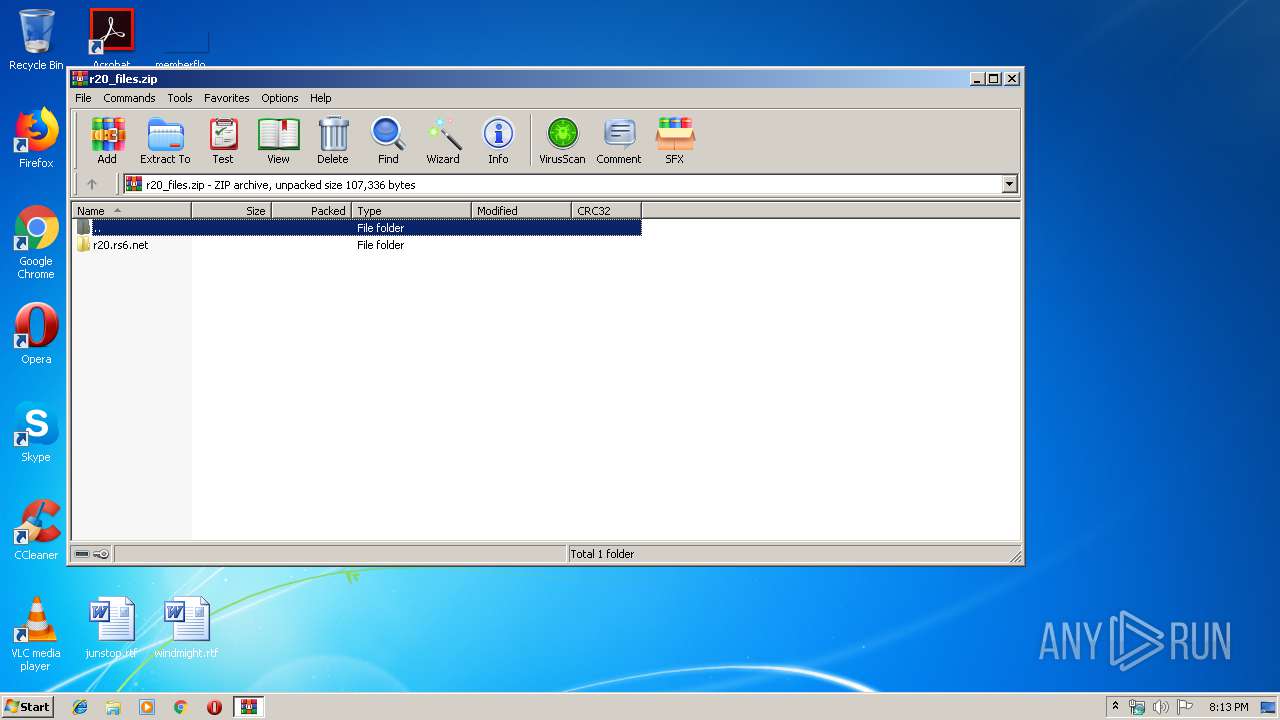
| File name: | r20_files.zip |
| Full analysis: | https://app.any.run/tasks/22908b7b-d1b7-4831-b259-8541ee0abfb9 |
| Verdict: | Malicious activity |
| Threats: | TrickBot is an advanced banking trojan that attackers can use to steal payment credentials from the victims. It can redirect the victim to a fake banking cabinet and retrieve credentials typed in on the webpage. |
| Analysis date: | December 06, 2019, 20:13:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 40821D62F8B272AEEB52DAFDCDF10B83 |
| SHA1: | C5258F2C6FBE8BD7FF9B5DFFE798F243EEC7F3CF |
| SHA256: | 8B7E41572B6FA43922ACF5169CDB0BBAC7F799AFF79A72F62B597C680BA9402F |
| SSDEEP: | 1536:QVf57ZfijyDmjLoV6UwxqQxausvpcbYkDCin9+JFLpM0l+E:greHoAxfxa5AVn98F9PoE |
MALICIOUS
Application was dropped or rewritten from another process
- E346.exe (PID: 2208)
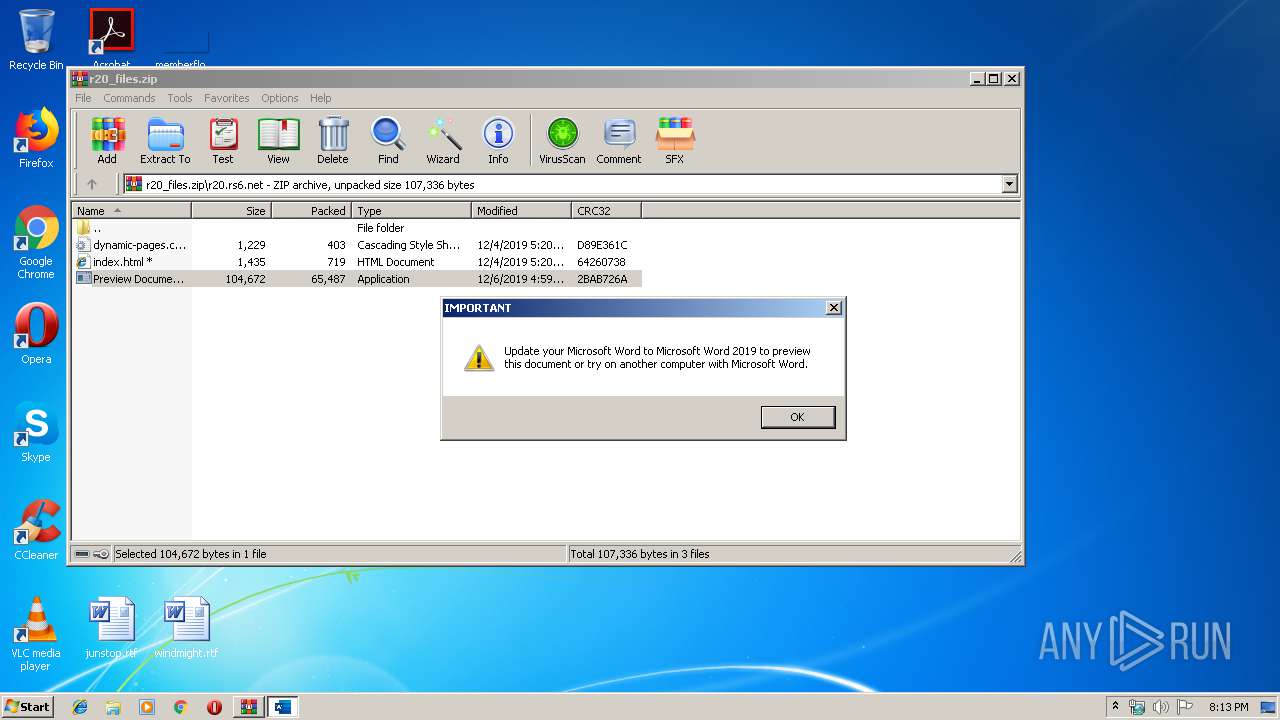
- Preview Document.exe (PID: 2344)
- E348.exe (PID: 2416)
- E348.exe (PID: 2280)
Loads the Task Scheduler COM API
- E346.exe (PID: 2208)
TRICKBOT was detected
- E346.exe (PID: 2208)
Known privilege escalation attack
- DllHost.exe (PID: 3752)
Connects to CnC server
- E346.exe (PID: 2208)
SUSPICIOUS
Creates files in the user directory
- Preview Document.exe (PID: 2344)
- E346.exe (PID: 2208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2576)
- Preview Document.exe (PID: 2344)
- E346.exe (PID: 2208)
Executed via Task Scheduler
- E348.exe (PID: 2280)
Executed via COM
- DllHost.exe (PID: 3752)
Checks for external IP
- E346.exe (PID: 2208)
INFO
Application launched itself
- iexplore.exe (PID: 2604)
Changes internet zones settings
- iexplore.exe (PID: 2604)
Manual execution by user
- iexplore.exe (PID: 2604)
Reads Internet Cache Settings
- iexplore.exe (PID: 3840)
Reads internet explorer settings
- iexplore.exe (PID: 3840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:12:06 16:59:02 |
| ZipCRC: | 0x2bab726a |
| ZipCompressedSize: | 65487 |
| ZipUncompressedSize: | 104672 |
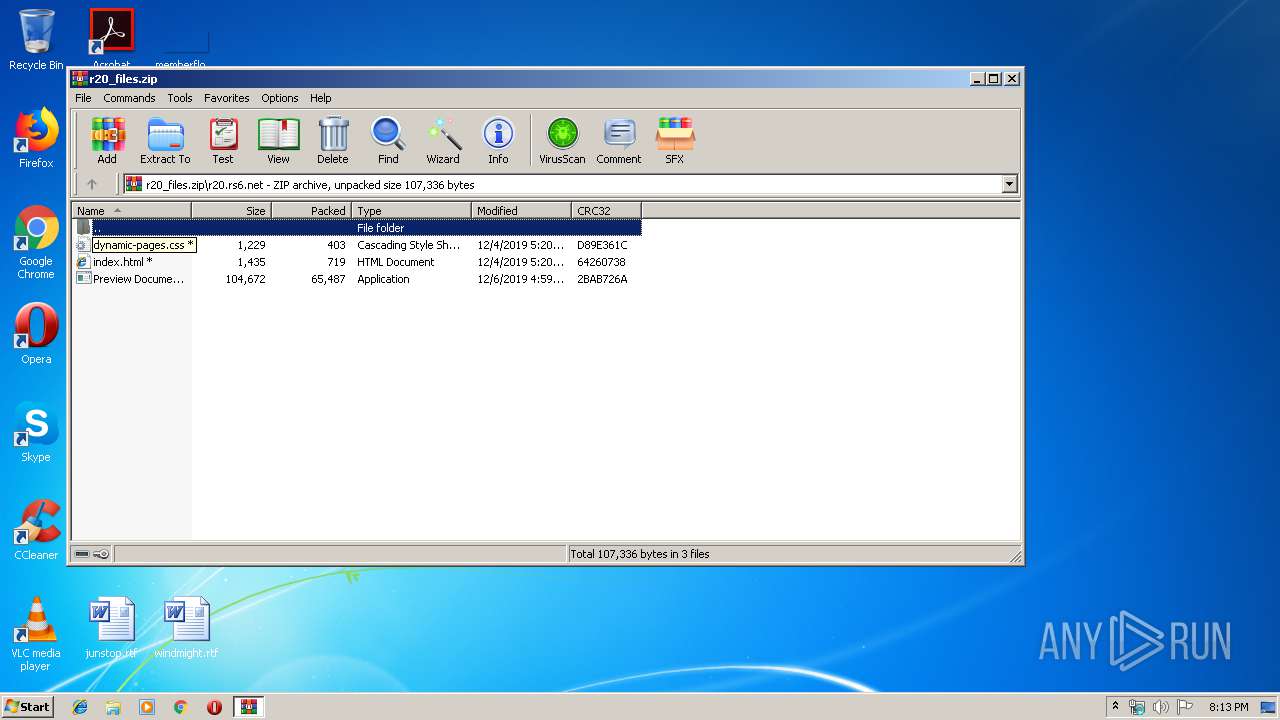
| ZipFileName: | r20.rs6.net/Preview Document.exe |
Total processes
43
Monitored processes
8
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2208 | C:\Users\admin\AppData\Local\Temp\E346.exe | C:\Users\admin\AppData\Local\Temp\E346.exe | Preview Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: MDI_Notepad MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2280 | C:\Users\admin\AppData\Roaming\syshealth\E348.exe | C:\Users\admin\AppData\Roaming\syshealth\E348.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: MDI_Notepad MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
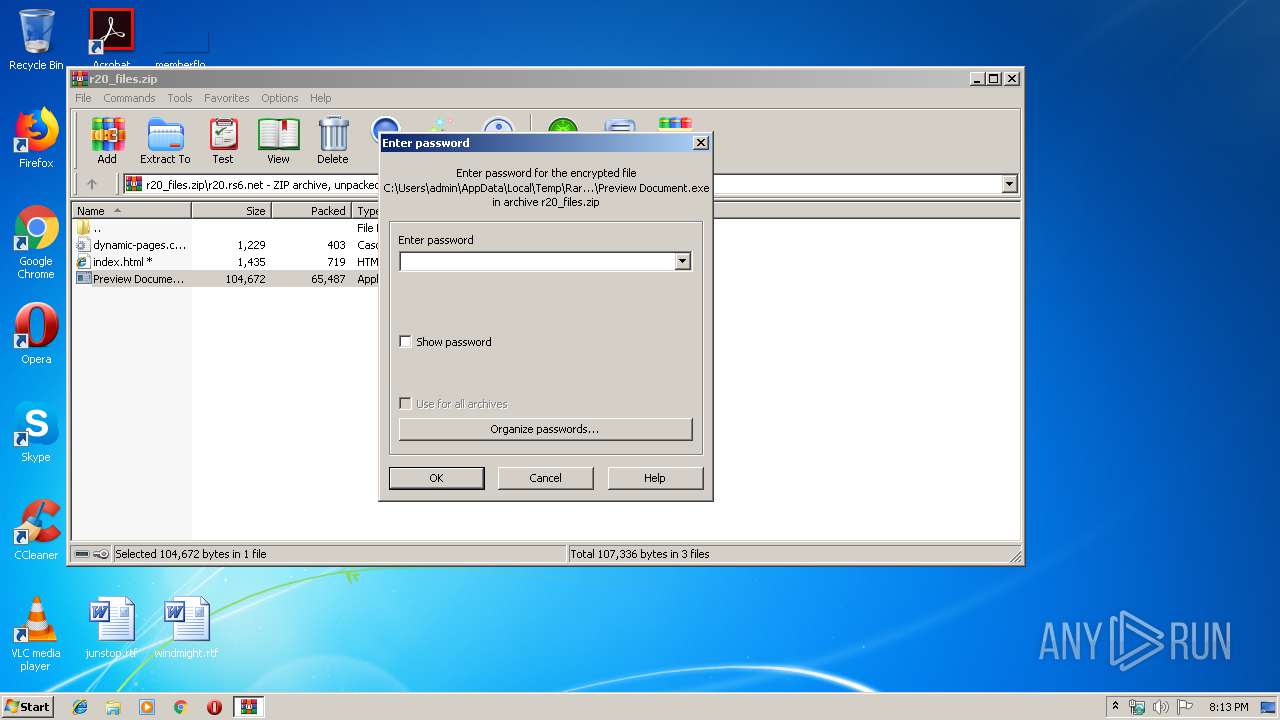
| 2344 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2576.21102\r20.rs6.net\Preview Document.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2576.21102\r20.rs6.net\Preview Document.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
| 2416 | "C:\Users\admin\AppData\Roaming\syshealth\E348.exe" | C:\Users\admin\AppData\Roaming\syshealth\E348.exe | — | DllHost.exe | |||||||||||
User: admin Integrity Level: HIGH Description: MDI_Notepad MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2576 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\r20_files.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2604 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3752 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3840 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2604 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 215
Read events
1 106
Write events
109
Delete events
0
Modification events
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\r20_files.zip | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-24585 |
Value: Cascading Style Sheet Document | |||
| (PID) Process: | (2576) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-912 |
Value: HTML Document | |||
Executable files
3
Suspicious files
5
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | E346.exe | C:\Users\admin\AppData\Local\Temp\Cab7C6.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | E346.exe | C:\Users\admin\AppData\Local\Temp\Tar7C7.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | E346.exe | C:\Users\admin\AppData\Local\Temp\Cab7D7.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | E346.exe | C:\Users\admin\AppData\Local\Temp\Tar7D8.tmp | — | |
MD5:— | SHA256:— | |||
| 2604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2208 | E346.exe | C:\Users\admin\AppData\Local\Temp\Cab885.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | E346.exe | C:\Users\admin\AppData\Local\Temp\Tar896.tmp | — | |
MD5:— | SHA256:— | |||
| 3840 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2344 | Preview Document.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@ajeetsinghbaddan[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
5
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2208 | E346.exe | GET | 200 | 34.236.80.17:80 | http://checkip.amazonaws.com/ | US | text | 16 b | malicious |
2208 | E346.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.4 Kb | whitelisted |
2604 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2208 | E346.exe | 185.205.210.121:443 | — | BelCloud Hosting Corporation | BG | malicious |
2604 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2208 | E346.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2208 | E346.exe | 34.236.80.17:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
2344 | Preview Document.exe | 104.27.175.75:443 | ajeetsinghbaddan.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ajeetsinghbaddan.com |
| suspicious |
www.ajeetsinghbaddan.com |
| suspicious |
www.bing.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
checkip.amazonaws.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2208 | E346.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2208 | E346.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex/Trickbot CnC) |
2208 | E346.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2208 | E346.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dyre/Trickbot/Dridex SSL connection |
2208 | E346.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrickBot.Spy SSL connection |
2208 | E346.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dyre/Trickbot/Dridex SSL Connection |
3 ETPRO signatures available at the full report