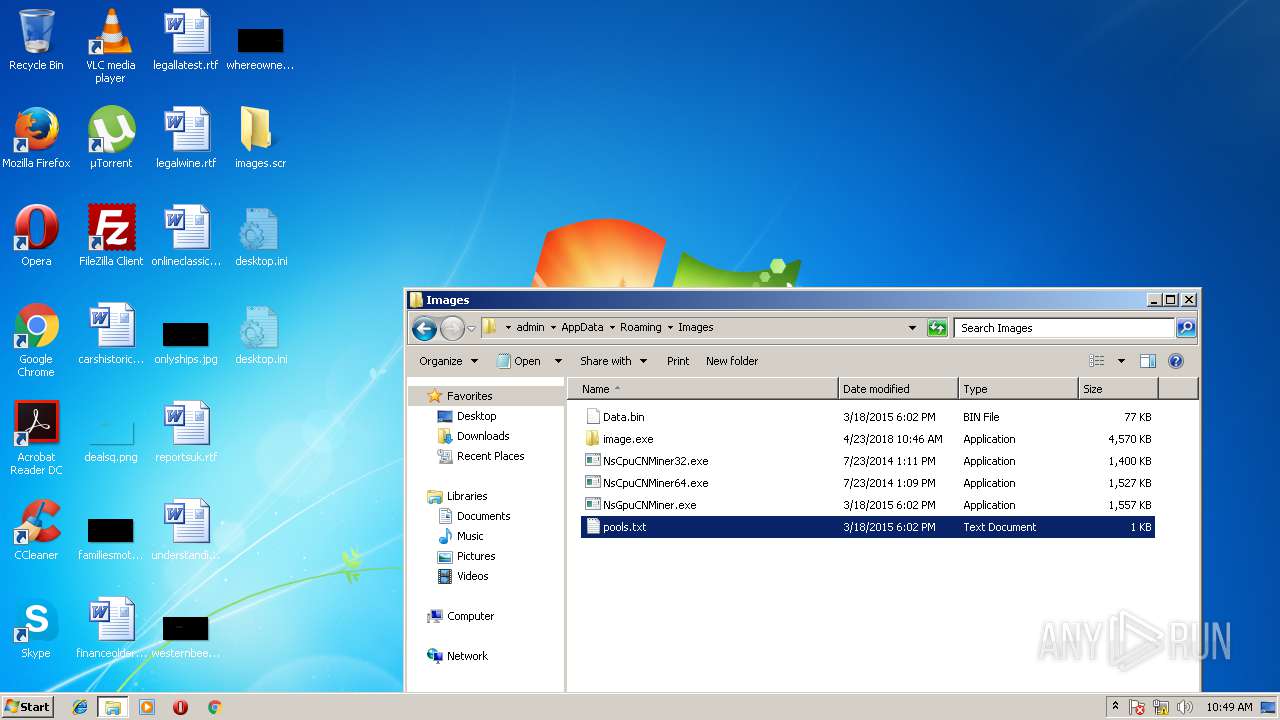
| 3172 | image.exe | C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner32.exe | executable | |
MD5:3AFEB8E9AF02A33FF71BF2F6751CAE3A | SHA256:A0EBA3FDA0D7B22A5D694105EC700DF7C7012DDC4AE611C3071EF858E2C69F08 | |||
| 432 | images.scr | C:\Users\admin\AppData\Roaming\Microsoft\Windows\IETldCache\index.dat | dat | |
MD5:D7A950FEFD60DBAA01DF2D85FEFB3862 | SHA256:75D0B1743F61B76A35B1FEDD32378837805DE58D79FA950CB6E8164BFA72073A | |||
| 3172 | image.exe | C:\Users\admin\AppData\Roaming\Images\NsGpuCNMiner.exe | executable | |
MD5:35D2C42B6EE0ACBCE9DFE8CC418FE5D8 | SHA256:7A2A860BB344526E8546ACD172522B4D276A4647F43DD4720281D40E390B283E | |||
| 3172 | image.exe | C:\Users\admin\AppData\Roaming\Images\Data.bin | binary | |
MD5:54EF305626A0EA8B3EB8B28B331E73E2 | SHA256:932055827D87637BA7E11565F22DDA3F09CC9457769788D94413E96CF346A6E4 | |||
| 3172 | image.exe | C:\Users\admin\AppData\Roaming\Images\tmp.ini | text | |
MD5:ACAF5EFC532BC6402BBFC03AD1C5F40C | SHA256:85AC75D560D635313A88FD2CAFDBBEE84EC9A4263D40B138E1F0C52E3DBDCA36 | |||
| 432 | images.scr | C:\Users\admin\AppData\Roaming\Images\image.exe | executable | |
MD5:3B367C3AA2426235679CD485DCFD6AE8 | SHA256:8BEE95131AE47D9A5E3C8CCCCEAAAD7E5567EAC66AE7C0D875C9A57D3FC7ACEF | |||
| 3172 | image.exe | C:\Users\admin\AppData\Roaming\Images\pools.txt | text | |
MD5:7DC8FD6041F1FD72D9CA2140D0973E5F | SHA256:B209B7AF96AB8DA92860BDA8856A4B5632E142011489DE12CAC9487FC22C652D | |||
| 3172 | image.exe | C:\Users\admin\AppData\Local\Temp\nse73F5.tmp\System.dll | executable | |
MD5:C17103AE9072A06DA581DEC998343FC1 | SHA256:DC58D8AD81CACB0C1ED72E33BFF8F23EA40B5252B5BB55D393A0903E6819AE2F | |||
| 432 | images.scr | C:\Users\admin\AppData\Local\Temp\nsv5012.tmp\inetc.dll | executable | |
MD5:D7A3FA6A6C738B4A3C40D5602AF20B08 | SHA256:67EFF17C53A78C8EC9A28F392B9BB93DF3E74F96F6ECD87A333A482C36546B3E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
6
DNS requests
4
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 91.235.116.58:80 | http://testswork.ru/test8.txt | RO | — | — | malicious |
— | — | GET | — | 91.235.116.58:80 | http://testswork.ru/test8.txt | RO | — | — | malicious |
— | — | GET | — | 91.235.116.58:80 | http://testswork.ru/test11.txt | RO | — | — | malicious |
— | — | GET | — | 91.235.116.58:80 | http://testswork.ru/test13.txt | RO | — | — | malicious |
— | — | GET | — | 91.235.116.58:80 | http://testswork.ru/test12.txt | RO | — | — | malicious |
— | — | GET | — | 91.235.116.58:80 | http://testswork.ru/test14.txt | RO | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.235.116.58:80 | testswork.ru | — | RO | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
teredo.ipv6.microsoft.com |
| whitelisted |
testswork.ru |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
— | — | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
— | — | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
— | — | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
— | — | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
— | — | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |