| File name: | KMSPICO.exe |
| Full analysis: | https://app.any.run/tasks/5dcf5ae4-9062-4a78-a90e-ee5783e29999 |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | July 10, 2025, 12:13:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 1C6EB8A6F72CCB74A5B07658B2273FC2 |
| SHA1: | C7F22E03B4D5087690C1890964E1258BD370B197 |
| SHA256: | 8A5850BB9793850879C2D4C5C040E120F404032161CF37D21FF5305601BF0B8C |
| SSDEEP: | 98304:RrL6kpKqPmNv+ziDArd2zWQRkDcHxV7OTx01nlBkCiPiH4O0j4vAsN01XcaMBoBI:8e1pB0Prp1b |
MALICIOUS
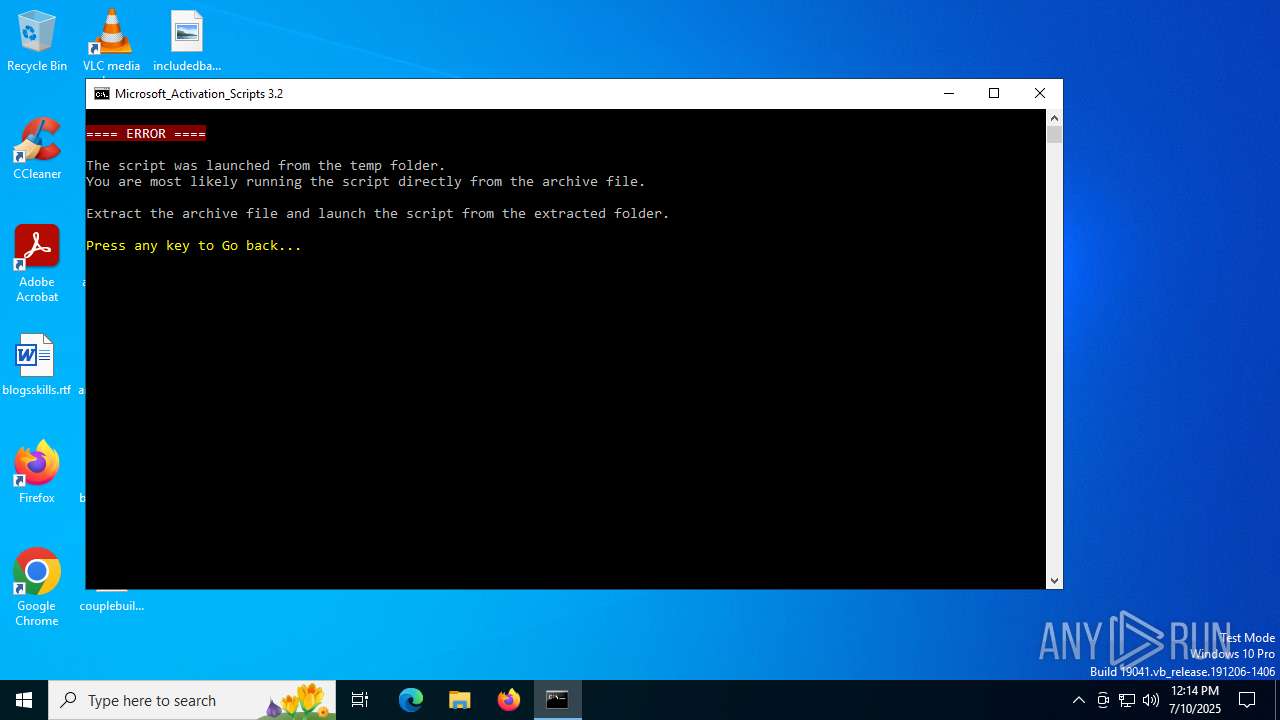
Executing a file with an untrusted certificate
- Soft.exe (PID: 4788)
- svchost015.exe (PID: 2620)
- pmKZgMw7LF7.exe (PID: 728)
- ObpH3uOpC.exe (PID: 6140)
- ObpH3uOpC.exe (PID: 1760)
GCLEANER has been detected (YARA)
- svchost015.exe (PID: 2620)
GCLEANER has been detected (SURICATA)
- svchost015.exe (PID: 2620)
Registers / Runs the DLL via REGSVR32.EXE
- ObpH3uOpC.tmp (PID: 6552)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- pmKZgMw7LF7.exe (PID: 728)
Connects to the CnC server
- svchost.exe (PID: 2200)
LUMMA mutex has been found
- pmKZgMw7LF7.exe (PID: 728)
Actions looks like stealing of personal data
- pmKZgMw7LF7.exe (PID: 728)
Steals credentials from Web Browsers
- pmKZgMw7LF7.exe (PID: 728)
TOFSEE has been detected (SURICATA)
- regsvr32.exe (PID: 5232)
SUSPICIOUS
Executable content was dropped or overwritten
- KMSPICO.exe (PID: 3400)
- Soft.exe (PID: 4788)
- svchost015.exe (PID: 2620)
- tSRwBW7YMRC.exe (PID: 6652)
- tSRwBW7YMRC.tmp (PID: 6572)
- xmldriveimage681.exe (PID: 6820)
- ObpH3uOpC.exe (PID: 6140)
- ObpH3uOpC.tmp (PID: 7160)
- ObpH3uOpC.exe (PID: 1760)
- ObpH3uOpC.tmp (PID: 6552)
Reads the date of Windows installation
- KMSPICO.exe (PID: 3400)
Reads security settings of Internet Explorer
- KMSPICO.exe (PID: 3400)
- svchost015.exe (PID: 2620)
- xmldriveimage681.exe (PID: 6820)
- ObpH3uOpC.tmp (PID: 7160)
There is functionality for taking screenshot (YARA)
- Soft.exe (PID: 4788)
- KMSPICO.exe (PID: 3400)
- svchost015.exe (PID: 2620)
Executing commands from ".cmd" file
- KMSPICO.exe (PID: 3400)
- cmd.exe (PID: 4236)
Starts CMD.EXE for commands execution
- KMSPICO.exe (PID: 3400)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 6812)
Starts SC.EXE for service management
- cmd.exe (PID: 4236)
Windows service management via SC.EXE
- sc.exe (PID: 2760)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4236)
Application launched itself
- cmd.exe (PID: 4236)
- cmd.exe (PID: 6812)
Potential Corporate Privacy Violation
- svchost015.exe (PID: 2620)
Reads the Windows owner or organization settings
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.tmp (PID: 7160)
- ObpH3uOpC.tmp (PID: 6552)
Process drops legitimate windows executable
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.tmp (PID: 7160)
- ObpH3uOpC.tmp (PID: 6552)
Connects to the server without a host name
- svchost015.exe (PID: 2620)
Starts POWERSHELL.EXE for commands execution
- xmldriveimage681.exe (PID: 6820)
- regsvr32.exe (PID: 5232)
The process drops C-runtime libraries
- tSRwBW7YMRC.tmp (PID: 6572)
The process hide an interactive prompt from the user
- regsvr32.exe (PID: 5232)
The process bypasses the loading of PowerShell profile settings
- regsvr32.exe (PID: 5232)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2200)
- pmKZgMw7LF7.exe (PID: 728)
- regsvr32.exe (PID: 5232)
Detected use of alternative data streams (AltDS)
- regsvr32.exe (PID: 5232)
Connects to SMTP port
- regsvr32.exe (PID: 5232)
Connects to unusual port
- regsvr32.exe (PID: 5232)
The process executes via Task Scheduler
- regsvr32.exe (PID: 4844)
Searches for installed software
- pmKZgMw7LF7.exe (PID: 728)
INFO
Checks supported languages
- KMSPICO.exe (PID: 3400)
- Soft.exe (PID: 4788)
- svchost015.exe (PID: 2620)
- tSRwBW7YMRC.exe (PID: 6652)
- tSRwBW7YMRC.tmp (PID: 6572)
- xmldriveimage681.exe (PID: 6820)
- ObpH3uOpC.tmp (PID: 7160)
- ObpH3uOpC.exe (PID: 6140)
- ObpH3uOpC.tmp (PID: 6552)
- ObpH3uOpC.exe (PID: 1760)
- XMLDriveImage.exe (PID: 6400)
- pmKZgMw7LF7.exe (PID: 728)
Create files in a temporary directory
- KMSPICO.exe (PID: 3400)
- Soft.exe (PID: 4788)
- tSRwBW7YMRC.exe (PID: 6652)
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.exe (PID: 6140)
- ObpH3uOpC.tmp (PID: 7160)
- ObpH3uOpC.tmp (PID: 6552)
- ObpH3uOpC.exe (PID: 1760)
Process checks computer location settings
- KMSPICO.exe (PID: 3400)
- xmldriveimage681.exe (PID: 6820)
- ObpH3uOpC.tmp (PID: 7160)
Reads the computer name
- KMSPICO.exe (PID: 3400)
- svchost015.exe (PID: 2620)
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.tmp (PID: 7160)
- xmldriveimage681.exe (PID: 6820)
- ObpH3uOpC.tmp (PID: 6552)
- XMLDriveImage.exe (PID: 6400)
- pmKZgMw7LF7.exe (PID: 728)
The sample compiled with english language support
- KMSPICO.exe (PID: 3400)
- Soft.exe (PID: 4788)
- svchost015.exe (PID: 2620)
- xmldriveimage681.exe (PID: 6820)
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.tmp (PID: 7160)
- ObpH3uOpC.tmp (PID: 6552)
Compiled with Borland Delphi (YARA)
- Soft.exe (PID: 4788)
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.tmp (PID: 6552)
Checks operating system version
- cmd.exe (PID: 4236)
Checks proxy server information
- svchost015.exe (PID: 2620)
- slui.exe (PID: 4192)
Reads the machine GUID from the registry
- svchost015.exe (PID: 2620)
- pmKZgMw7LF7.exe (PID: 728)
Reads the software policy settings
- svchost015.exe (PID: 2620)
- pmKZgMw7LF7.exe (PID: 728)
- slui.exe (PID: 4192)
Creates files or folders in the user directory
- svchost015.exe (PID: 2620)
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.tmp (PID: 6552)
Creates files in the program directory
- xmldriveimage681.exe (PID: 6820)
Changes the registry key values via Powershell
- xmldriveimage681.exe (PID: 6820)
Creates a software uninstall entry
- tSRwBW7YMRC.tmp (PID: 6572)
Manual execution by a user
- XMLDriveImage.exe (PID: 6400)
Detects InnoSetup installer (YARA)
- tSRwBW7YMRC.exe (PID: 6652)
- tSRwBW7YMRC.tmp (PID: 6572)
- ObpH3uOpC.exe (PID: 1760)
- ObpH3uOpC.tmp (PID: 6552)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1800)
- powershell.exe (PID: 5768)
Application launched itself
- chrome.exe (PID: 6372)
- chrome.exe (PID: 3000)
- msedge.exe (PID: 6372)
- chrome.exe (PID: 6776)
- chrome.exe (PID: 440)
- msedge.exe (PID: 7392)
- msedge.exe (PID: 6668)
- msedge.exe (PID: 6380)
- msedge.exe (PID: 6352)
- msedge.exe (PID: 7372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:20 10:01:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 307200 |
| InitializedDataSize: | 208384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32690 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
239
Monitored processes
100
Malicious processes
12
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2016,i,339227536937273896,17550948182919451682,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=2008 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3776,i,4305386634092348621,13363930377520407598,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3792 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | pmKZgMw7LF7.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Users\admin\AppData\Roaming\khXhM\pmKZgMw7LF7.exe" | C:\Users\admin\AppData\Roaming\khXhM\pmKZgMw7LF7.exe | svchost015.exe | ||||||||||||
User: admin Company: Heaventools Software Integrity Level: MEDIUM Description: PE Explorer Setup Exit code: 0 Version: 1.99.6.1400 Modules
| |||||||||||||||
| 856 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2000,i,16145313269972219927,17029531572792406574,262144 --variations-seed-version --mojo-platform-channel-handle=1984 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 952 | find /i "RUNNING" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3244,i,4305386634092348621,13363930377520407598,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3256 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1068 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 993
Read events
42 814
Write events
142
Delete events
37
Modification events
| (PID) Process: | (2620) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2620) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2620) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.1 (a) | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681 | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\XML Drive Image 0.58.0.4681\ | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: English | |||
| (PID) Process: | (6572) tSRwBW7YMRC.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\XML Drive Image_is1 |
| Operation: | write | Name: | DisplayName |
Value: XML Drive Image 0.58.0.4681 | |||
Executable files
45
Suspicious files
182
Text files
212
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2620 | svchost015.exe | C:\Users\admin\AppData\Roaming\khXhM\pmKZgMw7LF7.exe | executable | |
MD5:BE138AB308FA5F7B9BAECAE7B592A02C | SHA256:84BA2DE9ACCB2BC0714E1B28A7666436A97C6CF154ECC015B71894CE45D6720A | |||
| 2620 | svchost015.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:6820EE75B54FD7428654CE55E0EAB6FE | SHA256:2371A78A0FE50E821193BFC85C12E8B79D34285BBF55A56FBE65A1B485B0CD55 | |||
| 2620 | svchost015.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:BCE324C5AF0D35D723C9D1CA03A57171 | SHA256:A894F27EE0265437BD2AAE02AD7CF888F7A6FF6E899588634FD089D7137EB0C6 | |||
| 2620 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\fuckingdllENCR[1].dll | binary | |
MD5:4BC1EF6688690AF3DD8D3D70906A9F98 | SHA256:7703A6B77C0B0935F5900A2D846CFA3AB59B46D03A1A0844F6BCB5CF9496B2FE | |||
| 3400 | KMSPICO.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\MAS_AIO.cmd | text | |
MD5:51D1A565DAFB87D618FEC0487618DADD | SHA256:99B9D8E20701DDCA02676146F7878ECC79BC403CB7B51FBB1B15B2D8D8BC64C4 | |||
| 2620 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\text[1] | text | |
MD5:8E20D4A9B35A38CC167A3AF60AAE86EA | SHA256:9540DF47A22B6F4321DDF19EDB258922B91A91AC407F2DD507AF72C5F55CE6E1 | |||
| 4788 | Soft.exe | C:\Users\admin\AppData\Local\Temp\svchost015.exe | executable | |
MD5:CEEAE1523C3864B719E820B75BF728AA | SHA256:4E04E2FB20A9C6846B5D693EA67098214F77737F4F1F3DF5F0C78594650E7F71 | |||
| 2620 | svchost015.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2A42127F349D54E7AA939366FF86F74E_F6AD3ACFD3F6A32178BCCDCB3AF6610B | der | |
MD5:C71D1E14C55AF58CC8AE9A7FB68696CC | SHA256:B99EE9AEBE10A44B4EE7B210A3675C7DF19D193591433887BEA809FA408C4854 | |||
| 4788 | Soft.exe | C:\Users\admin\AppData\Local\Temp\svc9F2E.tmp | executable | |
MD5:091B95923E305D04A6AB93A2F7F6B3AB | SHA256:1CA7BE07E6DC3F58FE3DAD8C91AE68845A5373F8C71C8E4F87F9A1BCEE845693 | |||
| 2620 | svchost015.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
191
DNS requests
156
Threats
51
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.15:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2620 | svchost015.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2620 | svchost015.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2620 | svchost015.exe | GET | 200 | 142.250.185.131:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEEjyOcDij0ECCQHn9DSrJo0%3D | unknown | — | — | whitelisted |
6528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2620 | svchost015.exe | GET | 200 | 176.46.157.48:80 | http://176.46.157.48/success?substr=two&s=uniq&sub=none | unknown | — | — | unknown |
6528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2620 | svchost015.exe | GET | 200 | 176.46.157.48:80 | http://176.46.157.48/info | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6980 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.15:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2764 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2764 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2620 | svchost015.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
2620 | svchost015.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
2620 | svchost015.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
2620 | svchost015.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
2620 | svchost015.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2620 | svchost015.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2620 | svchost015.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2620 | svchost015.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
2620 | svchost015.exe | Misc activity | ET INFO Packed Executable Download |