| download: | /Kidovich/Solara-v3/releases/download/Setup/Solara.rar |
| Full analysis: | https://app.any.run/tasks/099b8132-72e2-418d-9ef3-3b61fdf636c9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 26, 2025, 16:14:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
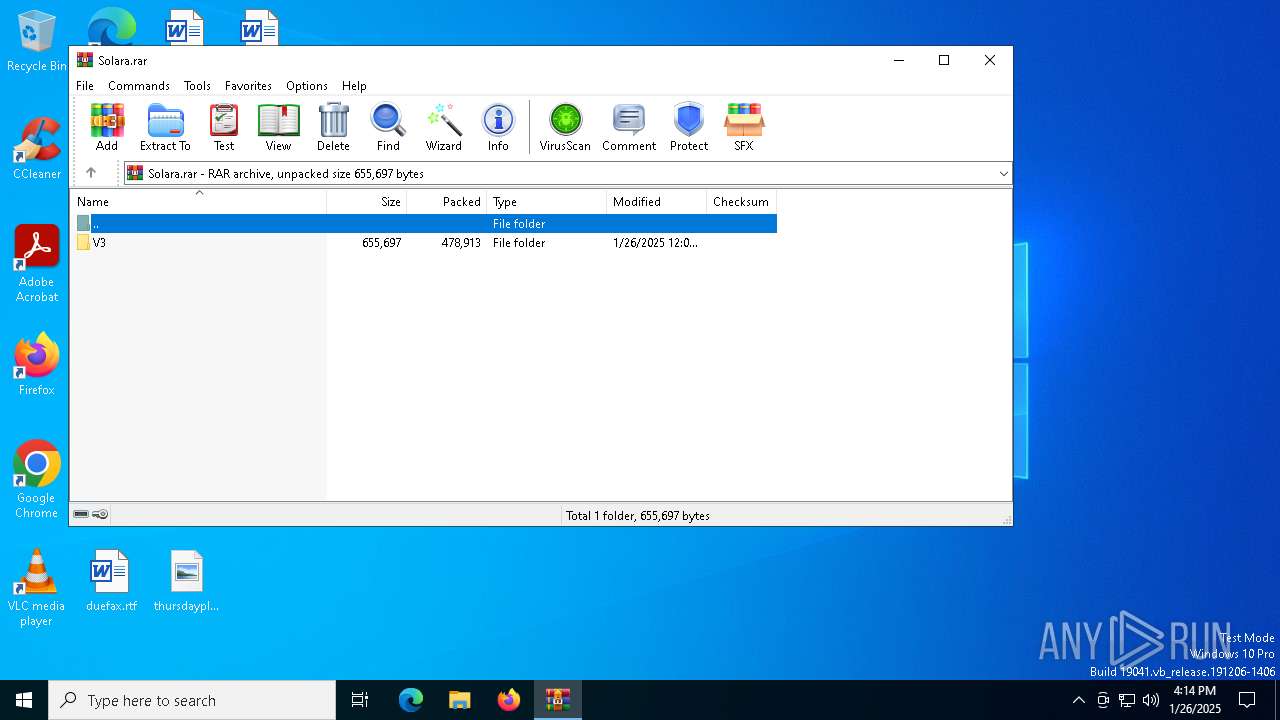
| File info: | RAR archive data, v5 |
| MD5: | 57C33E4430C0A01E796B97698743FA9F |
| SHA1: | C56E681BB9AD0F7227F03ED2C06CEB0902DED72E |
| SHA256: | 8B1F1B8C41417F7AA8A18E4546EC2F6CF987B04F4C05370532C969AD7E1BA957 |
| SSDEEP: | 24576:T6vsWPpY3PV2KW7/eAJJKg18REcFZX2wDV54:T6vsWPpY3PV2KW7/eAJJKg18REcFZX2X |
MALICIOUS
LUMMA has been detected (YARA)
- Solara V3.exe (PID: 3224)
LUMMA mutex has been found
- Solara V3.exe (PID: 3224)
Steals credentials from Web Browsers
- Solara V3.exe (PID: 3224)
Actions looks like stealing of personal data
- Solara V3.exe (PID: 3224)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6476)
Starts a Microsoft application from unusual location
- Solara V3.exe (PID: 3612)
- Solara V3.exe (PID: 6280)
- Solara V3.exe (PID: 6284)
- Solara V3.exe (PID: 3224)
Application launched itself
- Solara V3.exe (PID: 3612)
Executes application which crashes
- Solara V3.exe (PID: 3612)
There is functionality for taking screenshot (YARA)
- Solara V3.exe (PID: 3224)
Searches for installed software
- Solara V3.exe (PID: 3224)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6476)
The sample compiled with english language support
- WinRAR.exe (PID: 6476)
Manual execution by a user
- Solara V3.exe (PID: 3612)
Checks supported languages
- Solara V3.exe (PID: 3612)
- Solara V3.exe (PID: 3224)
Reads the computer name
- Solara V3.exe (PID: 3612)
- Solara V3.exe (PID: 3224)
Reads the software policy settings
- Solara V3.exe (PID: 3224)
- WerFault.exe (PID: 6472)
Creates files or folders in the user directory
- WerFault.exe (PID: 6472)
.NET Reactor protector has been detected
- Solara V3.exe (PID: 3224)
Checks proxy server information
- WerFault.exe (PID: 6472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 434927 |
| UncompressedSize: | 558080 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | V3/Solara V3.exe |
Total processes
136
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3224 | "C:\Users\admin\Desktop\V3\Solara V3.exe" | C:\Users\admin\Desktop\V3\Solara V3.exe | Solara V3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Userinit Logon Application Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | "C:\Users\admin\Desktop\V3\Solara V3.exe" | C:\Users\admin\Desktop\V3\Solara V3.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Userinit Logon Application Exit code: 3221226505 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4872 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6280 | "C:\Users\admin\Desktop\V3\Solara V3.exe" | C:\Users\admin\Desktop\V3\Solara V3.exe | — | Solara V3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Userinit Logon Application Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6284 | "C:\Users\admin\Desktop\V3\Solara V3.exe" | C:\Users\admin\Desktop\V3\Solara V3.exe | — | Solara V3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Userinit Logon Application Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6472 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3612 -s 856 | C:\Windows\SysWOW64\WerFault.exe | Solara V3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Solara.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 976
Read events
4 958
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Solara.rar | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6472 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Solara V3.exe_aeef444bcffc9275c16b253fddca8c36cdaece9_2d2c98f8_62d5cdc6-3e17-4c67-8e1c-7a54fa22d7eb\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6472 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Solara V3.exe.3612.dmp | — | |
MD5:— | SHA256:— | |||
| 6476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6476.39562\V3\mqutil.dll | executable | |
MD5:7D326B235AB064FF70376F1D015CC084 | SHA256:404DDA0BDF9A6C1C61653CF7E965F504B3A3A3B662F88C906AAA19A9C3DF160C | |||
| 6476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6476.39562\V3\mlhelps.dll | binary | |
MD5:9ABD95D760A752257BCB7F5EE3C14008 | SHA256:D9050E97477CFE7BE44992A505C2CDAD8F0F43A3C0BF0E1E1A3D1F175D92AC51 | |||
| 6472 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:680B0331A3CC8FCCE16367586EC7A721 | SHA256:19F1B5D2C7F62663C14D97578411DC610E5F33E6CE4165977314442435F15305 | |||
| 6472 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 6472 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER85FD.tmp.WERInternalMetadata.xml | binary | |
MD5:0A5EA4FE7910C27AA2B27941D7FBB800 | SHA256:75DB0271E1D5711564AD062A04B4DB41C68A7F2D7A3351F1CBC2BCBC6A0927ED | |||
| 6476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6476.39562\V3\lib.dll | binary | |
MD5:F3078D7CBE7D330F06C51DC177F58E6F | SHA256:83B293AF5AE8FA2F226DC86C4B9AEB5F6AF41880EB72C55C895C2AB445B0BBD9 | |||
| 6472 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:5929BC8C0CBA2F12CDB3FDFF304DBC19 | SHA256:0B8D184DDFFAD2C15673D792BF23EEA4E9140FF838170DFF8B72F14FDD7A4D49 | |||
| 6472 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:5DB006A56FCCBFB4B4B46B975C38C4C0 | SHA256:1A032767C4077C1B7A042D827657021759D03D1994FA94172C3B55CEB02E9169 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6472 | WerFault.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6472 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6432 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5868 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5868 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3224 | Solara V3.exe | 172.67.178.239:443 | innerkomen.com | CLOUDFLARENET | US | unknown |
6472 | WerFault.exe | 20.42.65.92:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6472 | WerFault.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
innerkomen.com |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |