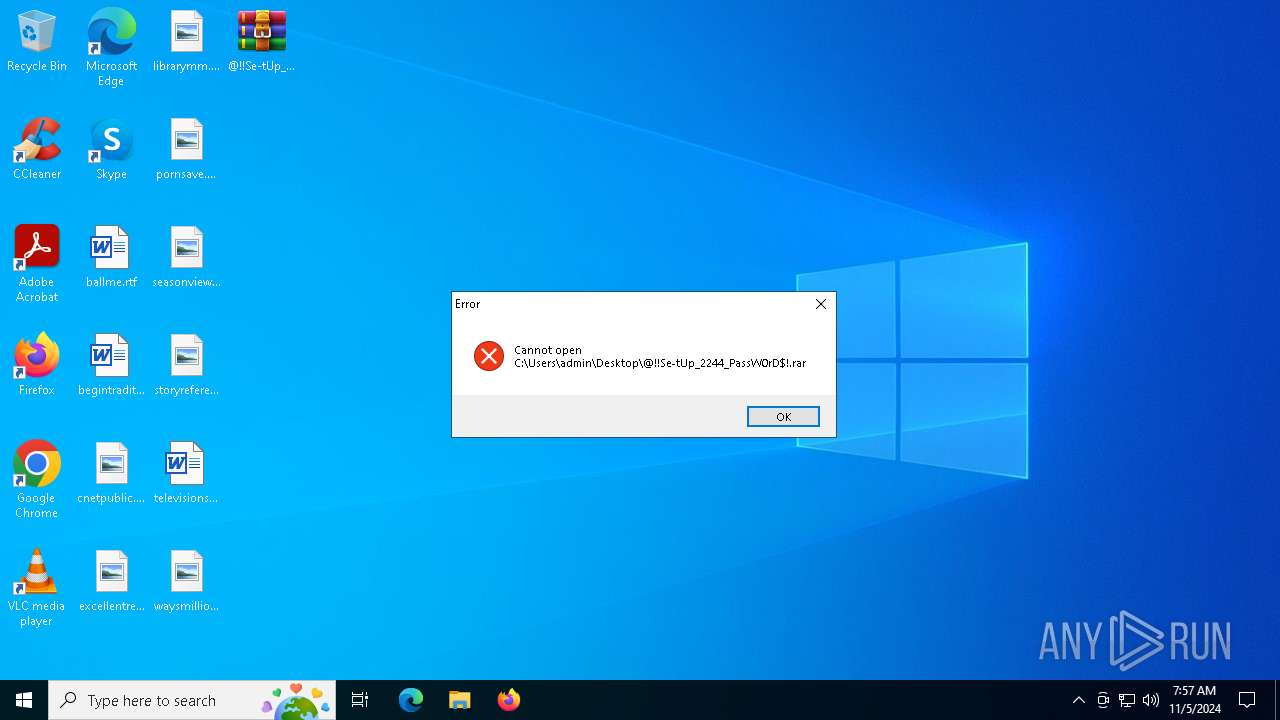
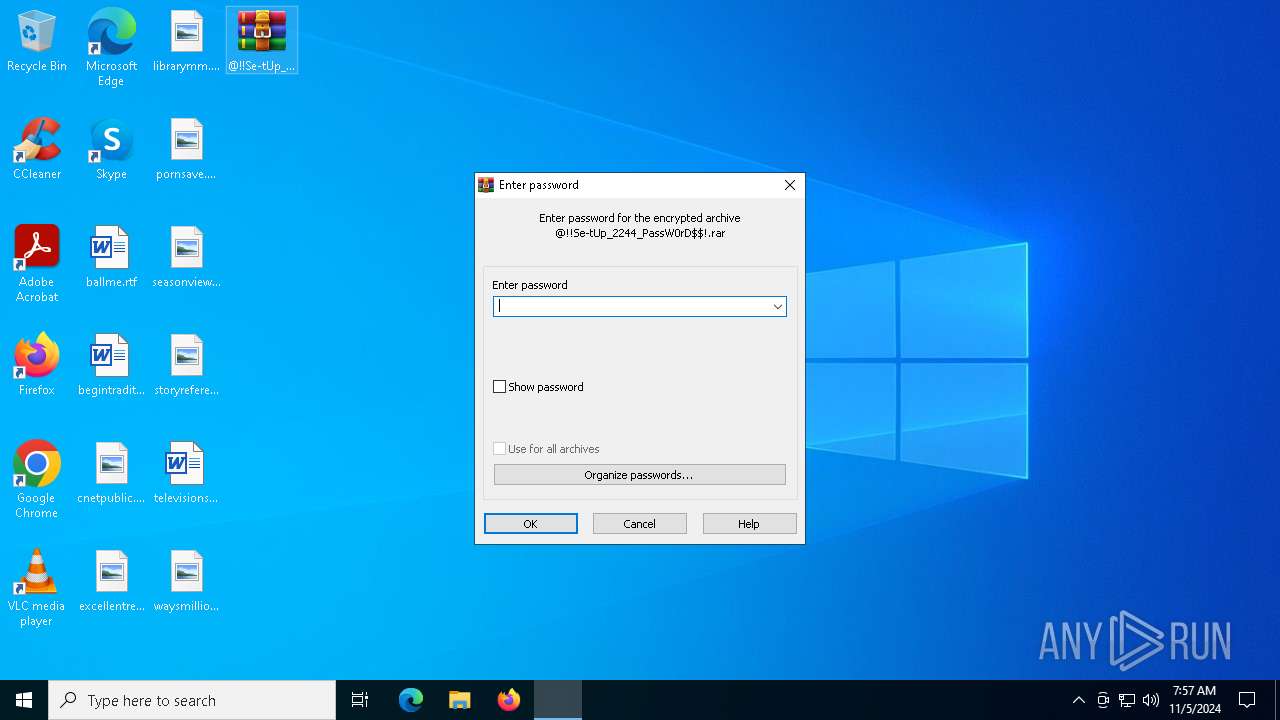
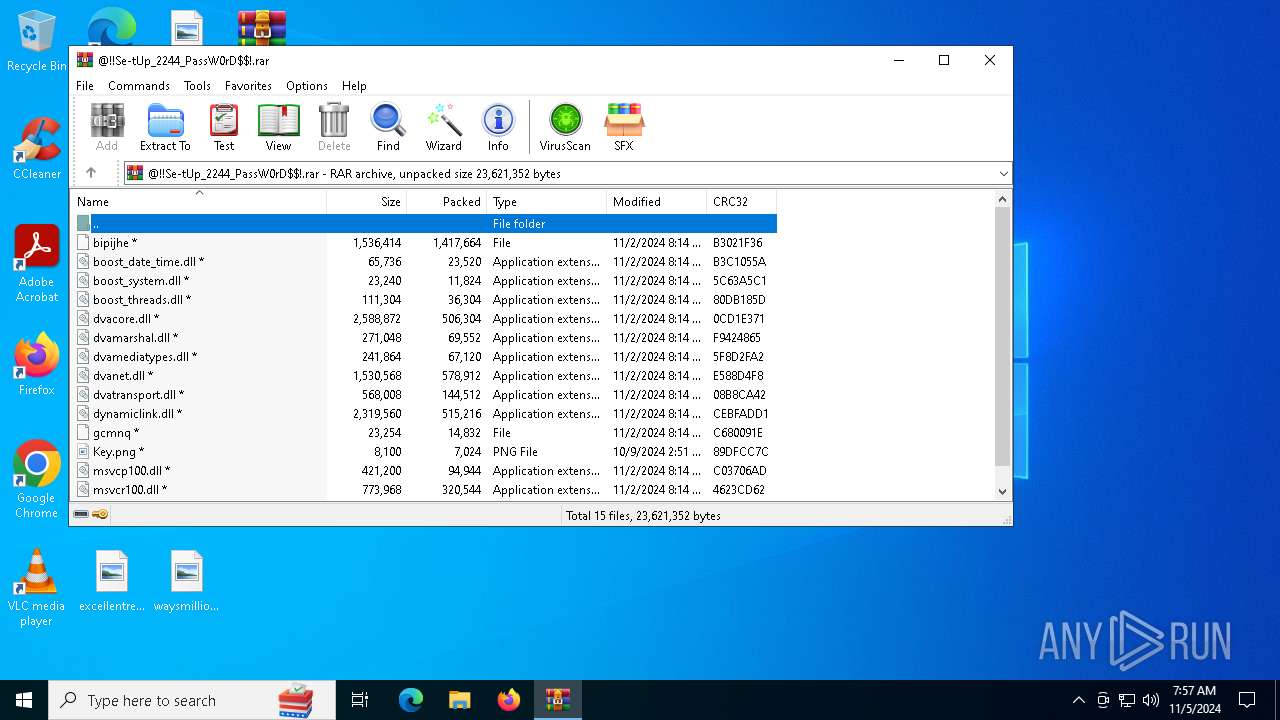
| File name: | @!!Se-tUp_2244_PassW0rD$!.rar |
| Full analysis: | https://app.any.run/tasks/efcb60bd-4006-436c-a86c-2d2193266d06 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 05, 2024, 07:57:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0288709E9ABEB331D93B022944CFFD2A |
| SHA1: | 90EC578579999E4F9221CE7F5530426A5F180693 |
| SHA256: | 8AA6804E6F2075B042C2CAE7FE71E83B246B04018F909B5ACF98165BEC6DB9E2 |
| SSDEEP: | 98304:9IIGUikrbUqHohhkOFlbDTjArllgdILd+WeiGs/iWY+fuY3rVglj3WPFyg6l4ALI:CkM3Z51LNCtD |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2172)
- explorer.exe (PID: 540)
LUMMA has been detected (SURICATA)
- Kleenka.pif (PID: 2312)
- svchost.exe (PID: 2172)
Changes powershell execution policy (Bypass)
- Kleenka.pif (PID: 2312)
Bypass execution policy to execute commands
- powershell.exe (PID: 7152)
Stealers network behavior
- svchost.exe (PID: 2172)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 540)
SUSPICIOUS
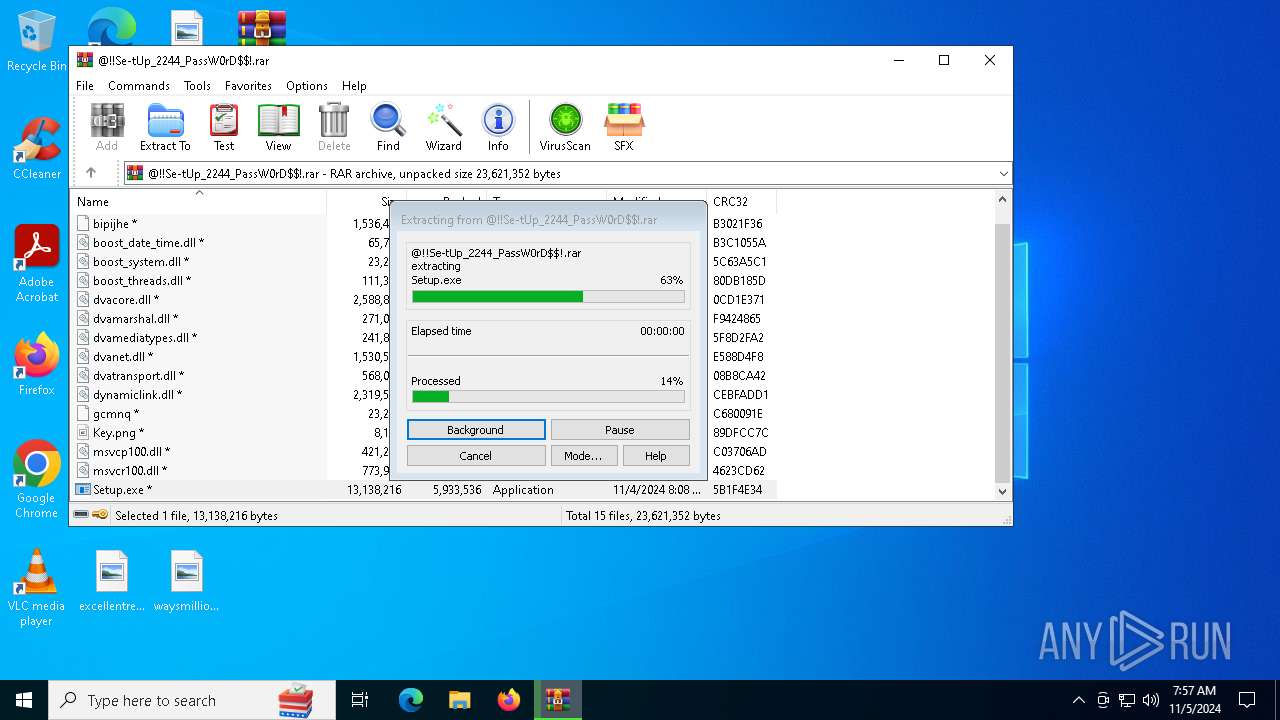
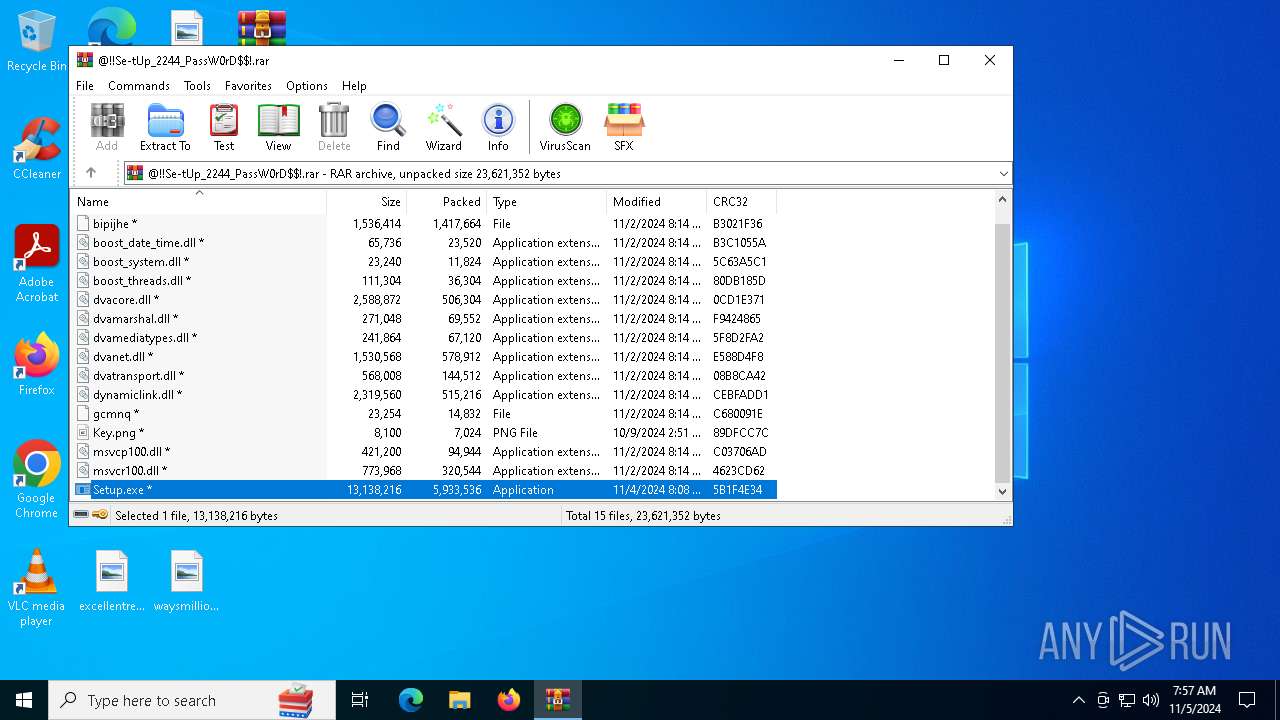
Executable content was dropped or overwritten
- choice.exe (PID: 2708)
- Setup.exe (PID: 6724)
- Kleenka.pif (PID: 2312)
- AutoIt3.exe (PID: 3644)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3764)
Starts application with an unusual extension
- choice.exe (PID: 2708)
Contacting a server suspected of hosting an CnC
- Kleenka.pif (PID: 2312)
- svchost.exe (PID: 2172)
- explorer.exe (PID: 540)
The process executes Powershell scripts
- Kleenka.pif (PID: 2312)
Starts POWERSHELL.EXE for commands execution
- Kleenka.pif (PID: 2312)
Starts itself from another location
- Kleenka.pif (PID: 2312)
There is functionality for communication over UDP network (YARA)
- RVRQ7VQ4T65IAQIJN.exe (PID: 6204)
Found regular expressions for crypto-addresses (YARA)
- MicrosoftEdgeUpdateCore.exe (PID: 6568)
Connects to unusual port
- MicrosoftEdgeUpdateCore.exe (PID: 6568)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3764)
Manual execution by a user
- WinRAR.exe (PID: 3764)
Application based on Golang
- MicrosoftEdgeUpdateCore.exe (PID: 6568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
142
Monitored processes
20
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | C:\WINDOWS\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | choice.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | nc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2312 | C:\Users\admin\AppData\Roaming\Kleenka.pif | C:\Users\admin\AppData\Roaming\Kleenka.pif | choice.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\@!!Se-tUp_2244_PassW0rD$!.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 2708 | C:\WINDOWS\SysWOW64\choice.exe | C:\Windows\SysWOW64\choice.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\Temp\G9AU8U\AutoIt3.exe" "C:\Users\admin\AppData\Local\Temp\G9AU8U\Afflicted.a3x" | C:\Users\admin\AppData\Local\Temp\G9AU8U\AutoIt3.exe | Kleenka.pif | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
| 3764 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\@!!Se-tUp_2244_PassW0rD$!.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4408 | C:\Users\admin\AppData\Roaming\acon\YJBDCGJZXFUAIWRZOCBOFPZK\nc.exe | C:\Users\admin\AppData\Roaming\acon\YJBDCGJZXFUAIWRZOCBOFPZK\nc.exe | — | Setup.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.3810.9 Modules
| |||||||||||||||
| 4432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | choice.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 127
Read events
12 097
Write events
30
Delete events
0
Modification events
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000004602040000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000680204000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (2648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F00000000000000000000000000000000000000000009E0204000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\@!!Se-tUp_2244_PassW0rD$!.rar | |||
Executable files
17
Suspicious files
10
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2708 | choice.exe | C:\Users\admin\AppData\Local\Temp\mjsjudquyx | — | |
MD5:— | SHA256:— | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\dvamarshal.dll | executable | |
MD5:4160806637A8913BD1917D00D1845018 | SHA256:8B0828A82448079B9936A317775AFAECE313679241442EA4EBD1CA06BE64D10D | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\dvatransport.dll | executable | |
MD5:C56CB2A849C920137088A6191D86C6BC | SHA256:5E12D3CF38ED4CAC63129F421633E2E78548722EC3ED34B6463A6840DB01A59F | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\dvanet.dll | executable | |
MD5:5790ABD90395C121EFA8B6D7A615F050 | SHA256:6C154B0E07F2A7A8DAFBCA6610FFC4B50899ED815A3A27F8F9F87D5EB99F1ADD | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\msvcp100.dll | executable | |
MD5:BC83108B18756547013ED443B8CDB31B | SHA256:B2AD109C15EAA92079582787B7772BA0A2F034F7D075907FF87028DF0EAEA671 | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\dvamediatypes.dll | executable | |
MD5:0641560E5ECD1702AA259AC8C48577E1 | SHA256:3FAA936558703316EDBFB0D57D697F0ED160149B1417F4D5D02D9EF3576FF779 | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\boost_system.dll | executable | |
MD5:CEF0081A028FDA210C1AD6417865CC95 | SHA256:4F3A1C28B3A15E6FBB3EA635B2C43FEA7DE4A797543B5CF2142FE6B0240F2C5F | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\boost_threads.dll | executable | |
MD5:44D1D2711F5FF5C0D5A566BEEED1FBE2 | SHA256:882F809095A5A2B8BE3C5A26D5882632D99B0622DB904DCA3FFCB48FD093D91C | |||
| 6724 | Setup.exe | C:\Users\admin\AppData\Local\Temp\7cf9ebd2 | image | |
MD5:D0C7C8492CBDC1656F76DB3EF16B9738 | SHA256:9264CE029A9AF385FCA15C2864D14520D3CBA1CD752A7BD1994BD18E6F4952F2 | |||
| 3764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3764.26162\Key.png | image | |
MD5:E7B140B81385DCFE2F10BC3A7AB27797 | SHA256:6991524FB4F77F0B62566D05AB00C08632DE14A70C73BC78911485390CF6325A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
53
DNS requests
31
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6228 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3960 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2312 | Kleenka.pif | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2312 | Kleenka.pif | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
540 | explorer.exe | POST | 200 | 104.21.23.211:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4836 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 2.23.209.176:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (proggresinvj .cyou) |
2312 | Kleenka.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (proggresinvj .cyou in TLS SNI) |
2312 | Kleenka.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (proggresinvj .cyou in TLS SNI) |
2312 | Kleenka.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (proggresinvj .cyou in TLS SNI) |
2312 | Kleenka.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (proggresinvj .cyou in TLS SNI) |
2312 | Kleenka.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (proggresinvj .cyou in TLS SNI) |
2312 | Kleenka.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (proggresinvj .cyou in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
7 ETPRO signatures available at the full report